Chapter 15: Testing and Auditing
In this chapter, we will provide details about testing and auditing your environment, which will help validate controls and ensure due diligence has been executed within your security program. The challenge we face when deploying security controls, hardening configurations, and security baselines, is validating that they are in place and working as designed. The security department may have obligations to the leadership team, board stakeholders, shareholders, and regulators to prove that you have implemented the appropriate recommended controls depending on your business or industry. This is where testing and auditing comes into play by helping provide evidence that controls are in place. These activities can be performed internally or through a third-party company for added benefit. We test to ensure that our controls are doing what they are designed to do. Without testing, we fail to validate whether the controls work, and can't truly understand our risk level.
The first section will cover the validation of controls within your environment by reviewing the different types of audits and assessments. We will discuss vendor management and the importance of ensuring vendors meet the agreed-upon controls. This due diligence requires collecting and reviewing vendor questionnaires and security audits. We will also review the Microsoft Defender for Cloud regulatory compliance section to measure the status of your Microsoft environment against common regulations.
In the following section, we will review vulnerability scanning to confirm that your implemented controls and configurations are working correctly. We will look at the different scanning types, including scanning options within Azure. Next, we will provide an overview of penetration testing and review the different methodologies and steps taken as part of test execution. Finally, we will review security awareness, training and testing, and the importance of this program within your environment.
In this chapter, we will cover the following topics:
- Validating security controls
- Vulnerability scanning overview
- Planning for penetration testing
- An insight into security awareness, training, and testing
Technical requirements
To follow along with the overviews and instructions in this chapter, the following requirements are recommended:
- A Microsoft cloud services account to access the Service Trust Portal
- An Azure subscription with contributor rights
- Microsoft Defender for Cloud
- Microsoft Defender for Endpoint
- Microsoft 365 E5
- Microsoft Defender for Office 365 Plan 2
Let's start by looking at validating your environment controls.
Validating security controls
Validating that controls are in place is a significant task in the security program and one that should not be neglected. Building a validation program to ensure the documented controls are enforced will help provide additional certainty and peace of mind. Having a second set of eyes to review anything you implement in the IT and security fields is always a good idea. This doesn't necessarily mean an incident will never happen, but it does show that you are executing due diligence and doing what is right.
In addition, it's important to validate that the vendors you partner with also maintain the same level of detail in protecting their environments. The more we move data to vendor-managed cloud and SaaS services, the more due diligence is needed to audit access and validate controls in the vendor's environment. This is changing the dynamics of how we work in security compared to the standard model of hosting data internally on-premises. Having a detailed vendor onboarding process that includes collaboration with other business teams, such as the legal and procurement department, helps to ensure the due diligence process is completed thoroughly.
First, let's look at auditing and review the different types of audits and compliance reports.
Audit types
Auditing is the process that checks the intended controls are in place. At a high level, you will typically see two types of audits:
- An internal audit is one that is completed by an internal team employed by the organization to conduct audits within the business.
- An external audit is completed by a third-party company. The idea behind an external audit is to avoid any conflict of interest within the organization by using an independent party with no ties to the organization. Depending on your company's industry, this could be a legal requirement.
Commonly seen in an internal audit scenario, the auditing team reports directly to the CEO or the board of directors and not internally to the IT or security department. This helps ensure accountability, prevents any conflicts of interest, and provides a system of checks and balances.
When looking at audits, one of the more common practices and well-known reporting offerings is the System and Organization Controls (SOC)—not to be confused with the security operations center. The SOC services are part of the American Institute of Certified Public Accountants (AICPA). It's a good idea to become more accustomed to SOC and other auditing standards within the industry, especially as you look to adopt more cloud services. As you meet with vendors and subscribe to services, it's important that these reports have been completed and the controls are in place for your vendors. Let's review SOC reports in more detail.
SOC reports
There are three different SOC reports to be familiar with:
- SOC 1 reports focus on the financial aspect of an organization, ensuring the correct financial controls and reporting are in place. This report comes with two types of reports:
- SOC 2 reports are focused more on the technology and security aspects of an organization to better protect users' data and reduce risk. The specific controls measured include security, availability, processing integrity, confidentiality, and privacy. Like SOC 1, there is a type 1 and type 2 report that follows the same format. SOC 2 reports are intended for internal use only and vendors will require a non-disclosure agreement (NDA) to be signed to view them.
- SOC 3 reports take the output of SOC 2 reports and write them in a more readable format that is less technical. This allows them to be made available for anyone to access and view.
You can view more information about the AICPA SOC services at https://www.aicpa.org/soc.
Important Note
ISO/IEC 27000 is another common certification family to ensure best practices are implemented as part of your security program. The ISO/IEC certification is used more widely internationally than SOC. You can view more information about the ISO/IEC standards at https://www.iso.org/isoiec-27001-information-security.html.
Even if your business is not required to complete an audit, it may be a good idea to go through the process of a SOC engagement to ensure you are maintaining the highest level of standards for the organization. Next, let's look at managing the risk inherited by conducting business with third parties.
Vendor risk management
The job of managing vendors can be quite a challenge for organizations. Onboarding vendors can be a thorough and lengthy process involving different departments, such as legal and procurement, to help ensure contracts are written and executed correctly to reduce any liability. As more services shift to third-party cloud-based vendors that host our user and customer data, the onboarding process must be more rigorous than ever before. This becomes even more challenging as you need to deal with both current and new privacy requirements. As part of the onboarding process, the right personnel from both the technical and security teams should also be included for review. Nowadays, there are probably very few contracts that don't include some use of technology and I'd imagine that at some point, all contracts with vendors will involve technology that needs to be reviewed by the technical and security teams.
From a technical and security standpoint, one recommendation is to implement a security questionnaire or risk assessment that can help assess and better understand the vendor being onboarded. To assist with this, a couple of third-party questionnaires that are commonly used include the following:
- The Standardized Information Gathering (SIG) questionnaire, provided by Shared Assessments: https://sharedassessments.org/sig/
- The Consensus Assessment Initiative Questionnaire (CAIQ), which is made available by the Cloud Security Alliance (CSA): https://cloudsecurityalliance.org/research/cloud-controls-matrix/
In addition to collecting a questionnaire, you will want to request additional documents to ensure a thorough review and assessment can be completed. This includes the following items:
- Third-party audit reports—for example, a SOC 2 report or ISO 27001 certification
- Penetration test results or any security findings that have been flagged as critical/high-risk
- An information security management program policy or overview
- A business continuity plan , disaster recovery plan, and cybersecurity incident response plan
- Any other supporting audit/risk/security documentation that's available
There are also third-party services that help provide additional insight into your vendor's security posture by means of a security score or grading system. The score is built around scanning publicly available vendor domains and any associated assets reachable over the internet to identify any known vulnerabilities. A couple of examples are as follows:
- SecurityScorecard: https://securityscorecard.com/product/security-ratings
- BitSight: https://www.bitsight.com/third-party-risk-management
Important Note
Vendor risk management is not just a one-time exercise but one that needs a life cycle attached to it. At a minimum, annual reviews should occur as audits and certifications expire.
Next, let's review the Microsoft Service Trust Portal for access to Microsoft's compliance reports.
The Microsoft Service Trust Portal
Microsoft has a public portal dedicated to providing audit and compliance reports for all its cloud services, known as the Service Trust Portal. To visit the Service Trust Portal, go to https://servicetrust.microsoft.com. The landing page will look like the following screenshot:

Figure 15.1 – The Microsoft Service Trust Portal
If you browse through the menu at the top of the web page, the audit-specific documents can be accessed by taking the following steps:
- Ensure you are on the Service Trust Portal home page, found at https://servicetrust.microsoft.com/.
- Click on Trust Documents.
- Click on Audit Reports.
- Scroll down to view the different reports and certificates available.
- Click on the SOC Reports tab under New and Archived Audit Reports to view the SOC-related reports from Microsoft.
- Select the report you would like to view, then sign in with your Microsoft account to access it:

Figure 15.2 – SOC reports for Microsoft
Next, let's look at accessing the Regulatory compliance dashboard in Microsoft Defender for Cloud.
Microsoft Defender for Cloud regulatory compliance
In addition to viewing the reports provided by Microsoft, you can also assess your own cloud environment from within Azure. As part of the Microsoft Defender for Cloud service, there is a Regulatory compliance section that will check your environment configurations against common compliance controls. Not all the controls will be automated, but the feature continues to be enhanced and it is a great tool to help with the assessment. There are many regulatory compliances available for reference, and they can be accessed by taking the following steps:
- Log in to https://portal.azure.com.
- Search for Microsoft Defender for Cloud and open it.
- Click on Regulatory compliance in the left-side menu within the Cloud Security section:
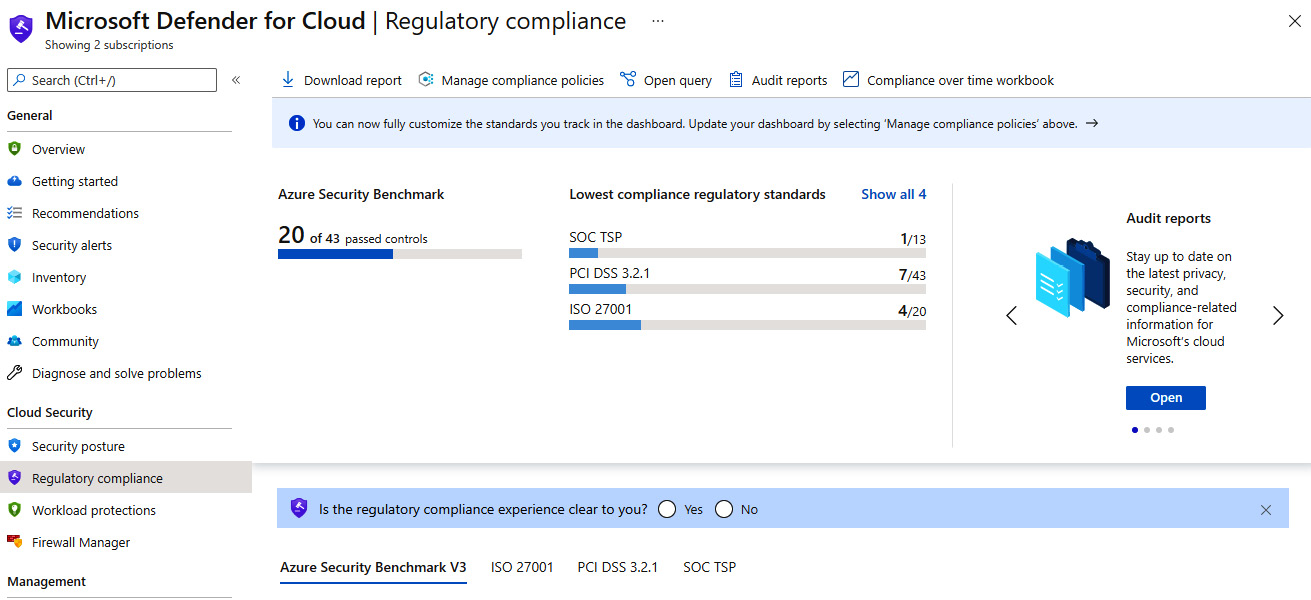
Figure 15.3 – Regulatory compliance dashboard
Important Note
To use the Regulatory compliance feature, you will need to upgrade your Microsoft Defender for Cloud plan from free to enhanced security features. The current costs can be found at https://azure.microsoft.com/en-us/pricing/details/defender-for-cloud/.
Within the dashboard, you can track individual controls based on assessments run by Defender for Cloud against your Azure resources and view them by control number, resource type, and the number of failed resources.
Next, let's look at using Microsoft On-Demand Assessments (ODA) to provide analysis of IT workloads running services with Microsoft.
Microsoft ODA
For Microsoft customers, as part of your support agreement, you gain access to the support hub called the Services Hub. The Services Hub can be accessed by going to https://serviceshub.microsoft.com. Depending on the level of support purchased, you can be granted access to run Microsoft ODA, which helps to analyze the security and performance of environments running on-premises, hybrid, or in the cloud that use Microsoft technology. The result is an output of your controls compared against Microsoft recommended best practices. There are currently over 49 assessments available, including the following:
- Active Directory and Active Directory Security
- Azure Active Directory
- Exchange and SharePoint (on-premises and online)
- Microsoft Endpoint Manager and Microsoft Endpoint Configuration Manager
- Windows Client and Windows Server Security
- SQL Server
To view the full list of available assessments, visit https://docs.microsoft.com/en-us/services-hub/health/.
There are several prerequisites needed to run ODA, and these will vary depending on the assessment you wish to run. Many of them require an active Azure Subscription, Log Analytics workspace, dedicated Windows server, and accounts with permissions to run remote scans against target systems. If you need help, as part of a Microsoft Unified Support agreement, engineers are available to assist you with the setup.
After an assessment is completed, the output includes an overview of all high/low priority recommendations and passed checks. The recommendations can be exported in Excel format for tracking, and an executive summary PowerPoint is available for presentation purposes.

Figure 15.4 – ODA results
You can run the ODA as many times as needed, which will allow you to incorporate the results into your ongoing vulnerability management program to track identified items to resolution.
Next, let's review other options available for validating security and compliance controls.
Other validations
There are many other tools available that offer solutions to help validate controls within your environment. Not all have been covered, but some additional options we have discussed throughout the book include the following:
- CIS-CAT Lite, CIS-CAT Pro Assessor, and CIS CAT Pro Dashboard from the Center for Internet Security (CIS) are assessment tools that will review your systems against CIS benchmarks. With the assessment, you will be provided with a score along with remediation steps for missing controls. CIS-CAT Lite is the free version of the assessment tool versus CIS-CAT Pro, which provides additional benefits such as 80+ available benchmarks and evidence-based reports: https://learn.cisecurity.org/cis-cat-lite.
- The Microsoft Security Compliance Toolkit includes the Policy Analyzer tool for assessing Windows Security Baselines built from GPOs and local group policies compared to current systems settings.
- In Chapter 2, Building a Baseline, we discussed the NIST Cybersecurity Framework. If you implemented NIST, you will need to validate your responses using a third-party vendor to review and assess whether your stated responses are accurate. The NIST website also has some resources on additional tools to help with the implementation and tracking of this framework: https://www.nist.gov/cyberframework/assessment-auditing-resources.
In this section, we reviewed what is needed to validate controls, primarily focusing on auditing and the resources available to complete audits and assessments. In the next section, we will look at vulnerability scanning and testing tools to ensure the hardening of your Windows devices.
Vulnerability scanning overview
While auditing is important for validating that security controls are in place, it's strongly recommended to incorporate a vulnerability scanning program into your security operations. Vulnerability scanning will provide additional insight into your environment by identifying known exploits and weaknesses and raising awareness about how vulnerable your systems are against new and emerging threats. Scan reports can alert IT and security teams where immediate remediation is needed without relying on updated control frameworks. Let's look at what a vulnerability scan involves.
An introduction to vulnerability scanning
Vulnerability scans or assessments look for and identify known vulnerabilities within your environment or systems. For example, a scan might detect that an application, operating system version, or file seen on the network has a known vulnerability. After a scan completes, a report is generated that highlights these weaknesses and includes a list of improvement actions. Vulnerability scans are typically scheduled to run automatically after the initial assessment has been set up. The following is a list of common types of vulnerability assessments that are used:
- Network/wireless assessments
- Web application assessments
- Application assessments
- Database assessments
- Host-based assessments
There are many vulnerability assessment tools available at your disposal. Some of the more common tools that you may be familiar with include the following:
- Qualys: https://www.qualys.com/
- Tenable (Nessus): https://www.tenable.com/
- OpenVAS: https://www.openvas.org/
- Nikto: https://cirt.net/nikto2
Microsoft also has vulnerability scanning solutions available as part of their Defender security suite. Let's look at an example of vulnerability scanning with Microsoft Defender for Cloud and Microsoft Defender for Endpoint.
Vulnerability scanning with Microsoft Defender for Cloud
Microsoft Defender for Cloud includes a built-in vulnerability assessment for Windows and Linux servers running on-premises, in Azure, and connected with Azure Arc. This assessment is included with the enhanced security features and is powered by Qualys without the need for additional licensing. After the scanner is deployed to servers, data is collected and analyzed using Qualys analytics, and reports the findings back to the Defender for Cloud console in Azure. For a review of additional Defender for Cloud features, see Chapter 13, Security Monitoring and Reporting, and Chapter 14, Security Operations.
The following article provides additional information about the vulnerability scanner, including the supported operating systems:
https://docs.microsoft.com/en-us/azure/defender-for-cloud/deploy-vulnerability-assessment-vm.
To enable the assessment on your virtual machines, follow these steps:
- Log in to https://portal.azure.com.
- Search for Microsoft Defender for Cloud and open it.
- Click on Recommendations in the left-side menu under the General section.
- Search for Machines should have a vulnerability assessment solution and click to open it.
- Select the virtual machines you would like to deploy to, then click on Fix.
After clicking Fix, the Qualys extension will be installed on the virtual machine and will begin collecting data. After about 48 hours, you will be able to view any discovered vulnerabilities by following these steps:
- From the Azure portal, browse to Microsoft Defender for Cloud.
- Click on Recommendations from the left-side menu.
- Within the main screen, look for Remediate vulnerabilities and expand the section.
- Click on Machines should have vulnerability findings resolved to view all the findings, as in the following screenshot:
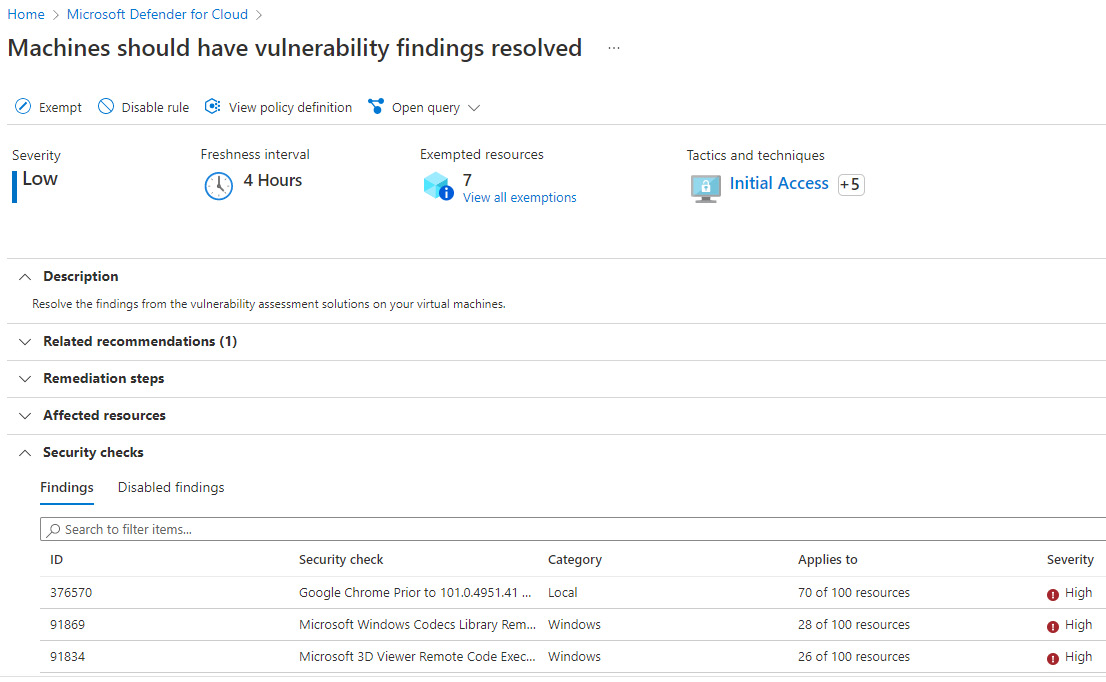
Figure 15.5 – Identified vulnerabilities
The following reference guide provides a list of the recommendations that you may see within the Recommendations section from the scans within Microsoft Defender for Cloud: https://docs.microsoft.com/en-us/azure/defender-for-cloud/recommendations-reference .
Next, let's look at reviewing weaknesses in the Microsoft 365 Defender portal.
The Microsoft 365 Defender portal
For devices onboarded to Microsoft Defender for Endpoint, you can access Vulnerability management from within the Microsoft 365 Defender portal to view identified vulnerabilities on your devices. To access this feature, take the following steps:
- Log in to the Microsoft 365 Defender portal by going to https://security.microsoft.com/.
- Click on the menu at the top left, then expand Vulnerability management.
- Click on the Weaknesses option to view all the identified vulnerabilities within your environment.
- Within the search field, you can refine the results by adding filters. For example, in the following screenshot, a filter was added to show vulnerabilities for Windows 10:

Figure 15.6 – The Microsoft 365 Defender Weaknesses console
We also reviewed the Weaknesses dashboard in Chapter 13, Security Monitoring and Reporting.
Now that we have reviewed validating controls through audits and finding weaknesses with vulnerability scanning tools, let's look at planning for penetration testing. A penetration test is another great way to identify security gaps and exploits that affect your organization's systems.
Planning for penetration testing
Penetration testing, or pen testing, is another method for identifying security risks and an important function of a mature security program. Pen tests validate risk by performing specific activities against targets in your environment, such as system hosts, applications, users, and devices to exploit known vulnerabilities. Tests are executed by skilled security professionals, referred to as ethical hackers, to try and replicate the activities of a malicious actor. This practice is commonly referred to as ethical hacking.
Penetration tests can be executed externally to simulate an outside threat trying to break in, or internally, to simulate an insider threat that has breached your perimeter network. There are many different types of penetration tests, and commonly cover the following areas:
- Systems and servers including Active Directory
- Web, API, and mobile applications
- Databases
- Networks (internal/external/DMZ), including wireless
- Social engineering, such as phishing simulations
- Physical security tests against facility access and data center controls
Penetration testing also can cover software testing. This type of testing is most likely executed in conjunction with your developers and programmers. This includes static and dynamic testing, misuse case testing, fuzz testing or fuzzing, and interface testing against APIs and user interfaces. One excellent resource used in this type of testing is OWASP (https://owasp.org/), which was reviewed in Chapter 1, Fundamentals of Windows Security.
There are a few different testing types that can be used as part of penetration testing, known as black box, gray box, and white box:
- Black box testing, also referred to as no- or zero-knowledge testing, is where the tester is provided no information about your environment upfront. This best represents an actual hacker.
- Gray box testing, also referred to as some- or partial-knowledge testing, is where the ethical hacker is provided with limited information about the environment.
- White box testing is also referred to as complete- or full-knowledge testing. In this type, the ethical hacker is provided with complete knowledge of the environment.
Depending on the size of your organization and the maturity of the security program, it might make sense to outsource the testing service to a vendor. Most penetration testing vendors are equipped to handle small to large-sized environments and include experts who are very familiar with ethical hacking techniques and follow the rules of engagement to not inadvertently cause damage to critical systems. Many third-party companies offer penetration testing services, and a few examples include the following:
- Secureworks: https://www.secureworks.com/services/adversarial-security-testing/penetration-testing
- Mandiant: https://www.mandiant.com/services/technical-assurance/penetration-testing
- Rapid7: https://www.rapid7.com/services/security-consulting/penetration-testing-services/
Organizations that are well-staffed and have the in-house expertise to execute their own internal penetration test include a red team (offensive) and a blue team (defensive), which would likely be the SOC team. These teams work together to address the risks in an organization, and often complete purple team (red and blue team) exercises. For example, the red team will execute an attack on the organization and the blue team will attempt to validate whether they were able to detect the attack and respond to it. If the attack is detected, the blue team is successful with their role. If they don't identify the attack, they can address gaps for improvement.
Tip
Blue teams should also run threat-hunting exercises. A threat hunt uses IOCs as clues to hunt or run sweeps for potential active threats in the environment.
There are many tools available to help conduct your own tests within your environment. Some of the more common tools you may be familiar with include the following:
- Metaspoilt: https://www.metasploit.com/
- Wireshark: https://www.wireshark.org/
- NMAP: https://nmap.org/
Building a successful internal testing program will require a substantial investment of effort, experience, and skilled experts to operate efficiently. Next, let's review the steps included when executing a penetration test.
Executing a penetration test
Whether a penetration test is conducted internally or outsourced to a third-party company, you will need to ensure a rigid process is followed as part of its execution. Simply deploying some tools and trying to uncover vulnerabilities without a plan and proper approval can be extremely risky and potentially disruptive. The penetration test needs to be carefully planned out with the correct approval in place before executing it. There may be slight variations and different approaches, but the following diagram illustrates a standard process for executing a penetration test.

Figure 15.7 – The penetration testing process
- The Scoping and Planning phase is where you will plan and define the scope of the test. This is where contracts will be signed, and the Rules of Engagement (RoE) document is agreed upon.
- Reconnaissance is the phase where information about the company or environment being targeted is gathered.
- In the Vulnerability Assessment and Scanning phase, you will scan the environment and search for and identify weaknesses and vulnerabilities.
- Exploitation is where you will attempt to exploit and breach the environment with any of the identified vulnerabilities.
- Reporting and Analysis is the final stage, where you will receive a report with an overview and detailed analysis of the test. This can also include recommended actions for remediation.
Tip
The rules of engagement document should be defined in clear language and approved and signed off by leadership before any work begins.
When you conduct a penetration test, you also need to be aware of other environments that could potentially be impacted if those services have rules of engagement defined. For example, Microsoft has a rules of engagement document that you will need to review if you're testing an environment hosted in Azure. You can find the Microsoft rules of engagement at https://www.microsoft.com/en-us/msrc/pentest-rules-of-engagement.
The following screenshot shows the Microsoft RoE introduction and scope:

Figure 15.8 – The Microsoft RoE
Make sure to review the section with the activities prohibited by Microsoft; the list is quite lengthy.
Tip
You should plan to execute a penetration test annually, at a minimum, within your environment.
After the test concludes, let's look at what the penetration test report findings may look like.
Reviewing the findings
The penetration test reports typically list any identified Low, Medium, High, and Critical vulnerabilities or concerns. It may also include an informational category that provides details on items of interest but may not be of high concern or applicable to your current systems. Once the test concludes and the report is finalized, the work doesn't stop. It is just as important that you take the report and build a plan around the remediation of those items.
After the remediation plan is developed, systems administrators and the security team should work together to mitigate any critical or high-risk items immediately and be held accountable by setting deadlines for completion. Once remediation and mitigation efforts have been completed, you will need to ensure you carry out re-testing to validate that the controls put in place work as designed so you can close the risk. In some instances, you might accept a risk if the cost to remediate outweighs the value of the data or the type of information at risk. In any case, building a remediation report that can be shared with leadership to show resolution to any identified vulnerabilities from a report is highly recommended. The following screenshot is an example of what could be used to document a vulnerability and accepted resolution:
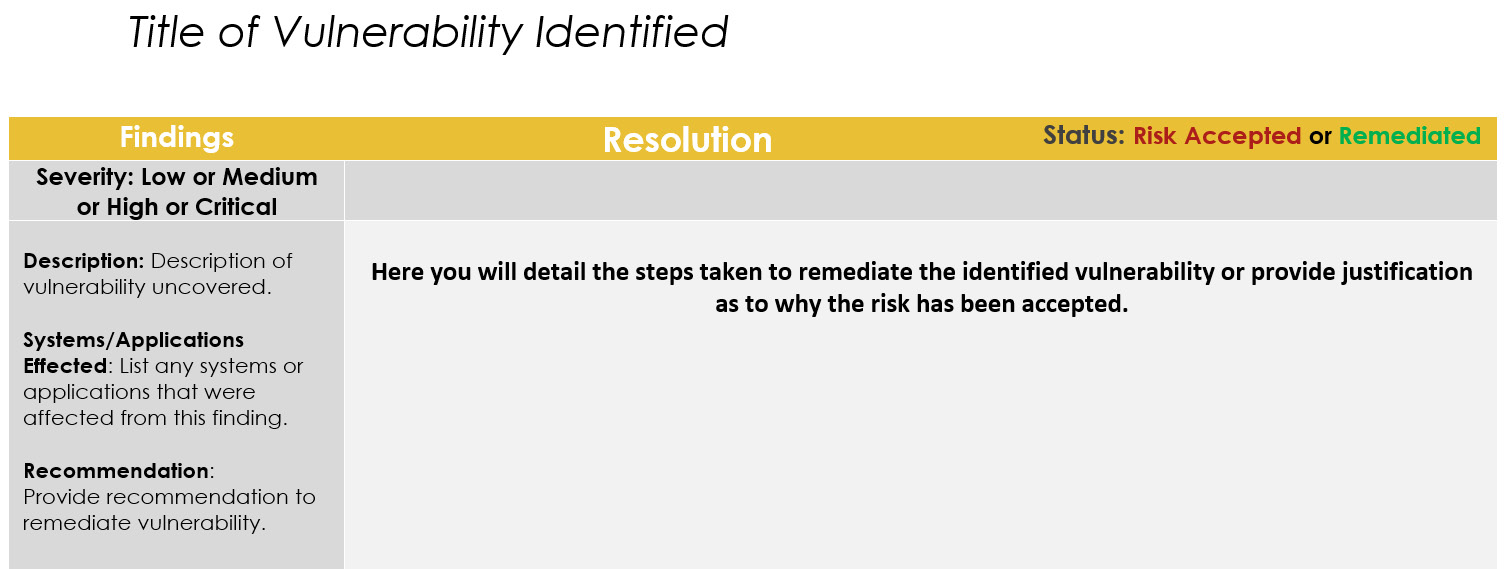
Figure 15.9 – Example of vulnerability remediation report
Any outstanding risks identified from a penetration test should also be included in a risk register, which is typically a document that tracks all known risks for your organization. If you don't have a risk register, it is highly recommended that you build one with visibility at the leadership level. Having a risk register is a great way for organizations to track known risks within their environment and document the risk owners and those who accepted the risk. Something as simple as an Excel spreadsheet could meet your needs, to begin with.
The output of a well-executed penetration test underscores the importance of its inclusion in a well-rounded security program. The results provide great value in identifying risks to your users, systems, and company data. Ensure you understand the technologies and concepts of penetration testing thoroughly to apply them efficiently within your environment.
Important Note
NIST has a very detailed document on security testing and assessment. You can view the SP 800-115, Technical Guide to Information Security Testing and Assessment publication at https://csrc.nist.gov/publications/detail/sp/800-115/final.
Next, we will review the importance of building a security awareness, training, and testing program.
An insight into security awareness, training, and testing
One area that shouldn't be overlooked is to ensure users participate in proper security awareness training and to test them using mock attacks. The human factor is often a weak link in the defenses, and providing awareness is critical to building a more resilient and secure organization.
There are three important components to consider in a robust employee security program. The first is testing, commonly executed through phishing campaigns, tabletop exercises (covered later in the chapter), or an attack simulator. The second is providing a robust and well-rounded training program, which includes keeping records of employees who have taken and passed the training. This shouldn't be a one-time event, but rather an ongoing event, as attack methodologies are constantly changing. Lastly, you need to provide consistent awareness to your users as deemed appropriate. Keeping security at the forefront by sending weekly communications with tips, tricks, and recommendations, or providing somewhere for users to learn more about security-related topics, such as the company intranet, will help strengthen your users' mindsets. Security should be considered a core company value.
Tip
Many security audits include showing proof of an active security awareness training program.
Just like with vulnerability and penetration testing, many vendors provide security awareness, training, and testing services and tools. A couple of the well-known vendors in the space include:
- KnowBe4: https://www.knowbe4.com/
- Proofpoint: https://www.proofpoint.com/us/products/security-awareness-training
Next, let's look at testing users by using the Microsoft 365 Defender attack simulation training tool.
Using attack simulation training with Microsoft 365 Defender
Microsoft has a tool available to test your users, named Attack simulation training as part of the Defender for Office licensing offering. With Attack simulation training, you can measure your user's awareness by choosing between different real-world scenarios commonly used in social engineering attacks, such as phishing emails. To use Attack simulation training, you will need to be a global administrator, security administrator, Attack simulation administrator, or an Attack Payload Author, and have a Microsoft 365 E5 or Microsoft Defender for Office 365 Plan 2 license. To access Attack simulation training and set up a simulation, take the following steps:
- Log in to https://security.microsoft.com/.
- From the left-side menu, click on Attack simulation training. The landing page will look like the following screenshot:

Figure 15.10 – Attack simulation training portal
- Select Simulations on the top menu to view any current simulations.
- To set up a new simulation, click on + Launch a simulation, then select which attack technique you would like to use:
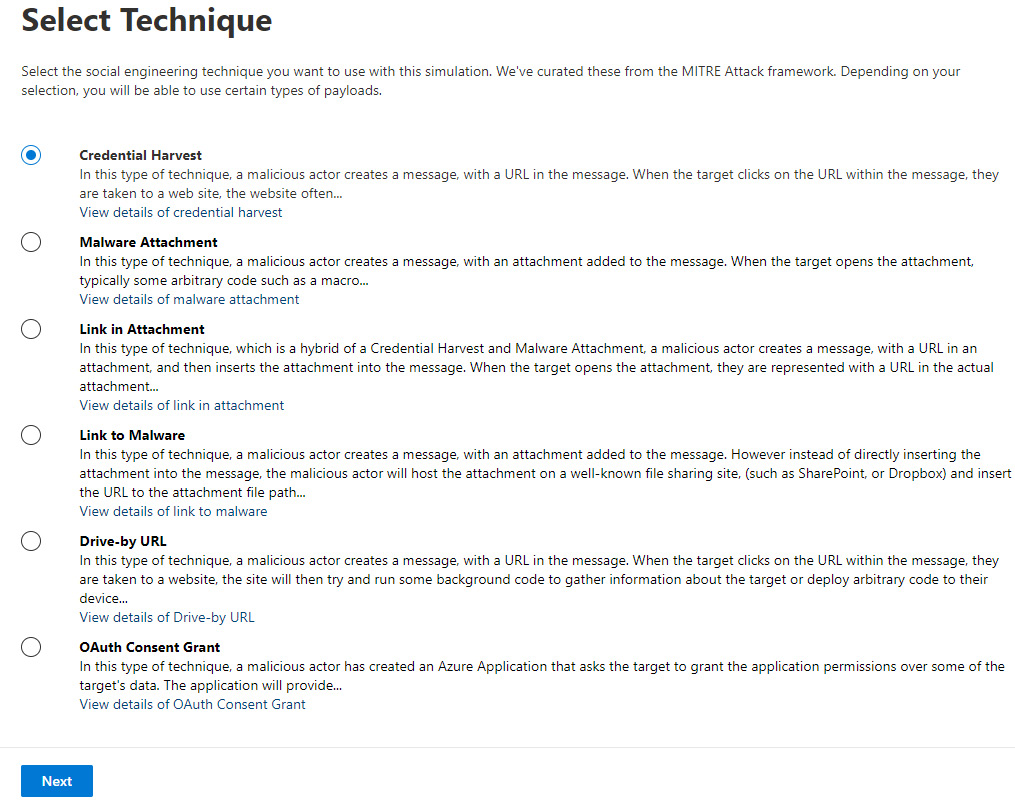
Figure 15.11 – Social engineering techniques
- Click Next, then enter a simulation name and description.
- Click Next, and you will then select the payload, which will be the malicious email sent to your users. Microsoft provides many different templates, or you can create your own. Once you select your payload, click Next.
- Select Target Users by selecting all or by specifying specific users. Click Next.
- Select whether you would like to assign training to the user. You can also redirect to a third-party platform or use Microsoft's native training experience. For this example, select Microsoft training experience (Recommended), then select Assign training for me (Recommended). Select a due date for training, then click Next.
- Customize your landing page. Select your landing page preference and landing page layout, and edit your layout if desired. Click Next.
- Next, select as required in Select end user notification. You will be required to complete additional steps depending on your selection. Click Next.
- Configure Launch Details for when you would like to launch the simulation, then click Next.
- Finally, review the simulation details and send a test before submitting to commit your selections. Click Submit when ready.
Tip
It is highly recommended to include all employee types, such as full-time employees, contractors, contingent workers, and interns, to complete the required training.
You can learn more about Attack simulation training by visiting the following link:
Next, let's discuss the importance of executing a tabletop exercise in the event of a critical security incident.
Executing a tabletop exercise
In Chapter 14, Security Operations, we mentioned the importance of preparing your organization for when an incident occurs. It's best to maintain the mindset that in today's world, it's only a matter of when, and not if an incident occurs. To best prepare, you will need to assemble the personnel (as identified in your CIRP) that will be involved in an incident response through a tabletop exercise. A tabletop exercise walks your key stakeholders through a realistic incident scenario, asking questions that require the team to make timely decisions, troubleshoot, and communicate in a way that replicates an actual incident. A trained moderator will assess each response and provide feedback on strengths and areas for improvement. Tabletop exercises may include a wide range of personnel, which covers different real-world scenarios based on your business' industry, size of the organization, and IT footprint. There may be more specific target groups within your organization, but at the minimum, you should provide the following types of tabletops at least annually:
- A technical tabletop exercise tests your technical team's ability to respond to a cybersecurity incident. This exercise is mostly technical in nature and focused around identifying whether an incident has occurred, investigating, and the response needed from a technical perspective.
- An executive tabletop exercise brings your executive leadership team together to test how they will respond to an incident. This will focus more on the decision-making skills, how and whom to communicate with, the process and timing to engage cybersecurity insurance, and whether to pay a ransom.
Running through these exercises helps ensure your key stakeholders are familiar with the CIRP. This will increase the efficiency of an incident response should one occur, identify any gaps within the CIRP, educate stakeholders about their roles and responsibilities, and satisfy any regulatory requirements to execute them.
For the exercise scenario, you can build it around any relevant event that may occur within your environment. Some examples include a ransomware situation, a business email compromise (BEC), a disgruntled employee extracting top-secret information, a cyber extortion scheme, and disruptive Distributed Denial-of-Service (DDoS) attacks, to name a few. When executing a tabletop exercise, bringing in a third-party vendor can help provide insight from an outside perspective with real-world expertise. You could also run your own internal tabletop exercise by following readily available templates. CISA has a great repository of tabletop exercise packages at your disposal for use at https://www.cisa.gov/cisa-tabletop-exercises-packages.
It is important that you don't overlook your security awareness, training, and testing components. Preparing your users has never been more important, and ensuring your organization is prepared to respond to an incident will help facilitate a quicker recovery of normal business operations.
Summary
In this chapter, we covered validating controls within your environment, including internal and external auditing. We reviewed different types of SOC compliance and discussed the importance of vendor assessments as part of your vendor onboarding process. Next, we reviewed the Microsoft Service Trust Portal and how to view Microsoft's available audits and assessments. We then reviewed the Microsoft Defender for Cloud regulatory compliance offering, before finishing the section with Microsoft ODA.
In the next section, we covered what a vulnerability scan is and the different types of assessments that should be run. We reviewed how Microsoft Defender for Cloud can help run assessments against Windows and Linux hosts. We then discussed the importance of penetration testing and remediation. This included reviewing the different types of penetration tests, the test execution process, the importance of remediation, and an overview of the rules of engagement that Microsoft has published. In the final section, we covered security awareness, training, and testing, and reviewed Microsoft's attack simulation training, before finishing off with an overview of tabletop exercises.
In Chapter 16, Top 10 Recommendations and the Future, we will outline 10 key takeaways and to-dos to consider after reading through this book. Then, we will look at the future of device security and management, and an overview of what IT security means for our future.
