Chapter 4. Knowledge of system as an element of cybersecurity argument
Abstract
System assurance embraces the entire system life cycle from the conception of ideas through to the retirement of a system. Systematic evaluation of the system's security posture requires a common framework to improve knowledge sharing between diverse disciplines and to identify, utilize, and manage relevant knowledge units in an integrated, coherent fashion. This framework involves a preselected vocabulary to describe systems, their external boundaries and internal resolution, behaviors, security policy, safeguards, and the entire assurance case.
This chapter describes the elements of the common vocabulary for managing facts about the system of interest as part of the integrated system model in support of the system assurance process. Chapters 5, 6 and 7 describe other units of cybersecurity knowledge used throughout the assurance process and show how these facts are integrated with the system facts to support the security posture analysis and gathering evidence for the system's assurance case.
Keywords
system, system boundary, subsystem, environment, operational environment, system model resolution, system life cycle, system life-cycle process, supply chain, supply chain assurance, security safeguard, conceptual commitment, common vocabulary, system architecture, viewpoint, operational view, system view, information exchange, system facts
When once your point of view is changed, the very thing which was so damning becomes a clue to the truth
—Arthur Conan-Doyle, The Casebook of Sherlock Holmes
Captain Hastings: Look at that, Poirot. Look at that view!
Hercule Poirot: Yes, well, views are very nice, Hastings. But they should be painted for us, so that we may study them in the warmth and comfort of our own home. That is why we pay the artist, for exposing himself to these conditions on our behalf.
—Agatha Christie, Poirot: The Adventure of Clapham Cook
4.1. What is system?
The word “system” became quite common in our everyday language to the extent that there is some confusion in its usage between different communities. Indeed, this word is used rather often, as we speak of “the solar system,” “a system of government,” “a health system,” “a system of winning poker,” a “communication system,” or a “weapon system,” and in so doing, we imply certain purposefulness and some sort of organization imposed on various elements that interact between themselves. A system is something that involves and exhibits behavior—a set of activities that can be defined in terms of the manipulation of materials, energy, or information.
A standard definition of a system by IEEE: System is a collection of components organized to accomplish a specific function or set of functions [IEEE 610.12].
Systems are studied by the general systems theory—an interdisciplinary theory about the nature of complex organizations in nature, society, and science, and is a framework by which one can investigate and/or describe any group of elements that are functioning together to fulfill some objective (whether intended, designed, man made, or not).
A standard definition of a system from the systems engineering community: A composite, at any level of complexity, of personnel, procedures, materials, tools, equipment, facilities, and software. The elements of this composite entity are used together in the intended operational or support environment to perform a given task or achieve a specific production, support, or mission requirement. [Air Force 2000]
On the other hand, certain communities prefer to use the word “system” in its narrow and concrete meaning—such as a particular computer application, or a physical system, a facility with a specific geographic location that involves a certain technology to provide service. Concrete systems are procured by organizations and fielded to support organizations and their operations [DoDAF 2007]. The context in which a concrete technical system operates is referred to as an “organization,” which is defined as “an organization structure with a mission.” In a business community, the term “enterprise” is often used to refer to the complex socio-technical organizations designed to provide goods and services to their customers.
National Institute for Standards and Technology (NIST) equates “system” and “information system” [NIST SP 800-18] and defines “information system” as a discrete set of information resources organized for the collection, processing, maintenance, use, sharing, dissemination, or disposition of information.
Certain communities prefer to use the term “network,” or “organization network” to mean a specific installation of personnel, operational procedures, technology, and physical facilities, that contain valuable information assets of the organization, in particular, the Network Rating Methodology from the National Security Agency (NSA) [Moore 2000].
The Information Technology Security community distinguishes a system, which is defined as a specific installation “with particular purpose and a known operational environment” and a product, which is defined as “a hardware and/or software package that can be bought off the shelf and incorporated into a variety of systems” [ISO 15408].
System assurance deals with man-made systems, created and utilized for the benefit of man. Cyber systems involve a combination of hardware, software, and humans. System assurance embraces the entire system life cycle from the conception of ideas through to the retirement of a system. System assurance supports the governance of systems and the processes for acquiring and supplying system products and services. Reasoning about systems for the purpose of evaluating security posture requires a common vocabulary that can be used to improve communication and cooperation between diverse disciplines and identify, utilize and manage relevant information units in an integrated, coherent fashion.
4.2. Boundaries of the system
The systems approach implies a commitment on our part to focus our attention only at the few selected elements (out of the entire universe), that are relevant to the particular behavior in question. For the systems approach to be applicable, it is important that the selected elements are discrete and identifiable. The set of elements selected as relevant to the system's behavior determine the so-called external boundary of the system. Systems approach involves another boundary that separates selected elements into the system and its environment. For a physical system, this boundary is usually the same as the scope of responsibility of the owner. A system performs its function as the result of interaction between its elements or subsystems. This interaction, which may be very complex indeed, generally insures that a system is not simply equal to the sum of its parts. Units of the system's behavior are the individual functions that are performed by the system's elements or the elements of its environment. The environment can include other systems that interact with the system of interest, either directly via interfaces or indirectly in other ways. The elements outside of the system boundary are only included because their interactions with the target system are relevant to the behavior of the system, therefore, any interactions between the elements of the environment of the system are usually ignored (see Figure 1).
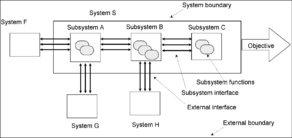 |
| Figure 1 Elements of the system |
System definition is based on the decision on where to draw the system's boundary. Consider a house alarm system. It includes a number of easily identifiable physical elements: several sensors, such as door/window contacts, motion sensors, glassbreak detectors, CO2 detectors, smoke detectors, water detectors; a control panel; a siren; a lot of wires if you are using an older model; or a wireless network (some newer wireless models have sensors that wirelessly communicate to the wireless receiver of the control panel). The control panel is powered by electricity and has a 12V backup battery. Should the battery be included as part of the alarm system? A house alarm system usually includes a communicator module, which is connected to the monitoring station. What about the telephone line that is running from the control panel to the telephone jack in the wall? What about the external line that runs from the house to the telephone pole? What about the telephone switching equipment in the grey metal box down the street? Do we include the monitoring station as part of the house alarm system? What about the police department and the fire department that are alerted by the monitoring station? Should they be included as parts of the system? The decision to establish the system boundary is made on the basis of what aspect of the system behavior is of concern. For example, if the immediate concern is how to adjust the motion detector in the family room so that Charlie the dog does not activate it when he jumps on the couch, the system boundary may be closed in. However, if the problem involves the response time when the police arrive at the premises, the boundary needs to be broader.
The choice of the appropriate system boundary determines the soundness and complexity of the analysis. Selection of the system boundaries must be commensurate with the goals of the analysis. To reach certain conclusions about a system, it may be desirable to include more elements within the external boundary. This may require complex, time-consuming analysis. If the money, time, and staff available are inadequate for this task and more efficient analysis approaches are not possible, then the system boundary must be “moved in” and the amount of information expected to result from the analysis must be reduced [Vesely 1981].
The entry points to the system are determined by the external interfaces based on the selected system boundary.
4.3. Resolution of the system description
The system approach also involves a commitment to a set of characteristics of the elements that are relevant to the behavior in question. These characteristics establish a limit of resolution of the system definition. The level of the resolution increases when one of the subsystems, for example B, is decomposed, for purposes of the analysis, into smaller sub-subsystems (see Figure 2). The smallest sub-subsystems, X, Y, and Z, are the smallest identifiable elements mentioned in the general definition of a system and constitute an internal boundary for the system. The more detailed level of resolution may involve additional characteristics of the system's elements. In the house alarm example, do you extend analysis to the individual cells of the photo sensor in the motion detector? What about the circuit board? Are you going to consider soldering on the circuit board? What about the molecular structure of the wires?
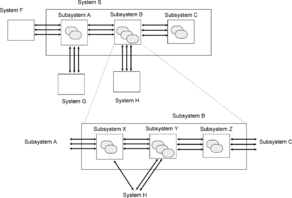 |
| Figure 2 Determining system's boundaries |
The limit of resolution (the internal boundary) must be established from considerations of feasibility and from the goal of the analysis. Once the limit of resolution has been established (and thus the “system's elements” defined), we assume no knowledge and are not concerned about interactions taking place at lower levels. Functions of the system elements are adjusted to the selected level of resolution to adequately describe the overall behavior of the system.
The same system can be described at various levels of resolution. In Figure 2, the interaction between subsystem B and system H (in the environment of the target system S), can be described directly at the top level of the resolution, or at a more detailed level of the protocol that involves subsystems X and Y. Functions of the subsystem B are implemented by the functions of the corresponding subsystems X, Y, and Z at a more detailed level of resolution.
We now see that the system boundary serves to delineate system outputs (effects of the system on its environment) and system inputs (effects of the environment on the system); the limits of resolution serve to define the elements of the system and to establish the basic interactions within the system.
Cyber systems involve multiple layers of protocols and involve interactions between a multitude of systems; therefore, the security boundary that the owner of any given system has to be concerned about can be extremely large and complex. Vulnerabilities may occur in different components, often outside of the jurisdiction of the system's owner (and beyond his reach) or at lower levels of the protocol outside of the resolution of the original system definition. As the consequence, a rather detailed resolution of the system needs to be considered in order to understand and reduce the risk of cyber attacks.
4.4. Conceptual commitment for system descriptions
It is important to understand that the determination of the system boundaries and limits of resolution are fundamental decisions of the system analysis. While certain elements of a system, such as the physical elements and their relationships, observable events, and the objects being exchanged are often predetermined by the corresponding identifiable objects in the real world, the functions of the elements are often abstractions introduced by the system analysis based on the selected level of resolution. In addition, certain system elements are introduced during the system analysis as aggregations of existing physical elements to lower the resolution and obtain a more compact and comprehensive system definition. For example, the home alarm system can be described as a sensing subsystem (an aggregation of all contacts, sensors, and detectors), a control subsystem (involving the control panel and all keypads), and the signaling subsystem (involving the siren and the communicator module and the monitoring station).
The system's elements, their characteristics, the system boundaries, and limits of resolution are defined before the security analysis begins and are adhered to during the analysis, because these elements constitute the conceptual commitment for the target system and the foundation of the vocabulary for describing any properties of the system of interest, including its security. However, in practical situations, the boundaries or limits of resolution may need to be adjusted because of information gained during the analysis, in particular, the level of resolution of some system elements may need to be increased to allow more accurate analysis. The system boundaries and limits of resolution, and any adjustments, must be clearly defined in order to facilitate information exchanges during the analysis of the system.
Now let us share a few comments, which will help put the material of this chapter into the bigger context of this book. We believe that the idea of a “conceptual commitment” is central for establishing an ecosystem for exchanging knowledge. Conceptual commitment means using a carefully preselected set of concepts (a vocabulary) to describe systems, their behaviors, security policy, safeguards, and the entire assurance case. The elements of such a preselected common vocabulary consist of nouns and noun phrases that describe individual entities/objects in the system and in any associated domains; and verbs and verb phrases that describe relationships between objects. We use a certain methodology to build discernable common vocabularies; this methodology helps identify discernable noun and verb concepts (this methodology is introduced in Chapter 9). Discernable concepts are important because they are unambiguous and allow maintaining traceability links to lower levels of resolution. Incidentally, the OMG Assurance Ecosystem includes standards that define how to exchange well-defined vocabularies and how to systematically transform a well-defined vocabulary into an XML schema for exchanging information about the individual objects. At the same time, the elements of the well-defined vocabulary are identifiable facts that can be stored in a database, or in a suitable fact-based repository. One of the characteristics of the OMG system assurance process is the use of the “integrated system model,” which is stored in a fact-based repository. In the upcoming chapters we are going to introduce the elements of the common vocabulary for cybersecurity for the OMG Assurance Ecosystem. We will do that with varying degrees of formality, because this book is not a formal specification. This chapter will introduce the noun and verb concepts in a very informal way because we assume familiarity with the basic system engineering concepts, and also, because these concepts are, in general, well established and are used in a rather uniform way. However, keep in mind that when we are saying “identify,” for example, “identify a system component,” this means: use the definition of the “system component” from the common vocabulary, apply the definition to locate the corresponding object in the system of interest, and then add the corresponding facts into the integrated system model. When the objects are already known (because they were identified as part of a preexisting process in the life cycle of the system of interest), the task of “identification” is to map the existing definition to the common vocabulary and add the new facts to the integrated system model. The mapping between vocabularies is often required because different methodologies make different conceptual commitments.
When managing descriptions of the system at increasing levels of resolution, it is important to maintain the so-called vertical traceability links between the elements at different levels of resolution. In terms of a physical, fact-based repository, a traceability link is a particular relationship (a fact) in which one object is implemented by one or more other objects. For the purposes of the cost-efficient analysis, it is also important to be able to transfer the characteristics of systems, established at higher levels of the resolution, to the lower resolution descriptions (where there are fewer elements, with more abstract functions and characteristics), so that the majority of the analysis and managing of the information is done using the system description with the lower resolution. Chapter 9 provides further guidance related to managing multiple pieces of information, managing conceptual commitments, and describes the mechanisms for performing analysis at varying levels of resolution. Chapter 11 describes a standard protocol for exchanging system facts that extends the vertical traceability links all the way down to the very low-level implementation facts (such facts are discovered automatically by compiler-like tools).
The integrated system model also has the so-called “horizontal links,” which are relationships between objects, based on the verb concepts defined in the common vocabulary. When facts from different vocabularies are integrated, for example, when we want to map a threat to a system function, we establish a physical relationship (a fact) between the two concepts from the two parts of the common vocabulary.
The rest of this chapter describes the elements of the common vocabulary for managing facts about the system of interest as part of the integrated system model in support of the system assurance process outlined in Chapter 3. Chapters 5, 6 and 7 describe other units of the cybersecurity knowledge used throughout the assurance process and shows how these facts are integrated with the system facts to support the security posture analysis and gathering evidence for the system's assurance case.
4.5. System architecture
Knowledge about systems of concern to system assurance includes both the general knowledge of the systems theory and systems engineering, as well as specific knowledge about a particular system under assessment. System knowledge involves several viewpoints:
• Hierarchy: Systems, Subsystems, Units, Assemblies, Components, Parts, Activities, Protocols
• Elements: Hardware, Software, Personnel, Procedures, Entry points, Environments, Facilities, Documentation
• Operations: Functions, Tasks, Modes, Phases
• Domains: Boundaries, Zones, Organizational Boundaries, Criticality, Complexity, Security, Safety
• Life cycle: Activities, Enabling Systems, Supply Chain
These viewpoints are interconnected: a single identifiable element of a system participates in multiple relationships with other elements in other viewpoints. For example, a server participates in several hierarchies: A server is part of the accounting subsystem, and at the same time, it is part of the network of the data center unit. The accounting subsystem is part of the finance department hierarchy, which is in turn part of the organization of interest. However, the server is owned by a different organization, which leases it to the organization of interest. There are diverse hierarchies of elements associated with the server itself: The server consists of two RAID disk arrays, each with four hard disks; a processing unit, consisting of four core processors; a memory unit, consisting of four memory chips; a bus; two network controllers; and several other controllers of the peripheral devices. Another hierarchy associated with the server includes various software products installed on this server, including the operating system, device drivers, the transaction processing monitor, the application server, the web server, and various application programs. The server supports various functions, such as managing the ledger and managing the inventory; however, there are other equipment units that are also involved with these tasks, such as the database server, the network switch, the firewall, the desktop computers, etc. The server of interest is associated with several other hardware units that are part of the same network but that are involved in different business functions. Several personnel roles are associated with the server and various functions that it is involved with. The server is located in a certain facility. The server supports several interfaces (both at the logical level and at the physical level), including low levels of protocol; for example, the server supports web access over HTTP protocol, but at the same time supports TCP and IP protocols and the Ethernet protocol. The protocols supported by the server also constitute a hierarchy. Each of these viewpoints involves certain events and scenarios.
Life cycle processes bring another set of viewpoints to the system organization. The server was manufactured by another organization at yet a different location. The server was installed by yet another organization. A different organization produced the operating system. The web server software is developed using the open source model. A certain application program uses a web service provided by the human resources department of the organization of interest (which is located in a different facility in a different country). Another application uses a web service provided by an external organization. Most of the application software was developed by the personnel of the engineering department of the organization of interest, while the business objects layer was implemented by a contractor.
Different stakeholders of the system have specific concerns, and therefore, need different views of the system, which focus on the elements, hierarchies, and relationships that are relevant to their concerns. Facts about the system of interest are arranged into meaningful units, called views, which focus on a few elements and their relationships, tailored to the specific concerns of system's stakeholders. Each view is defined by the corresponding viewpoint, which describes what element types and relationship types need to be addressed by the compliant view. The viewpoint is an element of generic knowledge that is utilized as a template for building a view about the system.
Figure 3 illustrates an integrated system model that contains certain unique elements and relationships between them, including hierarchies. In particular, the model contains four types of elements (represented as circles with different shading), two types of relationships (thin and thick lines), and several overlapping hierarchies. The middle part of the figure illustrates three views of the system. Note that certain elements occur on multiple views, and that each view contains a limited selection of elements and relationships. The right part of the figure shows the viewpoints describing the views, which illustrates the rules for selection of the elements and relationships on each view. In particular, the top view only shows the white elements and how they are organized in hierarchies. It does not show black and grey elements, despite the fact that there are relationships to them. This view does not show the hierarchy of the grey elements either. The bottom two views share the same viewpoint. They focus on thick relationships between white, black, and grey elements, focusing on a certain initial element.
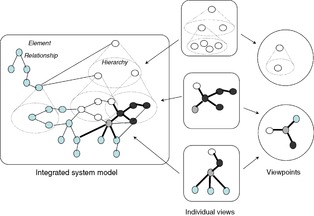 |
| Figure 3 Illustration of integrated system model |
ISO/IEC 42010 defines system architecture as “the fundamental organization of a system embodied in its components, their relationships to each other, and to the environment, and the principles guiding its design and evolution.” The concept of views and viewpoints is central to the ISO architectural description of systems. The particular set of viewpoints is determined by a particular architecture framework, while the vocabulary for the system elements and their relationships is, to a large extent, specific to the system of interest.
Each viewpoint also defines a vocabulary and is thus part of the conceptual commitment for exchanging information about the system of interest.
4.6. Example of an architecture framework
The US Department of Defense Architecture Framework (DoDAF) [DoDAF 2007] describes a particular set of 26 viewpoints to ensure uniformity and standardization in the documentation and communication of architecture. The 26 DoDAF viewpoints are designed to document the entire architecture, from requirements to implementation.
Viewpoints can be grouped into four categories of views (see Figure 4):
• Operational Viewpoints (OV): Focuses on the behaviors and functions describing the enterprise mission aspects.
• System Viewpoints (SV): Describes the system and applications supporting the mission functions.
• All Viewpoints (AV): Is the overarching information describing the architecture plans, scope, and definitions.
• Technical Standards Viewpoints (TV): Describes the policies, standards, and constraints.
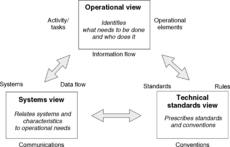 |
| Figure 4 Department of Defense Architecture Framework Information Flow |
Table 1Table 2Table 3 and Table 4 illustrate the architecture views of the DoDAF. As you can see, these products represent the fundamental viewpoints described above.
4.7. Elements of a system
System description uses the following fundamental elements:
• System elements (referred to as subsystems, components, or nodes);
• Relations between the system elements (referred to as channels or interfaces);
• System functions (activities that comprise the system's behavior; functions are performed by nodes);
• Relations between the system functions (dependencies between the activities);
• Objects that are exchanged between the functions (in many cases, these are limited to information elements, but in a general system, these objects can include material objects, energy, even people, for example, when describing the National Hockey League as a system that involves exchanges between various clubs).
Systems can be described at several increasing levels of resolution. At a minimum, there are two such levels: operational and systems.
Operational viewpoints describe the tasks and activities, operational elements, and information exchanges required to conduct operations. Operational viewpoints involve the following key noun concepts:
Operational node is an element of the operational architecture that produces, consumes, or processes information. Usually an operational node represents an operational role, fulfilled by an organization or a human, and organization, or an organization type, a logical grouping of organizations, etc.
Information exchange needline represents a need for some kind of information exchange between two connected operational nodes. A needline represents a flow of information, and not a physical communications link.
Information exchange is an act of exchanging information between two distinct operational nodes and the characteristics of the act, including the information element that needs to be exchanged and the characteristics of the exchange; for example, transaction type, access control requirement, confidentiality, integrity, availability, dissemination control, protection needs, classification, and classification caveat.
Information element is the information content that is required to be exchanged between nodes. Information elements can be organized in hierarchies.
Operational activity is an action performed in conducting the operation of the enterprise.
Operational activity is performed at operational node. Activities can be organized in hierarchies. Operational capability is one or more sequences of activities.
Event is a specification of a significant occurrence that has a location in time and space. In the context of state diagram, an event is an occurrence that can trigger a transition.
State is defined as a condition or situation during the life of an object during which it satisfies some condition, performs some activity, or waits for some event.
Figure 5 illustrates the operational views and their relationships.
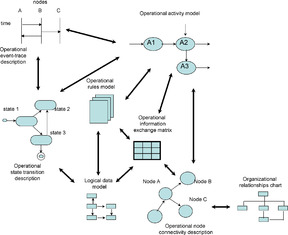 |
| Figure 5 Relationships between operational views |
Systems viewpoints describe systems, services, and interconnections supporting operations. System viewpoints involve the following noun concepts.
Systems node – a node with the identification and allocation of resources (e.g., platforms, units, facilities, and locations) required to implement specific roles and missions.
System item – an element of a system, such as a hardware item or a software item.
Service – a distinct part of the functionality that is provided by a system on one side of the interface to some other system on the other side of the interface to include those capabilities to execute a business or mission process or exchange information among both machine and human users via standard interfaces and specifications.
Interface is an abstract representation of one or more communication paths between system nodes or between systems (including communication systems).
System function – a data transform that supports the automation of operational activities or information exchange.
Figure 6 illustrates the relationships between the operational and system views.
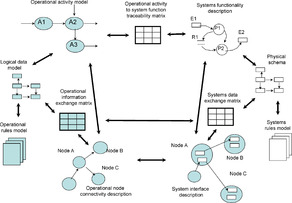 |
| Figure 6 Relationships between the operational and system views |
4.8. System knowledge involves multiple viewpoints
A system can be described from multiple viewpoints. We need to examine various viewpoints in more detail to decide which of them is more suitable to contain the “location” of vulnerability.
The following are the major categories of viewpoints:
• The Event Trace viewpoint
• The Structure viewpoint
• The Data Flow viewpoint
• The “Rules” viewpoint
• The State Transition viewpoint
The Event Trace viewpoint is literally the most visible one, because event flow views describe sequences of events. Events are individual, observable occurrences. What occurrence is claimed to be observable is determined by the selection of the boundaries of the system, both external and internal. Usually, events are observable at the external boundary of the system. The Event Trace view shows the system in operation, as it can be perceived by an outside observer. Event Trace view shows information exchanges between the elements of the system. Event Trace is often described as a dynamic viewpoint that represents behaviors of the system as sequences of events in the order in which they occurred in time. Certain events may occur simultaneously. Certain events that occur together (either in sequence or simultaneously) can be combined into “phases,” which are often confused with “states.” Certain events and event sequences (at some resolution, of course) are common to large families of systems. A debug trace of an application is an event view, and the contents of a log file is an event view.
The next viewpoint is the Structure viewpoint, which is related to the “locations” of the systems as it describes the elements of the system as the “places” in which activities that produce events take place. The elements of the system are involved in interactions, which mean that there is flow of something between various elements. The Structure viewpoint defines the participants of the interactions, which is, of course, determined by the external boundaries (the scope of the system) and the selected resolution. Some of the “places” are directly at the boundary of the system, which means they are the discrete points of interaction between the system and its environment. These elements are often referred to as the system “entry points.”
Additional Structure views can be used to represent various relationships between nodes; for example, an organizational relationship chart represents organizations and their parts, roles, and other relationships among organizations.
The events are correlated with the flow of objects, although a software intensive system is mainly about the flow of information. This viewpoint can describe the flow of money, the flow of color, the flow of goods, and the flow of personnel, even the flow of service offerings, or the flow of knowledge. The Data Flow viewpoint describes how data flows between the activities of the system or between the activities and the system's environment as the system performs its function. This viewpoint emphasizes the capabilities and operational activities of the system, the relationships between activities, their inputs and outputs, etc.
Flows of data and events are determined by some rules that distinguish one system from another. The Rules viewpoint is the static viewpoint that describes the elements of the system, the events they cause, and the rules they impose on the event flow, the associated data flow, how these rules determine the possible events of the system in operation, and how the rules constrain possible behaviors, which are sequences of events. The code of a software application is an example of a Rules view.
Now we have defined all the ingredients, and we can define the concept of a state, which is somewhat more elusive. In general, state is defined as a condition or mode with regards to circumstances or with regards to form, such as structure, growth, or development. State is a very fundamental concept, but it is the least visible one, since it is an abstraction of behavior.
State corresponds to a "stable" condition of the system of interest, at a certain period of time, that is determined by the behavior of the system at the previous periods. Usually, a state can be described by a simpler subset of the behavior rules. Behavior of a stateless system does not depend on the previous periods. As opposed to the behavior phases (or event-based states), systems may easily have an infinite number of states. Defining vulnerabilities in terms of states should be avoided, because of the difficulties in systematic examination of all states. Viewpoints as locations of vulnerabilities are illustrated at Figure 7.
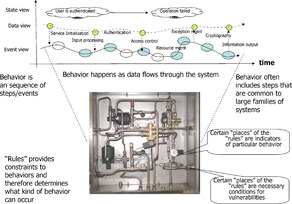 |
| Figure 7 Illustration of viewpoints of the system |
Additional viewpoints may be needed to address the concerns of other stakeholders of the system. For example, the Motivation viewpoint describes the objectives of the system (the ends) and the mechanisms (the means) that are used to achieve the objectives.
4.9. Concept of operations (CONOP)
The CONOP (sometimes called ConOps) stands for the Concept of Operations. CONOP is a brief overview of a system at a low resolution. Usually, a CONOP document addresses the following questions:
• What does the system do for the organization?
• Who are the stakeholders? In particular, who are the User and other key players, such as the System Operator, the System Security Officer, etc.?
• What is the motivation for deploying the system (e.g., what current deficiencies are addressed for which the IT requirements are defined)?
• When are the main activities occurring? (the event flow view)?
• What are the main activities (decision points)?
• What are the connection points to other systems?
CONOP also defines the key security requirements of the system, such as the access rights of the users and their need-to-know. Chapter 12 illustrates a CONOP for the system used in the case study.
4.10. Network configuration
In general, a computation is a sequence of steps/events performed by the system or one of the activities within the system. The computation is performed by the code, which is supported by other components of the system. Code provides the constraints to computations and therefore, determines which computations can occur. For example, the computation is determined by the control flow relationships between individual activities, and further by the data flow relationships describing how individual activities act as producers and consumers of data. These relationships are the constraints for the computation (see Figure 7).
In order to analyze a computation, all system components have to be considered, including the so-called application code, but also the runtime platform and all runtime services, as some of the key control and data flow relationships are provided by the runtime platform, as the computation flows through the application code into the runtime platform and services and back to the application code. Application code alone in most cases does not provide an adequate picture of the computation, as some segments of the flow are determined by the runtime platform and are not visible in the application code. For example, while a large number of control flow relationships between different activities in the application code are explicit (such as statements in a sequence, or calls from a statement to another procedure), some control flow relations are not visible in the code, including the so-called callbacks, where the application code registers a certain activity with the runtime platform (for example, an event handler or an interrupt handler) and it is the runtime platform that initiates the activity. Without the knowledge of such implicit relationships, the system knowledge is not complete at a very fundamental level, leading to incomplete coverage of code analysis by vulnerability detection tools, and subsequently, to false negative and false positive report findings.
A system is a collection of activities that exchange information to achieve some common purpose. Computations occur at system nodes that are connected by channels. Following the NIST Common Vulnerability Scoring System (CVSS) [NIST IR-7435 2007], [Schiffman 2004] approach we distinguish local channels between system nodes deployed at the same machine, adjacent network channels between system nodes deployed at the same local area network, and remote channels. This distinction is important because it determines the class of access required in order to exploit vulnerability. Each system node performs computation to provide services to other system nodes or the environment of the entire system. Data interchanges use channels. We distinguish between data at rest (for example, databases), data in motion (data in the channel), and data in use (data flowing inside the computation) (see Figure 8).
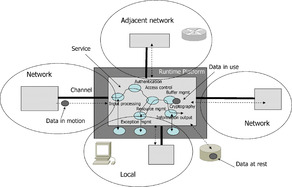 |
| Figure 8 Network context for computation |
The runtime platform manages resources on behalf of the application. This is a very important consideration, as, in fact, many vulnerabilities are related to the usage of the resources (see Figure 9).
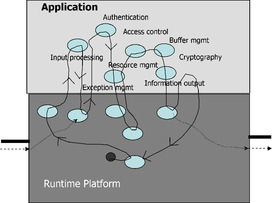 |
| Figure 9 Runtime platform – the key component when assessing system |
4.11. System life cycle and assurance
So far we have addressed the system facts that are related to the operations of a system. These facts describe the system as a mechanism that performs some activities to achieve required objectives. The system facts addressed the common vocabulary for describing the system in terms of its components, functions, and rules, and the implications of selecting boundaries and resolutions of such descriptions. The evolution of the system (covering the time from conception to operations, and from operations to disposal) bring another dimension to the knowledge of system. Consideration of the system life cycle is an important concern for system assurance because the evolution of the system also includes the evolution of its security posture. Ultimately, a strong security posture is determined by organization of the system (the various rules that are enforced during the operation of the system, whether by technical mechanisms, physical mechanisms, or administrative measures). However, the confidence in the security posture involves knowledge of the evolution of the system, and claims regarding various aspects of how the system was put together. Cyberdefense measures extend to the early phases of the system life cycle: Defenders need to be confident that the desired security mechanisms are built correctly so that they are available during the operations as efficient elements of the operational defense. In order to achieve this, additional defense mechanisms are designed and added to upstream activities of the system life cycle. The evolutionary countermeasures are accounted for in the system assurance case together with the operational countermeasures. Claims about evolutionary countermeasures involve knowledge of system life cycle activities prior to operations, and sometimes also of the activities involved in the disposal of the system.
The system life cycle involves multiple activities. ISO/IEC 15288:2008, “Systems and software engineering—system life cycle processes,” defines a standard framework for describing the system life cycle in terms of various activities involved in creating and utilizing systems. Collectively these activities are bringing together the elements of the future system and are imposing the required organization upon them so that the system emerges, and when launched into operation, its elements are engaged in coordinated interactions that satisfy the objective of the system. The system assurance process as described in Chapter 3 is a logical cross section of the diverse activities throughout the system life cycle organized together to systematically build confidence in the security posture of the system.
4.11.1. System life cycle stages
The system life cycle framework defined in ISO/IEC 15288:2008 [ISO 15288] focuses on the underlying essential set of characteristic life cycle stages that exist in the complete life cycle of any system that exists, despite a necessary and apparently limitless variety in system life cycles. Life cycles vary according to the nature, purpose, use, and prevailing circumstance of the system. However, the system life cycle activities can be arranged into several common categories, which become parts of the common vocabulary for descriptions of systems. The first such categorization is based on the evolutionary timeline. Evolution of each system can be arranged into several stages. Each stage has a distinct purpose and contribution to the whole life cycle and is to be considered when planning and executing the system lifecycle (see Table 5).
The stages provide a framework within which enterprise management has high-level visibility and control of the project and technical processes. The stages describe the major progress and achievement milestones of the system through its life cycle; they give rise to the primary decision gates of the life cycle. These decision gates are used by organizations to contain the inherent uncertainties and risks associated with costs, schedule, and functionality when they create or utilize a system.
4.11.2. Enabling systems
Throughout the life cycle of a system of interest, essential services are required from systems that are not directly a part of the operational environment, e.g., development system, production system, training system. Each of these systems enables a certain stage of the system of interest to be conducted and facilitates progression through the system life cycle. These enabling systems contribute indirectly to the services provided by the system of interest when it is being utilized.
As with any system, each enabling system also has its own life cycle. Each enabling system's life cycle is linked and synchronized to that of the system of interest, specifying, in particular, when a need for it is specified during conception of the system of interest, or later, if lead times permit, and when the enabling system is operated to provide its particular service to the system of interest.
This has profound implications to the system assurance process. Some of the security controls (safeguards) for the system of interest are applied to the system of interest itself. For example, in a home security system, there is a requirement to install a sensor on every entrance door and on every glass panel of the ground floor of the building; such safeguards can often be examined during the assessment of the system of interest as they are implemented by certain artifacts within the scope of the system of interest; other requirements applied to the system of interest include administrative controls, for example, the requirement that the residents entering the building receive training regarding tailgating.
On the other hand, some of the security controls are applied to one of the enabling systems; for example, adequate testing of the door sensors by the manufacturer is applied to the production system, and adequate design of the sensors is an example of a security control applied to the development system. The system of interest, as well as any of the enabling systems, includes people, process, hardware and software elements, its own operational environment, facilities, etc. For example, system assurance may involve several physical security controls, separate for the development system facilities, production system facilities, and the facilities of the system of interest. Each system involves its own threat model. In general, each system has its own risk management process; however, from the viewpoint of the system of interest, there are often contractual relations in place to deliver assurance back to the main assurance process of the system of interest, because threats to the enabling systems may have consequences affecting the system of interest (see Figure 10).
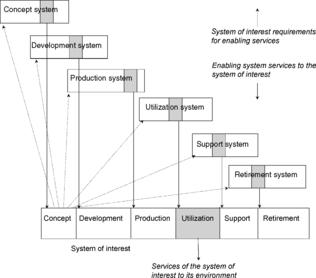 |
| Figure 10 System of interest and supporting services from enabling system |
These considerations determine the location of the security controls and the sources of evidence for assurance. Security posture of the system of interest (during its operation) is affected by all stages of all enabling systems. Therefore, the security controls need to be placed to all critical systems, based on the combined threat model. The evidence for the security evaluation consists of two major categories:
• The process-based evidence, which includes the records of security-related activities throughout the system life cycle, including those in the system of interest and in the enabling systems; the results of verification and validation performed at various stages, including those in the enabling systems; and the results of system analysis at various stages. Process-based evidence is gathered throughout the system life cycle as the corresponding activities take place. Therefore, one cannot retrofit this evidence, for example, during the security assessment performed during the transition into the operation of the system of interest. This evidence is gathered by the participants of the system life cycle, including the enabling systems. The system assurance activities that result in gathering the process-based evidence must be planned through the system assurance case before the corresponding stages take place. The evidence of the security controls throughout the concept, development, and production phases (including the enabling systems) contribute to the process-based assurance. The evidence of the system analysis throughout the system life cycle contributes to the goal-based assurance.
• The product-based evidence, which includes the evaluation of the process-based evidence, and any independent analysis of the system of interest. This analysis is restricted to the system of interest and is to a large extent predictive. The product-based evidence is gathered by the security evaluation team. The verdict of the security evaluation is based on the product-based evidence.
The balance between the process-based evidence and the product-based evidence determines the rigor of the assurance as well as the cost of assurance. Process-based assurance involves a reasonably small overhead for gathering evidence throughout the life cycle. The process-based assurance provides indirect evidentiary support to the security posture of the system, while system analysis usually provides more direct evidence. The key parameters in this equation are the efficiency of the system analysis, and the efficiency of managing the evidence items and evaluating them within the context of the system assurance case.
Utilization stage enabling systems are of particular importance to assurance of the operational risk because their operational stages coexist with the operational stage of the system of interest. They include, among others, operating system, services that are utilized by the system of interest, support infrastructure, such as power supply or internet provisioning, operator training system, and user training systems. Security safeguards applied to these systems have more direct impact on mitigating the operational risk of the system of interest.
4.11.3. Supply chain
Each enabling system may itself be considered as a system of interest, having in turn its own enabling systems. For system assurance, it is important to understand the entire supply chain organization. It is very common that multiple components of the system of interest and its immediate enabling systems are preexisting, off-the-shelf components (for example, commercially available hardware, operating systems, programming languages and the corresponding programming environments, configuration management systems, and network equipment, to name just a few key elements of a software intensive system). Some of these components are directly integrated as parts of the system of interest, while other components contribute indirectly by enabling the development and production stages of the life cycle of the system of interest, and thus, affecting its elements. Preexisting components limit the end-to-end assurance of the system of interest because certain security controls cannot be enabled, and the corresponding evidence may not be available. Since the initial level of assurance of the preexisting components may be low (the initial assurance is the assurance case that is provided with the component), assurance must rely on the evaluation evidence resulting from the direct evaluation of the artifacts of the system of interest.
4.11.4. System life cycle processes
The system life cycle framework, defined in ISO/IEC 152888:2008, involves the following four groups of processes.
1. Enterprise processes: The enterprise processes manage the organization's capability to acquire and supply system products or services through the initiation, support, and control of projects.
2. Agreement processes: Establishment of agreements with organizational entities external to the organization and internal to the organization. The agreement processes consist of the acquisition process—used by acquiring organization—and the supply process—used by supplying organizations. System assurance is often an important item for agreement between an acquirer and the supplier.
3. Project management processes: The project management processes are used to establish and evolve project plans, to assess actual achievement and progress against the plans, and to control execution of the project through to fulfillment.
4. Technical processes: The technical processes are used to define the need for a system and to transform that need into an effective product, to permit consistent reproduction of the product where necessary, to utilize the product to provide the required services, to sustain the provision of those services and, when the product is retired from service, to dispose of that product.
Enterprise processes provide the context for the system assurance process. According to ISO/IEC 15288:2008, the enterprise processes include the enterprise management process, investment management process, system life cycle management process, and resource management process. These processes are often referred to as the enterprise governance.
Enterprise management produces strategic and tactical plans and objectives for system life cycle management, including quality management, assurance, and control in accordance with ISO 9001. Enterprise management is the main consumer of the system assurance, which contributes to the assessment of the impact of security on strategic and tactical plans to review the system life cycle policies and procedures and confirm their continuing suitability, adequacy and effectiveness, and make changes as appropriate.
The system assurance process, as it is outlined in Chapter 3, must be managed together with other life cycle processes because it consumes resources of the enterprise, and is usually considered a good investment, which enables the organization to become more competitive within a larger supply chain, and not only a “necessary evil” to satisfy the mandatory regulatory requirements [NDIA 2008].
According to ISO/IEC 15288:2008, the project management processes include the planning process, assessment process, control process, decision making process, risk management process, and configuration management process. Project management processes contain locations in which many important process-based administrative safeguards are applied.
The project definition phase of the system assurance process, as outlined in Chapter 3, is the point of alignment with the enterprise processes, including the determination of the objectives, the criteria, and the budget of the assurance. Assurance case enables rational decision making regarding the activities involved in achieving strong security posture of the system by identifying the actions that provide adequate justification, including the rationalization of safeguards and the corresponding arguments and evidence. Assurance case is an instrument for rational governance of the system life cycle activities because it identifies and justifies what safeguards will be implemented (e.g., trusted supplier selection, trusted component acquisition, programming language selection, anti-virus tool use), and what evidence must be collected to justifiably achieve the required security posture at the desired level of assurance. Assurance case development clarifies the interaction between functionality, cost, schedule, security, safety, dependability, and other attributes of the system so that the appropriate trade-offs can be made through risk management. System assurance is tightly related with the risk assessment process because the knowledge of the operational environment and the particular threats is an input to the system assurance process, where it is used to justify the efficiency of the security safeguards.
System assurance, including the assurance case development and maintenance, system evaluation, and evidence gathering is executed as part of the technical processes of the system life cycle. According to ISO/IEC 15288:2008, the technical processes include the following:
• Stakeholder requirements definition process: This process defines the need for a system that can provide services to users and other stakeholders in a defined environment. This is achieved by developing a model, frequently textual, that concentrates on system purpose and behavior and is described in the context of the operational environment and conditions. The stakeholder requirements identify the parties involved with the system throughout its life cycle and express their needs, wants, desires, and expectations, together with the constraints they and the operational environment impose. This involves capturing, clearly articulating, and managing the requirements of each and every stakeholder, or stakeholder class, in a form that permits continuous tracing of decisions to their needs throughout the life cycle. The Stakeholder Requirements are the reference against which each and every resulting operational system services is validated in order to confirm that the system fulfills needs.
• Requirements analysis process: This process transforms the stakeholder, needs-driven view of desired system services into a technical view of required system products that could deliver those services. The resulting system requirement specifies, from the developer's perspective, what the system is required to do in order to satisfy stakeholder needs. The objective is to build a representation of future system products that will meet stakeholder needs, and that, as far as constraints permit, avoids implementation issues. The system requirements are the basis for tests that verify the conformance of a supplied system to the designers' intended solution.
• Architectural design process: This process synthesizes a solution that satisfies system requirements. Architectural design involves identifying and exploring one or more implementation strategies at a level of resolution consistent with the system's technical and commercial requirements and risks. From this, a design solution is defined in terms of the requirements for a complete set of technically and commercially viable components from which the system is configured. The architectural design is also a basis for planning and devising an assembly and test strategy that will detect and diagnose faults during the integration steps.
• Implementation process: This process implements a component required in an acquirer's system. This may be achieved by designing, making, and testing a novel component; making and testing a new component according to an existing design; or adapting and testing an existing component. The implementation process continues the design undertaken at the system/subsystem levels by performing detailed design in accordance with selected implementation technologies. The component is fabricated and/or assembled according to the selected implementation technologies. A fabricated or adapted component is tested against criteria derived from the component characteristics defined in the system requirements and possibly in an acquisition agreement.
• Integration processes: The verified components are assembled to create the system product specified in the system requirements.
• Verification process: Through assessment of the system product, verification demonstrates that its behavior and characteristics comply with its specified design requirements. Verification provides the information required to effect the remedial actions that correct failings in the realized system or the processes that act on it.
• Transition process: The transition process installs the verified system in its operational locations according to an agreed schedule, together with the utilization stage enabling systems (e.g., operating system, support system, operator training system, user training system), as defined in agreements, in order to establish the capability to provide the system services specified by the stakeholder needs.
• Validation process: The validation process is conducted to provide objective evidence that the services provided by the system when in use comply with the needs of the stakeholders and are defined in the requirements documents contained in the agreement to acquire the system. Where variances are identified, these are recorded and guide corrective actions. Since validation is a comparative assessment against needs, it also results in confirmation that stakeholders', and in particular the users', needs were correctly identified and requested; again, variances lead to corrective actions.
• Operation and maintenance process: The operation and maintenance process enables staffing and training personnel for operation and maintenance activities, operating the system, maintaining the system, monitoring the system and the operator-system performance, and recording problems for analysis.
• Disposal processes: The disposal process is applied to deactivate and remove the system from operational service, consigning it to a final condition, and returning the environment to its original or an acceptable condition. System elements are destroyed, stored, and/or reclaimed in an environmentally sound manner.
Security-related system assurance makes security considerations visible throughout the entire system life cycle, which allows systematic analysis of all factors contributing to the security posture of the system and planning the related activities and safeguards in a cost-efficient, timely, and consistent manner. The value of an end-to-end assurance case is that the systematic and objective development of the security argument and claims accumulates knowledge related to the security posture in a single integrated system model; extends justification to the existing risk management and security activities; and accumulates evidence from multiple sources.
4.11.5. The implications to the common vocabulary and the integrated system model
System life cycle considerations, including the stages and the technical processes, enabling systems, and the supply chain has implications to the common vocabulary for describing system facts and the organization of the integrated system model for assurance.
The integrated system model no longer has only one system boundary; it needs to include the boundaries of various enabling systems (commensurate with the selected scope of assurance). Relationships between system elements must include evolutionary relations, where an element of an enabling system creates an element of the system of interest. The integrated system model must include the organizational boundaries and attributes of the supply chain elements.
Finally, the integrated system model must be able to include the system life cycle processes and their activities in order to provide traceability links between the safeguards and the corresponding activities in the system life cycle (see Figure 11).
 |
| Figure 11 System life cycle with corresponding views |
Bibliography
Air Force System Safety Handbook. (2000) Air Force Safety Agency Kirtland AFB; NM 87117-5670.
DoD Architecture Framework. 1.5. (2007) .
IEEE Std 610.12-1990 IEEE Standard Glossary of Software Engineering Terminology Description. (1990) .
ISO/IEC 15408-1:2005, Information Technology – Security Techniques - Evaluation Criteria for IT Security Part 1: Introduction and General Model. (2005) .
ISO/IEC 15288-1:2008 Life Cycle Management – System Life Cycle Processes. (2008) .
NDIA, Engineering for System Assurance Guidebook. (2008) .
A.P. Moore, B. Strohmayer, Visual NRM User's Manual: Tools for Applying the Network Rating Methodology. (2000) Naval Research Lab Washington DC Center For Computer High Assurance Systems.
NIST SP 800-18 Information Security Guide for Developing Security Plans for Federal Information Systems. (2006) .
P. Mell, K. Scarfone, S. Romanosky, NIST Interagency Report 7435 The Common Vulnerability Scoring System (CVSS) and Its Applicability to Federal Agency Systems. (2007) .
M. Schiffman, G. Eschelbeck, D. Ahmad, A. Wright, S. Romanosky, CVSS: A Common Vulnerability Scoring System. National Infrastructure Advisory Council (NIAC). (2004) .
W.E. Vesely, F.F. Goldberg, N.H. Roberts, D.F. Haasl, Fault Tree Handbook. (1991) US Nuclear Regulatory Commission; NUREG-0492.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
