
We’ll Cover
Since their introduction, wireless technologies have quickly reached ubiquity in both the commercial and residential space. One of the primary benefits of using wireless technologies over traditional wired technologies is their ease of use. This ease of use, as with many other technologies, comes with serious security concerns.
Based on some media reports, you might think that wireless technologies are riddled with security holes that are almost impossible to plug. There have been reports of “hackers” driving around town, laptops in hand and large antennas sticking from their cars, who are able to penetrate any wireless network with the click of a button. Although there is some truth to these reports, most of the time they are chock full of sensationalism. In this book, you’ll learn the technical details of wireless vulnerabilities as well as how to actually exploit them. I’ll also present real-world solutions and mitigating controls to minimize these security risks.
If you are tasked with managing the security of your company’s existing wireless network or with evaluating the risks associated with implementing a new wireless network, you will find in this book the resources necessary to make sound decisions in managing the risks associated with wireless technologies. Although this book is geared toward the IT professional who wishes to get up to speed quickly on securing his wireless network, if you have interest in current wireless security threats, how to exploit them, and how to defend against them, you will likewise find this book interesting and enlightening. The foundation for mitigating security risks is always a sound education. Your education begins now.
What You Will Learn
In this book, you will not find a mind-melting array of technical details for implementing wireless networks, you will also not find a review of networking in general. You are expected to have a baseline understanding of the configuration and implementation of wireless networks. For an introduction to wireless networking, see Bruce Hallberg’s book Networking: A Beginner’s Guide, Fifth Edition (McGraw-Hill, 2009).
You will, however, find the information you need to quickly get up to speed on the security issues and mitigating defenses for wireless technologies. You will also find easy-to-follow real-world examples of attacks against wireless technologies and examples of the applicable mitigating defenses. In addition, you will find real-world solutions to common objectives for wireless networks. Whether you need a refresher in securing wireless networks or want to add a new skill set to help advance your career, you will find the information easy to digest and, above all, relevant to the real world.
Security 101: The 11 Security Principles
Despite your familiarity with security fundamentals, a quick review is essential, if for no other reason than to ensure we are speaking the same language. Take your time in this section and make sure you understand all the security principles before moving on.
Following are the 11 principles you will find relevant to any security process you participate in. You will find most of these principles relevant to any security discussion, regardless of the technology, whether it’s wireless networking, Bluetooth, network security, or even physical and nontechnical security practices.
1. Security versus convenience.
2. It is impossible to eliminate all risks.
3. Rules of risk calculation and mitigating controls.
4. Not all risks must be mitigated.
5. Security is not just keeping the bad guys out.
6. ROI doesn’t work for security.
7. Defense In Depth.
8. Least Privilege.
9. CIA triad.
10. Deterrents, prevention, detection.
11. Prevention fails.
Principle 1: Security vs. Convenience
Additional security is typically accompanied by additional inconvenience. There is much debate on this topic, but at a very basic level you can always add more security by making things more inconvenient. We won’t dive too deeply into this, but you should understand the basic concept. A simple example will help clarify.
Suppose you have some personal papers that you lock in a small safe. To make it more secure, you lock that safe in a larger safe. Now whenever you wish to access these papers, you have the added inconvenience of needing to open two safes in addition to having to remember two separate combinations.
However, a paradox manifests itself in the real world, as illustrated in Figure 1-1, which shows what I like to call the security convenience bell curve. Typically, as you increase the inconvenience factor, you also increase security, but there comes a point when this inconvenience has an adverse effect on security.
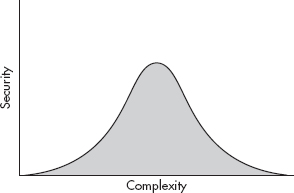
Figure 1-1 Security convenience bell curve
An example of the security convenience bell curve would be a company’s “password change frequency” policy. At first, the company’s policy requires users to change their passwords every six months. In an attempt to make the company even more secure, the policy is modified so that users must change their password every three months. However, after a few times of changing their passwords, users find it difficult to remember them and start writing them on sticky notes that are then stuck to their monitors or under their keyboards. This is obviously not a good place for confidential data and ultimately makes the business less secure.
Principle 2: It Is Impossible to Eliminate All Risks
First, let’s start with an accurate definition of risk. Per Dictionary.com, risk is the “exposure to the chance of injury or loss” or “a hazard or dangerous chance.”
That’s relatively straightforward, so what’s all the confusion about? The confusion comes from the fact that many people think that for a given security issue, there is a “fix” that completely eliminates any risk from that issue. You must understand that it is, without a doubt, 100 percent impossible to eliminate all risk from any technology, system, or even situation. For every mitigating control there is a discrete level of risk, no matter how minute. Risk is inherent in everything we do, in every choice we make, every single day. The idea of risk versus return on investment (ROI) has been intimately involved in the decision-making process of business owners for centuries; this same knowledge can be applied to our latest technologies in the security realm.
This is best understood by looking at an example. As kids we were told to look both ways before crossing the street, so let’s look at the risks associated with crossing the street.

Now, if you start glancing up at the sky every time you leave your house to look out for falling airplanes, your friends might look at you a little funny—and rightly so. This is simply to prove the point that you cannot eliminate 100 percent of all risks from any given situation, no matter how unlikely it is that a particular threat might occur. Now you may be thinking that to eliminate all these risks, you could simply stay home and never cross any street. Well, in this case you run the risk of living an unfulfilling or unhealthy life, which exposes you to health risks. Again, this might seem like a strange and extreme example, but it is essential for you to understand that there are inherent risks in every choice we make.
It should also be noted that the purpose of analyzing risk is not always to choose the path with the least risk. Rather, it is to make an informed decision that best suits the person or organization. More on this later.
Principle 3: Rules of Risk Calculation and Mitigating Controls
To appropriately compare different risks, we need a consistent method for calculating risk. Although a multitude of different risk equations are available, the most basic equation is as follows:
Risk = Consequence × Probability
Let’s look at each component of this equation individually and then apply the equation to our previous examples of falling airplanes and distracted drivers.
Quantitative costs are anything you can put a hard number to. For example, in quantitative terms, the cost to replace a $100 phone is—you guessed it—$100.
LINGO
Consequence is the impact felt if a particular vulnerability is exploited. This can be expressed in both hard figures (quantitative, such as “cost”) or more ethereal terms (qualitative, such as “suffering”).
Qualitative costs are much more subjective and harder to define and may be drastically different between persons or organizations. The easiest way to understand qualitative costs is to think of the emotional costs of an incident. For example, if you have a special gift that was given to you, it may be worth only a few dollars if you were to try and sell it, but it might cause a lot of emotional pain if it were lost. Thus, the qualitative cost of replacing it might be very high. This is an extremely simplistic way to look at qualitative cost, but it should help you grasp the concept quickly.
Here are few examples of quantitative impacts:
LINGO
Probability is the likelihood that a particular vulnerability will be exploited. Obviously, in certain circumstances, probability is much easier to define, but in general the answer should be relatively straightforward. For certain calculations, you can look at historic data to come up with a good answer for probability.
For example, let’s say that in Kansas, in the previous 10 years there have been 60 tornadoes. Sixty tornadoes over 10 years would be roughly six tornadoes a year. Therefore, a good probability exists that Kansas will experience roughly six tornadoes next year.
And here are a few examples of qualitative impacts:
The preceding calculation will result in the associated risk level. The actual label for the risk level could be a number or a phrase from a corresponding risk matrix, like the one shown in Figure 1-2.
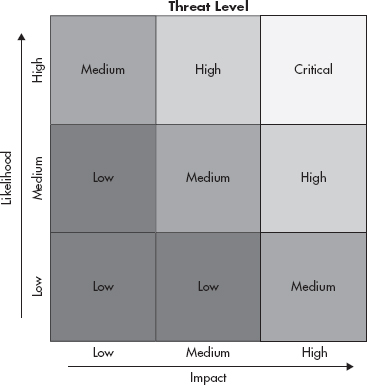
Figure 1-2 Risk matrix
To use the risk matrix in Figure 1-2 you simply identify the likelihood and impact of a potential threat. For example, the likelihood of someone stealing a server might be low and the impact might be low (if you encrypt your hard drives). You would then plot this threat as existing in the lower left quadrant and have an overall threat of low. You could then compare this to other threats and deal with them as your business dictates.
The actual naming convention or the numbers used in the calculation of each component can be essentially arbitrary as long as the same system is used for each calculation. For example, it doesn’t matter if you calculate probability in months, years, or decades, as long as you use the same period for each calculation.
If you’re developing a security program for your own company, feel free to start from scratch and come up with a numeric or naming system that fits your business. The key here is consistency: As long as you’re identifying risk levels using a common system, you’ll be able to identify areas that you wish to mitigate first. You can find plenty of examples to choose from on the Internet, so look for one that fits your business. The Department of Homeland Security provides many good resources at www.dhs.gov.
Now let’s use our previous examples to calculate the risk level associated with each. We’ll define an arbitrary system for each component first. Impact will be a number between 1 and 10, with 1 being the lowest impact and 10 being the highest. Probability will be a yearly probability based on statistical information.
| Vulnerability | Falling Airplane |
| Impact | 10 (Death) |
| Probability | 0.000001 (one out of every 1,000,000 people dies from a falling airplane every year in America) |
| Risk Level | 0.00001 (10 ×0.000001) |
| Vulnerability | Distracted Driver |
| Impact | 10 (Death) |
| Probability | 0.001 (one out of every 1,000 people die from a “distracted” driver every year) |
| Risk Level | 0.01 |
As you can see, the risk level from distracted drivers is much greater than that of falling airplanes. Therefore, you might want to protect yourself from distracted drivers before worrying about falling airplanes.
The difficult part here is that different people might define different probabilities or different vulnerability levels to the same threat. For example, the probability of getting struck by a car while crossing the street is much higher for someone living in New York City than it is for someone living in a rural community in Kansas.
 Note
Note
Various organizations and industries have slightly different risk formulas—whether it’s just different naming conventions for each component or a different number of components. This should not be seen as a bad thing; certain industries and businesses can benefit from having more complex or more simplistic formulas. However, understanding the current example will give you a strong baseline from which you can approach other formulas.
Into Action
Wondering how all this applies to wireless networking? Let’s take a look at a real-world example.
Let’s assume you have 100 wireless access points deployed in your organization with 1,000 wireless users. A new exploit is released that affects the version of firmware currently running on all your access points. The exploit allows an authenticated user to reboot the wireless access point. We’ll calculate the risk level using a High/Medium/Low scheme used in Figure 1-2. (Remember that the risk calculation is Risk = Consequence × Probability.)
Thus, the risk calculation would be Low × Low = Low Risk.
If it costs you four man-hours per access point to apply a patch for this vulnerability, then it might not be worth the cost to mitigate this risk. Instead, it might be more cost effective to live with this risk and use those 400-man hours elsewhere.
Principle 4: Not All Risks Must Be Mitigated
Not all security risks must be mitigated. Yes, I know, as a fellow security fanatic it sounds counter to what we believe. If there’s a security hole, plug it! But in reality, there are plenty of risks that we don’t mitigate already. It’s relevant to bring these calculations to a conscious level. You’ve already read an obvious example—the risk of falling planes. Now let’s look at the cost to mitigate the risk of falling airplanes.
You could construct a house for a few million dollars that could withstand the impact from a falling plane, but when you consider the extremely remote possibility of a falling plane striking your house, you’ll probably come to the conclusion that it’s not worth the cost. Yes, this is just another extreme example, so let’s look at a very simple business example.
A new regulation has come out that affects your business. If you fail to comply with the regulation, you will be fined $5,000 every year. You’ve hired an external firm to assess the cost to make you compliant with the regulation and they think at a bare minimum it will cost you $2,000,000. It’s not hard to see here that it makes more business sense to just pay the fine and not try to make your business compliant.
Four main approaches can be taken to manage risk: You can accept the risk, avoid the risk, transfer the risk, or mitigate the risk. In the two previous examples, we’ve chosen to accept the risk associated with each scenario. Now let’s look at our other options for dealing with the risk of the new regulation.
| Avoid | Let’s imagine that the regulation only applies to companies doing business in Texas. If your company can prosper without doing business in Texas, then you’ve just avoided the risk. |
| Transfer | Maybe you can transfer the risk to a third party. If you could outsource the part of your business that’s covered by the regulation and let the third party worry about it, then you’d have transferred the risk. |
| Mitigate | If instead of avoiding, transferring, or accepting the risk, you might decide to implement controls to adhere to the regulation. Thus, you would have effectively mitigated the risk of a fine due to the regulation. |
Principle 5: Security Is Not Just Keeping the Bad Guys Out
Security is not just about keeping the bad guys out. An extremely common misconception is that the primary concern for security administrators is keeping malicious outsiders from accessing critical systems. Of course, this is a vital component to a comprehensive security plan; however, it is far from being the only concern. The problem with adopting a “keep the bad guys out” mentality is the development of the so-called “candy” network, with a hard outer shell and a delicious gooey center. We’ll address this topic in more detail later.
You may hear many reports stating that the majority of security breaches come from internal personnel. Now, although I agree with this statement in theory, a little speculation might help to clarify exactly what is meant by it. Here are the key points:
Principle 6: ROI Doesn’t Work for Security
The traditional calculation of return on investment (ROI) doesn’t work for expenditures for security. At a very basic level, the calculation for return on investment determines how much profit will be produced if you invest X amount of money (or resources) into something. Using the ROI model, you can compare multiple investments and determine which is appropriate. Therefore, spending money on security cannot be justified with ROI, because it’s not a revenue-generating business process. Instead, you’re spending money (and resources) to protect a greater amount of money (or resources) from being lost. Also keep in mind the qualitative risks, such as reputation, image, and the long-term effects of damage to these.
Principle 7: Defense In Depth
You can improve security via Defense In Depth. True security does not come from one risk-mitigating control; instead, it comes from the implementation of many synergistic solutions. One of the most basic examples of this is one we’re all very familiar with: a bank. Banks don’t just rely on a big vault to keep all their assets safe; instead, they also employ armed security guards, cameras, door locks, fences, educated employees, alarm systems, and so on. This is the essence of Defense In Depth and the foundation for a more secure environment.
Principle 8: Least Privilege
You can improve security with Least Privilege. One of the most important and often overlooked methods for configuring security devices and implementing policies is that of Least Privilege. Least Privilege means giving users the bare minimum rights they need to perform their duties and then giving them additional privileges as necessary. The opposite way (the most common) is to give the most amount of privileges and then remove “dangerous” privileges one by one. This can also be referred to as blacklisting versus whitelisting.
Principle 9: CIA Triad
The CIA Triad is an industry-accepted model for securing systems (specifically, but not exclusively, data). The acronym stands for Confidentiality, Integrity, Availability. Each of these is vital to ensuring the security of data:
Principle 10: Prevention, Detection, Deterrents
Within the security realm, most mitigating security controls fall into at least one of the following three major categories. Going along with the Defense In Depth strategy, it is wise to implement multiple types of security controls whenever possible.
Many security controls fall into multiple categories. For example, cameras both detect and potentially deter criminal activity. An electric fence could both prevent someone from walking onto your property as well as deter anyone from trying to scale it.
Principle 11: Prevention Fails
Another common theme in the security realm is the fact that (essentially) every prevention measure will eventually fail (or is capable of failing). This doesn’t mean that every single implementation of a preventative security measure will be bypassed by someone with malicious intent, but only that it is possible. Another way to look at this is that, in the security industry, the attackers and the defenders are always “one upping” each other. Consider the following examples:
The intruders scale the fence and come into my house.
The intruders toss a large mattress on top of the razor wire and scale over the fence.
The intruders use tranquilizers to knock my dogs out.
Again, these examples are a bit comical, but they should prove the point that you can’t rely entirely on prevention to secure your environment. Instead, you need a strong Defense In Depth strategy that uses deterrent techniques and methods of detection well.
Definition of Hacker
The proper definition of the word hacker has been the source of much heated debate. I choose to use the word to portray both those with and without malicious intent. For me, the quintessential characteristic of a hacker is a tenacious and creative problem-solving ability. Whether the person is malicious or a saint is irrelevant.
 Note
Note
Want to take your career to the next level? Start evaluating security expenditures with the knowledge you’ve just obtained. C-level executives don’t think in terms of secure versus insecure; they think in terms of risk mitigation and risk management (that is, is this security technology going to prevent me from losing more money than it costs?). It’s your job to be able to turn packet dumps and firewall configurations into terms of risk management.
So in a business context you have two calculations to consider for risk:
For end users, there’s another component to the calculation that is slightly harder to define because emotion is involved. For example, some people live in very safe neighborhoods but still purchase guns for their houses. They might not need a gun to actually be secure, but because emotionally it makes them feel more secure they are more apt to make unnecessary expenditures.
Wireless Networking Basics
A brief introduction to the various wireless technologies is necessary to ensure we are speaking the same language. If you feel comfortable with these topics, feel free to skip ahead to the next chapter. In this section, we will look at a few definitions that represent a vital, foundational understanding of wireless technologies. I won’t be providing any information for actually configuring devices; however, the information provided should be universal across devices.
802.11a/b/g/n
802.11 is the name for the working group from the Institute of Electrical and Electronic Engineers (IEEE) for wireless local area networks. IEEE working groups are essentially committees of experts who define standards of operation for specific technologies so that manufacturers can build standards that can interoperate. Nowadays, there’s a virtual alphabet soup of wireless technologies. We won’t focus too much on the differences here; just understand that with each new generation generally you have an increase in bandwidth and/or security features.
The IEEE identifies each standard with a letter. For example, 802.11a is different from 802.11b. Although there are some commonalities between technologies, there are also differences, as well as advantages and disadvantages to choosing one technology over the other. For the most part, the differences between standards are in speed, modulation techniques, and whether they are backward compatible and a security technique that works for one will work for the others. For example, even though 802.11g was developed after 802.11b, it still supports WEP to ensure backward compatibility.
However, keep in mind that some specific tools will only work for a specific standard. For example, if a program is written specifically to work with 802.11b, it might not work for 802.11a or even 802.11g. Because the underlying protocols for how data is handled are the same across standards, the attacks and defense in theory will be identical.
The 802.11 standards prescribe which frequencies these technologies use as well as the channels available to them. For example, the 802.11b standard operates in the 2.4 GHz frequency and, in the United States, has 11 unique channels available for use (labeled Channels 1 through 11). These unique channels assist in allowing networks to be physically close and not interfere with each other. However, depending on the country, the channels available for use may be different. For example, in Japan the channels are actually 1 through 14. This has security implications because an access point operating on Channel 14 may go completely unnoticed in the U.S. More on this later.
The following is a simple cheat sheet of the 802.11 standards.
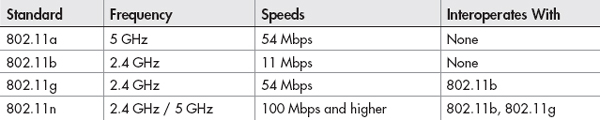
In Actual Practice
Some of the components of wireless local area networks (LANs) have been reused in other technologies. Most of the security issues that apply to wireless LANs are directly applicable to other technologies. For example, eavesdropping attacks are a concern for any wireless technology and may be mitigated differently based on the technology. For instance, recent attacks have made it possible to intercept conversations between a Bluetooth headset and a cell phone.
Various wireless LAN technologies are fairly similar, which is understandable considering that each new generation of standard is typically backward compatible with its predecessor. Technologies that are unique to a specific generation of wireless technologies will be noted as such.
Wireless networks can operate in one of two basic modes: Infrastructure and Ad-Hoc. In Infrastructure mode, clients connect to an access point. In Ad-Hoc mode, no access point is involved; instead, clients communicate with each other (or end nodes). We’ll use the term end node because nowadays a client can be anything from a laptop to a cell phone to a printer with a built-in wireless network card.
In Actual Practice
It should be noted that operating in Ad-Hoc mode does not necessarily mean you do not have connectivity past any of the clients. For example, one of the clients could be configured to perform routing or Network Address Translation (NAT) and could be providing Internet access for other clients. This is an important point to keep in mind for security reasons, and we’ll touch on this again in Chapter 5.
Access Points
Access points are a vital component of any scalable wireless network. An access point essentially connects two dissimilar technologies, and a wireless access point represents the physical device that is the liaison between wireless communications and wired communications. It is worth noting that back-end communication does not necessarily have to be wired communication. For example, some cellular providers have started offering access points with built-in cellular network cards to connect to their cellular network. In this case, you would still connect to the access point but the access point itself would not need a wired network connection.
Access points have come a very long way since their introduction. Many new features (some existing and new) have been added to access points. For example, captive web portals have existed for a long time before wireless networks became popular but they’ve been implemented in many access points. We will not discuss every feature available, but definitely keep in mind that from a security perspective all this added functionality comes with its own inherent risks. For example, whereas you once could only configure an access point from a web interface or a limited command line, now you have an almost full-fledged command line with common network tools. Thus, tools such as Ping, Telnet, SSH, and Traceroute make an access point an even more appealing target for an attacker to leverage his position and infiltrate deeper into a network. Also keep in mind that with added complexity comes a greater chance to misconfigure an access point. More knowledge is required to securely configure an access point with more features. We’ll go over this in more detail in Chapter 6.
Autonomous vs. Controller Based
Originally, access points were configured one at a time; such access points are referred to as autonomous access points because they function as singular units. Obviously, for large-scale deployments this requires too much time. Management systems were first introduced to solve this problem, and now we have controller-based systems that make configuration even easier.
A management system would typically be installed on a server (or desktop) and would simply interact with existing management protocols, thus allowing administrators to automate some of the more mundane tasks. Existing management protocols include tools such as Telnet, SSH, and SNMP. An administrator could, for example, create a template profile with a specified SSID, encryption method, and authentication method and apply this template to an access point.
The management system would then telnet (or connect using another management protocol) to the access point and apply the configuration. This, of course, requires that first the administrator configure basic IP connectivity on the access point and enable Telnet. Therefore, a level of administrative burden is associated with adding new access points.
To make things even easier on administrators, we have a new generation of access points that are commonly referred to as lightweight access points. A few protocols deal with lightweight access points, mainly the Cisco proprietary LWAPP (Lightweight Access Point Protocol) and CAPWAP (Control And Provisioning of Wireless Access Points), which is a standard, interoperable protocol based on LWAPP. It is not necessary to understand the specifics of these protocols; they will be discussed in greater detail later.
Lightweight access points generally allow an administrator to perform 99 percent of the configuration ahead of time, thus greatly reducing the total administrative effort. An administrator can create a profile that completely configures an access point. When a new access point is added to the network, it “discovers” the controller and “automagically” downloads and applies the appropriate configuration. A myriad of different options are available for how the access point discovers the controller and how it downloads its configuration. We will be reviewing these options in Chapter 11. The important thing to note is that you don’t even need an IP address configured on your lightweight access points. You can literally take your shiny new lightweight access point out of the box, plug it into your network, and it will be configured automagically and provide wireless services within minutes.
Think about how beneficial this would be for large-scale deployments. However, although this is the latest and greatest technology for configuring wireless access points, it is not necessary for all new wireless deployments. You must still evaluate the return on investment. In many cases, just configuring (a few) access points by hand can be a much more cost-effective solution. We will evaluate the different options for using a controller-based system in a few test scenarios in later chapters.
SSID, BSSID, MAC Address
The SSID, BSSID and MAC address are all essential unique identifiers for a wireless network. The Service Set Identifier (SSID) is the human readable name associated with an 802.11 wireless network. It is often called the wireless “network name” and can be shared by multiple access points. The Basic Service Set Identifier (BSSID) uniquely identifies a specific access point and is in the same format as a MAC address; thus, most commonly, it is the MAC address of the access point. The Extended Service Set Identifier (ESSID) can essentially be thought of as a group of BSSIDs that share the same Layer 2 network and the same SSID.
Beacons and Broadcasts
Access points send out beacons, which are radio broadcasts that advertise the wireless settings for a specific BSSID. These settings typically contain the SSID, encryption method, and so on. Many access points have an option to disable the broadcast of the SSID. Enabling this option does not typically disable beacons but rather configures the access points to send a beacon with a blank SSID. However, this does not prevent an attacker from obtaining the SSID, which you will read about in Chapter 3.
Associating and Authenticating
Association and authentication are performed by clients when they want to join a wireless network. Associating to an access point means that your client and the access point have “agreed upon” which parameters to use to ensure proper communication. Things such as the channel and encryption method have been verified to be the same. Authentication is a way of verifying that you are authorized to connect to the network. There are multiple methods of authentication, and authentication happens prior to association. We will discuss the vulnerabilities with certain authentication mechanisms in Chapter 3 as well as look at examples of more secure options.
Encryption
Encryption is utilized just as it is in any other technology. It obscures the data so that only “authorized” people can view the actual data. You have many different choices for encrypting network data; some are new implementations created for wireless technologies, and others have been around for a while. In Chapters 3 and 4, we explore these encryption options as well as crack some of them.
We’ve Covered
In this chapter, we covered the foundational knowledge you should have to get the most from this book. We reviewed 11 different security principles that apply across many scenarios, not just wireless networking. We also covered the fundamental components for wireless communications, including the basics of wireless networking. We’ll refer to the topics introduced here in more detail in future chapters, but you can always refer to this chapter for a reference on the basics.
The 11 security principles
Wireless networking basic concepts
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
