Chapter 11
Endpoint Protection and Detection
This chapter covers the following topics:
Introduction to Endpoint Protection and Detection
The following SCOR 350-701 exam objectives are covered in this chapter:
Domain 5.0 Endpoint Protection and Detection
5.1 Compare Endpoint Protection Platforms (EPP) and Endpoint Detection & Response (EDR) solutions
5.2 Explain antimalware, retrospective security, indicator of compromise (IOC), antivirus, dynamic file analysis, and endpoint-sourced telemetry
5.3 Configure and verify outbreak control and quarantines to limit infection
5.4 Describe justifications for endpoint-based security
5.5 Describe the value of endpoint device management and asset inventory such as MDM
5.7 Describe endpoint posture assessment solutions to ensure endpoint security
5.8 Explain the importance of an endpoint patching strategy
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz allows you to assess whether you should read this entire chapter thoroughly or jump to the “Exam Preparation Tasks” section. If you are in doubt about your answers to these questions or your own assessment of your knowledge of the topics, read the entire chapter. Table 11-1 lists the major headings in this chapter and their corresponding “Do I Know This Already?” quiz questions. You can find the answers in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes and Q&A Sections.”
Table 11-1 “Do I Know This Already?” Section-to-Question Mapping
Foundation Topics Section |
Questions |
Introduction to Endpoint Protection and Detection |
1 |
Cisco AMP for Endpoints |
2–9 |
Cisco Threat Response |
10 |
1. Which of the following is not a feature of the AMP solution?
File reputation
File sandboxing
File retrospection
Web content filtering and redirect
2. You are hired to deploy AMP for Endpoints. In order to allow a connector to communicate with Cisco cloud servers for file and network disposition lookups, a firewall must allow the clients to connect to the Cisco servers over which of the following protocols and ports?
TCP port 443 and TCP port 80
TCP port 443 or TCP port 32137
UDP port 32137 and TCP port 443
TCP port 443, UDP port 53, and UDP port 500
3. Which of the following AMP for Endpoints features allow you to create lists for Custom Detections, Application Control, Network, and Endpoint indicators of compromise (IOC)?
Inbox feature
Group Policies
Outbreak Control
None of these answers is correct.
4. Advanced custom detections offer many more signature types to the detection, including which of the following?
File body–based signatures
MD5 signatures
Logical signatures
All of these answers are correct.
5. You can use outbreak control IP lists in conjunction with _____ detections, which allows you to flag or even block suspicious network activity.
device flow correlation (DFC)
PAC files
group policies
AVC
6. You are hired to deploy AMP for Endpoints, and one of the requirements is that you must use an exclusion set to resolve conflicts with other security products or mitigate performance issues by excluding directories that contain large files that are frequently written to, like databases. Which of the following is an exclusion type available in AMP for Endpoints that can help you accomplish this task?
Threat-based exclusion
Extension-based exclusion
Wildcards
All of these answers are correct.
7. Cisco AMP for Endpoints has connectors for which of the following operating systems?
Windows
macOS
Android
All of these answers are correct.
8. Which of the following is used by the Cisco ESA to handle incoming SMTP connection requests? These entities demarcate the email-processing service configured on a Cisco ESA interface.
WCCP redirects
MX records
SMTP MSAs
Listeners
9. Which of the following clients allow you to aid the distribution of the AMP for Endpoints connector and can be used for remote access VPN, secure network access, and posture assessments with Cisco’s Identity Services Engine?
DUO
AnyConnect
Tetration
Cisco SMA
10. Which of the following is a “one-pane-of-glass” console that automates integrations across Cisco security products (including AMP for Endpoints) and threat intelligence sources?
Cisco SMA
Cisco Threat Response (CTR)
Tetration
Firepower Management Console
Foundation Topics
Introduction to Endpoint Protection and Detection
Throughout this book, you have been learning about the various technologies that can also help detect threats in endpoint devices. You have learned that security technologies and processes should not just focus on detection but should also provide the capability to mitigate the impact of an attack. Organizations must maintain visibility and control across the extended network during the full attack continuum:
Before an attack takes place
During an active attack
After an attacker starts to damage systems or steal information
In Chapter 4, “Authentication, Authorization, Accounting (AAA) and Identity Management,” you learned about the Cisco ISE, 802.1X, Network Access Control (NAC), endpoint posture assessment, and how clients like AnyConnect are used to interact with network devices and Cisco solutions to protect not only the endpoint, but also the underlying network. You also learned the uses and importance of a multifactor authentication (MFA) strategy.
In Chapter 7, “Cisco Next-Generation Firewalls and Cisco Next-Generation Intrusion Prevention Systems,” you learned all about the components that make up the AMP architecture and the AMP cloud.

In Chapter 7, you also learned that the AMP solution enables malware detection, blocking, continuous analysis, and retrospective views with the following features:
File reputation: AMP allows you to analyze files inline and block or apply policies.
File sandboxing: AMP allows you to analyze unknown files to understand true file behavior.
File retrospection: AMP allows you to continue to analyze files for changing threat levels.
This chapter will go over the Cisco Advanced Malware Protection (AMP) for Endpoints in more detail. This chapter looks at where AMP for Endpoints fits into the AMP architecture. You’ll also learn about the types of AMP for Endpoints connectors, how to create policies for them, and how to install them. The chapter describes how to use the AMP cloud console, and you will even get a look at AMP detecting and remediating malware.

Endpoint Threat Detection and Response (ETDR) and Endpoint Detection and Response (EDR)
Before diving deep into AMP for Endpoints, let’s define what the industry refers to as Endpoint Threat Detection and Response (ETDR) and Endpoint Detection and Response (EDR). Gartner defines EDR as the “tools primarily focused on detecting and investigating suspicious activities (and traces of such) other problems on hosts/endpoints.”
EDR solutions monitor endpoint and network events and record the information in a central database so that you can perform further analysis, detection, investigation, and reporting. Typically, software (an agent) is installed on the endpoint that allows ongoing monitoring and detection of potential security threats.
The minimum capabilities of a good EDR solution are as follows:
Filtering: The ability to filter out false positives (to help reduce “alert fatigue,” which increases the potential for real threats to go undetected).
Threat blocking: At the end of the day, the EDR solution must be able to contain the threats, not just detect them.
Help with digital forensics and incident response (DFIR): The ability to allow an organization to effectively perform DFIR tasks, as well as threat hunting to prevent data loss (data breaches).
Cisco AMP for Endpoints
AMP for Endpoints provides more than just endpoint-level visibility into files. It also provides cloud-based detection of malware, in which the cloud constantly updates itself. This enables very rapid detection of known malware because the cloud resources are used instead of endpoint resources. This architecture has a number of benefits. With the majority of the processing power being performed in the cloud, the endpoint software remains very lightweight.

The AMP cloud is able to provide a historical view of malware activity, segmented into two activity types:
File trajectory: What endpoints have seen the files
Device trajectory: Actions the files performed on given endpoints
With the data storage and processing in the cloud, the AMP solution is able to provide powerful and detailed reporting, as well as provide very robust management.
The AMP for Endpoints agent is also able to take action. For example, it can block malicious network connections based on custom IP blacklists or intelligent dynamic lists of malicious IP addresses.
AMP for Endpoints is the connector that resides on—you guessed it—endpoints. It resides on Windows, Mac, Linux, and Android endpoints. Unlike traditional endpoint protection software that uses a local database of signatures to match a known bad piece of software or a bad file, AMP for Endpoints remains lightweight, sending a hash to the cloud and allowing the cloud to make intelligent decisions and return the verdicts Clean, Malware, and Unknown.

Figure 11-1 shows the AMP for Endpoints high-level architecture.
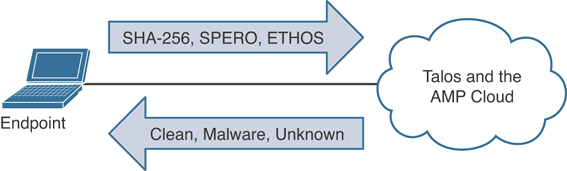
Figure 11-1 AMP for Endpoints High-Level Architecture
AMP for Endpoints connectors must be able to reach the AMP cloud. That means the agents may have to be able to go through firewalls and proxy servers to reach the Internet. If traversing a firewall and/or web proxy to reach the Internet, those products must allow connectivity from the AMP connector to the Cisco servers over HTTPS (TCP 443).
To allow a connector to communicate with Cisco cloud servers for file and network disposition lookups, a firewall must allow the clients to connect to the Cisco servers over TCP 443 by default or TCP 32137.

Outbreak Control
With a solution as powerful and extensive as AMP for Endpoints, it is difficult to determine where to start describing how to configure and use the system; however, it makes logical sense to begin with Outbreak Control because the objects you create within Outbreak Control are key aspects of endpoint policies.
Outbreak Control allows you to create lists that customize AMP for Endpoints to your organization’s needs. You can view the main lists from the AMP cloud console by clicking the Outbreak Control menu, which offers options in the following categories: Custom Detections, Application Control, Network, and Endpoint IOC (indicators of compromise), as shown in Figure 11-2.
You can think of custom detections as a blacklist. You use them to identify files that you want to detect and quarantine. When a custom detection is defined, not only do endpoints quarantine matching files when they see them, but any AMP for Endpoints agents that have seen the files before the custom detection was created can also quarantine the files through retrospection, also known as cloud recall.
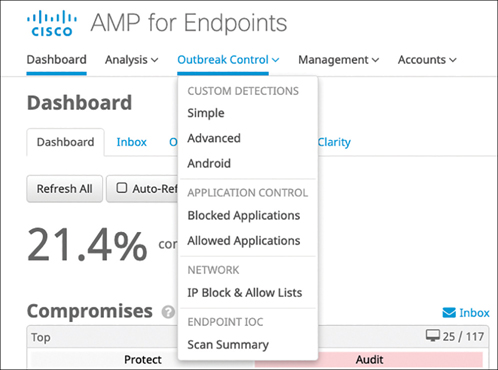
Figure 11-2 AMP for Endpoints Outbreak Control
Simple custom detection allows you to add file signatures, while the advanced custom detections are more like traditional antivirus signatures.
Creating a simple custom detection is similar to adding new entries to a blacklist. You define one or more files that you are trying to quarantine by building a list of SHA-256 hashes. If you already have the SHA-256 hash of a file, you can paste that hash directly into the UI, or you can upload files directly and allow the cloud to create the SHA-256 hash for you.
To create a simple custom detection, navigate to Outbreak Control > Custom Detections > Simple and the list of all existing simple custom detections appears, as shown in Figure 11-3. To add a new one, you must type it in the Name box and click Save, as shown in Figure 11-3.
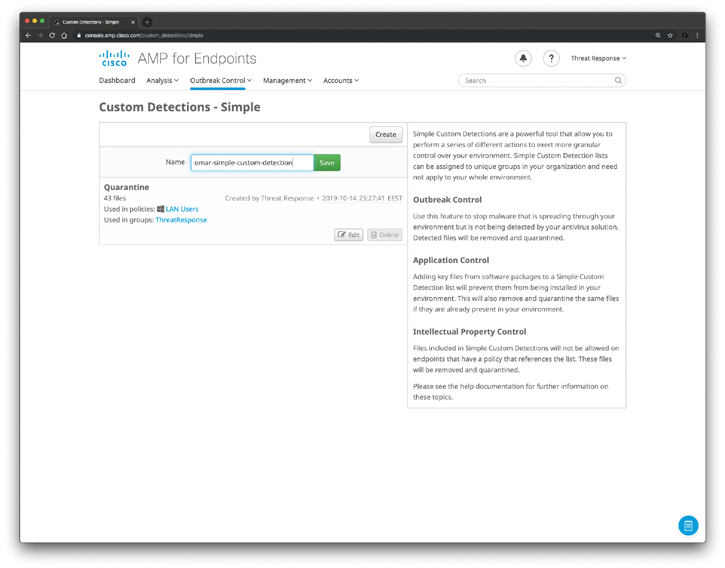
Figure 11-3 AMP for Endpoints Outbreak Control Options
The detection is then added to the list, as shown in Figure 11-4, and automatically edited—with the contents displayed on the right side.

Figure 11-4 AMP for Endpoints Simple Custom Detection Example
If you already have the SHA-256 hash of a file, simply paste it in, add a note, and click Save; otherwise, you can upload a file, add a note, and click Upload. Once the file is uploaded, the hash is created and shown on the bottom-right side. You must click Save, or the hash will not be stored as part of your simple custom detection.
Simple custom detections just look for the SHA-256 hash of a file. Advanced custom detections offer many more signature types to the detection, based on ClamAV signatures, including the following:
File body–based signatures
MD5 signatures
MD5, PE section–based signatures
An extended signature format (with wildcards, regular expressions, and offsets)
Logical signatures
Icon signatures
To create an advanced custom detection, navigate to Outbreak Control > Custom Detections > Advanced, and the list of all existing advanced custom detections appears, as shown in Figure 11-5.

Figure 11-5 Outbreak Control Custom Detections
To add a new custom detection, you must type it in the Name box and click Save to add it to the list. Click Edit to display the contents of the new advanced detection object on the right side, as shown in Figure 11-6. The signature types can be auto-detected, or you can manually select them from the drop-down list. Figure 11-6 shows the available signature types.
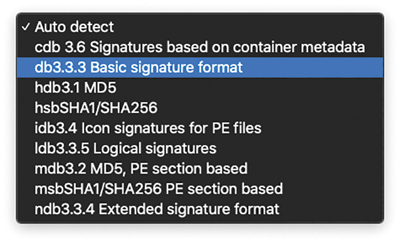
Figure 11-6 Outbreak Control Custom Detections Available Signature Types
Next, you click the Build Database From Signature Set button, and a success message is displayed, showing the successful creation of the advanced custom detection signature set. A View Changes link is visible with every custom detection, both simple and advanced. The AMP cloud maintains an audit log for each of the detection lists, and you can view it by clicking that link.
Android detections are defined separately from the ones used by Windows or Mac. These detections provide granular control over Android devices in an environment. The detections look for specific applications, and you build them by either uploading the app’s .apk file or selecting that file from the AMP console’s inventory list.
You can choose to use Android custom detections for two main functions: outbreak control and application control.
When using an Android custom detection for outbreak control, you are using the detection to stop malware that is spreading through mobile devices in the organization. When a malicious app is detected, the user of the device is notified and prompted to uninstall it.
You don’t have to use these detections just for malware, but you can also use them to stop applications that you don’t want installed on devices in your organization. This is what AMP refers to as “application control.” Simply add apps to an Android custom detection list that you don’t want installed, and AMP notifies the user of the unwanted application and prompts the user to uninstall it, just as if it were a malicious app.

IP Blacklists and Whitelists
You can use outbreak control IP lists in conjunction with device flow correlation (DFC) detections. DFC allows you to flag or even block suspicious network activity. You can use policies to specify the behavior of AMP for Endpoints when a suspicious connection is detected and also to specify whether the connector should use addresses in the Cisco intelligence feed, the custom IP lists you create yourself, or a combination of both.
You use an IP whitelist to define IPv4 addresses that should not be blocked or flagged by DFC. AMP bypasses or ignores the intelligence feeds as they relate to the IPv4 addresses in the whitelist (also often called the “allow list”).
You use IP blacklists to create DFC detections. Traffic that matches entries in the blacklist are flagged or blocked, as the DFC rule dictates.
To create an IP list, navigate to Outbreak Control > Network > IP Block and Allow Lists, as shown in Figure 11-7.
Figure 11-7 AMP for Endpoints IP Block & Allow Lists
In the screen shown in Figure 11-7, you click Create IP List to start a new IP list, and you’re brought to the New IP List configuration screen, where you can create an IP list either by typing the IPv4 addresses in classless interdomain routing (CIDR) notation or by uploading a file that contains a list of IPs. You can also specify port numbers to block or allow. After the list is created, you can edit it only by downloading the resulting file and uploading it back to the AMP console. Figure 11-8 shows the New IP List screen, with a mixture of entries entered as text. You name the list, choose whether it is a whitelist (IP Allow List) or a blacklist (IP Block List), and enter a series of IPv4 addresses, one line at a time. Each line must contain a single IP or CIDR.

Figure 11-8 Creating a New IP List
You click Create IP List to create the text file in the cloud console, and your new IP list is shown on the screen. If you click Edit, you can change the name of the IP list. To update the contents of the list, you must click Download and then delete the list. Then you create a new list with the same name and upload the modified file.
As for custom detections, the AMP console maintains an audit trail for IP lists that you can view by clicking View Changes.

AMP for Endpoints Application Control
Like files, applications can be detected, blocked, and whitelisted. As with the other files, AMP does not look for the name of the application but the SHA-256 hash.
To create a new application control list for blocking an application, navigate to Outbreak Control > Application Control > Blocked Applications. Figure 11-9 demonstrates this process. As you would expect, to create a new list, you click Create. You must name the list and click Save before you can add any applications to the blocking list.
Once the list has been created and saved, click Edit to add any applications. If you already have the SHA-256 hash, add it. Otherwise, you can upload one application at a time and have the AMP cloud console calculate the hash for you, as long as the file is not larger than the 20MB limit. You can also upload an existing list. Figure 11-10 shows a blocking list with an existing application hash shown at the bottom of the right-hand column, while another file is being uploaded for hash calculation.

Figure 11-9 Application Control—Blocked Applications
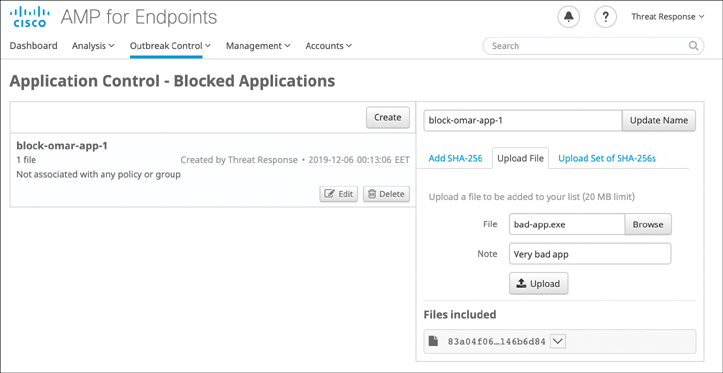
Figure 11-10 Blocking a New Application

Exclusion Sets
There is one more object that you should try to create before you build your policies, and that is an exclusion set. An exclusion set is a list of directories, file extensions, or even threat names that you do not want the AMP agent to scan and subsequently not convict as malware.
You can use an exclusion set to resolve conflicts with other security products or mitigate performance issues by excluding directories that contain large files that are frequently written to, like databases. If you are running an antivirus product on computers with the AMP for Endpoints connector, you should exclude the location where that product is installed.
It’s important to remember that any files stored in a location that has been added to an exclusion set will not be subjected to application blocking, simple custom detections, or advanced custom detections.
These are the available exclusion types:
Threat: This type excludes specific detections by threat name.
Extension: This type excludes files with a specific extension.
Wildcard: This type excludes files or paths using wildcards for filenames, extensions, or paths.
Path: This type excludes files in a given path.
For Windows, path exclusions may use constant special ID lists (CSIDL), which are Microsoft given names for common file paths. For more on CSIDL, see https://docs.microsoft.com/en-us/windows/win32/shell/csidl?redirectedfrom=MSDN.
Cisco-maintained exclusions are created and maintained by Cisco to provide better compatibility between the AMP for Endpoints Connector and antivirus, security, or other software. Click the Cisco-Maintained Exclusions button to view the list of exclusions. These cannot be deleted or modified and are presented so you can see which files and directories are being excluded for each application. These exclusions may also be updated over time with improvements, and new exclusions may be added for new versions of an application. When one of these exclusions is updated, any policies using the exclusion will also be updated so the new exclusions are pushed to your connectors. Figure 11-11 shows Cisco-maintained exclusions.

Figure 11-11 Cisco-Maintained Exclusions
Each row displays the operating system, exclusion set name, the number of exclusions, the number of groups using the exclusion set, and the number of computers using the exclusion set. You can use the search bar to find exclusion sets by name, path, extension, threat name, or SHA-256. You can also filter the list by operating system by clicking the respective tabs.
To create a new exclusion set, navigate to Management > Exclusions, as shown in Figure 11-12.
Figure 11-12 AMP for Endpoints Exclusions
In Figure 11-12, you see a list of any existing exclusions and can create new ones. Click New Exclusion Set and select the operating system for the new exclusion set (Windows, Mac, or Linux), as shown in Figure 11-13.

Figure 11-13 Selecting the Operating System for the New AMP for Endpoints Exclusion Set
After selecting the operating system for the new AMP for Endpoints exclusion set, the screen in Figure 11-14 is displayed.
In the example in Figure 11-14, Mac OS was selected. You can use the search bar to find exclusion sets by name, path, extension, threat name, or SHA-256. You can also filter the list by operating system by clicking the respective tabs. Click View All Changes to see a filtered list of the Audit Log showing all exclusion set changes. Click any exclusion set to expand its details. You can click View Changes in this view to see changes made to just that particular set.

Figure 11-14 Adding an AMP for Endpoints Exclusion Set

AMP for Endpoints Connectors
AMP for Endpoints is available for multiple platforms: Windows, Android, Mac, and Linux. You can see the available connectors from the cloud console by navigating to Management > Download Connector. In Figure 11-15, you see the types of endpoints.
Figure 11-15 Downloading the AMP for Endpoint Connector

AMP for Endpoints Policies
You can configure different policies for each of the supported platforms, respectively. To create a new policy, navigate to Management > Policies, as shown in Figure 11-16.
A policy is applied to an endpoint via groups. Groups allow the computers in an organization to be managed according to their function, location, or other criteria as determined by the administrator.

Figure 11-16 AMP for Endpoints Policies
You can create a new group by navigating to Management > Groups. The screen shown in Figure 11-17 will be displayed.
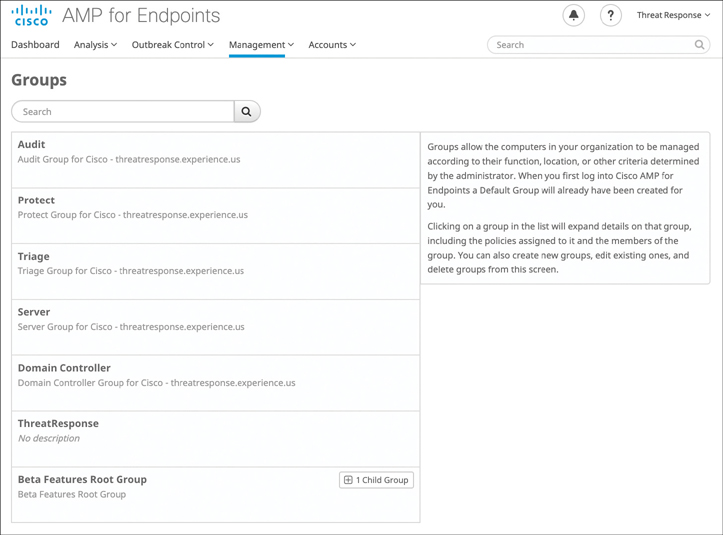
Figure 11-17 AMP for Endpoints Groups
AnyConnect AMP Enabler
You can use the AMP Enabler add-on to AnyConnect to aid in the distribution of the AMP connector to clients who use AnyConnect for remote access VPN, secure network access, posture assessments with Cisco’s Identity Services Engine, and more. Figure 11-18 shows the AnyConnect Secure Mobility Client with the AMP Enabler tile.
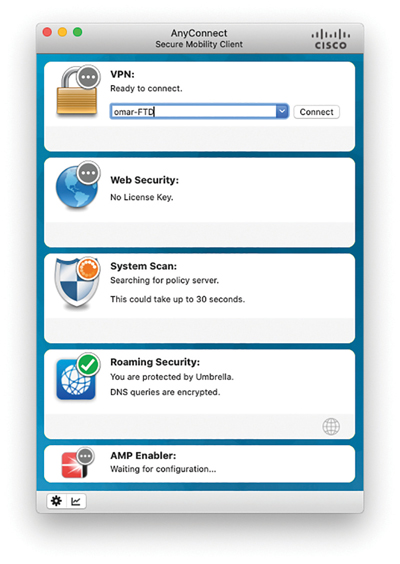
Figure 11-18 AnyConnect AMP Enabler

AMP for Endpoints Engines
There are three detection and protection “engines” in AMP for Endpoints:
TETRA: A full client-side antivirus solution. Do not enable the use of TETRA if there is an existing antivirus product in place. The default AMP setting is to leave TETRA disabled, as it changes the nature of the AMP connector from being a very lightweight agent to being a “thicker” software client that consumes more disk space for signature storage and more bandwidth for signature updates. When you enable TETRA, another configuration subsection is displayed, allowing you to choose what file scanning options you wish to enable.
Spero: A machine learning–based technology that proactively identifies threats that were previously unknown. It uses active heuristics to gather execution attributes, and because the underlying algorithms come up with generic models, they can identify malicious software based on its general appearance rather than basing identity on specific patterns or signatures.
Ethos: A “fuzzy fingerprinting” engine that uses static or passive heuristics.
AMP for Endpoints Reporting
AMP for Endpoints includes a series of reporting dashboards that can be very useful to understand what’s happening in your endpoints. The main dashboard, illustrated in Figure 11-19, provides a view of threat activity in your organization over the past 30 days, as well as the percentage of compromised computers. You can filter by platform, date ranges, and other attributes.
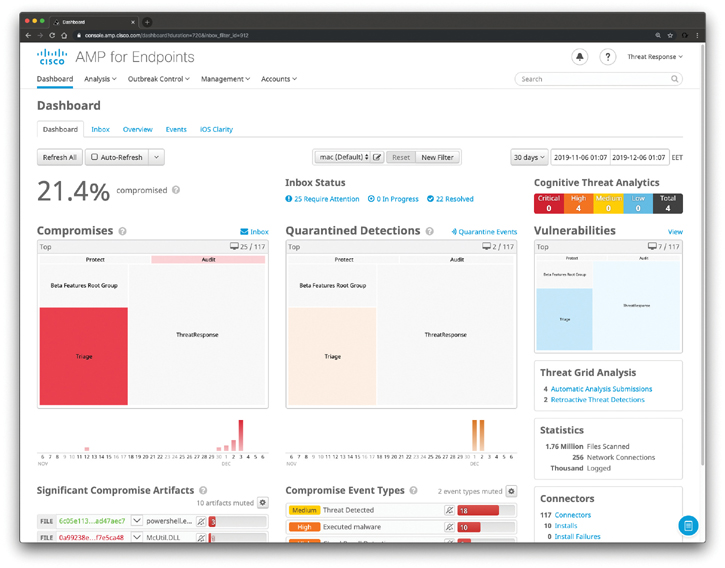
Figure 11-19 AMP for Endpoints Main Dashboard
Figure 11-20 shows the AMP for Endpoint Inbox report. The Inbox is a tool that allows you to see compromised computers in your business and track the status of compromises that require manual intervention to resolve. You can filter computers to work on by selecting Groups in the heat map, selecting a day with compromises in the bar chart, selecting an SHA-256 hash checksum from the Significant Compromise Artifacts list, or selecting from the Compromise Event Types list. These filters can be saved and set as your default view. You can also filter the computer list by those that require attention, those that are in progress, and those that have been resolved by clicking the matching tabs. You can order the list by date or severity by selecting from the Sort drop-down menu. When a computer is marked as resolved, it is no longer reflected in data on the Dashboard or Inbox.
Figure 11-21 shows the AMP for Endpoints Overview dashboard, which displays the status of your environment and highlights recent threats and malicious activity in your AMP for Endpoints deployment. You can click the headings of each section to navigate directly to relevant pages in the console to investigate and remedy situations.
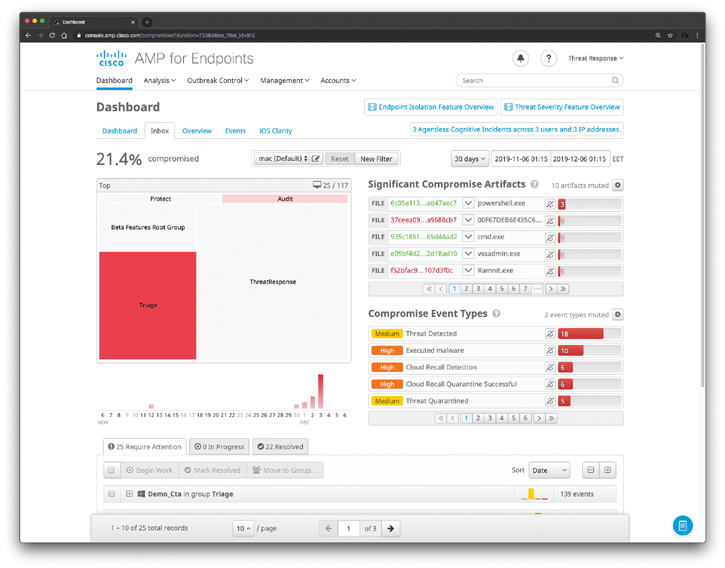
Figure 11-20 AMP for Endpoints Inbox

Figure 11-21 AMP for Endpoints Overview Dashboard
Figure 11-22 shows the AMP for Endpoints Events dashboard, displaying the most recent events in your AMP for Endpoints deployment.
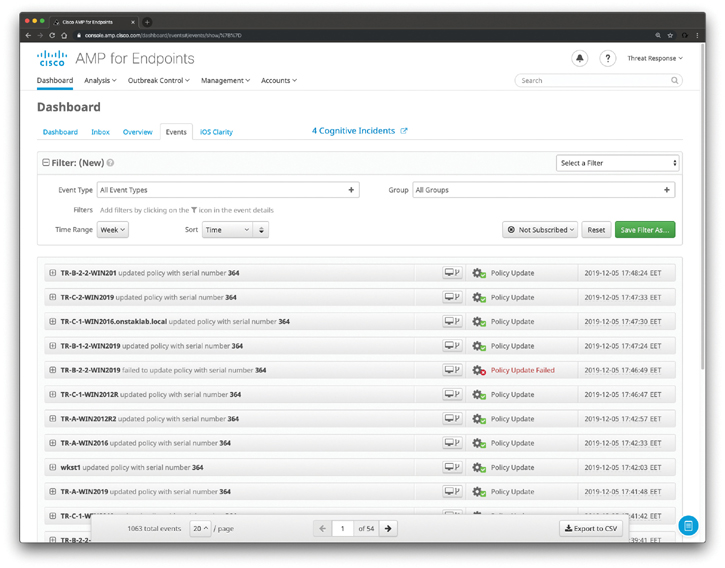
Figure 11-22 AMP for Endpoints Events Dashboard
Figure 11-23 shows the iOS Clarity dashboard in AMP for Endpoints. If you have already linked your Meraki SM or other mobile device manager (MDM), this tab displays a summary of activity, a list of the most recently observed applications on your managed iOS devices, and a list of devices that have not reported back in more than seven days.


Figure 11-23 AMP for Endpoints Events iOS Clarity Dashboard
Cisco Threat Response
Cisco Threat Response is a “one-pane-of-glass” console that automates integrations across Cisco security products and threat intelligence sources. This is an ongoing effort from Cisco to provide a single console for the management of most of its security products.
Cisco Threat Response integrates with the following Cisco security solutions:
Cisco Advanced Malware Protection
AMP for Endpoints
Cisco Threat Grid
Cisco Umbrella
Cisco Email Security
Cisco Next-Generation Firewalls (NGFW)
Next-Generation Intrusion Prevention System (NGIPS)
The screenshots in the previous sections were collected using a Cisco Threat Response console.
Exam Preparation Tasks
As mentioned in the section “How to Use This Book” in the Introduction, you have a couple of choices for exam preparation: the exercises here, Chapter 12, “Final Preparation,” and the exam simulation questions in the Pearson Test Prep Software Online.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topic icon in the outer margin of the page. Table 11-2 lists these key topics and the page numbers on which each is found.

Table 11-2 Key Topics for Chapter 11
Key Topic Element |
Description |
Page Number |
List |
Surveying the AMP for endpoints core features |
|
Section |
Endpoint Threat Detection and Response (ETDR) and Endpoint Detection and Response (EDR) |
|
List |
Reviewing file trajectory and device trajectory |
|
Understanding the AMP for Endpoints architecture |
||
Section |
Outbreak Control |
|
Section |
IP Blacklists and Whitelists |
|
Section |
AMP for Endpoints Application Control |
|
Section |
Exclusion Sets |
|
Section |
AMP for Endpoints Connectors |
|
Section |
AMP for Endpoints Policies |
|
Section |
AMP for Endpoints Engines |
|
Tip |
Describing the value of endpoint device management and asset inventory such as MDM |
Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary.
Review Questions
1. Which of the following is an AMP for Endpoints engine that uses machine learning to proactively identify threats that were previously unknown? This solution uses active heuristics to gather execution attributes, and because the underlying algorithms come up with generic models, they can identify malicious software based on its general appearance rather than basing identity on specific patterns or signatures.
TETRA
Ethos
Spero
All of these answers are correct.
2. Which of the following is a list of directories, file extensions, or even threat names that you do not want the AMP agent to scan and definitely not to convict as malware?
Exclusion set
Application blacklist
TETRA blacklist
None of these answers is correct.
3. Like files, applications can be detected, blocked, and whitelisted with AMP for Endpoints. AMP for Endpoints does not look for the name of the application but which of the following elements?
An SHA hash (checksum)
An outbreak signature
A custom signature
A Spero signature
4. Device flow correlation (DFC) can be used for which of the following scenarios?
To correlate AMP for Endpoint logs with Cisco ISE logs
To correlate AMP for Endpoint logs with Cisco FMC logs
To correlate AMP for Endpoint logs with Tetration logs
To flag or block suspicious network activity
5. You are investigating a potential threat outbreak in your organization. Which of the following can be used to see what endpoints have seen a potential malware file?
Outbreak groups
Outbreak filters
Device trajectory
File trajectory
