CHAPTER 12
USE CASES IN SECURITY
For the purposes of this chapter, we will look at use cases, opportunities, and challenges in the general security industry, making no distinction between the cyber-security and physical/facility security subsectors. This is because the subsectors are less distinct with each passing day. Indeed, for all practical purposes, the entire security industry has blended into one already, given the digitalization of devices and sensors and the advent of the Internet of Things.
EVERYTHING IS ON THE INTERNET
The term “Internet of Things” refers to all things being connected to the Internet. That’s not an exaggeration. Literally everything—from smart refrigerators and digitalized toilets inside the home and smart utility meters outside; to lighting fixtures in public spaces and sensors of all kinds; mobile, wearable computing, and implanted medical devices; vehicles from planes, trains, cars, and trucks to golf carts and farm tractors; TVs, set-top boxes, gaming consoles and even baby monitors; manufacturing, home health and hospital equipment—everything is being connected to the Internet.
Every single one of those things is producing digitalized information at a phenomenal rate. In other words, they are making big data non-stop. This form of data is called machine data, that is, data created by machines rather than by humans. It is arguably the easiest of all data forms to parse and analyze because of its tendency toward standardized output. For the most part, it is structured data. It’s not messy like social media data is, wherein human expression is unstructured. Humans can say or mean the same thing using a variety of words, sentiments, and emoticons. Something as simple as a pun or sarcasm can warp the final interpretation in analysis. Wherever conformity exists in data, analysis is far more accurate and faster.
Not only are all of those devices producing data that is easy for analysts—in security or otherwise—to use, they are potentially recording every detail of our individual and collective lives. Nothing, no matter how mundane or esoteric, escapes the machine collective’s notice. Databases everywhere are brimming with the stories of our lives.
It is in this context that security experts must now work, whether they are charged with cyber-security (protecting data) or with physical security (protecting facilities, events, and persons). Very little in security work relies on direct human observation anymore.
“It’s not in the hands of the security pro on the ground anymore,” a security professional, who asked to remain anonymous, lamented at a professional conference. “Everything is being pushed to the network guys.”
But that is not to say that security work has gotten any easier. Despite all this data, all these additional mechanical eyes, and all the other extensions of the security expert’s manifested presence, the exponential growth of threats and the steady rise in the sophistication of the attacks are still outpacing security efforts.
Compounding the problem is the need to preserve individual privacy. Whenever privacy is given priority, risk increases. Wherever security is given priority, individual privacy is breached and rarely can it return to its previous setup. This privacy conundrum remains the biggest challenge of our day. See Chapter 9, “The Privacy Conundrum,” for more details on that dilemma.
Indeed, recognizing the effects on privacy and security, the Federal Trade Commission, in an effort to get ahead of the Internet of Things curve, held a workshop in November 2013. Called “Internet of Things—Privacy and Security in a Connected World,” the idea was to begin to explore the issues and “focus on privacy and security issues related to increased connectivity for consumers, both in the home (including home automation, smart home appliances, and connected devices), and when consumers are on the move (including health and fitness devices, personal devices, and cars).” See http://www.ftc.gov/news-events/events-calendar/2013/11/internet-things-privacy-security-connected-world for more information on that event.
With that backdrop in mind, this chapter focuses on big data’s role and discusses use cases in the security industry.
DATA AS FRIEND AND FOE
People tend to think of big data in black or white terms, as good or evil, with nary a shred of gray in between. But data is only information; the good, bad, and the ugly parts grow out of how it is used.
Privacy issues often arise when data is collected for one purpose but then stored where it can be used for entirely different purposes later. In other words, the data is gathered and stored, but it becomes impossible for that information to be retrieved, deleted, or otherwise guarded by the person that information is about. This leaves the door wide open for future abuse, even when the original purpose was benign.
On the other hand, security professionals can only do so much in identifying immediate threats in real time. It is often the case that they need to backtrack through data to find the trail of evildoers and predict what they are likely to do next. In other words, once security professionals are aware of suspicious or malevolent activity or intent, they often need to examine more data than just the data presented in the moment. That means looking at past data, including data collected and stored earlier before anything or anyone was suspected. Hence, there is value in collecting and storing massive amounts of data over time.
And therein lies the rub. Policies that are good for privacy are bad for security and vice versa. Yet those who seek privacy also want to be safe and those who seek to provide security also want privacy for themselves. Data, then, is both friend and foe in both causes.
The challenge is in finding the right balance between privacy and security, but that is easier said than done.
Take antivirus software for example. In order for the software to identify and eliminate computer viruses in your email, downloads, files, and apps on your computer, the software must be able to “see” what is there. That means your email, downloads, and files on your computer are not technically private. But neither would your email and computer files be private if there were no antivirus programs as many cyber-criminals would then be watching and stealing your information.
Unfortunately, antivirus software and cyber-security efforts in the past were limited to detecting computer threats after they occurred. There really wasn’t a way to predict or detect cyber-threats any earlier. That means no matter how diligent a user was in using the protective software, viruses, Trojans, worms, and other cyber-threats still got through the defenses.
Further complicating this problem is the fact that no two antivirus/malware software products work the same way or catch the same threats. This means that a cyber-threat can slide past some protective software and not others. But even if a user were to use two or more anti-malware programs, it is unlikely that all threats would be caught or blocked. Indeed, there are plenty of cyber-threats that are not detected by any security software.
This is largely due to the fact that threats are caught after attacks happen. Until that point, security software and security pros do not know they exist and therefore can’t block or otherwise thwart them. Further, some cyber-attacks are so sophisticated that they can disable or “blind” antivirus/malware software to their presence. Other malware can instantly replicate itself the moment after being eradicated by antivirus software. The level of sophistication being displayed by some cyber-attacks and cyber-spying cannot be overstated. Further, the level of sophistication in cyber-crimes radically increases with the passing of every day. Indeed, big data is itself a target, as cyber-criminals find it relatively easy to hide their tools within the massive amounts of data now encumbering companies everywhere.
However, there is real hope that this paradigm can be upended through the use of big data. Massive amounts of data enable information security (InfoSec) professionals to see emerging threats and patterns earlier and even to predict impending attacks. Big data also aids in identifying the source of the attack, which can lead to attackers ending up behind bars instead of hovering over keyboards. Obviously, this is a huge win for the good guys.
USE CASES IN ANTIVIRUS/MALWARE EFFORTS
One antivirus-related example is how Kaspersky Lab uses big data in the development and ongoing refinement of its Internet security and InfoSec products. Kaspersky Lab is headquartered in Moscow, Russia but its holding company is registered in the UK. It is an international group operating in nearly 200 countries and territories around the world. It produces products for individuals, small and mid-sized businesses, and huge corporations and governments.
The company uses its cloud-assisted Kaspersky Security Network (KSN) to collect data on new threats and vulnerabilities, such as viruses, malware, and phishing websites, from millions of voluntary participants.
“It’s important to have a global view of new threats that may appear in one region and quickly spread to other regions,” said Vladimir Zapolyansky, director of Global Product & Technology Intelligence at Kaspersky Lab.
This information is sent quickly to its security experts and then warnings are sent to its global customer base in response. Much of this process is automated to further speed communications. The company claims that when a new threat is detected, the new threat intelligence spreads to its customer base in as little as 60 seconds.
Big data-fueled antivirus/malware efforts, particularly when coupled with crowd-sourcing, produce faster detections and responses than were previously possible. In general, big data driven security programs take minutes rather than hours to detect the problem and send a warning to vulnerable clients.
Returning to the example, KSN is a complex distributed infrastructure. It is a hybrid model using both traditional protection tools and new tools such as big data and cloud technologies. This enables Kaspersky to quickly identify previously unknown threats and move rapidly to block or eliminate them. It also helps them blacklist online attack sources and provide reputational data for applications and websites.
Even so, this is no easy task. According to Kaspersky Lab’s internal data, “about 315,000 new samples of malware appear ‘in the wild’ every day.”
Privacy issues get even trickier when a security company relies essentially on crowdsourcing to help catch the bad guys. Eliciting the help of millions of voluntary participants means respecting their privacy in the process or else volunteers will fall from the program in quick succession. In other words, trust is everything.
According to “Kaspersky Security Network,” a Kaspersky whitepaper, “KSN’s working mechanism includes several key processes such as the continuous, geographically-distributed monitoring of real-life threats to users’ computers, analysis of that data, and the delivery of relevant intelligence and countermeasures to protected endpoints.”
In other words, Kaspersky is collecting data from each volunteer’s computer on an entirely automated basis. So how does it do that and still protect each volunteer’s privacy? The company explains in its KSN whitepaper:
All the information obtained is depersonalized. Kaspersky Lab organizes the information it receives in large chunks according to data type, and nobody can trace which data was received from any one individual. Kaspersky Lab protects all the information collected by KSN in accordance with current legal and security statutory requirements.
While it is true that anonymized data can be reidentified by experts, the data KSN collects appears to be contained within Kaspersky’s databases rather than shared or sold in the raw, which greatly reduces the risk that such would occur. Of course Kaspersky could do so internally, but that is unlikely as well since frankly there’s little to no benefit in the company doing so.
In essence, any program launched by a user is evaluated by several factors, including the vendor’s digital signature and control hash, source verification, and program integrity. If the computer program is found to be legitimate, it’s added to a whitelist. If not, it’s added to a blacklist. KSN ensures a constant update of both lists. According to Kaspersky, here’s the internal process on the handling of newfound malware:
As soon as a program is defined as malware, it is reported to Kaspersky Lab’s Urgent Detection System and the information becomes available through Kaspersky Security Network. Therefore, even before the signature for that piece of malware is created and downloaded to secured endpoints, they receive a corresponding measure of protection. In that way Kaspersky Lab’s clients receive prompt information about new threats—including a basis to stop unknown ones—minutes after the launch of a cyber-attack. A traditional signature database update takes hours to do the same thing.
The company uses other technologies such as a reputational technology they call “Wisdom of the Crowd,” which notes popularity and reputation of a program based on KSN user input, and cloud-assisted anti-spam technology. The cloud portion detects and blocks spam without the need for an anti-spam filter to be placed on the computer.
Figure 12.1 shows the basic principles used in Kaspersky Lab’s products’ interaction with KSN.
Figure 12.1 The basic principles used in Kaspersky Lab’s products’ interaction with KSN.
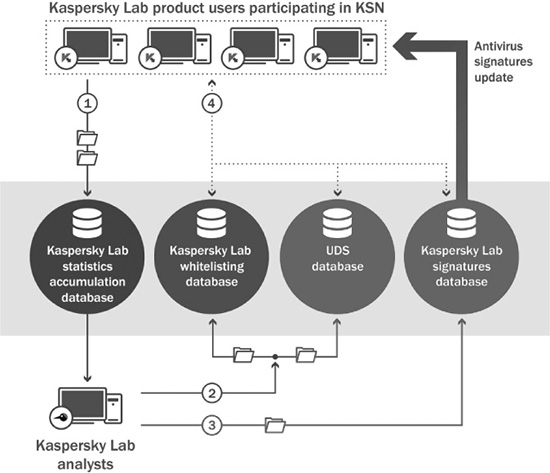
Source: Reprinted with permission. Copyright Kaspersky Lab.
While each provider’s processes are different in building and maintaining their antivirus/malware programs, most readily see the advantages of using big data in their mix. Some providers excel at wielding big data and others not so much, just as is the case in other industries.
In general, use cases for this sector are in detecting emerging threats, predicting upcoming threats, speeding the response to same, blocking and eliminating threats, arresting and prosecuting criminals by both identifying the source and providing a data trail of their activities as evidence, and in general, improving the mix and strength of defenses.
HOW TARGET GOT HIT IN THE BULL’S EYE
It’s important to note that many companies that provide antivirus/malware programs for individuals also provide enterprise-grade, that is, corporate-level, data protection. In this section, the focus is on the obstacles and opportunities encountered in a standard enterprise where IT labors specifically to protect the company’s proprietary and sensitive data, including but not limited to payment processing and personal data. It’s an ongoing and exceedingly difficult challenge fraught with many liabilities.
One example of how failure to protect data can lead to chaos and huge losses, both in immediate and future monies, is the infamous Target breach of 2013. For a snapshot of what happened, consider this excerpt from a January 10, 2014 report in The Washington Post by Jia Lynn Yang and Amrita Jayakumar:
The Target breach already ranks as one of the worst ever. During the peak of holiday shopping last month, Target said that up to 40 million customers’ credit and debit card information had been stolen from people who shopped in stores from Nov. 27 to Dec. 15. On Friday, the company said a new group of 70 million customers—some of whom might also have had their card data stolen—have had their personal information compromised, as well.
The growing scandal has triggered at least two class-action lawsuits, drawn state and federal investigations, and damaged Target’s bottom line. The company on Friday cut its fourth-quarter earnings forecast and said it expects sales to decline by 2.5%.
“All the costs are going to eat up their profits,” said John Kindervag, an analyst with Forrester. “There’s going to be shareholder revolts. There’s going to be prosecutions. They’ve stepped in quicksand. It’s not going to be fun.”
Protecting data is essential for as you can see from this report, the implications of not doing so effectively can be devastating.
So how did the Target breach happen? Brian Krebs, former investigative reporter for The Washington Post and now a noted and highly respected, independent cyber-security blogger, was the person who first broke the Target breach story. He continued to investigate the situation and periodically post his findings on his blog called KrebsOnSecurity. On February 14, 2014, he posted details on the cause of the breach:
The breach at Target Corp. that exposed credit card and personal data on more than 110 million consumers appears to have begun with a malware-laced email phishing attack sent to employees at an HVAC firm that did business with the nationwide retailer, according to sources close to the investigation.
Last week, KrebsOnSecurity reported that investigators believe the source of the Target intrusion traces back to network credentials that Target had issued to Fazio Mechanical, a heating, air conditioning and refrigeration firm in Sharpsburg, Pa. Multiple sources close to the investigation now tell this reporter that those credentials were stolen in an email malware attack at Fazio that began at least two months before thieves started stealing card data from thousands of Target cash registers.
Two of those sources said the malware in question was Citadel—a password-stealing bot program that is a derivative of the ZeuS banking Trojan—but that information could not be confirmed. Through a PR firm, Fazio declined to answer direct questions for this story, and Target has declined to comment, citing an active investigation.
There is no question that, like Target, Fazio Mechanical was the victim of cyber-crime. But investigators close to the case took issue with Fazio’s claim that it was in full compliance with industry practices, and offered another explanation of why it took the Fazio so long to detect the email malware infection: The company’s primary method of detecting malicious software on its internal systems was the free version of Malwarebytes Anti-Malware.
To be clear, Malwarebytes Anti-Malware (MBAM) free is quite good at what it’s designed to do – scan for and eliminate threats from host machines. However, there are two problems with an organization relying solely on the free version of MBAM for anti-malware protection: Firstly, the free version is an on-demand scanner that does not offer real-time protection against threats (the Pro version of MBAM does include a real-time protection component). Secondly, the free version is made explicitly for individual users and its license prohibits corporate use.
The giant retailer had security practices in place but it failed to find and protect against vulnerabilities and poor practices presented by its vendor/contractor base. Krebs explained how that group was plugged into Target’s systems:
Fazio’s statement also clarified that its data connection to Target was exclusively for electronic billing, contract submission and project management. The company did not specify which component(s) of Target’s online operations that Fazio accessed externally, but a former employee at Target said nearly all Target contractors access an external billing system called Ariba, as well as a Target project management and contract submissions portal called Partners Online. The source said Fazio also would have had access to Target’s Property Development Zone portal.
The malware connected and spread from there.
A Senate staff report titled “A ‘Kill Chain’ Analysis of the 2013 Target Data Breach” produced on March 26, 2014 for Chairman Rockefeller, Committee on Commerce, Science and Transportation, notes numerous failures that perhaps a big data approach might have thwarted.
Among the failures the Senate report notes is this: “Target appears to have failed to respond to multiple automated warnings from the company’s anti-intrusion software that the attackers were installing malware on Target’s system.” Further the report says that Target “appears to have failed to respond to multiple warnings from the company’s anti-intrusion software regarding the escape routes the attackers planned to use to exfiltrate data from Target’s network.”
We’ll get to the common problems in security alerts and how big data can help with that later in this chapter. For now, consider Figure 12.2 from the Senate report for a quick view of events in the Target breach displayed in a timeline.
Figure 12.2 Timeline chart of events in the 2013 Target breach.
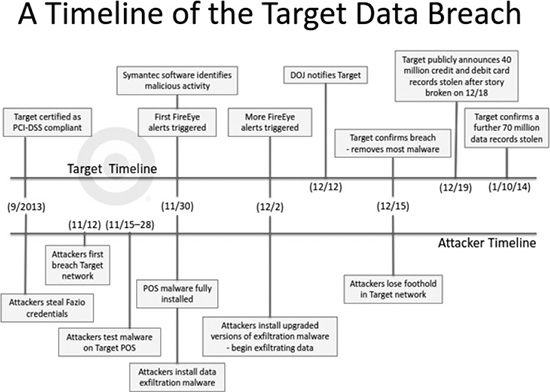
Source: Senate staff report titled “A ‘Kill Chain’ Analysis of the 2013 Target Data Breach” produced on March 26, 2014 for Chairman Rockefeller, Committee on Commerce, Science and Transportation.
Big Data as Both Challenge and Benefit to Businesses
Companies, both big and small and in every industry, face similar difficulties and unexpected vulnerabilities. Both are growing exponentially.
“We have seen complex enterprises struggle with both the benefits and challenges of big data,” said Kristine Briggs, vice president of Operations at Neohapsis, a security, compliance, and risk management consulting company based in Chicago. “From data classification, to identity and access management, IP protection, storage, and compliance, our clients have what seem to be ever-growing challenges in effectively securing, and most importantly, getting value out of, their data. Add the challenges and opportunities presented by cloud computing, and the situation becomes even more complicated.”
But most enterprises are not only interested in protecting data and reducing their risks, they also want to see return on investment (ROI) from the security data they glean in the process.
“In addition to the imperative of securing their most critical data, many enterprises want to get value out of their cyber-security data if possible; most global enterprises have implemented Security Information/Event Management systems (SIEMs) and Governance Risk and Compliance (GRC) systems to try to achieve this, very few with stellar results,” said Briggs. “SIEMs can help manage the volume of security and event data, but rarely provide the intelligence needed to react quickly, and more importantly they are rarely tuned to be able to correlate the data from different sources to come to intelligent, actionable conclusions.”
“Put more simply, you get lots of data, and can generate dashboards on things like unpatched systems and other tactical points, but they rarely provide what you need to actually improve your security posture on a strategic level. GRC systems, though conceptually attractive, are very complex to implement and customize, and generally take a team of people to get a commensurate amount of value to balance out the cost. Neither type of system effectively supports the constant organizational and technological change we see in global enterprises today.”
Figure 12.3 shows a Neohapsis NeoX user interface used to manage vulnerabilities across an entire company. The figure shows a highly filterable list page of vulnerabilities aggregated together from many different providers. Complex searches can be accomplished by drilling down through any of the facets. Reduced time managing vulnerabilities generally equates to more time available to prioritize, remediate, and retest.
Figure 12.3 This is a Neohapsis NeoX user interface used to manage vulnerabilities across an entire company. The figure shows a highly filterable list page of vulnerabilities aggregated together from many different providers.
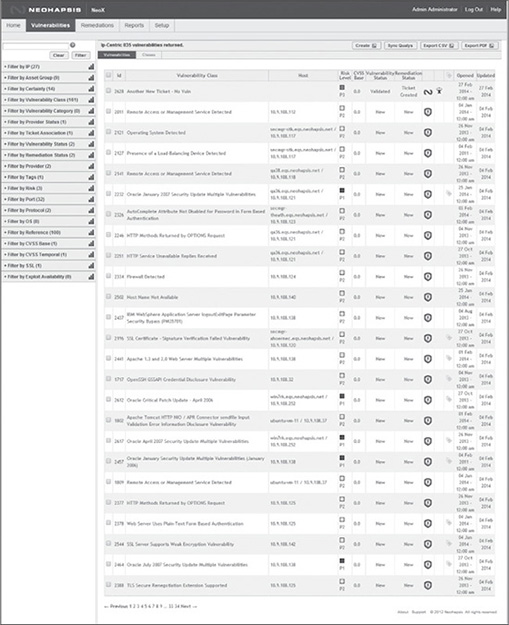
Source: Reprinted with permission. Copyright © Neohapsis.
It should also be noted that the security community faces potential liabilities. For example, security firm Trustwave faced two lawsuits filed by Green Bank and Trustmark Bank claiming the firm was negligent, along with Target, for the Target breach. These banks and others lost millions of dollars since by law they, rather than their customers, must absorb the costs of fraudulent credit and debit card charges as well as the costs of reissuing new cards to customers.
Those lawsuits have since been dropped, but without prejudice, meaning they can be filed again at some later date before the applicable statutes of limitation run out. The security industry is completely unnerved by the lawsuits, and the potential for future such suits, that could cost them everything. They are flocking in droves to big data tools to help protect them against such liabilities.
Big data analytics, when used effectively, provide the means to use data from a variety of sources, add inputs in the algorithm to include new and/or more factors for evaluation, and analyze massive amounts of information in real or near real time.
There are many use cases for big data in cyber-security. As noted in the earlier section, namely they are in detecting emerging threats, predicting upcoming threats, speeding the response to threats, blocking and eliminating threats, arresting and prosecuting criminals by both identifying the source and providing a data trail of their activities as evidence, and generally improving the mix and strength of defenses.
But that is only part of the story in using big data in security.
WHERE VIRTUAL AND REAL WORLDS COLLIDE
Up to this point, this discussion has been focused on pure cyber-attacks. But given the ongoing convergence between the real and virtual worlds, security personnel have to broaden their scope to include threats that cross that rather tenuous line. For example, cyber-criminals, activists, and cyber-terrorists are not limited to stealing, blocking, or manipulating digitalized data. They can cause havoc, damage, and even human casualties in the real world too.
Given the Internet of Things and the fact that almost all critical infrastructure in any developed country is now dependent on digital operations, the potential for highly damaging cyber-attacks in the real world cannot be overstated. Power grids, water systems, and entire economies are just a few of the things that can be crashed by sophisticated cyber-attacks. People can also be attacked and even assassinated by cyber-attacks on medicine delivery systems and implanted medical devices such as pacemakers, as well as through other devices.
In response, the Whitehouse issued an Executive Order (13636) in February of 2013 calling for a “cyber-security framework” to protect critical infrastructure. The Executive Order tasked various governmental agencies with developing a cyber-security framework and identifying critical infrastructure in need of security. Subsequently, on February 12, 2014, the Commerce Department’s National Institute of Standards and Technology (NIST) released a framework for improving critical infrastructure cybersecurity.
“The framework provides a consensus description of what’s needed for a comprehensive cybersecurity program,” said Under Secretary of Commerce for Standards and Technology and NIST Director Patrick D. Gallagher. “It reflects the efforts of a broad range of industries that see the value of and need for improving cybersecurity and lowering risk. It will help companies prove to themselves and their stakeholders that good cybersecurity is good business.”
NIST also released an accompanying roadmap document and stressed that the framework “is expected to be a first step in a continuous process to improve the nation’s cybersecurity.” In others words, this effort will never end.
Life in the modern world is fragile. A country’s entire banking and financial system can be completely wiped out without a single bank vault being cracked. Security is no longer limited to vaults, locks, and body guards or border guards. Attacks can come from far away, absent the physical presence of the perpetrators and without sound or any other warning.
While most citizens of every country are completely unaware of the fragility of their reality, security professionals suffer no such illusion. Despite their instincts, experience, and diligence, security pros cannot be everywhere at once nor can they personally observe everything that may indicate a looming threat. Big data tools are quite frankly their only hope in evening the odds. Even so, as it has been said before, an attacker needs only to succeed once whereas a protector must succeed in every case and on every front.
Use cases for big data in this category include those in any other cyber-security effort as well as in the development of innovative protective measures. This includes but is not limited to offline overrides in medical equipment that react to unauthorized changes in commands or performance and offline secondary and compartmentalized or containerized emergency and backup systems such as for electric grids, water, and banking systems.
Indeed, one of the biggest benefits of big data in security is its ability to predict likely threats and afford the means to design both prevention and response.
MACHINE DATA MAYHEM
InfoSec used to focus on endpoints, such as computers and mobile devices. When that proved no longer effective, the industry shifted to focus on protecting the network. That was followed by an intense focus on protecting the data. Eventually keeping everything behind a firewall became impossible as more data flowed in and out, from and to various sources and devices. In other words, as more of everything became connected, from employees bringing their own malware laden devices to work, in what is now called Bring Your Own Device (BYOD) programs, and data moved to and from the cloud and between sources, the notion of a firewall and company security was forced to change too.
The Farmer’s Security Dilemma
Along comes the Internet of Things to infuse even more data from more sources into any given business and the general data pool. For example, a farmer might buy a tractor that can deliver more data to him on the condition of his farm. But that same tractor likely also reports data to the manufacturer about how the tractor is performing. It could also report to the dealer so the dealer can start marketing more parts, accessories, services, and new models to the farmer. The farmer may also elect to share his tractor’s data with a farming association or a mega-vendor, such as Monsanto. Or, the tractor manufacturer may share that farmer’s tractor data with a whole slew of other entities unbeknownst to the farmer.
All told, that one farm tractor is reporting an awful lot of data in various directions, and only some of it with the farmer’s expressed knowledge and consent. The rest is likely harvested and shared without his direct knowledge.
Some uses of that data are helpful to the farmer and to other farmers, but a good bit of it is really used to help the collaborators peddle their wares to farmers. It is not necessarily helpful to the farmer for a vendor to know so much about his business—particularly not if he also must rely on the vendor to sell him products on credit. The vendor could easily look at the farm data and withhold the sale considering the farm a bad credit risk before a single plant in the field broke ground.
There are other ways that data can be used against farmers too. Early in 2014 the American Farm Bureau Federation warned farmers that danger lurked in all that data sharing. In a January 22, 2014 report in NPR, Dan Charles summed up the Bureau’s concerns this way:
“Mary Kay Thatcher, the farm bureau’s senior director for congressional relations, says farmers should understand that when data move into the cloud, they can go anywhere.
For instance: Your local seed salesman might get the data, and he may also be a farmer—and thus your competitor, bidding against you for land that you both want to rent. ‘All of a sudden he’s got a whole lot of information about your capabilities,’ Thatcher says.
Or consider this: Companies that are collecting these data may be able to see how much grain is being harvested, minute by minute, from tens of thousands of fields. That’s valuable information, Thatcher says. “They could actually manipulate the market with it. They only have to know the information about what is actually happening with harvest minutes before somebody else knows it. I’m not saying they will,” says Thatcher. “Just a concern.”
Now imagine smack in the middle of all that, the growing complexities in securing that data. It’s moving in multiple directions and it is unclear whether anyone, least of all the farmer, knows where it all resides much less how well protected this data is. The data then becomes exponentially vulnerable, i.e. the risk expands with the number of locations in which this data resides and is subject to the security weaknesses in each company that is holding the data.
Further, because the farmer (the data source) has little to no idea on what information is being reported to whom, there is no real way for him to protect his data. Even if the farmer had exceptional computer and security skills, it is doubtful that he could sufficiently protect his data or detect intrusions because too much of the data gathering mechanisms are deliberately hidden from him on the equipment. With so little security protection at the source, the data harvesters are also at risk of a hacker entering the data stream and/or following it to the data gatherer’s repository and systems. A hacker could even mimic a machine and attack Dow, John Deere, Monsanto, or any other farm machine data harvester in a way very similar to the Target data breach. In several other ways too.
The Internet of Things Repeats the Farmer’s Security Dilemma Ad Infinitum
Similar concerns lurk in machine data sharing in every arena. A wearable fitness app tells the wearer important information about their own health. But it could also report that information to the manufacturer who could then sell or share it with an employer or a health insurance company to be used against the owner. A home smart refrigerator can do the same thing by reporting to others what you and your family are eating. Hackers can have a field day with all of it.
The same is true with personal car data, which follows almost exactly the tractor scenario, albeit with different players. And if you think the gadgets that car insurance companies are handing out are a great freebie designed to save you money, think again. The data from those things are marketed as a way for insurance companies to reward good drivers but in all likelihood it will be used to hike premiums on everyone one hair shy of being a driving saint. If you opt out of giving them your data, the insurance companies will probably hike your premiums as a result. Make no mistake, no company collects and analyzes big data with the intent of decreasing its revenues and profits.
And today’s tech-equipped cars are making selling a used car a security hazard too. Twenty years ago you merely signed over your title and handed the keys to the new buyer. But today you need to “wipe” your media center’s Bluetooth connection data and purge phone records or else face your personal contacts and phonebook winding up in the hands of the next driver. According to an April 16, 2014 report in Business Insider, Vice President Joe Biden was caught up in this when he returned his leased Cadillac without wiping his cell phone contacts. Many of his “important numbers,” including that of his wife Jill, remained in the car’s data stores.
In the case of enterprises, data flowing from consumer devices to field sensors, and every other type of machine, is adding tremendous amounts of data that now has to be stored, analyzed, and protected. Further, malware can be attached or fed through these machines to corrupt or breach the entire database. But this threat can also extend to damaging real company property and operations, rather than just stealing data.
Therefore, big data use cases are two-fold in this area: managing the data generated by the machines and protecting the enterprise and the machines from malicious attacks implemented through machine data.
CURRENT AND FUTURE USE OF ANALYTICS IN SECURITY
We’ve touched on some of the challenges in modern day security and how big data is used to offset or thwart them. Let’s now take a look at how security work itself is prone to problems and what can be done to address those issues.
At the moment, security tools, whether big data driven or not, are highly segmented. The result is a cacophony of noise. There are multiple alerts on these systems signifying a dizzying array of factors and most are plagued with false reads. Security professionals encounter extreme difficulty in making sense of it all, much less in prioritizing or effectively responding to any of it.
To remedy this, Avivah Litan, a respected analyst with Gartner Research, recommends the security industry move toward context-aware analytics. Specifically in her presentation, “Seven Dimensions of Context-Aware Security Analytics,” at the 2014 Gartner BI & Analytics Summit, she wrote that “context awareness refines the behavior of intelligent systems.”
And indeed it does. The reason there are too many alerts and far too many false reads is that most intelligent systems today are not as smart as they could be. Everything is being analyzed in a vacuum, that is, in a data silo. Context bursts that silo and gives meaning to the actions noted.
Figure 12.4 is a slide from Litan’s presentation showing the existing processes of intelligent systems in a typical ATM withdrawal.
Figure 12.4 The intelligent systems in a typical ATM withdrawal.
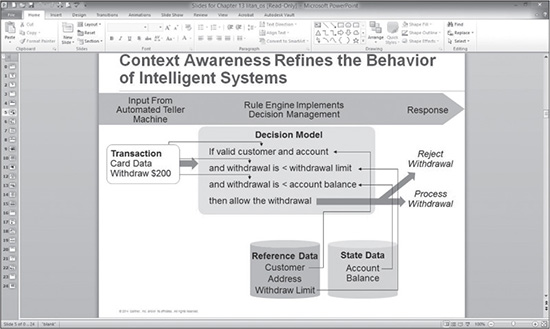
Source: Gartner 2014 Business Intelligence & Analytics Summit Presentation, “The Seven Dimensions of Context-Aware Security Analytics,” Avivah Litan, March 31–April 2, 2014.
Figure 12.5 is a slide from Litan’s presentation showing that same process using context-aware security analytics.
Figure 12.5 Using context-aware security analytics on the same process.
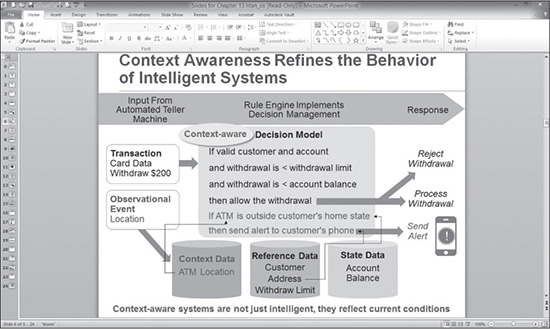
Source: Gartner 2014 Business Intelligence & Analytics Summit Presentation, “The Seven Dimensions of Context-Aware Security Analytics,” Avivah Litan, March 31–April 2, 2014.
As you can tell from these two comparative slides, context-aware analytics aid both the bank’s security efforts and its customer relationships. While all customers expect full security in their banking, they do not like their debit and credit cards unnecessarily blocked from use. And that happens quite regularly as bank security personnel struggle to identify legitimate purchases and withdrawals. By using context-aware analytics, as Litan suggests, customers are not unduly frustrated and bank security personnel can more efficiently direct their attention to blocking actual theft.
Litan further suggests that these context-aware analytics be applied in seven layers that collectively better inform security personnel and improve security protocols in a more comprehensive manner.
Figure 12.6 is a slide from Litan’s presentation showing all seven layers.
Figure 12.6 The seven layers of context-aware security systems.
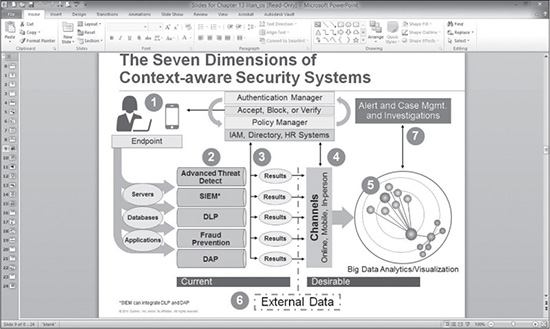
Source: Gartner 2014 Business Intelligence & Analytics Summit Presentation, “The Seven Dimensions of Context-Aware Security Analytics,” Avivah Litan, March 31–April 2, 2014.
Specific use cases include, but are not limited to, the following depicted in Figure 12.7, another slide from Litan’s presentation.
Figure 12.7 Layer 5: Big data analytics. Sample use cases by sector.

Source: Gartner 2014 Business Intelligence & Analytics Summit Presentation, “The Seven Dimensions of Context-Aware Security Analytics,” Avivah Litan, March 31–April 2, 2014.
As was pointed out previously in other chapters, ROI is very high when the use case is highly defined and the output is both actionable and measurable. Litan makes that point as well, specific to context-aware security analytics. Here in Figure 12.8, she cites specific use cases that tend to render high ROI in the use of this type of analytics.
Figure 12.8 Return on investment is high with well-defined use cases.
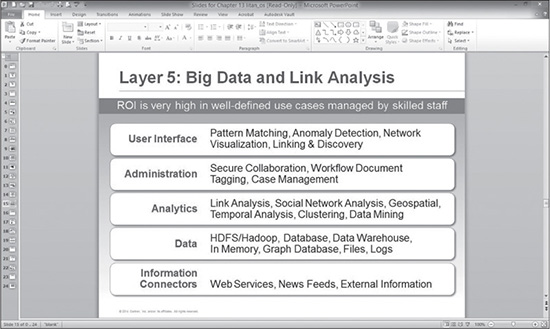
Source: Gartner 2014 Business Intelligence & Analytics Summit Presentation, “The Seven Dimensions of Context-Aware Security Analytics,” Avivah Litan, March 31–April 2, 2014.
All told, the security industry is arguably the most active in big data use and with good reason. It must protect itself as vigilantly as it protects customers and constituents. There is no margin for error in the face of increasing and more sophisticated threats and the ever-growing number of laws and regulations. Meanwhile, enterprises expect security efforts to be effective without impeding the flow of business or diminishing customer satisfaction. It’s a big order that can only be fulfilled with strategic data analysis.
SUMMARY
In this chapter you learned that for all practical purposes, both the physical and digital security sectors have blended into one, given the digitalization of devices and sensors and the advent of the Internet of Things. You discovered that as many if not more security risks reside in purposeful sharing and surreptitious data gathering by previously trusted sources, such as manufacturers and vendors, than as exist in the criminal world. Opportunities for hackers are growing and data breaches will increase. You also learned that many new security risks are popping up in unexpected places such as in the sale of a used car, the operation of a farm tractor and the use of smart home appliances. Ultimately you learned the many ways big data is both friend and foe in security efforts and a few ways to make it friendlier.
