CHAPTER
2
Malware Taxonomy
The first part of your journey into malware analysis is to understand the nature of malware, including why it exists and what its purpose, directive, and primary function are. Understanding all of these topics will help you get to the core of the malware’s behavior, which is the main goal of analyzing malware.
The first step in accomplishing this is to understand the different classes of malware. This is where malware taxonomy comes into the picture. Malware taxonomy is the process of classifying malware into different groups using a systematic approach based on its characteristics or attributes. It results in well-organized groups of malware with recognizable relationship patterns. Becoming familiar with these patterns enables you to identify specific malware that belongs to a certain class. It also leads to the discovery of a new and unknown class of malware, especially if the characteristics or attributes of the newly discovered malware do not fit any of the known classes. Familiarization with different classes of malware helps you predict malware behavior based on patterns of characteristics or attributes that are revealed during the stages of analysis. If this gathered data is similar to a certain class of malware, it will be easy for you to conclude what the malware’s main directive is. In this instance, you save time and effort by not going through the other steps of analysis because what you need to know was already revealed by the patterns you found.
In this chapter, I will discuss the different classes of malware and how each class differs from the others. I will highlight the main functionalities and directives so you can better understand each malware class.
Malware Classes
Malware has been classified in different ways. Classifications include target operating system (OS), such as Windows, OS X, or Unix; target device, such as mobile devices or desktop devices; vector dependencies; spreading mechanisms; type of victims; and more. Each of these taxonomy methods serves a purpose. It may be a specific purpose or something that covers a wide range of needs. An analyst who wants to eliminate or mitigate a malware’s infection vector might be interested in classifying malware based on vector dependencies and spreading mechanisms, while someone who wants to build a computing infrastructure might be more interested in classifying malware based on target OS, target device, and type of victims the malware is after. In most cases, an understanding of all these classes is needed to secure an organization.
In this book, I will classify malware based on its behavior. The categories are as follows:
![]() Infectors
Infectors
![]() Network worms
Network worms
![]() Trojan horses
Trojan horses
![]() Backdoors
Backdoors
![]() Remote-access Trojans
Remote-access Trojans
![]() Information stealers
Information stealers
![]() Ransomware
Ransomware
![]() Scareware
Scareware
![]() Fakeware
Fakeware
![]() Greyware
Greyware
It is important to note that malware does not neatly fall into just one category. The attackers do not write malware to stick to one class alone or follow strictly the description of a specific class. This is not their concern. Their main concern is for malware to execute based on their directive. If achieving the attacker’s directive means creating a malware that infects files to spread, which is classified as an infector, and with backdoor capability, then so be it. In reality, therefore, most malware will exhibit two or more of the behaviors in the previous list. This reality can pose a challenge in classifying malware. To solve this, researchers and the industry at large moved to classify malware based on class priority. The classes listed previously are based on priority, with infectors being the highest priority and greyware being the lowest. This is the common practice in the industry.
To better illustrate this, let’s take two imaginary malware as an example: first a malware that spreads via e-mail that also has the ability to infect files, and second a malware that is destructive that also has a backdoor capability that provides access to a compromised system. Based on class prioritization, the first example of the e-mail malware is classified as an infector, while the second example is classified as a Trojan.
TIP
Malware classes can be considered as attributes or characteristics and tagged as such. If one malware exhibits two or more class behaviors, it can be tagged with those classes.
When it comes to classifying malware, it is always good to tag it with all the classes it belongs to, especially in a malware database. Based on the e-mail malware example, the malware can be classified, or tagged, as an infector and a network worm. This makes it easy to query for malware based on class behavior. In this scenario, the prioritization is not an issue. Instead, the main issue is to tag the malware with all the class behaviors it is exhibiting. This is useful when it comes to profiling malware.
Infectors
A malware that spreads by attaching a copy of its malicious code to a target host is known as an infector. Its main directive is to populate by infecting other computer files that are usually of the same file type. The first infectors were called computer viruses. Named after their real-world counterparts that spread from one human host to another causing an epidemic within a small community, these computer viruses instead infect files causing a system-wide infection within the compromised system. In the old days, computer viruses were considered to have reached pandemic proportions if computer systems from different geographical locations became infected because of removable media usage such as floppy disks.
Before the term malware was coined, all malicious programs were collectively called computer viruses. Computer viruses are self-replicating programs that spread from one host to another. They were mainly file and boot sector infectors. But because of advances in technology and the ability to spread to other systems through other means that are much more efficient and faster than file and boot sector infection, infectors have vanished into the annals of malware history.
Infectors are rare nowadays, but it is still important to know about them, especially if you are going to deal with malware that has been armored by tools such as binders and joiners, which I will discuss in detail in succeeding chapters.
LINGO
Binders and joiners are malware tools that enable a malware to attach itself to a benign file.
Infectors are divided into the following types:
![]() File infectors
File infectors
![]() Boot sector viruses
Boot sector viruses
![]() Multipartite viruses
Multipartite viruses
File Infectors
File infectors defined the computer virus era. All widespread computer viruses during the DOS era were file infectors. File infectors attach themselves to host programs, and then these infected files serve as the virus carrier to other systems. When an infected file is executed, the virus code in the infected file gets executed first, and after that is done, the execution flow is then passed to the code of the host program. As far as the victim is concerned, the program did what is supposed to do but unknown to him the virus code was executed first.
LINGO
The changing of execution flow from virus code to the host code is also referred to as passing control.
Before a host becomes an infected file or a virus carrier, file infection has to take place. File infection can occur in two ways.
![]() Through direct infection
Through direct infection
![]() Through memory infection
Through memory infection
Direct infection occurs when a virus actively looks for files in the system to infect. Depending on the search parameters of the virus, it might search for files in selected folders such as the operating system folder, the programs folder, or the current folder where the virus was executed; or it can search for files in the whole system.
Memory infection, on the other hand, occurs when a host file is executed and is loaded in memory. In this form of infection, the virus does not actively look for files to infect; rather, it sits in memory waiting for a host file to be executed. Once a host file is executed, the virus attaches itself to the host file’s code in memory, and when the operation is complete, the virus code is saved to the file on disk.
NOTE
Direct infection occurs when the host files are static, while memory infection occurs when the host file is running. As a result, direct infection has the potential of infecting all malware-supported file types in the system, even those files that have not been executed for a long time.
There are different types of file infectors.
![]() Executables
Executables
![]() Macros
Macros
![]() Scripts
Scripts
Executables In the early years of malware, almost all infectors were executables. They were either a COM file or an EXE file. Some of them infect exclusively their own file type; i.e., COM infects COM only, and EXE infects EXE only. But there are those that infect all file types regardless of what the original malware’s file type is; i.e., COM infects both COM and EXE, and EXE infects both COM and EXE.
Regardless of what file type the computer virus is, it follows certain patterns when it comes to infecting or attaching its code to the host file. These patterns of infection serve as a way to classify viruses and file infectors.
They are the following:
![]() Overwriting viruses
Overwriting viruses
![]() Companion viruses
Companion viruses
![]() Parasitic viruses
Parasitic viruses
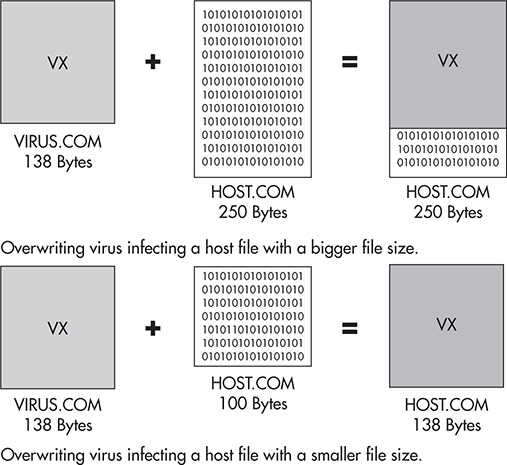
An overwriting virus is the most destructive of all file infectors because, as the name suggests, the virus overwrites the host code with its own. This results in the total destruction of the host file. There is no way to recover from this infection unless there is a backup of the overwritten host file. Figure 2-1 shows the results of an overwriting virus infection.
Figure 2-1 Overwriting virus infection.
Figure 2-1 shows two different scenarios. If the size of the host file is bigger than the overwriting virus, the resulting file is the overwriting virus plus the remaining bytes at the end of the host file. The virus simply overlays itself on the host file. If the size of the host file is equal to or smaller than the overwriting virus, the resulting file is the overwriting virus itself, an exact copy, because it has completely overwritten the host file.
In some cases where performance is a must, such as it was during the DOS era, the overwriting virus, regardless of the size of the host file, simply replaces the host file with its own copy and changes its name to that of the host file. Although this improves the malware’s performance, it also has a drawback. Replacing the host file with a copy of the virus can lead to easy detection via optical inspection by simply listing the files in the directory. For example, say an overwriting virus with a file size of 470 bytes infects a folder of several thousands of files that originally have different file sizes. Listing the files in this folder will show all of them having 470 bytes each, which will arouse suspicion. In addition, assuming the malware does not have a routine to retain the original date of the infected host files, the infected files will have similar timestamps, which will definitely scream infection. These telltale signs are so obvious that optical inspection makes it easy to spot the virus.
Another telltale sign of an overwriting virus infection is that every time an infected host file is executed, it will not function as expected because the virus code completely destroyed the original program or host code so there is nothing to pass the control to after the virus code has executed, which is often silent. As far as the user is concerned, nothing happened. This will raise the level of suspicion that something might be wrong.
NOTE
The only way to recover from an overwriting virus infection is by restoring the affected files from backup.
Companion viruses are the second type of executable file infectors. Companion viruses are interesting because they are the only ones that do not really attach their malware code to the host file. I often refer to them as an exception to the rule. But even without attaching companion virus code to the host file, the virus code is still executed first, and control is still passed to the host program code for it to execute its function and not raise suspicion. The virus is able to do this, without the need to attach its code, by using the operating system’s rules and capabilities, which are the following:
![]() File type execution hierarchy
File type execution hierarchy
![]() Ability to set a file’s attribute to HIDDEN
Ability to set a file’s attribute to HIDDEN
File type execution hierarchy, on the other hand, deals with deciding which files with the same name but different executable extension get to be executed first. In DOS and Windows, this hierarchy exists. The order of execution based on filename is COM, then EXE, and then BAT. For example, if there are three files with the names HELLO.BAT, HELLO.EXE, and HELLO.COM in the same folder, typing HELLO only without any extension at the command line will execute HELLO.COM. Deleting HELLO.COM and typing HELLO at the command line again executes HELLO.EXE. Deleting HELLO.EXE leaves the user with HELLO .BAT, so typing HELLO executes HELLO.BAT. Evidently, taking advantage of file type execution hierarchy works best in command lines, which is why companion viruses were highly successful during the DOS era but not in modern operating systems.
TIP
Make it a habit to type the entire filename when executing a file at the command line.
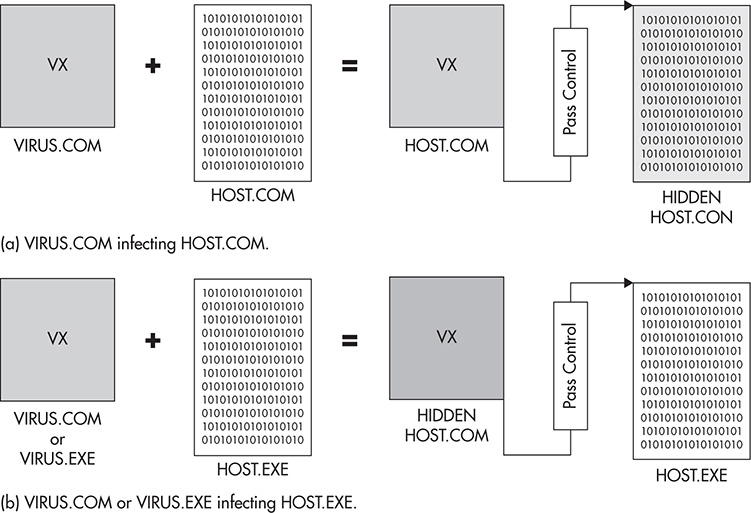
Figure 2-2 (a) shows an example of a companion virus renaming a target host file’s extension and setting its attribute to HIDDEN. For example, when VIRUS.COM infects HOST.COM, the virus renames HOST.COM to HOST.CON (note the N) and sets its attribute to HIDDEN. Then the virus renames itself to HOST.COM. So when the user executes HOST.COM, he is actually executing the virus, and then after the virus executes, it passes control to HOST.CON, which is the real HOST.COM. This scenario is applicable to COM files because COM is highest when it comes to file execution hierarchy.
Figure 2-2 Companion virus infection.
Figure 2-2 (b) shows how VIRUS.COM or VIRUS.EXE deals with an EXE file. Instead of renaming and setting the attribute of the target host file (HOST.EXE), the virus renames itself and sets its attribute to HIDDEN. As a result, the virus becomes HOST.COM with a HIDDEN attribute. So when the user types HOST at the command prompt, he is actually executing the virus because of the COM’s highest hierarchy and not HOST.EXE. Once the virus is finished executing, the virus passes control to HOST.EXE. This scenario is the main reason why it is always suggested to type the whole filename including the extension when executing a program at a command line.
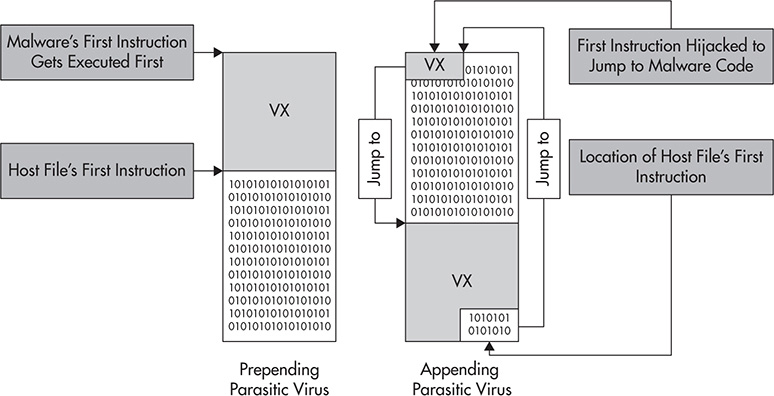
The third type of computer virus, parasitic virus, is the most definitive executable virus of all because, technically speaking, this virus attaches itself to the host file during infection and still lets the host file function as intended. This is the classic form of file infection. A parasitic virus takes control of a target host file’s first instruction by replacing it with a jump or a pointer to the virus code. To pass control back to the host file after the virus executes, the virus saves the location of the host file’s real first instruction.
There are two types of parasitic viruses, as shown in Figure 2-3.
Figure 2-3 Parasitic virus infection.
![]() Prepending
Prepending
![]() Appending
Appending
A prepending parasitic virus attaches itself to the top of the host file. In this type of infection, there is little need for file instruction manipulation because the virus code is on top of the file, so the virus code gets executed first.
As for an appending virus, the virus code attaches itself at the end of the file. If parasitic virus is the classic form of file infection, an appending parasitic virus is the classic form of parasitic virus infection. It hijacks the host file’s first instruction to point to the virus code. After virus execution, it passes control back to the host program code. As mentioned, the virus is able to do this by saving the location of the host file’s first instruction.
Macros What is a macro? A macro is a set of instructions that performs a specific task automatically. The task can be a series of mouse movements, clicks, and keystrokes that follow a specific pattern that can be repeated in an automated fashion. Macros can be constructed using an application-specific macro language. A macro language is a form of scripting that enables a user to program tasks to run automatically. This is utilized mostly in word processors and spreadsheets to automate tasks such as formatting text and crunching numbers.
An application-specific macro language is essentially a programming language. And if there is an opportunity to program or write instructions, there is always the possibility to write a virus. It didn’t take long for virus writers to use macro languages for their creations. This resulted in a new form of file infectors called macro viruses, which are viruses created from an application-specific macro language.
The most popular macro viruses have been written mostly using the Microsoft Office macro language. It produced the following macro viruses:
![]() Single-platform macro virus
Single-platform macro virus
![]() Microsoft Word macro virus
Microsoft Word macro virus
![]() Microsoft Excel macro virus
Microsoft Excel macro virus
![]() Microsoft Access macro virus
Microsoft Access macro virus
![]() Microsoft PowerPoint macro virus
Microsoft PowerPoint macro virus
![]() Cross-platform macro virus
Cross-platform macro virus
Single-platform macro viruses infect only the same file type the macro is written in. For example, a Word macro virus will infect only Word document files and nothing more. Cross-platform macro viruses, on the other hand, have the ability to infect other Office file types. This is possible because in Microsoft Office, Visual Basic for Applications (VBA) is the macro language used across Office documents.
Cross-platform macro viruses infect not only other Office document file types but also executables.
Scripts Since a macro is a scripting language, it is not far-fetched to use other scripts as platforms for viruses. The only difference between a macro virus and a script virus is that the script does not need to be embedded in a file. It can be embedded, or it can be a stand-alone script.
The most utilized scripting languages to write script viruses are Visual Basic Script (VBS) and JavaScript. VBS is supported by Windows, so there are no special dependencies needed for it to run properly. As for JavaScript, it usually works as part of an application such as a web browser and a Portable Document Format (PDF) file. Therefore, for it to function as intended by the virus writer without revealing its true nature, the virus takes advantage of vulnerabilities present in the application where JavaScript is implemented.
Any file format that uses or can interpret scripts has the potential to be infected.
Boot Sector Viruses
A virus always wants to get control of the system’s execution flow first, even before the operating system. One way to achieve that is to infect the boot sector of the disk.
The boot sector is located at sector 1 of each volume. As defined by Microsoft,1 the boot sector is a critical disk structure for starting a computer. It contains executable code and data required by the code, including information that the file system uses to access the volume. The boot sector is created when a volume is formatted. At the end of the boot sector is a 2-byte structure called a signature word or end-of-sector marker, which is always set to 0x55AA.
For example, a Windows 2000 boot sector consists of the following elements:
![]() An x86-based central processing unit (CPU) jump instruction
An x86-based central processing unit (CPU) jump instruction
![]() The original equipment manufacturer identification (OEM ID)
The original equipment manufacturer identification (OEM ID)
![]() The BIOS parameter block (BPB) data structure
The BIOS parameter block (BPB) data structure
![]() The extended BPB
The extended BPB
![]() The executable boot code, also known as the bootstrap code, that starts the operating system
The executable boot code, also known as the bootstrap code, that starts the operating system
Similar to a file infector, a boot sector virus works by taking control of the boot sector’s first instruction. It does this by hijacking the x86-based CPU jump instruction and pointing it to the malicious boot sector virus code. Once the virus code executes, it passes control back to the original boot sector code. The location of this can be found in the hijacked x86-based CPU jump instruction. Executing the original bootstrap code or executable boot code is crucial so that the system will boot properly. Since a boot sector contains only 512 bytes of code, there is not enough space for a boot sector virus. A boot sector virus, therefore, often utilizes other sectors of the disk to hide its code.
Multipartite Viruses
Multipartite viruses are viruses that infect both files and boot sectors. This type of virus has a file infector and a boot sector infector component. It does not matter whether the boot virus or the file virus counterpart is executed. Both parts usually follow the same formula; that is, the virus looks for host files to infect and then looks for boot sectors to infect. If the virus supports Master Boot Record (MBR) infections, it looks for a fixed hard disk and attempts to infect it.
The Master Boot Record, as defined by Microsoft,1 is the most important data structure on the disk. It is created when the disk is partitioned. The MBR contains the following:
![]() A small amount of executable code called the master boot code
A small amount of executable code called the master boot code
![]() The disk signature
The disk signature
![]() The disk partition table
The disk partition table
At the end of the MBR is a 2-byte signature word or end-of-sector marker, which is always set to 0x55AA.
NOTE
0x55AA marks the end of a master boot record, an extended boot record (EBR), and the boot sector.
LINGO
Nowadays, multipartite refers to viruses that are capable of multiplatform infection, not just boot and file infections.
Network Worms
A network worm is a type of malware that replicates or spreads via a network with little or no user intervention using widely used network services such as Internet browsers, e-mail, and chat, among others. Worms usually rely on social engineering to spread, while the most advanced worms exploit software vulnerabilities to infect other systems. The reach of the network worm when it comes to potential victims is massive. Everyone who is online or connected to any network such as the Internet is a potential victim.
Network worms changed the game when it came to the speed and coverage of infection. Before the advent of network worms, malware infections were limited to file infections, which spread slowly. And if they did spread, the coverage was usually just a small geographical area. But network worms spread widely and quickly across networks with no geographical boundaries, giving meaning to the term malware outbreak. What took days or even months for a typical malware to spread across different geographic location takes only seconds for a network worm to accomplish.
LINGO
Malware outbreak describes a worldwide malware infection occurring in a short time.
Network worms are further classified based on their network-propagating features.
![]() Mass mailers
Mass mailers
![]() File-sharing worms
File-sharing worms
![]() Instant messaging (IM) worms
Instant messaging (IM) worms
![]() Internet Relay Chat (IRC) worms
Internet Relay Chat (IRC) worms
![]() Local network worms
Local network worms
![]() Internet worms
Internet worms
Mass Mailers
Worms that spread via e-mail are called mass mailers. Social engineering is usually this worm’s most potent weapon. It fools the user into downloading and executing an e-mail attachment, which is the worm itself. Or if the e-mail is not carrying any file to avoid anti-spam solutions, it persuades the user into clicking a link, which oftentimes leads to a download site that installs a malware onto the user’s machine.
File-Sharing Worms
A file-sharing worm spreads through publicly facing file-sharing folders by dropping a copy of itself into a folder using an enticing filename that users will likely download to their systems and execute. File-sharing worms usually take advantage of file-sharing peer-to-peer programs to spread.
A few example of enticing file names are below.
![]() MSOfficeCrack.EXE
MSOfficeCrack.EXE
![]() FreeAntivirus.EXE
FreeAntivirus.EXE
![]() PopularGameUnlockedVersion.EXE
PopularGameUnlockedVersion.EXE
IM Worms
Instant messaging worms spread through IM. The worm utilizes the infected system’s installed IM software by sending messages to the user’s contact list. The message usually contains a malicious link pointing to a drive-by download site. In some cases, instead of sending a malicious link, the IM worm initiates file transfers to the target victims in the contact list. Since the file transfer is coming from a known contact and the file has an enticing name, there is a big chance the target victim will accept the file transfer, download it, and then execute it. IM worms are good at exploiting trust because the target user thinks the link or file is coming from a friend.
LINGO
The server component is the one that is deployed by the attackers to compromise a system, while the client component is the one that the attackers use to control the server component in the compromised system.
IRC Worms
IRC worms spread through IRC channels by sending messages containing malicious links or instructions that the receiver or target victim should type in return for something such as “free software” or “ops channel privilege.” The links point to a website that serves the worm, while the instruction that the target victim is being socially engineered to type results in a series of commands that can infect not just the target victim’s system but also the other users in the channel.
IRC worms also utilize direct client-to-client (DCC) file transfer requests. The worm usually sends the requests to users joining the channel. These files, like any other socially engineered malicious files, have enticing names to increase their chances of being executed in the target system.
Local Network Worms
Local network worms spread within the confines of a local area network (LAN). A local network worm spreads by scanning for write-enabled share folders in servers or hosts connected to the network. Once it finds these types of share folders, it drops a copy of itself there using enticing names, as usual. The worm also searches for public folders in the network and drops a copy of itself there.
Another way this type of worm spreads, without using shared folders, is by exploiting vulnerabilities found in an OS or other software used in a corporate environment. Successful exploitation often leads to machine compromise. Instead of scanning for folders, the worm scans for software used in host machines connected to the local area network.
Internet Worms
Internet worms spread to other system by scanning the Internet for vulnerable machines. Oftentimes, Internet worms use vulnerable browsers to infiltrate target systems. An unpatched system that is connected to the Internet always runs the risk of being infected by an Internet worm.
NOTE
An unpatched system is a good way to collect malware samples just by connecting to the Internet.
Trojan Horse
A Trojan horse, also known simply as a Trojan, is a destructive malware in disguise. It passes itself as a harmless, legitimate program that is enticing to the user. It can disguise itself as a game, a tool, or even popular software. The main idea is to convince the user to run it.
The main directive of a Trojan is destruction of files or the system. The end result is usually loss of files and an inoperable system. The only way to recover from a Trojan is by restoring from backup or reinstalling the whole system.
Backdoors
Backdoors enable an attacker to gain access to a compromised system, bypassing any form of digital safeguards and authentication, usually through the use of vulnerable and undocumented OS and network functions. The access can be an open shell with root permission.
An important characteristic or attribute of a backdoor is stealth because its success lies in it being hidden and undetected. Once it is discovered, it is “game over” for the attacker.
Remote-Access Trojan
A remote-access Trojan (RAT), also known as remote administration Trojan, is a malicious system administration tool that has backdoor capabilities, enabling an attacker to gain root access to the compromised machine through a stealthy malicious program running in the system. Unlike a backdoor that typically uses a shell, a RAT uses a client-server model. A RAT has a user interface (UI), also known as the client component, that the attacker can use to issue commands to the server component residing in the compromised machine.
Looking at the RAT’s user interface, you can immediately determine what the attacker can do to the compromised machine. The UI is so revealing that it is easy to analyze the malware. But the challenge here is obtaining a copy of the client component, which is usually in the attacker’s possession. Most of the time, researchers and analysts are left only with the server part, which is extracted from the compromised machine.
One of the most popular RATs was SubSeven by mobman, as shown in Figure 2-4.
Figure 2-4 SubSeven by mobman.
Information Stealers
An information stealer, as the name implies, is a malware that steals information. The stolen information could be a password, financial credentials, proprietary data, intellectual property, or anything that is reserved for somebody else’s eyes and not the attacker’s.
Information stealers are further classified into the following:
![]() Keyloggers
Keyloggers
![]() Desktop recorders
Desktop recorders
![]() Memory scrapers
Memory scrapers
Keyloggers
Keyloggers capture keystrokes in a compromised system. The captured keystrokes can be stored locally for future retrieval, which was true for early keyloggers, or sent to a remote server to which the attacker has access.
Desktop Recorders
Desktop recorders work by taking a screenshot of the desktop or the active window when the conditions are met for the malware to capture such information. Usually, the conditions are event driven, such as a mouse click or keyboard press, or is determined by a certain time interval. Desktop recorders are oftentimes used to get around virtual keyboards utilized by some online banks.
One disadvantage of desktop recorders is the amount of data they store. The file size of each screenshot quickly adds up.
Memory Scrapers
Data and code when in memory are decrypted, which is the only way they can be processed. Memory scrapers take advantage of this fact by stealing information in memory while it is being processed. Memory is always the best place to grab data because everything is decrypted.
Ransomware
Ransomware is a malicious program that holds data or access to systems or resources containing that data hostage unless the victim pays a ransom. This type of malware is a form of virtual extortion that can be any of the following:
![]() Data encryption
Data encryption
![]() Data destruction
Data destruction
![]() User lockout
User lockout
Data Encryption
In this type of extortion, the ransomware encrypts a victimized user’s data. The data can be specific such as documents, pictures, or files with specific extensions, or it can be a lockdown of the whole disk or a certain partition. The main idea here is that the data is held hostage, preventing the user from accessing it. To restore access, the user needs to pay a ransom, after which the data will be decrypted by the malware or the user will be provided with a decryption tool and key. Or a more devious act can be purported by the attacker, such as running away with the money and leaving the victimized user with inaccessible data and a big hole in his pocket.
The most telling characteristic of this type of ransomware is that it has encryption algorithms.
Data Destruction
This is like saying, “Pay up or I will blow up the town.” In this scenario, the user is given a time frame to pay or the data or hard drive will be wiped clean. This typically happens after data is encrypted to prevent the user from copying or backing up anything, and then the attackers resort to this type of extortion so they get the money immediately.
The most telling characteristic of this type of ransomware is that it usually has a disk-wipe or data-deleting feature.
User Lockout
Instead of encrypting data, how about just denying the user access to the system itself? This is what user lockout is. The user is locked out and denied login access to the system. This also renders the system unusable because the user is stuck at the login screen. If the user does decide to pay the extortionist, he would need a different system to do it.
NOTE
Not all ransomware can do what it claims to do. Fake ransomware relies on scare tactics to coerce a user into paying a ransom.
Scareware
Scareware is a form of digital fraud. These are malicious programs that are designed to scare users into installing a program and even paying for it. Fake antivirus (AV) programs are the most popular scareware. These are programs that fool the user into thinking that his system is infected with multiple malware and the only way to solve the problem is to install the full version of the program and pay a nominal fee such as $30.
Scareware can victimize the user in three ways. First, it convinces the user to install something into the system, which is most likely malware. If there are User Account Control (UAC) prompts or requests to grant administrative permission, the user is likely to agree to them. Second, it asks for the user’s credit card to “unlock” the full features of the program to make the bad things go away, giving the attackers access to the victim’s credit card information that they can use to sell or use for their own purposes. Third, the user’s credit card is charged an average of $30 for the software. The attackers just made money on bogus software. In short, the victim installed the malware, gave his credit card number away, and paid for everything.
NOTE
The difference between a ransomware and a scareware is that a ransomware asks the user to pay money to gain access to the user’s system or data, while a scareware scares the user into paying money to solve a problem that does not exist.
Fakeware
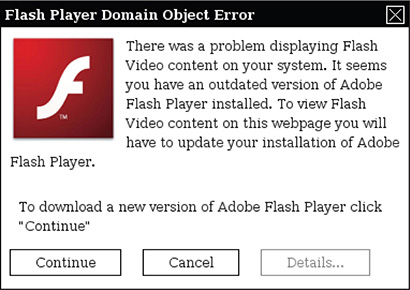
If other malware such as Trojans use enticing names to get executed, fakeware passes itself along as a legitimate program update. It disguises itself as an update of popular software, including security software. Figure 2-5 shows an example of a fakeware disguising itself as a Flash Player update.
Figure 2-5 Fakeware disguising itself as a Flash Player update.
It is always suggested that users update their software to avoid being exploited by attackers. This is the sentiment that attackers are banking on when it comes to fakeware. If users believe a fakeware is a legitimate update, it has a higher chance of being installed on the system.
The difference between a fakeware and a fake AV program is the part where the user is charged money for installing the software. Even with this difference, it is acceptable that a fake AV program be classified as both scareware and fakeware.
TIP
Always update software using manufacturer-suggested methods such as visiting a specific link manually or using the software’s own update features. Treat updates popping up randomly with suspicion.
Greyware
There are files that are not malicious but can be malicious based on how they are used and what effects they have on a user. This is why they are classified as gray-area software or greyware.
The most common greyware types are the following:
![]() Joke
Joke
![]() Hacktools
Hacktools
![]() Adware
Adware
![]() Spyware
Spyware
LINGO
Greyware is also known as a potentially unwanted program (PUP).
Joke
A joke greyware is a program designed to fool the user into believing that something is wrong with the system when really there is nothing wrong. The classic joke programs usually invert the display, make the mouse cursor move in the other direction, mess up the keyboard, and even make disc drives open and close. These programs are harmless and do nothing malicious to the system, but they are nuisances.
Joke programs are supposed to be fun, but they have the potential of producing unwanted consequences depending on the victim’s reaction. Take, for example, the blue screen of death (BSOD) joke program. This program makes the user believe that the system is not functioning anymore. If the user is not aware that this is a joke, he might resort to formatting the system immediately to fix the “problem.” If the user has backed up of all his files, this is fine. He only lost time in formatting and restoring his system, but if the user has no backup, he just lost all his files because of a simple joke program.
Hacktools
Hacktools is short for hacking tools. These are programs that give users access to a target system. Hacktools are similar to network administrator tools. Most of them function the same way. The only difference is the intent for which they are used. A network administrator tool can be used to manage a network to make sure that everything is running smoothly, but in the wrong hands, that same tool can be used to compromise a network.
Some organizations want hacktools and administration tools absent from all systems connected to their network except for those used by network and system administrators. Think of these like guns. Guns in the hands of law enforcement are used for preserving the peace and for upholding the law, but guns in the wrong hands can have deadly consequences.
Adware
Adware is short for advertisement software or ad-supported software. These are programs that display advertisement pop-ups. These pop-ups are definitely a nuisance because they appear more frequently than they are supposed to, and most of the time, the pop-ups are offensive to some users.
Adware became popular in free software. A developer posts or shares a product for free, but to recover development costs and to generate income, the freeware is most of the time bundled with adware. This gave rise to the term ad-supported software. The user can continue using the software as long as the ads are displayed.
NOTE
There is nothing bad about ad-supported software. It becomes bad or considered a nuisance only when pop-ups appear almost all the time even if the freeware is not running.
Spyware
Spyware is pretty self-explanatory. Some people consider it really bad and would even group it under the category of information stealers. When spyware was booming, almost everybody was calling anything that stole information spyware. There is nothing wrong with this because technically speaking a spyware is an information stealer, but there is a difference between greyware spyware and the information stealers class of malware. Spyware, in the strictest sense, is software that can be purchased for the purpose of spying. This means it is available to anybody who can afford it. On the other hand, the information stealers class of malware is available only to the attackers. Their functionalities are added exclusively to the attacker’s malware creation.
The target consumer of spyware usually includes those who want to monitor their family members’ activity online, but most of the time it can be used to spy on other people as well. When Internet cafés were becoming popular, most unscrupulous owners would plant spyware in the system that they used for renting out to patrons. This made it a major security and privacy concern that gave rise to a lot of anti-spyware companies in the nineties and early part of the 21st century.
NOTE
Almost all spyware comes with an end user license agreement (EULA) stating that the user must own the computer where the spyware is being installed and that the publishers have no liability whatsoever resulting from the use or misuse of their software.
Recap
Malware taxonomy is the process of classifying malware. Depending on the need, malware can be classified in different ways. But for our purposes, you can classify malware based on its behavior or directive. The following are the different classes of malware that were discussed in this chapter:
![]() Infectors
Infectors
![]() Network worms
Network worms
![]() Trojan horses
Trojan horses
![]() Backdoors
Backdoors
![]() Remote-access Trojans
Remote-access Trojans
![]() Information stealers
Information stealers
![]() Ransomware
Ransomware
![]() Scareware
Scareware
![]() Fakeware
Fakeware
![]() Greyware
Greyware
Classifying malware enables analysts to come up with well-organized groups of malware with recognizable patterns. Familiarity with these patterns is important to make an educated guess about a malware’s main functionality, especially if the data gathered during analysis is not enough to paint a complete picture of the malware. It also makes analysis efficient by enabling analysts to predict malware behavior based on the patterns that are revealed during the different stages of analysis, thus saving time and effort by not having to go through the other steps of analysis.
1 Microsoft Technet: http://technet.microsoft.com/en-US/.