Cyber end effect activities fall into the two categories of cyber reconnaissance for intelligence gathering and cyber-attacks. The previously discussed activity of cyber exploitation is necessary in many cases to enable intelligence gathering and is always necessary for cyber-attacks. Some might argue that exploitation is not always needed to attack another system and that they could do things like denial-of-service attacks. An example of such an attack might be sending so much traffic to the target system that it cannot process it correctly and fails in some way. If we revisit our definition of exploitation though, and its purpose of manipulating the target system to cause behavior that benefits the attacker, we can see how attacks are in fact exploitation. If I am sending too much traffic for a routing system to handle and it fails over into an open state, allowing all traffic, or even if it just shuts down or stops processing traffic from other senders as well, then I have manipulated that system to behave in a way I wanted which means I exploited it.

Increasing Noise Level of Cyber-Attacks
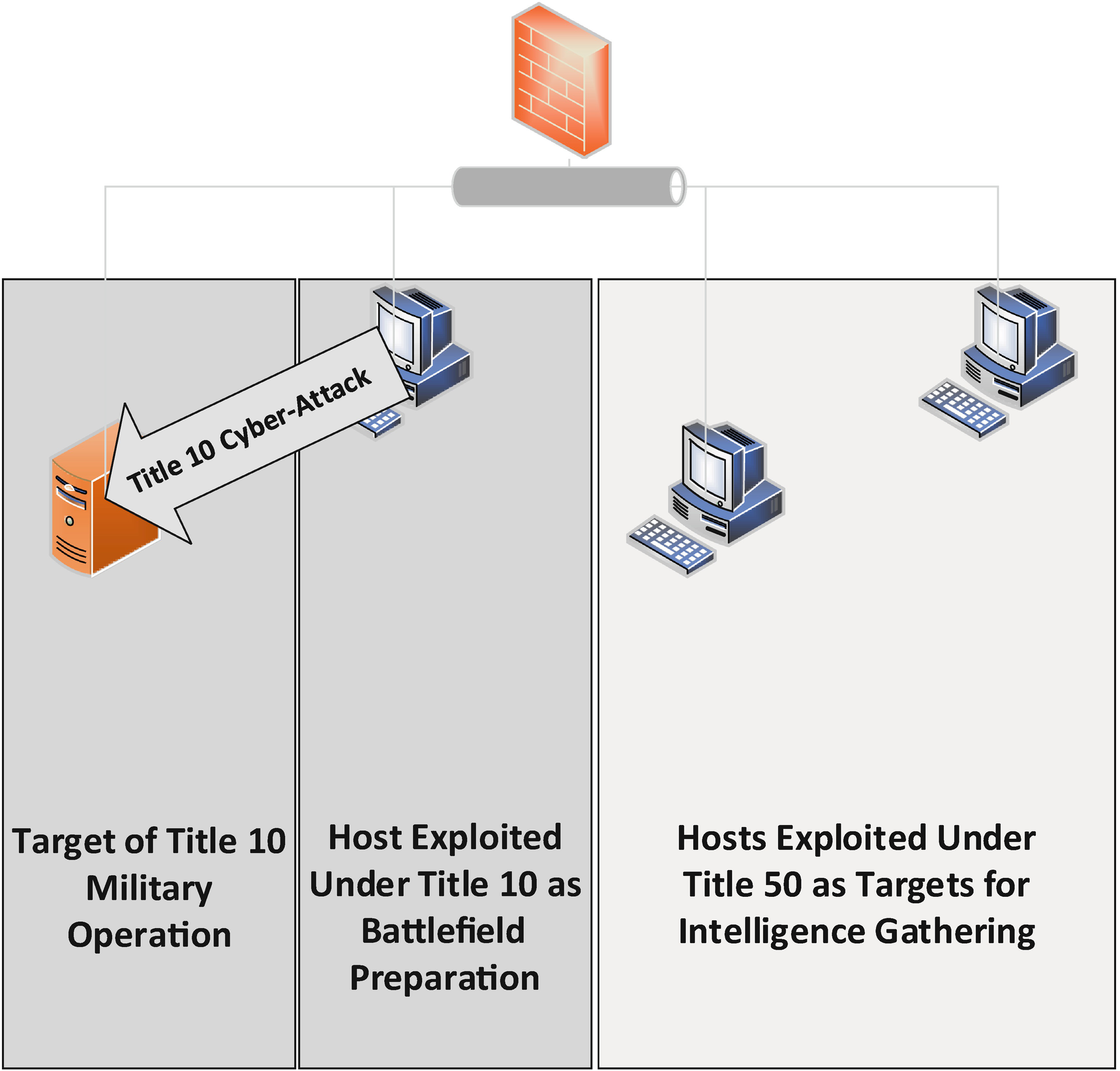
Title 10 Attack Launched from a Title 10 Exploited Host
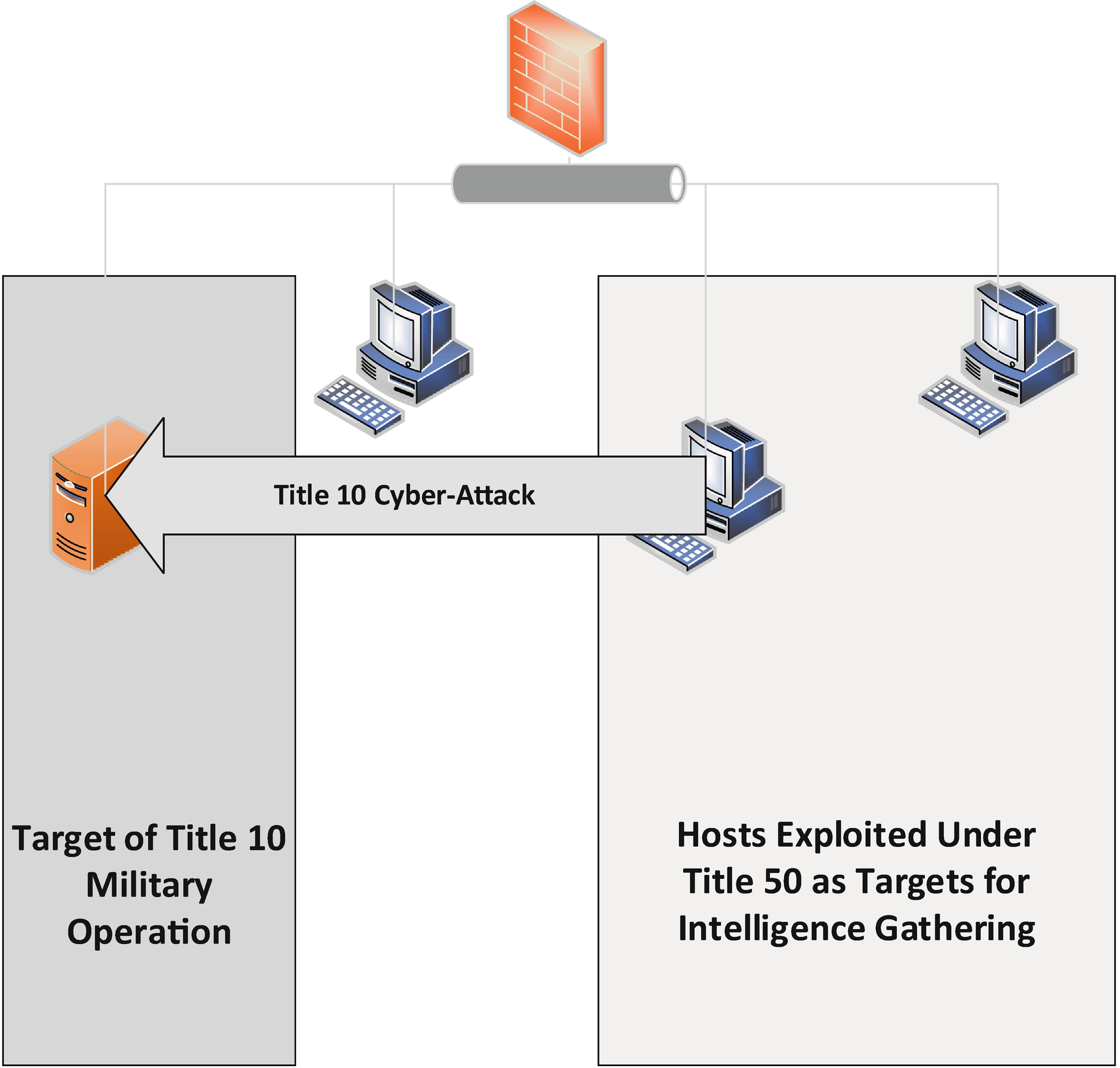
Title 10 Attack Launched from a Title 50 Exploited Host

Logical Relationships
Attack Types
There are two types of cyber-attacks, those meant to deny something from the enemy and those meant to manipulate the enemy. Manipulation may not seem like an attack activity, yet if we consider the idea of an action being noticed by one entity or another and that that activity is not intelligence collection or battlefield preparation, it should be considered a Title 10 cyber-attack action, no matter how benign or impactful that noticeable end effect may be.
Denying the Enemy
Denying the enemy using attacks in the cyber domain falls within one of three categories of degradation, destruction, and disruption. The goal of these activities is to deny resources to the enemy which can be anything from terrain, troops, supplies, situational awareness, and essentially anything utilized by the enemy that could improve or empower its warfighting ability. To illustrate the contrast between these different types of cyber activity and how they impact both enemy and friendly forces, the following examples will follow a similar theme. Each activity will be represented in a physical analogy, a wholly cyber example, and a cyber-physical example. Cyber-physical activities are those that bridge the cyber realm into a physical domain (air, sea, land, space) of war with the intent of having an effect in that domain. The activity exemplars will be framed in a scenario where the state launching the activity is attempting to impact an enemy state who is highly reliant on its oil economy and who has been engaging in acts of war against the launching nation.
Attacks that Degrade
Degradation denies the enemy resources by weakening its capabilities.
Non-cyber Example
A good example of non-cyber degradation of an enemy such as the one previously mentioned is sanctions. Sanctions allow one state to degrade another ability to maintain economical might and governing stability. Against an enemy highly reliant one type of good to maintain both its economy and government, restricting the ability for that nation to market, sell, and profit from its resource can be highly impactful and is often a priority tactic compared to other more violent physical degradation options.
Cyber Example
The headquarters of the state-owned oil company has a large firewall that manages connections to all external assets such as refineries and drilling rigs. The aggressor state sends heavy amounts of network traffic at the external points of presence reachable from the internet. The traffic is so much that it makes the firewall drop communications. The ability to communicate over the network becomes so bad for the state-owned oil company that it has to resort to telephone calls, in-person hand-offs of information, and transmission of orders to external assets by mail and messenger. This severely degrade the ability for the state to operate is most important resource.
Cyber-Physical Example
The aggressor state might target the drilling rigs that the enemy state uses to produce its oil and fund the rest of its efforts as a nation. To do this and cause degradation, the attacker might be utilizing a cyber weapon that uses the cyber domain to affect the physical. If a virus could alter the speed control for the drills used to find and pump oil, it might make those drills less efficient and make it harder for the enemy to garner more resources. It also may make the drill heads more likely to break and need replacement which would further degrade the state’s oil production.
Attacks that Disrupt
Disruption denies the enemy resources by interrupting or stopping enemy activities.
Non-cyber Example
In the scenario we are discussing a physical example of disrupting the enemy would be to blockade the port or ports from which the enemy transports its oil. Doing so doesn’t destroy any of these assets, which can be valuable as they could be utilized later by the attacking state. This could be considered a more effective way of denying resources to the enemy state than a degradation effort, but it is also much more overt and likely to lead to outright armed conflict with kinetic weapons. This type of disruption also has the added bonus of potentially hemming up the enemy state naval forces as well as they would be prevented from leaving port where they are vulnerable or returning to port for supplies if they were out at sea.
Cyber Example
A cyber domain disruption of this enemy could be manifested by attacking the enemy state’s ability to leverage global finances and move its valuable oil products to garner other resources. In this effort the attacker state launches a cyber-attack tool which was able to infect the state computers which access and participate in global stock exchanges. Once installed, the tool aims to ensure no stock purchase or sale requests made reach the exchanges. This disruption would severely hamper the ability of the enemy state to maintain economic stability, putting great pressure on the government.
Cyber-Physical Example
Instead of using naval vessels to blockade enemy ports, a cyber-physical disruption would consist of something with similar end effect but enabled through the cyber domain. Here, a cyber-attack tool could be delivered to the enemy oil tankers trying to leave the port loaded with oil. This cyber-attack tool takes control over engine or navigation controls and is used to either make the tankers dead in the water or cause them to steer in gentle circles. In this attack, the assets aren’t destroyed and are available for the attacker to potentially use later, but the disruption of shipping oil from the port is also achieved.
Attacks that destroy
Destruction is relatively straightforward and easy to understand; this attack effect denies the enemy a resource by destroying it.
Non-cyber Example
There are any number of destructive capabilities in many state arsenals, but in keeping with the theme of these examples, the physical destructive example I would cite is the destruction of enemy oil refineries using sea to land based missiles. The destruction of oil refineries limits the potential for loss of innocent lives or widespread ecological disaster by striking targets already kept far from civilian areas due to its inherent dangers and whose oil lines can eventually be shut off. Conversely, striking something like an oil tanker is not only likely to cause loss of innocent lives but would also lead to huge ecological impacts.
Cyber Example
Keeping a destructive denial of resources entirely within the cyber domain while still being effective requires slightly more creativity than our other examples. If the attacker could identify and gain access to all locations where sales, shipping, and production logs were kept for the state-owned oil company and then summarily corrupt or encrypt all of those digital files, it could potentially lead to a significant denial to the enemy state as it is likely that most transactions are completely carried out and stored in the cyber domain. Even were this not the case, the attack would still be effective in compromising the state’s ability to do business with its state-owned oil company.
Cyber-Physical Example
For a cyber-physical effect, let’s consider an example that again results in a similar impact to the physical example but which is cyber enabled instead of due to the damage caused by a missile. The attacking state might try and deploy a virus that alters the way the oil refineries maintain gas and liquid pressures in the refinement systems with the goal of causing them to fail catastrophically. The end goal of destroying refineries is accomplished but with a less likely violent reaction by the enemy state.
Manipulating the Enemy
Manipulation , as a form of cyberspace attack, controls or changes information, information systems, and/or networks in gray or red cyberspace to create physical denial effects, using deception, decoying, conditioning, spoofing, falsification, and other similar techniques. It uses an adversary’s information resources for friendly purposes, to create denial effects not immediately apparent in cyberspace. The targeted network may appear to operate normally until secondary or tertiary effects, including physical effects, reveal evidence of the logical first-order effect.
I think this definition very refined and also, coming in the form of warfighting doctrine from a nation state’s military, is topically representative of what we can expect from this type of cyber-attack. I find it useful to categorically break this type of attack into two different types, each having two varied intentions. There are manipulation attacks which alter the indicators a system is showing and thus the perception of a human interpreting the system wouldn’t be based on reality. There are also those that manipulate a system’s ability to perceive inputs as designed which also would ultimately misrepresent reality to the human interpreting it. This second type of manipulation is broadly termed as sensor perception compared to the human perception. In either case, manipulation attacks can be done for aggressive or protective reasons. Aggressive manipulation of human or sensor perception is done to enable attack effects against the enemy. Protective manipulation on the other hand is done to protect the warfighting resources of the attacker whether they be lives of troops or cyber tools.
Human Perception: Aggressive
The following are examples of manipulation of human perception for aggressive means.
Non-cyber Example
Some may argue that influence operations are outside the scope of military activity and fall more within the realm of espionage. I believe that as long as the goal of such influence is not to overthrow the local governing parties and is directed toward adding military operations, it does still fall within Title 10 activity, especially when we consider the battlefield preparation clause. As a physical example of this, imagine the attacking state dropped flyers from airplanes much like was done in World War II by both the allies and the axis forces. If these flyers said that oil refineries were going be struck by missiles in 2 days, it could be done with two potentially effective impacts on the enemy.
First, the enemy might lose resource production capabilities as people were afraid to work at the oil refineries even if no attack was launched, which has nearly the same outcome as if they were actually attacked. Second, this could be a distraction as the attacker actually planned to attack oil lines that transport the oil from the refineries to customers. This second benefit might be considered more protective than aggressive though as it distracts resources from defending the actual target of a strike.
Cyber Example
A completely cyber domain contained example of a manipulation attack might involve state social media accounts and other state dissemination capabilities. The attacker would want to gain access to these systems with the goal of changing the language of what is posted via these capabilities as an attack on the enemy state. This could be done by changing information put out by the state attempting to calm and ensure order to statements that are incendiary and instill insecurity in the populace. The enemy state may be saying everything is fine with the economy and there were no financial issues in an attempt to maintain economic and governing stability. If the attacker changed that to posts saying if issues with oil resources go on for even a few more days there might be economic collapse, it could certainly have an aggressive impact on the enemy state.
Cyber-Physical Example
A cyber-enabled effect for a manipulation of human perception might be something as simple as making all danger indicators for oil pipelines and refineries constantly stay green despite what sensors are reading. The underlying systems are still performing their job and identifying danger situations, but instead of conveying that accurately, the indicators perceived by the systems are constantly showing that there are no issues. This combined with other affects could lead to extremely effective attacks against such systems without humans realizing until failure was catastrophic. Even in the absence of other attacks against these systems, there remains the possibility that they fail on their own and that the humans who are supposed to monitor them would be unaware until something destructive occurred to indicate there was an issue.
Human Perception: Protective
The following are examples of altering human perceptions through attacks for protective reasons.
Non-cyber Example
Going back to World War II, we can find another classic example of manipulation of human perception, and this time to protect attacker resources. Using wood and other materials, troops constructed fake tanks so that observers from a distance or in the air would think that tank units were deployed in an area they were not. This means that the enemy is less likely to keep looking for other tank units and would likely waste their own resources engaging these fake tanks. This might allow the real tanks to gain better position or successfully engage enemy forces.
Cyber Example
Protecting the attacking state forces from the enemy is also well accomplished completely within the cyber domain. Imagine the attacking state had advanced forces in the country behind enemy lines, and those forces who are currently operating in a covert nature prior to the military operation think they were caught on security cameras. If the attacking state had access to the network those cameras were on and was able to replace the camera recordings that potentially captured the advanced forces with copies of ones where nothing was going would be an example of a cyber manipulation in the cyber realm to prevent the enemy’s ability for human perception to identify the advanced forces.
Cyber-Physical Example
Let’s say that the cyber example was not completely successful and one of the advanced operatives was captured by local law enforcement and needs immediate rescue before it is determined he was from the attacking nation and was placed at risk to grave harm to himself and potentially divulging damaging information about the attacking state’s operations as well. A cyber-physical attack could be used to leverage cyber accesses in the police headquarters where the operative was being held as part of rescue efforts. For instance, if the attacking state was able to use access gained via cyber exploitation to execute a cyber-attack that set off all the fire alarms at all police stations in the city of the state police headquarters, it would cause enough commotion and confusion to make it safer and easier for special forces operators to infiltrate and rescue the captured operative. Here the human ability of the enemy state to perceive what was really going on and adequately respond to the rescue attempt of the attacker operative was successfully manipulated.
Sensor Perception: Aggressive
The following are examples of manipulation of sensor perception for aggressive means.
Non-cyber Example
A very literal and non-cyber way of interacting with enemy sensors in an aggressive activity could be using mobile lasers to remotely heat sections of oil pipeline in remote locations of the enemy state. This would cause sensors to incorrectly think there was a dangerous issue and either shut down parts of the oil distribution network or require response by human inspectors. Either way the operation is an attack on the oil distribution network by abusing the sensor’s ability to detect heat as an indicator of danger.
Cyber Example
A cyber example of aggressively attacking a sensor’s ability to perceive and thus relay correct information could be an attack against laboratory devices belonging to the enemy state-owned oil company. In this situation malicious code attacks and alters the controlling functions of different measurement and detection devices within the oil company laboratory in an effort to have them develop flawed formulas that they believe in the lab to be improvements which in fact make their important state reliant resource worse. This type of attack could also interfere with the sensor’s ability to read quality measurements from different oil products and, by altering the sensor’s ability to measure quality, impact the company from preventing poor product, making it to markets and impacting their reputation as a provider and exporter. This example is holey cyber since the attack on the sensors happens via the cyber domain, and the end effect is the laboratory producing data into the cyber domain that is inaccurate and potentially disastrous to the enemy state.
Cyber-Physical Example
There are many examples of how altering the ability of a sensor to correctly read its target metrics could lead to issues of a cyber-physical nature. One such might be infecting the ballast control software for the enemy state oil tankers with malware that makes the ballast and list sensors of the tankers report read inaccurately. This type of attack could lead to oil tankers rolling from side to side or sinking too deep in shallow waters and running aground. This attack could thus be a manipulation of sensors in an aggressive way that leads to either destruction, by leading the tankers to run aground, or a disruption in causing them to roll uncontrollably and prevent them from taking on their cargo or transporting it, out of the port. If done in a more controlled and less noticeable manner, this manipulation of sensors could also degrade by making the tankers much less efficient due to ballast instability in their travel to offload the enemy state’s export of oil.
Sensor Perception: Protective
The following are examples of altering human perceptions through attacks for protective reasons.
Non-cyber Example
Suppose the attacking state needs to drop ordinance from jets to destroy assets of the enemy state either in preparation for or party to a military invasion. The enemy state likely has anti-aircraft capabilities such as surface to air missiles. In this scenario the jet may launch chaff or flak upon detection of a surface to air missile launch in hopes of distracting the missile and protecting the jet. This is a non-cyber example of protectively influencing sensor protection. The missile was homing in on the attacker jet before the anti-missile capabilities drew the missile away from the jet, saving the pilot and aircraft and allowing it to drop its ordinance on the target.
Cyber Example
Just as bomb dropping aircraft may need protection entering enemy airspace, cyber-attack activities may need assistance entering enemy cyberspace. There might be enemy firewalls sniffing and identifying traffic that would prevent both battlefield preparation and even more dire cyber-attack effects as a war with an enemy state continued. If an attack tool was uploaded to the firewall post-exploitation that could alter the ability of that firewall to pick up on just the attacker’s traffic, it would be an example of a cyber effect on sensor perception to protect the ongoing and future operations. Instead of leveraging a misconfiguration or altering the enemy system to make it misconfigured, this type of attack might affect the enemy firewall device at a lower level such that its ability to see specifically the attacker traffic is nullified, but to the managers and administrators of that firewall, all rules and configurations would continue to look correctly in place because they had not been modified.
Cyber-Physical Example
Bridging the gap between these scenarios to a cyber-physical affect could be an effort to attack radar systems. These are complex systems and are reliant on extremely tailored sensors as well as computing systems. The attacker may want to mitigate detection by the enemy state radars by using a cyber-attack to manipulate the ability of the radar system to read radar signatures of larger objects, instead interpreting them incorrectly as bird-sized objects. In this case the radar system affected by a cyber-attack tool would be relaying what it perceived as accurate information to the human monitors that the incoming objects were birds and not attack helicopters.
Espionage
Some of the examples given, especially those falling categorically under the manipulation type of cyber-attack, certainly come close to the line between cyber-attack activities under Title 10 and what may be considered espionage. Firstly, the individual conducting the act has a large part to do with it. Uniformed members of the armed services, particularly in the United States, are typically not authorized to perform espionage activities. More certainly, if they did, even through cyber means, it would have to be under the command and direction of some other entity besides the Department of Defense.
Let’s take the grayest example in a world that is not really black or white anyways. We discussed an example of cyber-attack activity where the attackers were manipulating message boards, social media, and other mediums. In a situation where this effort ties in some way to a military operation, be it short in duration or a long-standing invasion, it can be considered safely within the Title 10 authority of cyber-attack via manipulation against an enemy state. It becomes espionage when the efforts of that social media manipulation are aimed at sowing discord and upheaval in the enemy state’s inhabitants in hopes of overthrowing or altering or weakening that state’s government and/or national defense capabilities.
Summary
In this chapter we discussed in depth the cyber domain warfighting activity of cyber-attack and provided numerous analogies as teaching points for the categorical differences in types of cyber-attacks. The difference in both traditional warfighting and unconventional cyber warfighting was discussed in respect to both denial and manipulation categories of attack. Scenarios were used to show the differences between degradation, disruption, and destruction cyber-attack operations and similarly used to illustrate both aggressive and protective manipulation attacks against the perception of both human and sensors. Lastly, we discussed how espionage in the cyber domain can seem similar but is motivationally different than cyber manipulation activities.
