Introduction
Congratulations on choosing to become a Systems Security Certified Practitioner (SSCP)! In making this choice, you’re signing up to join the “white hats,” the professionals who strive to keep our information-based modern world safe, secure, and reliable. SSCPs and other information security professionals help businesses and organizations keep private data private and help to ensure that published and public-facing information stays unchanged and unhacked. Whether you are new to the fields of information security, information assurance, or cybersecurity, or you’ve been working with these concepts, tools, and ideas for some time now, this book is here to help you grow your knowledge, skills, and abilities as a systems security professional. Let’s see how! You’re here because you need a ready reference source of ideas, information, knowledge, and experience about information systems security. Users of earlier editions of the CBK describe it as the place to go when you need to look up something about bringing your systems or networks back up and online—when you can’t exactly Google or Bing it. As a first responder in an information security incident, you may need to rely on what you know and what you’ve got at hand as you characterize, isolate, and contain an intruder and their malware or other causal agents. This book cannot answer all of the questions you’ll have in real time, but it may just remind you of important concepts as well as critical details when you need them. As with any reference work, it can help you think your way through to a solution. By taking key definitions and concepts and operationalizing them, showing how they work in practice, this book can enrich the checklists, troubleshooting guides, and task-focused procedures that you may already be using in your work. Good question! This Common Book of Knowledge (CBK) provides you the data, information, knowledge—and in some cases, some bits of wisdom—that have been hard-won by the experience of many SSCPs and other information security professionals. This CBK is structured around the SSCP domains of knowledge; as such, it’s not a cover-to-cover learning journey but more of an atlas for such a journey. The SSCP Official Study Guide exists because (ISC)2 wanted a book that would teach as well as guide, explain as well as capture the common knowledge about keeping information systems secure, protecting information assets, and information assurance that all SSCPs should have at their mental fingertips. As creators of the SSCP program, (ISC)2 defines that common body of knowledge, in continuous consultation with system security experts and practitioners from business, industry, government, and academia from around the world. This book is its natural companion. This book directly reflects the SSCP Common Body of Knowledge, which is the comprehensive framework that (ISC)2 has developed to express what security professionals should have working knowledge of. These domains include theoretical knowledge, industry best practices, and applied skills and techniques. Chapter by chapter, this book takes you through these domains, with major headings within each chapter being your key to finding what you need when you need it. Topics that are covered in more than one domain will be found within sections or subsections in each chapter as appropriate. (ISC)² is committed to helping members learn, grow, and thrive. The Common Body of Knowledge (CBK) is the comprehensive framework that helps (ISC)² fulfill this commitment. The CBK includes all the relevant subjects a security professional should be familiar with, including skills, techniques, and best practices. (ISC)2 uses the various domains of the CBK to test a certificate candidate’s levels of expertise in the most critical aspects of information security. You can see this framework in the SSCP Exam Outline at www.isc2.org/-/media/ISC2/Certifications/Exam-Outlines/ SSCP-Exam-Outline-Nov-1-2018.ashx. Chapter by chapter, domain by domain, these domains are as follows: Chapter 1: Access Controls Policies, standards, and procedures that define who users are, what they can do, which resources and information they can access, and what operations they can perform on a system, such as:
Chapter 2: Security Operations and Administration Identification of information assets and documentation of policies, standards, procedures, and guidelines that ensure confidentiality, integrity, and availability, such as:
Chapter 3: Risk Identification, Monitoring, and Analysis Risk identification is the review, analysis, and implementation of processes essential to the identification, measurement, and control of loss associated with unplanned adverse events. Monitoring and analysis consists of determining system implementation and access in accordance with defined IT criteria. Collecting information for identification of, and response to, security breaches or events, such as the following:
Chapter 4: Incident Response and Recovery The show must go on is a well-known saying that means, even if there are problems or difficulties, an event or activity must continue. Incident response and recovery ensures the work of the organization will continue. In this domain the SSCP gains an understanding of how to handle incidents using consistent, applied approaches like business continuity planning (BCP) and disaster recovery planning (DRP). These approaches are utilized to mitigate damages, recover business operations, and avoid critical business interruption.
Chapter 5: Cryptography The protection of information using techniques that ensure its integrity, confidentiality, authenticity, and nonrepudiation, and the recovery of encrypted information in its original form.
Chapter 6: Network and Communications Security The network structure, transmission methods and techniques, transport formats, and security measures used to operate both private and public communication networks.
Chapter 7: Systems and Application Security Countermeasures and prevention techniques for dealing with viruses, worms, logic bombs, Trojan horses, and other related forms of intentionally created damaging code.
Your employers or clients have entrusted the safety and security of their information systems to you, as one of their on-site information security professionals. Those systems are under constant attack—not just the threat of attack. Each day, the odds are great that somebody is knocking at your electronic front doors, trying the e-window latches on your organization’s web pages, and learning about your information systems and how you use them. That’s reconnaissance in action, the first step in the cybersecurity kill chain. As an SSCP you’re no doubt aware of the cybersecurity kill chain, as a summary of how advanced persistent threat (APT) actors plan and conduct their attacks against many private and public organizations, their IT infrastructures, and their information assets and systems. Originally developed during the 1990s by applying military planning doctrines of effects-based targeting, this kill chain is similar to the value chain concept used by businesses and public-sector organizations around the world. Both value chains and kill chains start with the objective—the desired end state or result—and work backward, all the way back to choosing the right targets to attack in the first place.1 Lockheed-Martin first published its cybersecurity kill chain in 2011; the MITRE Corporation, a federally funded research and development corporation (FFRDC), expanded on this in 2018 with its threat-based Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) framework. ATT&CK takes the kill chain concept down into the tactics, techniques, and procedures used by squad-level and individual soldiers in the field. (Note that in military parlance, planning flows from strategic, through operational, to tactical; but common business-speak usage flips the names of the last two steps, looking at business operations as being the point-of-contact steps with customers, and the tactical layer of planning translating strategic objectives into manageable, measurable, value-producing packages of work.) ATT&CK as a framework is shown in Figure 1, highlighting the two major phases that defenders need to be aware of and engaged with: prestrike planning and the enterprise-level targeted strikes at your systems, your data, and your mission. FIGURE 1 MITRE’s ATT&CK cybersecurity kill chain model © 2018 The MITRE Corporation. This work is reproduced and distributed with the permission of The MITRE Corporation. MITRE, Lockheed Martin, and others may give slightly different names to the different phases of their kill chain models. For example, MITRE’s combines exploitation with installation, while emphasizing the persistent presence of the adversary inside your systems as they maintain their capabilities to quietly wreak havoc and achieve their objectives. The names of the phases aren’t important; their underlying flow of ideas is what matters. To date, there does not seem to be any evidence that any given attacker has used exactly one planning model or another. There is abundant evidence, however, that defenders who do not understand these models pay for their ignorance—or, more precisely, their employers and clients do. Combining these two models gives us eight phases of the life of an APT’s kill chain and suggests which domains of knowledge (and therefore which chapters) may be your first ports of call as you plan to detect, prevent, degrade, or defeat the individual tasks that might make up each step in such a kill chain’s operation. These are shown in Table 1. TABLE 1 Kill Chain Phases Mapped to Chapters You might be wondering why all chapters seem to apply to the Reconnaissance phase. The key to this is to recognize that the attacker will seek to find all possible sources of information about your organization, its business associates and relationships, its communications patterns, and its IT systems. APTs seek understanding of their targets’ business and social networks, the “watering holes” where their people gather to collaborate with others in their trade or market. They’ll try to suck up every unencrypted, unprotected, unsecured bit of anything that might be of use to them, as they determine your value to them as a set of exploitable opportunities. As the defender, this is your first clear opportunity to practice what insurance companies call “all-risks coverage” by exerting all possible efforts to identify, prioritize, and control all hazards that your systems and your organization might be exposed to. The attack execution phase, by contrast, must rely heavily on your organization’s ability to detect and respond in real time, or as close to real time as you can manage. Industry-wide, we’re not doing too well on this front. It takes businesses and organizations an average of 197 days to detect an intrusion into their IT systems, according to research for IBM Security done by the Ponemon Institute in 2018.2 On average, worldwide, any given business may suffer as much as $3.86 million USD in losses due to a data breach attack. A ransom attack, however, can demand $50 million USD or more in payouts. Those firms that have chosen not to pay off their attackers have reportedly suffered even greater losses. The same research conducted by Ponemon, by the way, demonstrates that having an effective security incident response plan in place, with first responders properly trained and equipped, can save at least $340,000 per incident. As an SSCP, you’ve got your work cut out for you. Let this book be one of the many sources of knowledge, experience, and information you can count on, before, during, and after intruders start to target your organization’s information, its systems, and its very existence. The world of information systems security is constantly changing. You need to continually grow your skills and keep up with the latest changes in the ways that businesses and organizations use the Internet and information technologies, as well as how the threat actors continually evolve to find new and different ways to exploit our systems against us. As a digital citizen of the 21st century, staying current—staying on the cutting edge of change, if not sometimes on the bleeding edge of it—is part of how you meet your due care and due diligence responsibilities to your clients, to your employers, and to the larger society around you. As a recognized member of that profession, the world expects you to stay sharp, stay focused, and stay informed. That journey begins with this book, which provides you with a tangible foundation for your learning, exploration, and discovery. As a resource, this book provides the following strengths:
Possibly one of the best ways to see your SSCP in the context of your professional growth and development can be found on the CyberSeek website. CyberSeek is a partnership sponsored by NIST that brings together the current state of the job market in cybersecurity, information security, or information risk management. It combines data on job market demand for such skills, current average salaries, and even insight on the numbers of professionals holding various certifications. The real gem, however, for the new cybersecurity or information security pro is its Career Mapping tool. See this at www.cyberseek.org and use it to help navigate the options to consider and the opportunities that an earned SSCP after your name might open up. As an international, nonprofit membership association with more than 140,000 members, (ISC)2 has worked since its inception in 1989 to serve the needs for standardization and certification in the cybersecurity workplaces around the world. Since then, (ISC)2’s founders and members have been shaping the information security profession and have developed the following information security certifications:
Each of these certifications has its own requirements for documented full-time experience in its requisite topic areas. Newcomers to information security who have not yet had supervised work experience in the topic areas can take and pass the SSCP exam and then become recognized as Associates of (ISC)2. Associates then have two years to attain the required experience to become full members of (ISC)2. SSCP credentials are maintained in good standing by participating in various activities and gaining continuing professional education credits (CPEs). CPEs are obtained through numerous methods such as reading books, attending seminars, writing papers or articles, teaching classes, attending security conventions, and participating in many other qualifying activities. Visit the (ISC)2 website for additional information concerning the definition of CPEs. Individuals are required to post a minimum of 20 CPE credits each year on the (ISC)2 member website. Generally, the CPE credit post will be recognized immediately by the system, but it’s also subject to random audit. Please note that any CPEs accomplished prior to being awarded the (ISC)2 certification may not be claimed. If an individual accomplishes more than 20 CPEs for one year, the remainder may be carried forward to the following year. The (ISC)2 website describes CPEs as items gained external to your current employment duties. As an SSCP, you’ve become one of more than 140,000 members worldwide. They, like you, are there to share in the knowledge, experience, and opportunity to help accomplish the goals and objectives of being an information security professional. Nearly 12,500 of your fellow members participate in local area chapters, and (ISC)2 has over 140 local chapters around the world. You can find one in your area by visiting www.isc2.org/Chapters. Being an active part of a local chapter helps you network with your peers as you share knowledge, exchange information about resources, and work on projects together. You can engage in leadership roles and participate in co-sponsored local events with other industry associations. You might write for or speak at (ISC)2 events and help support other (ISC)2 initiatives. You can also be a better part of your local community by participating in local chapter community service outreach projects. Chapter membership earns you CPE credits and can make you eligible for special discounts on (ISC)2 products and programs. This book is for you. This is your journey map, your road atlas, and your handbook. Make it work for you. Choose your own course through it, based on what you need on the job today and every day. Go for it.About This Book
![]() Why This CBK as Well as a Study Guide?
Why This CBK as Well as a Study Guide?The SSCP Seven Domains
Using This Book to Defeat the Cybersecurity Kill Chain
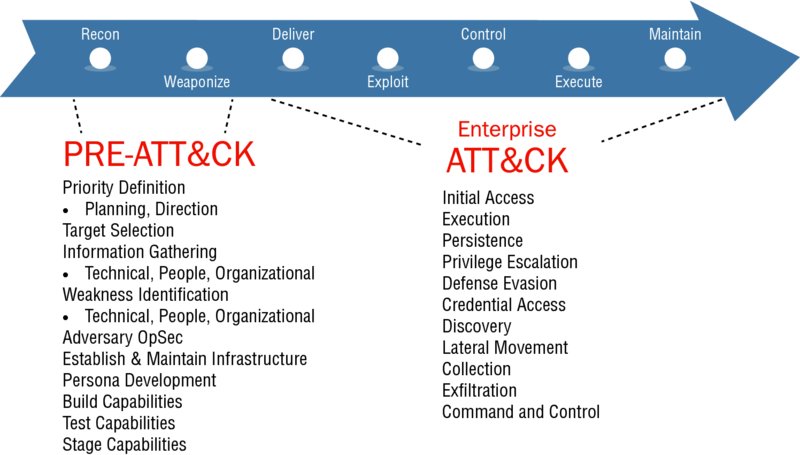
Kill Chain Phase
Attack Operations
Defensive Options
Reconnaissance
All-source intelligence gathering to inform the attack: OSINT, scanning, early intrusion, social engineering
All chapters: enhance overall risk/security posture, awareness, vigilance
Weaponization
Select and prepare access techniques and pathways
Chapters 1, 7
Delivery
Email, USBs, URLs, access control gaps, etc.
Chapters 1, 2, 5, 6, 7
Exploitation
Malware, rootkit exploits, live off the land
Chapters 1, 4, 6, 7
Installation
Backdoors, false or subverted user IDs
Chapters 1, 7
Command & Control
Privilege escalation, credential access; lateral movement; find, fix, select in-system targets
Chapters 1, 2, 4, 6
Execute the Attack
Exfiltrate; corrupt; encrypt for ransom; springboard to other targets
Chapters 4, 5
Maintain Hostile Presence
Continue to exploit target’s systems and data; continue hiding one’s tracks
Chapters 1, 4, 6, 7
Where Do You Go from Here?
The SSCP CBK and Your Professional Growth Path
Maintaining the SSCP Certification
Join a Local Chapter
Let’s Get Started!
Notes
