Successful completion of the attribution process is done via a positive identification of the perpetrating actor and infallible determination of that actor’s motivation. If that motivation is deemed to be a cyber-attack, by open acknowledgment of irrefutable proof, we have established that we have an enemy. This enemy is one that is engaged in warfighting activity, targeting us, within the cyber domain. At this point that enemy must be considered as being openly engaged in conflict with our own state. As such, responses to the enemy state’s cyber-attack could be from or within any combination of warfighting domains. It might be appropriate to ignore, sanction, respond in kind, or escalate to something such as a kinetic capability like a missile or bomb. For the purposes of this book, we will not attempt to weigh out appropriate non-cyber responses to cyber-attacks of enemy states. Instead I will outline how a cyber response action could actually be conceived and executed.
Most importantly to cyber activity as a warfighting construct is an understanding of how the enemy and the actual target of a response action differ. The enemy identified by the attribution process may not be a specific actor but the wider state behind that actor. This is why motivation, and specifically a Title 10–like attack motivation, must be determined to drive a similar response. In a Title 10–like activity, the attribution process may determine a specific unit, organization, or even individual behind cyber activity. However, since it is Title 10–type activity, it is attributed to the sponsoring state, as the individual, unit, or organization is considered an agent of that state. Also, in this case, the attributed state is now considered an enemy, and there is a potential for open conflict or even declared war with that enemy.
Tactical vs. Strategic Response
Attribution resulting from Title 10 cyber activity could establish a foreign state as an enemy in a declared conflict. In response to that specific Title 10 activity which initiated the conflict itself, the victim state is likely to conduct its own warfighting activity. Such a response may target the enemy state-sponsored perpetrating unit, or it might be something else.
Think of the bombing of Pearl Harbor. That action led to open and declared war between the United States and the Empire of Japan. The first real response by the United States didn’t target the Japanese naval fleet which launched the attack on Pearl Harbor. Instead the US government and military felt it more strategically appropriate to respond by attacking the Japanese homeland. This was accomplished by the Doolittle Raid, an attack by US bombers launched from naval vessels which dropped ordinance on the Japanese capital of Tokyo and other locations on the island of Honshu. This was done to send a message that the United States could also strike far across the Pacific Ocean at the Japanese home front. In this example the enemy was determined to be the Empire of Japan, and the target of the response was determined to be Tokyo, not the warfighters responsible for the attack on Pearl Harbor. At a tactical level, US forces attempted to return fire and ward off parts of the attack during the air raid over Hawaii. This return fire was a tactical response to an ongoing attack and not a strategic response as part of a larger conflict like the Doolittle Raid was.
The attack on Pearl Harbor is a great analogy for describing some of the constraints and challenges to cyber warfare. In cyber warfare, it would be hard to know that there was enemy activity against victim assets until the actual attack happens. Also, in the cyber domain, the tool that launched the attack effect may have been put in place months or years earlier. It is very likely that when the enemy has launched their attack they have been gone for a long while or at least are in the process of moving on to other targets. In cyber warfare, the attack effect is logically the last action an enemy actor will take within a network or organization. After the attack is launched, victim systems may be no longer accessible due to the type of attack. Additionally, the victim network is now aware that an actor has been within it and is probably on high alert and far more likely to thwart further Title 10– or even Title 50–type activities by an enemy within it.
Similarly, the Japanese attack on Pearl Harbor happened after much planning, strategic decision-making, preparation, and a long naval journey to Hawaii. Once the attack was launched, the Japanese fleet involved headed back away from Hawaii. Consider if they had stayed around Hawaii or even decided to attack other parts of the United States such as California. With hostilities now openly known, their attacks would likely be less effective if not a complete failure. The decision to strike Pearl Harbor was a strategic one by the Japanese Empire, and the attack itself was a tactical mission with its own tactical decisions within it. The only tactical response by the United States would be any exchange of fire between the US forces at Pearl Harbor and the perpetrating actors. Outside of actively engaging the attacking force during the attack, the response by the United States was decided at the strategic level as part of the wider conflict.
In fact, the US response didn’t take place until April 12, 1942, over 4 months after the December 7, 1941, attack on Pearl Harbor and the declaration of war by the United States on December 8, 1941. Though the open conflict was addressed by the United States the next day with a declaration of war, careful planning and consideration went into the strategic decision of how to respond to this new enemy and which enemy target and attack effect was appropriate. Imagine if the US response was as immediate as the declaration of war. The closest naval and air resources to Hawaii were probably days away at minimum. Also, any attempt to find the Japanese forces in the wide expanse of the Pacific Ocean, before the age of jet aircraft and imagery satellite, would like have proved futile so any attempt at a direct response to the perpetrating agent of the Japanese Empire was out of consideration.
Cyber warfare requires the same tactful response considerations. There is not a possibility for tactical response to ongoing actions such as a return of fire to the perpetrating unit. This is because the enemy is not actually present at the target being attacked, they are anywhere in the world with an internet connection, if there is a human involved at all. The attack is also potentially a leave-behind set to go off at some triggered event and not an active action by a human, even if a cyber return fire capability existed, it would have no effect. This is not to say that as part of open conflict, cyber-attack effects won’t target enemy cyber warfighting assets or capabilities. Simply put, any decision to conduct cyber warfare against an enemy is decided at the strategic level and not the tactical one. Warfighting responses from the cyber domain are not technically nor tactically possible as a return fire action to an ongoing enemy attack. This is extremely important to understand as we move forward with our discussion on how targeting decisions for cyber warfighting effects are made.
Let’s revisit the Pearl Harbor analogy one last time. Imagine that the naval ships docked in Pearl Harbor as well as the Japanese aircraft carriers and aircraft were all remotely piloted like modern-day drones. For this example, let’s also say that the Japanese planes dropped one load of bombs and then left US airspace immediately to return to their aircraft carriers which then steamed homeward and the United States had no anti-aircraft capabilities in Pearl Harbor. The attack would be launched, US assets would be destroyed, but there would be no active engagement between the US ships and the Japanese aircraft or fleet. Realizing what happens, the United States still declares war the next day, but obviously there is no realistic way to go after the Japanese fleet, so they strategically consider how to send a similar message what the Japanese just did, which is the Doolittle Raid deep into the Japanese Empire.
A cyber domain Pearl Harbor–like incident would play out the same way. The enemy would execute its attack capability. Let’s say the cyber-attack took over the computers driving many US aircraft during the over 100 aircraft JFEX exercise and crashed them all into the ground. Let’s also say the enemy state then openly acknowledged the attack. The duration of that attack effect, from the point where the aircraft computers were taken over until they crashed into the ground, would be only minutes. During that attack effect window, there is not time to return fire, nor a target readily identifiable as the attack took place in US airspace, aboard US aircraft which crashed on US soil. Such a cyber-attack effect could have been put in place months even years prior to the exercise. As an example, let’s say the cyber-attack tool was introduced to the aircraft systems due to supply chain interdiction 4 years earlier. The aggressor nation swapped legitimate computer chips used for an upgrade of the aircraft computer systems with one of their own malicious design mid-shipment. The attack triggered when the planes flew over the airspace used for the JFEX exercise over Nevada which is always held in the same place each time and is the biggest air exercise the United States conducts.
This is only a hypothetical scenario which is however it clearly illustrates that any response to a cyber-attack will involve a strategic decision-making process for target selection and attack methodology. One last time, there is no realistic scenario for cyber-attack effect return fire. There is no effective or realistic potential for actively targeting enemy cyber forces during their attack. The victim may respond at a later date by targeting the cyber forces, but it won’t happen while their attack is going on. Remember, without positively knowing the intention and motivation of cyber activity, we cannot realistically determine if it is Title 10–type actions or Title 50. The cyber activity that prepared the battlefield for the effect by installing the attack tool took place years earlier. Even if the actor was caught during their supply chain interdiction attempt, there is no way of easily determining what the malicious chips actually did. Even if we did reverse engineer them and determine they could crash planes, we still can’t know if the enemy was going to actually execute the attack effect so we could not launch our own Title 10 activity or declare open hostilities just off catching them during their interdiction operation. Thus, we have elaborated on earlier positions that we cannot determine motivation positively as being Title 10 in nature and respond in kind until the attack is actually executed. Additionally, since the attack was essentially launched years before hand, there is no opportunity to tactically return fire with a cyber-attack of our own.
I feel I have belabored this point with my own opinion and analogous examples enough now. I do so because there is constantly this talk of engaging cyber enemies in military and political circles and that is just not a realistic possibility. As you also now realize, actively engaging cyber adversaries is simply not how cyber warfighting would work. It is in fact far more likely that we were able to respond to an ongoing cyber-attack effect using something kinetic like a missile or bomb. This however is also an extremely unlikely scenario. Now that we have arduously gone over why, we will move forward accepting that any cyber response to an act of war, be it cyber or otherwise, will be deterministically and strategically decided in regard to both target selection and manner of effect. Next, I will cover how we move from knowing who the enemy is to decide what part of that enemy to target and with what kind of attack.
Target Selection
With hostilities declared, the enemy identified, and a cyber response determined to be appropriate, we need to decide what we want to target with a cyber response and what we want that attack effect to be. If we pause to think about that though, it is much more logical that cyber-attack effects are chosen for use based on the target and not vice versa. It makes more sense for a target to be selected first and then cyber warfighting conducted if deemed the appropriate way of affecting that target. Unlike some warfighting options in other domains, such as cruise missiles and nuclear bombs, cyber weapons rely on at least a fundamental understanding of the target to actually work. We don’t need to know the inner workings of an enemy troop transport to hit it with a missile and destroy it. If we wanted to use a cyber-attack to instead crash the vehicle or simply kill its engines, we actually need to accomplish several feats. We need to get our attack tool installed on the truck, and with enough privileges that it can take adequate actions to execute the attack activity when called upon.
What we will not attempt to do in this book is identify what type of attack effects are appropriate in response to what aggressions. Those kinds of decisions I will leave to strategists and commanders involved in real conflict. What we will do though is walk through the process of targeting and scoping whatever enemy resource is identified. In offensive cyber security assessments such as penetration testing or red teaming, accurate scoping of those engagements drives the rest of the process and ultimately determines how successful the assessment can be. Cyber-attack targeting is much the same. The scope and method of the attack dictate the entire tactical decision-making process during a cyber-attack mission. Since we have also determined that the targets available to cyber warfighting are limited to those targets for which the aggressor can develop working attack effects, we will focus on that concept first.
Appropriate Targets
- 1.
A cyber-attack effect is the best option available to deny or manipulate the target.
- 2.
A cyber-attack effect already exists that produces the desired denial or manipulation of the target, or
- 3.
A cyber-attack effect that produces the desired denial or manipulation of the target is capable of being developed in a timeline that supports the intended strategic benefit.
- 4.
There is a realistic potential for access of the enemy target and delivery of the cyber-attack effect.
The Cyber Option
What makes a cyber-attack effect the right choice when targeting enemy resources? In the increasingly internetworked world within which war must be fought, cyber is likely to increase in the future as a weapon of choice. It has the benefit of being launched with no inherent danger to the perpetrating agents of the state which is no small thing. Another benefit to cyber over kinetic weapons is that they can be positioned and left behind to be triggered only when deemed necessary. If one country feared aerial invasion by another and was able to compromise their aircraft as discussed in the earlier example, perhaps they would and only intend to trigger the attack effect if the enemy state invades their airspace. There is also the optics of cyber warfare. At least for now, and until someone uses cyber weapons to target something like a hospital or accidentally kills innocents, cyber warfare is perceptively non-violent. This means retribution on the conducting state by the wider international community is less likely, if it could be tied back to that state at all. There are plenty of other reasons to choose a cyber option for Title 10–type attack actions as opposed to something such as an invasion force or cruise missile. Regardless of the reasons, the decision that a cyber-attack is the most appropriate or best-case scenario is the first step in targeting an enemy resource with a cyber warfighting activity.
Existing Capability
If cyber-attack is considered preferential to conventional options, then there must also be an existing attack capability as the development timelines of a new cyber-attack effect would likely make it not a first choice. The capability to attack the enemy resource must be readily available and must produce an effect that realizes the strategic need to attack that resource in the first place. For instance, one state may have a cyber weapon capable of affecting its enemy’s tanks. Tanks are highly computerized weapon systems in today’s militaries and could be susceptible to cyber-attacks. One cyber weapon may be capable of shutting down the electric engine controls for the tank, stopping it dead in its tracks. Another cyber weapon may be able take over the firing and targeting system of the main canon so that ordinance went off inside the barrel when fired. Both effects are considered cyber-attacks and as such would fall under Title 10 definitions; however, maybe one of those effects delivered the strategic goal of the intended attack and the other did not. If the goal was to take over the enemy tanks for later use, then having the canon discharge into the tank and destroy it would not be strategically viable. Therefore, even if a cyber-attack effect exists, it must deliver the intended impact to be a viable choice.
Developing the Capability
If a capability that meets the strategic impact requirement for targeting an enemy resource does not exist, cyber warfare may still be appropriate if there is a realistic possibility it can be developed. The real consideration in this case is whether or not that development will happen in a time frame which doesn’t change the strategic viability of the attack. Say we consider the same two cyber-attacks against tanks we just discussed. There might be a realistic capability that the non-destructive cyber-attack could be developed, but perhaps it is likely to take 6 months. If the enemy is planning on invading with their tanks in the coming weeks, this would not be an appropriate target selection. Just because it would be best to target an enemy resource with a cyber-attack and there is possibility of finding an attack effect that delivers the needed impact does not mean it is a responsible choice of weapon. Time and other constraints can drastically alter the feasibility of a cyber-attack.
Access to the Target
In some cases, a cyber-attack target may be readily accessible across internet connections from the attacking state to the enemy. In any other case, there must be an ability to access the desired resource to then deliver the attack effect. Imagine the Japanese Empire decided an aerial bombardment of Pearl Harbor the best attack scenario against the United States but that they did not have aircraft carriers. Their planes had nowhere near enough range to make it from any outpost to the Hawaiian Islands and then, despite being the best attack option, aerial bombardment would no longer be within the consideration of attack options. We will discuss the challenges and requirements for developing access in the next chapter, but for targeting decisions, there simply needs to be an existing ability to access the target for delivery of cyber-attack effect tools or a realistic possibility of creating that access.
BDA
Battle damage assessment (BDA) is the evaluation of the effectiveness of a stand-off weapon and the damage it inflicted on a target. Traditionally this practice is applied to long-distance missile strikes or bomb drops where the actual striking of the enemy target is not directly observed. BDA is an extremely important aspect of warfare as it allows for continuous assessment of weapon effectiveness. If a missile consistently comes back with poor BDA because it fails to inflict the anticipated destruction on targets, that information needs to be made available to decision makers. This type of information allows strategic decision-making to evolve over the course of a conflict to allow for more effective targeting of enemy resources with friendly weapon systems.
Cyber warfare, with its extremely dispersed engagement situations, needs BDA whenever possible just as cruise missiles or high-altitude bomb drops. If a cyber-attack effect is deemed appropriate and launched at multiple enemy targets but fails to deliver on the strategic goal of those activities, the decision makers need that information. BDA is not simply important to evaluating whether or not a launched weapon, cyber or kinetic, was effective enough to meet the commander’s intent for the attack. There is another aspect to BDA which is important to just war concepts and international conventions such as the Geneva Convention.
If BDA comes back indicating a missile is destroying more than intended or with less precision than expected that is extremely important information to commanders and their strategic decision-making needs. Unnecessary destruction and potential harm to innocents and non-combatants is an ugly side effect of any conflict, and if a weapon cannot reliably avoid such impacts, it should cease to be used or at a minimum employed with different rules of engagements . Cyber weapons are no different. Imagine a virus intended to shut off power to military installations spread beyond them and started shutting off power in hospitals and prisons and other places which endangered the non-combatant population of the enemy state. This would be as strong a reason to alter the use of a cyber weapon as excessive collateral damage would be to a missile.
Unfortunately, unlike kinetic weapons, we cannot fly over the target of a cyber strike and evaluate its effectiveness. In attacks enabled by the cyber domain where the attack is a cyber-physical attack with a result noticeable in another warfighting domain such as air, land, space, or sea, we can still potentially evaluate the results and conduct BDA. On the other hand, I do not know the most correct methodology to conducting BDA in cyber domain attack activities. Rather I am asserting that conducting effective warfare in a just war and following international conventions in the conduct of cyber warfare would in part rely upon BDA capabilities which the cyber domain does not easily accommodate.
Target Fidelity
In the previous chapter, we discussed the attribution process and how certain attributes of cyber-attack effects certainly had a shelf life. When the target of a cyber domain attack is another cyber entity such as a computing system, there is a similar concern with the timeliness of target development and subsequent attack. When a computer system is targeted by a cyber-attack, the confirmation of target identity is likely done via electronic addresses such as IP address or MAC address. Those addresses can be changed at literally any time for any number of reasons. This is particularly the case of systems with internet-facing addresses.
The volatility of such addresses is hard to determine. As such, a remote cyber-attack against an internet-facing enemy system is targeted and sent via its IP address. What if between the decision to go ahead and execute the cyber-attack and the exploit operation that put the cyber-attack tool in place, the remote address changed. At this point there is certainly a chance that the state launched a Title 10 cyber-attack against an electronic address that potentially is being used by a completely different state than when it was originally targeted.
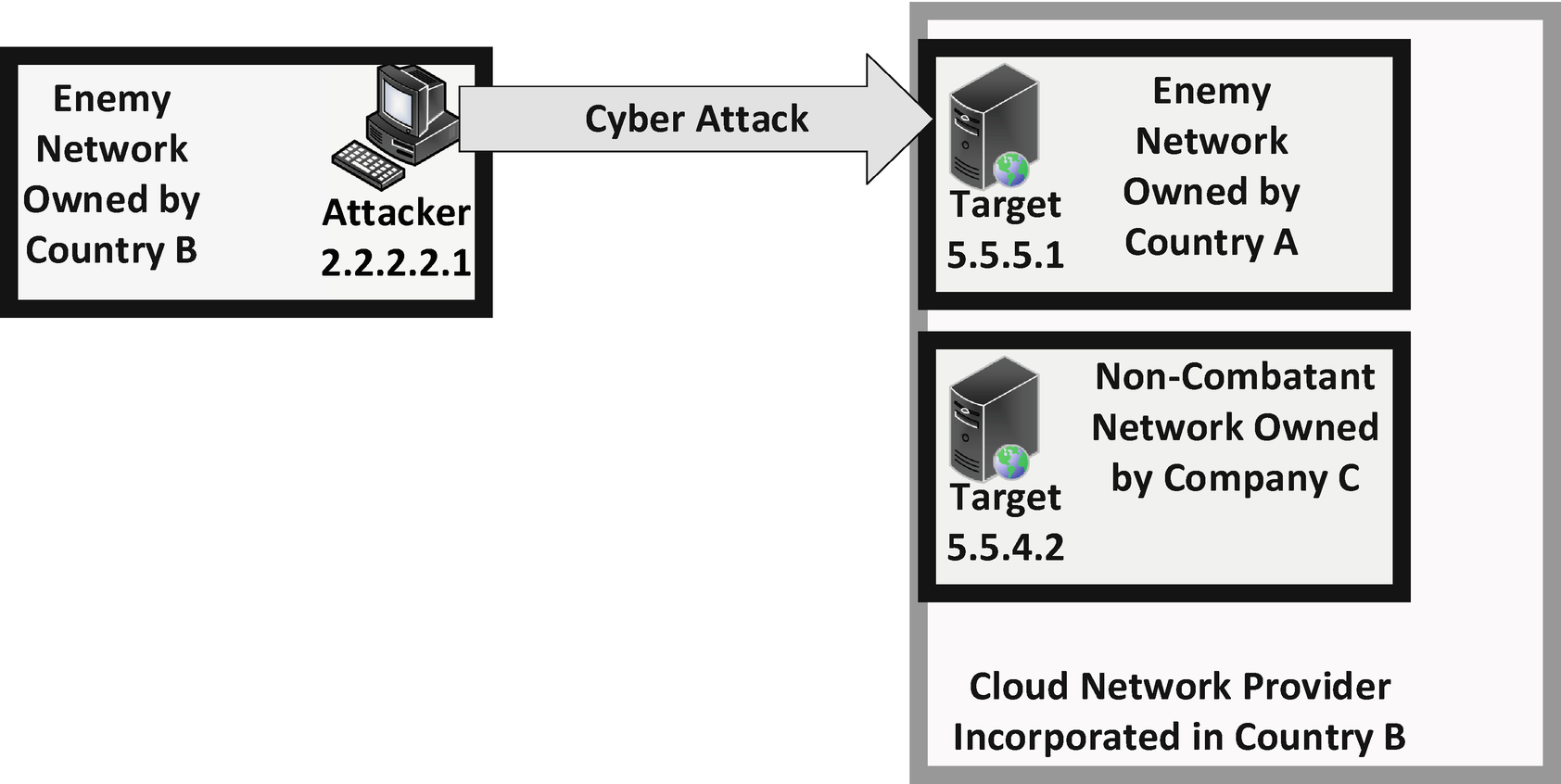
Intended Target

Unintended Target
Due to the ease with which a target system can appear differently on a network or the internet, target fidelity must be strongly considered and constantly re-evaluated in the target determination process. This is less so the case when an attack tool is installed on the intended target system is simply waiting for the command to execute. In this situation the attack tool may check at certain intervals for an execution command and act only when it is received. In any case the volatility of cyber domain targets specifically must bare increased scrutiny than targets engaged in a cyber-physical nature or via conventional warfare.
Rules of Engagement
The rules of engagement (ROE) for any armed conflict (even one where those arms are exclusively cyber weapons) are largely and generally defined by the national legal authorities of the participating combatants as well as international law and convention as we discussed at the beginning of this book. It is important when conducting cyber warfare to have cyber-specific ROEs pertaining to the carrying out of a cyber-attack mission. At a high level, the ROEs will dictate the permitted methodologies for engaging the chosen target, what is required for the attack against the target to be successful, at what point an attack must be aborted, and when it is considered a failure.
Method
In the ROE the method of attack is laid out. This covers how the attack is intended to be executed against the target system. The role of a ROE differs from other warfighting activities such as troop patrols or naval engagements. In those activities ROEs must also outline how escalation of force is established and executed. As we discussed, cyber warfare does not present return fire or active engagement situations between friendly and enemy forces. Instead the ROE should be strictly defined such that the perpetrator of the cyber-attack can perform the Title 10 activity to deliver the strategically identified target and effect. The ROE also ensures that the allowed actions, if followed correctly, result in a legal and moral act of war. Since the cyber realm shrouds warfighting actions to the point that their intent and actions are easily misinterpreted, there is no room for improper execution of cyber-attack effects.
Success
An ROE should also outline what mission success is. If the mission is to deploy a cyber-attack tool to targets, those conducting that mission need to know when they can stop. This is one way in the cyber domain the ROE limits excessive use of force. It may seem silly in a warfighting domain where bullets and mortars aren’t flying around, but it is still extremely important. The strategic decisions that go into deciding on targets and the end effects that are chosen for them are often very complex and situational. Altering the outcome of that mission by an overzealous use of cyber force against enemy systems could impact the outcome to the enemy of the targeted systems suffering the intended attack. Imagine a cyber-attack mission was to cripple 50% of a certain type of systems in an enemy network to get them to react a certain way. If the attack effect is deployed instead to 75% of those systems, the resulting impact to the enemy may dictate they react in a way different than if only half their systems were crippled. If the strategic goal of the mission was not met because an extra 25% of systems were affected, it would not only be an unplanned over-use of force but would negatively impact the strategic efforts that led to the use of cyber-attack effects in the first place.
Abort
Just as a definition of success limits the use of force in cyber warfare to what was intended by strategic decision makers, defining when to abort a mission is just as important. Abort decisions mainly revolve around two issues, a loss of target fidelity and intended attack effect consequences. Loss of target fidelity is essentially what we discussed earlier in this chapter. The decision to abort based on a loss of fidelity prevents the targeting of unintended or potentially innocent systems. If the targeting information leads the attacker to a system which no longer appears to be as it was when the attack was strategically decided, it should be aborted. This avoids negative impact to warfighting strategic goals as well as prevents violations of international convention and national authorities by preventing Title 10 activities from being conducted against improper targets such as non-combatants.
The second aspect involved in cyber-attack mission abort scenarios is any unintended consequences of attack actions. This could be a situation where cyber-attack effects are having unexpected impacts to systems. Imagine 100 enemy systems were potential targets and the mission was to execute the cyber-attack against 50% of them. After the first five attempts, the attack effect is not occurring or perhaps is causing a different effect than was strategically decided as appropriate. This could be because a patch came out for the operating system or other software on the targets which made the attack effect behave in previously unknowable ways. This is certainly a good point to abort an attack mission. There is also the impact attack effects can have on other friendly activities within the cyber domain such as intelligence gathering or battlefield preparations for other missions. Cyber-attacks are likely planned well in advance with careful consideration to how the attack effect will impact things like cyber intelligence gathering activities against the enemy. If the attack effect started behaving unexpectedly for whatever reason, the mission must cease to avoid unintended consequences to other cyber domain activities.
Failure
Though an abort of a cyber mission certainly results in a failure of that mission, there are other reasons that the failure of a mission is decided. Failure of a cyber mission is a result of the cyber-attack effect not being able to achieve the strategic goal within the constraints outlined within the scope of the attack or ROE. For example, let’s say that of 100 potential target systems, 50% need to be affected by the cyber-attack within a window of a week. For any number of reasons that may not be possible and at the 1-week mark if 50% have not been exploited, the mission needs to be labeled a failure and a reconvening of the strategic target process conducted. There are any number of mission constraints that if not met could constitute a failure, and in all cases, they are part of what limits cyber-attack effects to appropriate use.
Summary
In this chapter we covered the targeting of enemy resources by cyber-attack effects. We used historical warfighting examples as an instructive analogy for how tactical and strategic decision-making processes are involved in target and effect choices. The reader should walk away with the understanding that actively engaged cyber forces returning fire at each other is an essentially ludicrous and unrealistic scenario in cyber warfare. We then talked about what leads to the decision to use cyber weapons, how to assess their effectiveness with BDAs, as well as how target fidelity and ROEs constrain the warfighter in missions within the cyber domain.
