Chapter 1. Overview of Network Security
At the same time networks are growing exponentially, they are becoming complex and mission critical, bringing new challenges to those who run and manage them. The need for integrated network infrastructure comprising voice, video, and data (all-in-one) services is evident, but these rapidly growing technologies introduce fresh security concerns. Therefore, as network managers struggle to include the latest technology in their network infrastructure, network security has become a pivotal function in building and maintaining today’s modern high-growth networks.
This chapter presents a broad description of network security in the context of today’s rapidly changing network environments. The security paradigm is changing, and security solutions today are solution driven and designed to meet the requirements of business. To help you face the complexities of managing a modern network, this chapter discusses the core principles of security—the CIA triad: confidentiality, integrity, and availability.
In addition to discussing CIA, this chapter discusses security policies that are the heart of all network security implementations. The discussion covers the following aspects of security policies: standards, procedures, baselines, guidelines, and various security models.
The chapter takes a closer look at the perimeter security issue and the multilayered perimeter approach. The chapter concludes with the Cisco security wheel paradigm involving five cyclical steps.
Fundamental Questions for Network Security
When you are planning, designing, or implementing a network or are assigned to operate and manage one, it is useful to ask yourself the following questions:
1. What are you trying to protect or maintain?
2. What are your business objectives?
3. What do you need to accomplish these objectives?
4. What technologies or solutions are required to support these objectives?
5. Are your objectives compatible with your security infrastructure, operations, and tools?
6. What risks are associated with inadequate security?
7. What are the implications of not implementing security?
8. Will you introduce new risks not covered by your current security solutions or policy?
9. How do you reduce that risk?
10. What is your tolerance for risk?
You can use these questions to pose and answer some of the basic questions that underlie fundamental requirements for establishing a secure network. Network security technologies reduce risk and provide a foundation for expanding businesses with intranet, extranet, and electronic commerce applications.
Solutions also protect sensitive data and corporate resources from intrusion and corruption.
Advanced technologies now offer opportunities for small and medium-sized businesses (SMB), as well as enterprise and large-scale networks to grow and compete; they also highlight a need to protect computer systems against a wide range of security threats.
The challenge of keeping your network infrastructure secure has never been greater or more crucial to your business. Despite considerable investments in information security, organizations continue to be afflicted by cyber incidents. At the same time, management aims for greater results with fewer resources. Hence, improving security effectiveness remains vital, if not essential, while enhancement of both effectiveness and flexibility has also become a primary objective.
Without proper safeguards, every part of a network is vulnerable to a security breach or unauthorized activity from intruders, competitors, or even employees. Many of the organizations that manage their own internal network security and use the Internet for more than just sending/receiving e-mails experience a network attack—and more than half of these companies do not even know they were attacked. Smaller companies are often complacent, having gained a false sense of security. They usually react to the last virus or the most recent defacing of their website. But they are trapped in a situation where they do not have the necessary time and resources to spend on security.
To cope with these problems, Cisco has developed the SAFE Blueprint, a comprehensive security plan that recommends and explains specific security solutions for different elements of networks.
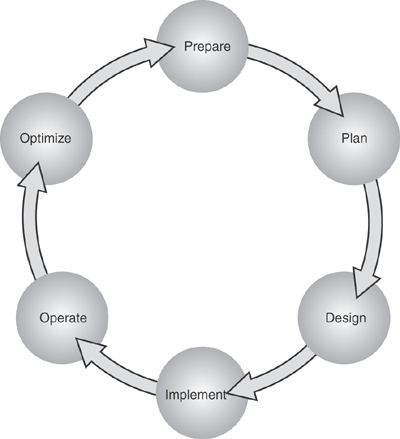
Cisco also offers the integrated security solution, which delivers services above and beyond the “one size fits all” model. In addition, Cisco services are designed to deliver value throughout the entire network life cycle that includes the stages of prepare, plan, design, implement, operate, and optimize (PPDIOO). the Cisco PPDIOO model, as shown in Figure 1-1, encompasses all the steps from network vision to optimization, enabling Cisco to provide a broader portfolio of support and end-to-end solutions to its customers.
Figure 1-1. The Cisco PPDIOO Model
Transformation of the Security Paradigm
As the size of networks continues to grow and attacks to those networks become increasingly sophisticated, the way we think about security changes. Here are some of the major factors that are changing the security paradigm:
• Security is no longer about “products”: Security solutions must be chosen with business objectives in mind and integrated with operational procedures and tools.
• Scalability demands are increasing: With the increasing number of vulnerabilities and security threats, solutions must scale to thousands of hosts in large enterprises.
• Legacy endpoint security Total Cost of Ownership (TCO) is a challenge: Reactive products force deployment and renewal of multiple agents and management paradigms.
• Day zero damage: Rapidly propagating attacks (Slammer, Nimda, MyDoom) happen too fast for reactive products to control. Therefore, an automated, proactive security system is needed to combat the dynamic array of modern-day viruses and worms.
With modern-day distributed networks, security cannot be enforced only at the network edge or perimeter. We will discuss perimeter security in more detail later in this chapter.
Zero-day attacks or new and unknown viruses continue to plague enterprises and service provider networks.
To attempt to establish protection against attacks, enterprises try to patch systems as vulnerabilities become known. This clearly cannot scale in large networks, and this situation can be addressed only with real-time proactive-based systems.
Security now is about management and reduction of risk in a rapidly evolving environment. Maximum risk reduction is achieved with an integrated solution built on a flexible and intelligent infrastructure and effective operations and management tools. Business objectives should drive security decisions. Today, we are in the new era that forces us to rethink security and outbreak prevention.
Principles of Security—The CIA Model
A simple but widely applicable security model is the confidentiality, integrity, and availability (CIA) triad. These three key principles should guide all secure systems. CIA also provides a measurement tool for security implementations. These principles are applicable across the entire spectrum of security analysis—from access, to a user’s Internet history, to the security of encrypted data across the Internet. A breach of any of these three principles can have serious consequences for all parties concerned.
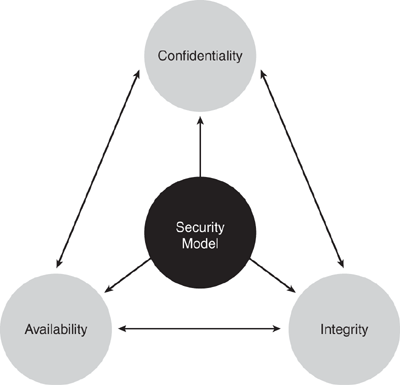
Confidentiality
Confidentiality prevents unauthorized disclosure of sensitive information. It is the capability to ensure that the necessary level of secrecy is enforced and that information is concealed from unauthorized users. When it comes to security, confidentiality is perhaps the most obvious aspect of the CIA triad, and it is the aspect of security most often attacked. Cryptography and encryption methods are examples of attempts to ensure the confidentiality of data transferred from one computer to another. For example, when performing an online banking transaction, the user wants to protect the privacy of the account details, such as passwords and card numbers. Cryptography provides a secure transmission protecting the sensitive data traversing across the shared medium.
Integrity
Integrity prevents unauthorized modification of data, systems, and information, thereby providing assurance of the accuracy of information and systems. If your data has integrity, you can be sure that it is an accurate and unchanged representation of the original secure information. A common type of a security attack is man-in-the-middle. In this type of attack, an intruder intercepts data in transfer and makes changes to it.
Availability
Availability is the prevention of loss of access to resources and information to ensure that information is available for use when it is needed. It is imperative to make sure that information requested is readily accessible to the authorized users at all times. Denial of service (DoS) is one of several types of security attacks that attempts to deny access to the appropriate user, often for the sake of disruption of service.
Policies, Standards, Procedures, Baselines, Guidelines
A security model is a multilayered framework made of many integrated entities and logical and physical protection mechanisms, all working together to provide a secure system that complies with industry best practices and regulations.
Security Policy
A security policy is a set of rules, practices, and procedures dictating how sensitive information is managed, protected, and distributed. In the network security realm, policies are usually point specific, which means they cover a single area. A security policy is a document that expresses exactly what the security level should be by setting the goals of what the security mechanisms are to accomplish. Security policy is written by higher management and is intended to describe the “whats” of information security. The next section gives a few examples of security policies. Procedures, standards, baselines, and guidelines are the “hows” for implementation of the policy. Information security policies underline the security and well-being of information resources; they are the foundation of information security within an organization.
Trust is one of the main themes in many policies. Some companies do not have policies because they trust in their people and trust that everyone will do the right thing. But, that is not always the case, as we all know. Therefore, most organizations need policies to ensure that everyone complies with the same set of rules.
In my experience, policies tend to elevate people’s apprehension because people do not want to be bound by rules and regulations. Instead, people want freedom and non-accountability. A policy should define the level of control users must observe and balance that with productivity goals. An overly strict policy will be hard to implement because compliance will be minimal or ignored. On the contrary, a loosely defined policy can be evaded and does not ensure accountability and responsibility. A good policy has to have the right balance.
Examples of Security Policies
Depending on the size of the organization, potentially dozens of security policy topics may be appropriate. For some organizations, one large document covers all facets; at other organizations, several smaller, individually focused documents are needed. The sample list that follows covers some common policies that an organization should consider.
• Acceptable use: This policy outlines the acceptable use of computer equipment. The rules are established to protect the employee and the organization. Inappropriate use exposes the company to risks including virus attacks, compromise of network systems and services, and legal issues.
• Ethics: This policy emphasizes the employee’s and consumer’s expectations to be subject to fair business practices. It establishes a culture of openness, trust, and integrity in business practices. This policy can guide business behavior to ensure ethical conduct.
• Information sensitivity: This policy is intended to help employees determine what information can be disclosed to nonemployees, as well as the relative sensitivity of information that should not be disclosed outside an organization without proper authorization. The information covered in these guidelines includes but is not limited to information that is either stored or shared via any means. This includes electronic information, information on paper, and information shared orally or visually (such as by telephone, video conferencing, and teleconferencing).
• E-mail: This policy covers appropriate use of any e-mail sent from an organization’s e-mail address and applies to all employees, vendors, and agents operating on behalf of the company.
• Password: The purpose of this policy is to establish a standard for creation of strong passwords, the protection of those passwords, and the frequency of change.
• Risk assessment: This policy is used to empower the Information Security (InfoSec) group to perform periodic information security risk assessments (RA) for the purpose of determining areas of vulnerability and to initiate appropriate remediation.
Tip
Examples of policies listed previously and other templates can be found at the SANS website:
Note
Policies need to be concise, to the point, and easy to read and understand. Most policies listed previously are on average two to three pages.
Standards
Standards are industry-recognized best practices, frameworks, and agreed principles of concepts and designs, which are designed to implement, achieve, and maintain the required levels of processes and procedures.
Like security policies, standards are strategic in nature in that they define systems parameters and processes.
Standards vary by industry. There are two notable standards in security information management—ISO 17799 and COBIT. These are discussed in Chapter 25, “Security Framework and Regulatory Compliance.”
Procedures
Procedures are low-level documents providing systematic instructions on how the security policy and the standards are to be implemented in a system. Procedures are detailed in nature to provide maximum information to users so that they can successfully implement and enforce the security policy and apply the standards and guidelines of a security program.
Employees usually refer to procedures more often than other policies and standards because procedures provide the actual details of the implementation phase of a security program.
Baselines
A baseline is the minimum level of security requirement in a system. Baselines provide users the means to achieve the absolute minimum security required that is consistent across all the systems in the organization. For example, a company might have a baseline for Windows 2000 servers to have Service Pack 4 installed on each server in the production environment. The procedure document would supplement the baseline by spelling out step-by-step instructions on where to download Service Pack 4 and how to install it to comply with this security level.
Guidelines
Guidelines are recommended actions and operational guides for users. Similar to procedures, guidelines are tactical in nature. The major difference between standards and guidelines is that guidelines can be used as reference, whereas standards are mandatory actions in most cases.
Figure 1-3 depicts the fundamental relationship among security policies, standards, baselines, guidelines, and procedures.
Figure 1-3. Relationships Among Security Policies, Standards, Procedures, Baselines, and Guidelines

Security Models
An important element in the design and analysis of secure systems is the security model, because it integrates the security policy that should be enforced in the system. A security model is a symbolic portrayal of a security policy. It maps the requirements of the policy makers into a set of rules and regulations that are to be followed by a computer system or a network system. A security policy is a set of abstract goals and high-level requirements, and the security model is the do’s and don’ts to make this happen.
You should know about several important security models even though describing them in detail is beyond the scope of this book:
• The Bell-LaPadula Model (BLM), also called the multilevel model, was introduced mainly to enforce access control in government and military applications. BLM protects the confidentiality of the information within a system.
• The Biba model is a modification of the Bell-LaPadula model that mainly emphasizes the integrity of the information within a system.
• The Clark-Wilson model prevents authorized users from making unauthorized modification to the data. This model introduces a system of triples: a subject, a program, and an object.
• The Access Control Matrix is a general model of access control that is based on the concept of subjects and objects.
• The Information Flow model restricts information in its flow so that it moves only to and from approved security levels.
• The Chinese Wall model combines commercial discretion with legally enforceable mandatory controls. It is required in the operation of many financial services organizations.
• The Lattice model deals with military information. Lattice-based access control models were developed in the early 1970s to deal with the confidentiality of military information. In the late 1970s and early 1980s, researchers applied these models to certain integrity concerns. Later, application of the models to the Chinese Wall policy, a confidentiality policy unique to the commercial sector, was developed. A balanced perspective on lattice-based access control models is provided.
Perimeter Security
Opinions on perimeter security have changed a great deal over the past few years. Part of that change is that the very nature of perimeter security is becoming increasingly uncertain, and everyone has a different view of just what it is. The limits of the perimeter itself are becoming broad and extensive, with no geographic boundaries, and remote access is becoming part of the integral network.
Is Perimeter Security Disappearing?
In essence, the perimeter has been transformed and extended to the various levels within the network. In other words, networks today do not have a single point of entrance; they are multi-entry open environments where controlled access is required from anywhere within the network. This transformation leads us to start thinking in terms of multiperimeter networks.
The Difficulty of Defining Perimeter
Traditional networks are growing with the merging of remote network access. Wireless networks, laptops, mobile phones, PDAs, and numerous other wireless gadgets need to connect from outside the enterprise into the corporate network. To fulfill these needs, the concept of inside versus outside becomes rather complicated. For example, when you connect to the corporate network using a virtual private network (VPN), you are no longer on the outside the network. You are now on the inside of the network, and so is everything that is running on your computer.
Globally networked businesses rely on their networks to communicate with employees, customers, partners, and suppliers. Although immediate access to information and communication is an advantage, it raises concerns about security and protecting access to critical network resources.
Network administrators need to know who is accessing which resources and establish clear perimeters to control the access. An effective security policy balances accessibility with protection. Security policies are enforced at network perimeters. Often people think of a perimeter as the boundary between an internal network and the public Internet, but a perimeter can be established anywhere within a private network, or between your network and a partner’s network.
A Solid Perimeter Security Solution
A comprehensive perimeter security solution enables communications across it as defined by the security policy, yet protects the network resources from breaches, attacks, or unauthorized use. It controls multiple network entry and exit points. It also increases user assurance by implementing multiple layers of security.
The Cisco wide range of Cisco perimeter security solutions provides several levels of perimeter security that can be deployed throughout your network as defined by your security policy. These solutions are highly flexible and can be tailored to your security policy.
Security in Layers
As discussed earlier, security in layers is the preferred and most scalable approach to safeguard a network. One single mechanism cannot be relied on for the security of a system. To protect your infrastructure, you must apply security in layers. This layered approach is also called defense in depth. The idea is that you create multiple systems so that a failure in one does not leave you vulnerable, but is caught in the next layer. Additionally, in a layered approach, the vulnerability can be limited and contained to the affected layer because of the applied security at varying levels.
Multilayer Perimeter Solution
As stated previously, today’s solutions are shifting toward the approach of placing safeguard mechanisms at various layers of the network, not just at the boundary or edge devices. Today, it is recommended to deploy Intrusion Prevention System (IPS) devices on both the inside and outside boundaries of private networks. Firewalls, on the other hand, are placed between various business segments or departments within the same organization, dividing the network into logical groupings and applying perimeter defense at each segment or department. In this multiperimeter model, each segment can have different layers of defense within it.
Effective perimeter security has become increasingly important over recent years. Perimeter security cannot be trusted to only the traditional defense mechanisms of firewalls and IDS. Web applications, wireless access, network interconnectivities, and VPNs have made the perimeter a much more complicated concept than it was a couple of years ago.
A layered approach requires implementing security solutions at different spectrums of the network. Another similar concept is islands of security. To implement islands of security, do not restrict your thinking to perimeter security. Do not depend on just one method for your security. You should, instead, have layers of protection—perimeter, distribution, core, and access layer. Figure 1-4 illustrates a basic multilayered security mechanism, which is designed to protect the data flow in the system.
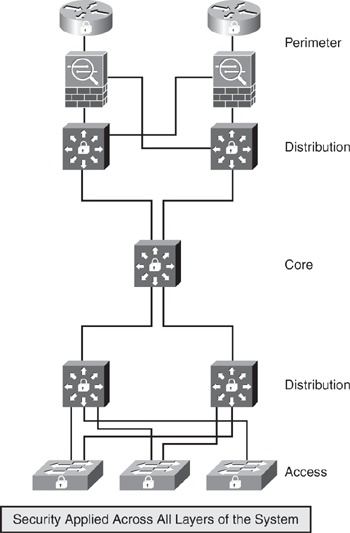
This layered approach is related to the technology of an environment and the complexity of each of the technologies at each layer. The complexity comes from different protocols, applications, hardware, and security mechanisms that work at one or more of the seven layers in the OSI model. Just as there are different levels within an environment, different types of attacks can occur at each level and would require respective countermeasures.
The Domino Effect
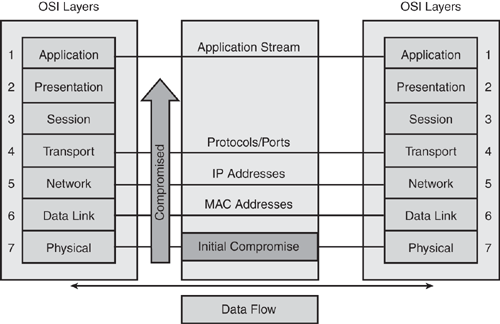
• The OSI reference model was built to enable different layers to work independently of each other. The layered approach was developed to accommodate changes in the evolving technology. Each OSI layer is responsible for a specific function within the networking stack, with information flowing up and down to the next subsequent layer as data is processed. Unfortunately, this means that if one layer is hacked, communications are compromised without the other layers being aware of the problem. For example, as shown in Figure 1-5, if the physical layer (Layer 1) was compromised, it could cause all other layers to be compromised in succession. Security is only as strong as the weakest link. When it comes to networking, any layer can be the weakest link.
Security Wheel
Network security is a continuous process built around the corporate security policy. The security wheel depicted in Figure 1-6 shows a recursive, ongoing process of striving toward perfection—to achieve a secured network infrastructure. The paradigm incorporates the following five steps:
Step 1. Develop a security policy
A strong security policy should be clearly defined, implemented, and documented, yet simple enough that users can easily conduct business within its parameters.
Step 2. Make the network secure
Secure the network by implementing security solutions (implement authentication, encryption, firewalls, intrusion prevention, and other techniques) to stop or prevent unauthorized access or activities and to protect information and information systems.
This phase detects violations to the security policy. It involves system auditing and real-time intrusion detection and prevention solutions. This also validates the security implementation in Step 2.
Step 4. Test.
This step validates the effectiveness of the security policy through system auditing and vulnerability scanning and tests existing security safeguards.
Step 5. Manage and improve.
Use information from the monitor and test phases to make improvements to the security implementation. Adjust the corporate security policy as security vulnerabilities and risks are identified. Manage and improve corporate security policy.
Figure 1-6. The Security Wheel
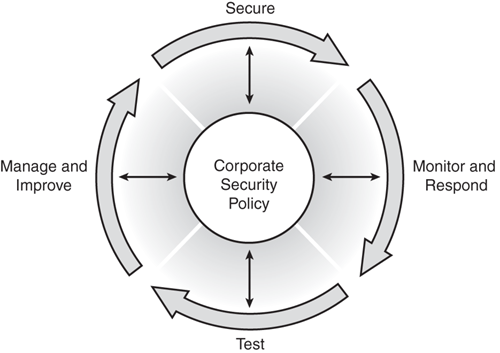
Lessons learned from Steps 2 through 5 should always be reflected back to the corporate security policy in Step 1, so that the high-level security expectations are being met. This should be an ongoing process, a continuous life cycle!
Summary
This chapter gave an overview of network security and discussed the challenges of managing a secured network infrastructure. The chapter discussed how the security paradigm is changing and that security solutions today are no longer product based. Instead, they are more solution oriented and designed with business objectives in mind. The chapter also discussed the core principles of security—the CIA triad of confidentiality, integrity, and availability—followed by brief discussion of aspects of security policies: standards, procedures, baselines, guidelines, and various security models. The chapter takes a detailed look at the perimeter security issue and the multilayered security approach. The chapter concludes with the Cisco security wheel paradigm involving five cyclical steps.
References
Harris, Shon. CISSP All-in-One Exam Guide, Second Edition. McGraw-Hill Osborne Media, 2003.
https://www2.sans.org/resources/policies/#template
http://www.cisco.com/go/securityconsulting
http://www.doc.ic.ac.uk/~ajs300m/security/CIA.htm
http://portal.acm.org/citation.cfm?id=619980
http://www.gammassl.co.uk/topics/chinesewall.html
http://www.devx.com/security/Article/20472
Guel, Michele. “A Short Primer for Developing Security Policy,” Cisco Systems, http://www.sans.org/resources/policies/#primer
