Chapter 3
Cybersecurity Framework
Chapter Objectives
After reading this chapter and completing the exercises, you will be able to do the following:
Understand confidentiality, integrity, and availability (the CIA security model).
Describe the security objectives of confidentiality, integrity, and availability.
Discuss why organizations choose to adopt a security framework.
Understand the intent of the National Institute of Standards and Technology (NIST) Cybersecurity Framework.
Understand the intent of the ISO/IEC 27000-series of information security standards.
Outline the domains of an information security program.
Our focus in this chapter on information security objectives and framework will answer the following (and many other) questions associated with the need to maintain secure data storage and communications among and between government, public, and private sectors. In context, our efforts to sustain reliable and secure communications has become a worldwide global effort with cybersecurity.
What are we trying to achieve in pursuit of cybersecurity?
What is the ultimate goal of writing cybersecurity policies?
What tangible benefit will come to our customers, our employees, our partners, and our organizations from our Herculean effort?
To organize the effort, a framework is required. A framework lends itself to many easily related metaphors. The most obvious is that of any building: no foundation, no building. More specifically, the better the framing of any building, the longer it will last, the more it can hold, and the more functional it becomes. Of course, with any building there must first be a plan. We hire architects and engineers to design our buildings, to think about what is possible, and relay the best way to achieve those possibilities.
In the same way, we need a framework for our information security program. Much like the many rooms in a building, each with its own functions, we segment our information security program into logical and tangible units called domains. Security domains are associated with designated groupings of related activities, systems, or resources. For example, the Human Resources Security Management domain includes topics related to personnel, such as background checks, confidentiality agreements, and employee training. Without the framework, every new situation will see us repeating, redesigning, and reacting, which all together can be referred to as “unplanned,” or spending time in crisis. Fortunately, in the information security arena there is absolutely no reason to choose crisis over preparedness. Strategies involving proactive, rather than reactive, procedures have become the ad hoc standard for systems of cybersecurity governance. A number of public and private organizations, including the International Organization for Standardization (ISO) and the National Institute of Standards and Technology (NIST), have all invested considerable time and energy to develop standards that enable proactive cybersecurity frameworks.
In this chapter, you are introduced to the standards developed by both organizations. Before we begin building our information security program and policies, we need to first identify what we are trying to achieve and why. We begin this chapter by discussing the three basic tenets of information security. We then look at the escalating global threat, including who is behind the attacks, their motivation, and how they attack. We apply this knowledge to building the framework of our information security program and how we write our policies.
Confidentiality, Integrity, and Availability
The elements of confidentiality, integrity, and availability are often described as the CIA model. It is easy to guess that the first thing that popped into your mind when you read those three letters was the United States Central Intelligence Agency. In the world of cybersecurity, these three letters represent something we strive to attain and protect. Confidentiality, integrity, and availability (CIA) are the unifying attributes of an information security program. Collectively referred to as the CIA triad or CIA security model, each attribute represents a fundamental objective of information security.
You may be wondering which is most important: confidentiality, integrity, or availability? The answer requires an organization to assess its mission, evaluate its services, and consider regulations and contractual agreements. As Figure 3-1 illustrates, organizations may consider all three components of the CIA triad equally important, in which case resources must be allocated proportionately.
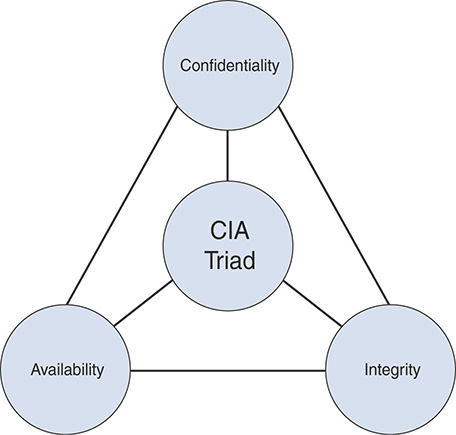
FIGURE 3-1 CIA Triad
What Is Confidentiality?
When you tell a friend something in confidence, you expect them to keep the information private and not share what you told them with anyone else without your permission. You also hope that they will never use this against you. Likewise, confidentiality is the requirement that private or confidential information not be disclosed to unauthorized individuals.
There are many attempts to define what confidentiality is. As an example, the ISO 2700 standard provides a good definition of confidentiality as “the property that information is not made available or disclosed to unauthorized individuals, entities, or processes.”
Confidentiality relies on three general concepts, as illustrated in Figure 3-2.

FIGURE 3-2 Confidentiality General Concepts
There are several ways to protect the confidentiality of a system or its data; one of the most common is to use encryption. This includes encryption of data in transit with the use of site-to-site and remote access virtual private networks (VPNs), or by deploying server and client-side encryption using Transport Layer Security (TLS).
Another important element of confidentiality is that all sensitive data needs to be controlled, audited, and monitored at all times. This is often done by encrypting data at rest. Here are some examples of sensitive data:
Social security numbers
Bank and credit card account information
Criminal records
Patient and health records
Trade secrets
Source code
Military secrets
The following are examples of security mechanisms designed to preserve confidentiality:
Logical and physical access controls
Encryption (in motion and at rest)
Database views
Controlled traffic routing
Data classification is important when you’re deciding how to protect data. By having a good data classification methodology, you can enhance the way you secure your data across your network and systems.
Not only has the amount of information stored, processed, and transmitted on privately owned networks and the public Internet increased dramatically, so has the number of ways to potentially access the data. The Internet, its inherent weaknesses, and those willing (and able) to exploit vulnerabilities are the main reasons why protecting confidentiality has taken on a new urgency. The technology and accessibility we take for granted would have been considered magic just 10 years ago. The amazing speed at which we arrived here is also the reason we have such a gap in security. The race to market often means that security is sacrificed. So although it may seem that information security requirements are a bit extreme at times, it is really a reaction to the threat environment.
You also have to pay attention to confidentiality laws. For example, information exchanged between doctors and patients or lawyers and clients is protected by confidentiality laws called the “doctor-patient privilege” and the “attorney-client privilege,” respectively.
As it pertains to information security, confidentiality is the protection of information from unauthorized people and processes. Federal Code 44 U.S.C., Sec. 3542 defines confidentiality as “preserving authorized restrictions on access and disclosure, including means for protecting personal privacy and proprietary information.”
None of us likes the thought of our private health information or financial information falling into some stranger’s hands. No business owner likes the thought of her proprietary business information being disclosed to competitors. Information is valuable. Social security numbers are used for identity theft. Bank account credentials are used to steal money. Medical insurance information can be used to fraudulently obtain services or to make counterfeit claims. Military secrets can be used to build weaponry, track troop movements, or expose counterintelligence agents. The list goes on and on.
Because there is value in confidential information, it is often a target of cybercriminals. For instance, many breaches involve the theft of credit card information or other personal information useful for identity theft. Criminals look for and are prepared to exploit weaknesses in network designs, software, communication channels, and people to access confidential information. The opportunities are plentiful.
Criminals are not always outsiders. Insiders can be tempted to “make copies” of information they have access to for financial gain, notoriety, or to “make a statement.” The most recent threat to confidentiality is hacktivism, which is a combination of the terms “hack” and “activism.” Hacktivism has been described as the fusion of hacking and activism, politics, and technology. Hacktivist groups or collectives expose or hold hostage illegally obtained information to make a political statement or for revenge.
FYI: Examples of Cybersecurity Vulnerabilities Impacting Confidentiality and How to Assess Their Associated Risk
The Common Vulnerability Scoring System (CVSS) uses the CIA triad principles within the metrics used to calculate the CVSS base score. Let’s take a look at two examples of security vulnerabilities that have an effect on confidentiality:
Cisco WebEx Meetings Server Information Disclosure Vulnerability: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180117-wms3
Cisco Adaptive Security Appliance Remote Code Execution and Denial of Service Vulnerability: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180129-asa1
The first vulnerability (Cisco WebEx Meetings Server Information Disclosure Vulnerability) is a medium-severity vulnerability that has a CVSS base score of 5.3. The CVSSv3 base score vector and parameters can be seen at the CVSS calculator at the following link:
The vulnerability affects confidentiality, but it does not affect integrity or availability.
The second vulnerability (Cisco Adaptive Security Appliance Remote Code Execution and Denial of Service Vulnerability) is a critical vulnerability that has a CVSS base score of 10. The CVSSv3 base score vector and parameters can be seen at the CVSS calculator at the following link:
This vulnerability has a direct impact on confidentiality, integrity, and availability.
FYI: Hacktivism
Throughout the years, hacktivists have used tools to perform website defacements, redirects, denial of service (DoS) attacks, information theft, website parodies, virtual sit-ins, typosquatting, and virtual sabotage. Examples include the “hacker group” that goes by the name Anonymous and their infamous hacks, and Lulzec attacks, which had a direct impact on organizations like Fox.com, the Sony PlayStation Network, and the CIA. The Lulzec hacker group leaked several passwords, stole private user data, and took networks offline. Another example is the attacks against numerous network infrastructure devices around the globe, where attackers left United States flags on the screens and configurations of those devices after abusing the Smart Install protocol.
The ability to obtain unauthorized access is often opportunistic. In this context, opportunistic means taking advantage of identified weaknesses or poorly protected information. Criminals (and nosy employees) care about the work factor, which is defined as how much effort is needed to complete a task. The longer it takes to obtain unauthorized access, the greater the chance of being caught. Complexity also plays a part—the more complex, the more opportunity to screw up, the more difficulty to cover tracks. The more a “job” costs to successfully complete, the less profit earned. The information security goal of confidentiality is to protect information from unauthorized access and misuse. The best way to do this is to implement safeguards and processes that increase the work factor and the chance of being caught. This calls for a spectrum of access controls and protections as well as ongoing monitoring, testing, and training.
What Is Integrity?
Whenever the word integrity comes to mind, so does Brian De Palma’s classic 1987 film The Untouchables, starring Kevin Costner and Sean Connery. The film is about a group of police officers who could not be “bought off” by organized crime. They were incorruptible. Integrity is certainly one of the highest ideals of personal character. When we say someone has integrity, we mean she lives her life according to a code of ethics; she can be trusted to behave in certain ways in certain situations. It is interesting to note that those to whom we ascribe the quality of integrity can be trusted with our confidential information. As for information security, integrity has a very similar meaning. Integrity is basically the ability to make sure that a system and its data has not been altered or compromised. It ensures that the data is an accurate and unchanged representation of the original secure data. Integrity applies not only to data, but also to systems. For instance, if a threat actor changes the configuration of a server, firewall, router, switch, or any other infrastructure device, it is considered that he or she impacted the integrity of the system.
Data integrity is a requirement that information and programs are changed only in a specified and authorized manner. In other words, is the information the same as it was intended to be? For example, if you save a file with important information that must be relayed to members of your organization, but someone opens the file and changes some or all of the information, the file has lost its integrity. The consequences could be anything from co-workers missing a meeting you planned for a specific date and time, to 50,000 machine parts being produced with the wrong dimensions.
System integrity is a requirement that a system “performs its intended function in an unimpaired manner, free from deliberate or inadvertent unauthorized manipulation of the system.” A computer virus that corrupts some of the system files required to boot the computer is an example of deliberate unauthorized manipulation.
Errors and omissions are an important threat to data and system integrity. These errors are caused not only by data entry clerks processing hundreds of transactions per day, but also by all types of users who create and edit data and code. Even the most sophisticated programs cannot detect all types of input errors or omissions. In some cases, the error is the threat, such as a data entry error or a programming error that crashes a system. In other cases, the errors create vulnerabilities. Programming and development errors, often called “bugs,” can range in severity from benign to catastrophic.
To make this a bit more personal, let’s talk about medical and financial information. What if you are injured, unconscious, and taken to the emergency room of a hospital, and the doctors need to look up your health information. You would want it to be correct, wouldn’t you? Consider what might happen if you had an allergy to some very common treatment, and this critical information had been deleted from your medical records. Or think of your dismay if you check your bank balance after making a deposit and find that the funds have not been credited to your account!
Integrity and confidentiality are interrelated. If a user password is disclosed to the wrong person, that person could in turn manipulate, delete, or destroy data after gaining access to the system with the password he obtained. Many of the same vulnerabilities that threaten integrity also threaten confidentiality. Most notable, though, is human error. Safeguards that protect against the loss of integrity include access controls, such as encryption and digital signatures; process controls, such as code testing; monitoring controls, such as file integrity monitoring and log analysis; and behavioral controls, such as separation of duties, rotation of duties, and training.
What Is Availability?
The last component of the CIA triad is availability, which states that systems, applications, and data must be available to authorized users when needed and requested. The most common attack against availability is a denial-of-service (DoS) attack. User productivity can be greatly affected, and companies can lose a lot of money if data is not available. For example, if you are an online retailer or a cloud service provider and your ecommerce site or service is not available to your users, you could potentially lose current or future business, thus impacting revenue.
In fact, availability is generally one of the first security issues addressed by Internet service providers (ISPs). You may have heard the expressions “uptime” and “5-9s” (99.999% uptime). This means the systems that serve Internet connections, web pages, and other such services will be available to users who need them when they need them. Service providers frequently utilize service level agreements (SLAs) to assure their customers of a certain level of availability.
Just like confidentiality and integrity, we prize availability. We want our friends and family to “be there when we need them,” we want food and drink available, we want our money available, and so forth. In some cases, our lives depend on the availability of these things, including information. Ask yourself how you would feel if you needed immediate medical care and your physician could not access your medical records. Not all threats to availability could be malicious. For example, human error or a misconfigured server or infrastructure device can cause a network outage that will have a direct impact to availability.
Figure 3-3 shows a few additional examples of threats to availability.

FIGURE 3-3 Threats to Availability
We are more vulnerable to availability threats than to the other components of the CIA triad. We are certain to face some of them. Safeguards that address availability include access controls, monitoring, data redundancy, resilient systems, virtualization, server clustering, environmental controls, continuity of operations planning, and incident response preparedness.
Talking About Availability, What Is a Denial of Service (DoS) Attack?
Denial-of-service (DoS) and distributed DoS (DDoS) attacks have been around for quite some time now, but there has been heightened awareness of them over the past few years. A DoS attack typically uses one system and one network connection to perform a denial of service condition to a targeted system, network, or resource. DDoS attacks use multiple computers and network connections that can be geographically dispersed (that is, distributed) to perform a denial of service condition against the victim.
DDoS attacks can generally be divided into the following three categories:
Direct DDoS attacks
Reflected DDos attacks
Amplification DDoS attacks
Direct DDoS attacks occur when the source of the attack generates the packets, regardless of protocol, application, and so on, that are sent directly to the victim of the attack.
Figure 3-4 illustrates a direct DDoS attack.
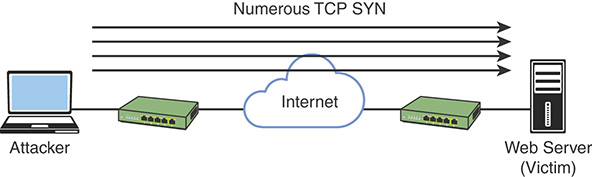
FIGURE 3-4 A Direct DDoS Attack
In Figure 3-4, the attacker launches a direct DoS to a web server (the victim) by sending numerous TCP SYN packets. This type of attack is aimed at flooding the victim with an overwhelming number of packets, oversaturating its connection bandwidth, or depleting the target’s system resources. This type of attack is also known as a “SYN flood attack.”
Reflected DDoS attacks occur when the sources of the attack are sent spoofed packets that appear to be from the victim, and then the sources become unwitting participants in the DDoS attacks by sending the response traffic back to the intended victim. UDP is often used as the transport mechanism because it is more easily spoofed because of the lack of a three-way handshake. For example, if the attacker (A) decides he wants to attack a victim (V), he will send packets (for example, Network Time Protocol [NTP] requests) to a source (S) that thinks these packets are legitimate. The source then responds to the NTP requests by sending the responses to the victim, who was never expecting these NTP packets from the source, as shown in Figure 3-5.
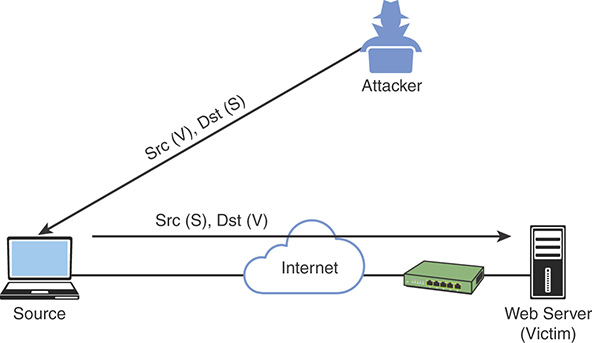
FIGURE 3-5 Reflected DDoS Attacks
An amplification attack is a form of reflected attack in which the response traffic (sent by the unwitting participant) is made up of packets that are much larger than those that were initially sent by the attacker (spoofing the victim). An example is when DNS queries are sent, and the DNS responses are much larger in packet size than the initial query packets. The end result is that the victim’s machine gets flooded by large packets for which it never actually issued queries.
Another type of DoS is caused by exploiting vulnerabilities such as buffer overflows to cause a server or even network infrastructure device to crash, subsequently causing a denial-of-service condition.
Many attackers use botnets to launch DDoS attacks. A botnet is a collection of compromised machines that the attacker can manipulate from a command and control (CnC) system to participate in a DDoS, send spam emails, and perform other illicit activities. Figure 3-6 shows how a botnet is used by an attacker to launch a DDoS attack.
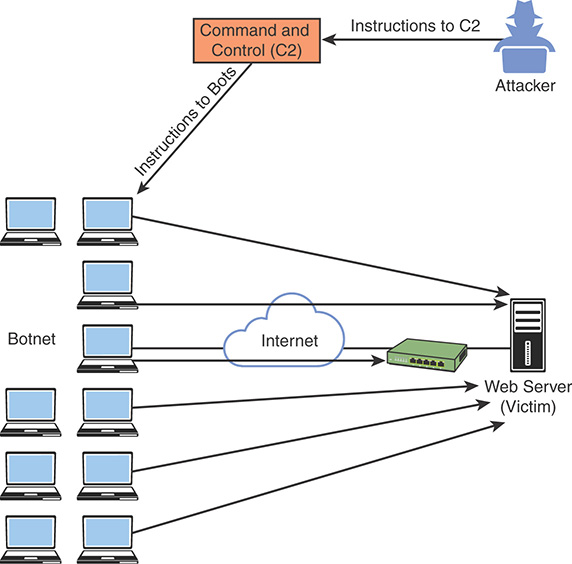
FIGURE 3-6 Botnets and Command and Control Systems
In Practice
The “Five A’s” of Information Security
Supporting the CIA triad of information security are five key information security principles, commonly known as the Five A’s. Here is a quick explanation of each:
Accountability: The process of tracing actions to their source. Nonrepudiation techniques, intrusion detection systems (IDS), and forensics all support accountability. This can help protect integrity and also confidentiality.
Assurance: The processes, policies, and controls used to develop confidence that security measures are working as intended. Auditing, monitoring, testing, and reporting are the foundations of assurance that all three elements in CIA are protected.
Authentication: The positive identification of the person or system seeking access to secured information or systems. Password, Kerberos, token, and biometric are forms of authentication. This also allows you to create control mechanisms to protect all CIA elements.
Authorization: Granting users and systems a predetermined level of access to information resources.
Accounting: The logging of access and usage of information resources.
CIA plus the Five A’s are fundamental objectives and attributes of a cybersecurity program.
In Figure 3-6, the attacker sends instructions to the CnC; subsequently, the CnC sends instructions to the bots within the botnet to launch the DDoS attack against the victim.
Who Is Responsible for CIA?
It is the information owners’ responsibility to ensure confidentiality, integrity, and availability. What does it mean to be an information owner? Under FISMA, an information owner is an official with statutory or operational authority for specified information and responsibility for establishing the criteria for its creation, collection, processing, dissemination, or disposal, which may extend to interconnected systems or groups of interconnected systems. More simply, an information owner has the authority and responsibility for ensuring that information is protected, from creation through destruction. For example, a bank’s senior loan officer might be the owner of information pertaining to customer loans. The senior loan officer has the responsibility to decide who has access to customer loan information, the policies for using this information, and the controls to be established to protect this information.
Information technology (IT) or information systems (IS) departments are widely perceived as owning the information and information systems. Perhaps this is due to the word “information” being part of the department title. For the record, with the exception of information specific to their department, IT and IS departments should not be considered information owners. Rather, they are the people charged with maintaining the systems that store, process, and transmit the information. They are known as information custodians—those responsible for implementing, maintaining, and monitoring safeguards and systems. They are better known as system administrators, webmasters, and network engineers. We will be taking a closer look at each of these roles in the next chapter.
NIST’s Cybersecurity Framework
Before discussing the NIST Cybersecurity Framework in detail, let’s define a security framework. Security framework is a collective term given to guidance on topics related to information systems security, predominantly regarding the planning, implementing, managing, and auditing of overall information security practices. One of the most comprehensive frameworks for cybersecurity is the NIST Cybersecurity Framework, https://www.nist.gov/cyberframework. NIST’s guidance into the trustworthiness of systems covers various technical areas. These areas include general cybersecurity guidance, cloud computing, big data, and physical systems. These efforts and guidance focus on the security objectives of confidentiality, integrity, and availability (CIA).
What Is NIST’s Function?
Founded in 1901, NIST is a nonregulatory federal agency within the U.S. Commerce Department’s Technology Administration. NIST’s mission is to develop and promote measurement, standards, and technology to enhance productivity, facilitate trade, and improve quality of life. The Computer Security Division (CSD) is one of seven divisions within NIST’s Information Technology Laboratory. The mission of NIST’s CSD is to improve information systems security as follows:
By raising awareness of IT risks, vulnerabilities, and protection requirements, particularly for new and emerging technologies.
By researching, studying, and advising agencies of IT vulnerabilities and devising techniques for the cost-effective security and privacy of sensitive federal systems.
By developing standards, metrics, tests, and validation programs
to promote, measure, and validate security in systems and services, and
to educate consumers and to establish minimum security requirements for federal systems.
By developing guidance to increase secure IT planning, implementation, management, and operation.
The 2002 E-Government Act [Public Law 107-347] assigned the NIST the mission of developing an Information Assurance Framework (standards and guidelines) designed for federal information systems that are not designated as national security systems. The NIST Information Assurance Framework includes the Federal Information Processing Standards (FIPS) and Special Publications (SP). Although developed for government use, the framework is applicable to the private sector and addresses the management, operational, and technical aspects of protecting the CIA of information and information systems.
NIST defines information security as the protection of information and information systems from unauthorized access, use, disclosure, disruption, modification, or destruction in order to provide CIA. Currently, there are more than 500 NIST information security–related documents. This number includes FIPS, the SP 800 series, information, Information Technology Laboratory (ITL) bulletins, and NIST interagency reports (NIST IR):
Federal Information Processing Standards (FIPS): This is the official publication series for standards and guidelines.
Special Publication (SP) 800 series: This series reports on ITL research, guidelines, and outreach efforts in information system security and its collaborative activities with industry, government, and academic organizations. SP 800 series documents can be downloaded from https://csrc.nist.gov/publications/sp800.
Special Publication (SP) 1800 series: This series focuses on cybersecurity practices and guidelines. SP 1800 series documents can be downloaded from https://csrc.nist.gov/publications/sp1800.
NIST Internal or Interagency Reports (NISTIR): These reports focus on research findings, including background information for FIPS and SPs.
ITL bulletins: Each bulletin presents an in-depth discussion of a single topic of significant interest to the information systems community. Bulletins are issued on an as-needed basis.
From access controls to wireless security, the NIST publications are truly a treasure trove of valuable and practical guidance.
So, What About ISO?
ISO is a network of the national standards institutes of more than 160 countries. Each member country is allowed one delegate, and a Central Secretariat in Geneva, Switzerland, coordinates the system. In 1946, delegates from 25 countries met in London and decided to create a new international organization, whose objective would be “to facilitate the international coordination and unification of industrial standards.” The new organization, ISO, officially began operations on February 23, 1947.
ISO is a nongovernmental organization. Unlike the United Nations, its members are not delegations of national governments. Nevertheless, ISO occupies a special position between the public and private sectors. This is because, on the one hand, many of its member institutes are part of the governmental structure of their countries, or are mandated by their government. On the other hand, other members have their roots uniquely in the private sector, having been set up by national partnerships of industry associations. ISO has developed more than 13,000 International Standards on a variety of subjects, ranging from country codes to passenger safety.
The ISO/IEC 27000 series (also known as the ISMS Family of Standards, or ISO27k for short) comprises information security standards published jointly by ISO and the International Electrotechnical Commission (IEC).
The first six documents in the ISO/IEC 27000 series provide recommendations for “establishing, implementing, operating, monitoring, reviewing, maintaining, and improving an Information Security Management System.” In all, there are 22 documents in the series, and several more are still under development.
ISO 27001 is the specification for an Information Security Management System (ISMS).
ISO 27002 describes the Code of Practice for information security management.
ISO 27003 provides detailed implementation guidance.
ISO 27004 outlines how an organization can monitor and measure security using metrics.
ISO 27005 defines the high-level risk management approach recommended by ISO.
ISO 27006 outlines the requirements for organizations that will measure ISO 27000 compliance for certification.
The framework is applicable to public and private organizations of all sizes. According to the ISO website, “the ISO standard gives recommendations for information security management for use by those who are responsible for initiating, implementing or maintaining security in their organization. It is intended to provide a common basis for developing organizational security standards and effective security management practice and to provide confidence in inter-organizational dealings.”
NIST Cybersecurity Framework
NIST’s Cybersecurity Framework is a collection of industry standards and best practices to help organizations manage cybersecurity risks. This framework is created in collaboration between the United States government, corporations, and individuals. The NIST Cybersecurity Framework is developed with a common taxonomy, and one of the main goals is to address and manage cybersecurity risk in a cost-effective way to protect critical infrastructure.
Private sector organizations are often using the NIST Cybersecurity Framework to enhance their cybersecurity programs
One of the goals of NIST’s Cybersecurity Framework is to not only help the United States government, but provide guidance to any organization regardless of size, degree of cybersecurity risk, or maturity.
Note
Chapter 16 covers the NIST Cybersecurity Framework in detail.
ISO Standards
The ISO 27002 standard has its origins in Great Britain. In 1989, the UK Department of Trade and Industry’s (DTI’s) Commercial Computer Security Centre (CCSC) developed the “Users Code of Practice,” designed to help computer users employ sound security practices and ensure the CIA of information systems. Further development came from the National Computing Centre (NCC), and later a group formed from British industry, to ensure that the Code was applicable and practical from a user’s point of view. The document was originally published as British Standards guidance document PD 0003: A Code of Practice for Information Security Management. After more input was received from private sector organizations, the document was reintroduced as British Standard BS7799:1995. After two revisions in 1997 and 1999, BS7799 was proposed as an ISO standard. Though the first revisions were defeated, it was eventually adopted by the ISO after an international ballot closed in August 2000 and was published with minor amendments as ISO/IEC 17799:2000 on December 1, 2000. A new version, ISO 17799:2005, was published in 2005. In 2007, this version was renamed as 27002:2005 and incorporated into the 27000 series. The most significant difference between the 17799 series and the 27000 series is an optional certification process. Organizations’ ISMS may be certified compliant with ISO/IEC 27001 by a number of Accredited Registrars worldwide.
In October 2013, ISO 27002:2005 was replaced with ISO 27002:2013. Two categories were added: Cryptography and Supplier Relationships. The Operations and Communications domain was split into two separate categories. Most important, a decision was made to remove the risk assessment guidance because it was a subset of ISO 27005, which specifically addresses information security risk management, including risk assessment, risk treatment, risk acceptance, risk communication, risk monitoring, and risk review. More information about ISO can be found at www.iso.org.
The ISO 27002:2013 Code of Practice is a comprehensive set of information security recommendations comprising best practices in information security. It is intended to serve as a single reference point for identifying the range of controls needed for most situations where information systems are used in industry and commerce as well as by large, medium, and small organizations. The term “organization” is used throughout this standard to mean both commercial and nonprofit organizations, such as public sector and government agencies. 27002:2013 does not mandate specific controls but leaves it to the organization to select and implement controls that suit them, using a risk-assessment process to identify the most appropriate controls for their specific requirements. The recommended practices are organized into the following “domains” or categories:
Information Security Policies
Organization of Information Security
Human Resources Security
Asset Management
Access Control
Cryptography
Physical and Environmental Security
Operations Security
Communications Security
Systems Acquisition, Development, and Maintenance
Supplier Relationships
Information Security Incident Management
Business Continuity Management
Compliance Management
We will use both the ISO 27002:2013 Code of Practice and the NIST guidance as a framework for developing procedures and policies. Using this framework will allow us to organize our approach to developing policies; it provides a structure for development and a method of grouping similar policies. The first step is to become familiar with the goals and intent of each of the security domains (or categories). In subsequent chapters, we examine each domain in depth, evaluate security practices, and develop policy.
Information Security Policies (ISO 27002:2013 Section 5)
The Information Security Policies domain focuses on information security policy requirements and the need to align policy with organizational objectives. The domain stresses the importance of management participation and support. This domain is covered in Chapter 4, “Governance and Risk Management.”
The corresponding NIST Special Publications are as follows:
SP 800-12, R1: “An Introduction to Information Security”
SP 800-100: “Information Security Handbook: A Guide for Managers”
Organization of Information Security (ISO 27002:2013 Section 6)
The Organization of Information Security domain focuses on establishing and supporting a management structure to implement and manage information security within, across, and outside the organization. Inward-facing governance concentrates on employee and stakeholder relationships. Outward-facing governance concentrates on third-party relationships. Third parties include vendors, trading partners, customers, and service providers. This domain is covered in Chapter 4.
The corresponding NIST Special Publications are as follows:
SP 800-12, R1: “An Introduction to Information Security”
SP 800-14: “Generally Accepted Principles and Practices for Securing Information Technology Systems”
SP 800-100: “Information Security Handbook: A Guide for Managers”
Human Resources Security Management (ISO 27002:2013 Section 7)
The Human Resources Security Management domain focuses on integrating security into the employee life cycle, agreements, and training. Human nature is to be trusting. This domain reminds us that there are both good and bad people and that we need to keep our eyes wide open. Chapter 6, “Human Resources Security,” covers this domain in more detail.
The corresponding NIST Special Publications are as follows:
SP 800-12: “An Introduction to Computer Security—The NIST Handbook”
SP 800-16: “Information Technology Security Training Requirements: A Role- and Performance-Based Model”
SP 800-50: “Building an Information Technology Security Awareness and Training Program”
SP 800-100: “Information Security Handbook: A Guide for Managers”
Asset Management (ISO 27002:2013 Section 8)
The Asset Management domain focuses on developing classification schema, assigning classification levels, and maintaining accurate inventories of data and devices. The importance of documented handling standards to protect information is stressed. This domain is covered in Chapter 5, “Asset Management and Data Loss Prevention.”
The corresponding NIST Special Publications are as follows:
SP 800-60: “Guide for Mapping Types of Information and Information Systems to Security Categories” (two volumes)
SP 800-88, R1: “Guidelines for Media Sanitization”
Access Control (ISO 27002:2013 Section 9)
The Access Control domain focuses on managing authorized access and preventing unauthorized access to information systems. This domain extends to remote locations, home offices, and mobile access. This domain is covered in Chapter 9, “Access Control Management.”
The corresponding NIST Special Publications are as follows:
SP 800-41, R1: “Guidelines on Firewalls and Firewall Policy”
SP 800-46, R2: “Guide to Enterprise Telework, Remote Access, and Bring Your Own Device (BYOD) Security”
SP 800-63-3: “Digital Identity Guidelines”
SP 800-63A: “Enrollment and Identity Proofing”
SP 800-63B: “Authentication and Life Cycle Management”
SP 800-63C: “Federation and Assertions”
SP 800-77: “Guide to IPsec VPNs”
SP 800-113: “Guide to SSL VPNs”
SP 80 0-114: “User’s Guide to Telework and Bring Your Own Device (BYOD) Security”
SP 800-153: “Guidelines for Securing Wireless Local Area Networks (WLANs)”
Cryptography (ISO 27002:2013 Section 10)
The Cryptography domain was added in the 2013 update. The domain focuses on proper and effective use of cryptography to protect the confidentiality, authenticity, and/or integrity of information. Special attention is paid to key management. This domain is included in Chapter 10, “Information Systems Acquisition, Development, and Maintenance.”
The corresponding NIST Special Publications are as follows:
800-57: “Recommendations for Key Management—Part 1: General (Revision 3)”
800-57: “Recommendations for Key Management—Part 2: Best Practices for Key Management Organization”
800-57: “Recommendations for Key Management—Part 3: Application-Specific Key Management Guidance”
800-64: “Security Considerations in the System Development Life Cycle”
800-111: “Guide to Storage Encryption Technologies for End User Devices”
Physical and Environmental Security (ISO 27002:2013 Section 11)
The Physical and Environmental Security domain focuses on designing and maintaining a secure physical environment to prevent unauthorized access, damage, and interference to business premises. Special attention is paid to disposal and destruction. This domain is covered in Chapter 7, “Physical and Environmental Security.”
The corresponding NIST Special Publications are as follows:
SP 800-12: “An Introduction to Computer Security—The NIST Handbook”
SP 800-14: “Generally Accepted Principles and Practices for Securing Information Technology Systems”
SP 800-88: “Guidelines for Media Sanitization”
SP 800-100: “Information Security Handbook: A Guide for Managers”
Operations Security (ISO 27002:2013 Section 12)
The Operations Security domain focuses on data center operations, integrity of operations, vulnerability management, protection against data loss, and evidence-based logging. This domain is covered in Chapter 8, “Communications and Operations Security.”
The corresponding NIST Special Publications are as follows:
SP 800-40, R3: “Guide to Enterprise Patch Management Technologies”
SP 800-115: “Technical Guide to Information Security Testing and Assessment”
SP 800-83, R1: “Guide to Malware Incident Prevention and Handling for Desktops and Laptops”
SP 800-92: “Guide to Computer Security Log Management”
SP 800-100: “Information Security Handbook: A Guide for Managers”
Communications Security (ISO 27002:2013 Section 13)
The Communications Security domain focuses on the protection of information in transit. The domain incorporates internal and external transmission as well as Internet-based communication. This domain is covered in Chapter 8.
The corresponding NIST Special Publications are as follows:
SP 800-14: “Generally Accepted Principles and Practices for Securing Information Technology Systems”
SP 800-45: “Guidelines on Electronic Mail Security”
SP 800-92: “Guide to Computer Security Log Management”
Information Systems Acquisition, Development, and Maintenance (ISO 27002:2013 Section 14)
The Information Systems Acquisition, Development, and Maintenance domain focuses on the security requirements of information systems, applications, and code from conception to destruction. This sequence is referred to as the systems development life cycle. This domain is covered in Chapter 10.
The corresponding NIST Special Publication is SP 800-23: “Guidelines to Federal Organizations on Security Assurance and Acquisition/Use of Tested/Evaluated Products.”
Supplier Relationships (ISO 27002:2013 Section 15)
The Supplier Relationship domain was added in the 2013 update. The domain focuses on service delivery, third-party security requirements, contractual obligations, and oversight. This domain is included in Chapter 8.
There is no corresponding NIST Special Publication.
Information Security Incident Management (ISO 27002:2013 Section 16)
The Information Security Incident Management domain focuses on a consistent and effective approach to the management of information security incidents, including detection, reporting, response, escalation, and forensic practices. This domain is covered in Chapter 11, “Cybersecurity Incident Response.”
The corresponding NIST Special Publications are as follows:
SP 800-61, R2: “Computer Security Incident Handling Guide”
SP 800-83: “Guide to Malware Incident Prevention and Handling”
SP 800-86: “Guide to Integrating Forensic Techniques into Incident Response”
Business Continuity (ISO 27002:2013 Section 17)
The Business Continuity Management domain focuses on availability and the secure provision of essential services during a disruption of normal operating conditions. ISO 22301 provides a framework to plan, establish, implement, operate, monitor, review, maintain, and continually improve a business continuity management system (BCMS). This domain is covered in Chapter 12, “Business Continuity Management.”
The corresponding NIST Special Publications are as follows:
SP 800-34: “Contingency Planning Guide for Information Technology System, Revision 1”
SP 800-84: “Guide to Test, Training and Exercise Programs for Information Technology Plans and Capabilities”
Compliance Management (ISO 2700:2013 Section 18)
The Compliance Management domain focuses on conformance with internal policy; local, national, and international criminal and civil laws; regulatory or contractual obligations; intellectual property rights (IPR); and copyrights. This domain relates to Part III, “Regulatory Compliance” (covered in Chapters 13, 14, and 15).
The corresponding NIST Special Publications are as follows:
SP 800-60 Volume I: “Guide for Mapping Types of Information and Information Systems to Security Categories”
SP 800-60 Volume II: “Appendices to Guide for Mapping Types of Information and Information Systems to Security”
SP 800-66: “An Introductory Resource Guide for Implementing the Health Insurance Portability and Accountability Act (HIPAA) Security Rule”
SP 800-122: “Guide to Protecting the Confidentiality of Personally Identifiable Information (PII)”
Too Many Domains?
As with policies, for an information security program to be effective, it must be meaningful and relevant as well as appropriate to the size and complexity of the organization. Not all organizations will need all the policies referenced in the ISO 27002 Code of Practice. The key is to understand what domains are applicable to a given environment and then develop, adopt, and implement the controls and policies that make sense for the organization. Remember, policies must support, not hinder, the mission and goals of an organization.
Section 4.1 of the 27002:2013 Code of Practice document informs us that the order of the domains does not imply their importance, nor are they listed in priority order. As such, this book takes the liberty of reordering the sections and, where applicable, combining domains. Starting with Chapter 4 and continuing through Chapter 12, we map the security objectives of each domain to realistic, relevant, and usable practices and policies. We define goals and objectives, explore in detail relevant security issues, and discuss the applicability of the standard.
Note
Within each chapter, you will find “In Practice” sidebars that contain relevant policy statements. Each policy statement is preceded by a synopsis. The synopsis is included only as explanatory text and would not normally be included in a policy document. At the end of the book, you will find a comprehensive information security policy document that includes all the policy statements as well as the supporting policy elements discussed in Chapter 2, “Cybersecurity Policy Organization, Format, and Styles.”
Summary
Ensuring confidentiality, integrity, and availability is the unifying principle of every information security program. Collectively referred to as the CIA triad or CIA security model, each attribute represents a fundamental objective and corresponding action related to the protection of information, processes, or systems. Confidentiality is protection from unauthorized access or disclosure. Integrity is protection from manipulation. Availability is protection from denial of service (DoS). In support of the CIA triad are the security principles known as the Five A’s: accountability, assurance, authentication, accounting, and authorization.
An information owner is one who has been assigned the authority and responsibility for ensuring that information and related systems are protected from creation through destruction. This includes making decisions on information classification, safeguards, and controls. Information custodians are those responsible for implementing, maintaining, and monitoring the safeguards based on decisions made by information owners. Cohesive decision making requires a framework.
A security framework is a collective term given to guidance on topics related to information systems security, predominantly regarding the planning, implementing, managing, and auditing of overall information security practices. In this chapter you learned highlights of NIST’s Cybersecurity Framework. Chapter 16 covers the NIST Cybersecurity Framework in detail. The International Organization for Standardization (ISO) has published a technology-neutral Code of Standards for Information Security known as the ISO/IEC 27002:2013. This standard has been internationally adopted by both private and public organizations of all sizes. ISO 27002:2013 is divided into 14 domains. Each of these categories has a control objective, compliance requirements, and recommended policy components. NIST has a number of Special Publications that complement the ISO Code of Practice. The publications provide in-depth research, recommendations, and guidance that can be applied to security domains and specific technologies. The ISO standards and the NIST Cybersecurity Framework could also be used by regulatory organizations to provide assurance that a cyber policy is robust and complete. In this book, we use both to build our information security policy and program.
Test Your Skills
Multiple Choice Questions
1. Which of the following are the three principles in the CIA triad?
A. Confidence, integration, availability
B. Consistency, integrity, authentication
C. Confidentiality, integrity, availability
D. Confidentiality, integrity, awareness
2. Which of the following is an example of acting upon the goal of integrity?
A. Ensuring that only authorized users can access data
B. Ensuring that systems have 99.9% uptime
C. Ensuring that all modifications go through a change-control process
D. Ensuring that changes can be traced back to the editor
3. Which of the following is a control that relates to availability?
A. Disaster recovery site
B. Data loss prevention (DLP) system
C. Training
D. Encryption
4. Which of the following is an objective of confidentiality?
A. Protection from unauthorized access
B. Protection from manipulation
C. Protection from denial of service
D. Protection from authorized access
5. Which of the following is a good definition for confidentiality?
A. The property that information is not made available or disclosed to unauthorized individuals, entities, or processes
B. The processes, policies, and controls used to develop confidence that security measures are working as intended
C. The positive identification of the person or system seeking access to secured information or systems
D. The logging of access and usage of information resources
6. An important element of confidentiality is that all sensitive data needs to be controlled, audited, and monitored at all times. Which of the following provides an example about how data can be protected?
A. Ensuring availability
B. Encrypting data in transit and at rest
C. Deploying faster servers
D. Taking advantage of network programmability
7. Which of the following statements identify threats to availability? (Select all that apply.)
A. Loss of processing capabilities due to natural disaster or human error
B. Loss of confidentiality due to unauthorized access
C. Loss of personnel due to accident
D. Loss of reputation from unauthorized event
8. Which of the following terms best describes the logging of access and usage of information resources?
A. Accountability
B. Acceptance
C. Accounting
D. Actuality
9. Which of the following combinations of terms best describes the Five A’s of information security?
A. Awareness, acceptance, availability, accountability, authentication
B. Awareness, acceptance, authority, authentication, availability
C. Accountability, assurance, authorization, authentication, accounting
D. Acceptance, authentication, availability, assurance, accounting
10. An information owner is responsible for _____________________.
A. maintaining the systems that store, process, and transmit information
B. protecting the business reputation and results derived from use of that information
C. protecting the people and processes used to access digital information
D. ensuring that information is protected, from creation through destruction
11. Which of the following terms best describes ISO?
A. Internal Standards Organization
B. International Organization for Standardization
C. International Standards Organization
D. Internal Organization of Systemization
12. Which of the following statements best describes opportunistic crime?
A. Crime that is well planned
B. Crime that is targeted
C. Crime that takes advantage of identified weaknesses or poorly protected information
D. Crime that is quick and easy
13. Which of the following terms best describes the motivation for hacktivism?
A. Financial
B. Political
C. Personal
E. Fun
14. The longer it takes a criminal to obtain unauthorized access, the _____
A. more time it takes
B. more profitable the crime is
C. better chance of success
D. better chance of getting caught
15. Which of the following terms best describes an attack whose purpose is to make a machine or network resource unavailable for its intended use?
A. Man-in-the-middle
B. Data breach
C. Denial of service
D. SQL injection
16. Information custodians are responsible for _____
A. writing policy
B. classifying data
C. approving budgets
D. implementing, maintaining, and monitoring safeguards
17. The National Institute of Standards and Technology (NIST) is a(n) ______
A. international organization
B. privately funded organization
C. U.S. government institution, part of the U.S. Department of Commerce
D. European Union agency
18. The International Organization for Standardization (ISO) is _____
A. a nongovernmental organization
B. an international organization
C. headquartered in Geneva
D. all of the above
19. The current ISO family of standards that relates to information security is _______________.
A. BS 7799:1995
B. ISO 17799:2006
C. ISO/IEC 27000
D. None of the above
20. Which of the following terms best describes the security domain that relates to managing authorized access and preventing unauthorized access to information systems?
A. Security policy
B. Access control
C. Compliance
D. Risk assessment
21. Which of the following terms best describes the security domain that relates to how data is classified and valued?
A. Security policy
B. Asset management
C. Compliance
D. Access control
22. Which of the following terms best describes the security domain that includes HVAC, fire suppression, and secure offices?
A. Operations
B. Communications
C. Risk assessment
D. Physical and environmental controls
23. Which of the following terms best describes the security domain that aligns most closely with the objective of confidentiality?
A. Access control
B. Compliance
C. Incident management
D. Business continuity
24. The primary objective of the __________ domain is to ensure conformance with GLBA, HIPAA, PCI/DSS, and FERPA.
A. Security Policy
B. Compliance
C. Access Control
D. Contract and Regulatory
25. Processes that include responding to a malware infection, conducting forensics investigations, and reporting breaches are included in the _____________ domain.
A. Security Policy
B. Operations and Communications
C. Incident Management
D. Business Continuity Management
26. Which of the following terms best describes a synonym for business continuity?
A. Authorization
B. Authentication
C. Availability
D. Accountability
27. Which domain focuses on service delivery, third-party security requirements, contractual obligations, and oversight?
A. Incident Handling and Forensics
B. Security Policy
C. Supplier Relationships
D. Information Security Incident Management
28. Which domain focuses on proper and effective use of cryptography to protect the confidentiality, authenticity, and/or integrity of information?
A. Cryptography
B. Cryptanalysis
C. Encryption and VPN Governance
D. Legal and Compliance
29. Which domain focuses on integrating security into the employee life cycle, agreements, and training?
A. Operations and Communications
B. Human Resources Security Management
C. Governance
D. Legal and Compliance
30. Which of the following security objectives is most important to an organization?
A. Confidentiality
B. Integrity
C. Availability
D. The answer may vary from organization to organization
31. Which of the following are some of the components of NIST’s Cybersecurity Framework core functions? (Choose all that apply.)
A. Identify
B. Integrity
C. Detect
D. Protect
E. All of the above
Exercises
Exercise 3.1: Understanding CIA
Define the security term “confidentiality.” Provide an example of a business situation where confidentiality is required.
Define the security term “integrity.” Provide an example of a business situation in which the loss of integrity could result in significant harm.
Define the security term “availability.” Provide an example of a business situation in which availability is more important than confidentiality.
Exercise 3.2: Understanding Opportunistic Cybercrime
Define what is meant by an “opportunistic” crime.
Provide an example.
Locate (online) a copy of the most recent Verizon Data Breach Incident Report. What percentage of cybercrimes are considered “opportunistic”?
Exercise 3.3: Understanding Hacktivism or DDoS
Find a recent news article relating to either hacktivism or a distributed denial of service (DDoS) attack.
Summarize the attack.
Explain why the attacker was successful (or not).
Exercise 3.4: Understanding NIST and ISO
At their respective websites, read the Mission and About sections of both ISO (www.iso.org) and the NIST Computer Security Resource Center (http://csrc.nist.gov/). Describe the similarities and differences between the organizations.
Which do you think is more influential, and why?
Identify how they complement each other.
Exercise 3.5: Understanding ISO 27002
Choose one of the ISO 27002:2013 categories and explain why this domain is of particular interest to you.
ISO 27002 Supplier Relationships (Section 15) was added in the 2013 version. Why do you think this section was added?
27002:2013 does not mandate specific controls but leaves it to the organization to select and implement controls that suit them. NIST Special Publications provide specific guidance. In your opinion, which approach is more useful?
Projects
Project 3.1: Conducting a CIA Model Survey
Survey 10 people about the importance of the CIA model to them. Use the following table as a template. Ask them to name three types of data they have on their phone or tablet. For each data type, ask which is more important—that the information on their device be kept confidential (C), be correct (I), or be available (A).
#
Participant Name
Device Type
Data Type 1
CIA
Data Type 2
CIA
Data Type 3
CIA
1.
Sue Smith
iPhone
Phone numbers
I
Pictures
A
Text messages
C
2.
3.
Summarize the responses.
Are the responses in line with your expectations? Why or why not?
Project 3.2: Preparing a Report Based on the NIST Special Publications 800 Series Directory
Locate the NIST Special Publications 800 Series directory.
Read through the list of documents. Choose one that interests you and read it.
Prepare a report that addresses the following:
Why you chose this topic
What audience the document was written for
Why this document would be applicable to other audiences
The various sections of the document
Whether the document addresses confidentiality, integrity, or availability
Project 3.3: Preparing a Report on ISO 27001 Certification
Research how many organizations are currently ISO 27001–certified.
Prepare a report on how an organization achieves ISO 27001 certification.
Project 3.4: NIST’s Cybersecurity Framework Spreadsheet
Download NIST’s Cybersecurity Framework spreadsheet from: https://www.nist.gov/cyberframework.
Familiarize yourself with the different components, categories, subcategories, and informative references of the NIST Cybersecurity Framework.
Download NIST’s CSF tool from https://www.nist.gov/cyberframework/csf-reference-tool. Familiarize yourself with all the capabilities of the tool and how it may allow you to start developing your own cybersecurity program.
Prepare a report that explains how an enterprise or private sector organization can leverage the framework to help with the following:
Identify assets and associated risks.
Protect against threat actors.
Detect and respond to any cybersecurity events and incidents.
Recover after a cybersecurity incident happened.
Case Study
Policy Writing Approach
Regional Bank has been growing rapidly. In the past two years, it has acquired six smaller financial institutions. The long-term strategic plan is for the bank to keep growing and to “go public” within the next three to five years. FDIC regulators have told management that they will not approve any additional acquisitions until the bank strengthens its information security program. The regulators commented that Regional Bank’s information security policy is confusing, lacking in structure, and filled with discrepancies. You have been tasked with “fixing” the problems with the policy document.
Consider the following questions: Where do you begin this project? Would you use any material from the original document? What other materials should you request? Would you want to interview the author of the original policy? Who else would you interview? Should the bank work toward ISO certification? Which ISO 27002:2013 domains and sections would you include? Should you use NIST’s Cybersecurity Framework and related tools? What other criteria should you consider?
Create a project plan of how you would approach this project.
References
Regulations Cited
“NIST Cybersecurity Framework,” accessed 04/2018, https://www.nist.gov/cyberframework.
“Federal Code 44 U.S.C., Sec. 3542,” accessed 04/2018, https://www.gpo.gov/fdsys/pkg/CFR-2002-title44-vol1/content-detail.html.
“The Cybersecurity Framework: Implementation Guidance for Federal Agencies,” accessed 04/2018, https://csrc.nist.gov/publications/detail/nistir/8170/draft.
“Public Law 107–347–E-Government Act of 2002,” official website of the U.S. Government Printing Office, accessed 04/2018, www.gpo.gov/fdsys/pkg/PLAW-107publ347/content-detail.html.
ISO Research
“International Standard ISO/IEC 27001,” First Edition 2005-10-15, published by ISO, Switzerland.
“International Standard ISO/IEC 27000,” Second Edition 2012-12-01, published by ISO, Switzerland.
“International Standard ISO/IEC 27002:2013,” Second Edition 2013-10-01, published by ISO, Switzerland.
“About ISO,” official website of the International Organization for Standardization (ISO), accessed on 04/2018, https://www.iso.org/about-us.html.
“A Short History of the ISO 27000 Standards: Official,” The ISO 27000 Directory, accessed on 04/2018, www.27000.org/thepast.htm.
“An Introduction to ISO 27001, ISO 27002, … ISO 27008,” The ISO 27000 Directory, accessed on 04/2018, www.27000.org.
“The ISO/IEC 27000 Family of Information Security Standards,” IT Governance, accessed 04/2018, https://www.itgovernance.co.uk/iso27000-family.
“ISO/IEC 27000 Series,” Wikipedia, accessed 04/2018, https://en.wikipedia.org/wiki/ISO/IEC_27000-series.
NIST Research
“NIST General Information,” official website of the National Institute of Standards and Technology, accessed 04/2018, https://www.nist.gov/director/pao/nist-general-information.
“NIST Computer Security Division,” official website of the NIST Computer Security Resource Center, accessed 04/2018, https://csrc.nist.gov.
“Federal Information Processing Standards (FIPS) Publications,” official website of the NIST Computer Security Resource Center, accessed 04/2018, https://www.nist.gov/itl/fips-general-information.
“Special Publications (800 Series) Directory,” official website of the NIST Computer Security Resource Center, accessed 04/2018, https://csrc.nist.gov/publications.
Other References
“Distributed Denial of Service Attack (DDoS),” Security Search, accessed 05/2018, http://searchsecurity.techtarget.com/definition/distributed-denial-of-service-attack.
“Hacktivism,” Wikipedia, accessed 05/2018, http://en.wikipedia.org/wiki/index.html?curid=162600.
Poulen, K., and Zetter, K. “U.S. Intelligence Analyst Arrested in WikiLeaks Video Probe,” Wired Magazine, accessed 05/2018, http://www.wired.com/threatlevel/2010/06/leak/.
“Edward Snowden,” accessed 05/2018, https://www.biography.com/people/edward-snowden-21262897.
“What Is WikiLeaks,” WikiLeaks, accessed 05/2018, https://wikileaks.org.
“Cisco security: Russia, Iran switches hit by attackers who leave US flag on screens,” ZDNet, accessed on 05/2018.
