Chapter 19
Remote Access Security
Think of remote access as a telecommuting tool because it's used by companies to allow remote employees to connect to the internal network and access resources that are in the office. Remote access is great for users who work from home or travel frequently, but clearly, to a stalking hacker, using an unsecured remote access connection is like stealing candy from a baby.
Using remote access requires a server configured to accept incoming calls and also requires remote access software to be installed on the client. Microsoft Windows operating systems, since Windows 95, have had remote access client software built in, and there are many third-party remote access clients available as well. Several different methods exist to create remote access connections. In this chapter we'll look at remote access and the VPN types that make it secure.
Site-to-Site VPN
Site-to-site VPNs, or intranet VPNs, allow a company to connect its remote sites to the corporate backbone securely over a public medium like the Internet instead of requiring more expensive wide area network (WAN) connections like Frame Relay. This is probably the best solution for connecting a remote office to a main company office because all traffic that goes between the offices will be encrypted with no effort on the part of the users.
In this scenario, all traffic that goes between the offices will go through the VPN tunnel. A site-to-site VPN is shown in Figure 19.1, along with a remote access called a client-to-site VPN covered in the next section. This solution requires a remote access client on the user device.
Client-to-Site VPN
Remote access VPNs or client-to-site VPN allow remote users like telecommuters to securely access the corporate network wherever and whenever they need to. It is typical that users can connect to the Internet but not to the office via their VPN client because they don't have the correct VPN address and password. This is the most common problem and one you should always check first.
In this scenario only the traffic between the user and the office will go through the VPN tunnel. A remote access VPN is shown in Figure 19.1. This solution requires a remote access client on the user device.

FIGURE 19.1 Site-to-site and client-to-site VPN
Clientless VPN
A clientless VPN enables end users to securely access resources on the corporate network from anywhere using an SSL/TLS-enabled web browser. They need no remote access client to do this, only a browser that can perform SSL or the more secure TLS. A clientless VPN is shown in Figure 19.2.
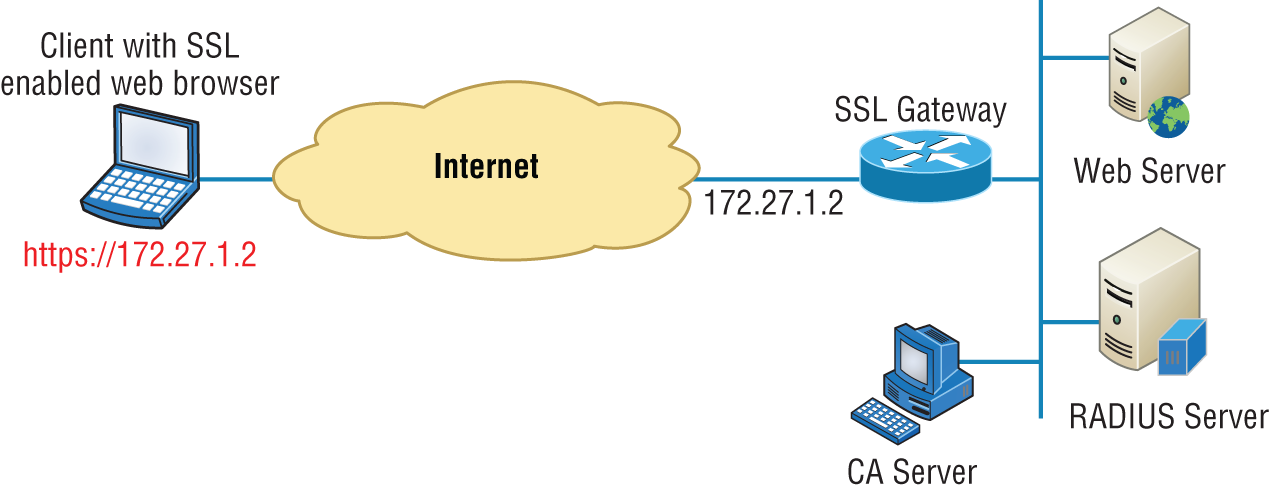
FIGURE 19.2 Clientless VPN
Split Tunnel vs. Full Tunnel
When a client-to-site VPN is created it is possible to do so in two ways, split tunnel and full tunnel. The difference is whether the user use the VPN for connecting to the Internet as well as for connecting to the office.
Split tunneling works by using two connections at the same time: the secure VPN connection and an open connection to the Internet. So in split tunneling, only traffic to the office goes through the VPN. Internet traffic does not. The security issue with this is that while the user is connected to the VPN, they are also connected to the most untrusted network, the Internet.
With full tunnel, all traffic goes through the VPN, which means the user is accessing the Internet through the connection of the office and so all traffic will be examined by the office security. Split and full tunnel are shown in Figure 19.3.

FIGURE 19.3 Split and full tunnel
Remote Desktop Connection
There are times when you need to make a remote connection to a machine to perform troubleshooting but you are miles away. Connectivity software is designed to allow you to make a connection to a machine, see the desktop, and perform any action you could perform if you were sitting in front of it.
Microsoft has made what it calls Remote Desktop software available for free with Windows products since Windows NT. When this software is installed (installed by default in later versions) on both source and destination computers, a remote desktop connection can be made.
Commercial tools are also available that (of course) claim to have more functionality, and they probably do have a few extra bells and whistles. These include LogMeIn.com, GoToMyPC, and others.
The advantages of these connectivity tools are obvious. With these tools, you can do anything you need to on the machine as long as you can connect. They also allow you to see what a user is actually doing when they encounter a problem rather than having to rely on what they tell you they are doing. You can even show a user what they are doing wrong. Most of these tools allow for chat sessions and for either end of the connection to take control of the machine. You can also transfer files to them if required (maybe a DLL got deleted, for example).
Remote Desktop Gateway
Remote Desktop Protocol (RDP) is a proprietary protocol developed by Microsoft. It allows you to connect to another computer and run programs. RDP operates somewhat like Telnet, except instead of getting a command-line prompt as you do with Telnet, you get the actual graphical user interface (GUI) of the remote computer. Clients exist for most versions of Windows, and Macs now come with a preinstalled RDP client.
Microsoft currently calls its official RDP server software Remote Desktop Services; it was called Terminal Services for a while. Microsoft's official client software is currently referred to as Remote Desktop Connection, which was called Terminal Services Client in the past.
RDP is an excellent tool for remote clients, allowing them to connect to their work computer from home, for example, and get their email or perform work on other applications without running or installing any of the software on their home computer.
RDP allows users to connect to a computer running Microsoft's Remote Desktop Services, but a remote computer must have the right kind of client software installed for this to happen. Most Windows-based operating systems include an RDP client, and so do most other major operating systems, like Linux, Solaris, and macOS. Microsoft began calling all terminal services products Remote Desktop with Windows Server 2008 R2. RDP uses TCP port 3389.
After establishing a connection, the user sees a terminal window that's basically a preconfigured window that looks like a Windows desktop or another operating system's desktop. From there, the user on the client computer can access applications and files available to them by using the remote desktop.
The most current version of RDC is RDC 1.2.1953. When logged in using RDP, clients are able to access local files and printers from the remote desktop just as if they were logged into the network.
RDP Gateway
RDP Gateway is a more secure version of RDP created by RouterHosting. It is more secure than the public or MS version in the following ways:
- You don't need to use a VPN. Using the SSL channel, RDP Gateway can tunnel directly to the remote server to increase the security of RDS.
- No pass through a third-party website or service.
- Native Windows Server service.
- Can be combined with Network Access Protection.
- Can be used along with Microsoft Internet Security and Acceleration (ISA), the Microsoft implementation of RADIUS.
SSH
Secure Shell is a network protocol that is designed as an alternative to command-based utilities such as Telnet that transmit requests and responses in clear text. It creates a secure channel between the devices and provides confidentiality and integrity of the data transmission.
It uses public-key cryptography to authenticate the remote computer and allow the remote computer to authenticate the user, if necessary. This public key is placed on any computer that must allow access to the owner of a matching private key (the owner keeps the private key in secret). The private key is never transferred through the network during authentication.
Don't use Telnet! Telnet is totally insecure because it sends all data in crystal-clear text—including your name and password. And I'm pretty sure you know that's a really bad thing these days. If Microsoft doesn't even enable it on its latest OSs, then you know it really must be insecure.
Some configuration is usually necessary if you want things to work as they really should, and yes, sometimes it's a little painful to get everything running smoothly, but it's all worth it in the long run. Personally, I disable Telnet on all my routers and use SSH exclusively. No lie—I never use Telnet anymore if I can help it. Even so, you should still understand Telnet and get in some practice with it in case you do ever need it.
Virtual Network Computing (VNC)
Virtual Network Computing (VNC) is a remote desktop sharing system that uses the Remote Frame Buffer (RFB) protocol. It is platform independent and provides an experience much like Remote Desktop Protocol (RDP).
VNC includes the following components:
- VNC server: Software that runs on the machine sharing its screen
- VNC client (or viewer): Software on the machine that is remotely receiving the shared screen
- VNC protocol (RDP)
One big difference in VNC and RDP is that VNC sends raw pixel data (which does make it work on any desktop type) while RDP uses graphic primitives or higher-level commands for the screen transfer process.
Virtual Desktop
Using operating system images for desktop computers is not a new concept. Nor is delivering these desktop images to users from a virtual environment when they start their computer. This allows for the user desktop to require less computing power, especially if the applications are also delivered virtually and those applications are running in a VM in the cloud rather than in the local desktop eating up local resources. Another benefit of using virtual desktops is the ability to maintain a consistent user environment (same desktop, applications, etc.), which can enhance user support.
Authentication and Authorization Considerations
The most effective way to control both authentication of remote users and the application of their permissions is to provision an AAA server. AAA services is covered in Chapter 5, “Networking Devices,” and Chapter 16, “Common Security Concepts.”
In-Band vs. Out-of-Band Management
Out-of-band management refers to any method of managing the server that does use the network. An example of this technology is Integrated Lights-Out, or iLO, a technology embedded into HP servers that allows for out-of-band management of the server. The physical connection is an Ethernet port that will be on the server and will be labeled ILO. In Figure 19.4, one of these ILO ports is shown (labeled number 2) in an HP Moonshot chassis (these hold blade servers). HP iLO functions out-of-the-box without additional software installation regardless of the server's state of operation, giving you complete access to the server from any location via a web browser or the iLO Mobile app.

FIGURE 19.4 ILO port
Summary
In this chapter you learned the importance of providing both fault tolerance and high availability. You also learned about VPN architectures. These include site-to-site VPNs, client-to-site VPN, clientless VPN, split tunnel vs. full, and SSH VPN.
We also looked at SSL and TLS, including common applications with respect to VPNs. Finally, we identified other remote access solutions., such as VNC, RDP, remote desktop gateway, remote desktop connections, and virtual connections.
Exam Essentials
- Explain VPN architectures. These include site-to-site VPNs, client-to-site VPN, clientless VPN, split tunnel vs. full, and SSH VPN.
- Describe SSL and TLS. This includes the differences between the two and the advantages of TLS. It also includes common applications with respect to VPNs.
- Identify other remote access solutions. These include VNC, RDP, remote desktop gateway, remote desktop connections, and virtual connections.
Written Lab
Complete the table by filling in the appropriate definition for each term.
You can find the answers in Appendix A.
| Term | Definition |
|---|---|
| Clientless VPN | |
| Full tunnel | |
| Site-to-site VPN | |
| Split tunnel | |
| Client-to-site VPN |
Review Questions
You can find the answers to the review questions in Appendix B.
- Integrated Lights-Out is an example of which of the following technologies?
- Captive portal
- Out-of-band management
- Clientless VPN
- AAA
- The most effective way to control both authentication of remote users and the application of their permissions is to provision which of the following?
- Captive portal
- AAA
- LDAP
- RDP
- Which of the following is an operating system image delivered over the network at each startup?
- VNC
- Virtual desktop
- Remote desktop
- RDP
- Which of the following is not a component of Virtual Network Computing (VNC)?
- VNC server
- VNC client
- VNC desktop
- VNC protocol
- Which of the following is a network protocol that is designed as an alternative to command-based utilities such as Telnet?
- SSL
- SSH
- STP
- STFP
- Which of the following allows you to tunnel directly to the remote server with no VPN?
- Split tunnel
- RDP Gateway
- Full tunnel
- VNC
- Which of the following was formerly called Terminal Services Client?
- Virtual desktop
- Remote Desktop Connection
- VNC
- RDP Gateway
- Which of the following operates somewhat like Telnet, except instead of getting a command-line prompt as you do with Telnet, you get the actual graphical user interface (GUI) of the remote computer?
- RBAC
- SSH
- RDP
- SSL
- Which of the following is not an example of a remote desktop connection?
- RDP
- LogMeIn
- GoToMyPC
- SSH
- Split tunnel and full tunnel are examples of which type of VPN?
- Client-to-site
- Site-to-site
- RDP VPN
- Clientless VPN
