Chapter 23. Security Monitoring and Correlation
The monitoring and correlation of network security infrastructure in the modern day network is becoming a challenge because each network component generates its own set of logs, events, alerts, and various notification messages, thereby creating a massive collection of event logs for analysis and investigation.
Cisco Security Monitoring, Analysis, and Response System (CS-MARS) is a comprehensive appliance-based solution providing security information and event management. CS-MARS offers network intelligence to identify and correlate events, pinpoint attack paths, and provide comprehensive security threat control and mitigation.
This chapter provides details of the appliance-based security information management (SIM) system that uses the industry standard CS-MARS solution.
The chapter takes a closer look at the core concepts of the CS-MARS appliance and its features and capabilities, and highlights the key concepts such as events, sessions, rules, and incidents.
The chapter gives an overview of the various deployment scenarios and implementation of the CS-MARS solution using the Standalone, Local Controllers (LC), and Global Controllers (GC) options. The chapter provides an overview of the CS-MARS web-based management interface and a basic overview of configuring CS-MARS appliance.
Security Information and Event Management
Security information and event management systems provide network intelligence by aggregating security events and logs from various network devices, analyzing the logs through various querying and correlation technology techniques, and generating meaningful reports regarding network anomalies and security events occurring within the network.
CS-MARS is a comprehensive security information and event management solution that identifies, manages, and mitigates security threats. CS-MARS integrates with the existing network and security infrastructure and is capable of discovering the existing network. CS-MARS can be an integral part of maintaining and enforcing the overall security policy and regulatory compliance solution.
Cisco Security Monitoring, Analysis, and Response System (CS-MARS)
CS-MARS is an appliance-based security information management (SIM) system providing security monitoring and correlation services to identify, contain, and respond to networkwide security threats.
CS-MARS is another key solution that extends the Cisco Self-Defending Network initiative and essential deployment for a security information management system.
CS-MARS offers network intelligence by using sophisticated event correlation technology to precisely identify and correlate events, validate threats, pinpoint attack paths, and provide comprehensive security threat control and mitigation solutions. Through various techniques, CS-MARS maps the entire network, thereby providing complete network visibility and reaction capability by leveraging data from all over the network.
Table 23-1 provides a summary of the common features and capabilities of the CS-MARS appliance-based security information management solution.
Table 23-1. CS-MARS Features and Capabilities
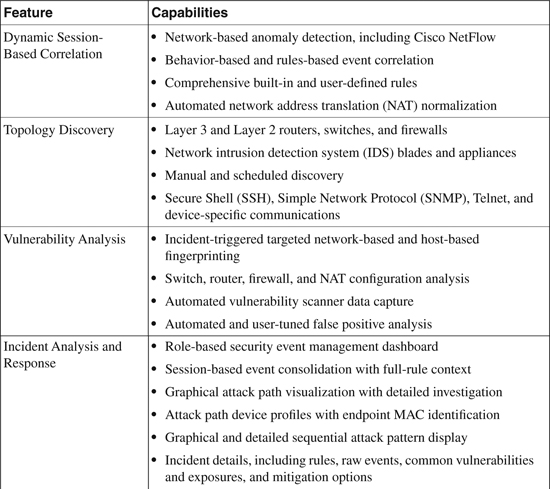
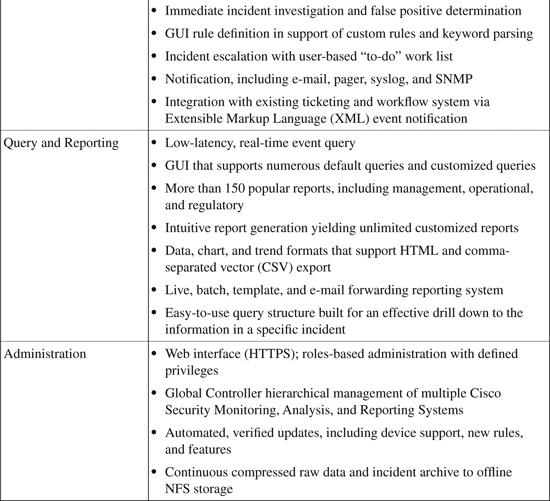
The information in Table 23-1 is compiled from Cisco Security Monitoring, Analysis, and Response System 4.3.1 and 5.3.1 at http://www.cisco.com/en/US/products/ps6241/products_data_sheet0900aecd80272e64.html.
Security Threat Mitigation (STM) System
CS-MARS is a state-of-the-art security threat mitigation (STM) system providing cutting-edge capabilities. New advanced STM features include data sessionization, topological awareness, and mitigation capabilities.
CS-MARS offers security countermeasures by combining state-of-the-art network intelligence, context correlation using the ContextCorrelation feature, vector analysis using the SureVector feature, anomaly detection, hotspot identification, and automated mitigation using the AutoMitigate capabilities. These are defined in the list that follows:
• Cisco ContextCorrelation: CS-MARS software includes an integrated ContextCorrelation feature that performs data normalization against the topology by processing the captured raw events and logs, device configurations, and same source and destination applications across Network Address Translation (NAT) boundaries. Corresponding events are grouped into sessions in real-time. System-defined and user-defined correlation rules are then applied to multiple sessions to identify meaningful incidents. CS-MARS has a default set of comprehensive predefined rules, which identify a majority of common anomaly scenarios and day-zero attacks. ContextCorrelation significantly reduces raw event data by packaging the incidents into groups, rather than individual data points.
• Cisco SureVector: CS-MARS software includes the integrated SureVector analysis engine that allows the processing of similar event sessions to determine whether threats are valid and have been successful in causing damage. CS-MARS validates threat information by performing endpoint scans to eliminate false positives and by using the SureVector™ engine to investigate the raw data, device logs, and third-party vulnerability assessment data. Further fine-tuning of the system can reduce additional false positives.
• Cisco AutoMitigate: CS-MARS software includes an integrated AutoMitigate feature that allows a real-time dynamic mitigation solution to stop the attacks. CS-MARS can identify the offending and compromised system down to the endpoint MAC address. Using the AutoMitigate feature, CS-MARS can identify available devices along the attack path and dynamically provide mitigation recommendations by suggesting the relevant device commands and configurations that can be deployed on a particular device to quickly and accurately prevent or contain an attack.
Figure 23-1 shows CS-MARS with extended security threat mitigation (STM) system capabilities of using Cisco ContextCorrelation, SureVector, and AutoMitigate features.
CS-MARS offers an automated event log collection system capturing data from various heterogeneous network devices (Layer 2 and Layer 3) across multiple devices such as routers, switches, firewalls, IDS, IPS, and server-based systems, aggregating all into a centralized database to perform intelligent correlation and to group related events of the same traffic flow.
Figure 23-1. CS-MARS—Security Threat Mitigation (STM) System
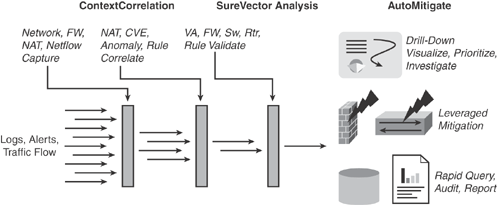
Figure 23-2 depicts how CS-MARS works by capturing raw data and configuration from various devices and processing the isolated events, performing analysis, and correlating threat information into valid incidents, thus greatly reducing false positives.
Figure 23-2. CS-MARS—How It Works
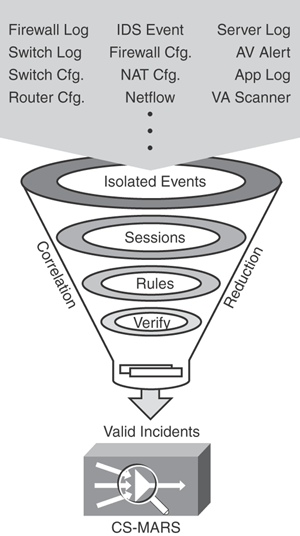
CS-MARS uses a policy-based approach to block security attacks by transforming raw data into actionable intelligence, identifying and correlating real security threats, and providing recommendations for mitigation recommendations.
Topological Awareness and Network Mapping
CS-MARS builds topological awareness and paints network maps of the entire topology by performing discovery of the network devices within the network. CS-MARS is capable of capturing a wide range of Cisco and non-Cisco devices, including Layer 2 and Layer 3 devices.
CS-MARS has an integrated network discovery function that builds a topology map containing device configuration and current security policies, which enables it to model packet flows through a network.
CS-MARS reads a network device configuration and populates into a central database, allowing the construction of a complete topological map of the network.
CS-MARS provides network behavioral analysis by profiling network traffic, capturing raw data, and aggregating and correlating from heterogeneous devices from a wide range of devices in a single CS-MARS appliance.
Figure 23-3 shows CS-MARS capturing raw data and configuration files from various heterogeneous network devices (Layer 2 and Layer 3).
Figure 23-3. CS-MARS—Receiving Raw Data from Cisco and Non-Cisco Devices
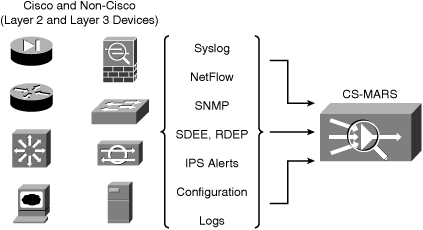
CS-MARS is capable of receiving high volumes of data with its secure and stable architecture. It can receive more than 15,000 events per second or more than 300,000 Cisco NetFlow events per second.
CS-MARS offers a high-performance aggregation and consolidation service by capturing millions of raw events and grouping them efficiently into classified incidents with unprecedented data reduction.
CS-MARS is able to deliver high-performance correlation through inline processing logic and the use of an embedded high-performance database system.
Table 23-2 is a list of supported reporting devices (Cisco and non-Cisco) that can be captured by CS-MARS appliance.
Table 23-2. CS-MARS Device Support List
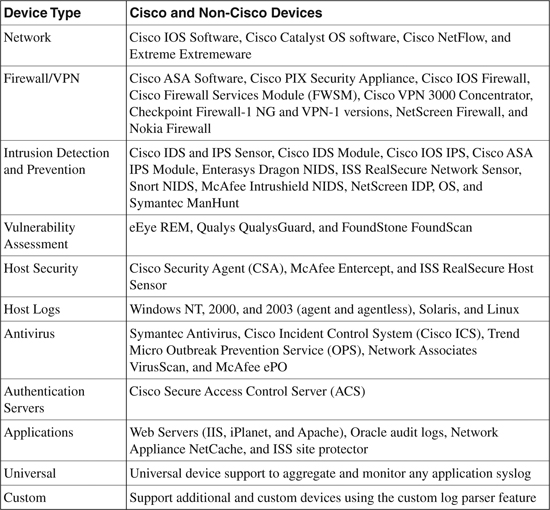
The information in Table 23-2 is compiled from Cisco Security Monitoring, Analysis, and Response System 4.3.1 and 5.3.1 at http://www.cisco.com/en/US/products/ps6241/products_data_sheet0900aecd80272e64.html.
Note
CS-MARS continues to improve its device support. For a comprehensive, up-to-date list with supported version information, refer to the following URL: http://www.cisco.com/en/US/products/ps6241/products_device_support_tables_list.html.
Key Concepts—Events, Sessions, Rules, and Incidents
CS-MARS uses various terms to define contextual analysis and the process of threat investigation. These may vary from the traditional terminologies used for other systems:
• Event: Each log event (raw data) received by CS-MARS from any reporting device (such as syslog, SNMP trap, NetFlow, IPS alert, Security Device Event Exchange (SDEE), or Windows log) is referred to as an event in CS-MARS. Retrieved raw messages from the reporting devices are mapped into events.
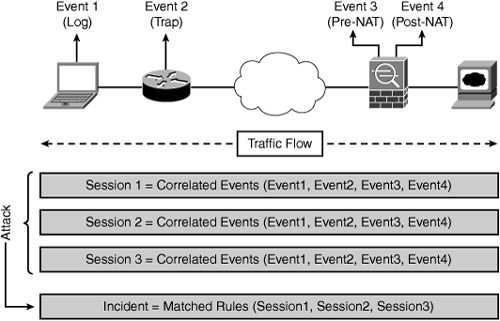
• Sessions: Correlated events that are related to the same network flow received from one or more devices. The session is created for like events that are common to a particular criteria—for example, timestamp, source IP address, source port, destination IP address, destination port, or protocol information. Figure 23-4 depicts a CS-MARS session.
• Rule: Used to perform logic on events that create sessions and incidents. A rule defines patterns of normalized event types and the notification action CS-MARS will take when the rule fires. These patterns can be signatures of attacks, probes, configuration errors, or anomalous network traffic behavior. CS-MARS has two types of rules: inspection rules and drop rules.
• Incident: A session matched against a rule that is indicative of malicious behavior. An incident is triggered when a rule or collection of rules matched. As shown in Figure 23-5, incidents can contain one or more events detailing the event correlation, such as a complete story of an attack. Rules fire to create incidents.
Figure 23-4 depicts how a session is interpreted in CS-MARS.
Figure 23-4. CS-MARS—Session Interpretation
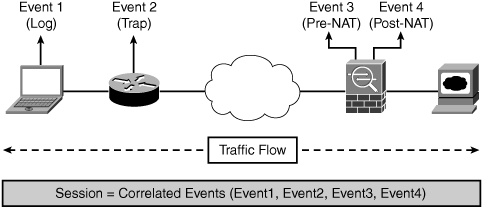
Figure 23-5 depicts how an incident is interpreted in CS-MARS.
Figure 23-5. CS-MARS—Incident Interpretation
Event Processing in CS-MARS
CS-MARS uses the following steps to process events when it receives a raw message.
1 Receive raw messages from network devices either via pulling mode or listening mode
2 Parse raw messages
3 Normalize raw messages to events—statically map raw messages from different vendor devices to CS-MARS known event types
4 Sessionization/NAT correlation—identify commonality within the event, such as source IP/port, destination IP/port, protocol to sessionize events
5 Run events against rule engine
6 False positive analysis
7 Vulnerability assessment against suspected hosts
8 Traffic profiling and statistical anomaly detection
Figure 23-6 shows the event process flowchart in CS-MARS.
Figure 23-6. CS-MARS Event Process Flowchart
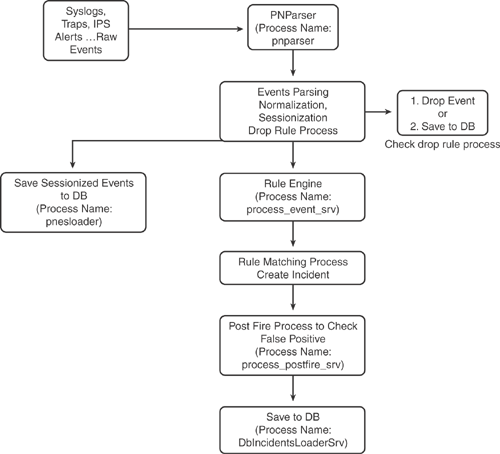
The information in Figure 23-6 is compiled from the Cisco Networkers Breakout Session presentation #BRKSEC-3006—Network Security Monitoring and Correlation with CS-MARS.
False Positive in CS-MARS
CS-MARS interprets false positives differently than other systems. In general terms, when a message is considered a false positive, this means that a system has incorrectly identified an attack but in reality it did not happen. However, in CS-MARS a false positive means the attack was identified correctly but it was unsuccessful against the target victim.
There are four basic types of false positives in CS-MARS:
• System Confirmed False Positive
• User Confirmed False Positive
• User Confirmed Positive
Figure 23-7 illustrates the false positive process flowchart in CS-MARS.
Figure 23-7. CS-MARS False Positive Process Flowchart
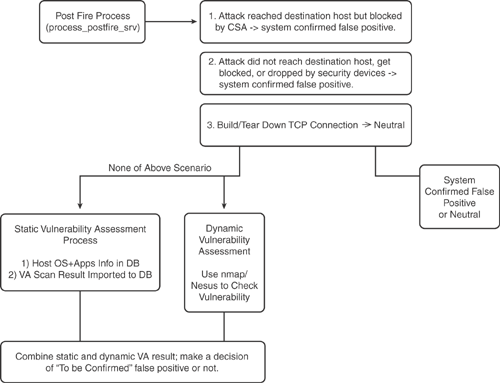
The information in Figure 23-7 is compiled from the Cisco Networkers Breakout Session presentation #BRKSEC-3006—Network Security Monitoring and Correlation with CS-MARS.
Deploying CS-MARS
There are several ways to deploy CS-MARS appliance into the network. Careful planning is required before considering and selecting the appropriate CS-MARS model. The decision greatly depends on the anticipated events per second (EPS) and NetFlow flows per session (FPS) for that network or segment.
The following are two types of CS-MARS deployment scenarios:
• Standalone: A single CS-MARS is deployed into the network collecting raw data from one or more network devices. Standalone deployment is also referred to as Local Controller (LC).
• Global: Two or more LCs are deployed into the network collecting raw data from various network devices. In this setup, a separate Global Controller (GC) CS-MARS appliance is required to manage the LC. The GC does not receive raw data from the reporting devices; it is only used to manage the LC and overall CS-MARS deployment.
Standalone and Local Controllers (LC)
There is no major difference between LC and standalone CS-MARS deployments. Both scenarios use the same hardware and software. The only difference is that standalone is an independent, fully operated CS-MARS deployment, whereas LC works in conjunction with GC and communicates primarily with the GC.
The LC performs the following functions:
• Collects all raw events from various devices
• Sessionizes events across different devices
• Applies inspection rules for incidents
• Performs false positive analysis
• Delivers consolidated information in diagrams, charts, queries, reports, and notifications
• Detects inactive reporting devices
• Derives set of IOS/IPS Distributed Threat Mitigation (DTM) signatures based on attacks reported by monitored Cisco IPS appliances
• Acts as a repository for the IOS/IPS DTM signatures, from which IOS/IPS devices can download current signature sets
Each LC model differs in its capability to process and store events from various reporting devices.
Table 23-3 shows a complete list of CS-MARS models and their capabilities (EPS and FPS) that can be deployed as local and standalone controllers.
Table 23-3. CS-MARS Local and Standalone Controllers
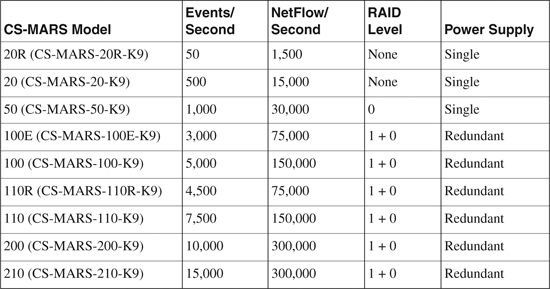
The Events per Second (EPS) listed in Table 23-3 are quoted as the maximum events per second with dynamic correlation and all other features enabled.
If high availability is required in CS-MARS deployment, begin at a CS-MARS model 100 (CS-MARS-100-K9), which has RAID 1 + 0 capabilities. The models with RAID 1 + 0 have redundant power supplies and hot swappable drives. The CS-MARS models 110 (CS-MARS-110-K9) and 210 (CS-MARS-210-K9) have special built-in battery backups for RAID cache.
LCs receive and pull raw data from a wide range of reporting devices, such as routers, switches, firewalls, IDS/IPS systems, and vulnerability assessment systems.
The LC summarizes information about the health of the network based on data it receives from the reporting devices that it monitors.
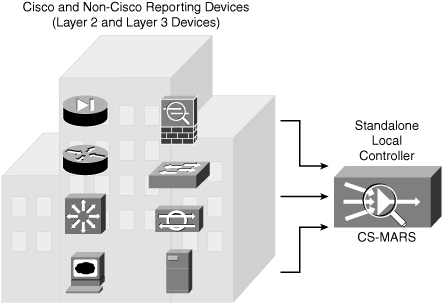
Figure 23-8 depicts a standalone LC being deployed as an independent appliance and is a fully operated CS-MARS implementation.
Figure 23-8. CS-MARS Standalone Local Controller (LC)
Global Controllers (GC)
The Global Controller (GC) is used to manage two or more LC zone deployments allowing scaling of the network monitoring without increasing the management burden on the LC.
The GC provides complete control and management of the LC across various sites (zones) and provides a single user interface for defining new device types, inspection rules, reports, and queries.
GC provides a central console to manage multiple LCs. It also provides additional capabilities, including
• Global authentication across all LCs
• Unified report generation across all LCs
• Unified rule generation for LC deployment
• Global view of the network
• Centralized software management
• Reduced traffic across WAN links
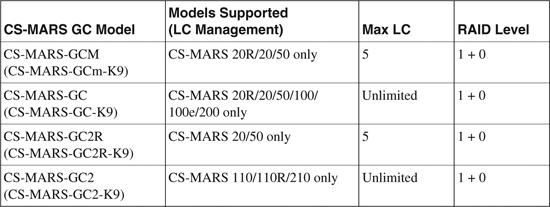
Three basic CS-MARS models are available for GC deployment scenarios.
Table 23-4 shows a complete list of CS-MARS models and their capabilities for GC deployments.
Table 23-4. CS-MARS Global Controllers (GC)
Note
All CS-MARS GC models have redundant power capability.
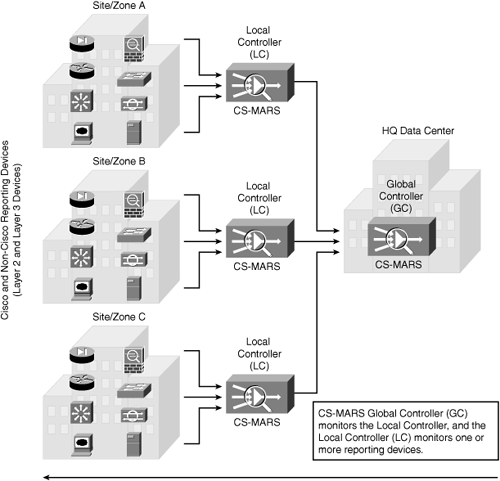
Figure 23-9 depicts a GC scenario deployed at the central HQ Data Center managing several LCs across different sites.
Software Versioning Information
Two major software versions are available in CS-MARS deployment. There is significant feature parity across the two releases supporting different hardware platforms. The appliance model has little impact on the available features support across the two releases.
• Software Version 4.3.x: The 4.3.x software release supports the CS-MARS models MARS-20R, MARS-20, MARS-50, MARS-100e, MARS-100, MARS-200, MARS-GCM, and MARS-GC appliances.
• Software Version 5.3.x: The 5.3.x software release supports features on new appliance CS-MARS models MARS-110R, MARS-110, MARS-210, MARS-GC2, and MARS-CG2R.
Note
Database table structure changes between software versions; thus, an existing database cannot be restored onto a different software version, because it can cause data corruption. If you do not require preserving any configuration and event data, it is better to start with a clean system. Reimaging it can be much faster than the upgrade procedure.
Figure 23-9. CS-MARS Global Controller
Reporting and Mitigation Devices
From a top-down deployment perspective (refer to Figure 23-9), CS-MARS GC monitors the LC, and the LC monitors one or more reporting devices.
A reporting device is any Layer 2 or Layer 3 device (Cisco or non-Cisco) that provides CS-MARS with raw data about the network from traffic flows and the configuration files, allowing CS-MARS to analyze and respond to possible attack targets.
A mitigation device is any reporting device that can deny a traffic flow within the attack path.
CS-MARS provides mitigation support in two forms:
• For supported Layer 3 devices, CS-MARS provides recommendations for a suggested Layer 3 device for mitigation and a set of corresponding commands that can be used to stop an ongoing, detected attack. This information can also be used to manually block the attack.
• For supported Layer 2 devices, CS-MARS provides recommendations for a suggested Layer 2 device for mitigation and a set of corresponding commands to stop the ongoing detected attack.
Note
Refer to Table 23-2 for a complete list of the supported reporting devices.
Based on the confirmed incident and correlated data, CS-MARS provides suggested mitigation rules for detected attacks and, in some cases, it can push those rules to the mitigation device, to stop the attack by restricting network access to the infected hosts.
Figure 23-10 illustrates an example of CS-MARS recommendation for enforcement that points along the attack path with a set of corresponding commands to stop the attack.
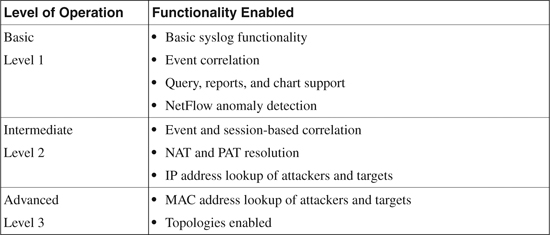
Levels of Operation
Another important consideration to be taken into account when deploying CS-MARS is the type of operation that CS-MARS will perform. This needs to be decided before CS-MARS is configured to receive raw data from reporting devices.
Three basic levels of operation exist in CS-MARS, based on the type of data it can collect from the reporting device. These levels dictate the capability of CS-MARS to identify attacks from end to end:
• Basic: At the basic level 1, CS-MARS performs similar to a smart Syslog server, collecting logs from the reporting devices and supporting routine queries and basic reports.
• Intermediate: At the intermediate level 2, CS-MARS processes isolated events and performs session-based correlation, including resolving NAT and PAT translations at the IP address layer.
• Advanced: At the advanced level 3, CS-MARS functions at its full potential with all its capabilities. When advanced operation is enabled, the CS-MARS appliance discovers and displays the full topology, draws attack paths, and enables MAC address lookups of the hosts involved in an attack.
Figure 23-10. CS-MARS Mitigation Device Identified and Corresponding Commands Recommended
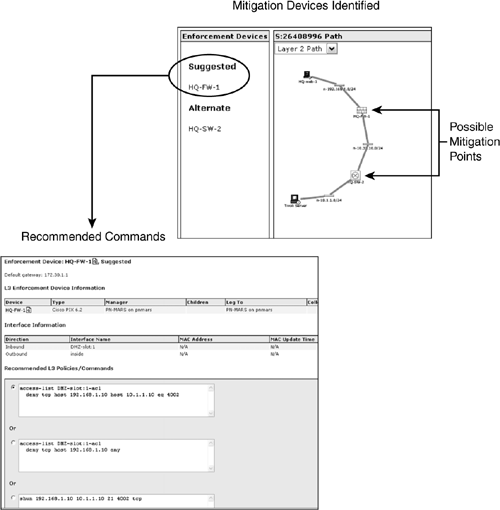
Table 23-5 summarizes the CS-MARS level of operations and the functionality enabled at each level.
Table 23-5. CS-MARS Level of Operation and Functionality
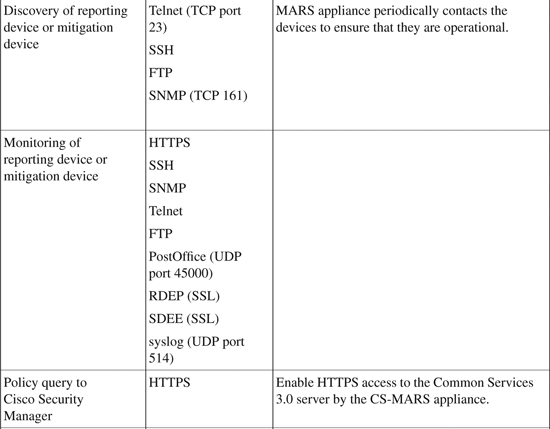
Traffic Flows and Ports to Be Opened
Required traffic flows identify the necessary protocol and port numbers that must be allowed by gateways/firewalls/ACLs if they separate the CS-MARS appliance from a reporting device, mitigation device, or supporting device (as listed in Table 23-2). Different protocol and port numbers are used for varying functions when CS-MARS communicates with a reporting device.
Additionally, traffic flows between a GC and any monitored LCs must be allowed.
Table 23-6 identifies the various traffic flows and their associated protocol and port numbers that must be opened if there is a gateway, firewall, ACL, or any type of filtering device between CS-MARS and the reporting devices.
Table 23-6. CS-MARS Required Traffic Flows and Ports to Be Opened
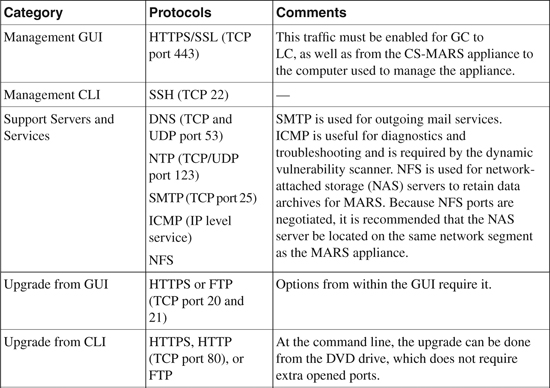
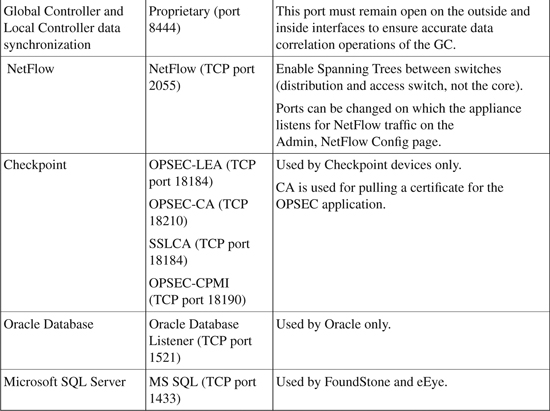
The information in Table 23-6 is compiled from “Install and Setup Guide for Cisco Security MARS, Release 5.2.x” at http://www.cisco.com/en/US/docs/security/security_management/cs-mars/5.2/installation/guide/plan.html.
In addition to the listings in Table 23-6, if the GC and LC are separated by a firewall or any type of filtering device, the ports listed in Table 23-7 need to be allowed explicitly, on both the inside and outside interfaces of the firewall, to ensure proper operation of the GC.
Table 23-7. CS-MARS Required Traffic Ports to Be Opened for Global Controller to Local Controller Communication
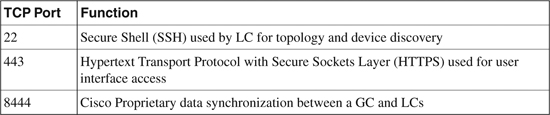
The information in Table 23-7 is compiled from “User Guide for Cisco Security MARS Global Controller, Release 5.2.x” at http://www.cisco.com/en/US/docs/security/security_management/cs-mars/5.2/user/guide/global_controller/gccfg.html.
Web-Based Management Interface
The CS-MARS appliance can be centrally managed through a secure web-based interface supporting role-based administration.
The web-based management interface is easy to use and user friendly using a tabbed, hyperlinked, browser-based interface approach. The web-based interface can be accessed from any computer on the network that has IP reachability to the CS-MARS appliance. The web-based management interface can be used to perform all administrative functions.
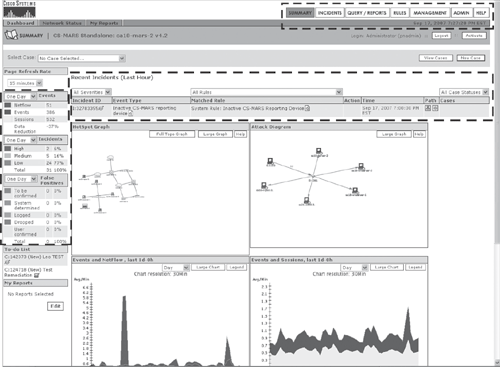
Figure 23-11 shows a sample output of CS-MARS web-based management interface dashboard (Summary page).
Figure 23-11. CS-MARS—Management Dashboard Summary Page
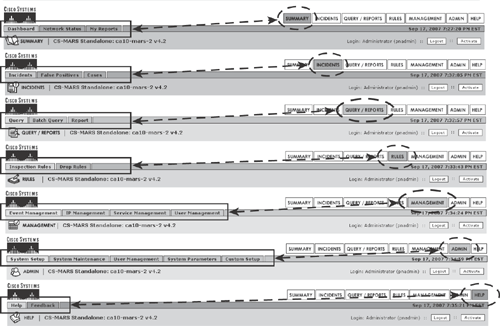
As shown in Figure 23-12, the web-based management interface offers seven menu option tabs in the right corner, which further allow navigating to the pages relevant to the tab’s subtabs. Figure 23-12 shows sample outputs from each of the seven menu option tabs and their subtabs from the management interface dashboard.
Figure 23-12. CS-MARS Web-Based Management—Seven Menu Option Tabs and Subtabs
Initializing CS-MARS
Depending on the LC or GC, and whether you are using software version 4.3.x or version 5.3.x, several parameters need to be configured on the CS-MARS appliance system. These can either be configured via the CLI console or the web-based management interface.
After booting the CS-MARS appliance for the first time, you need to configure the following basic parameters as part of the initialization process using the CLI console. Basic parameters include the following:
• Hostname
• IP address and subnet mask
• Default gateway addresses
• DNS server IP addresses (if DNS is used)
• NTP server address (if NTP is used)
• Time, date, and time zone
Login via the console access to the CS-MARS system using the default administrative user account and password (pnadmin/pnadmin) to complete the basic initialization process.
After the CS-MARS appliance is initialized, all the remaining tasks, such as adding the reporting and mitigation devices, can be completed using the web-based management interface, as shown in Figure 23-12, using a standard web browser from any client PC on the network as follows:
Note
Prior to using the system, the device license must be installed from the web console as the first step.
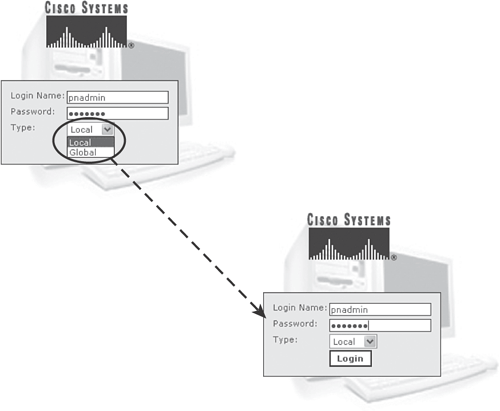
Figure 23-13 shows the default login page for the CS-MARS appliance. Indicate whether it is an LC or a GC and log in using the default administrative user account and password (pnadmin/pnadmin) or any other user account provided by the administrator.
Figure 23-13. Default Login Page for CS-MARS Appliance
Tip
For a comprehensive list of configurations and the user guide, refer to the following Cisco documentation pages: http://www.cisco.com/en/US/products/ps6241/products_user_guide_list.html.
Summary
Because of increased security attack frequency, security monitoring and correlation of network infrastructure is extremely crucial. The result is that each component within the infrastructure is enabled to generate various logs and alerts to yield essential information to aid forensic analysis, auditing, and threat mitigation. Unfortunately, this generates a tremendous amount of raw data for the end user to analyze and effectively utilize for security threat mitigation.
The Cisco Security Monitoring, Analysis, and Response System (CS-MARS) appliance-based security information management (SIM) system offers a comprehensive solution to address this issue.
The CS-MARS offers network intelligence to precisely identify and correlate events, pinpoint attack paths, and provide a comprehensive security threat control and mitigation solution.
This chapter provided an overview of the CS-MARS solution using various illustrations.
The chapter provided the core concepts of the CS-MARS appliance and its features and capabilities, and highlighted the key concepts necessary to understanding and implementing the CS-MARS solution.
The chapter provided an overview of CS-MARS deployment scenarios and a basic overview of configuring CS-MARS appliance. For more information on CS-MARS deployment setups and configurations, refer to the following:
Security Monitoring with Cisco Security MARS
http://www.ciscopress.com/title/1587052709
Security Threat Mitigation and Response: Understanding Cisco Security MARS, Adobe Reader
http://www.ciscopress.com/title/1587054086
References
http://www.cisco.com/en/US/products/ps6241/products_data_sheet0900aecd805cae35.html
http://www.cisco.com/en/US/products/ps6241/products_data_sheet0900aecd80272e64.html
http://www.cisco.com/univercd/cc/td/doc/product/vpn/ciscosec/mars/5_2/uglc5x/taskflow.htm#
http://www.cisco.com/en/US/products/ps6241/prod_quick_installation_guide09186a0080851b91.html
http://www.cisco.com/en/US/products/ps6241/products_installation_guide_book09186a008083b016.html
http://www.cisco.com/en/US/products/ps6241/products_user_guide_book09186a008083e365.html
http://www.cisco.com/en/US/products/ps6241/products_user_guide_book09186a008084ffa8.html
http://www.cisco.com/en/US/products/ps6241/products_installation_guide_chapter09186a008083b6d0.html
http://www.cisco.com/en/US/products/ps6241/prod_installation_guides_list.html
http://www.cisco.com/en/US/products/ps6241/products_user_guide_list.html
http://www.ciscopress.com/title/1587052709
http://www.ciscopress.com/title/1587053322
Networkers Breakout Session: BRKSEC-3006—Network Security Monitoring and Correlation with CS-MARS