We are going to take a look at the following changes that have taken place in the security framework of Microsoft Dynamics AX 2012:
- Role-based security
- Extensible data security framework
- Server enforcement of security
- Custom authentication
The following figure shows the security architecture of Dynamics AX:
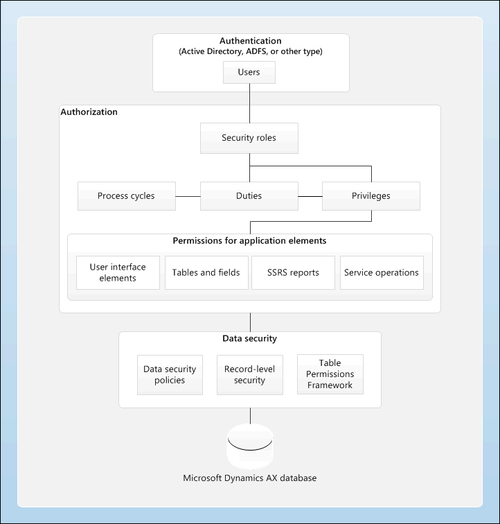
Source: Microsoft Tech-Net
In earlier versions of Microsoft Dynamics AX, the IT administrator wasted a lot of time and effort in managing the application security by creating user groups. By using the role-based security that Microsoft Dynamics AX 2012 offers, managing the security within the application will be easier and aligned with your business as it provides predefined roles found in business.
It also provides predefined business-related duties that are assigned with roles and matched with the users assigned to a specific role.
Any data located in any table can be secured easily. The new framework helps you easily create policies based on data to secure your data in different tables.
You can specify which data you want the user to access—present, past, and even future records. Besides that, you can determine the level of access based on an effective date, so you may want to give the user access to the present data and not to the past data, based on a determined date. For your information, record-level security is still being used in Microsoft Dynamics AX 2012.
In earlier versions of Microsoft Dynamics AX, authorizations were performed on the client's machine, but in Microsoft Dynamics AX 2012, authorizations are performed on the server. There is an addition made in Table Permission Framework (TPF) that will not only deny users access to full records, but also deny access for any field that was not supported before. This increases the consistency of security between client types and shifts the security load to the server.
It is already known that user authentications are based on Active Directory, so all users must be domain users. But if we want to talk about the external users, in earlier versions of Microsoft Dynamics AX you had to create the external users as domain users, so in the new version of Microsoft Dynamics AX 2012, external users will no longer require domain accounts to be able to access Microsoft Dynamics AX 2012. There are a lot of methods besides Active Directory; these methods simplify the administration and maintenance required for external users and is called pluggable authentication.
Pluggable authentication is new in Microsoft Dynamics AX 2012, and is used to allow access to Enterprise Portal to users who are not part of Active Directory. There are other types of authentication in addition to Active Directory, and they are as follows:
- Active Directory Federated Service (ADFS): This allows users who are associated with an external Active Directory to access Enterprise Portal.
When an ADFS user is removed from the external Active Directory, that user does not have access to Enterprise Portal.
- Forms-based authentication: This allows users to authenticate against a custom database of users.
- Live ID: Users can authenticate themselves to Enterprise Portal by using their Windows Live ID.
The following figure shows the pluggable authentication architecture for Dynamics AX 2012:
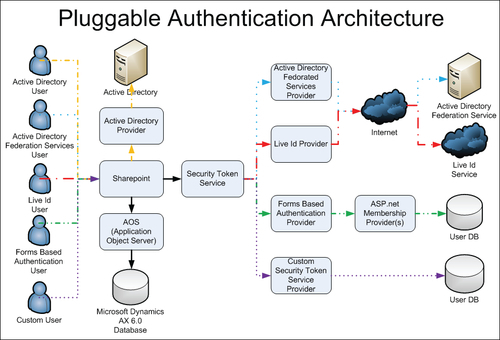
Source: What's New - Technical in Microsoft Dynamics® AX 2012 for Implementation
In Dynamics AX, the administration and authorization are based on the users, user groups, domain, and access rights. The new concept of security in AX 2012 has made the security easier to manage and provides a lot of benefits that enable the creation and editing of the user's duties and responsibilities more efficiently.
Users are assigned to roles based on their responsibilities in the organization and their participation in the business processes. So, when you make the necessary setup for editing or creating roles, the role assignment and privileges are updated based on changes in business data. Roles apply across all companies and not for a single organization, so the administrator no longer has to maintain separate user groups for each company.
Administrators and auditors can obtain information more easily about every user and their duties, responsibilities, and permissions; also, they can adjust the security for each user, based on their job in the company, with easier and faster steps.
Microsoft Dynamics AX 2012 provides better security audit trails and also a lot of security reports that help the auditors and administrators receive information about each user's privileges, duties, and permissions more easily. The new built-in feature Segregation of Duties makes sure no user has access to conflicting tasks or permissions.
In this section we will cover the following topics:
- Creating a new user
- Importing users from Active directory
- Creating a claim user
- Setting up user
- Setting up user options
- Setting up user relations
- Adding a user to a predefined profile
- Granting a user access to a specific company
- Tracking user-related information
- Assigning users to different roles
- Adding users to different roles
