Chapter 4. The Underground Economy of Security Breaches
The latest statistic from NetCraft puts today’s Internet at 185,497,213 sites. Though the absolute number suffered some loss lately due to the late economic downturn, the Internet growth at mid-2008 was measured at over 130,000 sites per day! It is estimated that the worldwide Internet user population will reach 500 million some time soon. The Internet is fast becoming one of the most significant markets in our modern economy.
Not surprisingly, just like its physical counterpart, the Internet is fostering one of the biggest underground economies.
As one might expect, this cyber underground has one main goal: money. The actors in this economy employ a wide array of digital ammunitions—including malware, botnets, and spam—to help them achieve this goal.
Unlike the physical world, where behavior can be held in check in most places by laws and regulations, the laws that govern the digital universe are, for all intents and purposes, ill-defined and poorly enforced. As a result, the cyber underground flourishes. In recent years, cyber attacks have graduated from the ad hoc, script-kiddie attacks to large-scale, organized crimes.
The 2007 CSI/FBI Study offers these statistics:
The average annual loss due to computer crime jumped from $168,000 in 2004 to $350,424 in 2006. This figure represents a three-year high since 2004.
For the first time in history, financial fraud overtook virus attacks as the largest cyber source for financial losses.
The cyber underground is, without a doubt, a global, thriving economy whose actors can reap handsome benefits from their activities and investments. The increasingly organized nature of the market and its growing sophistication mark a move toward automation and optimization, ultimately yielding higher financial gains for the criminals.
So how does this underground economy work? How do the various actors interact with each other and conduct illicit activities? This chapter presents high-level results of my investigation into these topics.
I’ll end this article with some suggestions for ways we could disrupt the cyber underground or mitigate its destructive effects. But I’m not a law enforcement professional, so finding solutions is not my role. Rather, I hope to initiate an open discussion that will spur a community effort to combat the rise of this underground economy.
The Makeup and Infrastructure of the Cyber Underground
Perverse as it may sound, the cyber underground is a thriving community, with all kinds of collaboration and trading taking place every minute. The members of that community rarely work alone; it is a common practice for different parties to exchange assets (e.g., data and malware) to achieve mutually beneficial goals or shorten the time to launch an attack.
The cyber underground breaks down into an assortment of different actors, which I loosely classify as follows:
- Malware producers
Much of the malware for purchase today is of production quality: highly functional, easy to use, and effective. A professional malware writer goes through production cycles similar to those of a legitimate software producer, including testing, release, and frequent updates once out in the field.
- Resource dealers
These actors profit by selling computing or human resources. Computing resources often come from a botnet comprised of infected machines that can execute commands given remotely as part of an attack. Human resources represent actual hackers, residing in all corners of the world, waiting to be mobilized. A resource dealer’s existence depends on the ability to tap into the massive botnet pool, and as such they are constantly on the lookout to amass more botnet resources. Their main mission is the creation, maintenance, and expansion of botnets.
- Information dealers
An information dealer sells valuable information—such as customer data, bank accounts, and security vulnerabilities—for a profit. Their main goal, therefore, is to gather more information of that nature. An information dealer is sometimes the customer of malware producers, paying for information-stealing malware. In February 2008, the security firm Finjan reported that a database of information containing more than 8,700 FTP user accounts was up for sale. In the wrong hands, this information can result in a massive compromise of trusted domains. A person with valuable credit card information is called a “carder.”
- Criminals, fraudsters, and attack launchers
These are the final consumers of the underground economy. They pay for resources, malware, and information to launch attacks such as financial frauds, distributed denial-of-service (DDoS), and other crimes.
- Cashiers
This player in the cyber underground holds legitimate bank accounts but acts on behalf of fraudsters to route and accept money through those accounts. The cashier is the party that cashes out an account and sends the money (often via Western Union) to the fraudster. A cashier typically receives handsome financial rewards.
As the descriptions show, these categories of cyber criminal often play interlocking roles, each being a client or supplier for other categories. In addition, a single party often plays multiple roles: a malware producer may sell valuable information that he reaped from unleashing the malware, and a resource dealer may produce malware to perpetuate the reach of a botnet. When necessary, the different actors may trade their respective assets for mutual gains.
An interesting development in this underground economy is the adoption of traditional business tactics. Many form long-term business relationships with their vendors and consumers. A malware producer, for instance, will thoroughly test her code before release and will often issue updates and patches to keep her customers happy. The cyber underground is, for all intents and purposes, a serious industry. As we’ll see later, cyber criminals even carry out their own variant of demographically targeted advertising!
The Underground Communication Infrastructure
Internet Relay Chat (IRC) networks are a classic and well-understood method for communication in the cyber underground. A proliferation of cheap hosting services worldwide is making it extremely easy to set up professionally managed IRC networks. If one network starts to be monitored by law enforcement, criminals can move to different networks with relative ease. When one notorious network called Shadowcrew was taken down by the Secret Service, it had approximately 4,000 members and was conducting a booming business of trading stolen personal data.
IRC members often take measures to conceal their identities. On sites like Shadowcrew and BoA Factory, members often use anonymizing proxies or virtual private networks (VPNs) to avoid being traced.
The underground market and its members are also avid users of social networking. Public forums represent a well-exercised way to vet potential business partners. Many members trade on reputation; a fraudulent transaction may result in some level of complaints against the person in the open trading channel, and the negative reputation will severely impede this person’s further trading activities.
The Attack Infrastructure
The different actors in the cyber underground use a variety of tools and mechanisms to obtain information, garner resources, and launch attacks. In addition to one-off exploits and attacks targeting a particular vulnerability or a particular system, which we explore in depth in later sections, many attacks often involve the use of a botnet.
Attackers create a botnet by luring unsuspecting users to download malicious code, which turns the user’s computer into one of the “bots” under the command of the bot server. After installation, the infected bot machine contacts the bot server to download additional components or obtain the latest commands, such as denial-of-service attacks or spam to send out.
With this dynamic control and command infrastructure, the botnet owner can mobilize a massive amount of computing resources from one corner of the Internet to another within a matter of minutes. It should be noted that the control server itself might not be static. Botnets have evolved from a static control infrastructure to a peer-to-peer structure for the purposes of fault tolerance and evading detection. When one server is detected and blocked, other servers can step in and take over. It is also common for the control server to run on a compromised machine or by proxy, so that the botnet’s owner is unlikely to be identified.
Botnets commonly communicate through the same method as their creators’ public IRC servers. Recently, however, we have seen botnets branch out to P2P, HTTPS, SMTP, and other protocols. Using this real-time communication infrastructure, the bot server pushes out instructions, exploits, or code modifications to the bots. The botnet, therefore, can be instructed to launch spam, DDoS, data-theft, phishing, and click fraud attacks. As such, botnets have become one of the most versatile attack vehicles of computer crime.
The Payoff
According to The Aegenis Group, the black market value of a payment card account number was estimated to be between $4 and $6 in the 2007–2008 period. Magnetic stripe data for a payment card carries a price tag between $25 and $35, depending upon the credit limit and type of card. Full information sufficient to open a bank account, including birthday, address, and Social Security number, goes for approximately $200 to $300.
Other personal data, such as driver license numbers, Social Security cards, and PayPal or eBay accounts, are often seen for sale on the black market. Drivers’ licenses and birth certificates go for about $100. A PayPal or eBay account goes for $5 to $10.
Thus, a piece of malware that exploits an unpatched vulnerability can fetch anywhere between $20,000 and $40,000 a pop, depending on the consequences. Bot army building software (e.g., the exploits and bot agent code) goes for approximately $5,000–$10,000 on the black market.
The rising black market value of personal data and data-stealing malware has created a cottage industry of criminals (the information dealers mentioned earlier) that focus on trading financial information. The incidents at TJX and Hannaford Brothers illustrate just the tip of the iceberg; the magnitude of the problem is not yet well understood by the general public. In the next few sections, we explore the data-gathering game of the cyber underground and how they’ve turned it into a massively profitable business.
The Data Exchange
The following is a fragment of a captured IRC conversation between an information dealer and a consumer:
<A> selling adminpassword of online store with hundreds of cvv2 and Bank account # and Routing #. I receive the payment 1st (WU/E-Gold). Also trade cvv2 for [WEBSITE] account.
This information dealer obtained credit card and checking account information by hacking an online store, or more likely bought the information from somebody who actually hacked the store. Buying and selling financial information remains the number one activity in the underground market. Compromised information is often dealt multiple times before the information is put to use.
It’s alarming how much “full” personal information is out there for sale. A package of such information includes almost every vital aspect of one’s identity: everything you’d need to apply for an account, pass simple web authentication, and buy goods online. The following is a captured advertisement (actual details obfuscated) from one of the underground trading channels:
<A> Full info for sale <A> Name: John Smith <A> Address 1: XXX S Middlefield Road. <A> City: XXX <A> State: CA <A> Zip: XXXXX <A> Country: usa <A> Date Of Birth: 04/07/19XX <A> Social Security Number: XXX-XX-5398 <A> Mothers Maiden Name: Jones <A> Drivers License Number: XXXX24766 <A> Drivers License State: CA <A> Credit Card Number: XXXXXXXXXXXX2134 <A> Credit Card Brand: Visa <A> EXP Date: 10/2010 <A> CVV Number: 178 <A> Card Bank Name: Citibank <A> Secret Question 1: What is the model and make of your first car? <A> Secret Question 1 Answer: Geo, Prism <A> Secret Question 2: What is your first Pet's name? <A> Secret Question 2 Answer: Sabrina
As you can see, whoever possesses this information can easily assume the identity of the person to whom this information belongs. Mechanisms such as knowledge-based authentication (KBA) using secret questions are useless against this wealth of stolen information.
Information Sources
So where do the information dealers get this data? From a number of sources, including:
- Financial institutions
These are attractive targets because they house all the information a fraudster needs to commit financial crimes. For that reason, online banking sites are constantly under attack; criminals are looking for “way-in” loopholes to take them through the web server to the backend customer data.
- Merchant stores
Many retailers, whether online or physical, have poor security and data privacy practices, and thus remain a popular source for those with a prying eye for private financial data. The data breaches at both TJX and Hannaford Brothers were due to insufficient security procedures.
- Individual cardholders
Spyware, key loggers, and pharmware on a user’s desktop are other conduits through which private data is gathered.
- Phishing
Phishing sites masquerading as legitimate businesses can lure users into giving up private information such as login IDs and passwords. Phishing is still a widespread threat, especially for less computer-savvy users.
Attack Vectors
The cyber underground players of today use many attack methods for data gathering. I’ll list a few prominent ones here. But many other, more esoteric methods have been observed in the wild that are beyond the scope of this study.
Exploiting website vulnerabilities
A vulnerable website, particularly that of a financial institution or an online e-commerce site, is often the most direct route to valuable data. Because the web server runs software that issues SQL commands to retrieve and modify the internal database (e.g., sensitive customer information), a successful SQL injection attack that fools the web server into passing arbitrary SQL commands to the database can fetch whatever data it chooses.
A well-known women’s clothing store was recently informed by their web application firewall vendor that an SQL injection error in their web application could lead to the compromise of their entire customer database, including credit card numbers, PINs, and addresses.
It is almost routine now for security vendors who engage in web application scanning to discover not one, not two, but many SQL injection attack vulnerabilities in existing web applications. With the advent of Web 2.0 and its still-esoteric secure code development practices, we should not be surprised that many web applications are vulnerable to data theft attacks.
Organized crime groups have long realized that digital data theft represents a gold mine for them. It is known that some of these groups have both automated and manual means to scan the Internet continuously, looking for vulnerable sites.
Malware
Many Internet crimes today can be traced back to some form of malware. For example, spyware, installed on a user’s machine, can steal private information on the hard disk, such as Social Security numbers, credit card information, and bank account information. Injected iFrames, a form of malware that typically lives on the server, can capture user login information and other proprietary communications between the browser and the server. Bot-building malware, once installed on a user’s machine, wakes up once every so often to participate in botnet activities unbeknownst to the user.
The most popular means of malware distribution today is via the Web. Users browsing the Web who come in contact with a malware distribution or hosting site may subject their computers to a malware infection. Many such infections produce no visual clues and therefore are not easily identifiable without special detection tools.
A disturbing trend is that we are seeing more and more legitimate websites unwittingly participating in malware distribution. Malware injected on the website (e.g., the injected iFrames mentioned earlier) can transparently redirect a user’s browser to a third-party site that hosts malware. Google reports that 6,000 out of the top one million ranked websites (according to Google’s page rank algorithm) have been listed as “malicious” at some point. Many are legitimate sites that are compromised at one point or another. Social networking sites and high-volume e-commerce sites have all been hot targets for malware distribution.
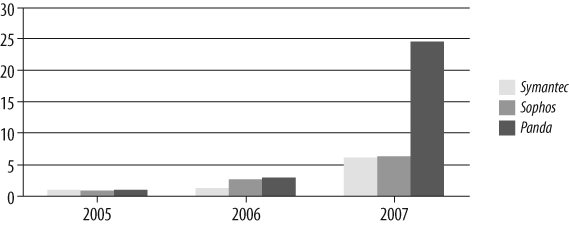
Symantec reports that in 2007, 1,950 new malware instances were discovered every day! Figure 4-1 shows the normalized growth of new malware from 2005 to 2007, according to the numbers reported by Sophos, Symantec, and Panda Labs. In this figure, the most conservative of the three vendors, Sophos, reported a greater than 100% growth in new malware for the last two years. Panda Labs reported a whopping 800% increase in malware from 2006 to 2007.
Much of the increase springs from increasing variations of the same malware; that is, polymorphic malware that is written once but can take on many forms to evade signature detection. Indeed, the rate at which malware producers today release malware and the way in which malware morphs itself has rendered signature-based detection all but useless.
Phishing, facilitated by social-engineering spam
Email spam propels more phishing threats on the Web. Instead of carrying actual malware, spam today tends to promote phishing or malware-laden websites.
Another visible trend is the increase in targeted spam attacks that deliver specially engineered spam messages to a special interest group of recipients; for instance, it is not uncommon to see prescription drug savings messages targeting senior citizens and hot stock tip messages targeting active traders. Such targeted spam has a much higher success rate, which helps to sustain phishing as a viable attack method.
Antispam technologies have seen significant advances in the past a few years. However, the absolute volume of spam on the Internet has almost doubled since 2005. This has significantly strained the limit of many antispam systems.
The Money-Laundering Game
A significant step toward greater viability by the cyber underground economy is the ability to turn financial frauds into actual, usable cash. This is a nontrivial step that involves extracting cash from legitimate financial institutions.
One of the most valuable assets in the cyber underground is so-called “drop” accounts where money can be routed and withdrawn safely. These are often legitimate accounts owned by parties that are willing to play the cashier role discussed earlier in exchange for a cut of the take.
Let’s say Johnny the hacker has full account information for 20 Bank of America customers. Johnny could set up a bank transfer from these compromised accounts (to which he has access) to another Bank of America account owned by Betty, the cashier acting on his behalf. Betty then goes to her local bank and cashes out her entire account. She wires 50% of Johnny’s deposit to a predetermined location, which will be picked up by Johnny, and keeps the remaining 50%.
Being a cashier carries a nontrivial level of risk. Experienced cashiers rarely stay put, often having at their disposal a number of different accounts opened with fraudulent credentials. A good cashier can often demand a market premium. Without the drop accounts and the cashiers, the underground economy would be nothing more than an academic study.
How Can We Combat This Growing Underground Economy?
Are companies doing enough to protect their data from computer crime? Some would argue not. In economic terms, the cost associated with a data breach includes both private costs, i.e., those internal to a firm, and external costs, i.e., those that other entities are forced to pay due to the breach. The problem is that traditional cost models, such as total cost of ownership (TCO), rarely take into account any external costs. As such, the investment in protection technologies rarely matches the true cost of a data breach. It is time for us as a community to face up to these costs and look for alternative solutions, perhaps even ones that are traditionally deemed too cost prohibitive. Some thoughts on alternative directions follow.
Devalue Data
One reason that fraudsters target data is that data carries value. What if we devalue the data, hence reducing the incentive for data theft?
One way to devalue data is to restrict what you can do with it. Take the case of credit cards. If issuing banks reduced general credit limits and made it difficult to obtain cards with high limits, they would significantly curb the appetite for stolen cards and as a result reduce the volume of data theft incidents.
Clearly, this approach goes against the modus operandi of those who are in the lending business. But if the recent credit market crash taught us anything, it is to exercise caution before extending credit. As data theft incidents become more common and the cost of protecting data rises further, financial institutions will, at some point, reevaluate the true value behind data. Why not do it now?
Separate Permission from Information
One common pitfall in most security systems is to confuse the granting of permission (authentication and authorization to do something, such as make a purchase) with the possession of information that uniquely identifies a client. Names and birth dates are personal information that identify a person and can be used for identity theft. Credit card numbers have a similar value to criminals, even though they provide little information beyond some credit history. Authentication and authorization should not require the actual possession of sensitive identifying information.
Imagine a payment card whose number is a one-way hash of the spatial geometry of a person’s face and a PIN of some sort. A transaction is authorized only when a facial scan and the PIN verify the card number; the card is otherwise useless. If we design truly hard-to-bypass authentication procedures, we can even publish everyone’s identifiers and not think twice about it.
Institute an Incentive/Reward Structure
Today, compliance is a big driver in the adoption of security technologies. Several other authors discuss it in this book. However, compliance is centered on penalties: if you are not compliant, there will be a price to pay. There is very little incentive structure to reward good behavior.
The impact of reward structure on improving performance is well understood. It is perhaps time for the information security community to stop relying solely on compliance and start investigating how we can improve overall data protection competency by rewarding good behavior. This should include rewards for internal behavior within an organization as well as across organizations in society.
Establish a Social Metric and Reputation System for Data Responsibility
Just as “greenness” measures a company’s commitment to the environment, we need an analogous metric that measures the company’s maturity in its data-handling operations. And just as greenness can help a company achieve social goodwill, a good data security reputation should result in customer royalty and heightened trust from business partners. Perhaps such a metric and reputation framework would make firms more inclined to internalize some of the external cost, if it will help them garner a more favorable reputation.
Clearly, implementing these proposals would require a shift in thinking and, in some cases, a complete overhaul of infrastructures, which can be an expensive undertaking. But if we do not drastically change the way we approach the problem, count on it: we will not have seen the last of security disasters like those involving Hannaford Brothers and TJX.
Summary
In the physical world, no one organization or company would be expected to fight organized crime single-handedly. It should be fairly obvious that the same logic applies in the virtual world. Eliminating the underground cyber economy is not the job of one group, one organization, or even one country. It requires the collaboration of many entities and many organizations, including users, researchers, security operations, law enforcement agencies, and task forces organized by commercial consortia and governments.