One of the possible attacks that we would want to protect our model against is MITM attacks. A MITM attack occurs when an intruder tries to eavesdrop on a supposedly private communication to deploy a trained machine learning model.
Let's try to understand MITM attacks sequentially using an example scenario.
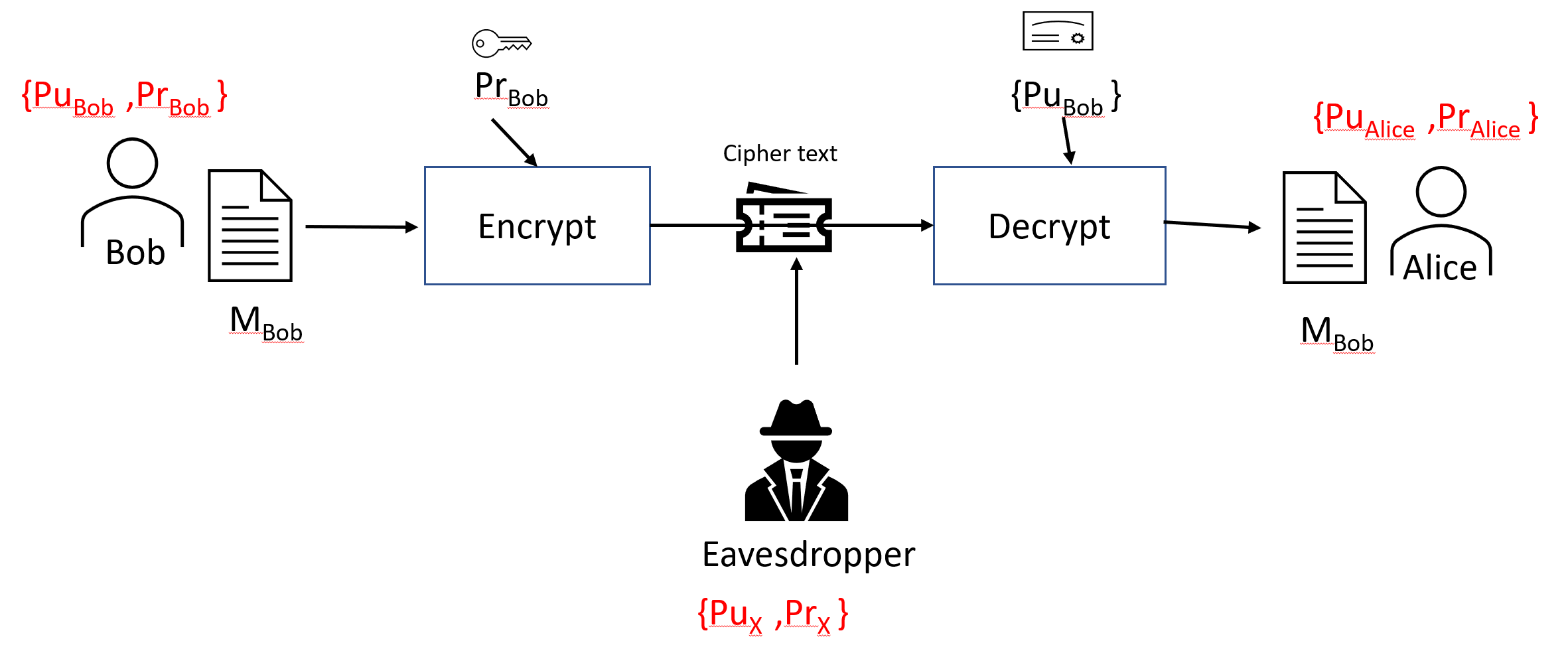
Let's assume that Bob and Alice want to exchange messages using PKI:
- Bob is using {PrBob, PuBob} and Alice is using {PrAlice, PuAlice}. Bob has created a message, MBob, and Alice has created a message, MAlice. They want to exchange these messages with each other in a secure way.
- Initially, they need to exchange their public keys to establish a secure connection with each other. This means that Bob uses PuAlice to encrypt MBob before sending the message to Alice.
- Let's assume that we have an eavesdropper, X, who is using {PrX, PuX}. The attacker is able to intercept the public key exchanges between Bob and Alice and replace them with its own public certificate.
- Bob sends MBob to Alice, encrypting it with PuX instead of PuAlice, wrongfully thinking that this is Alice's public certificate. Eavesdropper X intercepts the communication. It intercepts the MBob message and decrypts it using PrBob.
This MITM attack is shown in the following diagram:
Now, let's look at how we can prevent MITM attacks.
