Chapter 2: Building a Baseline
In this chapter, we are going to cover the importance of building a baseline for your Windows systems. As you deploy tens to hundreds to thousands of Windows devices, you need to ensure you are deploying your devices pre-hardened and secured. In addition to this, you need to ensure consistency with every system that is deployed. This is where building a foundation is critical, and that must be followed. In addition to the baseline requirements, very stringent policies, standards, and procedures must be followed. Anyone falling outside of these boundaries will create additional risk for the organization, so it is critical a well-defined program is put in place early with the backing and support of leadership.
The following will be covered in this chapter:
- Overview of baselining
- Introduction to policies, standards, procedures, and guidelines
- Incorporating change management
- Implementing a security framework
- Building baseline controls
- Incorporating best practices
Overview of baselining
Security baselining is the practice of implementing a minimum set of standards and configuration within your environment, more specifically, capturing a minimum configuration for your Windows devices. Building a baseline provides a minimum defined standard that will help ensure a more secure environment as you deploy systems and devices within the enterprise. Depending on the size of your organization, baselines could be in the form of checklists or spreadsheets that someone follows to ensure the predefined security controls are in place. A more advanced method includes capturing a snapshot or image that is already configured with predefined security controls. In addition to the starting baseline, there are additional management tools to layer and enforce baseline configurations. A couple of examples include Group Policy Objects (GPOs) and Mobile Device Management (MDM).
Unless you are a small business with under 100 employees, it will be impractical to deploy any type of system or device and individually configure it every time a new one is built, especially if your user count and servers start reaching hundreds to thousands with an extremely high volume of device deployments on a day-to-day basis. This could also be very error-prone. Because of this, it will be extremely important that a well-defined program is put in place to minimize potential error-prone steps involved with deploying systems, and devices receive their baseline and hardening configurations systematically.
Another important factor to consider with baselining is that your organization may be required to follow strict compliance regulations that will force the need to ensure specific security requirements are adhered to. Baselines will help when being audited, or when the need to provide evidence arises. Some regulatory compliance examples include the following:
- Sarbanes-Oxley Act (SOX)
- Health Insurance Portability and Accountability Act (HIPAA)
- Federal Information Security Management Act (FISMA)
- Payment Card Industry Data Security Standard (PCI DSS)
- General Data Protection Regulation (GDPR)
- California Consumer Privacy Act (CCPA)
- Gramm Leach Bliley Act (GLBA)
We can expect this to continue to grow as privacy continues to become a big discussion point and challenge. It is important to have a minimum understanding of what regulatory compliances are and how they directly relate to your organization's sector. They will play a big part in planning your overall security baselining.
As you begin to define and deploy your baselines, you will find that one will not fit all. You are going to need to document and build them for different use cases. These are some examples of where unique baselines may need to be defined:
- Network devices (switches, routers, firewalls, and so on)
- Windows systems: servers and clients
- Linux/Unix systems
- Storage/file servers
- Database servers
- Web servers
- Application servers
- Operational Technology (OT)
- Internet of Things (IoT)
As we look more specifically at the Windows environment, you may end up with baselines for different architectures:
- For Windows Server, you have the following: Windows Domain Controller (DC) Server, Windows Server Internet Information Services (IIS), Windows SQL Database Server, Windows DNS Server, Windows Remote Desktop Services, and others.
- For a Windows client, you have the following: Windows standard client (user workstation), Privileged Access Workstation (PAW), Windows virtual client, OT and IoT clients, and others.
Now that we've provided an overview of what baselines are, the next few sections will cover details around the foundation and overall strategy that supports the ability to build well-defined baselines and ensure consistency. Deploying baselines without well-defined policies, processes, and a framework will not be successful in the long term and can leave your organization vulnerable. In addition, having these foundations in place provides a platform to ensure leadership engagement and sign-off, which drives a consistent message to the organization and the important role each associate plays in its success.
Introduction to policies, standards, procedures, and guidelines
A follow-on to the baselining overview section is policies, standards, procedures, and guidelines. This section works hand in hand with baselining and holds extreme importance within an organization. It is critical as part of your security program that well-defined policies, standards, and procedures are in place and being followed by everyone. In addition, it is important that the policies are signed off and enforced by leadership. Without this support, it becomes more difficult to enforce and collectively get behind security at an organizational level.
Start by defining and creating your company policies. As a result, your standards can then be built to form the foundation of your baselines. Once these baselines are created, procedures and guidelines can be built to implement the baselines and help accomplish the end goal. Keeping this strategy in mind will drive compliance with your company policies.
The following provides a brief overview, with recommendations of policies, standards, procedures, and guidelines.
Defining policies
A security policy is the first level of formalized documentation for your organization's security program and is mandatory. Policies are a critical component of your overall security program, which requires sign-off and support from the leadership team to ensure success. Policies should be very broad and general with no direct tie to the technology or solutions within the organization. In general, they should not change often, but periodic review is critical. Some examples of policies may include acceptable use policy, change management policy, disaster recovery policy, privacy policy, information security program policy, and so on.
If you don't have any policies in place, it is highly recommended you begin with some basics, as it relates to your Windows security today. The following, at a minimum, should be included as part of securing your devices and referenced in a policy:
- Security updates
- Encryption
- Firewall
- Password policy, Multi-Factor Authentication (MFA), and biometrics
- Local administrative access strategy
- Security protection tools and antivirus
- Compliance and protection policies
- Data loss prevention and information protection
An example of a documented policy may include All systems must be kept up to date with the most recent security updates.
Next, let's look at setting standards to follow the defined policies.
Setting standards
Standards follow policies in that they define the specifics of the policy and are mandatory. These provide the direction needed to support the policies. Standards help enforce consistency throughout the organization and will provide specifics on the technology to be deployed.
Referring to the recommended items listed in the policy, the following are examples of standards for policies:
- All Windows workstations will be configured using Windows Update for Business and Windows servers using WSUS or Azure Update Management. Update schedules will be defined and documented by the business use case.
- All Windows servers and end user workstations will be encrypted using BitLocker and/or Azure Disk Encryption.
- A Windows firewall will be enabled and configured on all Windows end-user devices and servers. Connection rules will be documented.
- A PIN and biometrics with Windows Hello must be used, and accounts will be required to use a password with a minimum of 12 characters. Passwords must contain a lowercase, uppercase, numerical, and special character and are required to be changed annually.
- MFA will be required for all users accessing the corporate environment and resources.
- There will be no standard user accounts assigned with local admin access on any Windows device.
- All Windows end-user devices and servers will be enabled with Microsoft Defender for Endpoint.
- Compliance policies for conditions such as device risk and minimum OS version will be assigned and enforced with Conditional Access on Windows devices.
- Unified labeling with data loss prevention and information protection will be deployed to all Windows end-user devices.
Next, let's look at building procedures to define a set of instructions used to accomplish tasks.
Creating procedures
Procedures are the step-by-step instructions used to accomplish a repeatable task or process. The instructions are intended to achieve a specific goal and assist with implementing the defined policies, standards, and any guidelines that may apply. Procedures may change frequently depending on software version changes, hardware replacement, and so on. For better organization of procedures, you may want to look at third-party tools for help. One example is a tool known as Nintex Promapp that helps document and share your organization's processes: https://www.nintex.com/process-automation/process-mapping/.
Here is an example of a procedure:
- Deploy a new device with Windows.
- Ensure the device is connected to the internet.
- Verify that the device configurations and applications have been installed.
- Check whether the device is compliant.
Finally, let's look at creating guidelines to act as recommended best practices.
Recommending guidelines
Guidelines provide recommendations or best practices and are not mandatory requirements. They can be complementary controls in addition to standards, or even provide guidance where a standard may not apply.
An example of a guideline might be: Ensure you save and close all documents and programs before rebooting after receiving the latest Windows updates.
Although not mandatory, guidelines provide a lot of value to users to help them to be more productive with technology. When building guidelines, it's important to think about how to efficiently provide the users with visibility and access to the guidelines. An effective communication plan is critical to ensure the users read and use the guidelines. The following are five ideas that will help with communicating your guidelines:
- Build a theme around your guideline communications, for example, Smart Tech Guidelines.
- Insert a section on guidelines in the company newsletters and/or communications.
- Link your guidelines back to a central repository for users to come back and access it.
- Keep your guidelines short and to the point.
- Make your guidelines relevant to both professional and personal usage.
The following diagram illustrates the hierarchy of policies, standards, procedures, and guidelines with the addition of where baselines fall within the model:
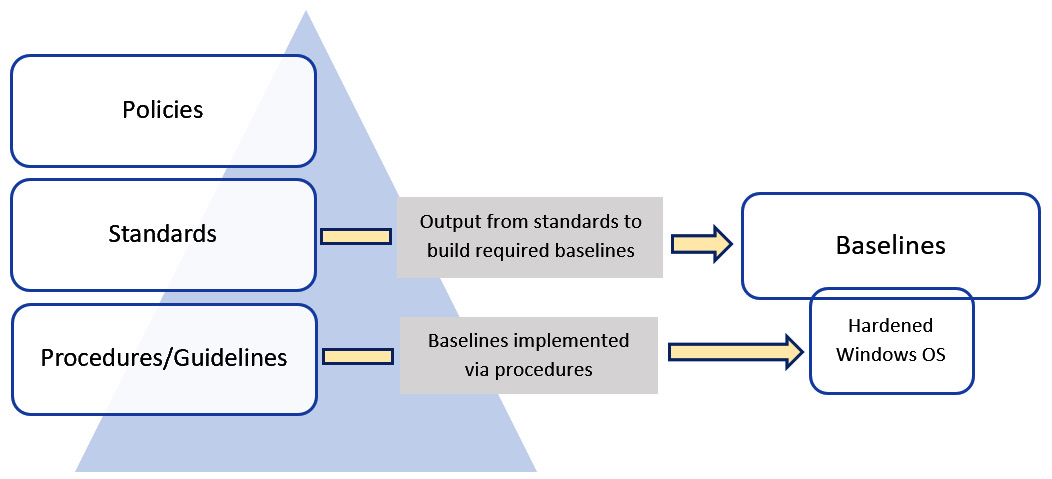
Figure 2.1 – Policies, standards, procedures, guidelines, and baselines
In the next section, we will provide an overview of the change management process. It's important to follow a change control process whenever you're implementing change in an environment.
Incorporating change management
It is critical that you understand the importance of change management and its place as part of the overall security program. Your organization most likely has some form of change control process in place today. If not, it is highly recommended that one be enabled to provide a more structured and reliable environment.
The following diagram provides an example of a change flow process that you should implement if one doesn't exist within your environment today:

Figure 2.2 – Change management flow process
Change management is typically part of a larger program, more specifically around service management. One of the more common frameworks to help with change management is Information Technology Infrastructure Library (ITIL).
Tip
Visit this website to learn more on ITIL: https://www.axelos.com/certifications/itil-service-management/what-is-itil.
As part of your security program, you will want to ensure that you have all your baselines signed off from management and that they are well documented. More importantly, you will need to ensure that the baselines are being implemented with every deployment. If any exceptions or deviations from the baselines are needed, it will be extremely important that the requests are pushed through the change management process and audited. They will need to be reviewed and approved by the appropriate teams, which will most likely include sign-off from someone in the security team who will be part of the change process. The same will apply to any changes needed to the baselines. As hardware, software, and operating systems change, there will be a need to modify the baseline to meet the changes. These changes should also go through a change control process to ensure everyone agrees to and approves the changes.
Important Note
If a security incident occurs on a system where a baseline wasn't correctly applied and approvals were not received for that exception, you could be putting the company and your job at risk.
Next, let's look at security frameworks and widely adopted frameworks that can be incorporated into your own security program.
Implementing a security framework
There's a possibility that your organization may have an information security framework in place today. If not, it's highly recommended you begin that journey straight away to help lay the foundation of your security program and strategy. There are many different frameworks available for implementation, and the direction you take may depend on multiple factors according to your business type, industry requirements, and regulations.
An information security framework is designed to build a well-defined basis for your organization's security program. One of the primary reasons to implement an information security framework is to help reduce risk as much as possible. It will help cover the foundation of everything you need to be aware of within your security program and help to identify any gaps within the organization.
Implementing an information security framework isn't easy and can be extremely complex, requiring a major time investment. Implementing a framework won't just happen overnight; it will take a lot of planning and many months, and even years, to implement correctly. It will be important to think of the framework as more of a journey that continues to evolve and improve over time.
A significant benefit of implementing a framework is the ability to provide a well-constructed overview of your security program and strategy to executive management and leadership. The framework will help provide the executive team with a comprehensive view of what security controls are in place and a roadmap of work to be completed. This will also allow them to provide feedback, prioritize needs, provide valuable input, and provide justification for budget allocation. The ability to make the security program and strategy transparent to leadership is a significant advantage.
The following are some of the more common and widely adopted frameworks in the world today:
- Control Objectives for Information and Related Technology (COBIT): https://www.isaca.org/resources/cobit
- International Standards Organization 27000 Family (ISO): https://www.iso.org/isoiec-27001-information-security.html
- National Institute of Standards and Technology (NIST) Framework for Improving Critical Infrastructure Cybersecurity, also known as the NIST Cybersecurity Framework: https://www.nist.gov/cyberframework
- NIST SP 800-53: Security and Privacy Controls for Federal Information Systems and Organizations: https://csrc.nist.gov/publications/detail/sp/800-53/rev-5/final
- NIST SP 800-171: Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations: https://csrc.nist.gov/publications/detail/sp/800-171/rev-2/final
- Health Information Trust Alliance Common Security Framework (HITRUST CSF): https://hitrustalliance.net/hitrust-csf/
Your industry and location may dictate which framework is to be used, but in general, they can all be used throughout any industry as a foundation. As an example, healthcare will most likely adopt the HITRUST framework. ISO 27000 and COBIT most likely will have a more global presence over NIST, which is leveraged by the US government primarily.
To help with your implementation, let's take a closer look at the NIST framework for improving critical infrastructure cybersecurity. Although the framework was initially created for critical infrastructure, it can be used by any organization of any industry and size. This framework has gained a lot of popularity and is being adopted by many. The NIST Cybersecurity Framework is built around five core functions, as shown here:

Figure 2.3 – NIST Cybersecurity Framework core functions
More information about the five functions in the NIST framework can be found at this link: https://www.nist.gov/cyberframework/online-learning/five-functions
Within these functions are categories that break down the focus to a subcategory, with a set of references on how to manage the risk within that given subcategory. To take this a step further, let's review the specific category that relates to the baseline configuration that you will follow as part of your overall implementation. The following figure breaks down the Protect function of the NIST framework:

Figure 2.4 – Example from the NIST Cybersecurity Framework
Tip
The NIST framework for improving critical infrastructure cybersecurity web page that contains the preceding example can be found at https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.04162018.pdf.
As you can see from the figure, the NIST Cybersecurity Framework provides the needed guidance and resources that can be used to meet the controls. Ensuring a framework is adopted will build a solid foundation to ensure the required baseline controls to harden your systems are put in place. Frameworks represent the overall controls at a higher level and help ensure there are no gaps in your security program, including any gaps in your Windows infrastructure.
Next, let's look at baseline controls. Baseline controls are set to define a standard set of configurations for your devices.
Building baseline controls
Following on from the previous section, we will cover more specifics of the baseline controls that can be used for your Windows devices. Here we will cover the following:
- Center for Internet Security (CIS)
- Windows security baselines
- Intune's security baselines
Let's look at each of these options in detail.
CIS
First, we will look at CIS. You may already be familiar with CIS, and you will see CIS listed on a lot of most-popular-framework lists, although it's not a fully comprehensive framework like others listed previously. Instead, CIS is more of a tactical compilation of controls and guidelines that allow organizations to meet the requirements of a chosen framework. The following screenshot is of the current CIS home page, which can be visited at this link: https://www.cisecurity.org/.

Figure 2.5 – CIS home page
CIS is a non-profit organization comprising a global community to provide protection against the ongoing cybersecurity threat landscape. More specifically, the CIS vision is "Leading the global community to secure our ever-changing connected world." Their mission is "… to make the connected world a safer place by developing, validating, and promoting timely best practice solutions that help people, businesses, and governments protect themselves against pervasive cyber threats."
Tip
You can learn more about CIS at https://www.cisecurity.org/about-us/, and sign up for the MS-ISAC advisories, newsletters, and webinars at https://learn.cisecurity.org/ms-isac-subscription.
CIS has an overwhelming number of tools and resources available, with many being free of charge. More specifically, CIS provides two sets of best practices widely adopted throughout the world: CIS Controls and CIS Benchmarks. As of version 8, the CIS Controls are a broader set of 18 foundational and advanced controls that provide a more comprehensive approach to overall security protection for your organization, whereas the CIS Benchmarks are focused more on the specific hardening of your systems, software, networks, and more.
Tip
CIS cybersecurity best practices can be found at https://www.cisecurity.org/cybersecurity-best-practices/.
If you opt to move forward with the CIS Benchmarks, you will need to download the checklist and customize it for your specific needs. The list of available benchmarks is extensive and includes categories for the following:
- Desktop and web browsers
- Mobile devices
- Network devices
- Security metrics
- Server operating systems
- Server application and roles
- Virtualization platforms
- Cloud and Microsoft apps
CIS also has the option of purchasing hardened images to provide for easier deployment moving forward.
To download the latest CIS Benchmarks, follow these steps:
- Open a browser and navigate to https://www.cisecurity.org/cis-benchmarks/.
- Click on Access all Benchmarks.
- Enter the required information, agree to the terms, and then click Get Free Benchmarks Now.

Figure 2.6 – CIS Benchmarks download page
- Go to your mailbox and look for an email from CIS (check the junk email folder also).
- Open the email and click Access PDFs.
- You will be provided with a list of all the available CIS Benchmarks in PDF format. Microsoft Windows Desktop will be at the top of the list:

Figure 2.7 – CIS Benchmark Microsoft Windows Desktop PDFs
- Scroll down and you will see Windows Server CIS Benchmarks.
- Keep scrolling down and you will also see Microsoft Azure CIS Benchmarks:
Figure 2.8 – CIS Benchmark Microsoft Azure PDFs
- In addition, there are many more Windows-specific CIS Benchmarks for specific roles, such as IIS, SQL, and Exchange.
- Once you download the PDFs, follow and implement the recommendations to harden your systems.
Tip
Visit here to access CIS Hardened Images that map back to the CIS Benchmarks: https://www.cisecurity.org/cis-hardened-images.
If you are using Azure as your data center, there are also CIS Hardened Images available in Azure Marketplace for simpler, hardened deployment for your servers. Log in to https://portal.azure.com, navigate to Marketplace, and search for CIS Windows.
Figure 2.9 – Azure Marketplace CIS hardened images
Next, let's look at security baselines specifically for Windows and the Microsoft Security and Compliance toolkit baselines for Windows.
Windows security baselines
As part of their services, Microsoft offers Windows security baselines from the Microsoft Security Compliance Toolkit (SCT), which provides recommended configurations to harden your Windows systems. The following options are available for selection from the Microsoft download site:
- Windows 11 security baselines
- Windows 10 security baselines
- Windows Server security baselines
- Microsoft Office security baselines
- Microsoft Edge security baselines
- Policy Analyzer and Local Group Policy Object (LGPO) tools
To give an idea of the complexity of securing Windows, the Group Policy Object (GPO) consists of thousands of configurable settings. This clearly shows the need to leverage pre-defined baselines to help with the hardening of your Windows devices. The more common Microsoft tools used to implement these baselines will consist of the following:
- Microsoft Intune
- Group Policy Objects
- Microsoft Endpoint Configuration Manager
Tip
Go here to view additional information on Windows security baselines: https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-security-configuration-framework/windows-security-baselines.
If you go in the Microsoft direction with Windows security baselines, the available resources can be downloaded for free to allow the implementation of a baseline. To download the resources, follow these steps:
- Go to https://www.microsoft.com/en-us/download/details.aspx?id=55319.
- Click Download.

Figure 2.10 – Microsoft SCT 1.0 download
- Select the desired versions, or click the box next to the filename to select all.
- Click Next.
- You will receive all the toolkits in .zip format.
Downloading the toolkit referenced previously will provide you with everything needed to deploy the recommended baselines from Microsoft. The following describes what's included in the security baselines ZIP file(s):
- The documentation folder includes an Announcement file that summarizes the recommendations and new settings. It also contains the full baseline in XLSX format and a New Settings spreadsheet. There are PolicyRules files that are useful when viewing comparisons with the Policy Analyzer tool.
- The GP Reports folder lists the outputs of each GPO in HTML format.
- The GPOs folder contains the Globally Unique Identifiers (GUIDs) for each GPO setting.
- The Scripts folder contains helpful scripts that can be used to map the GPO GUIDs to friendly names or to import baselines into Active Directory.
- The Templates folder includes ADMX and ADML files for Group Policies that are referenced in the new baselines and might not be included in the latest available download of Administrative Templates.
The following figure shows a quick snapshot of the baseline settings in Excel format that can be deployed using the provided GPOs within the toolkit for Windows 11:
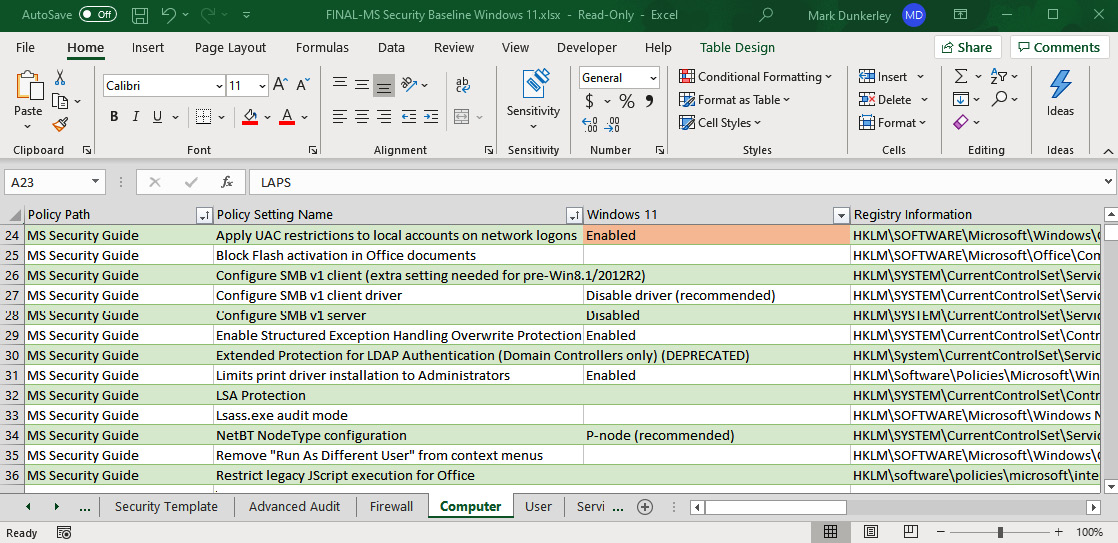
Figure 2.11 – FINAL-MS Security Baseline Windows 11.xlsx
The following screenshot shows the download in Excel format for Windows Server 2022:

Figure 2.12 – FINAL-MS Security Baseline Windows Server 2022.xlsx
Notice that Microsoft provides separate settings for a member server versus a Domain Controller (DC), providing additional settings specifically for your DCs as part of the Windows Server baseline. Also, if you look at the bottom of the spreadsheet, you will see the different categories the hardening is being applied to.
Comparing policies with Policy Analyzer
The Policy Analyzer tool is useful for comparing GPOs against other GPOs, the local policy settings on the computer, and the local registry. If you have downloaded the Microsoft SCT already, ensure you have selected PolicyAnalyzer.zip and Windows 11 Security Baseline.zip at a minimum. Extract them if you wish to follow along.
Let's compare the out-of-the-box Windows 11 settings to the Windows 11 security baseline by following these steps:
- Open PolicyAnalyzer.exe as Administrator.
- Click on Add, choose File, and select Add files from GPO(s)….
- Open the directory where you extracted the Windows 11 security baselines, navigate to the GPOs folder, and select the folder with the GUID for the MSFT Windows 11 – Computer policy (9FE25A81-CB6B-4F76-B9D2-147E9BED9A06).
Tip
There are many GUIDs inside the GPO folder of the extracted baseline. Clicking on the gpreport.xml file will display the policy friendly name, or use the MapGuidsToGpoNames.ps1 file in Scripts | Tools for help.
- In Policy File Importer, click on Import. Give it a friendly name such as MSFT Windows 11 – Computer, then click on Save.
- This will bring you back to the main menu of Policy Analyzer. Ensure the policy you imported is selected, then click on View/Compare to bring up Policy Viewer.
The column headings are straightforward and provide an overview of the policy group or registry key as well as the policy setting. If you click on a row, detailed information will be presented about the policy in the details pane below the policies. Here are some notes to keep in mind about the menu options:
- Selecting View | Show only Differences will display all of the differences between the recommended baseline and what's currently set in the local registry.
- Selecting View | Show only Conflicts will display settings that differ from the recommended baseline to the current setting. These will be highlighted in yellow.
- Selecting Export | Export table to Excel will export only the table with differences or conflicts.
- Selecting Export | Export all data to Excel will include the details pane explanation.
The following screenshot shows the Policy Viewer output after clicking on View/Compare. Anything highlighted in yellow is a conflict between the GPO and current setting in the local registry:

Figure 2.13 – Policy Viewer in Policy Analyzer
We will provide more details on the implementation of security controls in Section 2, Applying Security and Hardening.
Tip
The Microsoft Security Compliance Toolkit (SCT) also provides additional details on the available tools to manage your Windows baselines: https://docs.microsoft.com/en-us/windows/security/threat-protection/security-compliance-toolkit-10.
Next, let's look at Intune's security baselines to configure Windows devices managed by Intune, to secure and enhance protection for your users and devices.
Intune's security baselines
If you are using Microsoft Endpoint Manager to manage your end-user Windows devices, you can take advantage of the built-in Intune security baselines to secure and harden your devices for your users. The baselines can be used pre-configured as is, or they can be customized to better meet your requirements. To use Intune's security baselines, your device needs to be running the following at a minimum:
- Windows 10 version 1809 and later
- Windows 11
There are currently four security baselines available in Microsoft Endpoint Manager that can be applied to your devices, and they are listed here:
- Security Baseline for Windows 10 and later
- Microsoft Defender for Endpoint Baseline
- Microsoft Edge Baseline
- Windows 365 Security Baseline
These baselines are extremely powerful for hardening your devices that are managed by Microsoft Endpoint Manager. The Intune security baselines bring the next generation of device security configuration with ease, as we look to move away from the legacy management of using and relying on GPOs.
To access the Intune security baselines, do the following:
- Log in to https://endpoint.microsoft.com/.
- Click on Endpoint Security on the left menu.
- Click on Security baselines.
- Here you will see the available security baselines for use:

Figure 2.14 – Intune security baselines
As already mentioned, the baselines all come pre-configured with default values based on Microsoft's recommendations for a baseline. Microsoft has a very comprehensive overview of the configurations and what the defaults are for each of their baselines. They also maintain a history of the released versions for review. You can link to each of the baseline settings here: https://docs.microsoft.com/en-us/mem/intune/protect/security-baselines#available-security-baselines.
Tip
We will cover Intune security baselines in more detail in Section 2, Applying Security and Hardening.
No matter which method you use to implement your baselines, it is highly recommended when making any configuration changes from newly released baselines to ease them into production and thoroughly test them first. In addition, ensure any changes go through your change control process for tracking and offer transparency to the business.
Next, let's recap the chapter by providing a checklist of best practices that will help when building a security framework and implementing your baselines.
Incorporating best practices
To finish off the chapter, we wanted to provide a checklist of the most important items that will help enforce your security baselines. The following list is ranked in order of importance as you look to build and enforce your baselines:
- Select and deploy a framework to build a foundation; the NIST Cybersecurity Framework is a great place to start.
- Select a baseline foundation; we covered CIS, Windows security baselines, and Intune's security baselines.
- For your Windows devices, use Policy Analyzer from the Microsoft SCT to review your baselines, or use the CIS-CAT Pro tools to review your system configurations against the CIS Benchmarks.
- Create or use (and re-use) a Golden Image template for each use case and always keep up with the latest updates. CIS has pre-defined hardened images that can be used.
- Build well-documented and easy-to-follow procedures that others can use and follow.
- Use automation of controls and tools to reinforce the baseline; MDM with Intune or Active Directory Group Policy as an example.
- Use compliance policies to validate controls are in place. This will also help with auditing devices that are non-compliant.
- Implement a quarantine or risk access policy with non-compliant devices.
- Implement efficient monitoring and reporting for device compliance. Microsoft Power BI is a great way to visually provide reports.
- Always keep up with the latest Windows versions and the technology used to manage the devices. The modern world is very dynamic and moving at an extremely fast pace.
It's important to note that while creating a security framework and enforcing controls with full compliance is desirable, exceptions will need to be accounted for. It is recommended that your organization also includes a risk register that clearly documents the systems and applications that cannot comply with the defined policies and standards. The register should identify all risks as well as rate the implications or severity each risk has for potential impacts on the organization. These implications should not only be focused on from the security lens, but also identify potential legal liabilities and cost implications if the risks were exploited. Leadership should be made aware of these risks and sign off on their acceptance. Furthermore, a stakeholder should be named to act as the accountable party and the register should be reviewed frequently to identify any possible solutions to mitigate the risks.
Summary
Throughout this chapter, we provided an overview of baselining to help you understand its importance and role within the overall security program. Next, you learned about policies, standards, procedures, and guidelines and the importance of them as part of your overall security strategy. We also looked at how these policies, standards, procedures, and guidelines interact and build upon each other to structure the baseline model. We then covered the change management process with respect to baseline management.
Finally, we reviewed frameworks and their role within the security function of your organization, discussing the more widely adopted frameworks implemented. Following this section was an overview of baseline controls that are available for Windows. These option. included CIS, Windows security baselines, and Intune's security baselines, and we gave you an idea of where to retrieve pre-defined templates, configurations, and images before providing best practices as part of baselining.
In the next chapter, we will cover hardware and virtualization. The chapter will review the importance of ensuring both your hardware and virtualized machines adhere to the same level of security that you implement on the Windows OS.
