Chapter 13. The Importance of Proactive Threat Hunting
This chapter covers the following topics related to Objective 3.3 (Explain the importance of proactive threat hunting) of the CompTIA Cybersecurity Analyst (CySA+) CS0-002 certification exam:
• Establishing a hypothesis: Discusses the importance of this first step in threat hunting
• Profiling threat actors and activities: Covers the process and kits application
• Threat hunting tactics: Describes hunting techniques, including executable process analysis
• Reducing the attack surface area: Identifies what constitutes the attack surface
• Bundling critical assets: Discusses the reasoning behind this technique
• Attack vectors: Defines various attack vectors
• Integrated intelligence: Describes a technology that addresses the need for shared intelligence
• Improving detection capabilities: Identifies methods for improving detection
Threat hunting is a security approach that places emphasis on actively searching for threats rather than sitting back and waiting to react. It is sometimes referred to as offensive in nature rather than defensive. This chapter explores threat hunting and details what it involves.
“Do I Know This Already?” Quiz
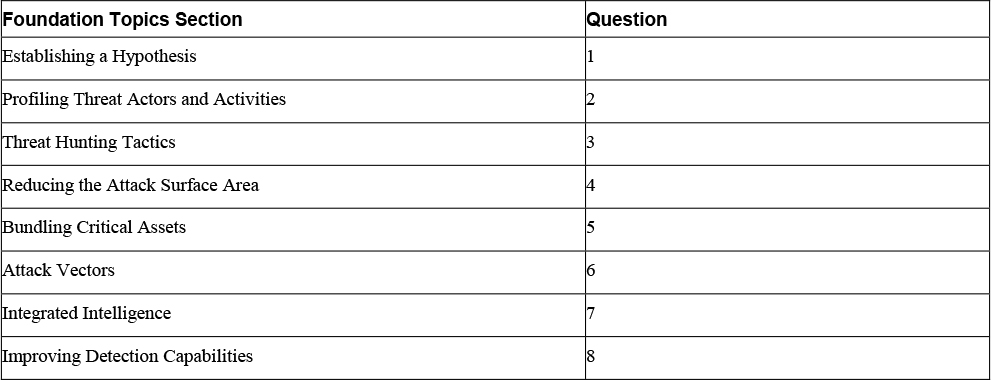
The “Do I Know This Already?” quiz enables you to assess whether you should read the entire chapter. If you miss no more than one of these eight self-assessment questions, you might want to skip ahead to the “Exam Preparation Tasks” section. Table 13-1 lists the major headings in this chapter and the “Do I Know This Already?” quiz questions covering the material in those headings so that you can assess your knowledge of these specific areas. The answers to the “Do I Know This Already?” quiz appear in Appendix A.
Table 13-1 “Do I Know This Already?” Foundation Topics Section-to-Question Mapping
1. Which of the following is the first step in the scientific method?
a. Ask a question.
b. Conduct an experiment.
c. Make a conclusion.
d. Establish a hypothesis.
2. The U.S. Federal Bureau of Investigation (FBI) has identified all but which of the following categories of threat actors?
a. Hacktivists
b. Organized crime
c. State sponsors
d. Terrorist groups
3. Which of the following might identify a device that has been compromised with malware?
a. Executable process analysis
b. Regression analysis
c. Risk management
d. Polyinstantiation
4. Which of the following allows you prevent any changes to the device configuration, even by users who formerly had the right to configure the device?
a. Configuration lockdown
b. System hardening
c. NAC
d. DNSSec
5. Which of the following is a measure of how freely data can be handled?
a. Transparency
b. Sensitivity
c. Value
d. Quality
6. Which metric included in the CVSS Attack Vector metric group means that the attacker can cause the vulnerability from any network?
a. B
b. N
c. L
d. A
7. Which of the following focuses on merging cybersecurity and physical security to aid governments in dealing with emerging threats?
a. OWASP
b. NIST
c. IIC
d. PDA
8. In which step of Deming’s Plan–Do–Check–Act cycle are the results of the implementation analyzed to determine whether it made a difference?
a. Plan
b. Do
c. Check
d. Act
Foundation Topics
Establishing a Hypothesis
The first phase of proactive threat hunting is to establish a hypothesis about the aims and nature of a potential attack, similar to establishing a hypothesis when following the scientific method, shown in Figure 13-1. When security incidents are occurring, and even when they are not occurring at the current time, security professionals must anticipate attacks and establish a hypothesis regarding the attack aims and method as soon as possible. As you may already know from the scientific method, making an executed guess about the aims and nature of an attack is the first step. Then you conduct experiments (or gather more network data) to either prove or disprove the hypothesis. Then the process starts again with a new hypothesis if the old one has been disproved.

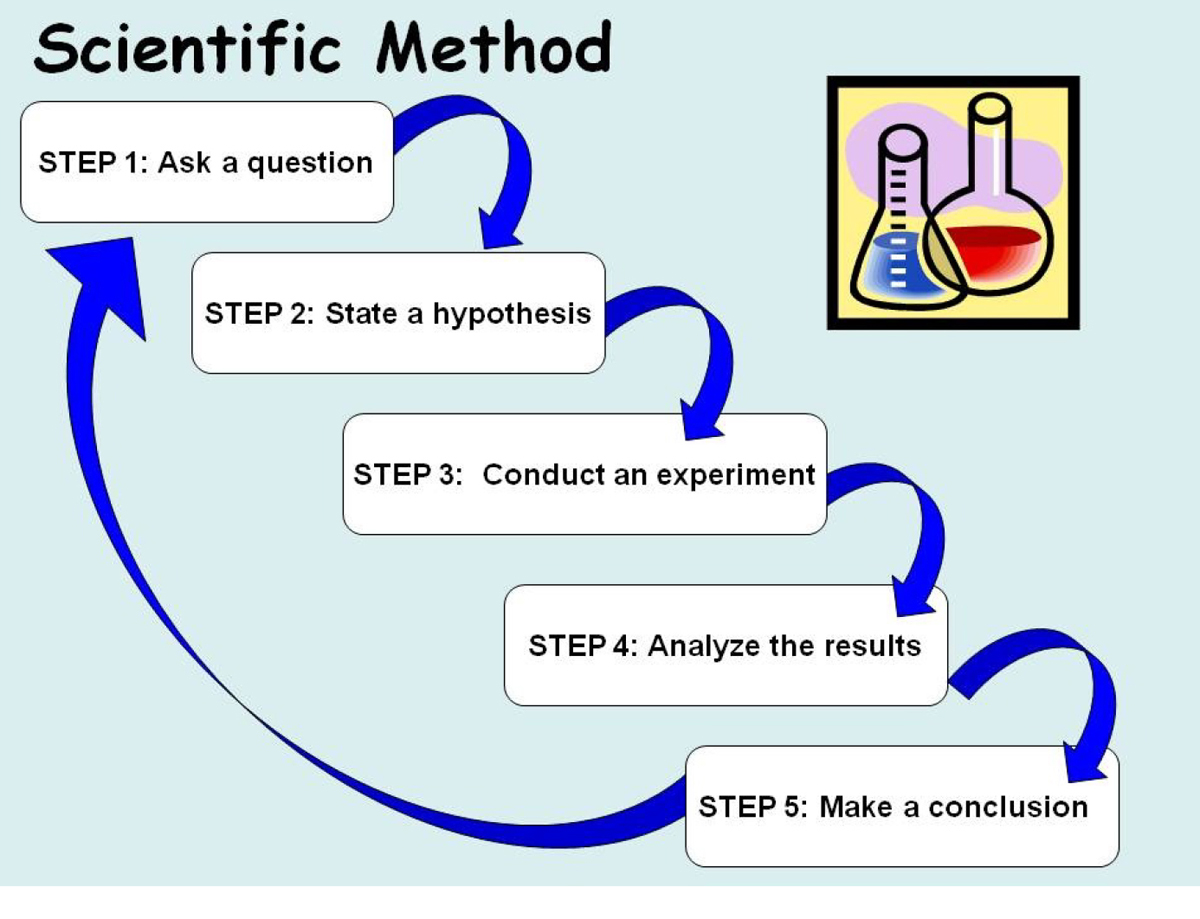
Figure 13-1 Scientific Method
For example, if an attacker is probing your network for unknown reasons, you might follow the method in this way:
1. Why is he doing this, what is his aim?
2. He is trying to perform a port scan.
3. Monitor and capture the traffic he sends to the network.
4. Look for the presence of packets that have been crafted by the hacker compared to those that are the result of the normal TCP three-way handshake.
5. These packet types are not present; therefore, his intent is not to port scan.
At this point another hypothesis will be suggested and the process begins again.
Profiling Threat Actors and Activities
A threat is carried out by a threat actor. For example, an attacker who takes advantage of an inappropriate or absent ACL is a threat actor. Keep in mind, though, that threat actors can discover and/or exploit vulnerabilities. Not all threat actors will actually exploit an identified vulnerability. While you learned about basic threat actors in Chapter 1, “The Importance of Threat Data and Intelligence,” the U.S. Federal Bureau of Investigation (FBI) has identified three categories of threat actors:
• Organized crime groups primarily threatening the financial services sector and expanding the scope of their attacks
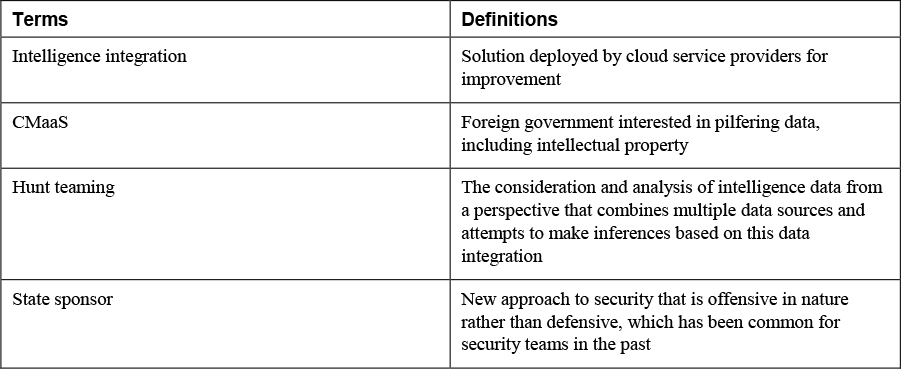
• State sponsors or advanced persistent threats (APTs), usually foreign governments, interested in pilfering data, including intellectual property and research and development data from major manufacturers, government agencies, and defense contractors
• Terrorist groups that want to impact countries by using the Internet and other networks to disrupt or harm the viability of a society by damaging its critical infrastructure
While there are other, less organized groups out there, law enforcement considers these three groups to be the primary threat actors. However, organizations should not totally disregard the threats of any threat actors that fall outside these three categories. Lone actors or smaller groups that use hacking as a means to discover and exploit any discovered vulnerability can cause damage just like the larger, more organized groups.
Hacker and cracker are two terms that are often used interchangeably in media but do not actually have the same meaning. Hackers are individuals who attempt to break into secure systems to obtain knowledge about the systems and possibly use that knowledge to carry out pranks or commit crimes. Crackers, on the other hand, are individuals who attempt to break into secure systems without using the knowledge gained for any nefarious purposes. Hacktivists are the latest new group to crop up. They are activists for a cause, such as animal rights, that use hacking as a means to get their message out and affect the businesses that they feel are detrimental to their cause.
In the security world, the terms white hat, gray hat, and black hat are more easily understood and less often confused than the terms hackers and crackers. A white hat does not have any malicious intent. A black hat has malicious intent. A gray hat is somewhere between the other two. A gray hat may, for example, break into a system, notify the administrator of the security hole, and offer to fix the security issues for a fee. Threat actors use a variety of techniques to gather the information required to gain a foothold.
Threat Hunting Tactics
Security analysts use various techniques in the process of anticipating and identifying threats. Some of these methods revolve around network surveillance and others involve examining the behaviors of individual systems.
Hunt Teaming
Hunt teaming is a new approach to security that is offensive in nature rather than defensive, which has been the common approach of security teams in the past. Hunt teams work together to detect, identify, and understand advanced and determined threat actors. Hunt teaming is covered in Chapter 8, “Security Solutions for Infrastructure Management.”
Threat Model
A threat model is a conceptual design that attempts to provide a framework on which to implement security efforts. Many models have been created. Let’s say, for example, that you have an online banking application and need to assess the points at which the application faces threats. Figure 13-2 shows how a threat model in the form of a data flow diagram might be created using the Open Web Application Security Project (OWASP) approach to identify where the trust boundaries are located.

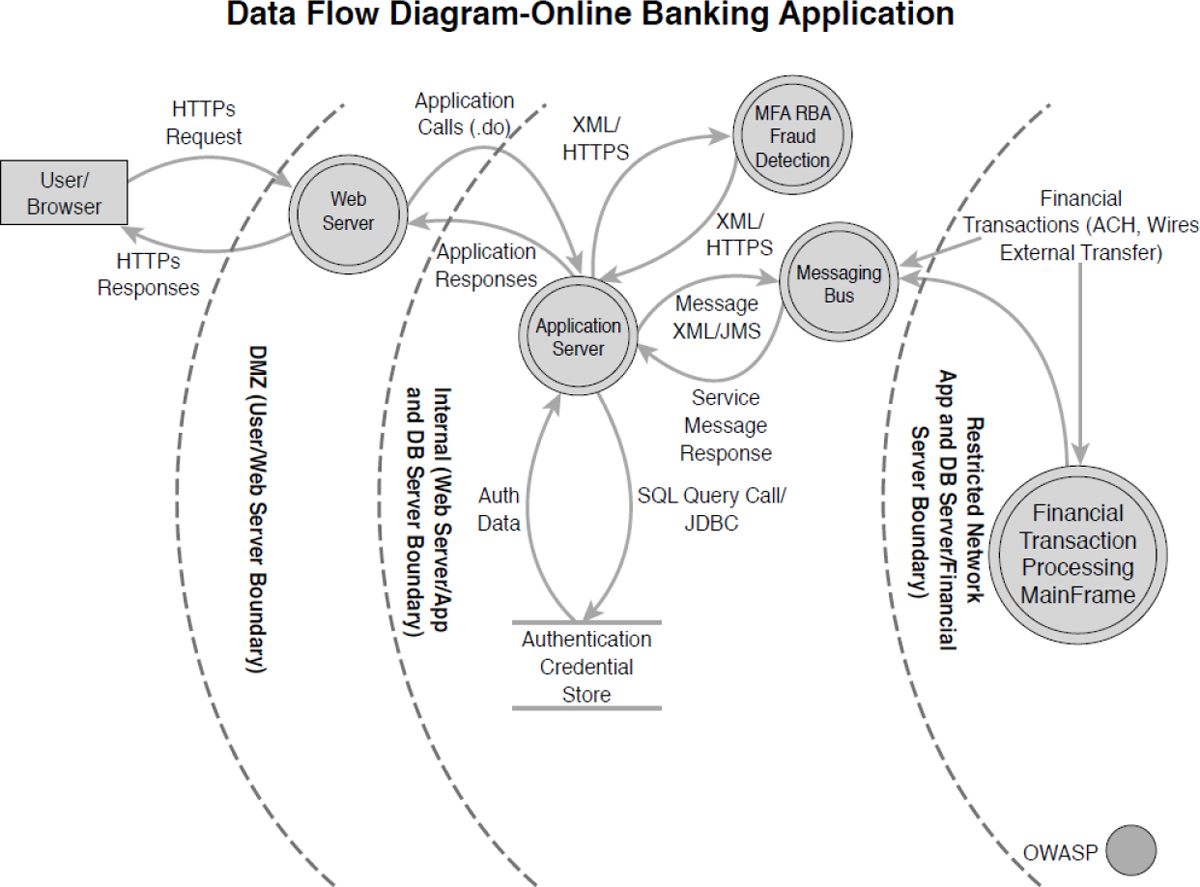
Figure 13-2 OWASP Threat Model
Threat modeling tools go beyond these simple data flow diagrams. The following are some recent tools:

• Threat Modeling Tool (formerly SDL Threat Modeling Tool) identifies threats based on the STRIDE threat classification scheme.
• ThreatModeler identifies threats based on a customizable comprehensive threat library and is intended for collaborative use across all organizational stakeholders.
• IriusRisk offers both community and commercial versions of a tool that focuses on the creation and maintenance of a live threat model through the entire software development life cycle (SDLC). It connects with several different tools to empower automation.
• securiCAD focuses on threat modeling of IT infrastructures using a computer-based design (CAD) approach where assets are automatically or manually placed on a drawing pane.
• SD Elements is a software security requirements management platform that includes automated threat modeling capabilities.
Executable Process Analysis
When the processor is very busy with very little or nothing running to generate the activity, it could be a sign that the processor is working on behalf of malicious software. This is one of the key reasons any compromise is typically accompanied by a drop in performance. Executable process analysis allows you to determine this. While Task Manager in Windows is designed to help with this, it has some limitations. For one, when you are attempting to use it, you are typically already in a resource crunch, and it takes a bit to open. Then when it does open, the CPU has settled back down, and you have no way of knowing what caused it.
By using Task Manager, you can determine what process is causing a bottleneck at the CPU. For example, Figure 13-3 shows that in Task Manager, you can click the Processes tab and then click the CPU column to sort the processes with the top CPU users at the top. In Figure 13-3, the top user is Task Manager, which makes sense since it was just opened.
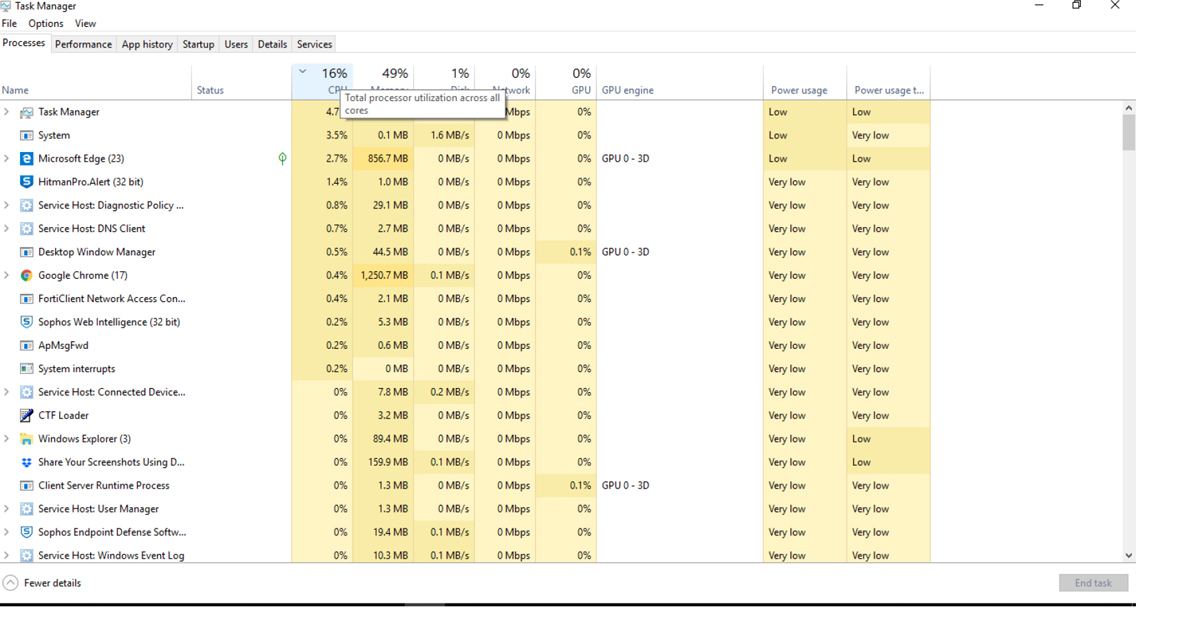
Figure 13-3 Task Manager
A better tool to use is Sysinternals, which is a free download at https://docs.microsoft.com/sysinternals/. The specific part of this tool you need is Process Explorer, which enables you to see in the Notification area the top CPU offender, without requiring you to open Task Manager. Moreover, Process Explorer enables you to look at the graph that appears in Task Manager and identify what caused spikes in the past, which is not possible with Task Manager alone. In Figure 13-4, you can see that Process Explorer breaks down each process into its subprocesses.
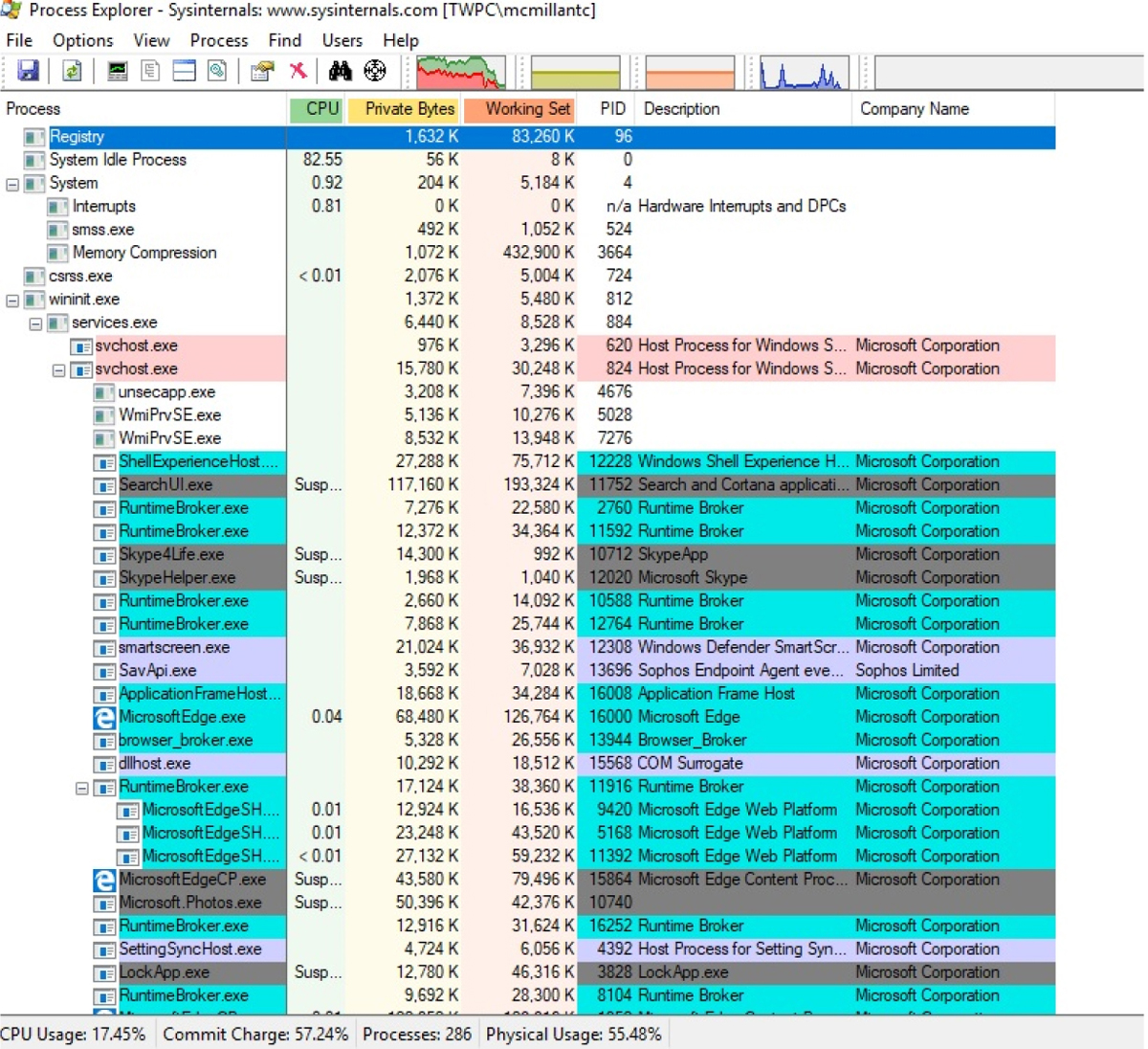
Figure 13-4 Process Explorer
An example of using Task Manager for threat hunting is to proactively look at times and dates when processor usage is high during times when system usage is typically low, indicating a malicious process at work.
Memory Consumption
Another key indicator of a compromised host is increased memory consumption. Many times it is an indication that additional programs have been loaded into RAM so they can be processed. Then once they are loaded, they use RAM in the process of executing their tasks, whatever they may be. You can monitor memory consumption by using the same approach you use for CPU consumption. If memory usage cannot be accounted for, you should investigate it. (Review what you learned about buffer overflows, which are attacks that may display symptoms of increased memory consumption.)
Reducing the Attack Surface Area
Reducing the attack surface area means limiting the features and functions that are available to an attacker. For example, if I lock all doors to the facility with the exception of one, I have reduced the attack surface. Another term for reducing the attack surface area is system hardening because it involves ensuring that all systems have been hardened to the extent that is possible and still provide functionality.
System Hardening
Another of the ongoing goals of operations security is to ensure that all systems have been hardened to the extent that is possible and still provide functionality. System hardening can be accomplished both on physical and on logical bases. From a logical perspective:

• Remove unnecessary applications.
• Disable unnecessary services.
• Block unrequired ports.
• Tightly control the connecting of external storage devices and media, if allowed at all.
System hardening is also done at the physical layer. Physical security was covered in Chapter 7 but some examples include
• Fences around the facility
• Locks on the doors
• Disabled USB ports
• Display filters
• Clean desk policy
Configuration Lockdown
Configuration lockdown (sometimes also called system lockdown) is a setting that can be implemented on devices including servers, routers, switches, firewalls, and virtual hosts. You set it on a device after that device is correctly configured, and it prevents any changes to the configuration, even by users who formerly had the right to configure the device. This setting helps support change control.
Full tests for functionality of all services and applications should be performed prior to implementing this setting. Many products that provide this functionality offer a test mode, in which you can log any problems the current configuration causes without allowing the problems to completely manifest on the network. This allows you to identify and correct any problems prior to implementing full lockdown.
Bundling Critical Assets
While organizations should strive to protect all assets, in the cybersecurity world we tend to focus on what is at risk in the cyber world, which is our data. Bundling these critical digital assets helps to organize them so that security controls can be applied more cleanly with fewer possible human errors. Before bundling can be done, data must be classified.
Data Classification Policy
Data should be classified based on its value to the organization, its sensitivity to disclosure, and its criticality. Assigning a value to data allows an organization to determine the resources that should be used to protect the data. Resources that are used to protect data include personnel resources, monetary resources, and access control resources. Classifying data allows you to apply different protective measures. Data classification is critical to all systems to protect the confidentiality, integrity, and availability (CIA) of data.
After data is classified, the data can be segmented based on the level of protection it needs. The classification levels ensure that data is handled and protected in the most cost-effective manner possible. An organization should determine the classification levels it uses based on the needs of the organization. A number of commercial business and military and government information classifications are commonly used. The information life cycle should also be based on the classification of the data. Organizations are required to retain certain information, particularly financial data, based on local, state, or government laws and regulations.
Sensitivity and Criticality
Sensitivity is a measure of how freely data can be handled. Some data requires special care and handling, especially when inappropriate handling could result in penalties, identity theft, financial loss, invasion of privacy, or unauthorized access by an individual or many individuals. Some data is also subject to regulation by state or federal laws and requires notification in the event of a disclosure. Data is assigned a level of sensitivity based on who should have access to it and how much harm would be done if it were disclosed. Criticality is a measure of the importance of the data. Data considered sensitive may not necessarily be considered critical. Assigning a level of criticality to a particular data set must take into consideration the answer to a few questions:
• Will you be able to recover the data in case of disaster?
• How long will it take to recover the data?
• What is the effect of this downtime, including loss of public standing?
Data is considered critical when it is essential to the organization’s business. When essential data is not available, even for a brief period of time, or its integrity is questionable, the organization is unable to function. Data is considered required but not critical when it is important to the organization but organizational operations can continue for a predetermined period of time even if the data is not available. Data is considered nonessential if the organization is able to operate without it during extended periods of time.
Commercial Business Classifications
Commercial businesses usually classify data using four main classification levels, listed here from highest sensitivity level to lowest:

1. Confidential
2. Private
3. Sensitive
4. Public
Data that is confidential includes trade secrets, intellectual data, application programming code, and other data that could seriously affect the organization if unauthorized disclosure occurred. Data at this level would only be available to personnel in the organization whose work relates to the data’s subject. Access to confidential data usually requires authorization for each access. In the United States, confidential data is exempt from disclosure under the Freedom of Information Act. In most cases, the only way for external entities to have authorized access to confidential data is as follows:
• After signing a confidentiality agreement
• When complying with a court order
• As part of a government project or contract procurement agreement
Data that is private includes any information related to personnel, including human resources records, medical records, and salary information, that is used only within the organization. Data that is sensitive includes organizational financial information and requires extra measures to ensure its CIA and accuracy. Public data is data whose disclosure would not cause a negative impact on the organization.
Military and Government Classifications
Military and government entities usually classify data using five main classification levels, listed here from highest sensitivity level to lowest:

1. Top secret: Data that is top secret includes weapon blueprints, technology specifications, spy satellite information, and other military information that could gravely damage national security if disclosed.
2. Secret: Data that is secret includes deployment plans, missile placement, and other information that could seriously damage national security if disclosed.
3. Confidential: Data that is confidential includes patents, trade secrets, and other information that could seriously affect the government if unauthorized disclosure occurred.
4. Sensitive but unclassified: Data that is sensitive but unclassified includes medical or other personal data that might not cause serious damage to national security but could cause citizens to question the reputation of the government.
5. Unclassified: Military and government information that does not fall into any of the other four categories is considered unclassified and usually has to be granted to the public based on the Freedom of Information Act.
Distribution of Critical Assets
One strategy that can help support resiliency is to ensure that critical assets are not all located in the same physical location. Collocating critical assets leaves your organization open to the kind of nightmare that occurred in 2017 at the Atlanta airport. When a fire took out the main and backup power systems (which were located together), the busiest airport in the world went dark for over 12 hours. Distribution of critical assets certainly enhances resilience.
Attack Vectors
An attack vector is a segment of the communication path that an attack uses to access a vulnerability. Each attack vector can be thought of as comprising a source of malicious content, a potentially vulnerable processor of that malicious content, and the nature of the malicious content itself.
Recall from Chapter 2, “Utilizing Threat Intelligence to Support Organizational Security,” that the Common Vulnerability Scoring System (CVSS) has as part of its Base metric group a metric called Attack Vector (AV). AV describes how the attacker would exploit the vulnerability and has four possible values:
• L: Stands for Local and means that the attacker must have physical or logical access to the affected system.
• A: Stands for Adjacent network and means that the attacker must be on the local network.
• N: Stands for Network and means that the attacker can cause the vulnerability from any network.
• P: Stands for Physical and requires the attacker to physically touch or manipulate the vulnerable component.
Analysts can use the accumulated CVSS information regarding attacks to match current characteristics of indicators of compromise to common attacks.
Integrated Intelligence
Integrated intelligence refers to the consideration and analysis of intelligence data from a perspective that combines multiple data sources and attempts to make inferences based on this data integration. Many vendors of security software and appliances often tout the intelligence integration capabilities of their products. SIEM systems are a good example, as described in Chapter 11, “Analyzing Data as Part of Security Monitoring Activities.”
The Integrated Intelligence Center (IIC) is a unit at the Center for Internet Security (CIS) that focuses on merging cybersecurity and physical security to aid governments in dealing with emerging threats. IIC attempts to create predictive models using the multiple data sources at its disposal.
Improving Detection Capabilities
Detection of events and incidents as they occur is critical. Organizations should be constantly trying to improve their detection capabilities.
Continuous Improvement
Security professionals can never just sit back, relax, and enjoy the ride. Security needs are always changing because the “bad guys” never take a day off. It is therefore vital that security professionals continuously work to improve their organization’s security. Tied into this is the need to improve the quality of the security controls currently implemented. Quality improvement commonly uses a four-step quality model, known as Deming’s Plan–D–Check–Act cycle, the steps for which are as follows:

1. Plan: Identify an area for improvement and make a formal plan to implement it.
2. Do: Implement the plan on a small scale.
3. Check: Analyze the results of the implementation to determine whether it made a difference.
4. Act: If the implementation made a positive change, implement it on a wider scale. Continuously analyze the results.
This can’t be done without establishing some metrics to determine how successful you are now.
Continuous Monitoring
Any logging and monitoring activities should be part of an organizational continuous monitoring program. The continuous monitoring program must be designed to meet the needs of the organization and implemented correctly to ensure that the organization’s critical infrastructure is guarded. Organizations may want to look into Continuous Monitoring as a Service (CMaaS) solutions deployed by cloud service providers.
Exam Preparation Tasks
As mentioned in the section “How to Use This Book” in the Introduction, you have several choices for exam preparation: the exercises here, Chapter 22, “Final Preparation,” and the exam simulation questions in the Pearson Test Prep Software Online.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 13-2 lists a reference of these key topics and the page numbers on which each is found.

Table 13-2 Key Topics in Chapter 13
Define Key Terms
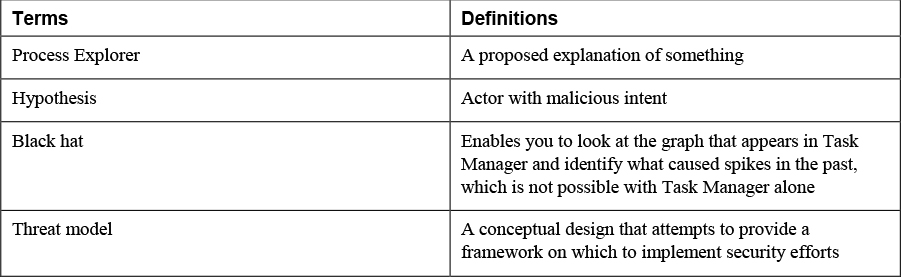
Define the following key terms from this chapter and check your answers in the glossary:
hunt teaming
Review Questions
1. Place the following steps of the scientific method in order.
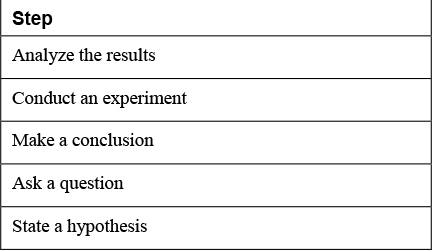
2. List and describe at least one threat modeling tool.
3. ____________________ allows you to determine when a CPU is struggling with malware.
4. Match the following terms with their definitions.

5. List the military/government data classification levels in order.
6. A(n) _____________________ is a segment of the communication path that an attack uses to access a vulnerability.
7. Match the following terms with their definitions.
8. List at least two hardening techniques.
9. Data should be classified based on its _____________ to the organization and its ____________ to disclosure.
10. Match the following terms with their definitions.