The microprocessor has a set of internal memory scratchpads called registers. These are divided into categories and sub-functions. For 32-bit designs, the general-purpose registers, or rather multipurpose registers, (E is for extended) are EAX, EBX, ECX, EDX, EBP, ESI, EDI, and ESP. Their 16-bit counterparts are AX, BX, CX, DX, BP, SI, DI, and SP
Four of them have the following 8-bit subdivisions, where H means High and L means Low:
- AX = AH,AL
- BX = BH,BL
- CX = CH,CL
- DX = DH,DL
For 64-bit programming, the general-purpose registers are RAX, RBX, RCX, RDX, RBP, RSI, RDI, and RSP:
- RAX (addressable as EAX/AX/AH/AL) plays the standard role of an accumulator. It is also used as the placeholder for the return value of a function call. All registers of this set are addressable in a 32/16/8-bit size as well.
- RBX plays the standard role of base indexing during memory access.
- RCX is normally used as a counter.
- RDX is normally used for data operations during division and data type extensions using EAX during multiplication in tandem.
- RBP is normally used as a base pointer.
- RDI is used as the destination index.
- RSI is used as the source index.
- RSP is the stack pointer.
There are 8 more general-purpose registers that can be used anyway: R8, R9, R10, R11, R12, R13, R14, and R15.
The bits 8–15 are not addressable for this set.
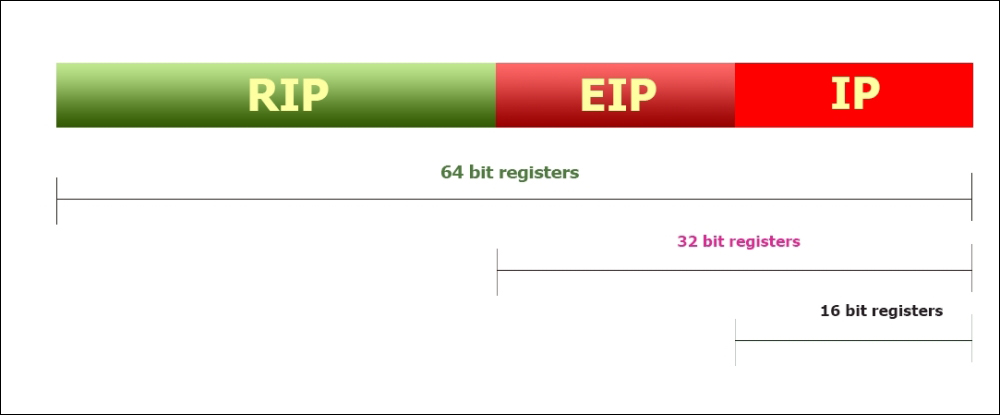
RIP, EIP, and IP are the 64-, 32-, and 16-bit addressed instruction pointer registers, also called the program counters. These keep track of the address of the next instruction to be executed.
The segment registers are CS, DS, ES, SS, FS, and GS.
While segmented mode programming has deprecated since Windows took over and DOS became obsolete, these registers are there for backward compatibility. These segments are now explicitly maintained by the Windows operating system and the programmer has no need to access these parts manually, apart from a few exceptions:
- CS stands for Code Segment
- DS stands for Data Segment
- ES stands for Extra Segment
- SS stands for Stack Segment
- FS is a general-purpose segment register that has a special purpose in Windows
FS is used to access the Process Environment Block (PEB), which is a user mode process memory data structure that is abstracted from the EPROCESS kernel data structure. These data structures are like databases and information gold mines that maintain the various details pertaining to a process that is loaded by the Windows loader. fs:[0] contains the start of the Structured Exception Handling (SEH)-linked list data structure. fs:[18] points to the TEB or the Thread Environment Block. fs:[30] points to the PEB. More will be discussed in the chapters ahead as these are completely related to Windows internals.
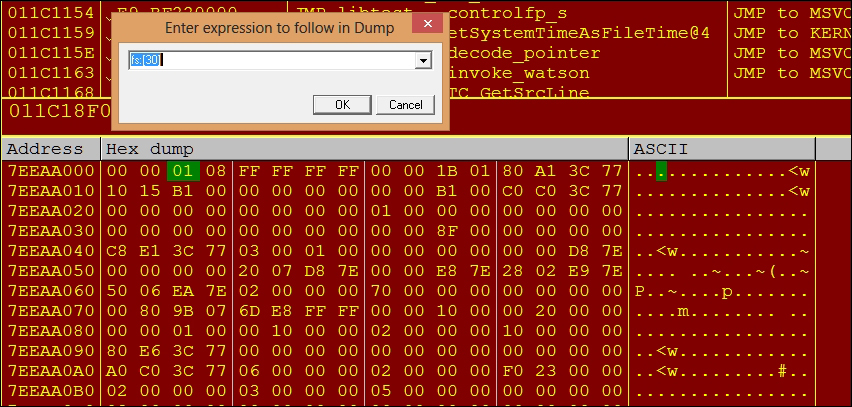
To take a quick view while debugging your applications, you might be interested to see the PEB inside your debugger. Without going into Windbg (the Microsoft Kernel debugger) just yet, a simple way to see the contents is to use OllyDbg and type fs:[30] after pressing Ctrl + G in the memory window. You will reach an address that typically starts with 0x7X XX XX XX. There is a field called PEB.BeingDebugged, which the IsDebuggerPresent() Win32 API checks for at offset 2 from the index base of 0 of the PEB. There are other comparable fields such as NtGlobalFlag at offset 0x68, which can be used by packers and malware as an anti-debug trick. You can see in the screenshot that the field value is set to 0x01, which means that the process can be aware that it is being debugged if it queries this field. Of course, this is a very basic technique to program and to overcome and is a feature of Windows by default.

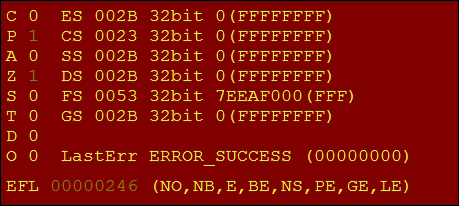
The EFLAGS register is in the OllyDbg register pane. The cumulative hexadecimal value of the EFLAGS register binary pattern is also given as 0x246.
The RFLAGS, EFLAGS, and FLAGS registers are the 64-, 32-, and 16-bit addressed status registers. Various important flags used in string manipulation instructions and conditional construct decision making use these register bit fields. The Zero flag, Direction flag, Overflow flag, Sign flag, Trap flag, and Carry flag are the most used in day-to-day programming.
The following exhibit is a schematic of the EFLAGS register in full detail with the most important ones for regular malware analysis.

The carry flag is set post addition or if borrow occurs post subtraction. It is also used to provide an alert of error conditions using overflow and carry-in versus carry-out integrity checks that mimic the XOR operation on the carry patterns.
The parity flag is set to 1 for an even number of bits in a number. It is used primarily for serial interfaces in legacy applications.
For the zero flag, if the result of an arithmetic or logic operation is zero, the flag is set to 1; if not, it is set to 0.
The direction flag is mostly used for string operations wherein the source and destination registers are incremented if the flag is set to 0. If it is set to 1, the direction is reversed.
The overflow flag is used to indicate overflow for signed arithmetic. Unsigned arithmetic operations do not make use of the overflow flag.
The trap flag is used for hardware debugging support and debugging registers provided on the microprocessor. This is used in single-stepping, and even breakpoint management internally, as the debugger has to keep track of when a breakpoint is hit and then insert the 0xCC opcode using Win32 APIs such as ReadProcessMemory() and WriteProcessMemory(). This is a TYPE 1 interrupt.
An interrupt can be described as a hardware- or software-specific signal—either derived from external hardware (an asynchronous event), a software-specific instruction (traps), or an internal event (divide by zero, software breakpoint, a single step trap, and so on). The internal event can also be an exception (a condition that needs to be handled by the OS or the application generating the exception). The exception, if correctable, is a fault (for example, a page fault generated on paged-out memory pages). Traps and faults differ in where execution resumes, as in the case of faults, the instruction is re-executed so that the second time around, the fault does not occur, whereas in traps, the next instruction from the trigger instruction is where the execution resumes. Exception handlers are the mechanism and provision by which the OS deals with such conditions.
Since we are dealing mainly with protected-mode CPU operation, the IDT (which stands for Interrupt Descriptor Table), is a CPU data structure constructed during the booting phase, which consists of 256 entries of 8 bytes each that map to individual interrupt routines. The INT instruction takes a numeric operand from 0x00 to 0xFF. INT 3 and INT 1(0xF1) are the only single opcode interrupt instructions with the others being 2 bytes long (0xCD 0xXX). You could use the 0xCD 0x3 opcode for INT 3, as well as substitute the interrupt number after 0xCD to get a 2-byte representation for each of the interrupts.
The resume flag is used to resume the execution during a debugging session.
Memory addressing is a more important feature to understand at this stage as instructions and minutiae can be studied from the disassembly of a program or by examining the assembly code inside a debugger.
Much of memory addressing and other details will be covered in the chapters ahead, but here are three important points to remember when writing assembly programs:
- Memory-to-memory data transfer is not permitted and can only be done via a register.
- An immediate value is a value encoded in the opcode sequence itself.
- Contiguous and conjugate data types such as arrays and structs are addressed using an SIB (which stands for Scale, Index, Base) scheme, as in Base + Scale * Index. Displacement can also be a factor, as in Base + Scale * Index + Displacement.
