A wireless LAN (WLAN) is typically viewed as access points (APs) that connect to the access layer of a LAN as a transparent bridge, allowing wireless clients to appear as though they are connected directly to the wired network while retaining the mobility that wireless networking provides.
The truth is that WLANs are complex and APs and clients must work in concert with one another to abstract the complexity of the 802.11 protocol. As such, a solid design and deployment plan is required to retain the easy-to-use interface to the clients.
This chapter introduces you to the specific design considerations for some of the most common WLAN deployment scenarios: retail, healthcare, branch office/telecommuter, education, public safety, and public access.
Luckily for most WLAN vendors, one market that relies on WLANs as a mission-critical application is the retail market. Next time you walk into your favorite home-improvement store, electronics store, or department store, look at the walls and ceiling. You're bound to find APs, or at the very least antennas mounted, to provide coverage for 802.11 client devices.
These types of business rely on client/server applications surrounding inventory control and supply-chain management. WLANs provide the employees the mobility they need in a store environment to quickly and efficiently check inventory with instantaneous updates to backend systems and databases, providing a huge cost savings in both timeliness and improved accuracy. The introduction of Voice over IP (VoIP)-enabled 802.11 clients has also been accepted by many companies as a replacement for proprietary narrowband, licensed, radio-frequency (RF) systems, 900 MHz systems, or two-way radios. These new VoIP handsets can provide functions over and above a typical voice handset by also providing two-way paging functionality and web-based application support. For example, an employee can clock in by simply logging into her VoIP handset and receive work assignments. Use of thin client interfaces on these data-capable VoIP handsets lets you deploy custom applications to streamline mundane or tedious operational tasks. One example includes interactive text-based messaging. For example, a store manager can sent a broadcast message to all active handsets to instruct one employee to do a particular task. All employees receive the message, and the one can acknowledge the message and proceed to complete the task.
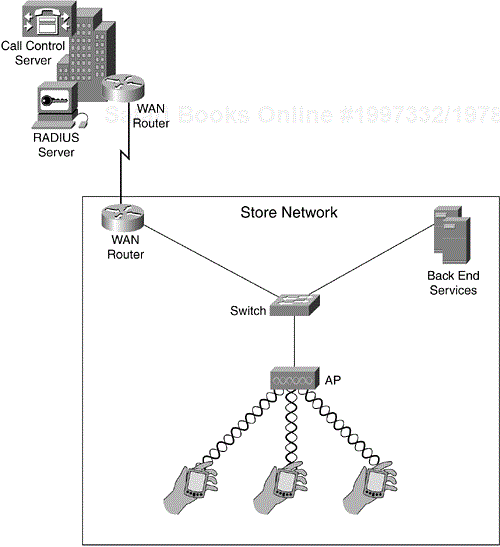
Retail stores have taken advantage of WLAN technology far prior to the ratification of 802.11 in 1997. Many companies were producing proprietary 2.4 GHz and 900 MHz wireless system in the 1990s and licensed narrowband systems in the 1980s, along with client devices such as barcode scanners. As you can imagine, most barcode-scanning applications have meager bandwidth requirements because the data stream is small and bursty in nature. For that reason, many of these early deployments were coverage-oriented in nature. Site surveys focused on minimizing the total number of APs required and providing maximum coverage. In a typical home-improvement warehouse, it is uncommon to see three to five access points cover the entire facility.
Today, the use of VoIP and a more diverse client base (including laptops, personal digital assistants [PDAs], and wireless printers) demands more capacity from the infrastructure. Newer deployments now consist of 10 to 20 APs just to provide the capacity and coverage for the insurgence of these converged applications.
Retail networks have many characteristics that distinguish them from other types of networks. Retail stores typically have the following:
Numerous stores (hundreds, sometimes thousands, of locations in different geographical locations)
Nonredundant, low bandwidth WAN connections back to a hub site or central site
Little or no information technology (IT) or networking staff on hand at the individual stores
Minimal IT infrastructure at the local stores
Figure 10-1 depicts a typical nonconverged retail store network.
The capacity and coverage issue is overcome with a more dense AP deployment; however, the preceding issues add new twists to how the network administrator designs and deploys a store network. A retail store typically has the following characteristics that a network manager needs to consider when designing a WLAN:
Primary client/server applications are housed locally in the store.
Converged applications (VoIP and security) are centralized at the hub or central site.
Management solutions can scale to support the large number of managed APs.
The store needs the ability to operate during outage conditions. Given that most WAN links are nonredundant, centralized backend databases would be useless to a store during a WAN outage. For this reason, the primary application servers are generally housed locally in the store.
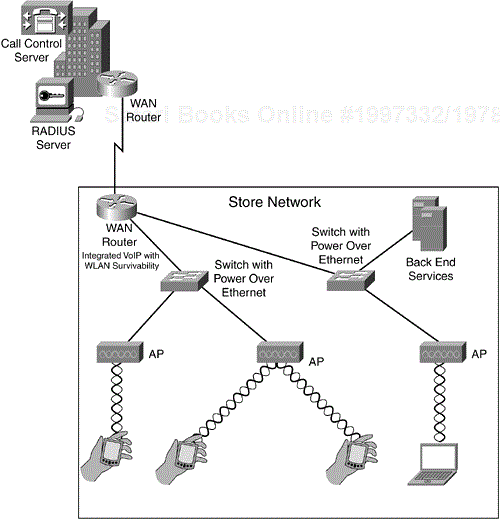
VoIP is generally a centrally managed application to make it cost effective. A WAN outage can impact VoIP signaling and operation. In response to this issue, many vendors offer survivability modes, where local-network infrastructure can detect the loss of central connectivity and assume a survivability mode. This mode allows an employee in a call to continue without noticing the outage (unless the call was across the WAN link). The same premise holds true for WLAN security. The emerging standards in the IEEE 802.11 task group I and Wi-Fi Protected Access (WPA) interoperability specification require the use of an authentication, authorization, and accounting (AAA) server for user-based authentication. RADIUS servers (the most common AAA server used for WLAN security) have limited management for decentralized deployments and face major challenges for administration and account synchronization. Most retail companies opt to centrally house this service to minimize these limitations. The downside to this approach is its vulnerability to WAN outages. If the WAN link or central AAA server becomes unavailable, wireless devices cannot authenticate and as a result are unable to access resources local to the store network. In such a situation, a wireless barcode scanner cannot access the inventory database located in the store because it cannot authenticate to the WLAN.
One solution for VoIP survivability in retail stores is Cisco Survivable Remote Site Telephony (SRST). SRST is typically implemented in branch-office routers, and the feature monitors VoIP signaling traffic back to the central call control server (the Cisco Call Manager). If the central server becomes unavailable due to WAN outage or server failure, the SRST device takes over call control so that in-store calls are possible.
Cisco also offers a similar solution for WLAN authentication survivability. Routers or switches running Cisco IOS Software with the IEEE 802.1X local authentication service can remain active and securely authenticate even when connectivity to the central AAA server is lost. These solutions provide maximum uptime for the WLAN and its applications while minimizing the impact and expense to the WAN. Figure 10-2 illustrates a retail store network with survivability functions incorporated.
Scaling network-management systems to adequately service large AP deployments is still a lingering issue for WLANs. Management tools that are widely available today are typically designed for wired networks. Large-scale retail deployments can range anywhere from hundreds to thousands of APs requiring the same element management of wired networks, including configuration and image management, reporting, and trending. These tools do not scale to meet the needs of most wireless deployments. As a result, network administrators are left to their own devices in designing creative and effective ways to manage their store networks. Many vendors are developing management platforms that rise to the occasion by providing the scalability and tools required to manage wireless networks. These tools have lacked the integration into wired management platforms necessary to allow a single point of management visibility into the ever-changing network. Retail customers have raised their voices and demanded that either tools be made available from their current vendors or they will switch vendors!
Wireless usage in healthcare has significantly increased with the proliferation of 802.11b devices and the erosion of price of 802.11b equipment. Healthcare environments see an immediate return on investment (ROI) with the use of WLANs, namely in the form of patient tracking, distribution of medication, claim collection for insurance companies, and increased doctor and nurse mobility (lending to faster patient response time and turn-around time).
Many companies are starting to deliver mobile applications on PDAs that allow doctors and nurses to process claims forms to insurance companies in a timely and, more importantly, accurate manner. This process reduces the number of rejected claims caused by human error and reduces the turn-around time for payment. Also, many healthcare information-systems vendors are starting to look at WLANs as an automation mechanism to deliver mobile applications.
Mobile healthcare applications exhibit the same characteristics as a retail store—from a packet perspective. That is, the traffic is low bandwidth and bursty. These deployments are usually coverage-oriented to reduce the number of APs, and it is common to see directional antennas to focus coverage of long hospital corridors, as opposed to use of the standard 2.2 dBi omnidirectional dipole antenna.
Many healthcare facilities with existing deployments are re-evaluating their coverage-oriented deployments to facilitate VoIP applications as well. Use of VoIP handsets allows healthcare staff to be reachable while they are mobile, again reducing patient response time and turn-around time. The coverage-oriented deployments that currently exist do not provide adequate capacity to facilitate VoIP over WLANs, so many deployments are being re-site–surveyed to facilitate VoIP as a primary application.
In the same vein as VoIP, location-based services are also gaining momentum in the healthcare market, although most of today's systems are non-802.11. Once these systems, which allow the pinpointing of a node to a 3 to 6 feet accuracy, can leverage 802.11 equipment, a new market of location aware applications will appear. These applications will track healthcare staff and patients, quickly locate equipment during an emergency, and display location-sensitive data when a staff member walks in proximity to a patient.
Many of the design considerations for enterprise campus deployments are covered in detail in Chapter 8, “Deploying Wireless LANs.” This section focuses on two other enterprise deployment types for WLANs: the branch office and the home telecommuter. Both of these deployment types are increasing in number and popularity and have specific considerations that are not captured by campus or large deployment guidelines.
As stated earlier, the economic crunch that hit the United States economy in late 2000 placed a financial barrier on enterprise spending. Any expenditure required significantly more justification than it did in years past. As WLAN technology has matured, and many of the key barriers to deployment (namely security) are addressed, enterprises are starting to embrace WLANs not so much for campus or headquarter deployments, but rather as a wired network replacement in small branch offices.
A large number of enterprises experience a significant amount of turnover in their branch offices. A major cost associated with this turnover has been the cost of Category 5 cabling for the data network. IT planners see a tremendous cost savings by leveraging WLANs in branch offices as a replacement for wired networks. 802.11 client devices are available for every platform, including laptops, PDAs, printers, and servers, and at the same time, 802.11 VoIP handsets are becoming more prolific. This availability gives an IT planner a great deal of flexibility for branch-office deployments. The WLAN is a truly converged network, allowing file and print services, voice, and Internet access, all at relatively low cost.
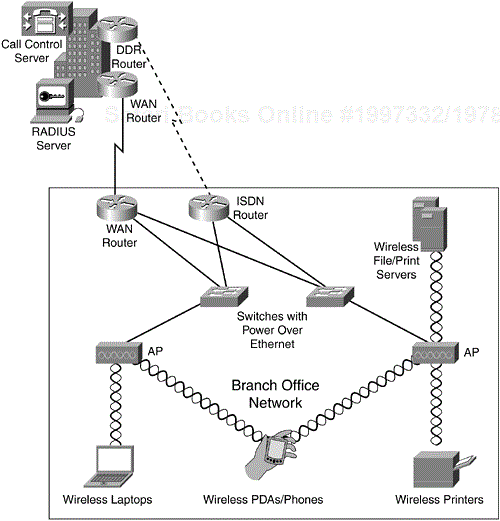
Enterprise branch offices are similar to retail store deployments in that a large number of branches or remote sites can connect via WAN links to a central site. Branch offices tend to have meager infrastructure requirements, as with retail stores, but they differ in a number of ways:
Redundant, high-bandwidth WAN connections back to hub site or central site
Some form of IT/networking staff local to the office
Some application back ends local to the site but a majority housed centrally
No mission-critical application that requires WLANs
Figure 10-3 depicts a WLAN-enabled branch office. Note the key differences between the branch office network and the retail store network: A redundancy WAN minimizes the requirement for local services (both for AAA servers for WLAN security and VoIP survivability), and almost every device is WLAN enabled. This setup is necessary to maximize the ROI of the WLAN. Remember that most enterprises do not have a mission-critical application that requires WLANs. WLANs in these environments provide value based on their cost reduction for cabling and portability.
This is a tremendous boon for the WLAN industry. WLAN technology is viral in nature. Most users get “addicted” to its flexibility and freedom and demand that they cannot work effectively without it. Many vendors estimate that deployments in the branch offices will force enterprises to deploy wireless in the campus headquarter sites.
Interestingly enough, enterprise branch office deployments share many of the challenges that retail stores do with security services (location of the AAA server), WAN survivability, and WLAN management. Many of the solutions developed to cater to the retail markets are being leveraged by the enterprise branch offices. It is important to note that in many cases, however, WAN survivability is addressed by WAN redundancy—that is, redundant WAN hardware and circuits. Enterprise branch offices tend to rely on applications and data that resides in enterprise data centers at the central site. Loss of WAN connectivity can in some cases halt operations in remote sites, necessitating such an investment in the WAN.
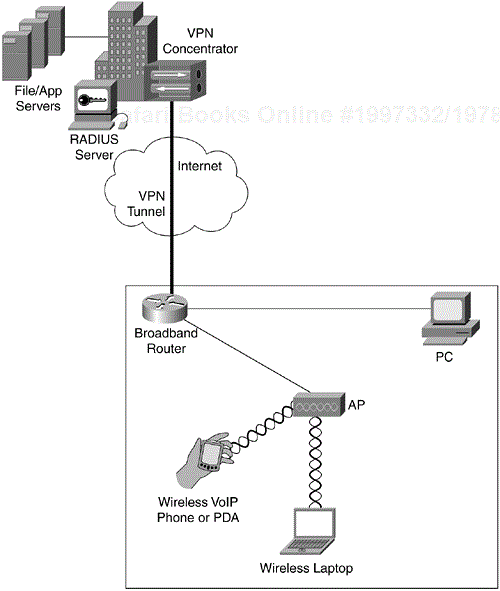
Enterprise telecommuters have many cost-effective mechanisms to access corporate data resources. Where once only expensive, clear-channel WAN circuits, or switched data services such as ISDN, were viable high-bandwidth options over dialup services, today telecommuters can select from a number of high-speed broadband solutions. Such solutions includes high-speed digital subscriber line (DSL) services, broadband cable modems, and high-speed satellite services, all for under $100 per month (in the United States). Couple with this availability the introduction of cost-effective, secure, and manageable virtual private network (VPN) equipment, and enterprises can extend the reach of their data networks and applications to an employee's home. Figure 10-4 illustrates a telecommuter's network solution where VPN over high-speed broadband Internet access facilitates access to the corporate network.
In some cases, the VPN client resides on the user's laptop or PC, establishing a secure tunnel from his machine to the VPN concentrator. This setup gives only a single device with the appropriate VPN client software access to the enterprise network. You would be unable to deploy devices such as IP phones in the employee's home. In Figure 10-4, the broadband router acts as a VPN client and all devices behind it are capable of accessing the corporate network. This setup enables network administrators to provide the telecommuting employee with a solution that leverages all corporate converged applications.
Although Figure 10-4 illustrates a network where the user has access to all converged applications, it also has the potential for many security holes. When the user has the VPN tunnel terminate on a specific endpoint, such as a laptop or PC, access to corporate resources are limited to that specific user and device. However, the scenario in Figure 10-4 allows any device behind the broadband router to access the corporate network via the VPN tunnel. With the proliferation of low-cost APs widely available and targeting the home market, the probability of an unsecured AP being connected to such a home network is extremely high. If the AP is not configured to operate securely, it is no different from having an unsecured AP operating in the corporate network. What is worse is that network administrators have next to no chance of detecting these APs. In a corporate campus, it is recommended that IT departments roll out rogue AP detection mechanisms and perform routine “walk-throughs” to manually detect rogue APs. This detection is just not possible with telecommuters.
The solution to this problem lies with the imminent 802.11i standard. Once 802.11i-compliant APs are widely available, IT departments can easily roll out hardware that is preconfigured and that leverages the central AAA servers for secured access. Although it does not prevent users from connecting unauthorized devices, using 802.1X on switch ports on the broadband router might also deter this behavior. Also, most employees that do connect rogue APs to networks do so not out of malice, but for the convenience the service provides. The IT department rolling out wireless in the home will have a huge impact on the reduction of rogue APs in the home.
Like healthcare and retail, education at both the university level and the primary/secondary level has experienced widespread adoption of wireless technologies. Educational institutions often do not have the luxury to lock network access to a particular room, nor can they afford to constantly reconfigure and retool their networks. WLANs give them the opportunity to provide ubiquitous coverage so that they can bring the network to the student instead of bringing the student to the network. As computers have become a larger part of the learning process, the time and resource savings that wireless brings has proven to be rewarding.
More than just the convenience and the cost savings, you might find that many school buildings were designed before the computer revolution. It just might not be feasible to run wires to the student. WLANs don't have these sorts of boundaries, so you can now bring the network to places where it might not have been possible several years ago. The time and cost savings of not having to wire or rewire often pays for the expense of the wireless infrastructure.
The physical deployment of wireless in an educational environment faces the same challenges as an enterprise office with many individual offices in the form of classrooms. You often need wireless coverage in the open spaces of grass-covered quadrangles and congested student unions and cafeterias. The greatest challenge schools face today is ensuring that the infrastructure can support a multivendor client environment. Even with the model of specialized computer purchase plans at the university level, it is common for students to provide their own computers and, with the low cost of WLAN client hardware, supply their own wireless network interface cards (NICs). At the primary/secondary level, it is common for a group that is separate from the network-infrastructure group to make computer-purchase decisions. These scenarios create a situation that can include client devices with many different operating systems and with wireless NIC devices that need to communicate with a common infrastructure.
At the time of this writing, running a multivendor environment with 802.11b and 40-bit or 128-bit WEP does not present much of a challenge because wi-fi–certified 802.11b devices are readily available. In time, the same will hold for 802.11a and 802.11g. The biggest catch at this point involves security because you might want to restrict the access level for different user groups. For example, overall access to a university network might be limited to students, educators, and staff while nonaffiliates are directly routed to the Internet. Even within the network community, there are different classes with students not having the same level of access as faculty.
WPA, as introduced in Chapter 4, “802.11 Wireless LAN Security,” provides a secure interoperable environment, but you might still be left with the task of supporting legacy, pre-WPA clients. If your AP infrastructure supports the use of VLANs, you can manage access by different user groups, students, and staff, according to VLANs. Similarly, you can provide different levels of security on different VLANs so that the individuals with computers that do not support 802.1x type authentication, for example, would still be allowed access to parts of the network. In this way, you can handle pre-WPA clients and operating systems that might not support your authentication mechanism.
You might also find temporary classrooms or remote educational sites need access to your network. Rather than trench or lease lines to these locations, the easiest and most rapidly deployable solution might be to employ wireless bridges to connect the remote network with the school network, as discussed in Chapter 2, “802.11 Wireless LANs.”
Public access refers to those deployments where the intent is to provide Internet access via the wireless medium to the general public in particular areas. The desire to provide this type of service has grown in hotels, cafes, airports, and any other locales where people congregate. As many of these businesses do not intend to provide free offerings, many of the developments in public access have been in the area of authentication that ties into billing systems. For deployments in Europe, integration of Subscriber Identity Module (SIM) smart-card authentication schemes has been key so that the solution can easily tie into existing Global System for Mobile Communication (GSM) billing systems. The authentication scheme can also determine what services a particular client is permitted to use.
The billing question raises the biggest user-experience issue for public access today, roaming. Roaming refers to the ability to use networks from multiple providers while maintaining a single customer-vendor relationship. At the time of this writing, for the most part, if you go to a different locale, you need to purchase airtime with the vendor providing the service, rather than have it billed to your home account. WECA has formed a wireless Internet service provider roaming (WISPr) committee. Because it is not a standards body, the output will be little more than best-practice suggestions. With the integration of SIM-based billing systems into 802.1x authentication schemes, the situation is improving, and with time, it is anticipated that roaming agreements between service providers will become a reality.
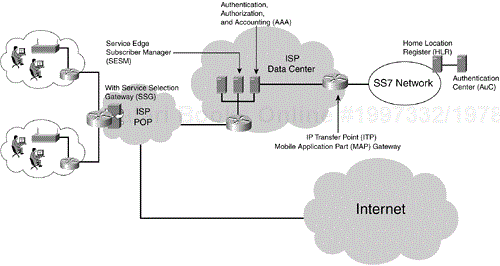
Figure 10-5 shows a sample architecture of a public access solution with multiple public access hot spots connected to a single point of presence (POP). An integrated service selection gateway (SSG) pops up the main user interface screen, handles the authentication process, and then directs and manages traffic based upon the profile and services purchased. The figure shows the SIM authentication interface to the signaling system 7 (SS7) network, along with the Internet connection.
The actual physical deployment of a public access hot spot is the most straightforward part of the problem at hand, with many of the same design techniques of other markets applying equally well here. In addition, on a small scale in a captured public market, you can fairly easily handle the billing and authentication mechanisms. As previously indicated, the true challenge is in the billing and roaming areas, and this area is where much of the development in this field will focus.
The Wi-Fi ZONE designation, provided by the Wi-Fi Alliance, means that the service provider offering the public-access service is using Wi-Fi CERTIFIED gear for an easy user experience. Wi-Fi ZONE providers are required to provide quality customer service and a high level of service that supports VPNs back to corporate networks. Either as a client looking for access or as a service provide, the designator is a key component of public access.
Public safety departments have used mobile radio technology for more than 70 years. However, it has most often been nothing more than a low data-rate service suitable for carrying voice and/or a small amount of data. With the advent of 802.11, we are on the doorstep of a data revolution that could see the delivery of voice, video, and high-speed data directly to first responders. A pilot program in one community has police officers carrying PDAs with an 802.11 wireless feed from wireless cameras inside crime scenes while the crime is taking place, while still other programs facilitate the sharing of database information across city and county boundaries.
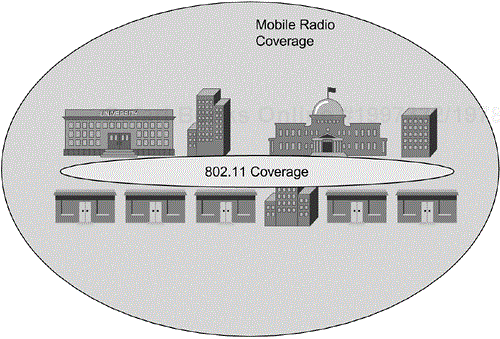
Given the unlicensed nature of the 802.11 frequencies, most public safety deployments employ the formation of zones of 802.11 coverage as an overlay to currently licensed lower data-rate solutions. Figure 10-6 illustrates a sample coverage scenario with 802.11 service in the central business district and lower-rate mobile radio coverage throughout the rest of the region. In more rural communities, via cooperative management of the spectrum, more ubiquitous shared public safety, business, and public access coverage might be possible with access segmented via VLANs. Depending on whether the desire is to bridge mobile networks or just to provide client access, you can use either wireless bridges or APs. Obviously, it is paramount that you the use adequate security in the form of authentication and encryption to secure public safety information, either in the form of the latest 802.11 security mechanisms or via VPNs.
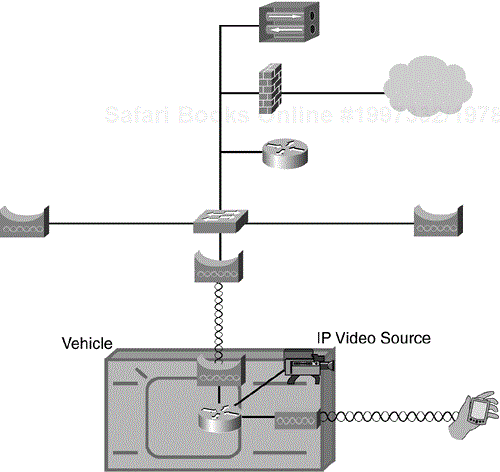
Figure 10-7 illustrates a deployment using wireless bridges to connect public safety vehicles to the municipal network, with video feeds, while creating a hot spot coverage zone around the vehicle for handheld devices. (VPNs provide security.)
In short, 802.11 can provide a complement to existing public safety mobile radio technologies that facilitates information sharing in a way that was never before possible. Because of the lack of interference protection, it is not suitable for widespread ubiquitous coverage but rather is a secondary technology. When used appropriately, it can provide a compelling and easy-to-use and -install solution.
This chapter introduced a number of different applications of WLANs in such diverse areas as healthcare, education, and public safety. In each of these areas, WLANs have enabled either efficiencies or actual applications that were not previously available. This chapter introduced the challenges of each application area, such as interoperability in a multiclient environment, along with potential solutions, such as the use of VLANs to segment user classes.