Chapter 5. Beautiful Trade: Rethinking E-Commerce Security
Information security has always been one of the largest barriers to e-commerce. Those of us who spend most of our waking moments thinking of new and different ways to secure these systems and applications know it starts with the data. After all, it’s information that we are trying to protect.
One of the primary challenges in e-commerce security is coming up with practical ways to secure payment transaction data. This term means a lot of different things to a lot of different applications, but for the purpose of this writing, let’s focus on credit card data such as account numbers, security and CV2 codes, PIN numbers, magnetic stripe data, and expiration and issue dates. We will also include extra data we deem necessary to make this process more secure, such as to authenticate or authorize a transaction.
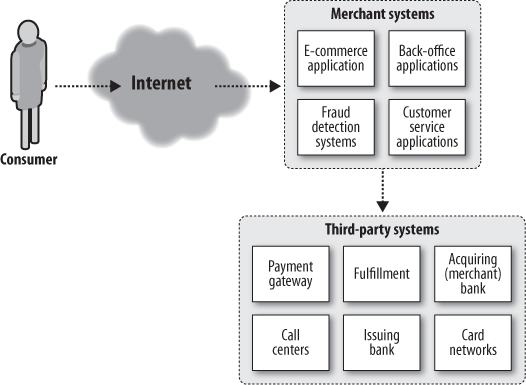
Let’s look at the possible points of failure for credit card information. When a consumer makes a purchase using his credit or debit account where a card is not involved, whether online or offline in a scenario such as a phone purchase, he supplies this data to the merchant in order to prove he has the resources or credit to pay for the merchandise. This data passes through various systems within and beyond the merchant environment through payment gateways, back-office applications, acquiring banking networks and systems, issuing banks, and card association networks.
Some of these merchants (affiliates) may resell items on behalf of other merchants, while other merchants (packagers) bundle merchandise and services from various providers and resellers. This currently means that the data must pass through all of the service providers and secondary merchant systems as well, increasing many times over the number of places where sensitive payment data is housed (see Figure 5-1). Finally, degrading safety further, many of these networks and systems contain legacy applications and operating systems that make it difficult to secure the payment data.
But what if we took another approach? What happens when we throw out a lot of today’s assumptions around electronic payments and e-commerce and assume that the merchant shouldn’t have to store the data at all? What if we never even handed this sensitive information over to the merchant in the first place? As we can see, one of the primary difficulties in securing this data is identifying all the places to which it travels. But what if this no longer mattered? Or at least mattered significantly less?
Deconstructing Commerce
In order to rethink e-commerce security, we must first examine what is in place today. The current security model contains fundamental flaws and suffers from assumptions that are overly broad and ultimately unnecessary. A series of patches and Band-Aids have been billed as best practices and part of an in-depth security strategy. And although these security practices are helpful in protecting data in a generic sense, they do not focus on the real issues of our payment systems.
As an industry, we have spent a great deal of time and money tracking this data, transforming this data through encryption, and protecting it in storage and transmission—all to make up for a lacking security model.
An entire industry has been created around the Payment Card Industry’s Data Security Standard requirements for merchants and service providers. But why? This data has become the crown jewels to many security professionals (and those who work against them) in the e-commerce and retail industries.
Analyzing the Security Context
The fundamental problem is that cardholder data becomes a shared secret. As we’ve seen, this secret often needs to be shared amongst a lot of parties in order to fulfill even a single transaction. Because security relies on the least common denominator of security controls amongst these parties, a leak is almost inevitable during the life of an account.
Visa, Inc. stated, in its earnings report for the third quarter of 2008, that the total transactions on Visa’s brands—Visa, Interlink, Plus, and Electron—grew 11% from $8.65 billion a year to $9.59 billion. This gives us some perspective when analyzing breach data. Visa is the largest of the card brands, but it is only one of many. And each transaction probably passed through multiple merchant systems, payment gateways, service providers, fulfillment systems, bank networks, and card networks. That’s an awful lot of shared secrets!
To compound the issues and complexities of these shared secrets, a merchant or service provider has several reasons to store information such as account numbers after finishing the initial transaction:
- Recurring charges
Many merchants offer services that require regular payments on a weekly, monthly, quarterly, or annual basis. In order to continue to charge the same account on a regular basis, the merchant needs to store sensitive payment information as long as the consumer remains a customer.
- Chargebacks
To issue a refund, the merchant must store the account number that its service or merchandise was charged to. As a measure of fraud prevention, many acquiring banks require the merchants and service providers to refund the exact card account that was originally charged.
- Consumer convenience
Consumers often elect to store their account information with a merchant where they make frequent purchases. This aligns with our discussion later around consumer incentives. For many people, convenience outweighs the risks.
Weak Amelioration Attempts
To address the problems associated with shared secrets among large groups of people, the card associations came up with the concept of a security code (CV2), a three- or four-digit number printed on the card. This is used as a pseudo-second factor for authentication, attempting to prove the purchaser has the card in her possession.
There are two weaknesses in this patch to the system. First, the security code becomes an additional shared secret. There are specific rules around handling security codes for merchants and service providers, but again we rely on the weakest link in the purchase path. Second, not all banks currently support this code, nor is it required in all cases. This means there is little incentive for the merchant or acquirer to reject a purchase based on a failed check of this code. Thus, the security code offers minimal improvement to the anti-fraud system.
While CV2 attempts to authenticate the consumer, we still lack authentication for the merchant. How does the purchaser know the merchant is legitimate? What prevents consumers from being socially engineered or phished out of their payment data?
The card associations and third-party payment providers have created additional security programs to authenticate and authorize payments in card-not-present situations. Let’s analyze a few of the more common processes in place today in order to assess what is working and any areas that may be flawed.
3-D Secure
3-D Secure is an XML-based protocol created by Visa to authenticate the consumer to the card. Visa, MasterCard, and JCB International have adopted the protocol under the names Verified by Visa, MasterCard SecureCode, and J/Secure, respectively.
3-D Secure transactions
The name 3-D Secure refers to the three domains involved in the security model. The first domain, the acquirer, is essentially the e-commerce merchant or acquiring bank. A merchant, using compliant software, makes a call to the issuing bank (the second domain, or issuer) to verify that the account holder (the third domain) is enrolled in the 3-D Secure card program. If the cardholder is enrolled, the issuing bank collects a PIN or password directly from the account holder via a frame on the merchant’s web page. This authentication protocol is transmitted in an XML document over Secure Sockets Layer (SSL). The SSL ensures confidentiality of the account holder’s PIN or password and the authenticity of both the host and client. At the same time, the PIN or password is not available to the merchant or acquiring bank, keeping this data confidential to only the account holder and her issuing bank. The procedure, while complex to describe, is a familiar third-party trust scenario:
The shopper connects to a merchant’s site, makes a purchase selection, and enters card details.
The Merchant Server Plug-in (MPI) sends the Primary Account Number (PAN) to the Directory Server.
The Directory Server queries the appropriate Access Control Server (ACS) to determine whether authentication (or proof of an authentication attempt) is available for the Primary Account Number.
If no appropriate Access Control Server is available, the Directory Server creates a response for the MPI and processing continues with step 5.
The Access Control Server responds to the Directory Server.
The Directory Server forwards the Access Control Server response (or its own) to the MPI.
If neither authentication nor a proof of authentication attempt is available, 3-D Secure processing ends, and the merchant, acquirer, or payment processor may submit a traditional authorization request, if desired.
The MPI sends a Payer Authentication Request (PAR) to the Access Control Server.
The Access Control Server receives the Payer Authentication Request.
The Access Control Server authenticates the shopper using processes applicable to the Primary Account Number (PAN), which may involve a password, chip, PIN, etc. Alternatively, the Access Control Server may produce a proof of authentication attempt.
The Access Control Server then formats the Payer Authentication Response message with appropriate values and signs it.
The Access Control Server returns the Payer Authentication Response to the MPI in order to cache the response for use in further transactions.
The Access Control Server can send selected data to an Authentication History Server (AHS).
The MPI receives the Payer Authentication Response.
The MPI validates the Payer Authentication Response signature (either by performing the validation itself or by passing the message to a separate Validation Server).
The merchant proceeds with an authorization exchange with the acquirer.
Following step 13, the acquirer processes the authorization with the issuer via an authorization system such as VisaNet, and then returns the results to the merchant.
Evaluation of 3-D Secure
3-D Secure has some nice features for authenticating the user to the account, as well as due diligence on the merchant side to ensure it is registered with the card brands; uses compliant payment software; and maintains an active, legitimate merchant account with an acquiring bank. But it has proven unwieldy in practice.
Phishing concerns have been a persistent issue with 3-D Secure. On the one hand, some phishers mimic its behavior. On the other hand, some users reject authentic 3-D Secure transactions as phishing attempts. This has to do with the somewhat out-of-band nature of the PIN authentication, since the request is coming from a different domain than the merchant, and the fact that the issuing bank and the DNS name may not be recognized by the consumer.
A more fundamental security problem in 3-D Secure is that, just like the CV2 number described in the previous section, it is not mandatory for all transactions. So the customer’s account number is still a valuable shared secret. All of the same precautions must go into protecting the Primary Account Number as it makes its way through the various merchant, payment, and supplier systems.
Precertification requires a notable overhead in setting up the protocol between the merchant, the bank, and the consumer. Although the overhead is significantly less than what we will see in our analysis of the SET protocol in the next section, it’s still not ideal.
Beyond the phishing complaint of some 3-D Secure consumers lies a liability issue. The card brands that support 3-D Secure have stated they will not hold merchants liable for fraudulent transactions run through 3-D Secure. This is a great incentive for the merchant to implement 3-D Secure, but moves the requirement of proof of a fraudulent transaction to the consumer, an area where the consumer previously had little liability. Since 3-D Secure is not foolproof, this may not go over very well with cardholders. It essentially places blame for a successful phishing attack on the victim.
Secure Electronic Transaction
Secure Electronic Transaction (SET) is a protocol Visa and MasterCard developed in 1996 for securing credit card transactions over insecure networks such as the Internet. SET utilizes X.509 certificates and extensions, along with public key cryptography to identify each party within the e-commerce transaction and transmit the data while maintaining confidentiality. SET’s unique binding algorithm substitutes a temporary certificate for the consumer’s account number, so that the online merchant never needs access to this sensitive information. Each party is required to preregister with the certificate authority (CA), allowing the card issuer to perform due diligence before it allows the merchant to perform e-commerce transactions, and then authenticating all parties in the transaction.
On the consumer end, SET creates a hash value of the order information together with the payment information. The payment information is sent to the bank along with the signed hash of the order information. The consumer-side software also sends the order information to the merchant with the signed hash of the payment information. Both the cardholder and the merchant create equivalent hashes, compared when they are received by the bank or payment gateway.
This protocol offers a number of different protections for the transaction:
It authenticates all parties in the initial transaction at time of registration with the CA.
It performs additional authentication at transaction time through the exchange of certificates with the consumer, merchant, and payment gateway.
Sensitive data such as the account number is shared only between the consumer and the bank and kept on a “need to know” basis, freeing the merchant from the need to store or transmit this information.
SET transactions
The sequence of events required for a transaction follow:
The customer obtains a credit card account with a bank that supports electronic payment and SET.
The customer receives an X.509 v3 digital certificate signed by the bank.
The customer places an order.
Each merchant has its own certificate, which it sends to the customer so his software can verify that it’s a valid store.
The order and payment are sent.
The merchant requests payment authorization from the issuing bank.
The merchant confirms the order.
The merchant ships the goods or provides the service to the customer.
The merchant requests payment.
Single-Use and Multiple-Use Virtual Cards
A recent trend in cardholder security comes via virtual cards. Companies such as PayPal, MBNA, and Citi are among some of the larger competitors in this space.
A virtual card is used in card-not-present transactions just like a regular credit card, and it is processed by the merchant in exactly the same manner. In fact, the merchant is not even aware that this card is virtual, and thus treats it with the same care as the other card account numbers going through the merchant systems.
How virtual cards work
Each supplier differs slightly in its implementation of virtual cards, but there are essentially two variants: single-use and multiple-use virtual cards. Both types are usually generated “on the fly” via a cardholder request. An existing card account holder requests a virtual card from her virtual card provider for use on a particular e-commerce site. The provider supplies the account holder with a virtual card number, including an expiration date and CV2 security code.
A single-use card can be used for a single transaction involving a limited payment. These cards typically expire in a matter of weeks or less and can be used only with the merchant designated during the cardholder’s request. Thus, lost or stolen information rapidly becomes invalid and worthless to the attacker.
Multiple-use virtual cards are also available through many virtual card providers. These allow for use cases where recurring charges apply, such as paying a monthly bill. Multiple-use cards still carry with them many of the security features of their single-use equivalents, such as being valid with a single merchant and containing limited monthly charge caps. If a multiple-use virtual card is lost or stolen, an attacker could use the card only at that merchant and only for the authorized amount of the recurring charge. This mitigates a great deal of fraud.
Broken Incentives
A common economic issue in information security involves broken incentives. Incentives are a critical factor in any system dealing with multiple parties, particularly where that system depends on people with free choice doing the “right thing.” If the proper incentives are not in place, breakdowns typically occur. To adjust for these external pressures that lead to breakdowns (market failures), financial systems adopt two methods:
- Regulation
Governments or industry consortia put rules in place to address market failures such as monopolies, pollution, lack of alignment with the “greater good,” or in this case a lack of information security. Forms of regulation in this area include the Health Insurance Portability and Accountability Act (HIPAA), the Gramm-Leach-Bliley Financial Services Modernization Act (GLBA), the Sarbanes-Oxley Act (SOX), etc.
- Liability
This legal framework enforces damages (often financial) on those judged liable for damages of commission or omission. In the case of information security, a person or company may be found liable if they do not take reasonable precautions to protect information.
Let’s look now at why the credit card “security market” experiences market failures. Following our financial model, we must examine the current incentives of the primary participants in this market: consumer, merchant, service provider, acquiring bank, issuing bank, and card associations.
Consumer
It’s often assumed that consumers guard their credit card information with care because they have the most to lose when it’s abused, but because of existing regulation to control some of these externalities, this is not actually the case. In the United States, a consumer is liable only for the first $50 of any fraud committed against his account. Typically, the issuing bank will also waive the $50 requirement in order to keep its customer base happy.
Therefore, while most consumers express a desire to protect their account numbers, security codes, and expiration dates, in the heat of a purchase there is actually very little incentive for the consumer to hold back the information. The incentives that do exist are not financial as much as saving the time and hassle associated with a compromised card.
As a point of comparison, there is a greater consumer incentive to protect a debit card, because the consumer is not protected by the same regulations as with credit cards. Also, debit cards are often tied directly to consumer checking and savings accounts, causing an immediate financial hit to the consumer upon a debit card security compromise.
Merchant and service provider
In the existing model, the merchant actually has quite a bit to lose in case of a breach. A compromise of cardholder data can lead to consequences related to both regulations and liability. The merchants are regulated by the card associations via the Payment Card Industry, which imposes a security standard that merchants must adhere to when handling data, along with the systems and networks that contains and transmit it. A merchant found in breach of this standard suffers both financial and operational penalties, enforced by the card associations. Financial penalties are often assessed against the acquiring bank, which in turn passes those fines on to the merchant. Merchants can also be found liable and sued by the issuing banks, indemnifying the banks for any costs associated with a breach, including the cost of reissuing cards.
Merchants also bear the financial responsibility of accepting fraudulent cards used to make purchases within their environment (except when using 3-D Secure). A merchant must put a number of fraud-detection systems in place in order to ensure that the card being used is valid and is wielded by the assigned cardholder. If a merchant ends up accepting a fraudulent card, the issuing bank issues a chargeback, refunding the consumer’s account. If the merchant has already processed the transaction and provided the product or service, it has to absorb the loss associated with that transaction.
Although the merchants have a lot of incentive to protect this information, they do not control enough of the purchase process to do so effectively. As noted earlier, this data must pass through multiple systems, including systems outside the merchant’s direct control. We also saw that many merchants hold on to some of this data long after the transaction, adding further risk.
Service providers are also regulated by the PCI Data Security Standard (DSS). According to the PCI Security Council, the definition of a service provider is a:
...business entity that is not a payment card brand member or a merchant directly involved in the processing, storage, transmission, and switching of transaction data and cardholder information or both. This also includes companies that provide services to merchants, services providers or members that control or could impact the security of cardholder data. Examples include managed service providers that provide managed firewalls, IDS and other services as well as hosting providers and other entities. Entities such as telecommunications companies that only provide communication links without access to the application layer of the communication link are excluded.
Many of the same rules that apply to merchants also apply to service providers, who have similar penalties and liabilities. Their incentives are not quite the same, however, as they do not have direct interaction with the consumer. That said, brand damage could still be a large factor within the business-to-business space.
Acquiring and issuing banks
The acquiring (merchant) bank and issuing banks are heavily regulated entities whose requirements for information protection go well beyond the Payment Card Industry. The issuing bank has an added incentive of representing the consumer in this transaction. This usually means it not only looks to protect this data, but often serves as an advocate to its customer. The merchant bank, while regulated by many of the financial laws and exchanges, usually serves as a middleman or pass-through and is therefore implicated in the penalties associated with merchants and service providers. When a merchant or one of its service providers is believed to have been breached, the acquiring bank will pass on any fines assessed by the card associations to these groups, since they directly manage the relationship with the merchant.
Card association
The card association’s primary incentive to prevent fraud is brand protection. Simply stated, excessive breaches of a given brand could taint the image and lower the use of its network. The financial consequences of a breach to the card associations are not necessarily tangible. The card associations mainly want consumers to feel safe when shopping with their card. The PCI DSS was formed by several card brands that combined their security programs in an attempt to self-regulate and protect their brand.
He who controls the spice
Overall, each player within a transaction carries some incentive to protect this data (ironically, the consumer has the least). But significantly, the incentives do not directly align with who has control. That is, no single player can completely control the protection of the data, nor do the parties have incentives commensurate with their control over the protection of the shared secret as it travels through the various environments.
The current system simply has too many parties that require knowledge of this shared secret with inadequate incentives to expect the information to remain confidential throughout its life. Multiply the generic diagram of a single transaction in Figure 5-1 by the number of transactions throughout the life of a card, and you’ll see that thousands of data handlers are often handed care of a single shared secret.
E-Commerce Redone: A New Security Model
By reviewing the current security model for e-commerce transactions, we now have a good feel for both its strengths and its weak points. Now I would like to propose a more elegant way to look at e-commerce security that renders the value of card account information useless to attackers and brings assurance to consumers.
When conducting a credit or debit transaction in a card-not-present use case, there are essentially seven base requirements that will ensure the transaction is secure while keeping the system usable for both consumers and merchants.
Requirement 1: The Consumer Must Be Authenticated
The first requirement is to authenticate consumers to ensure they are who they say they are. If consumer John is tied to credit account John123, we must first know this is indeed consumer John. So who is the best party and what is the best method to perform this authentication?
The best party is the manager of the cardholder’s account, which is the issuing bank in most cases. This is for several reasons: the issuer already has the information, so storing it with them does not add another point of failure to the system; also, they have the most resources to invest in the expertise and processes to do authentication properly; finally, there are much fewer issuers than there are other actors.
This authentication may be handled through a combination of any of the three classic factors of authentication:
Something the consumer knows, such as a password.
Something the consumer has, such as a token or certificate.
Something the consumer is, such as biometric data.
As we will see later, the latter two may add complexities to mass distribution and management.
Requirement 2: The Merchant Must Be Authenticated
The second requirement is to authenticate the merchant. This gives the consumer assurance that the merchant is legitimate and is providing the goods and services ordered by the consumer. Similar to the first requirement, the optimal party for authenticating the merchant is the manager of the merchant’s account—in most cases, the acquiring bank.
OK, so we have authenticated both the consumer and the merchant, but now we hit a challenge. The issuer and the acquirer have performed authentication, but the transaction is being initiated between the consumer and merchant. How do we share this authentication so that the two primary actors in this use case have verification of each other’s authenticity? We need the issuer and the acquirer to communicate this verification in a secure manner. I will go into more detail on this topic when I lay out the proposed process.
Requirement 3: The Transaction Must Be Authorized
This brings us to the third requirement: the transaction itself must be authorized. So far we have determined that consumer John is indeed consumer John and tied to consumer John’s account. We have verified that merchant Vencer Corp is a legitimate merchant tied to an acquiring bank. We now need to know that consumer John is authorized to make this purchase.
The third requirement, luckily, has not raised problems in e-commerce, provided the consumer is properly authenticated. The issuing bank can confirm the appropriate approvals for this transaction based on all the existing systems in place for account status, credit limits, etc. Thus, fraud from an intruder (often called “hostile fraud”) can be prevented if requirement 1 is perfected (easier said than done).
Admittedly, e-commerce systems can suffer from what is called (in a contradiction of terms) “friendly fraud,” which means fraud from the very person with whom the merchant wants to transact. Friendly fraud occurs when a consumer experiences a change of heart after the purchase or simply refutes legitimate charges. Detecting friendly fraud pre-transaction is more difficult than detecting hostile fraud. There may be ways to bring friendly fraud down to a more acceptable volume through digital signatures, but that’s beyond the scope of this chapter.
Requirement 4: Authentication Data Should Not Be Shared Outside of Authenticator and Authenticated
Our fourth requirement for a secure e-commerce transaction is not to share authentication data outside of the party being authenticated (in our case, either the consumer or the merchant) and the party responsible for the authentication. In a typical card-not-present transaction, these are four different entities. A consumer (1) should be authenticated by an issuing bank (2), while a merchant (3) is authenticated by its acquiring bank (4). The real trick here is sharing the verification of a successful or unsuccessful authentication among all of these parties without sharing the actual credentials.
Unlike today’s model with its (widely) shared secret, our new model must be able to share the consumer’s and merchant’s authentication status without sharing their credentials. If we accomplish this, breach of data at the merchant about the consumer’s authentication status has no impact on the consumer’s credit account. Consumers could then rely on the security of the issuing bank’s system, not the security of every merchant from which they have ever made a purchase.
Merchants are typically authenticated by this kind of single provider system, where the provider is the acquiring bank. Since the acquiring bank authenticates the merchant, my model shares this authentication status with the consumer prior to that transaction. As we will see later, I propose this should be handled between the acquirer and the issuer across the card networks.
Requirement 5: The Process Must Not Rely Solely on Shared Secrets
The fifth requirement simply repeats the central message of this chapter. The new model must not break if a merchant or service provider is compromised. Virtual card account numbers, discussed earlier, are a good way to meet this requirement—but it must become universal. When provided with nothing but one-time or limited-use accounts, a compromise at a single merchant or service provider will not break the overall e-commerce authentication model.
Requirement 6: Authentication Should Be Portable (Not Tied to Hardware or Protocols)
Portability is a must because there is simply too much infrastructure and too many systems currently in place to expect a massive redeployment or overhaul. We must build a model that allows for consumer and merchant authentication within the existing payment frameworks and networks.
Although SET provided a robust set of security controls and met most of the requirements mentioned so far, this area is where it fell short. Adding the extra overhead of a PKI infrastructure and process proved to be too much for the current payment process.
Requirement 7: The Confidentiality and Integrity of Data and Transactions Must Be Maintained
Our seventh and final requirement—to maintain confidentiality and integrity of data and transactions—is a no-brainer and a must for our new model to be taken seriously. This includes all authentication data, transaction and order data, and any data maintaining the state of any of these. This requirement must be adhered to as this data is transmitted across networks and stored throughout these systems.
The New Model
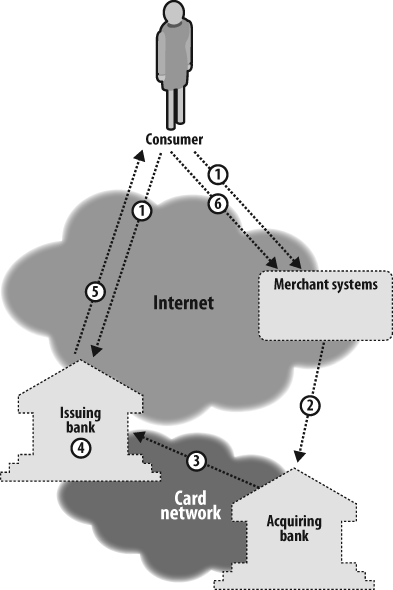
Considering the requirements in the previous sections, I would like to propose the following payment model for card-not-present transactions. Let’s begin by walking through an example e-commerce transaction within the new model at a high level:
A consumer sends order information to both the merchant and the issuing bank in a common format.
When the merchant receives the order information from the consumer, the merchant authenticates with its acquiring bank and sends order information to the bank in a one-way hash.
Upon successful authentication, the acquiring bank signs the hashed value of the order information and sends this value to the issuing bank over the card network.
The issuing bank verifies the signature of the acquiring bank and creates a one-way hash of the order information sent by the consumer. It then compares the hashes, which should match, in order to verify the order.
If the issuing bank successfully verifies both the acquirer’s signature and the consumer order information, the issuing bank sends a virtual card number to the consumer with a limit equal to the amount of the consumer order info.
The consumer submits payment information to the merchant using a virtual card account.
The steps are illustrated in Figure 5-2.
This fairly simple six-step process meets all of our requirements and will prevent a single compromise of any of the numerous systems that process the transaction from compromising the overall consumer account. Although none of these security concepts are new to us in the field of information security, they have not been used together effectively to secure modern e-commerce transactions. I believe the simplicity of this approach is what makes it beautiful and at the same time scalable to today’s environment. By melding a series of existing security features and processes, we can fundamentally change the overall model, creating a hybrid that is simple, secure, and beautiful.