When people generally speak of cyber-attacks or cyber warfighting, the onus typically seems to be on the end effect of the attack. This is understandable as the attack portion of cyber-attacks is usually a cyber-physical effect that even non-technical people can understand the impact of. When a cyber-attack can take control of a vehicle’s braking and steering, for instance, the cyber-physical effect of the attack is what makes the news. To the non-technical, losing control of their vehicle is highly relatable. Whereas the hackers among us are more interested in how the vehicle controlling code was delivered to the vehicle and how it was able to take over those computing functions. The term cyber-attack is commonly conveyed and interpreted as the entire process of bringing the attack end effect to bear on a system. In actuality the process involves cyber intelligence gathering or reconnaissance, cyber exploitation, and then ultimately a cyber-attack effect.
In this same vein of common interpretation, the access needed to deploy the attack effect is almost entirely glossed over. This leads to wider spread interpretation issues primarily in military and policy circles. The focus in a military discussion tends to be exclusive to what end effect can be delivered to the enemy, and there is not enough respect for the sheer effort and technical capabilities needed to get that end effect delivered, if it is even possible to do so. Cyber-attack effects are a dime a dozen, but the ability to accurately find a target and then hopefully gain access to it can be tantamount to impossible. Imagine there was a mission to find some individuals home and then cause a bunch of damage to it to intimidate that person for beating up a friend of yours. Now, consider that the only information you have about the person was their nickname and that they would frequent a restaurant you know about while they were in town on work trips. Also, they beat up your friend yesterday, and if you can’t damage their home in the next week, it is unlikely they will know that their house was trashed for beating up your friend. This doesn’t seem like a mission that is very likely to succeed, does it?
If you can even determine where the person is travelling from on their work trips and who they were and then somehow find their address and get to it in the next week, that alone seems far-fetched. Suppose you somehow did though, you find their house and you see they have camera systems and a dog and a sporadic work schedule. You want to trash the person’s house for beating up your friend, but you also don’t want to get caught, arrested, or bit, so now you need to figure out a way in; doing this as well in whatever time you have remaining in the week-long period is almost ridiculously unlikely. After all this effort to identify, locate, and sneak inside the person’s home, it becomes rather trivial to find a way to cause destruction to intimidate the person. You could do any number of things, light a fire, smash Windows, dump garbage, and so on. The cyber warfighting activity process is just like this, appropriate reconnaissance can take time, and accessing the target can be nearly impossible and is constrained by a multitude of factors, time being only one of them. Once you have access to the target, much like access the home in our analogy, it is comparatively trivial to enact a noticeable cyber-attack effect.
A big reason for this is that, once access is gained, the attacker often is within the same or even a more privileged context than the normal users of the target. Security software and policies still need to let a user perform their needed actions on a given system and such have to make some assumptions that those on the device with appropriate context are supposed to be there. If security was such that it questioned every move of every user on them, they wouldn’t be functional. This concept is similar to that of the process of clearing individuals with security clearances for work for the government and national security apparatus. At some point, once you have questioned and investigated the people and they have accessed a building with their badges and correct authority, there is an inherent trust that they are going to act as expected. Pieces of code on a cyber system are treated the same way. If after every security constraint and permission policy and filtering capability the code is still able to get onto the system and execute in a typical way, the system has to trust that it was not done maliciously.
Refined Definition
The activity must originate in the cyber domain of warfighting.
The activity must be covered by US Code Title 10.
The activity must be conducted under the direction of a US military commander and not be an intelligence-gathering activity and be wholly within the cyber domain in preparation of the battlefield for a planned military operation or as part of an ongoing military operation by leveraging activity originating from the cyber domain to cause a noticeable effect in another warfighting domain (air, land, sea, space).
I will also take this opportunity to make a statement about how the United States could improve perception of its power in the cyber domain of warfare. We need our enemies to know, at least in part, what we are capable of. The United States is a feared power in the other warfighting domains because people can cite examples of that power. A nuclear attack submarine or destroyer, Tomahawk missiles, stealth bombers, and extremely talented special forces operators all convey US military power and themselves act as a deterrence, thus furthering the expectation of protection. Enemies of the United States know what it means if STRATCOM (Nukes) and SOCOM (Special Forces Operators) are brought against them, as well as the likely end effect. The role CYBERCOM plays in warfare is not known or established, so how can it help act as a deterrence?
Perhaps a small part of the reason foreign states are not deterred in conducting cyber acts against the United States is they do not know our ability to respond in the cyber warfighting domain. Maybe, if after a military operation, the role cyber activities played in it was acknowledged, it would help others perceive us as a leading player in cyber warfare. The United States readily admits when it launches Tomahawk missiles at targets in another country, why not start admitting when cyber is involved in Title 10 activity? After all, legally the United States acknowledges its role in Title 10 activity, and cyber warfare must fall within that legal authority.
I make no suggestion that this is easily done. I also must make clear that there are trade-offs in declaring that cyber warfare was involved in a wider military operation. The technical extant of this trade-off will be covered in the next chapter. I do believe though that to deter cyber warfighting against us, we in part must demonstrate our ability to wage war in the cyber domain. However, this must be done in a way that does not hamper or hinder our ability to continue to conduct warfighting or intelligence gathering activity in the cyber domain. Doing both may prove impossible, but it is certainly an interesting discussion to have.
Exploitation
We will first cover the activity of cyber exploitation as it is often required to perform both intelligence gathering and attack effect activity. Exploitation is also often referred to as remote code execution which is simply a technical way of saying the attacker is influencing the way a remote system behaves. I will caveat this by saying that there is also local exploitation to systems where access is already attained but that the context of that access does not have the privilege needed to execute the desired end effect of reconnaissance or attack. In either case, this is accomplished through leveraging a vulnerability. Just because a system has a vulnerability does not mean the attacker will be able to use that vulnerability to influence the way the remote system behaves. Exploitation or an exploit is the weaponization of a given vulnerability to gain that remote access necessary to alter the behavior of the remote system. Exploits are needed to deliver any cyber-attack effect, and when uniquely weaponized, they can take years and millions of dollars and scores of people to create, and when used even once, they are potentially identified by the rest of the world and then will be fixed and no longer usable, a fact which must be heavily weighed when deciding to utilize them.
Types of Exploitation
There are many different ways of exploiting systems in the cyber domain, and to understand the various challenges to exploitation in general, we will break them down categorically and cover examples of each type of exploit. Exploitation types are perhaps more accurately vulnerability types as the different factors that present a vulnerability to a system dictate how that vulnerability can be leveraged and the system ultimately exploited and accessed for deployment of attack effects.
Code Vulnerability
A code vulnerability is exploited by taking advantage of a flaw in underlying instructions that allows for remote manipulation of the system in a way that was unintended by the designers of the code. Exploitation of a code vulnerability often takes lots of work even when the vulnerability has already been discovered. Weaponization of a vulnerability is taking that unintended flaw and leveraging it in a purposeful and controlled way. Utilizing code vulnerabilities can many times lead to unwanted results. Sometimes leveraging a vulnerability may lead to remote access to the system, and sometimes it may result in a crash and power off of the remote system. Such a vulnerability is considered weaponized when it has a reasonable chance of attaining the intended result for triggering the vulnerability and an acceptable chance of unintended consequences.
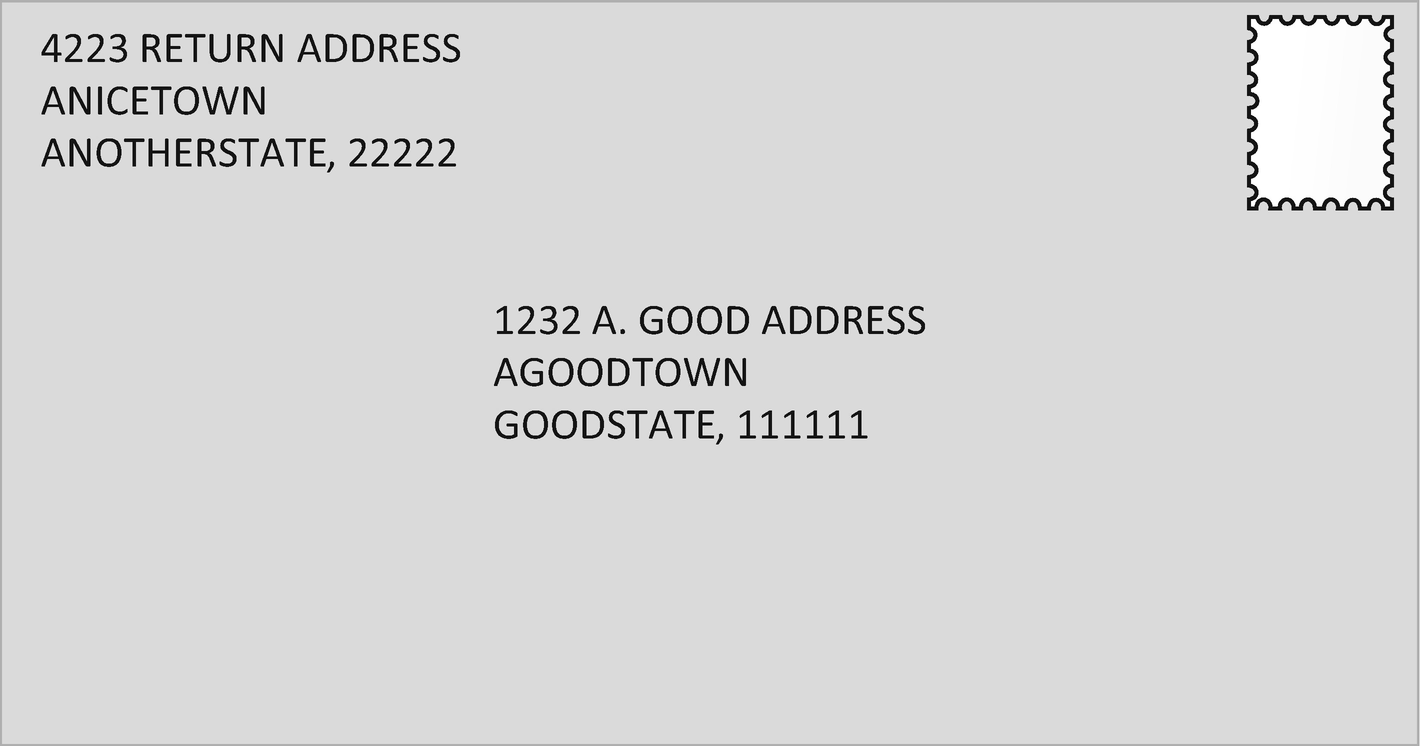
Acceptable Letter
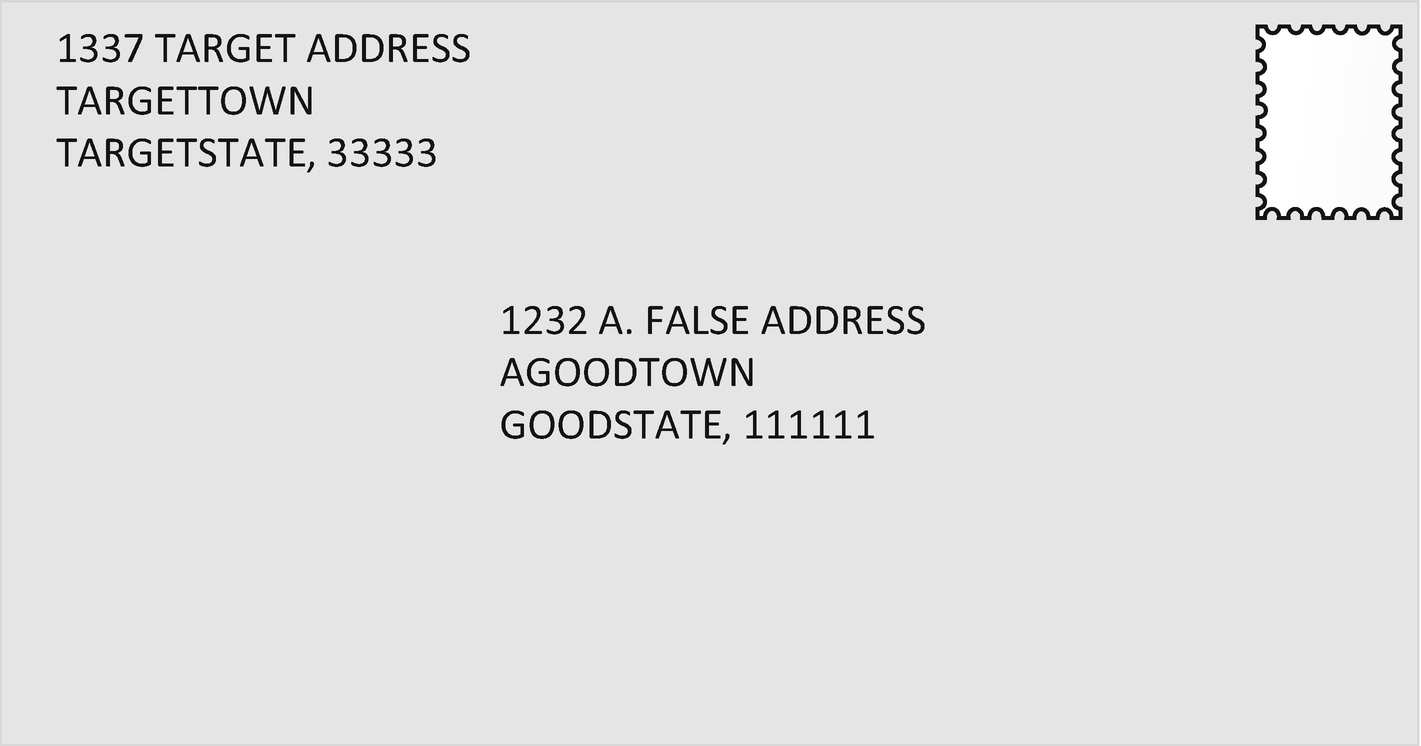
Rejected Letter
The sorter at the mail office sees that the address is longer than 20 characters and puts it in a bin to be returned to sender. Since the mail carrier who picked it up didn’t verify the return address was where he picked it up from, it gets sent to the actual target (1337 TARGET ADDRESS) and no one will be able to tell where it actually came from. The lack of a validated return address and the issue with destination addresses allowed for this exploitation.
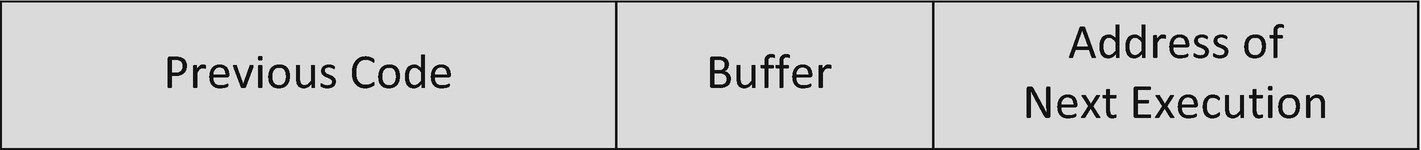
Logical Memory Layout
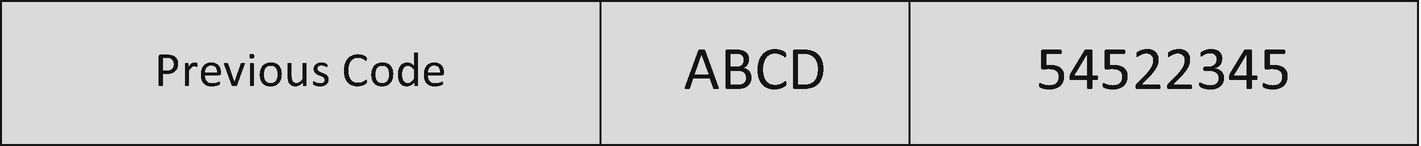
Example Memory
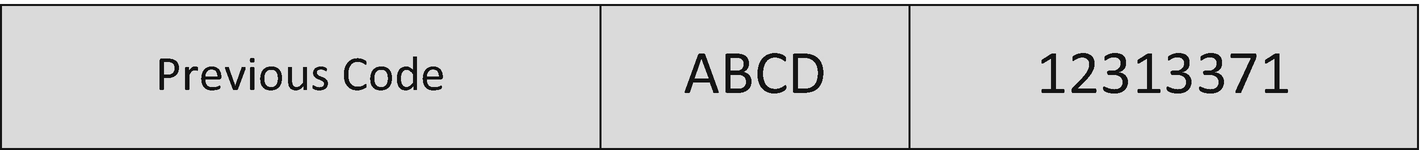
Overflown Buffer
In this example the fact that there is no check to make sure the text entering the buffer is four or less characters is the vulnerability, allowing us to dictate what will execute next by overwriting the existing memory address (54522345) for the next thing the computer will process with our own specific location instead (12313371). If the 5th through 12th characters we copied in were the location of say something malicious we wanted to execute, then we have exploited that vulnerability to get the computer to execute code on our behalf.
Misconfiguration
Exploitation of a misconfigured system is pretty straightforward. The system has a setting or otherwise configurable option which has left it vulnerable. Weaponization of this type of vulnerability involves turning the misconfiguration into an ability to manipulate the target. Unlike code vulnerabilities, misconfigurations sometimes stand by themselves as an essentially weaponizable capability. Imagine a misconfiguration that allowed a remote entity to power off a system that controlled security cameras. In this case there is no further development to turn the misconfiguration into an attack effect like there likely would be if there was a code vulnerability in the same camera controlling system.
As an example of misconfiguration vulnerability exploitation, I’ll use a facial recognition secured gate. After experiencing tons of false negatives where legitimate users were not being let through the gate, the security staff tuned down the sensitivity of the image detection that allowed individuals through after checking their face. This led to no more legitimate users being stopped at the gate, but it also meant that even those not in the facial recognition database were getting let through because the gate was no longer sensitive enough to tell the difference between most people. This is a misconfiguration that is allowing for a lot of false positives which is a dangerous result. A malicious individual could leverage this vulnerability to gain access to a building and sabotage something and the vulnerability itself required no weaponization for reliable exploitation, the individual simply walks up to the gate and is let through due to a false positive.
A relatable cyber system configuration vulnerability exploitation can be seen using the example of a misconfigured firewall. Firewalls are systems which filter incoming network traffic by acting on that traffic as it matches configured rules. Typically, the rules are in list form, and incoming traffic is compared against those rules either starting at the top and going down the list or vice versa. The safest way to configure a firewall is with a “deny all” as the last rule for comparison. This way, if traffic doesn’t match an explicit “allow” rule on the list, it will ultimately be denied. Firewall rules can be unsafely configured for the same reasons as in our facial recognition gate in the previous example. If traffic getting filtered by the firewall is having too many false negatives and the system is not able to function, there is a possibility that the administrators of that firewall will begin to make the rules less strict so that everyday operations in the system are allowed to happen as intended. This also opens up the firewall to more likely have false positives as well, and a malicious actor may communicate through the firewall due to this. In the same way that the misconfiguration of the facial recognition gate did not need weaponization neither would the vulnerability present in the misconfigured firewall. The malicious actor is simply able to pass by the security feature due to its vulnerable configuration.
Human Mistake
To err is human. Exploiting the vulnerability of human nature itself is a technique everyone is familiar with and which translates well into the cyber domain. Weaponizing this type of vulnerability can be unnecessary and impossible when the vulnerability of a human mistake presents itself as a target of opportunity. On the other hand, planned solicitation of human mistakes can be pre-weaponized to take advantage of likely courses of human actions.
An example of an opportunistic human mistake vulnerability is as simple as tailgating behind a person after they badge into a secure area. The vulnerability in this example is that the individual with legitimate access to the secure area didn’t make sure that the person behind them either also badged in or had to open the door themselves. There is not much weaponization potential for these kinds of human mistakes as they enable the attacker by chance. On the other hand, calling the phone number for technical assistance at a company and tricking the person on the other end of the call into divulging sensitive information will require some weaponization. The vulnerability here is the overly trusting human on the other end mistakenly giving up sensitive data. The weaponization of that vulnerability is turning that data into access to the company in some way.
Most are familiar with email phishing even they are not familiar with the term itself. It is the act of sending out emails that somehow trick the recipient into doing something. This example of cyber exploitation using the vulnerability of human mistakes is pre-planned and weaponized by already having some intended action or information to illicit from the recipients of the email. The email may tell the user that their bank password has expired and to visit a web site to reset it. The web site the user is directed to is set up by the attacker to log their credentials. The vulnerability is the human mistakenly thinking they need to reset their password and visiting the site in the email. The weaponization is the pre-built web site which logs the username and password they use so the attack can then access their bank account. An example of a target of opportunity type human mistake vulnerability in the cyber realm would be something like pulling up someone’s email after they leave an internet café and forget to turn off or lock the computer they were using.
Illegitimate Use of Legitimate Credentials
This is the easiest to understand and simplest to leverage of the vulnerability categories, and exploitation of the vulnerability is similarly straightforward. In a non-cyber instance using legitimate credentials illegitimately, think of a house key. You go to your hardware store and they copy your house key for you while you shop. While they make you a copy, they also make themselves on and get your billing address when you pay with your credit card. The pattern on the key is a legitimate credential that will let you open the lock of your home when you get home. It can also be used illegitimately by the hardware store worker the next day when you are away to break into your house and take your belongings. The cyber domain also has keys, and they also can be copied by malicious actors for illegitimate use. This is the same for PINs and passwords as well. In some cases, especially in the software used to run devices like smart devices such as Wi-Fi-capable coffee machines or workout equipment, the passwords for the software is configured at a factory and almost never changed. When these credentials become public, they can be used by malicious actors to gain access to a device and from there target other systems. In all these examples, the vulnerability is clearly that legitimate credentials were obtained somehow and then the exploitation is using those credentials illegitimately to manipulate the behavior of another system.
Valuing Vulnerability Categories
To one degree or another, each of the vulnerability exploitation categories discussed in this chapter is caused by human error. Exploitation of human mistakes and utilizing valid credentials obtained through nefarious means require real-time errors by humans to facilitate remote manipulation of a system. Misconfigurations are human errors in the past which make a system more vulnerable than it could be if the system was correctly configured and code vulnerabilities are present due to a design-level error which becomes widespread through each instance of like systems.
Certainly, the value of a given vulnerability and its successful exploitation will vary from end effect to end effect especially to the warfighter more concerned with the attack portion of cyber activity. Exploitation-specific value however places the onus on a vulnerability’s potential to allow for end effects whether those are Title 10 or Title 50 specific. In this sense human mistakes are the least valuable as the vulnerability presents itself often by chance and is typically no more immediately widespread than the individual who made the mistake. Slightly more exploitable than human mistakes are misconfigurations. This is because once discovered by an attacker, they can be repeatedly used.
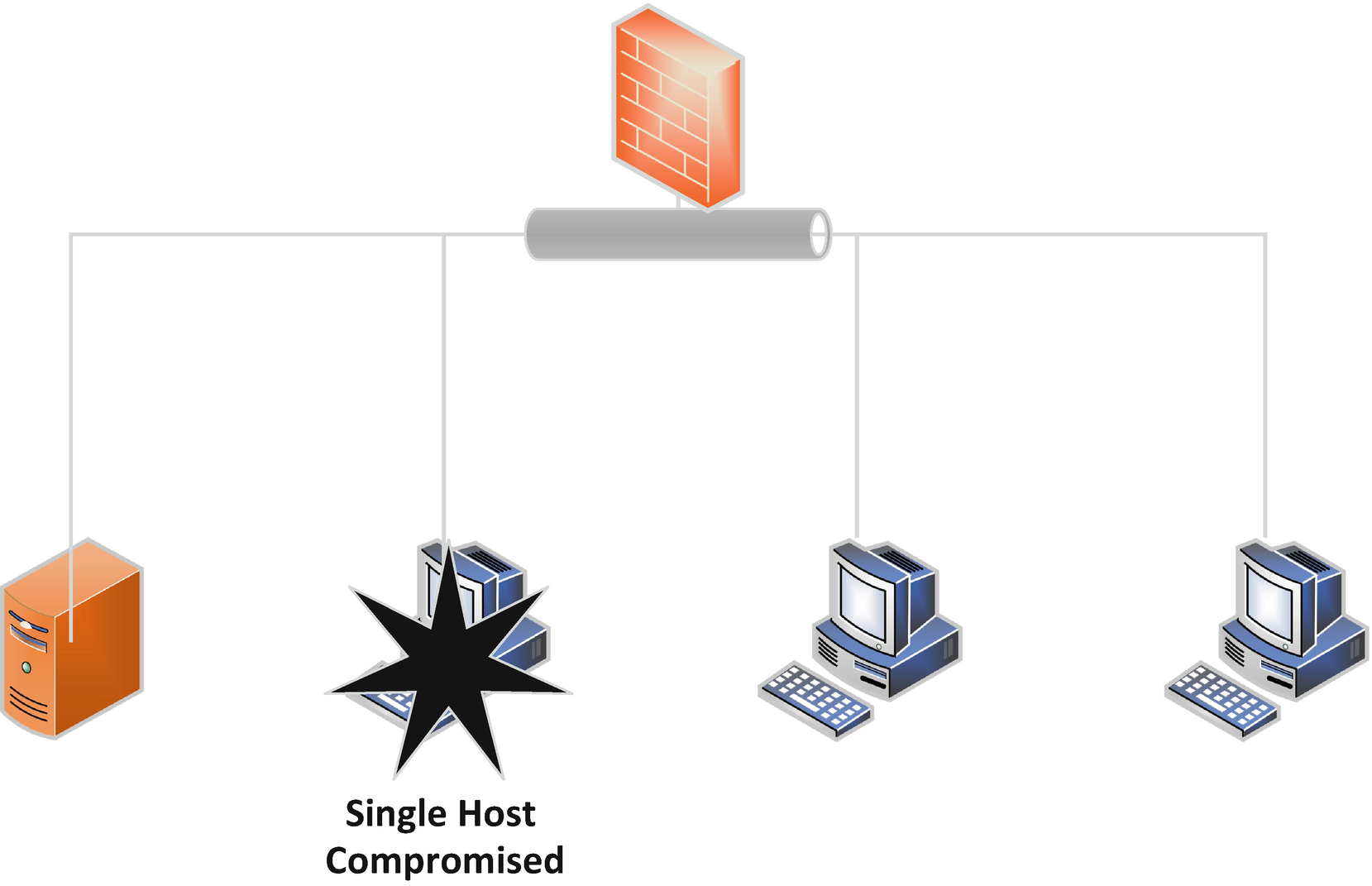
A Single Host Compromised by Mistake

Hosts Using the Same Template Compromised with Same Misconfiguration
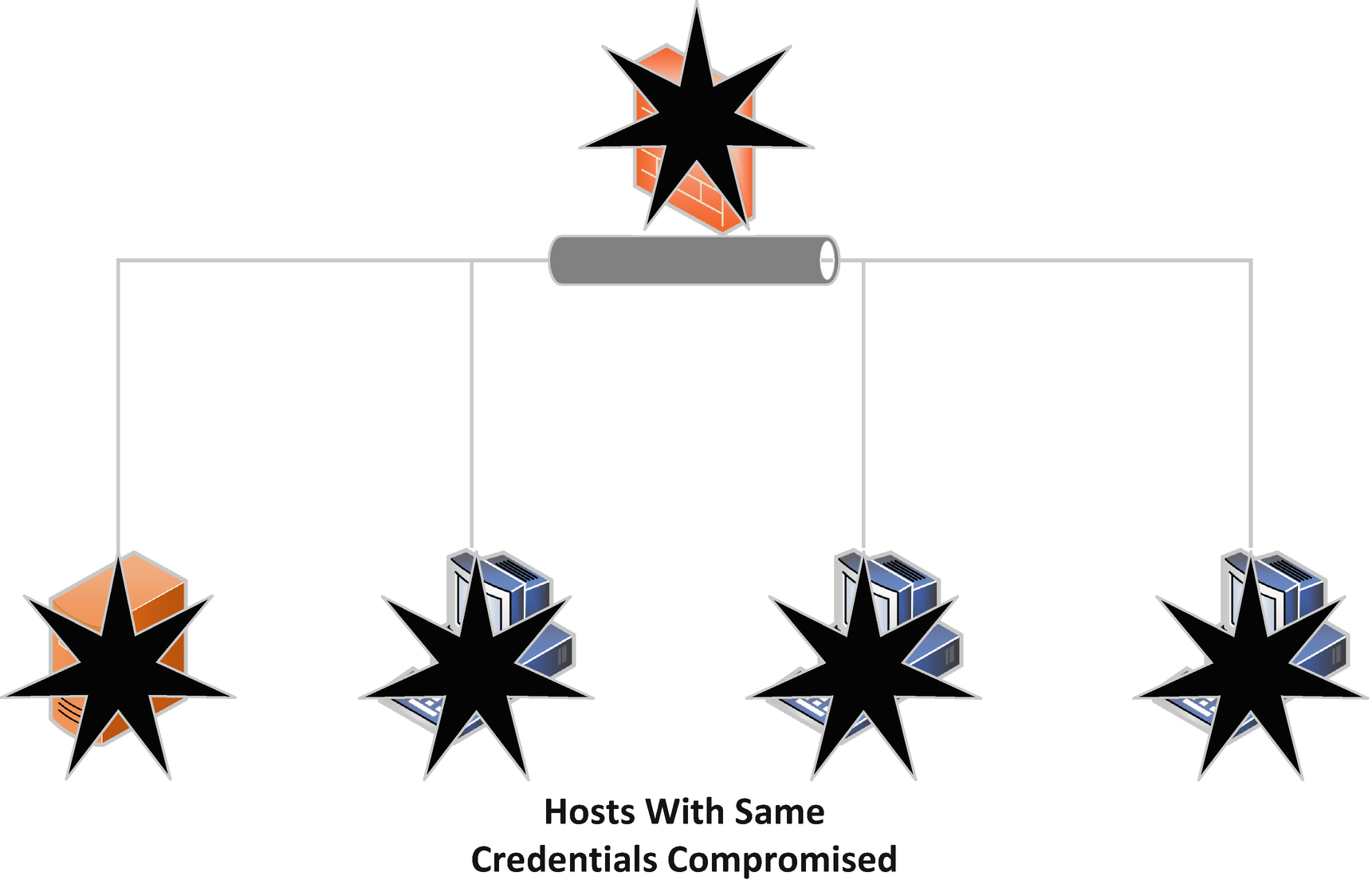
Credential Re-use Compromises Whole Network
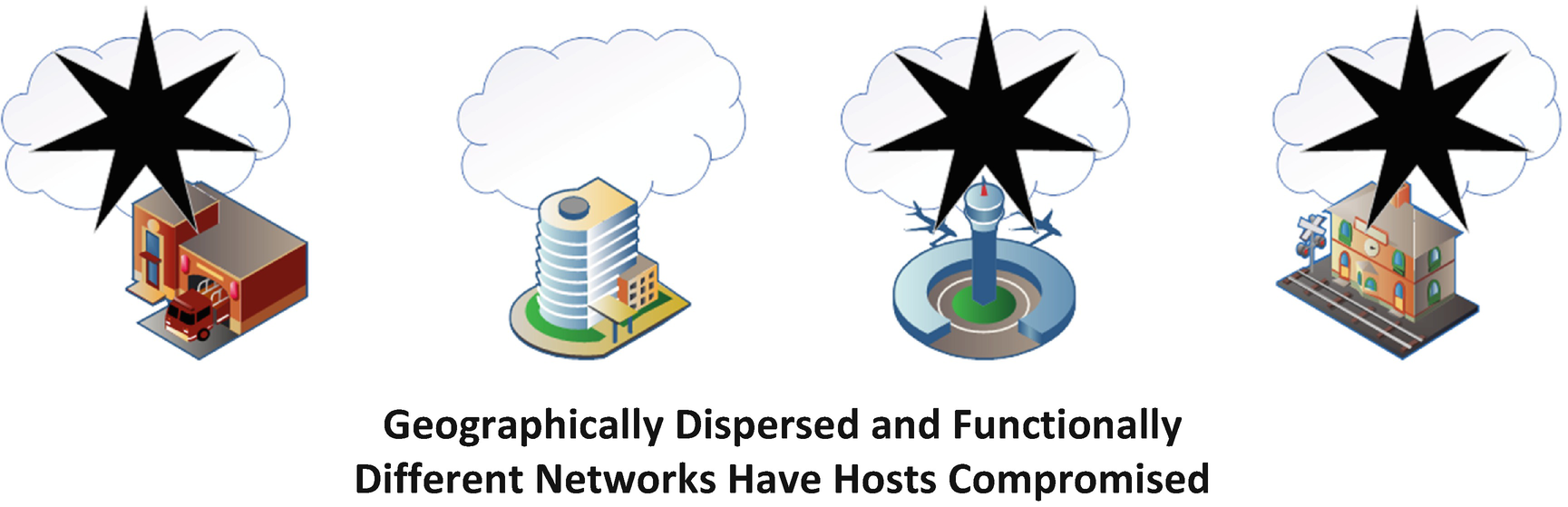
Code Vulnerability Can Compromise Any Host Using It
We have already discussed that code vulnerabilities are extremely difficult to discover which further increases their value. Thousands of hours can be spent attempting to find a code vulnerability in a particular system without any success. Further, if found and weaponizable, that vulnerability once leveraged is potentially identified by security systems on the target system or by forensic researchers as part of a resulting incident response. Worse yet, other organizations and individuals are also constantly looking for unknown vulnerabilities in code across the spectrum of applications and software. Therefore, even if you found a code exploit that worked against systems you needed to target but you were holding off for an important enough end effect, someone else may have discovered it and leveraged it in some other effort. If someone else using the same or even a related exploit of a vulnerability similar to the one you have been holding on to, the response by the security industry may mean your exploit no longer works or is detected. The same is true for security researchers who are also looking for code vulnerabilities for bounty programs and even just as employment. All this means that good, weaponized code vulnerabilities should be used only after weighing the cost-benefit and careful tradecraft consideration to avoid being caught and the vulnerability discovered when able. It also means that part of this decision should be that there is always the potential that the exploit and vulnerability that has been created for military use could become known to the public and then potentially useless at any time as well. I will also cede the point that exploiting human mistakes or misconfigurations, though potentially limited to a specific system, may lead to the compromise of entire organizations. This focuses on the potential vulnerability those devices themselves pose to the organization if compromised and not the categorical cyber vulnerability that was exploited to gain access to them.
Title Implications
So, we must now ask ourselves which authority exploitation within the cyber domain happens under so that we know how it is affected by the non-technical constraints. As it turns out, the activity of cyber exploitation is used to enable both Title 10– and Title 50–type actions. It is fairly obvious that the end effect of cyber reconnaissance to gather intelligence falls within Title 50 authorities and that cyber end effect of attack activities falls within Title 10. Exploitation is often needed in either case, whether to gain access to the targets of intelligence gathering activity or to pre-position cyber-attack effects. The litmus for which authority cyber exploitation activities fall within is dictate by the intent for the follow-on cyber end effect. If cyber exploitation is performed to gain access to a device to garner intelligence, then that exploitation was done under Title 50 authority’s subsequent oversight. Similarly if cyber exploitation allowed for an attack end effect tool to be installed on a system that was intended as a target of a military operation, it would fall under Title 10 as that exploitation would be considered battlefield preparation.
Summary
In this chapter we discussed the activity of exploitation within the cyber domain of warfighting. This activity leverages multiple different categorical vulnerability types and enables both the Title 50 end effect of intelligence gathering and the Title 10 effect of cyber-attack via battlefield preparation.
