Chapter 18
Network Hardening Techniques
It's true … you're not paranoid if you think they really are out to get you. Although “they” probably aren't after you personally. Your network—no matter the size—is seriously vulnerable, so it's wise to be very concerned about keeping it secure. Unfortunately, it's also true that no matter how secure you think your network is, it's a good bet that there are still some very real threats out there that could breach its security and totally cripple your infrastructure!
One of the ongoing goals of operations security is to ensure that all systems have been hardened to the extent that is possible and still provide functionality. The hardening can be accomplished both on a physical and logical basis. From a logical perspective, this is accomplished if you do this:
- Remove unnecessary applications.
- Disable unnecessary services.
- Block or disable unrequired ports.
- Tightly control the connecting of external storage devices and media if it's allowed at all.
In this chapter, you'll learn best practices for hardening devices and for hardening the network environment in which these devices reside. At the end of the chapter, you'll learn about the newest challenge to secure, the Internet of Things (IoT).
Best Practices
While hardening devices may present a challenge, you are not alone in your efforts to meet that challenge. Over time, best practices have been developed by those that came before you in this battle. These are lessons that have been learned the hard way and are certainly concepts and principles that you can utilize to ensure you don't make the same mistakes that led to these hard-earned lessons. In the following sections, you'll learn some of the more common best practices for hardening devices and the network environment.
Secure SNMP
In Chapter 13, “Using Statistics and Sensors to Ensure Network Availability,” you learned that SNMP has three versions. SNMPv3 supports strong authentication with confidentiality (encryption) and data integrity of messages via encryption between agents and managers. For this reason, you should always ensure that the version you are using is version 3.
Version 3 offers two methods of securing SNMP. The Transport Security Model (TSM) component of SNMPv3 enables security to be applied at the Transport layer. Protocols used by the Transport Security Model, such as TLS, are based on asymmetric cryptography.
RFC 3414 describes a user-based security model (USM) that provides message-based security and uses symmetric encryption along with usernames and passwords.
Router Advertisement (RA) Guard
In Chapter 10, “Routing Protocols,” you learned about how routers running IPv6 use a Router Advertisement in neighbor discovery and solicitation. Capturing these packet types could reveal information about the routers and their neighbors. These packet types can also be spoofed as well. IPv6 Router Advertisement (RA) Guard is not yet a standard but a proposal on a method of allowing the network administrator to block or reject unwanted or rogue RA Guard messages that arrive at the network device platform.
RA Guard compares configuration information on the switch with the information found in the received RA frame. Once the switch has validated the content of the RA frame, it forwards the RA to its unicast or multicast destination. If the RA frame content is not validated, the RA is dropped. As you see in Figure 18.1, the switch only validates RA packets from the two configured IPv6 addresses.
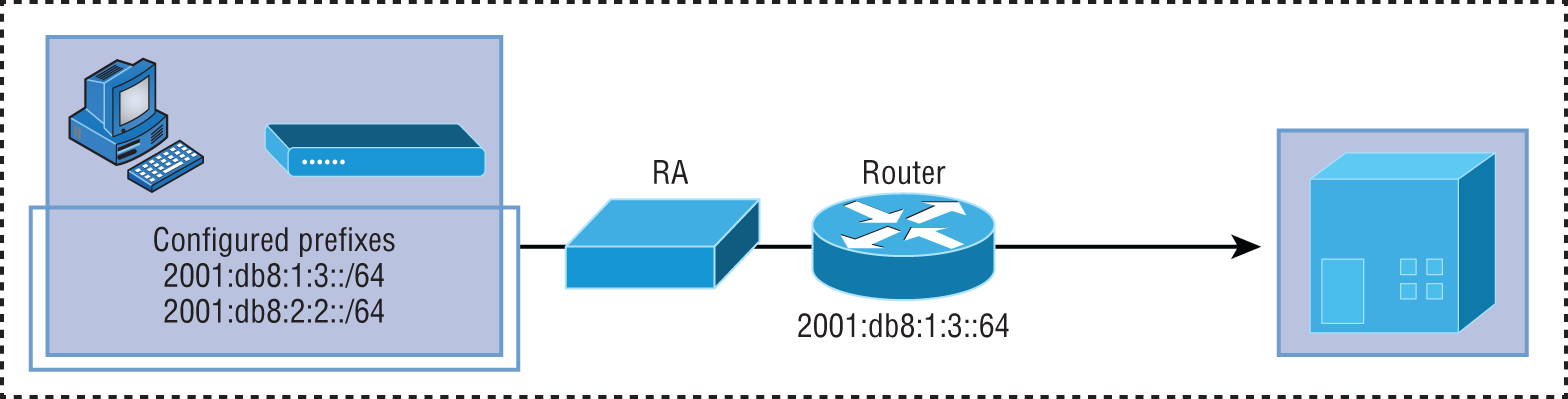
FIGURE 18.1 RA Guard
Port Security
In Chapter 11, “Switching and Virtual LANs,” you learned about the use of port security on a switch. This can be used as a device hardening technique in instances where you would like to provide layer 2 separation between devices connected to the same switch or residing in the same VLAN (in the case of VLANs spanning multiple switches).
This is also a network hardening technique in that it can help prevent a hacker from disconnecting a device from the wall and using that port for access. While your unused ports should always be disabled, legitimate ports are always at danger of misuse this way. By limiting network access on a port to a single MAC address (or in the case of an IP phone, two), access by any other MAC address can be prevented.
Finally, it can be used to prevent the connections of a hub to a switch port by limiting the number of MAC addresses that can transmit on a port to one or two addresses.
Dynamic ARP Inspection
Many on-path/man-in-the-middle attacks are made possible by the attacker polluting the ARP cache of the two victims such that their cache maps each other's IP addresses to the MAC address of the attacker, thus allowing the attacker to receive all traffic in the conversation.
Dynamic ARP inspection (DAI) is a feature that, when configured, uses the DHCP snooping database of IP address–to–MAC address mappings to verify the MAC address mappings of each frame going through the switch. In this way, any frames with incorrect or altered mappings are dropped by the switch, thus breaking any attacks depending on these bogus mappings. Because it uses the DHCP snooping database, the configuration of DHCP snooping is a prerequisite to enabling DAI.
Control Plane Policing
In a network, three planes typically form the networking architecture:
- Control plane: This plane carries signaling traffic originating from or destined for a router. This is the information that allows routers to share information and build routing tables.
- Data plane: Also known as the forwarding plane, this plane carries user traffic.
- Management plane: This plane administers the router.
Control plane policing is a feature that can be implemented to protect and secure packets on the control plane. It is a quality of service (QoS) policy that is applied by the router's control plane. By rate limiting the control packets that can arrive to the router processor, it can prevent denial of service (DoS) attacks.
Private VLANs
In Chapter 11 you learned about VLANs. You saw that devices that reside in different VLANs reside in different layer 3 networks as well. Private VLANs are a type you can implement on a switch to segregate devices that reside in the same layer 3 network.
When this is done, the private VLAN (called secondary) is simply a subsection of the main VLAN (called primary). The secondary VLAN can be of two types, community (which can contain multiple devices that can talk to one another) or an isolated VLAN (in which a single device can only talk to the switch). The second VLAN type is excellent for isolating a device from other devices.
Disable Unneeded Switchports
All unused ports on the switch should be disabled to prevent the connection of a rogue device into an unused wall outlet. Each switchport to which unused wall outlets are connected should be identified and disabled.
Disable Unneeded Network Services
Destination services and applications are specified in a packet in terms of a port number. When a device is open to receiving a connection to a service or application, it is said to be listening on the corresponding port. Therefore, closing or disabling a port eliminates the possibility of a malicious user connecting to that port and leveraging any weakness that may be known to be present with that service.
It is a standard device hardening practice to close any ports not required for the proper functioning of a device based on its role in the network. For example, a DNS server should have no other ports open but port 53, which is used to service DNS.
Change Default Passwords
Many network devices are configured with default administrator accounts and their default passwords. These accounts should be disabled and renamed if possible. At the very least, the passwords for these accounts should be changed from the default because they are well-known, available in documentation that comes with the product, and also widely available on the Internet.
Password Complexity/Length
Strong passwords should be at least 8 characters (the more, the merrier), but they shouldn't be any longer than 15 characters to make them easier to remember. You absolutely must specify a minimum length for passwords because a short password is easily cracked— after all, there are only so many combinations of three characters, right? The upper limit depends on the capabilities of your operating system and the ability of your users to remember complex passwords. Here's what I call “The Weak List” for passwords—never use them!
- The word password (Not kidding—people actually do this!)
- Proper names
- Your pet's name
- Your spouse's name
- Your children's names
- Any word in the dictionary
- A license plate number
- Birth dates
- Anniversary dates
- Your username
- The word server
- Any text or label on the PC or monitor
- Your company's name
- Your occupation
- Your favorite color
- Any of the above with a leading number
- Any of the above with a trailing number
- Any of the above spelled backward
There are more, but you get the idea, and these really are the most commonly used brainless passwords. These settings on a Windows machine are shown in Figure 18.2.
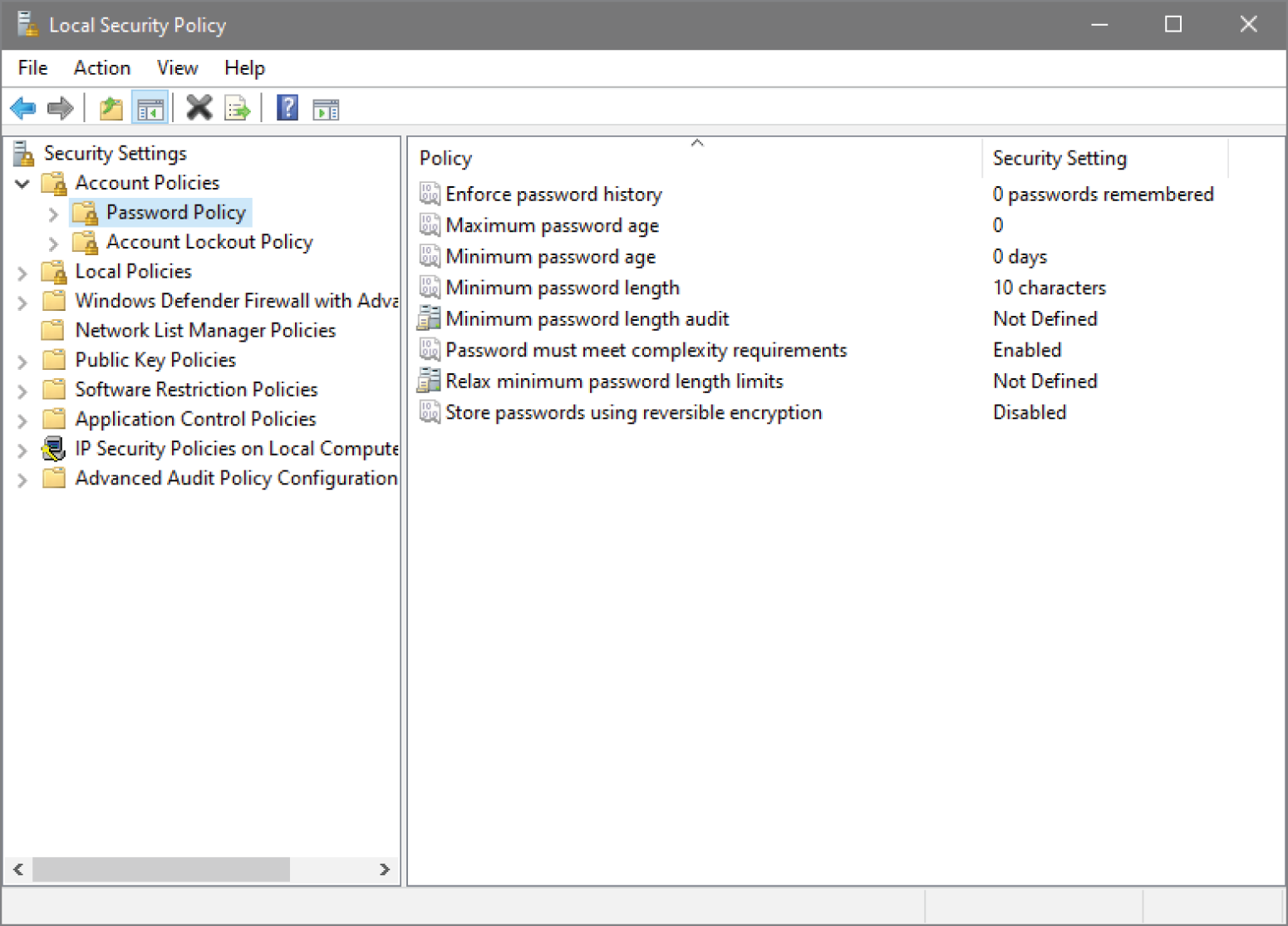
FIGURE 18.2 Password Policy settings
Using Characters to Make a Strong Password
The good news is that solid passwords don't have to be in ancient Mayan to be hard to crack. They just need to include a combination of numbers, letters, and special characters— that's it. Special characters aren't letters or numbers but symbols like $ % ^ # @). Here's an example of a strong password: tqbf4#jotld. Looks like gibberish, but remember that famous sentence, “The quick brown fox jumped over the lazy dog”? Well, this particular password uses the first letter of each word in that sentence with a 4# thrown in the middle of it.
Sweet—solid and easy to remember. You can do this with favorite quotes, song lyrics, and so on, with a couple of numbers and symbols stuck in the middle. Just make sure you don't sing the song or quote Shakespeare every time you log in!
If you want to test the strength of passwords to make sure they're nice and tight, you can use auditing tools like crack programs that try to guess passwords. Clearly, if that program has a really tough time or even fails to crack the password, you have a good one. By the way, don't just use a regular word preceded by or ending with a special character because good crack programs strip off the leading and trailing characters during decryption attempts.
Enable DHCP Snooping
A rogue DHCP server (one not under your control that is giving out incompatible IP addresses) can be an annoyance that causes users to be unable to connect to network resources, or it may play a part in several types of attacks. In either case, DHCP snooping is a switch feature that can help to prevent your devices from communicating with illegitimate DHCP servers.
When enabled, DHCP snooping allows responses to client requests from only DHCP servers located on trusted switch ports (which you define). When only ports where company DHCP servers are located are configured to be trusted, rogue DHCP servers will be unable to respond to client requests.
The protection doesn't stop there, however. The switch will also, over time, develop an IP address–to–MAC address table called the bindings table, derived from “snooping” on DHCP traffic to and from the legitimate DHCP server. The bindings table will alert the switch to any packets that have mappings that do not match the table. These frames will be dropped. The bindings table is also used with ARP inspection, which makes the configuration and enabling of DHCP snooping a prerequisite of ARP inspection.
Change Default VLAN
All switches have a VLAN by default called VLAN1. You can't change or even delete the default VLAN; it is mandatory. The default VLAN is simply the VLAN to which all access ports are assigned to until they are explicitly placed in another VLAN. While you can't change the default VLAN, you can create a new VLAN and move all switch ports to that VLAN. Since VLAN1 is typically set as the default for most vendors, it becomes a well-known configuration for attackers to abuse.
Patch and Firmware Management
In some cases, applying patches, especially device driver updates, can be problematic. Issues can include the device no longer working, loss of some key functionality, or generation of odd error messages. When this occurs, you may want to make use of the procedure covered in the next section.
Rollback
While rollback is a general term that applies to reversing any operation related to device drivers, it means to remove the newer driver and go back to using the previous driver. This is typically an available option if the last driver you used is the driver to which you want to roll back.
If you don't have automatic updates set up, you can download patches and hotfixes manually. A hotfix is just like a patch that updates software, but this term is reserved for a solution to potentially serious issues that could compromise your network and hosts. When a company like Microsoft used to create a whole bunch of patches, hotfixes, and upgrades, it would put them together in a larger bundle called a service pack. For instance, you could download Windows 7 Service Pack 1 (SP1) or Windows Server 2008 Service Pack 2 (SP2), which will update lots of components and address security, performance, and stability issues all at the same time. Windows 10 is different as there are no service packs. Instead, Microsoft issue updates when they are ready rather than batching them together in one huge update.
Firmware Updates
While keeping operating system and application patches up-to-date gets most of the attention, there are devices on your network that may require firmware updates from time to time. Firmware is a form of program code and related data that is stored in persistent memory of some sort, such as non-volatile RAM (NVRAM).
In many cases, firmware updates are designed to increase the functionality of a device.
In other cases, they may correct a bug or flaw in the system. Firmware updates are much more infrequent than other types of updates, so it's easy to forget about them. You should always agree to be contacted by manufacturers regarding these updates because they are not as widely publicized as other types of updates.
Updating firmware is a process sometimes called flashing, in which the old firmware instructions are overwritten by the new ones. You should carefully follow the process described in the manufacturer's documentation because failure to do so can lead to the device being made useless (sometimes called bricking the device).
Driver Updates
Drivers are files that allow a peripheral or component to talk to the hardware layer of the hosting device. In most cases, the drivers you need for a device will already be present in the drive cache that is installed with the operating system, but sometimes, especially with new devices, this will not be the case. In those instances, you will have to allow the system to locate the driver file from the media that came with the device, or in extreme instances, you may have to search for it on the Internet. You should always start your search on the website of the manufacturer. Drivers found elsewhere may be problematic and, in some cases, may introduce malware.
Drivers also need to be updated from time to time. If you have computers set to receive updates automatically, updated drivers can be among the items you select to receive. Not all devices can benefit from automatic updating, and you may be required to check manually from time to time for driver updates for other devices, such as printers, scanners, and cameras.
Access Control List
It's rare to find a network around these days that isn't connected to the Internet. The Internet is clearly a public internetwork that anyone can connect to, but your company's or personal network is, and should definitely be, a private one. The catch here is that every time you connect to the Internet (where everyone is welcome) from a private network, you're instantly vulnerable to security break-ins. This is where something we call a firewall comes into play. Firewalls are basically tools that you can implement to prevent any unauthorized users roaming around on public networks from gaining access to your private network.
Firewalls can be either stand-alone devices or combined with another hardware device like a server or a router. And although firewalls can use a lot of various technologies to restrict information flow, their primary weapon is known as an access control list (ACL).
Access control lists (ACLs) typically reside on routers to determine which packets are allowed to route through them based on the requesting device's source or destination Internet Protocol (IP) address. Oh, and just so you know, ACLs have been around for decades and have other uses apart from firewalls.
Figure 18.3 demonstrates how ACLs prevent users on Network B from accessing Network A.
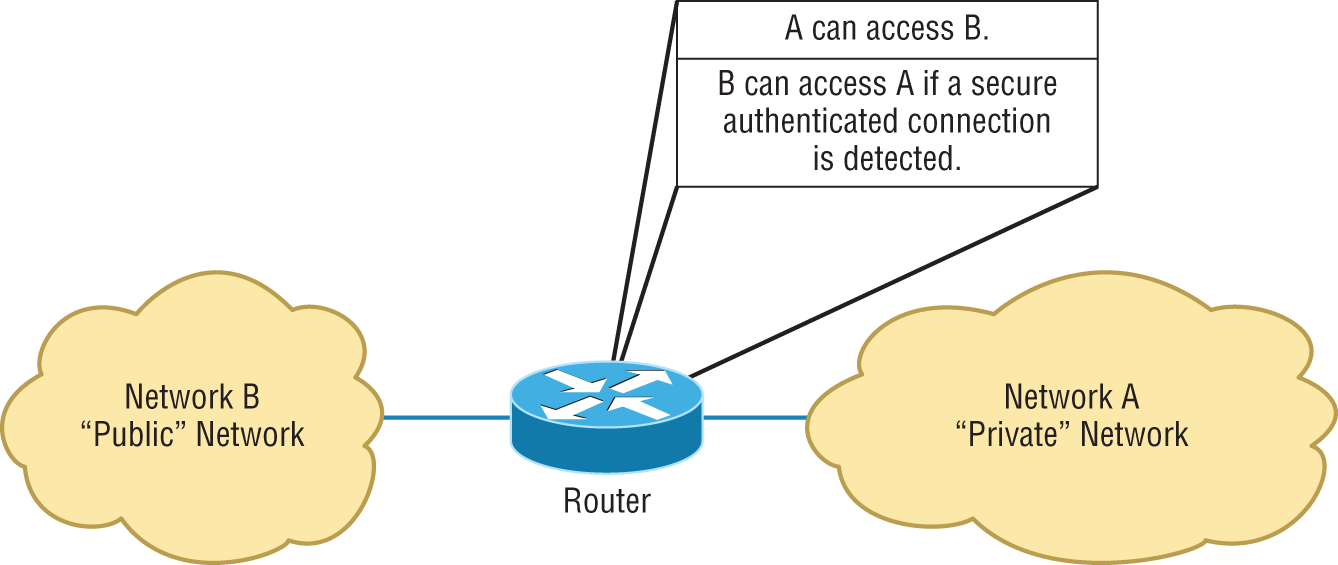
FIGURE 18.3 Two networks with an ACL-enabled router
Okay, what we see here is that users in Network A can pass through the router into Network B. This means that an IP spoofing attack, when someone pretends to have a network address on the inside of a firewall to gain network access, can still happen if a user in Network B pretends to be located in Network A.
You can create a wide array of ACLs, from the very simple to the highly complex, depending on exactly what you want to have them do for you. One example is placing separate inbound and outbound ACLs on a router to ensure that the data that's leaving your network comes from a different source than the data that's coming into it.
When configuring ACLs between the Internet and your private network to mitigate security problems, it's a good idea to include these four conditions:
- Deny any addresses from your internal networks.
- Deny any local host addresses (127.0.0.0/8).
- Deny any reserved private addresses.
- Deny any addresses in the IP multicast address range (224.0.0.0/4).
None of these addresses should ever be allowed to enter your internetwork. Interestingly enough, because of the way in which in-public IP addresses are issued, with some research you can create a filter that blocks a country, state, or even locale based on IP addresses!
Role-Based Access
Role-based access control (RBAC) is commonly used in networks to simplify the process of assigning new users the permission required to perform a job role. In this arrangement, users are organized by job role into security groups, which are then granted the rights and permissions required to perform that job. This process is pictured in Figure 18.4. The role is implemented as a security group possessing the required rights and permissions, which are inherited by all security group or role members.
This is not a perfect solution, however, and it carries several security issues. First, RBAC is only as successful as the organization policies designed to support it. Poor policies can result in the proliferation of unnecessary roles, creating an administrative nightmare for the person managing user access. This can lead to mistakes that reduce rather than enhance access security.
A related issue is that those managing user access may have an incomplete understanding of the process, and this can lead to a serious reduction in security. There can be additional costs to the organization to ensure proper training of these individuals. The key to making RBAC successful is proper alignment with policies and proper training of those implementing and maintaining the system.
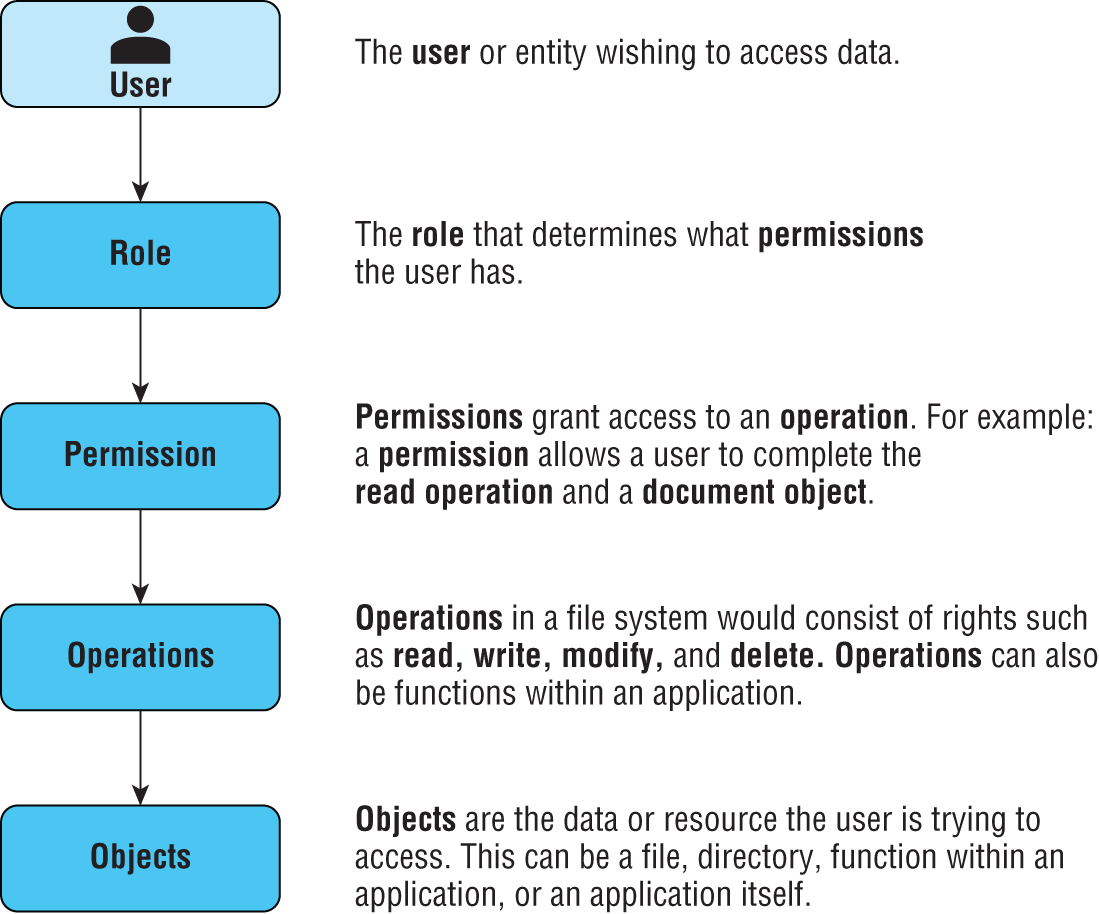
FIGURE 18.4 RBAC
Firewall Rules
In Chapter 5, “Networking Devices,” you learned about firewalls. If the access control lists are misconfigured on a firewall, the damage will fall into one of three categories:
- Traffic is allowed that shouldn't be allowed.
- Traffic that should be allowed is blocked.
- No traffic is allowed at all.
The first two problems are a matter of specifying the wrong traffic type in a permit or deny rule. Because in many cases the traffic type is specified in terms of a port number, it is critical to know the port numbers of the traffic you are dealing with.
The last problem can be either a simple omission or a complete misunderstanding of how ACLs work. At the end of every ACL is an implied rule that blocks all traffic that has not been allowed by earlier rules in the rule set. This means that all ACLs should have a rule at the end that allows all traffic that should be allowed. An ACL with no permit statements will block all traffic.
When developing rules for firewalls there are two basic approaches.
Explicit Deny
Using this approach, all traffic is allowed unless it is specially (explicitly) denied with a rule. This is also referred to as blacklisting in that you are creating a blacklist of denied traffic. The issue with this approach is that you must identify all possible malicious traffic, which can be overwhelming.
Implicit Deny
With this approach, all traffic is denied unless it is specifically or implicitly allowed by a rule. This is also called whitelisting in that you are creating a whitelist of allowed traffic with the denial of all other traffic. Many consider this to be the more secure approach. You need only identify what is required traffic, a much more manageable effort than identifying all possible malicious traffic.
Wireless Security
While we discussed wireless security in Chapter 12, “Wireless Networking,” now let's focus on some of the issues to be found with WLAN. In this section you'll learn about some techniques that can be used to secure them.
MAC Filtering
Client MAC addresses can be statically typed into each access point, allowing MAC filtering, and any frames that show up to the AP without a known MAC address in the filter table will be denied access. Sounds good, but of course all MAC layer information must be sent in the clear—anyone equipped with a free wireless sniffer can just read the client packets sent to the access point and spoof their MAC address. If you have a small number of wireless clients and you don't want to deploy an encryption-based access method, MAC address filters may be sufficient.
Antenna Placement
In Chapter 12 you learned about the importance of a site survey in identifying proper antenna placement. The security aspect of antenna placement is also critical. Since you cannot prevent the capture of wireless frames being broadcast by the AP, limiting the exposed areas of the broadcast signal helps to limit eavesdropping.
In the next section you will learn about using power levels to expand and contract the size of the cell around the AP. While this is an available option, keep in mind that as you raise and lower the power, you are expanding and contracting the signal in all directions. In some cases, there is a need to reshape the cell rather than expand or contract it.
When you need to reshape the cell, you use antennas to accomplish this. For example, you may want to send the signal down a long hallway while not transmitting outside the hallway into the parking lot. That could be done with a directional antenna. For more on antennas, see Chapter 12.
Power Levels
Location, location, location. You've got only two worries with this one: Your clients are either too far or not far enough from the AP. If your AP doesn't seem to have enough power to provide a connectivity point for your clients, you can move it closer to them, increase the distance that the AP can transmit by changing the type of antenna it uses, or use multiple APs connected to the same switch or set of switches to solve the problem. If the power level or signal is too strong, and it reaches out into the parking area or farther out to other buildings and businesses, place the AP as close as possible to the center of the area it's providing service for. And don't forget to verify that you've got the latest security features in place to keep bad guys from authenticating to and using your network.
Wireless Client Isolation
Wireless client isolation prevents wireless stations within an SSID from communicating directly with one another or with any devices on the wired network to which the wireless network might be connected. They can only access the Internet. The setting is shown in Figure 18.5.
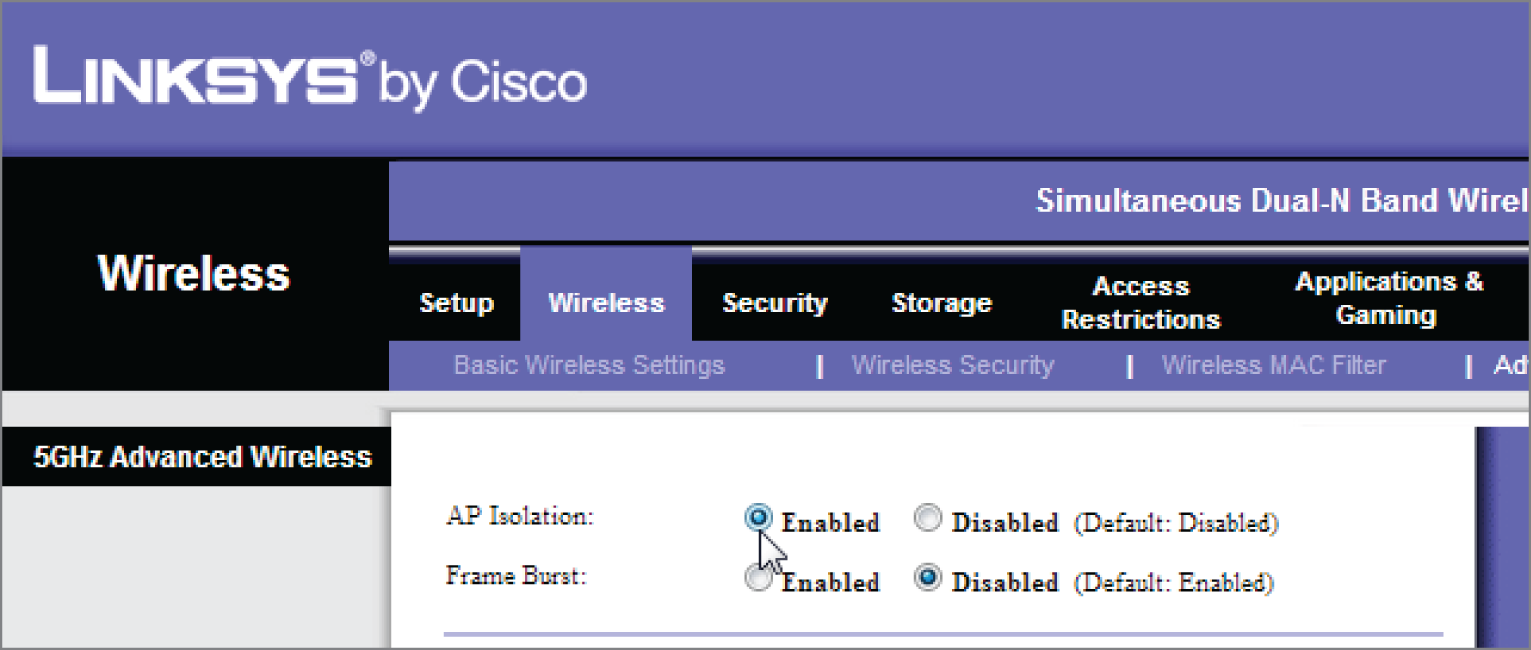
FIGURE 18.5 Isolation
Guest Network Isolation
A similar setting to client isolation is the guest network isolation feature. When enabled it creates two networks in one. One, the guest network, has client isolation in effect and has access only to the Internet. The second serves as the regular WLAN. Guests who join the guest Wi-Fi network are confined to an entirely separate network and given Internet access, but they can't communicate with the main wired network or the primary wireless network.
The setting is shown in Figure 18.6.
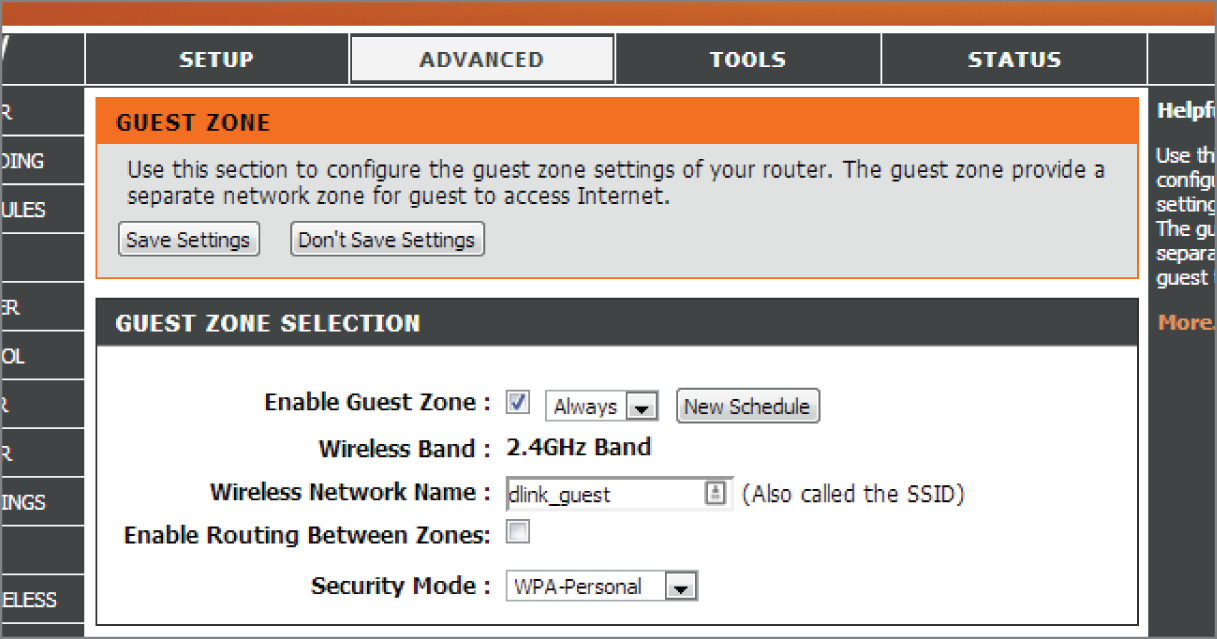
FIGURE 18.6 Guest network
Preshared Keys (PSKs)
In Chapter 12 you learned about preshared keys (PSK) used in some authentication and encryption systems. Please review that chapter.
EAP
In Chapter 16, “Common Security Concepts,” you learned about the Extensible Authentication Protocol (EAP), which is widely used in WLAN security. Please review that chapter.
Geofencing
Geofencing is the process of defining the area in which an operation can be performed by using global positioning system (GPS) or radio frequency identification (RFID) to define a geographic boundary. An example of usage involves a location-aware device of a location-based service (LBS) user entering or exiting a geofence. This activity could trigger an alert to the device's user as well as messaging the geofence operator.
Captive Portal
When a wireless network is in use, one method of securing access to a WLAN is using a captive portal. This is a web page to which users are directed when they attempt to connect to a WLAN. This web page may ask for network credentials, or in the case of a guest network such as at a coffee shop, hotel, or airport, it may only ask for agreement to the usage policy of the guest network.
IoT Access Considerations
In Chapter 5 you learned about the Internet of Things (IoT) devices. Many of these devices use a wireless connection to communicate with the systems gathering data from the sensors. These systems were not designed with security in mind.
IoT devices are easy recruits to a botnet, which is a group of systems that an attacker controls and directs to foist a DoS attack. Consider using VLANs and other forms of segmentation to prevent this. The role an IoT device will play is that of a zombie.
Summary
In this chapter you learned network hardening techniques, including securing SNMP, using Router Advertisement (RA) Guard, implementing port security and utilizing Dynamic ARP inspection. We also talked about wireless security hardening methods, including MAC filtering, proper antenna placement and proper power levels. Finally, we identified IoT access considerations.
Exam Essentials
- Explain network hardening techniques. These include securing SNMP, Router Advertisement (RA) Guard, port security, Dynamic ARP inspection, control plane policing, private VLANs, disabling unneeded switchports, disabling unneeded network services, changing default passwords, and enabling DHCP snooping.
- Describe wireless security hardening. The techniques used for wireless security hardening include MAC filtering, proper antenna placement, proper power levels, wireless client isolation, guest network isolation, preshared keys (PSKs), EAP, geofencing, and captive portal.
- Mitigate IoT threats. These include segmenting the IoT devices to help prevent their recruitment to a botnet.
Written Lab
Complete the table by filling in the appropriate term for each authentication method.
You can find the answers in Appendix A.
| Authentication Method | Term |
|---|---|
| Method of blocking rogue router advertisements | |
| Can prevent many on-path/man-in-the-middle attacks | |
| Can limit network access on a port to a single (or in the case of an IP phone, two) MAC address | |
| Carries signaling traffic originating from or destined for a router | |
| Carries user traffic |
Review Questions
You can find the answers to the review questions in Appendix B.
- Which of the following is a web page to which users are directed when they attempt to connect to the WLAN?
- Captive portal
- Evil twin
- PSK
- LBS
- Which of the following defines the area in which an operation can be performed?
- Captive portal
- Geofencing
- VLAN
- API
- Which of the following is a role that an IoT device can play in a botnet?
- Command and control
- Handler
- Zombie
- Broker
- Which of the following creates two WLANs in one?
- VLAN
- Client isolation
- Evil twin
- Guest network isolation
- Which of the following provides the best way to shape a broadcast cell?
- Antennas
- Power setting
- Repeaters
- Multiple APs
- Which of the following can be defeated with a wireless sniffer?
- VLAN hopping
- MAC address filters
- ARP poisoning
- RBAC
- Which of the following is also called whitelisting?
- Implicit allow
- Least privilege
- Implicit deny
- Need to know
- In which of the following systems are users organized by job into security groups, which are then granted the rights and permissions required to perform that job?
- RBAC
- MAC
- DAC
- BBAC
- When configuring ACLs between the Internet and your private network to mitigate security problems, it's a good idea to include all but which of the following?
- Deny any public addresses.
- Deny any addresses from your internal networks.
- Deny any local host addresses (127.0.0.0/8).
- Deny any reserved private addresses.
- Where should you always start your search for driver updates?
Drivers.com- Website of the manufacturer
- Windows Update
- Doesn't matter
