Chapter 9. Cisco Secure ACS Software and Appliance
As discussed in the previous chapter, with networks growing beyond the campus, network security increases in importance and administrative complexity. Identity security and access management are essential for networks and network resources to safeguard them from unauthorized access.
Cisco Secure Access Control Server (ACS) provides a centralized access management solution for managing enterprise-wide network users and network infrastructure resources with policy-based enforcement. ACS provides a comprehensive identity-based network access control solution for intelligent information networks.
Cisco Secure ACS Software for Windows
Cisco Secure ACS software for Windows provides a scalable, centralized identity-based access control solution. ACS provides the structure to enforce user-based policies and allows granular control of user access to network and network resources.
ACS software supplies the following provisions:
• Network access user authentication
• Resource authorization and privilege levels
• Network access security policy enforcement
• Audit information
• Access and command controls
• Support for RADIUS and TACACS+ security protocols
Cisco Secure ACS is one of the key components in the integration of the Cisco trust and identity security solutions. It provides the structure for access control security by provisioning the authentication, authorization, and accounting (AAA) architecture and policy control from a centralized identity networking framework, thereby allowing greater scalability and flexibility, increased security, and user productivity gains.
ACS support spans all major Cisco devices and other network access servers (NAS), also referred to as AAA client, including
• Wired and wireless LAN
• Access points
• Edge and core routers
• Dialup and broadband connections
• Cable access solutions
• Storage devices
• Content devices
• Voice over IP (VoIP)
• Firewalls
• Virtual private networks (VPN)
• IEEE 802.1X access control
• Cisco Network Admission Control (NAC)
Figure 9-1 depicts the AAA client-server model. Note that the diagram shows the external database as optional. ACS supports local user databases and external databases, which will be discussed further in this chapter.
Figure 9-1. AAA Client-Server Model Using ACS
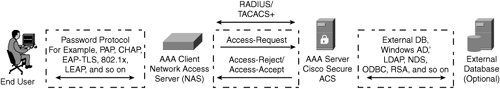
AAA Server: Cisco Secure ACS
The AAA framework implementation consists of two parts: the client side and the server side. As shown in Figure 9-1, Cisco Secure ACS serves as the AAA server side by providing authentication, authorization, and accounting services to network devices on the AAA client side. The Cisco ACS is also referred to as the network access server (NAS) or network access device (NAD). The NAS/NAD can be any Cisco device, such as the router, switch, firewall, concentrator, access point, or any other non-Cisco device. The AAA client serves as the gateway and forwards all access requests to the AAA server on behalf of the end user. The AAA server verifies the credentials by using its internal local database or optionally configured external database. The AAA server responds to the NAS with an [access-accept] or an [access-reject] message with a set of authorization attributes. Refer back to Figure 9-1 to see the basic flow.
ACS operates as a set of Windows services and can run on Microsoft Windows 2000 Server and the Windows Server 2003 operating system. ACS can be installed as a domain controller or a member server.
For further details, refer to the ACS installation and user guide:
• Cisco ACS for Windows Installation Guide: http://www.cisco.com/en/US/products/sw/secursw/ps2086/prod_installation_guides_list.html
• Cisco ACS for Windows User Guide: http://tinyurl.com/yvajyj
Protocol Compliance
ACS supports both RADIUS and TACACS+ AAA security protocols.
ACS conforms to TACACS+ protocol as defined by Cisco Systems in draft 1.78 on TCP port 49.
ACS conforms to RADIUS protocol in the following RFCs:
• RFC 2138
• RFC 2139
• RFC 2284
• RFC 2865
• RFC 2866
• RFC 2867
• RFC 2868
• RFC 2869
The RADIUS ports used in AAA have changed in RFCs. ACS supports both the older and newer RFC-defined ports in its implementation. For authentication and authorization, ACS accepts requests on UDP port 1645 and UDP port 1812. For accounting, ACS accepts requests on both UDP port 1646 and UDP port 1813.
In addition to the AAA protocol support, ACS extends support to the following common password protocols for end-user authentication (see Figure 9-1):
• ASCII
• Password Authentication Protocol (PAP)
• Challenge Handshake Authentication Protocol (CHAP)
• AppleTalk Remote Access Protocol (ARAP)
• MS-CHAP v2
• Lightweight Extensible Authentication Protocol (LEAP)
• Extensible Authentication Protocol Message Digest 5 (EAP-MD5)
• Extensible Authentication Protocol Transport Layer Security (EAP-TLS)
• Protected Extensible Authentication Protocol (PEAP)
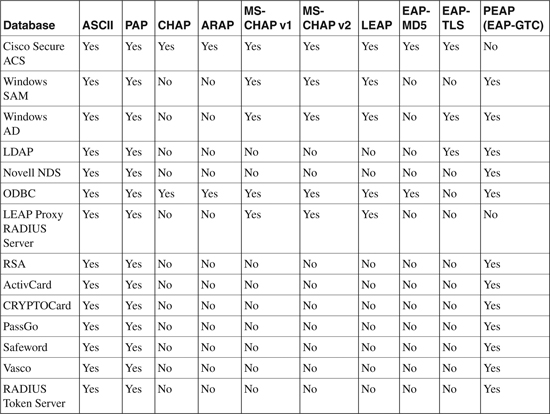
The implementation of the previously mentioned password protocol depends on the support of external databases available in ACS. Table 9-1 lists the Protocol-Database Compatibility reference supported by the various databases.
Table 9-1. Protocol-Database Compatibility
Advanced ACS Functions and Features
Cisco Secure ACS provides numerous functions and features that help secure and protect networks and resources within the network. These services are configured under various sections, as illustrated in Table 9-2, which can be found later in the chapter in the section “Configuring ACS.” Some of the advanced features commonly used are discussed in the sections that follow.
Shared Profile Components (SPC)
Shared Profiles are commonly used to group sets of authorization components that can be collectively applied to many users or groups and referenced by name within their profiles. These include Downloadable IP ACL, Network Access Restrictions (NAR), Network Access Filters (NAF), RADIUS Authorization Components (RAC), Command Authorization Sets, and other options. The following sections discuss some of these commonly used features.
The advantage of using Shared Profile Components is that it offers scalability by avoiding unnecessary repetitions in configuring long lists of devices for commands and other authorization parameters.
Downloadable IP ACLs
The Downloadable IP ACLs feature is used to offer per-user based ACL functionality. This feature is compatible with any Layer 3 network device that supports Downloadable IP ACLs functionality. ACS extends per-user ACL support in conjunction with NAF to allow the application of per-device specific filtering. NAF regulates the access control on the basis of a AAA client’s IP address. Hence, ACLs can be uniquely tailored on a per-user, per-device basis. Different sets of IP ACLs can be created that can be applied to various users or groups.
Before Downloadable IP ACLs were available, the RADIUS Cisco cisco-av-pair attribute [26/9/1] was used to achieve per-user filtering for each user or group. With Downloadable IP ACL, a single set of ACL can be defined and associated to each applicable user or group by referencing its name. This method is a more granular, easier-to-manage, and more scalable approach than configuring the RADIUS Cisco cisco-av-pair attribute for each user/group. RADIUS authentication is required to support the downloadable IP ACL feature.
The following Cisco devices support Downloadable IP ACL:
• PIX and ASA Firewalls
• VPN 3000 Concentrators
• Routers
Network Access Filter (NAF)
NAF is one of the newer features introduced in the ACS Shared Profile component.
Before NAF, per-device access restriction was not an option. The same level of access restrictions and ACLs were applied to all the devices in the network group. With NAF, granular application of access restrictions and downloadable ACLs is now possible, applying network-access restrictions and downloadable ACLs on network device names, network device groups (NDG), or their IP addresses. NAF can also use the IP address range and wildcards.
NAF can be defined as a named group with any combination of one or more of the following network elements:
• IP address
• AAA client (network device)
• Network device group (NDG)
Several applications of NAF exist. As discussed previously, NAF can be used in conjunction with Downloadable IP ACLs or in shared NARs to apply device-specific filtering and to regulate access control based on the AAA client’s IP address.
Note
NAF needs to be enabled on the Advanced Options page of the Interface Configuration section before it appears as a selection on the Shared Profile Components page.
RADIUS Authorization Components
The shared RADIUS Authorization Components (RAC) function is used to group RADIUS attributes that can be dynamically assigned to user sessions based on a certain policy. Using the “Network Access Profiles (NAP)” section of this chapter, you can map various policy types to a shared RAC with set conditions, such as NDGs and posture.
Shell Command Authorization Sets
Shell command authorization sets are also part of the SPC, providing a mechanism to control the authorization of each command in various privilege levels invoked by a user on any given device in the network. AAA must be configured on each network device to support command authorization sets.
Command authorization sets are used to group the commands into varying sets. These sets can then be applied to multiple users or groups within ACS, to offer per-user granular control to enforce restriction on which commands the users are able to execute per device.
Network Access Restrictions (NAR)
The NAR function is used to define additional conditions that must be met before a user can access the network. ACS applies these conditions to a single user or a group by using information from the attributes sent by the AAA clients.
NAR can be set up in several ways, but all of them work on the same principle—that of matching the attribute information received from the AAA client. Therefore, to effectively deploy NAR, it is important to understand the format of attributes sent by the AAA client.
NAR can be configured in two ways—positive or negative filtering. NAR can either be specified to permit or deny network access. However, if a NAR does not find sufficient information, it defaults to deny access.
Two types of NAR filters are available in ACS:
• IP-based filters: Limit network access based on the IP address of the end-user client and the AAA client.
• Non-IP-based filters: Limit access based on a simple string comparison of a value sent from the AAA client. This can be the command-line interface (CLI) number, the Dialed Number Identification Service (DNIS) number, the MAC address, or any other value originating from the client.
NAR filtering is applied in the following order of precedence:
1 Shared-NAR at the user level
2 Shared-NAR at the group level
3 Nonshared-NAR at the user level
4 Nonshared-NAR at the group level
Machine Access Restrictions (MAR)
Cisco Secure ACS supports machine authentication with Active Directory in Windows 2000 and 2003. ACS extends Windows machine authentication by providing the Machine Access Restriction (MAR) feature. The MAR feature, coupled with Windows machine authentication, is used to control authorization for users connecting via various protocols such as EAP-TLS, EAP-FASTv1a, and Microsoft PEAP when authenticating with a Windows external user database. Using MAR, you can impose tighter control to prevent users from passing machine authentication within a configurable length of time, and you can deny them access to a network altogether.
Network Access Profiles (NAP)
One of the recent features introduced in Cisco Secure ACS is called Network Access Profiles (NAP), also known as a profile. Profiles allow classification of incoming access requests according to their network location, membership in an NDG, protocol type, or other specific RADIUS attribute values that are sent by the network access device through which the user connects. Specific profiles can be mapped to AAA policies. For example, different access policies can be applied for users connecting through wireless and remote access VPNs.
NAP is essentially a profile-based authentication and authorization technique. It is a classification tool to identify a particular network-access request and apply a common policy based on the service request. NAP has several applications. Examples include VPN, NAC, and wireless local area network (WLAN). For example, when a user connects to the network through the VPN connection, the authentication can be forwarded to an external database, whereas if the same user connects via the wireless network, a local database can be used. ACS checks incoming requests against network access profiles. When a profile is matched, ACS pushes the configuration and policies to the client according to the profile filter during packet processing.
Cisco NAC Support
Cisco Secure ACS supports the Cisco Self-Defending NAC solution. NAC is a framework of integrated technologies and solutions built on an initiative led by Cisco Systems. NAC uses the network infrastructure to enforce security policy compliance on all endpoint devices seeking access to the network and network resources, thereby limiting damage from emerging security threats. NAC restricts network access only to compliant and trusted endpoint devices (such as PCs, servers, and PDA devices) and blocks network-access requests from noncompliant devices.
ACS acts as a policy enforcement point in NAC deployments by performing posture assessment (health checks) of the endpoint devices seeking network access. Posture validation is based on credentials received from the Posture Agent (PA) related to the endpoint device-type. The Cisco Trust Agent (CTA) acts as a PA in this scenario. Examples of posture validation policy include the type of operating system, service pack, patch levels, and other attributes, such as antivirus software and data (DAT) file versions. ACS performs the posture validation and applies per-user authorization, such as policy-based ACL or VLAN assignment, to the network device.
For more details on the Cisco NAC solution, refer to Chapter 13, “Network Admission Control (NAC).”
Configuring ACS
As discussed in the previous sections, ACS incorporates many technologies to render AAA services for network-access devices, thus providing a central access-control function. The basic overview of the ACS configuration menu with screenshots that follows illustrates the various ACS functions and features.
There are two basic ways to access the ACS web interface:
• On the server itself where ACS is installed, you can browse the ACS directly by typing http://loccalhost:2002 into the local web browser.
• You can also browse ACS remotely by typing http://ip_address_of_the_ACS:2002 into the web browser from another computer on the network.
Note
Ensure that there is IP connectivity to the ACS server before browsing remotely.
HTTP port 2002 is used for remote access capability to the IP address assigned to the ACS server. Use the administrative account to log in to the server. Note that the ACS administrator accounts are unique to the ACS server only. They are not related to other administrator accounts, such as those used by Windows users with administrator privileges. ACS administrator accounts have no correlation with the internal ACS database user accounts.
Note
By default, no username is configured for remote administration. Upon ACS installation, configure an administrative account by granting appropriate privileges to each ACS administrator and assigning relevant privileges for ACS management purpose only. By default, no privileges are granted to a new administrator account, unless Grant All is selected.
By default, an administrator account is not required to log into the ACS application from the local server where ACS is installed. However, it is strongly recommended that you enable logon from the local server. (Otherwise, a Windows-based administrator account will have full administrative rights to the ACS application.)
Tip
When ACS is running on Windows 2003, the ACS administrator account that runs the ACS services must have a Domain Administrator account to authenticate against Windows 2003.
Figure 9-2 shows the main menu page after the login is successful. On the main menu page, the left pane shows different submenu selection options with various configuration items. The middle screen displays the menu option selected, and an additional pane on the right will display a Help screen for the selected menu. The main menu page also displays the ACS version.
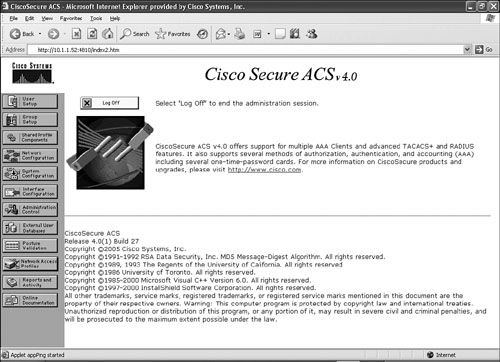
Table 9-2 illustrates the functions of the subitems available from the main menu shown in Figure 9-2.
Table 9-2. CS Main Menu Options
Figure 9-3. ACS User Setup Menu

Figure 9-4. ACS Group Setup Menu
Figure 9-5. ACS Shared Profile Components Menu
Figure 9-6. ACS Network Configuration Menu
Figure 9-7. ACS System Configuration Menu
Figure 9-8. ACS Interface Configuration Menu
Figure 9-9. ACS Administration Control Menu
Figure 9-10. ACS External User Databases Menu
Figure 9-11. ACS Posture Validation Menu
Figure 9-12. ACS Network Access Profiles Menu
Figure 9-13. ACS Reports and Activity Menu
Figure 9-14. ACS Online Documentation Menu
Cisco Secure ACS Appliance
Cisco Secure ACS Solution Engine (ACS SE) is a highly scalable appliance, 1U rack-mountable dedicated platform that serves as a high-performance access control server supporting centralized RADIUS and TACACS+ security protocols.
ACS SE offers the same set of functions and features as the Cisco Secure ACS software for Windows (the software product discussed earlier) in dedicated, security hardened, application-specific appliance packaging.
The underlying operating system on the ACS SE appliance is a customized and minimized version of the Windows 2000 operating system. The fact that the underlying operating system is robust Windows ensures absolute protection. ACS SE achieves this by implementing the following attributes:
• Runs only selective services required to perform the ACS core functions
• Removes all extraneous services
• Blocks all unused ports
• Does not support a keyboard or monitor
• Does not provide access to its file system
• Does not allow arbitrary applications to run
• Prevents all other access to the ACS server system
• Allows TCP/IP connections only via the ports necessary for its own operations
ACS SE includes some additional features specific to operating and managing the ACS appliance. These system administrative functions can be administered using the command-line application (shell) that operates the CLI via the serial console connection that is available on ACS SE appliance. For all other ACS SE configuration and administrative tasks, use the ACS web interface in the software described earlier. Some of these system-specific functions are as follows:
• Resetting the administrator username/password
• Resetting the system database password
• Reconfiguring the IP address
• Setting system timeouts
• Setting the system date/time/hostname/domain
• Patching rollback (removing installed patches)
• Recovering from loss of administrator credentials (password recovery)
• Reimaging the hard drive
Caution
Powering off the ACS SE by using only the power switch may cause the loss or corruption of data. To shut down the ACS SE, log in to the ACS SE from a serial console, and at the system prompt, type shutdown, and then press Enter. The ACS SE displays the message It Is Now Safe to Turn Off the Computer. At this point, press the power switch and hold it down for four seconds to turn off the ACS SE.
Summary
Cisco Secure ACS software and appliance engine provide a centralized network access control server to safeguard the network infrastructure resources from unauthorized access. ACS offers a network-access management solution and enforces policy-based solutions that use centralized RADIUS and TACACS+ security protocols and the AAA framework.
ACS provides a comprehensive identity-based network access control solution for intelligent information networks.
The chapter illustrated basic functions provided by the ACS software and illustrations of various features available. The chapter also provided a basic overview of implementing and configuring the Cisco Secure ACS server and its web interface.
The chapter concluded with a basic overview of the ACS SE, which is a dedicated security-hardened platform appliance that offers the same set of functions and features as available in the Cisco Secure Access ACS software for Windows.
References
User Guide for Cisco Secure ACS for Windows 4.0: http://tinyurl.com/yvajyj
Cisco Secure Access Control Server for Windows: http://tinyurl.com/qfxk7
Cisco Secure Access Control Server Solution Engine: http://tinyurl.com/b9dkd