Chapter 21. Staying Safe
The Internet reveals humanity both at its most glorious heights of achievement and at its downright sleaziest. As you gaze at the new moons of Pluto (as seen from the Hubble Space Telescope at http://hubble.nasa.gov), your email inbox is filling up with viruses awaiting their chance to hop onto your hard drive. Mixed in with those messages are pitches from rip-off artists and identity thieves.
Threats from the Internet fall into four broad categories: programs designed to damage the information on your hard drive (viruses, worms, and the like), software that steals personal information from your computer (spyware), hackers who break into and run programs on your computer without your knowledge, and scammers who use the Internet to take advantage of unsuspecting victims (phishing).
This chapter shows you how to protect your computer using software that detects—and deletes—malicious software code or blocks unwelcome access. It also shows you how to use your computer’s settings to control the information that flows in and out of your machine. And to help you keep your kids safe, the last section deals with parental controls.
Know Your Enemies
The steps to safeguarding your computer make more sense when you understand the nature of the threats you’re dealing with. Here’s the Internet’s Seven Most Wanted:
Viruses. A virus is a nasty little piece of code (that is, a small program) that invades your computer without your knowledge. Like a flu bug that spreads from person to person, a virus can replicate itself and jump from computer to computer by attaching itself to a host file. If you unwittingly open the infected host file—for example, a song you download illegally or a file called “Britney Bikini Pic.jpg”—the virus code leaps into action and starts doing its damage. Viruses can cause erratic computer behavior or even erase files on your hard drive.
Worms. A member of the evil virus family, a worm also spreads by replicating itself over networked computers. But a worm doesn’t need human involvement or even a host file to perform its nasty duty. Worms have caused entire office networks to crash, costing companies millions of dollars in damages and lost productivity.
Trojan horses. Like the Greek myth it was named after, a Trojan horse is a deceptive file or program. It appears enticing—a game, perhaps—so you cheerfully install it on your hard drive. Once it’s there, the software quietly gets down to business. Trojan horses can secretly transmit your passwords and account numbers to Internet criminals, or provide the means for someone to take over your computer.
Spyware. Not as destructive as a virus but just as sneaky, spyware has become a huge problem around the Internet. A spyware program gathers information about you and your computing habits and then quietly transmits the information back to its spymaster—often an advertising or marketing company.
Third-party cookies. Alongside the good cookies that let Web sites remember and automatically fill in your login information and other preferences, there are bad cookies. Called third-party or tracking cookies, they don’t even originate from the Web sites you surf to. Instead, a company that advertises on that site slips its own cookies onto your computer to trace your movements as you roam the Web.
Phishing. Those junk email messages clogging up your inbox are usually more of an annoyance than a threat. In the hands of sneaky identity thieves, though, email can be much more dangerous. Phishing refers to massemailed phony messages that trick people into handing over their passwords, credit card information, and even social security numbers. Just as the pronunciation implies, phishers sit back and wait for their victims to bite.
Hijacking. You’re the one who pays for the Internet connection and sits at the keyboard, so you’re the only one who can control your computer, right? Wrong. That connection is a conduit both into and out of your machine. If you don’t shield it properly with a firewall (Section 21.6.1), anyone with a bit of programming skill (and a lack of moral fiber) can pipe in programs and commands that take over your computer.
Note
Most of these maladies affect only Windows PCs. The Macintosh is largely unaffected by viruses, worms, spyware, and so on, partly because its smaller market share makes it a smaller target for the virus writers, and partly because it’s a more modern, much more secure operating system to begin with.
Fighting Internet Pests
Sadly, computers were a lot safer before people figured out how to link them into the giant network called the Internet. Although viruses dominate today’s technology news, they first appeared on PCs in 1986. Back then, just about the only way a virus could travel from one desktop computer to another was on an infected floppy disk. So although viruses have been around for a couple of decades, it took the Internet to make them truly dangerous.
Nowadays, malicious programs can email themselves to everyone in your Windows computer’s address book before you know it. They can secretly transmit information about your shopping and surfing habits back to unseen companies and pepper your screen with advertisements. A particularly virulent outbreak of nasty programming code can even crash Windows computers and grind the Internet to a halt.
Viruses, worms, and their ilk usually hitch rides on email messages sent from infected computers (whose owners probably have no idea they’re infected). Or perhaps yet another angry, frustrated programmer launches a mass mailing of malicious code in a desperate cry for attention.
Fortunately, plenty of antivirus programs can swat down pestware before it has a chance to infest your PC. A good antivirus program also screens your mail for you. (A decent junk mail or spam filter on your email program can isolate messages emailed to a ton of people. See Section 14.4.3 for more on how to activate the built-in spam filters you may already have in your email program.)
Many antivirus programs act like sentinels, performing real-time monitoring of your computer as you use it. These programs do things like check incoming email for infected attachments and screen CDs and other removable drives for evil code. You can also run periodic scans that sweep your entire system looking for viruses.
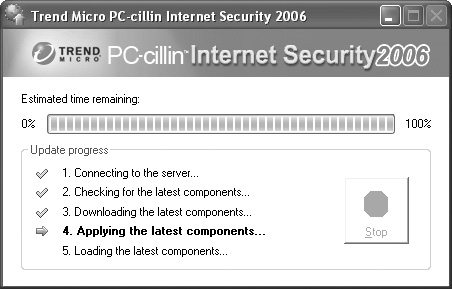
Every virus has its own telltale signature or pattern, sort of like the computer equivalent of a dirty fingerprint, that can be used to identify the malicious code. Antivirus programs keep a library of these virus patterns and use them to identify any viruses that may be lurking on, or about to enter, your computer. If the antivirus program finds a virus, it zaps it off your hard drive. To protect against the new viruses released into the wild every week, the antivirus program grabs updates from its manufacturer’s virus patterns library. Figure 21-1 shows an automatic update in progress.
These pattern updates are also called antivirus subscriptions. After a year of use, your antivirus program will likely start popping up alert boxes, reminding you to renew your subscription so you can keep getting updates. You may resent having to pony up $25 or $30 again, even though you paid $40 or $50 dollars for the software in the first place. But it costs the manufacturer money to update the pattern files as new viruses appear, and those files are what keep your PC virus-free throughout the year.
Depending on your PC manufacturer, you may be able to buy antivirus software separately or, for around $20 more, as part of an Internet security suite. These security suites, which range in price from about $50 to $70, offer protection from an assortment of Internet hazards. In addition to antivirus protection, you get firewall software (Section 21.6.2) to shield your machine from Internet intruders, spam filters to weed out junk mail from real messages (Section 14.5.1), spyware stompers to block sneaky programs from running around on your PC (Section 21.3), and other components that turn your computer into a wellguarded fortress.
An unprotected Windows PC can be invaded and infected after less than 15 minutes on the Internet. Security software is an absolute necessity for safe computing. In fact, your new computer may have included a trial version of security software. But if you have to shop for your own software bodyguard, here are some popular options:
Trend Micro PC-cillin Internet Security. This colorful, full-featured suite protects your PC from viruses, worms, and Trojan horses. It also guards against spyware, spam, wireless network squatters, and people or programs trying to infiltrate your machine. (www.trendmicro.com)
Norton Internet Security. Symantec’s Norton products have been fighting the good fight for years. The Windows suite includes Norton Antivirus, a robust firewall, spam and spyware protection, and a parental-control feature. (www.symantec.com)
McAfee Internet Security Suite. McAfee’s package includes antivirus software, a firewall, spam filtering, spyware strangling, and privacy protection. It also combats phishing (Section 21.5) and other forms of identity theft. (www.mcafee.com)
Panda Platinum Internet Security. Panda Software’s suite includes all the usual components—antivirus, firewall, spam, spyware, and other shields—as well as TruPrevent technology designed to isolate strange code even before it’s recognized as a virus. (www.pandasoftware.com)
Intego Internet Security Barrier. One of the rare security suites for the Macintosh, Intego’s arsenal provides antivirus and firewall protection, encrypts iChat instant message conversations, filters spam, and filters out material that’s inappropriate for children. It even has a backup program to save your bacon (along with your files) in case your Mac crashes hard and can’t get up. (www.intego.com)
Tip
There are, believe it or not, free antivirus programs for Windows: AVG Anti Virus Free Edition from Grisoft (www.grisoft.com) and AntiVir PersonalEdition (www.free-av.com). Free programs don’t get updated as frequently as programs you pay for, and you may not get much (or any) technical support. But if your software budget is $0, these programs afford your PC at least a basic booster shot against the raging virus plague.
In most cases, once you install your antivirus or security program, your work is done. Companies usually design antivirus software to start protecting your computer automatically, right out of the box. But you’re free to adjust the program’s settings if you feel the antivirus program is doing too much or too little. For example, if the automatic update window always seems to pop up while you’re working, you can change the schedule to another time. Or if you’re super paranoid, you can have it check for virus pattern updates more frequently.
Defeating Spyware
Spyware often arrives on your machine nestled inside the installer files for free software you download from the Internet—a game or file-sharing program, for example. Unfortunately for Windows fans, your operating system is spyware’s prime target. Some spyware hogs your computer’s processor, slowing it to a crawl and even causing other programs to crash. More belligerent types of spyware and overly aggressive adware give new meaning to the word nuisance—constantly changing your browser’s home page, adding unwanted bookmarks, or pestering you with pop-up ads. And as it transfers information about you across the Internet, spyware can even create holes in your computer’s security.
Sadly, it was probably you—yes, you—who let that spyware onto your computer in the first place. If you’re like most people, you probably never read all the fine print on that dreary screen of legalese that you have to click through every time you install new software. But if you’d read the user agreement, you may have seen that you were agreeing to allow the software’s maker to monitor and collect information about your computer or Web-surfing habits. (Some spyware is so sneaky, though, that it may not even come with a legal agreement; it will just slither onto your PC without announcing itself.)
Here’s a representative bit of creepy fine-print legalese, whereby you install a program: “…in exchange for your agreement to also install ad-serving software, which will display pop-up, pop-under, and other types of ads on your computer based on the information we collect as stated in this Privacy Statement.”
Needless to say, you don’t need a Harvard law degree to see that this software is going to flood your screen with pop-up advertisements. Unless you want a screen full of ads, click the “I don’t accept” box on the user-agreement screen or cancel the software installation (which probably happens anyway if you reject the user agreement).
Tip
The spyware rogue’s gallery includes programs that claim to be antispyware products, but are actually spyware themselves. You can find a list of these dirty-dealing double agents at Spyware Warrior (www.spywarewarrior.com). This site is an excellent resource for learning how to recognize spyware and its slightly more respectable cousin, adware. (See the box in Section 21.4.)
Trying to pry spyware off your system if you’ve gone ahead and installed it can be an exercise in frustration. If you try to uninstall it with the Windows Add/ Remove control panel (Start → Control Panel → Add or Remove Programs), you’ll find that it reappears the next time you start your PC. (Technically, that’s because it’s buried a backup copy of itself somewhere on your hard drive or added multiple entries for itself in your Windows registry file.)
Yanking out the spyware may also cause that free game or program you wanted in the first place to stop working, but you may not even care about that by then because you just want your computer back. Whatever your current relationship with spyware is, you may want to look into a rising new category of protective programs: antispyware software.
Most of the Internet security suites mentioned in Section 7.2.2.1 include protection against spyware infestation. But if antispyware is all you need, here are a few to consider for your Windows PC:
Webroot Spy Sweeper. One of the most comprehensive spyware shields available, Spy Sweeper rarely misses a trick. It ferrets out programs that hijack your browser, infest your Startup folder, and so on. The company’s Web site also offers free PC spyware scans, so you can see whether you have a problem before you plunk down the bucks; you need to download an 8 megabyte program to your PC to run the scan, which may make some people feel a little spied-upon. (www.webroot.com)
Sunbelt CounterSpy. This award-winning program makes short work of spyware. It also constantly monitors certain checkpoints around your PC to make sure no spies are loitering. (www.sunbeltsoftware.com)
Spybot Search & Destroy. Free, feisty, and famous for its spywhacking, Spybot Search & Destroy has cleaned PCs the world over for years. If you try this software and like it, consider donating to this valiant effort. You’ll find a PayPal link on the Download page. (www.safer-networking.org)
Lavasoft Ad-Aware. Ad-Aware was one of the earliest antispyware programs, and it’s still growing. You can download the free Ad-Aware Personal version, which removes spyware and similar infiltrators from your PC. Or for $27, you can bump up to Ad-Aware Plus and get scheduling and logging features, automatic updates, a continuous scanning option that blocks spyware that tries to install itself, and more. If you have an always-on broadband connection and spend a lot of time on the Web, the Plus option just might pay for itself in peace of mind. Its automatic features shoulder the burden of keeping spyware at bay. (www.lavasoft.de)
Windows Defender. Microsoft is developing its own spyware stopper; you can download a free test version at http://www.microsoft.com/athome/security/spyware/default.mspx .
Tip
It’s OK to protect yourself with more than one antispyware program. If your chosen spyguard is letting in a few nuisances, beef up your defense by adding another program.
At this writing, " Macintosh spyware” is still an oxymoron. If you’re worried that the Mac’s freedom from spyware may one day change, though, antispyware software companies are only too happy to take your money.
For example, SecureMac (www.securemac.com) has the latest news on every known Mac security issue and how to deal with it. The news and information are free, but SecureMac also sells its own antispyware program—MacScan. For $25, it promises to remove Trojan horses, spyware, and other Mac attackers.
Controlling Cookies
The cookies that Web sites silently and invisibly deposit on your hard drive are usually as sweet and harmless as they sound. These tiny text files are preference-setting files for individual Web sites. When Amazon.com greets you with “Welcome, Casey!” (or whatever your name is), or when NYTimes.com gives you access to the special, fee-only articles you’ve paid for, you know they’ve stored a cookie on your hard drive so they can recognize you when you return.
But when an advertiser on a Web site gives your computer a cookie, it does you no good at all. Called third-party or tracking cookies, these text files benefit only the advertiser. As long as you carry that cookie, the advertiser can keep track of your surfing habits. When you visit one of its affiliated Web sites, the company can use that information to show you ads likely to tempt you into clicking. If you think tracking cookies are an invasion of your privacy, you’re not alone.
Fortunately, Web browsers have no trouble spotting—and refusing—third-party cookies. You simply set your browser to block cookies that come from sites other than the one you’re visiting. To change your cookie settings, proceed like this:
Internet Explorer for Windows. Choose Tools → Internet Options → Privacy, tab and then click the Advanced button. In the Advanced Privacy Settings window (Figure 21-2), turn on “Override automatic cookie handling” and then, under “Third-party Cookies”, select Block.
Figure 21-2. Internet Explorer’s cookie controls are buried in the Advanced Privacy Settings dialog box. Go to the Tools → Internet Options → Privacy tab and click the Advanced button. Here, you can choose to have the browser block cookies rom third-party sites that want to snoop on your surfing whereabouts.Safari. Choose Safari → Preferences, and go to the Security panel. Next to Accept Cookies, select “Only from sites you navigate to.” This option even explains that it’s going to block advertisers’ cookies.
Firefox. Choose Tools → Options → Privacy → Cookies. Put checkmarks in the boxes next to “Allow sites to set cookies” and “For the originating site only.”
Phishing Lures
Phishing is the 21st-century version of a tired old con. You get an email message from eBay (or PayPal, or your credit card company, ISP, or bank) urging you to update or correct your account information. There’s even a link considerately offering to take you to the form you need to fill out. Should you do it? Well, would you let a stranger into your house just because he’s carrying a clipboard and says the gas company needs to check your furnace?
In a word, no. Don’t even think about it. Don’t click any links in the email body. Don’t reply to the message or attempt to contact the sender. Even if the email address or URL looks like it’s from a legitimate company—PayPal, Visa Card Services, or whatever—it never is. These links redirect you to a different Web site, a phony one, set up by the perpetrators to rob you of your passwords, credit card numbers, and even your identity. The perpetrator is just fishing for your personal information (get it?). Unfortunately, these scams go on year after year because people keep falling for them.
As phishing has gotten more sophisticated, software to combat it has also stepped up. Some Internet security suites (like Trend Micro) now include phishing protection. Newer email programs like Mozilla Thunderbird even alert you to suspicious messages (Figure 21-3). The latest browsers, including Internet Explorer 7, also let you know, with all the subtlety of a sledgehammer, when you’ve visited a Web site that’s not what it pretends to be.
There’s a simple way to avoid phishing altogether: Never, ever give a Web site personal information like Social Security numbers, account numbers, or passwords unless you initiated the communication. Ignore any email that asks you to supply personal or financial information. If a legitimate company needs to contact you, it will send you a letter or wait until the next time you log into your account.
Tip
For more information about how to protect yourself from phishing threats, or if you want to file a complaint, visit the Federal Trade Commission’s helpful site at http://onguardonline.gov.
Sealing Your Computer’s Firewall
Believe it or not, there are even more bad things that can happen when you’re online. Total strangers, next door or in Eastern Europe, can connect to your Windows PC, invisibly take control of it, and turn it into, for example, a relay station that helps them pump out millions of pieces of spam (junk email) every day. You might notice that your PC has slowed down, and you might not. But you’ve just become part of the problem.
How is this possible? To understand the technical underpinnings, you need to know about ports.
Ports are like TV channels. Your PC has a bunch of them, each one dedicated to letting certain kinds of Internet information pass through: surfing the Web, sending email, downloading files, playing videos, and so on. Trouble is, Internet intruders roaming around online know how to use these ports to their advantage. They use software that can slip into your PC through one of these ports.
Ready to yank your modem cable out of the wall yet? Relax. You can stop the baddies just by using a firewall, a security barrier that prevents people or programs from sneaking into your machine via your Internet connection. A firewall can be a software program or a physical piece of hardware.
Good firewalls can monitor both incoming and outgoing traffic. So, in addition to keeping out intruders, your firewall can detect—and stop—spyware or a virus trying to transmit information from your computer.
Hardware Firewalls
A hardware firewall is a physical box sitting squarely between your computer and the Internet outside so potential intruders can’t see your machine. You may have one and not even know it. For example, if you’ve installed a router (Section 1.1.1.2) so that more than one computer can share your cable modem, you may be delighted to learn that it’s probably a hardware firewall. It constantly screens the traffic to and from your networked computers.
Even if you don’t have a home network, a router with a built-in firewall is a good investment, especially if you have a broadband connection. When shopping, look for a router with a firewall that includes both SPI (Stateful Packet Inspection) and NAT (Network Address Translation). Security products like the AlphaShield ( www.alphashield.com)—which plugs in between your computer and your broadband modem—also monitor all Internet traffic and block any suspicious activity.
Software Firewalls
A software firewall is good protection, too. No wonder both Windows and Mac OS X come with such a feature built right in. (All the Internet security suites described in Section 7.2.2.1 include firewall programs as well.)
Tip
If you have a hardware firewall (like a router), you don’t need to turn on a software firewall too.
The Windows XP Firewall
When Windows XP first appeared back in 2001, it came with a nifty new feature—built-in firewall software. Unfortunately, Microsoft left the firewall turned off, and few people could find it to turn it on. So, in the interest of greater security, Service Pack 2 (which Microsoft released a few years later) automatically flips the Windows Firewall on. In fact, once you install this update, Windows XP pesters you (by popping up yellow warning balloons from the taskbar) if you turn the firewall off.
If you do have Service Pack 2 installed—either because you installed it or because you bought your computer after October 2004—you can find the on/off switch for the firewall like this. Choose Start → Control Panel → Security Center → Windows Firewall. (If you use the Control Panel’s Classic view, choose Start → Control Panel → Windows Firewall.) On the General tab of the Windows Firewall control panel, click the button next to “On (recommended)” and then click OK. The firewall’s off button is here, too, if you need to shut it down for a minute to troubleshoot your Internet connection or something.
Note
If you like the sound of a sturdy, free firewall that’s more powerful (because it blocks traffic coming and going through your computer) check out ZoneAlarm (www.zonelabs.com). With a friendlier interface, ZoneAlarm is often easier to use than the built-in Windows Firewall, which is set to block unauthorized traffic coming to your PC from the outside world, but it may not be much help against programs on your PC trying to sneak out to the Internet without your permission. ZoneAlarm works with systems as far back as Windows 98SE, so it gives you a firewall option if your PC is too old to run Windows XP. (And if you do have Windows XP, you can still use ZoneAlarm. The Windows Firewall is savvy enough to get out of the way when you install an alternative program.)
To try the software, scroll down to the bottom of ZoneLabs’ home page and click “Free ZoneAlarm and Trials.” You can get the free version here or buy the $50 full-featured edition with more controls and technical support. Once you download and install the program, ZoneAlarm makes your machine invisible to other computers nosing around on the Net.
Setting up the Mac OS X firewall
Apple’s system security for its Mac OS X Tiger system is even stricter than Microsoft’s: Out of the box, all communication ports and services on the Mac are closed to the outside. (That’s one reason the Mac hasn’t attracted hackers like Windows has.) The Mac also comes with its own built-in firewall that blocks all incoming Internet traffic except for the programs you allow through.
Its factory setting is Off, though, so you need to give it a little click-start.
To turn on the Mac OS X firewall, follow these steps:
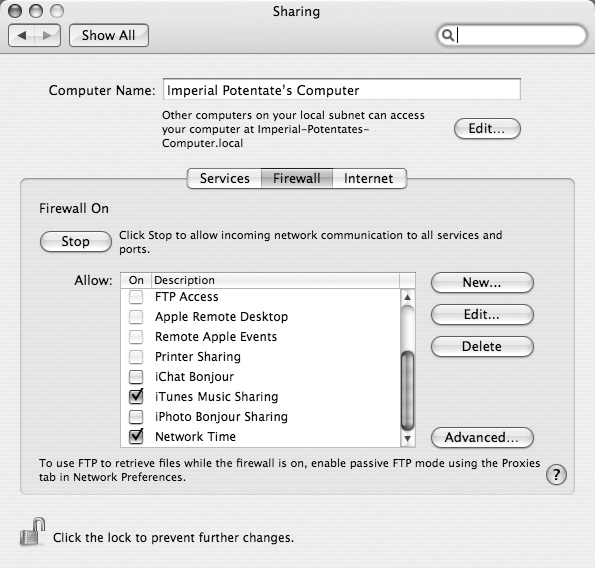
Go to
 → System Preferences → Sharing. Click the Firewall tab, and then click the Start button.
→ System Preferences → Sharing. Click the Firewall tab, and then click the Start button.The Mac fires up its firewall software. Again, the firewall starts out blocking every sort of Internet communication, so you must turn on the ones you want to use.
In the Allow list, select the programs or functions you want to let through the firewall.
As shown in Figure 21-5, turn on the checkboxes next to, say, iTunes Music Sharing and other network services you plan to use.
Tip
Want to make sure your computer’s firewall is doing its job? Several online sites offer to knock on your computer’s ports and see if there are any openings for intruders to slither through. Check out ShieldsUP (www.grc.com), Hackercheck (www.hackercheck.com ), or Planet Security’s firewall check (www.planet-security.net ).
Protecting Your Kids
The Internet appeals to children’s uninhibited, adventurous spirits. Kids find it rewarding to look up information themselves, explore online museum exhibits, and try their hand at interactive games. But the Internet isn’t a babysitter, and it has millions of people prowling around on it. Some sites and services (and, quite frankly, some of the aforementioned people) just aren’t suitable for children.
Tip
If you hear your kids talking about their online adventures and you have no idea what they’re talking about—IM? Blogging? Podcasts?—check out Chapters 15 and 19. This book demystifies it all.
Ground Rules for Kids
If your children use the Internet, it’s important to set up some ground rules to keep everyone safe and happy. For starters, keep the computer visible in a public location of your home, like the den or family room. Consider limiting the amount of time youngsters spend online, too.
But because you can’t be looking over your kids’ shoulders every minute, you can use protective software to filter out inappropriate material, as discussed in the box in Section 21.7.2.
There are also some basic words of wisdom to give to any child or teenager surfing the Internet:
Never give out your full name. Use a nickname or first name online.
Never give out a telephone number or home address to someone you meet online.
Never give out your passwords.
Never agree to meet someone you met online in person.
Never email or post photographs of yourself online.
Never assume that everyone online tells the truth about who they are.
Never hesitate to tell a parent if someone is harassing or bothering you online.
Advice for Parents
With the boom in chat rooms (Section 15.2.11), personal blogs (Section 19.1), message boards (Section 16.1), and Web-based social networking sites like MySpace (Section 17.1.4) that give plenty of opportunities for kids to express themselves online, getting youngsters to stick to the house rules can be difficult—but it’s vitally important. Parents looking for more information on letting their kids use the Internet safely may want to do some further reading around the Web:
WiredSafety. Perhaps the most all-inclusive Internet safety and help group on the Web, this site has sections of special interest for parents, lawenforcement officers, educators, women, and kids of all ages. WiredSafety keeps readers up to date on the latest issues affecting the online world. (www.wiredsafety.com)
SafeKids. Jam-packed with safety tips and guidelines for the parents of children and teens using the Internet, this site also has a discussion forum and news updates on the latest viruses, spam, and scams going around. (www.safekids.com )
StaySafe. This is an educational site funded by Microsoft that focuses on both the positive aspects of Internet life and secure navigation through the negative. (www.staysafe.org )
GetNetWise. This frank, no-nonsense site for parents offers tips, tools, and plenty of practical advice for protecting the young ones online. (http://kids.getnetwise.org )
Tip
Want some great sites to keep your baby Web surfers educated and entertained? KidSites (www.kidsites.com ) and the American Library Association’s Great Web Sites for Kids page (www.ala.org/greatsites) are great places to start. Another option is FirstGov for Kids (www.kids.gov), which provides links to NASA’s page for young space fans, national museum sites, and many states’ Web pages among its varied offerings.