Chapter 16
Common Security Concepts
To operate securely in a network environment, one must understand how to speak the language of security. As in any field, there is terminology that must be understood to discuss more involved topics.
In this chapter you will learn the basic concepts, terms, and principles that all network professionals should understand to secure an enterprise network.
Confidentiality, Integrity, and Availability (CIA)
The three fundamentals of security are confidentiality, integrity, and availability (CIA), often referred to as the CIA triad. Most security issues result in a violation of at least one facet of the CIA triad. Understanding these three security principles will help ensure that the security controls and mechanisms implemented protect at least one of these principles.
Confidentiality
To ensure confidentiality, you must prevent the disclosure of data or information to unauthorized entities. As part of confidentiality, the sensitivity level of data must be determined before putting any access controls in place. Data with a higher sensitivity level will have more access controls in place than data at a lower sensitivity level. Identification, authentication, authorization, and encryption can be used to maintain data confidentiality.
Integrity
Integrity, the second part of the CIA triad, ensures that data is protected from unauthorized modification or data corruption. The goal of integrity is to preserve the consistency of data, including data stored in files, databases, systems, and networks.
Availability
Availability means ensuring that data is accessible when and where it is needed. Only individuals who need access to data should be allowed access to that data. The two main areas where availability is affected are (1) when attacks are carried out that disable or cripple a system and (2) when service loss occurs during and after disasters. Technologies that provide fault tolerance, such as RAID or redundant sites, are examples of controls that help to improve availability.
Threats
The first line of defense in providing CIA is to know about the types of threats out there because you can't do anything to protect yourself from something you don't know about. But once you understand the threats, you can begin to design defenses to combat bad guys lurking in the depths of cyberspace just waiting for an opportunity to strike. Threats come in two forms, internal and external.
Internal
Internal threats are those that are sourced within your own network. These attacks come from inside the firewall. Sadly, we have more to fear from our own users than we do from external hackers (maybe we should treat them better). They have already discovered and penetrated the network, which is two-thirds of the hacking process.
External
External threats come from outside the firewall. These are typically hackers of all abilities. They include script kiddies (amateurs) and advanced persistent threats (APT, usually a state-sponsored team) and all types in between. Later you will learn that these two types require a different approach when performing penetration testing for vulnerabilities.
Vulnerabilities
A vulnerability is the absence of a countermeasure or a weakness in a countermeasure that is in place. Vulnerabilities can occur in software, hardware, or personnel. An example of a vulnerability is unrestricted access to a folder on a computer. Most organizations implement a vulnerability assessment to identify vulnerabilities. In the following sections, you'll learn about a method of classifying vulnerabilities and about one special type of vulnerability.
Common Vulnerabilities and Exposures (CVE)
The Common Vulnerability Scoring System (CVSS) is a system of ranking vulnerabilities that are discovered based on predefined metrics. This system ensures that the most critical vulnerabilities can be easily identified and addressed after a vulnerability test is met.
The output of using this classification system is a database of known vulnerabilities called Common Vulnerabilities and Exposures (CVE). It is maintained by the MITRE Corporation and each entry describes a vulnerability in detail, using a number and letter system to describe what it endangers, the environment it requires to be successful, and, in many cases, the proper mitigation. This system is used by security professionals to share and inform one another as new CVEs are discovered.
Zero-Day
Antivirus software uses definition files that identify known malware. These files must be updated frequently, but the update process can usually be automated so that it requires no help from the user. If a new virus is created that has not yet been identified in the list, you will not be protected until the virus definition is added and the new definition file is downloaded.
This condition is known as a zero-day attack because it is the first day the virus has been released and therefore no known fix exists. This term may also be applied to an operating system bug that has not been corrected.
Exploits
An exploit occurs when a threat agent takes advantage of a vulnerability and uses it to advance an attack. When a network attack takes advantage of a vulnerability, it is somewhat of an indictment of the network team as most vulnerabilities can be identified and mitigated. A good example of a vulnerability that was exploited was the unpatched Apache server that was compromised and led to the Equifax breach.
Least Privilege
The first step to mitigating damage that may be caused by disgruntled or malicious employees is to adhere to the principle of least privilege. This concept prescribes that users should be given access only to resources required to do their job. So if Ralph's job only requires read permission to the Sales folder, that's all he should get even if you know he's completely trustworthy. By doing this, you also limit the damage that could be done if Ralph's account is compromised.
Role-Based Access
Role-based access control prescribes creating roles or sets of permissions required for various job roles and assigning those permissions to security groups. When a new employee is assigned a role, they are simply placed in the group and thus inherit all required permissions.
When you create a role-based group, you should define what actions this role will be capable of. The choice of permissions or rights you assign to the group that represents this role (for example, customer service rep) should be driven by the tasks required and the resources required to do that job. This is an area where you should exercise least privilege. This principle states that no user should be given access to any resource that is not required to do their job.
Zero Trust
The Zero Trust concept supports least privilege. It prescribes that when a resource is created, the default permission should be No Access. It also means that when configuring ACLs on routers, all traffic should be blocked by default and only specific traffic allowed.
Defense in Depth
A defense-in-depth strategy refers to the practice of using multiple layers of security between data and the resources on which it resides and possible attackers. The first layer of a good defense-in-depth strategy is appropriate access control strategies. Access controls exist in all areas of an Information Systems (IS) infrastructure (more commonly referred to as an IT infrastructure), but a defense-in-depth strategy goes beyond access control. It also considers software development security, cryptography, and physical security. In the following sections, we'll look at some of the options you should consider in developing defense in depth.
Network Segmentation Enforcement
Maintaining security in the network can be made easier by segmenting the network and controlling access from one segment to another. Segmentation can be done at several layers of the OSI model.
One of the biggest reasons for implementing segmentation is for security purposes. At layer 1, this means complete physical separation. However, if you don't want to go with complete segmentation, you can also segment at layer 2 on switches by implementing VLANs and port security. This can prevent connections between systems that are connected to the same switch. They can also be used to organize users into common networks regardless of their physical location.
If segmentation at layer 3 is required, it's achieved using access control lists on routers to control access from one subnet to another or from one VLAN to another. Firewalls can implement these types of access lists as well.
Screened Subnet (aka Demilitarized Zone)
Use a screened subnet—previously known as a demilitarized zone (DMZ)—for all publicly viewable servers, including web servers, FTP servers, and email relay servers. A screened subnet is a version of the DMZ that is created with two firewalls (each of the routers are operating as a firewall) and the DMZ (also called the perimeter between them), as shown in Figure 16.1.
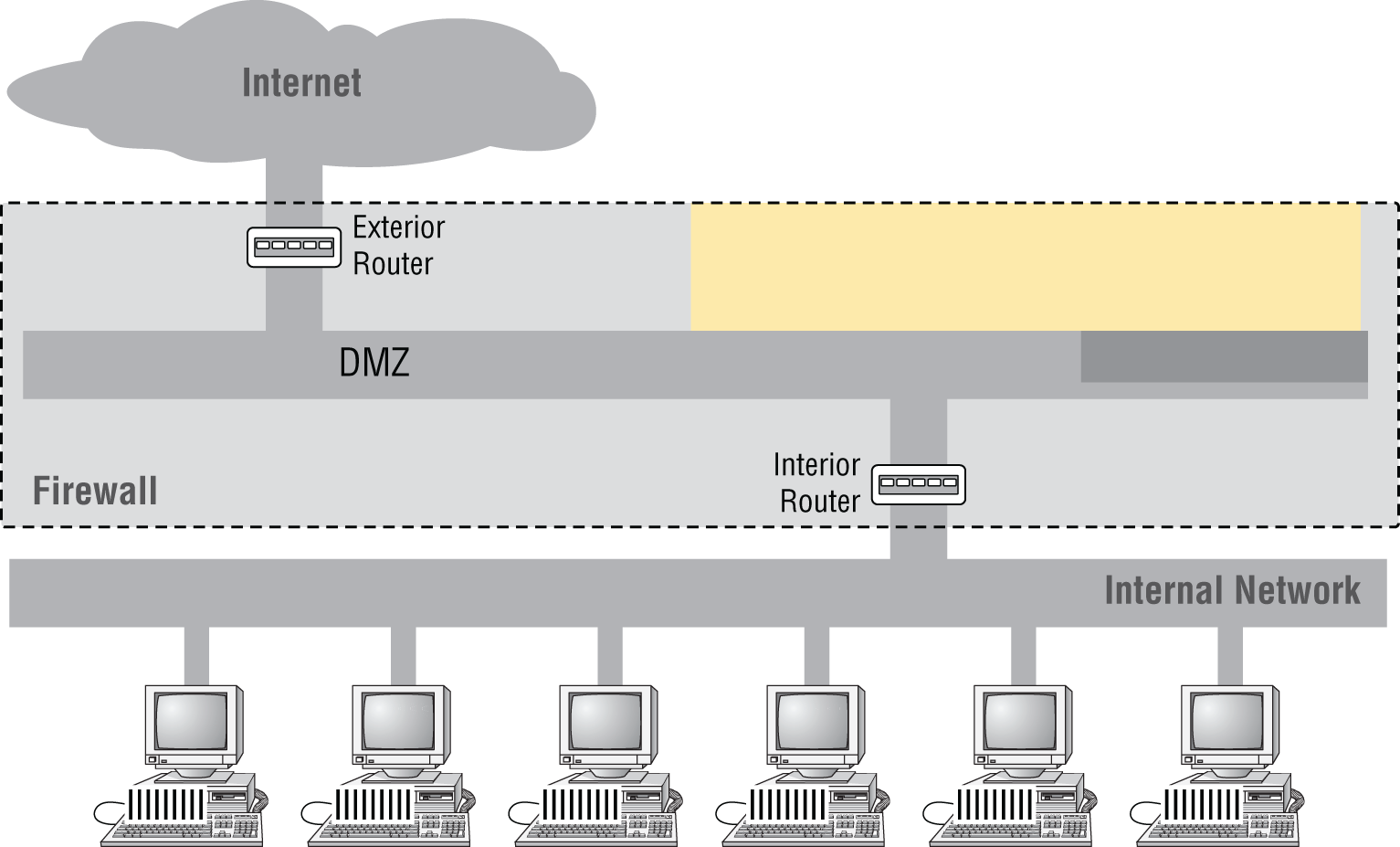
FIGURE 16.1 Screened subnet
In this case, two firewalling routers are used, and traffic must be inspected at both firewalls to enter the internal network. It is called a screened subnet because there is a subnet between the two firewalls that can act as a DMZ for resources from the outside world.
Separation of Duties
Separation of duties is a concept that specifies that any operation that is susceptible to fraud or abuse by employees should be broken into two tasks and then these two tasks should be assigned to different individuals. While there is no guarantee that these two individuals don't collude, the chance of that occurring are much less than the chance of a single individual committing fraud.
Network Access Control
Network Access Control (NAC) is a method of securing network hosts before they're allowed to access the network. Network Access Control systems that control access to devices based on their security settings include Cisco's Network Admission Control (NAC) and Microsoft's Network Policy and Access Services (NPAS). These systems examine the state of a computer's operating system updates and antimalware updates before allowing access, and in some cases, they can even remediate the devices prior to permitting access. In the following sections, key components of Network Access Control systems are covered.
Posture Assessment
When devices attempt to access the network, the devices are examined closely, which is called a posture assessment. The following items can be checked:
- Antimalware updates
- Operating system updates
- Windows Registry settings
When the assessment is complete and is positive, admission is granted. If problems are found, admission may be denied and the user notified that action must be taken, or the device may be directed to a remediation server that can install missing updates or quarantine the device if necessary.
Guest Network
When a device is attempting to connect to a network using a form of network access control, the device is first placed in a guest network until a posture assessment is performed. Until it is either approved or remediated, it will remain in the guest network. The guest network will not allow access to the balance of the network to prevent the device from introducing issues to the network.
Persistent vs. Nonpersistent Agents
Network Access Control systems can be deployed using either persistent or nonpersistent agents on the devices. A persistent agent is one that is installed on an NAC client and starts when the operating system loads. This agent provides functionality that may not be present in the nonpersistent agent, such as system-wide notifications and alerts and auto and manual remediation.
A nonpersistent agent is one that is used to assess the device only during the onetime check-in at login, usually through a captive web portal. The nonpersistent or dissolvable agent is removed from the device when the authentication web page is closed. It can be used to support the assessment of endpoints not owned by the organization and as such can help to make a bring your own device (BYOD) policy possible.
Honeypot
Another segmentation tactic is to create honeypots and honeynets. Honeypots are systems strategically configured to be attractive to hackers and to lure them into spending enough time attacking them while information is gathered about the attack. In some cases, entire networks called honeynets are attractively configured for this purpose. You need to make sure that either of these types of systems do not provide direct connections to any important systems. Their ultimate purpose is to divert attention from valuable resources and to gather as much information about an attack as possible. A tarpit is a type of honeypot designed to provide a very slow connection to the hacker so that the attack takes enough time to be properly analyzed.
Authentication Methods
A whole bunch of authentication schemes are used today, and although it's important to know about the different schemes and how they work, all that knowledge doesn't make a difference if your network's users aren't schooled on how to manage their account names and passwords correctly. In the following sections, you'll learn about authentication systems and techniques.
Multifactor
Multifactor authentication is designed to add an additional level of security to the authentication process by verifying more than one characteristic of a user before allowing access to a resource. Users can be identified in one of five ways:
- By something they know (password)
- By something they are (retinas, fingerprint, facial recognition)
- By something they possess (smart card)
- By somewhere they are (location)
- By something they do (behavior)
Two-factor authentication is when two of the above factors are being tested, while multifactor is when more than two of the above factors are being tested. An example of two-factor authentication would be requiring both a smart card and a PIN to log onto the network. The possession of either by itself would not be sufficient to authenticate. This protects against the loss and theft of the card as well as the loss of the password. An example of multifactor authentication would be when three items are required, such as a smart card, a PIN, and a username and password.
This process can get as involved as the security requires. In an extremely high-security situation, you might require a smart card, a password, a retina scan, and a fingerprint scan. The trade-off to all the increased security is an inconvenient authentication process for the user and the high cost of biometric authentication devices.
Authentication, Authorization, and Accounting (AAA)
In computer security speak, AAA (triple A, like the auto club) refers to authentication, authorization, and accounting. AAAA is a more robust version that adds auditing into the mix. AAA and AAAA aren't really protocols; instead, they're systematized, conceptual models for managing network security through one central location. Two common implementations of AAA are RADIUS and TACACS+.
Remote Authentication Dial-In User Service (RADIUS)
Although its name implies it, the Remote Authentication Dial-In User Service (RADIUS) is not a dial-up server. Like pretty much everything else, it originated that way, but it's evolved into more of a verification service. Today, RADIUS is an authentication and accounting service that's used for verifying users over various types of links, including dial-up. Many ISPs use a RADIUS server to store the usernames and passwords of their clients in a central spot through which connections are configured to pass authentication requests. RADIUS servers are client-server based authentication and encryption services maintaining user profiles in a central database.
RADIUS is also used in firewalls. When they're purposed this way, a user must provide a username and a password when they want to access a particular TCP/IP port. The firewall then contacts the RADIUS server to verify the credentials given. If the verification is successful, the user is granted access to that port.
Terminal Access Controller Access Control System Plus (TACACS+)
The Terminal Access Controller Access-Control System Plus (TACACS+) protocol is also a AAA method and an alternative to RADIUS. Like RADIUS, it is capable of performing authentication on behalf of multiple wireless APs, RAS servers, or even LAN switches that are 802.1X capable. Based on its name, you would think it's an extension of the TACACS protocol (and in some ways it is), but the two definitely are not compatible.
Here are two major differences between TACACS+ and RADIUS:
- RADIUS combines user authentication and authorization into one profile, but TACACS+ separates the two.
- TACACS+ utilizes the connection-based TCP, but RADIUS uses UDP instead.
Even though both are commonly used today, because of these two reasons TACACS+ is considered more stable and secure than RADIUS.
Figure 16.2 shows how TACACS+ works.
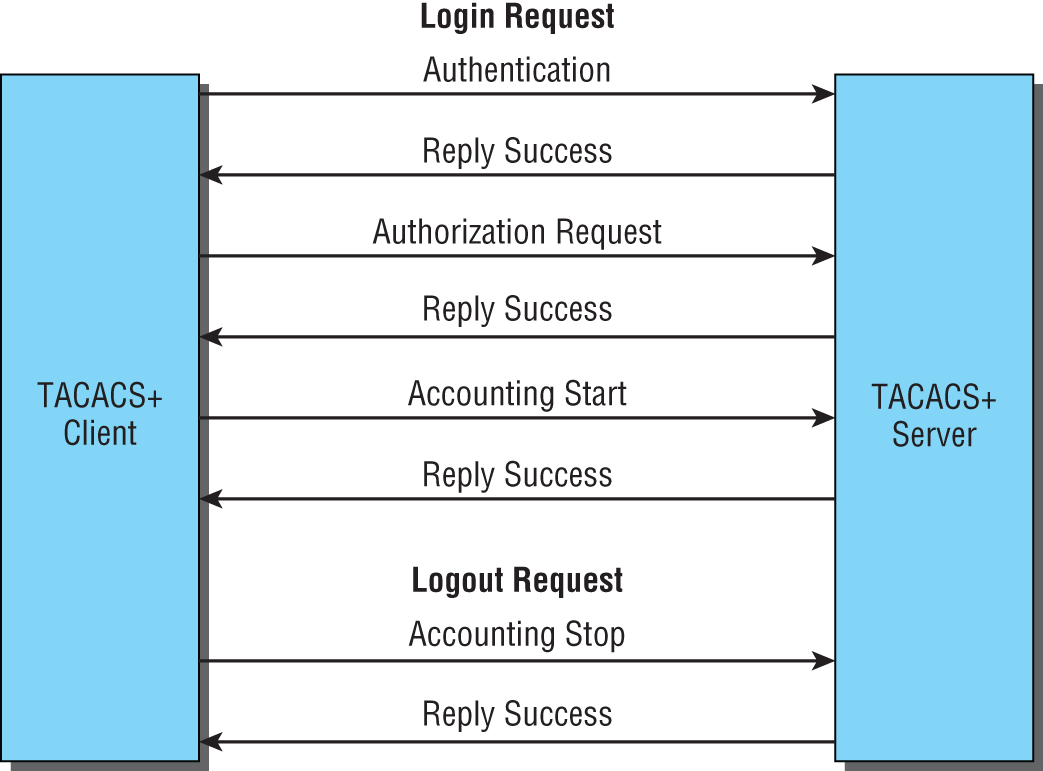
FIGURE 16.2 TACACS+ login and logout sequence
Just to clarify things, in the IT world, accounting has nothing to do with money. Here's what I mean: When a TACACS+ session is closed, the information in the following list is logged, or accounted for. This isn't a complete list; it's just meant to give you an idea of the type of accounting information TACACS+ gathers:
- Connection start time and stop time
- The number of bytes sent and received by the user
- The number of packets sent and received by the user
- The reason for the disconnection
The only time the accounting feature has anything to do with money is if your service provider is charging you based on the amount of time you've spent logged in or for the amount of data sent and received.
Single Sign-On (SSO)
In today's modern enterprises, users can be overwhelmed by the number of points in the network where they may be challenged to identify themselves. Most users have to log onto the domain to have network access at all, and then there may be company websites that require an authentication process to access databases, SharePoint sites, secured drives, personal folders, and on and on!
When users must remember multiple passwords, as the number increases, they begin to resort to unsafe security practices such as writing passwords on sticky notes, hiding passwords in their drawers, and even sharing them with coworkers. All of these practices undermine the security of the network.
Single sign-on addresses this problem. With single sign-on (SSO), when the user logs into the domain, the domain controller issues them an access token. This access token contains a list of all the resources (which can include folders, drives, websites, databases, and so on) to which they should have access. As a result, anytime the user accesses a resource, the token is verified behind the scenes, and the user never needs to provide another password!
LDAP
A directory service is a database designed to centralize data management regarding network subjects and objects. A typical directory contains a hierarchy that includes users, groups, systems, servers, client workstations, and so on. Because the directory service contains data about users and other network entities, it can be used by many applications that require access to that information. A common directory service standard is Lightweight Directory Access Protocol (LDAP), which is based on the earlier standard X.500.
X.500 uses Directory Access Protocol (DAP). In X.500, the distinguished name (DN) provides the full path in the X.500 database where the entry is found. The relative distinguished name (RDN) in X.500 is an entry's name without the full path.
LDAP is simpler than X.500. LDAP supports DN and RDN, but it includes more attributes, such as the common name (CN), domain component (DC), and organizational unit (OU) attributes. Using a client-server architecture, LDAP uses TCP port 389 to communicate. If advanced security is needed, LDAP over SSL communicates via TCP port 636.
Kerberos
Kerberos, created at MIT, isn't just a protocol, it's an entire security system that establishes a user's identity when they first log on to a system that's running it. It employs strong encryption for all transactions and communication, and it's readily available. The source code for Kerberos can be freely downloaded from lots of places on the Internet.
Kerberos works by issuing tickets to users who log in, kind of like going to an amusement park—as long as you have your ticket to ride, you're good to go. Even though the tickets expire quickly, they're automatically refreshed as long as you remain logged in. Because of this refresh feature, all systems participating in a Kerberos domain must have synchronized clocks. This synchronicity is a bit complicated to set up, although in Microsoft servers and domains the process is automatic, requiring only access to a recognized time server (which Microsoft also operates). The real negative hits happen if you have only one Kerberos authentication server—if it goes down, no one can log into the network. So when running Kerberos, having redundant servers is clearly vital. You should also know that because all users’ secret keys are stored in one centralized database, if that's compromised, you have a security tsunami on your hands. Luckily these keys are stored in an encrypted state. Figure 16.3 shows Kerberos in action.

FIGURE 16.3 Kerberos authentication
Local Authentication
When users authenticate to their computer, the authentication can be either to a domain or to the local machine. When local authentication is performed, the user's local account and password are verified with the local user database. This local user database is called Security Accounts Manager (SAM) and is located in C:windowssystem32config. In Linux, the database is a text file, /etc/passwd (called the password file), which lists all valid usernames and their associated information.
802.1X
Another form of network access control is 802.1X. This is a standard that defines a framework for centralized port-based authentication. It can be applied to both wireless and wired networks and uses three components:
- Supplicant: The user or device requesting access to the network
- Authenticator: The device through which the supplicant is attempting to access the network
- Authentication server: The centralized device that performs authentication
The role of the authenticator can be performed by a wide variety of network access devices, including remote access servers (both dial-up and VPN), switches, and wireless access points. The role of the authentication server can be performed by a Remote Authentication Dial-In User Service (RADIUS) or Terminal Access Controller Access-Control System Plus (TACACS+) server. The authenticator requests credentials from the supplicant and, upon receipt of those credentials, relays them to the authentication server, where they are validated. Upon successful verification, the authenticator is notified to open the port for the supplicant to allow network access.
This process is illustrated in Figure 16.4.
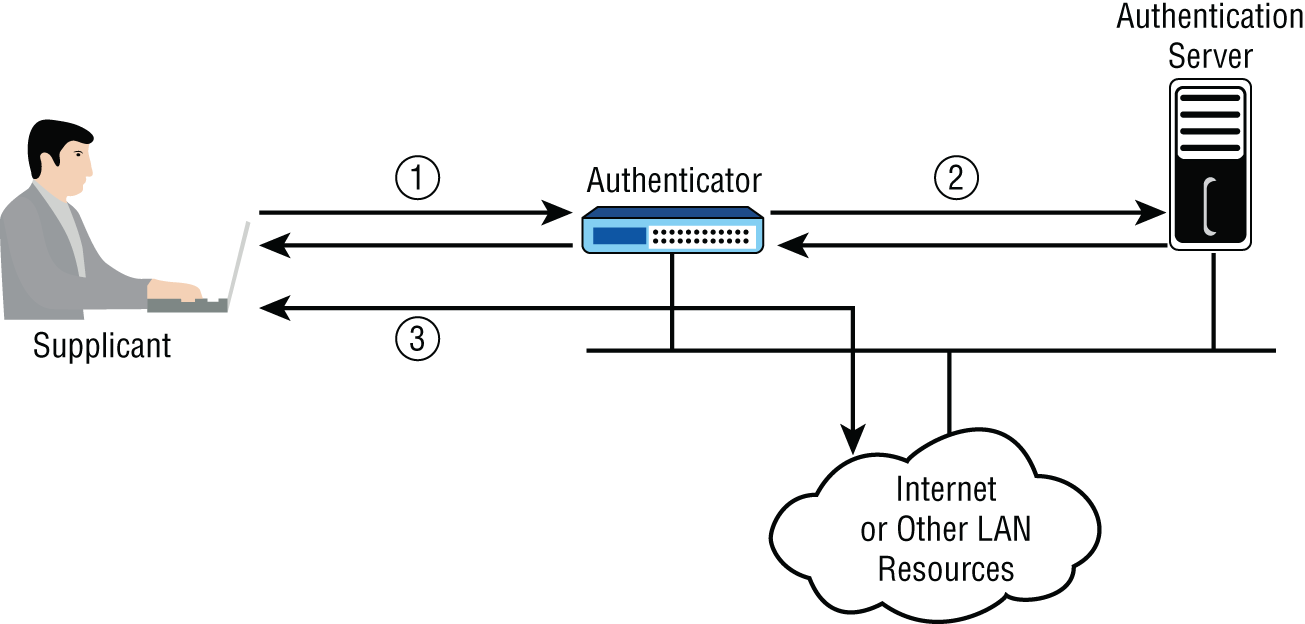
FIGURE 16.4 802.1X
Extensible Authentication Protocol (EAP)
Extensible Authentication Protocol (EAP) isn't a single method but a framework that enhances the existing 802.1X framework. The EAP framework describes a basic set of actions that will take place, and each EAP type differs in the specifics of how it operates within the framework. These variables include things like whether they use passwords or certificates as well as the ultimate level of security provided. Some of the EAP methods require that certificates be used as the credential during authentication. This means that to implement those methods, you must have a Public Key Infrastructure (PKI) in your network.
PEAP
Protected Extensible Authentication Protocol, also known as Protected EAP or simply PEAP, is a protocol that encapsulates the Extensible Authentication Protocol (EAP) within an encrypted and authenticated Transport Layer Security (TLS) tunnel. It requires only a server-side PKI certificate to create a secure TLS tunnel to protect user authentication.
EAP - FAST
EAP-FAST works in two stages. In the first stage, a TLS tunnel is established. Unlike PEAP, EAP-FAST's first stage is established by using a pre-shared key called a Protected Authentication Credential (PAC). In the second stage, a series of type/length/value (TLV)–encoded data is used to carry a user authentication.
EAP - TLS
EAP Transport Layer Security (EAP-TLS) is the most secure method, but it's also the most difficult to configure and maintain. To use EAP-TLS, you must install a certificate on both the authentication server and the client. An authentication server pair of keys and a client pair of keys need to be generated first, signed using a PKI, and installed on the devices. On the station side, the keys can be issued for the machine itself and/or for the user.
In the authentication stage, the station, along with the authentication server (RADIUS, etc.), exchange certificates and identify each other. Mutual authentication is a solid beneficial feature, which ensures that the station it's communicating with is the proper authentication server. After this process is completed, random session keys are created for encryption.
Preshared Key
Finally, a preshared key can be used to secure wireless transmissions. This is most labor intensive as it requires that all devices use the same key as the AP and that the keys be changed frequently to provide adequate security.
Security Risk Assessments
Security assessments are used to identify security weakness with the goal of eliminating them. This section of the chapter covers various assessment types that can be utilized to define where you are and help you define where you need to go.
Threat Assessment
Prior to performing a vulnerability or a penetration test, it is useful to identity the types of risk with which you are concerned. This effort can be enhanced by subscribing to threat feeds. Threat intelligence feeds are constantly updating streams of indicators or artifacts derived from a source outside the organization. These feeds are used to inform the organization as quickly as possible about new threats that have occurred. They contain the following information:
- Suspicious domains
- Lists of known malware hashes
- IP addresses associated with malicious activity
Later in this chapter, you will learn how security information and event management (SIEM) systems aggregate the log from various security devices into a single log for analysis. The reason for this is that by analyzing this single aggregated log, inferences can be made about potential issues or attacks that would not be possible if the logs were analyzed separately.
Using SIEM (or other aggregation tools) to aggregate threat feeds can also be beneficial, and there are tools and services for this. Among them are the following:
- Combine: Gathers threat intelligence feeds from publicly available sources.
- Palo Alto Networks AutoFocus: Provides intelligence, correlation, added context, and automated prevention workflows.
- Anomali ThreatStream: Helps deduplicate data, remove false positives, and feed intelligence to security tools.
- ThreatQuotient: Helps accelerate security operations with an integrated threat library and shared contextual intelligence.
- ThreatConnect: Combines external threat data from trusted sources with in-house data.
Vulnerability Assessment
Part of the security policy of an organization should address the type and frequency of vulnerability scans. These scans are designed to identify any security vulnerabilities that exist.
A vulnerability scanner can probe for a variety of security weaknesses, including misconfigurations, out-of-date software, missing patches, and open ports. One of the most widely used is Nessus, a proprietary vulnerability scanner developed by Tenable Network Security. A partial screen shot is shown in Figure 16.5. In the output, the issues found on a host are rated, and issues with the highest severity are at the top by default.
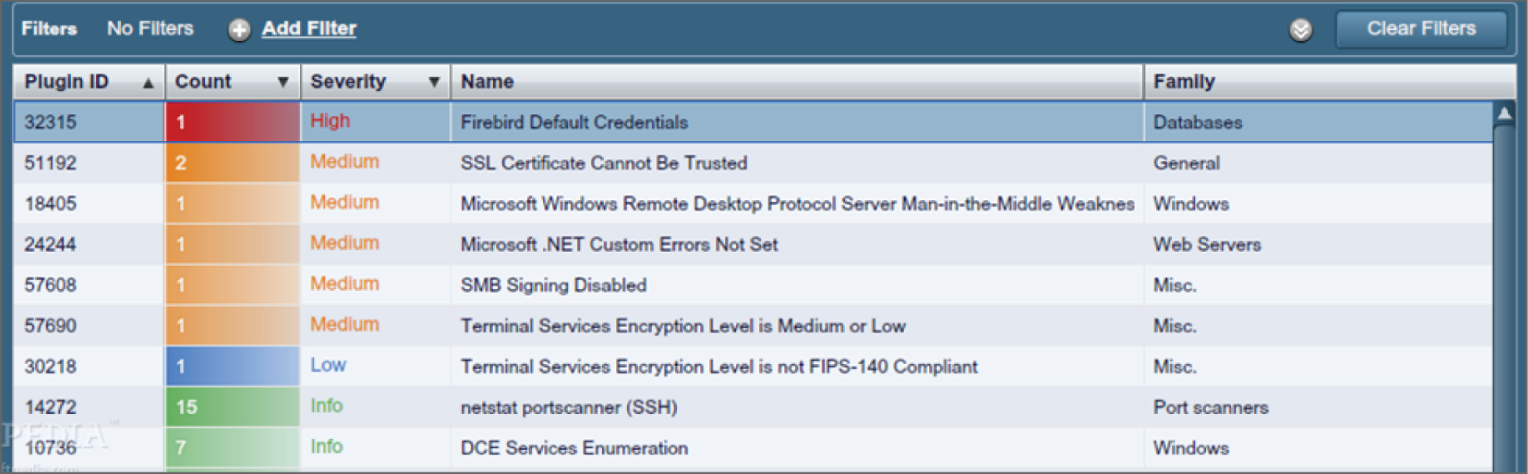
FIGURE 16.5 Nessus
Penetration Testing
A penetration test is designed to simulate an attack on a system, network, or application. Its value lies in its potential to discover security holes that may have gone unnoticed. It differs from vulnerability testing in that it attempts to exploit vulnerabilities rather than simply identify them.
Strategies for penetration testing are based on the testing objectives as defined by the organization:
- Blind Test: The testing team is provided with limited knowledge of the network systems and devices, using publicly available information. The organization's security team knows that an attack is coming. This test requires more effort by the testing team.
- Double-Blind Test: This test is like a blind test except the organization's security team does not know that an attack is coming. This test usually requires equal effort for both the testing team and the organization's security team.
- Target Test: Both the testing team and the organization's security team are given maximum information about the network and the type of test that will occur. This is the easiest test to complete, but it will not provide a full picture of the organization's security.
Business Risk Assessments
Although penetration testing can identify vulnerabilities, it is not the recommended way to do so. An organization should have a well-defined risk management process in place that includes the evaluation of risk that is present. When this process is carried out properly, threat modeling allows organizations to identify threats and potential attacks and implement the appropriate mitigations against these threats and attacks. These facets ensure that any security controls implemented are in balance with the operations of the organization.
Once all assets have been identified and their value to the organization has been established, specific threats to each asset are identified. An attempt must be made to establish both the likelihood of the threat's realization and the impact to the organization if it occurs. Only then can cost-effective mitigation be identified.
Process Assessment
Process assessment is the examination of all processes, policies and procedures that govern the way we do things. As technologies change and more options become available, new methods and approaches may be called for. The goal is continuous improvement.
Vendor Assessment
A business risk assessment should also include a careful review of all vendor relationships, asking the following questions:
- Are SLAs as robust as they should be and do they focus on security requirements?
- Are we too reliant on a single vendor for critical supplies and services? Is there a single point of failure in the supply chain?
- Does the access required indicate the need for additional agreements such as an interconnection agreement?
Security Information and Event Management (SIEM)
Security information and event management (SIEM) is a term for software products and services combining security information management (SIM) and security event management (SEM). SIEM technology provides real-time analysis of security alerts generated by network hardware and applications. You can get this as a software solution or a hardware appliance, and some businesses sell managed services using SIEM. Any one of these solutions provides log security data and can generate reports for compliance purposes.
The acronyms SEM, SIM, and SIEM are used interchangeably; however, SEM is typically used to describe the management that deals with real-time monitoring and correlation of events, notifications, and console views.
The term SIM is used to describe long-term storage, analysis, and reporting of log data. Recently, vSIEM (voice security information and event management) was introduced to provide voice data visibility.
SIEM can collect useful data about the following items:
- Data aggregation
- Correlation
- Alerting
- Dashboards
- Compliance
- Retention
- Forensic analysis
Notifications
SIEM systems not only assess the aggregated logs in real time, they generate alerts or notifications when an issue is discovered. This allows for continuous monitoring of the environment in a way not possible with other log centralization approaches such as syslog.
Summary
In this chapter you learned the basic concepts, terms, and principles that all network professionals should understand to secure an enterprise network. We covered concepts such as the CIA triad, internal and external threats, and how vulnerabilities can be classified using the CVE database.
You also learned that the defense-in-depth approach to security is the best and that utilizing design techniques such as a screened subnet along with other forms of segmentation makes addressing risks easier.
Finally, you learned about the various types of assessments that can be performed to test security, such as vulnerability assessments, penetration testing, risk assessments, and posture assessments.
Exam Essentials
- Explain common security concepts. These include the CIA triad, least privilege, zero-trust model, defense in depth, and separation of duties.
- Describe key security terms. Among these are vulnerabilities, exploits, and threats.
- Know how to utilize segmentation. You should know how to properly deploy screened subnets, VLANs, and broadcast domains as layer 1, 2, and 3 segmentations.
- Identify common authentication methods. These include multifactor, Terminal Access Controller Access-Control System Plus (TACACS+), single sign-on (SSO), Remote Authentication Dial-In User Service (RADIUS), LDAP, Kerberos, local authentication, 802.1X, and Extensible Authentication Protocol (EAP).
- Differentiate assessment types. These include vulnerability assessments, penetration testing, risk assessments, and posture assessments.
Written Lab
Complete the table by filling in the appropriate term for each authentication method.
You can find the answers in Appendix A.
| Authentication Method | Term |
|---|---|
| Utilizes the connection-based TCP protocol. | |
| When a user logs into the domain, the domain controller issues them an access token. | |
| The user's local account and password are verified with the local user database. | |
| Defines a framework for centralized port-based authentication. | |
| Combines user authentication and authorization into one profile. |
Review Questions
You can find the answers to the review questions in Appendix B.
- In which of the following access methods are new employees simply placed in the group and thus inherit all required permissions?
- Discretionary
- Role-based
- Mandatory
- Rule-based
- Which principle prescribes that users should be given access only to resources required to do their job?
- Least privilege
- Need to know
- Separation of duties
- Zero trust
- Which of the following occurs when a threat agent takes advantage of a weakness and uses it to advance an attack?
- Threat
- Breach
- Vulnerability
- Exploit
- Which of the following is an attack where no known fix exists?
- Advanced persistent
- Zero-day
- Pretexting
- Prime exploit
- Which of the following is maintained by the MITRE Corporation and includes entries that describe a vulnerability in detail, using a number and letter system?
- ISACA
- WHOIS
- CVE
- NIST
- Which of the following is not an external threat?
- Accidental file deletion by an employee
- DoS attack
- Fake contractor on site
- Malware infection by email
- Which concern do you have when you encrypt data before sending it?
- Accounting
- Availability
- Integrity
- Confidentiality
- You have decided that the default permission for all files will be NO access. What principle are you following?
- Defense in depth
- Need to know
- Separation of duties
- Zero Trust
- What are you following if you encrypt a file, apply access permissions to it, and lock the door to the room where the server on which the file resides is located?
- Defense in depth
- Need to know
- Separation of duties
- Zero Trust
- Which of the following is a method of checking the security health of network hosts before they're allowed to access the network?
- NAC
- DAC
- CVE
- CVSS
