Chapter 12
Business Continuity Management
Chapter Objectives
After reading this chapter and completing the exercises, you will be able to do the following:
Define a disaster.
Appreciate the importance of emergency preparedness.
Analyze threats, risks, and business impact assessments.
Explain the components of a business continuity plan and program.
Develop policies related to business continuity management.
Section 17 of the ISO 27002:2013 is “Business Continuity Management.” The objective of the Business Continuity Management domain is to ensure the continued operation and secure provision of essential services during a disruption of normal operating conditions. To support this objective, threat scenarios are evaluated, essential services and processes are identified, and response, contingency, and recovery and resumption strategies, plans, and procedures are developed, tested, and maintained. Business continuity is a component of organization risk management.
We have learned valuable lessons from the events of September 11, 2001, Hurricane Katrina, the 2013 Boston bombing, and Hurricane Maria’s devastation in Puerto Rico. Preparation and business continuity plans do more than protect business assets; in the long run, they protect employees and their families, investors, business partners, and the community. Business continuity plans are, in essence, a civic duty.
FYI: ISO/IEC 27002:2013 and NIST Guidance
Section 17 of ISO 27002:2013, “Business Continuity Management,” focuses on availability and the secure provision of essential services during a disruption of normal operating conditions. ISO 22301 provides a framework to plan, establish, implement, operate, monitor, review, maintain, and continually improve a business continuity management system (BCMS).
Corresponding NIST guidance is provided in the following documents:
SP 800-34: “Contingency Planning Guide for Information Technology System, Revision 1”
SP 800-53: “Security and Privacy Controls for Federal Information Systems and Organizations, Revision 5”
SP 800-84: “Guide to Test, Training and Exercise Programs for Information Technology Plans and Capabilities”
Emergency Preparedness
A disaster is an event that results in damage or destruction, loss of life, or drastic change to the environment. In a business context, a disaster is an unplanned event that has the potential to disrupt the delivery of mission-critical services and functions, jeopardize the welfare of employees, customers, or business partners, and/or cause significant financial harm. From a security perspective, a disaster manifests itself as a sustained disruption of system availability and/or confidentiality or integrity controls. The cause can be environmental, operational, accidental, or willful, as illustrated in Figure 12-1.

FIGURE 12-1 Disasters and Their Causes
Worldwide, a major disaster occurs almost daily. According to the Federal Emergency Management Agency (FEMA), a disaster has occurred, on average, every week in the United States for the past 10 years. The U.S. Department of Homeland Security (DHS) has identified the impact of 15 disaster scenarios that could take the country days (explosives) to weeks (food contamination) to months (pandemic, major hurricane) to years (nuclear detonation, major earthquake) to potentially recover from.
Preparing for a disaster can make the difference between life and death, success or failure, yet most businesses are not prepared. An Ad Council survey found that nearly two-thirds (62%) of respondents did not have an emergency plan in place for their business. When disaster inevitably strikes, without a plan, there is little chance of a successful response and recovery. The Insurance Information Institute reported that up to 40% of businesses affected by a natural or human-caused disaster never reopen.
The goal of emergency preparedness is to protect life and property. Disasters are unplanned; however, they should not be unanticipated. How much an organization should prepare depends on a number of factors, including risk tolerance, financial strength, regulatory requirements, and stakeholder impact. What we know for sure is that relying solely on insurance and post-disaster government assistance is shortsighted and, in some cases, negligent.
What Is a Resilient Organization?
A resilient organization is one that has the ability to quickly adapt and recover from known or unknown changes to the environment. Resilience doesn’t just happen. It requires management support, investment, planning, and layers of preparation. In their post-9/11 study, “The Five Principles of Organizational Resilience,” Gartner reminds us that “organizational resilience has taken on a new urgency since the tragic events of Sept. 11. The ability to respond quickly, decisively and effectively to unforeseen and unpredictable forces is now an enterprise imperative.” It cites leadership, culture, people, systems, and settings as the bedrock of an agile and adaptive organization.
Resilience begins with enterprise leadership setting the priorities, allocating the resources, and making the commitments to establish organizational resilience throughout the enterprise.
A resilient culture is built on principles of organizational empowerment, purpose, trust, and accountability.
People who are properly selected, motivated, equipped, and led will overcome almost any obstacle or disruption.
Organizations achieve agility and flexibility by combining a highly distributed workplace model with a highly robust and collaborative IT infrastructure.
Alternative workplace techniques such as office hoteling, telecommuting, and desk sharing provide the level of workplace flexibility and agility that is essential for mitigating the risk of catastrophic or disruptive incidents.
Regulatory Requirements
Business disruption has an economic and societal ripple effect. Emergency preparedness is a civic duty and, in many cases, a regulatory requirement. In 1998, President Clinton issued Presidential Decision Directive (PDD) 63 Critical Infrastructure Protection. The first in a series of executive branch directives, PDD-63 outlined roles, responsibilities, and objectives for protecting the nation’s utility, transportation, financial, and other essential infrastructure, and introduced the concept of public-private partnership. In 2003, President Bush issued Presidential Directive HSPD-7 Critical Infrastructure Identification, Prioritization, and Protection, which designates certain sectors of the national infrastructure as critical to the national and economic security of the United States and the well-being of its citizenry, and requires steps be taken to protect it, including emergency response and continuity measures.
Congress recognized the issue as well and included emergency preparedness in critical sector regulatory legislation. The Health Insurance Portability and Accountability Act (HIPAA) Contingency Plan Standard 164.308(a)(7) requires covered entities to “Establish (and implement as needed) policies and procedures for responding to an emergency or other occurrence (for example, fire, vandalism, system failure, and natural disaster) that damages systems that contain electronic protected health information.” The standard includes implementation specifications for data backup, disaster recovery, and emergency mode operation plans. The Gramm-Leach-Bliley Safeguards Act requires financial institutions to “identify reasonably foreseeable internal and external threats that could result in unauthorized disclosure, misuse, alteration, or destruction of customer information or customer information systems” and to “take measures to protect against destruction, loss, or damage of customer information due to potential environmental hazards, such as fire and water damage or technological failures.” Similar legislation has been issued by the Federal Energy Regulatory Commission (FERC) for utility companies, by the Nuclear Energy Regulatory Commission (NERC) for nuclear power plants, by the Federal Communications Commission (FCC) for telecom carriers, and by the Food and Drug Administration (FDA) for pharmaceutical companies.
In October 2012, the Department of Homeland Security issued Federal Continuity Directive 1. The directive states that “Federal Executive Branch organizations, regardless of their size or location, shall have in place a viable continuity capability to ensure resiliency and continued performance of their organization’s essential functions under all conditions.” Included in the directive was a restatement of the government’s roles in creating public/private partnerships in order to create and sustain a “culture of continuity.”
In May 2012, NIST released Special Publication 800-34, R1: Contingency Planning Guide for Federal Information Systems, which provides guidance for federal agencies. The guidance is applicable to public and private sector business continuity planning.
In Practice
Emergency Preparedness Policy
Policy Synopsis: Demonstrate the organization’s commitment to emergency preparedness and business continuity.
Policy Statement:
An emergency preparedness and business continuity strategy that ensures the safety of employees and customers, enables the company to perform essential functions absent normal operating conditions, protects organizational assets, and meets regulatory requirements is an organizational priority.
The company will designate necessary resources to develop and maintain emergency preparedness and business continuity plans and procedures.
Business Continuity Risk Management
Continuity planning is simply the good business practice of ensuring the execution of essential functions. Continuity planning is an integral component of organizational risk management. In Chapter 4, “Governance and Risk Management,” we defined risk management as the process of identifying, analyzing, assessing, and communicating risk and accepting, avoiding, transferring, or controlling it to an acceptable level considering associated costs and benefits of any actions taken. Risk management for continuity of operations requires that organizations identify threats (threat assessment), determine risk (risk assessment), and assess the internal and external impact of the disruption of mission-critical or essential services (business impact assessment). The two anticipated outcomes are (1) the identification and (if feasible) mitigation of significant threats and (2) the documentation of essential services. This information is then used to construct response, continuity, and recovery operations.
What Is a Business Continuity Threat Assessment?
A business continuity threat can best be defined as a potential danger to the organization. Threats can be business-specific, local, regional, national, or even global. The objective of a business continuity threat assessment is to identify viable threats and predict the likelihood of occurrence. Threat modeling takes into account historical and predictive geographic, technological, physical, environmental, third-party, and industry factors such as the following:
What type of disasters have occurred in the community or at this location?
What can happen due to the geographic location?
What could cause processes or information systems to fail?
What threats are related to service provider dependency?
What disasters could result from the design or construction of the facility or campus?
What hazards are particular to the industry sector?
Identified threats are rated in terms of the likelihood of occurrence and potential impact sans controls. The higher the rating, the more significant the threat. The challenge to this approach is the unexpected event. Sadly, as we saw on 9/11, threats are not always predictable. Table 12-1 presents threat assessments that take into account past occurrences.
TABLE 12-1 Threat Assessments: Historical
Threat Categories |
Threat |
Description |
Likelihood Scale 1–5 [5=highest] |
Impact Scale 1–5 [5=highest] |
Impact Description |
Inherent Risk (L*I) |
|---|---|---|---|---|---|---|
Environmental |
Wildfire |
Wildfire consumed 15,000 acres, approximately 50 miles northwest of HQ |
4 |
5 |
Campus fire. |
20 HIGH |
Service provider dependency |
Disruption of Internet connectivity |
Multiple periods of ISP downtime or extreme latency occurred. |
4 |
5 |
Disruption of external mail, VPN connectivity, and cloud-based applications. |
20 HIGH |
Service provider dependency |
Brownouts |
Summer temperatures and corresponding air conditioning usage consistently results in brief periods of low power. |
3 |
5 |
Power fluctuations have the potential to damage equipment. |
15 MED |
Location |
Flood |
Flash flooding is an annual occurrence on Highway 16. |
5 |
2 |
Campus not affected; however, deliveries and personnel may be. |
10 LOW |
What Is a Business Continuity Risk Assessment?
The business continuity threat assessment identifies the most likely and significant business continuity–related threats to the organization. The business continuity risk assessment evaluates the sufficiency of controls to prevent a threat from occurring or to minimize its impact. The outcome is the residual risk associated with each threat. The residual risk level provides management with an accurate portrayal of what happens if the threat is exercised under current conditions.
In a best-case scenario, the residual risk is within organizational tolerance. If the residual risk is not within tolerance, the organization must decide to take action to lower the risk level, approve the risk, or share the risk. Table 12-2 illustrates risk assessment considerations for the specific threat of a wildfire. The actual process and calculations used should mirror the organizational risk assessment methodology.
TABLE 12-2 Sample Wildfire Risk Assessment
Threat |
Area wildfires resulting in personnel evacuation and potential destruction. |
Inherent Risk |
High (as determined by the threat assessment). |
Control Assessment |
|
Physical Controls |
Fire berm around the campus. Contract with local firm for quarterly removal of flammable shrubs, leaves, dead limbs, and twigs within a 1,000-foot zone. |
Building Controls |
Fireproof construction. Sensor alarms with Fire Department (FD) notification. Fire and smoke sensors and sprinklers throughout the building. Fire safety maps throughout the building. Lighted emergency exits. No outside flammable substances stored near the building. |
Data Center Controls |
Sensor alarms with FD notification. Clean agent fire suppression system. Water mist system. |
Personnel Controls |
Evacuation plans. Fire drills conducted quarterly. |
Technology Controls |
Secondary data center 300 miles from primary campus. Near-time data replication. Secondary data center can support 200 concurrent remote users. |
Financial Controls |
Fire and hazard insurance policy. Business disruption insurance policy. |
Control Assessment |
Satisfactory. |
Identified Vulnerabilities |
Gas-powered generator. Gas fumes are combustible. |
Residual Risk |
Elevated. |
Risk Reduction Recommendation |
Replace gas-powered generator with diesel-powered generator. |
Lowering the risk level requires the organization to implement additional controls and safeguards and/or to modify existing ones. In general, preventative or mitigating controls that deter, detect, and/or reduce disruption and impact are preferable to contingency procedures or recovery activities. As new technologies become available, preventative controls should be reevaluated and recovery strategies modified. The widespread adoption of virtualization as a preventative control is a good example of how technological innovation can influence business continuity planning.
Approving the risk implies that the organization is willing to assume the level of risk even though it is not within an acceptable range. As we discussed in Chapter 4, approving elevated or severe risk level is an executive-level decision. The decision may be based on cost, market conditions, external pressures, or a willingness to play the odds.
Risk sharing is when the risk (and consequences) are distributed among two or more parties. Examples are outsourcing and insurance.
What Is a Business Impact Assessment?
The objective of a business impact assessment (BIA) is to identify essential services/processes and recovery time frames. In business continuity planning, essential means that the absence of, or disruption of the service/process, would result in significant, irrecoverable, or irreparable harm to the organization, employees, business partners, constituents, community, or country. Participants in the BIA process often incorrectly equate important with essential. There are a number of very important organization activities, such as marketing, recruiting, and auditing, that can be suspended in a disaster situation without impacting the viability of the organization, endangering constituents, or violating the law. On the other hand, there are mundane services, such as maintaining an ATM cash dispenser, that may be critical in a regional disaster. The key is to stay focused on the services required in the hours and days after a disaster strikes.
A business impact analysis is a multistep collaborative activity that should include business process owners, stakeholders, and corporate officers. This multistep collaborative activity is illustrated in Figure 12-2.
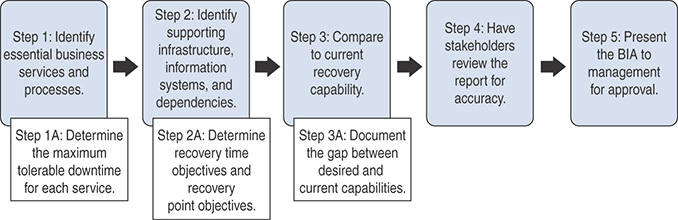
FIGURE 12-2 Business Impact Analysis
As noted in the previous steps, the BIA process incorporates three metrics:
The maximum tolerable downtime (MTD) is the total length of time an essential business function can be unavailable without causing significant harm to the business.
The recovery time objective (RTO) is the maximum amount of time a system resource can be unavailable before there is an unacceptable impact on other system resources or business processes.
The recovery point objective (RPO) represents the point in time, prior to a disruption or system outage, that data can be recovered (in other words, the acceptable data loss).
In a perfect world, every essential system would be either redundant or available for immediate or near-time recovery. In reality, no organization has unlimited financial resources. The MTD, RTO, and RPO are useful in determining the optimum recovery investment and ancillary plans.
The outcome of a business impact analysis is a prioritized matrix of services, the required infrastructure, information systems, and dependencies for each service, recovery objectives, assessment of capabilities, and delta between the current and desired state. This information is then used by executive management to make investment decisions and to guide the development of disaster recovery and business contingency plans and procedures. Assuming an organization rated “Customer Communications” as an essential business process or service, Table 12-3 illustrates the components of a BIA.
TABLE 12-3 Business Impact Assessment: Customer Communications
Essential Business Process or Service: Customer Communications |
|||
|---|---|---|---|
Delivery Channels |
Call Center |
Website |
|
Required Infrastructure |
Voice circuits. Wide area network power. |
Internet access. |
Internet access. Wide area network power. |
Required Devices/Information Systems |
IP phone system. Call center system. |
Hosted externally. |
Email system, including email application servers and gateway filters. Authentication servers. |
Third-Party Dependencies |
Telco voice circuits. |
Web hosting company. Internet service provider (ISP). |
DNS propagation. |
Maximum Tolerable Downtime (MTD) |
5 minutes. |
Need to update the site within 60 minutes. |
60 minutes. |
Recovery Time Objective (RTO) |
Immediate. |
30 minutes. |
45 minutes. |
Recovery Point Objective (RPO) |
12 hours for historical data. |
24 hours for website content. |
No acceptable data loss. |
Current Capability |
All calls will be automatically rerouted to the secondary data center. Redundant call center system located at secondary data center. Statistical data can be restored from backups. Data is replicated every 4 hours. |
Localized disaster would not impact the website. |
Redundant fully replicated email infrastructure located at the secondary data center. Assuming access to the secondary data center, external email will not be impacted. Incoming email will be delayed approximately 15 minutes, which is the time it takes for an MX record to be updated. |
Identified Issues/Points of Failure |
Call center staff is located at the primary location. Relocation will take a minimum of 8 hours. |
Administrative access (required for updating) is restricted to specific IP addresses. Updating the access list is a third-party function. SLA is 30 minutes. |
If the primary campus is available, the impact is minimal. If the primary campus is unavailable, only those users with remote access capability will be able to utilize email. |
Capability Delta |
755 minutes |
0 |
+ 30 minutes |
Data Loss Delta |
0 |
0 |
0 |
In Practice
Business Impact Assessment
Synopsis: Require and assign responsibility for an annual BIA.
Policy Statement:
The Chief Operating Officer is responsible for scheduling an enterprisewide annual BIA. System owner participation is required.
The BIA will identify essential services and processes. Essential is defined as meeting one or more of the following criteria:
Required by law, regulation, or contractual obligation.
Disruption would be a threat to public safety.
Disruption would result in impact to the health and well-being of employees.
Disruption would result in irreparable harm to customers or business partners.
Disruption would result in significant or unrecoverable financial loss.
For each essential service and/or process, the maximum tolerable downtime (MTD) will be documented. The MTD is the total length of time an essential function or process can be unavailable without causing significant harm to the business.
For each essential service and/or process, supporting infrastructure, devices/information systems, and dependencies will be identified.
Recovery time objectives (RTOs) and recovery point objectives (RPOs) for supporting infrastructure and devices/information systems will be documented.
Current capability and capability delta will be identified. Deviations that put the organization at risk must be reported to the Board of Directors.
The Chief Operating Officer, the Chief Information Officer, and the Business Continuity Team are jointly responsible for aligning the BIA outcome with the business continuity plan.
The Business Continuity Plan
The objective of business continuity planning is to ensure that organizations have the capability to respond to and recover from disaster situations. Response plans focus on the initial and near-term response and include such elements as authority, plan activation, notification, communication, evacuation, relocation, coordination with public authorities, and security. Contingency plans focus on immediate, near-term, and short-term alternate workforce and business processes. Recovery plans focus on the immediate, near-term, and short-term recovery of information systems, infrastructure, and facilities. Resumption plans guide the organization back to normalcy. Taken as a whole, this plan is referred to as the business continuity plan (BCP) or as the continuity of operations plan (COOP). The discipline is referred to as business continuity management.
In Practice
Business Continuity Plan Policy
Synopsis: Require the organization to have a business continuity plan.
Policy Statement:
The company’s business continuity strategy will be documented in a business continuity plan. The plan will include plans, procedures, and ancillary documentation related to emergency preparedness, disaster preparation, response, contingency operations, recovery, resumption, training, testing, and plan maintenance.
Roles and Responsibilities
If we consider that the objective of business continuity management is to keep the business in business, it stands to reason that the responsibility must be distributed throughout the organization. Business continuity management involves the entire organization, from the Board member who approves the policy to the employee who carefully follows a related procedure. Depending on the size and complexity of the organizations as well as the nature of disaster, third parties such as public health and safety personnel, insurance representatives, legal counsel, service providers, and government agencies may all have a role to play. Business continuity responsibilities can be categorized as governance, operational, and tactical.
Governance
Governance is a continuing process in which diverse objectives, competing interests, and a range of ideas are evaluated, and ultimately binding decisions are made and supported. It is the responsibility of the Board of Directors (or equivalent) to provide oversight and guidance, authorize business continuity management–related policy, and be legally accountable for the actions of the organization.
Executive management is expected to provide leadership, demonstrate commitment, allocate budget, and devote resources to the development and continued upkeep of the BCP. In an emergency, they declare a disaster, activate the plan, and support the Business Continuity Team.
Operational Management
When disaster strikes, quick mobilization is essential to mitigate damages. It is imperative that there be designated leadership with the authority to act quickly. This is the primary role of the Business Continuity Team (BCT), which is vested by the Board of Directors with the authority to make decisions related to disaster preparation, response, and recovery. BCT membership should represent a cross-section of the organization, including senior management, physical security, information technology (IT), human resources (HR), marketing/communications, information security, and business units. In concert, the team is responsible for the development, maintenance, testing, and updating of all related plans. The BCT may create subteams and assign responsibilities. Because the BCT will operate in unpredictable situations, second-in-command personnel should be trained and ready to assume their position. After executive management has declared a disaster and activated the plan, the BCT is responsible for assessing damage, managing the response, communications, continuity, and recovery activities, and providing status updates to executive management. It’s also tasked with providing a post-disaster assessment of recovery and response efforts.
Tactical Activities
Tactical responsibilities are distributed throughout an enterprise. Depending on the size of the organization, some of these responsibilities may be consolidated. Unfortunately, it is all too common to encounter organizations that view the IT department as the owner of the business continuity process and expect IT to “take care of it.” Although it is true that IT is a vital participant, business continuity management, as suggested by the following list, is an organization responsibility:
The IT department is responsible for designing and supporting resilience systems and for the recovery of information and information systems in a disaster situation.
Department managers are responsible for defining the operational needs of their department and for creating and maintaining functional departmental contingency procedures.
The HR department is responsible for the communication with and welfare of personnel and provides emergency-related services and assistance.
The marketing or communications department is responsible for crafting and releasing official statements, communicating with the media, and managing internal communication include updates.
The purchasing department is responsible for expediently ordering necessary supplies and equipment.
The training department is responsible for delivering business continuity–related training and ancillary materials.
The internal audit department audits the BCP and procedures and reports its findings to executive management. The audit satisfies the best practice requirements of separation of duties and oversight.
In Practice
Business Continuity Management Policy
Synopsis: Assign business continuity management responsibilities.
Policy Statement:
The Board of Directors is responsible for authorizing the business continuity plan. Reference to the business continuity plan is inclusive of plans, procedures, and ancillary documentation related to disaster preparation, response, contingency operations, recovery, resumption, training, testing, and plan maintenance. The Board must be apprised on a timely basis of any material changes to the business continuity strategy.
The Chief Operating Officer or designee is responsible for the development, maintenance, and management of the business continuity strategy and plan.
The Chief Financial Officer will include business continuity expenses in the annual operating budget.
The Office of Information Technology is responsible for designing and supporting resilient systems and for the recovery of information and information systems in a disaster situation.
Senior managers are responsible for defining the operational needs of their departments and for creating and maintaining functional departmental contingency procedures.
The Chief Operating Officer will appoint the Business Continuity Team chairperson. The chairperson will appoint members of the Business Continuity Team. The team must include representatives of key functional areas, including but not limited to operations, communications, finance, IT, information security, physical security, and facilities management. Team members are responsible for designating backups to serve in their absence.
Business Continuity Team responsibilities include active participation in business continuity preparation, response, recovery, and resumption activities. At its discretion, the Business Continuity Team may create subteams and assign responsibilities.
The President/CEO has authority to declare an emergency, activate the plan, and contact/assemble the Business Continuity Team. In her absence, the COO has the authority to declare an emergency, activate the plan, and contact/assemble the Business Continuity Team. In his absence, the CFO has the authority to declare an emergency, activate the plan, and contact/assemble the Business Continuity Team. If none of the above listed are available, the Business Continuity Team chair in consultation with the Chairman of the Board of Directors has the authority to declare an emergency, activate the plan, and contact/assemble the Business Continuity Team.
The Business Continuity Team will be the authoritative body during emergency response and recovery periods. Officers and employees will continue to conduct the affairs of the company under the guidance of the team leadership, except in matters that by statute require specific approval of the Board of Directors, or to conform to any governmental directives.
FYI: Business Continuity Management Education and Certification
DRI International (originally Disaster Recovery Institute International) is a nonprofit organization with the mission to make the world prepared. As the global education and certification body in business continuity and disaster recovery planning, DRI International sets the standard for professionalism. There are more than 11,000 active certified professionals worldwide. Continuity Professional certifications include Associate Business Continuity Professional (ABCP), Certified Functional Continuity Professional (CFCP), Certified Business Continuity Professional (CBCP), and Master Business Continuity Professional (MBCP). In addition, professionals may choose to specialize in audit, public sector, or health care. Learn more at www.drii.org.
Disaster Response Plans
What happens in those initial moments following a disaster has both an immediate impact and a noteworthy ripple effect. Disaster response can be either chaotic or orderly. The difference between these scenarios is established procedures and responsibilities. Think back to elementary school days. Hopefully, you never experienced a fire at your school. But if you had, chances are that everyone would have evacuated the building safely. Why? Teachers and staff had specific assignments. Evacuation routes were mapped out. Students were taught not to panic, to line up single file, to follow a leader, and to gather at a specific location. All of these procedures and roles were reinforced through regularly scheduled fire drills. Similarly, organizations that have prepared for a disaster are able to focus on three immediate response goals:
Protecting the health and safety of employees, customers, first responders, and the public at large.
Minimizing damage to property and the environment.
Evaluating the situation and determining next steps.
The response plan should define the organizational structure, roles, and responsibilities, designated command and control, communications, and alternate work sites. Ancillary to the disaster response plan is the occupant emergency plan and procedures for immediate personnel safety. This plan is maintained separately because it may be used in nondisaster situations.
Organizational Structure
An orderly response requires both disciplined leadership and acknowledgement of who is in charge. First and foremost, it is incumbent upon everyone to follow the instructions of first responders and public safety officials. Board-approved policy should vest corporate officers or executive management with the authority to declare an emergency and activate the plan. In a disaster situation, the organizational structure and/or chain of command may be affected by injury, death, travel restrictions, or personal circumstances. It is important to have a clearly defined Board-approved succession plan.
For decisions pertaining to the response, continuity, and recovery effort, the BCT is generally the authoritative body. Because this is a departure from normal operating conditions, it is critical that executive management publicly support the authority of the BCT and that employees know who is in charge.
Command and Control Centers
Upon declaration of a disaster and the activation of the BCP, all BCT members should report to a designated command and control center. Primary and alternate command and control centers (sometimes referred to as “war rooms”) are predetermined locations equipped to support the work of the BCT. A conference room, a training room, or even a large office can quickly be transformed into a command and control center. The command and control center is initially used to direct operations and then may be used as a meeting center until normal business operations resume. At a minimum, the command and control center should be prestocked with the BCP manuals, tables, chairs, whiteboards, phones, surge strips, and mobile device power cords. If available (and operational), having voice and video conferencing equipment on hand serves to facilitate communication. All BCT members should have directions to the location, keys, and access codes.
Communication
A disaster may occur with little or no advance warning. The importance of the capability to quickly alert and account for employees, service providers, and first responders cannot be overstated. Every organization should have an occupant emergency plan (OEP), which describes evacuation and shelter-in-place procedures in the event of a threat or incident to the health and safety of personnel. Such events include fire, bomb threat, chemical release, domestic violence in the workplace, or medical emergency. The OEP is distinct from the BCP and is often maintained by either the HR department or facilities management.
The business continuity response plan must assign responsibility for both internal and external communications and include instructions for using a variety of communications channels. To prevent miscommunication, a designated communications liaison and spokespersons should be appointed. All public statements should be authorized by the BCT. Employees should be instructed that all media requests and questions be referred to the designated spokesperson without comment (on or off the record). The widespread use of social media is both a blessing and a curse. Social media can be used to quickly disseminate information and misinformation. Particularly in an evolving situation, employees may not have all the facts and/or may inadvertently disclose confidential information; they should be strongly discouraged from posting any information about the event on personal social media accounts.
Relocation Strategies
In cases of natural, environmental, or physical disaster, relocation of critical business functions may be necessary. Relocation strategies need to consider both delivery and operational business functions. Delivery functions provide service or product to the customer. An example would be the teller line at a bank or a customer call center. Operational business functions provide the core infrastructure of the organization. They include accounting, marketing, HR, office services, security, and IT. It may not be practical to consider relocating all staff. The relocation plan should consider staffing levels for essential services, space considerations, utility and environmental needs, transportation, and logistics. Telecommuting, including mobile device access, may minimize personnel relocation requirements. Options for alternate operational locations include hot, warm, cold, and mobile sites. Alternate sites may be owned, leased, or even borrowed. Organizations that have multiple operational sites may be able to redirect the workload to a location that has not been impacted by the disaster situation.
A hot site is a location that is fully operational and ready to move into; it has been configured with redundant hardware, software, and communications capability. Data has been replicated to the hot site on a real-time or near-time basis. Figure 12-3 shows an example of a hot site.

FIGURE 12-3 A Hot Site Example
A warm site is an environmentally conditioned workspace that is partially equipped with information systems and telecommunications equipment to support relocated operations. Computers and devices located at warm sites need to be configured and brought online. Data needs to be restored. Figure 12-4 shows an example of a warm site.

FIGURE 12-4 A Warm Site Example
A cold site is a backup facility that has power, HVAC, and secure access. There is no staged equipment.
Mobile sites are self-contained units. The units are provided by a third party and generally arrive equipped with the required hardware, software, and peripherals. Data needs to be restored.
A mirrored site is fully redundant with real-time replication from the production site. Mirrored sites can assume processing with virtually no interruption.
A reciprocal site is based on an agreement to have access to/use of another organization’s facilities.
In addition to the previous options, it may be possible to offload operations to service bureaus or outsource operations to third parties.
In Practice
Emergency Response Plan Policy
Synopsis: Ensure that the organization is prepared to respond to an emergency situation.
Policy Statement:
The Chief Operating Officer is responsible for developing and maintaining the emergency response plan. The emergency response plan is a component of the enterprise business continuity plan.
The objective of the emergency response plan is to protect the health and safety of employees, customers, first responders, and the public at large, minimizing damage to property and the environment, and set in motion response, contingency, and recovery operations.
The emergency response plan must, at a minimum, address organizational alerts and notification, disaster declaration, internal and external communication channels, command and control centers, relocation options, and decision making authority.
Ancillary to the response plan are OEPs and the crisis communication plan (CCP). Both plans may be utilized in conjunction with and/or referenced by the response plan.
The Office of Human Resources is responsible for maintaining the OEP.
The Office of Communications and Marketing is responsible for maintaining a CCP.
Personnel responsible for response operations must receive appropriate training.
Response plans and procedures must be audited in accordance with the schedule set forth by the Business Continuity Team.
Response procedures must be tested in accordance with the schedule set forth by the Business Continuity Team.
Operational Contingency Plans
Operational contingency plans address how an organization’s essential business processes will be delivered during the recovery period. Let’s consider some examples:
Physical access to facilities at a maximum-security prison is regulated by a biometric fingerprint access control system. The access control system is managed and monitored by an information system. The back-end information system becomes unavailable due to power loss. The business contingency procedure would address an alternate method to lock and unlock doors. This may be a physical key or perhaps an access code. In either case, knowing where the key is or what the code is would be essential to operations.
A financial institution offers its customers the option of telephone banking services. Due to a fire, the telebanking phone system is not operational. Contingency procedures would address rerouting telebanking calls to customer service and ensuring that the customer service representatives (CSRs) could service the customers or at the very least provide information while the telebanking system is being recovered.
A federal agency is forced to vacate its premises due to a biochemical threat. The agency receives and processes unemployment claims. Its most critical task is producing unemployment checks based on the claims. Unemployed individuals depend on receiving these payments in a timely manner. Business contingency procedures address alternate methods to accept and process claims as well as to print and distribute checks. Procedures may include notifying recipients by phone that payments are delayed, estimating payments based on the previous week’s claims, and/or coordinating with another agency for processing and postal services.
Operational contingency plans and procedures are developed at the departmental level. They are the responsibility of the business process owner.
Operational Contingency Procedures
Operational contingency documentation should follow the same form as standard operating procedures. As with standard operating procedures, operational contingency operating procedures are instructions that should be understandable to everyone who may need to use them. They should be written as simply as possible. It is best to use short, direct sentences so that the reader can easily understand the procedure. Chapter 8, “Communications and Operations Security,” introduced four formats for writing procedural documentation: simple step, hierarchical, graphic, and flowchart. These same formats are recommended for writing operational contingency operating procedures.
In Practice
Operational Contingency Plan Policy
Synopsis: Ensure that the organization can continue to provide essential services during the recovery period.
Policy Statement:
Business process owners are responsible for developing and maintaining operational contingency plans. Operational contingency plans are a component of the enterprise business continuity plan.
The operational contingency plans must include strategies and procedures for providing essential services as determined by the business impact assessment during the recovery operations.
The amount of procedural detail required should be enough that competent personnel familiar with the service or process could perform the alternate operation.
External system dependencies and relevant contractual agreements must be reflected in the contingency plan.
Personnel responsible for contingency operations must receive appropriate training.
Contingency plans and procedures must be audited in accordance with the schedule set forth by the Business Continuity Team.
Contingency procedures must be tested in accordance with the schedule set forth by the Business Continuity Team.
The Disaster Recovery Phase
In the disaster recovery phase, the organization begins the process of restoring or replacing damaged infrastructure, information systems, and facilities. Recovery activities can range from immediate failover to redundant systems to the significantly longer process of procuring equipment, restoring data, and potentially rebuilding facilities. Regardless of the strategy employed, it is critical that procedures have been documented and tested. Priorities for recovery operations should be consistent with the results of the business impact analysis.
Developing recovery plans and procedures can be a daunting task. A proven successful approach is to break the plan down into categories and assign responsibilities at the operational level, such as mainframe, network, communications, infrastructure, and facilities.
Mainframe recovery is specific to the restoration of a mainframe computer (or equivalent capability) and corresponding data processing.
Network recovery is specific to information systems (servers, workstations, mobile devices, applications, data stores, and supporting utilities) and includes the restoration of functionality and data.
Communications recovery encompasses internal and external transmission systems, including local-area network (LAN), wide-area network (WAN), data circuits (T1, T3, MPLS), and Internet connectivity. Included in this category are connectivity devices such as switches, routers, firewalls, and IDSs.
Infrastructure recovery encompasses those systems providing a general operating environment, including environmental and physical controls.
Facilities recovery addresses the need to rebuild, renovate, or relocate the physical plant.
The criticality and priority determined by the business impact analysis provides the framework for choosing the appropriate strategy and level of investment.
Recovery Procedures
A disaster is not the time to figure out how to recover or restore a system, nor is it the time to determine inventory or search for vendor contacts. All these items need to be addressed beforehand and documented in recovery procedures and ancillary files. Recovery processes can be very technical. The procedures should explain in a logical progression what needs to be done, where it needs to be done, and how it needs to be done. Procedures may reference other documents. Table 12-4 illustrates a recovery procedure for an Active Directory domain controller.
TABLE 12-4 Active Directory Domain Controller Recovery Procedure
Active Directory Domain Controller Recovery |
|
Support Phone Numbers |
Cisco Support: 800-553-2447 Microsoft Technical Support Regular Support: 888-888-9999 Business Critical: 888-888-7777 |
General Information |
Active Directory domain controllers provide authentication, DNS, and DHCP services. If a domain controller fails, the remaining domain controllers will be able to authenticate user accounts, provide DNS resolution, and assign dynamic addresses. |
Configuration Information |
There are four Windows Server domain controllers: Two are located at the data center in rack 7G. One is located in the Building A data closet rack. It is the second device from the top. One is located in the Building B data closet rack. It is the fourth device from the top. There are five FSMO roles that are server-specific: schema master, domain naming master, PDC emulator, RID master, and infrastructure master. Reference/recovery/server_roles.xls for server assignments. For more information on FMSO roles, refer to http://support.microsoft.com/kb/324801. |
Recovery/Resumption Instructions |
|
The key to disaster recovery is the ability to respond using validated, maintained, and tested procedures. All recovery procedures should be reviewed annually. Planning for recovery is a component of the systems development life cycle (SDLC) process.
Service Provider Dependencies
Recovery plans often depend on vendors to provide services, equipment, facilities, and personnel. This reliance should be reflected in contractual service agreements. Service level agreements (SLAs) should specify how quickly a vendor must respond, the type and quantity of replacement equipment guaranteed to be available, personnel and facility availability, and the status of the organization in the event of a major disaster involving multiple vendor clients. Service agreements should be referenced in the procedure as well as contact information, agreement numbers, and authorization requirements. Service provider dependencies should be included in the annual testing.
In Practice
Disaster Recovery Plan Policy
Synopsis: Ensure that the organization can recover infrastructure, systems, and facilities damaged during a disaster.
Policy Statement:
The Office of Information Technology and the Office of Facilities Management are responsible for their respective disaster recovery plans. Disaster recovery plans are a component of the enterprise business continuity plan.
The disaster recovery plan must include recovery strategies and procedures for systems and facilities as determined by the business impact assessment.
Modifications to the recovery plan must be approved by the Chief Operating Officer.
The amount of procedural detail required should be enough that competent personnel familiar with the environment could perform the recovery operation.
External system dependencies and relevant contractual agreements must be reflected in the recovery plan.
Personnel responsible for recovery operations must receive appropriate training.
Recovery plans and procedures must be audited in accordance with the schedule set forth by the Business Continuity Team.
Recovery procedures must be testing in accordance with the schedule set forth by the Business Continuity Team.
The Resumption Phase
The objective of the resumption phase is to transition to normal operations. Two major activities are associated with this phase: validation of successful recovery and deactivation of the BCP.
Validation is the process of verifying that recovered systems are operating correctly and that data integrity has been confirmed. Validation should be the final step of every recovery procedure.
Deactivation is the official notification that the organization is no longer operating in emergency or disaster mode. At this point, the BCT relinquishes authority, and normal operating procedures are reinstated. After the dust settles, figuratively and literally, an after-action report with lessons learned should be documented by the BCT. The BCP should be reviewed and revised based on the findings and recommendations of the BCT.
Plan Testing and Maintenance
A BCP should be maintained in a state of readiness, which includes having personnel trained to fulfill their roles and responsibilities within the plan, having plans exercised to validate their content, and having systems and system components tested to ensure their operability. NIST SP 800-84: Guide to Test, Training and Exercise Programs for Information Technology Plans and Capabilities provides guidelines on designing, developing, conducting, and evaluating test, training, and exercise (TT&E) events so that organizations can improve their ability to prepare for, respond to, manage, and recover from adverse events.
Why Is Testing Important?
It would be hard to overstate the importance of testing. Until tested, plans and procedures are purely theoretical. The objective of a testing program is to ensure that plans and procedures are accurate, relevant, and operable under adverse conditions. As important as demonstrating success is uncovering inadequacies. The worst time to find out that your plans were incomplete, outdated, or just plain wrong is in the midst of a disaster. The extent and complexity of the testing program should be commensurate with the criticality of the function or system. Prior to testing, a test plan should be developed that details the test objective, type of test, success criteria, and participants.
In addition to procedures being tested, the BCP should be audited. At a minimum, testing exercises and audits should be conducted annually. The results of both should be provided to the Board of Directors.
Testing Methodologies
There are three testing methodologies: tabletop exercises, functional exercises, and full-scale testing. Tabletop exercises can be conducted as structured reviews or simulations:
A structured review focuses on a specific procedure or set of procedures. Representatives from each functional area participate in a systematic walkthrough of the procedures with the goal of verifying accuracy and completeness. A structured review can also be used as a training exercise with the objective of familiarization.
A tabletop simulation focuses on participant readiness. A facilitator presents a scenario and asks the exercise participants’ questions related to the scenario, including decisions to be made, procedures to use, roles, responsibilities, time frames, and expectations. A tabletop exercise is discussion-based only and does not involve deploying equipment or other resources.
Functional exercises allow personnel to validate plans, procedures, resource availability, and participant readiness. Functional exercises are scenario-driven and limited in scope, such as the failure of a critical business function or a specific hazard scenario. Functional exercises can be conducted in either a parallel or production environment.
Full-scale testing is conducted at the enterprise level. Based on a specific scenario, the business operates as if a disaster was declared. Normal operations are suspended. Recovery and contingency plans and procedures are implemented. Full-scale testing can be expensive and risky. It is, however, the most accurate test of plans and procedures.
Audits
A business continuity plan audit is an evaluation of how the business continuity program in its entirety is being managed. This includes policy, governance, assessments, documentation, testing, and maintenance. Audits are conducted by personnel independent of the response, contingency, or recovery efforts. Auditors will look at the quality and effectiveness of the organization’s BCP process and determine whether the testing program is sufficient. At a minimum, you can anticipate they will ask the following questions:
Is there a written business continuity policy and plan?
Has the business continuity policy and plan been approved by the Board of Directors?
How often is it reviewed and/or reauthorized?
How often is a BIA conducted? By whom?
Who is on the BCT?
What training have they had?
What training has the user community had?
Is there a written test plan?
How often is the plan tested?
Are the results documented?
If third parties are involved, what is the process for testing/verifying their procedures?
Who is responsible for maintaining the plan?
As with all examinations and audits, independence must be maintained. Examiners and auditors must not be connected to the management or maintenance of related policies, plans, procedures, training, or testing.
Plan Maintenance
BCPs must stay in sync with organizational and personnel changes. At a minimum, on an annual basis, roles and responsibilities, including BCT membership, should be revisited, a BIA conducted, and recovery and contingency plans evaluated. Aside from the annual review, the BCP may need to be updated due to changes in regulatory requirements, technology, and the threat landscape.
FYI: Regulatory Expectations
The best way to know what to expect from an audit is to be privy to audit work papers. Fortunately, one of the best sets of work papers is in the public domain. The Federal Financial Institutions Examination Council (FFIEC) develops and publishes guides and audit work papers for use by field examiners in financial institution regulatory agencies. These resources are found in the FFIEC Information Technology Examination Handbook InfoBase. The handbooks are available to the public and can be downloaded from the FFIEC website at www.ffiec.gov.
Another example is the European Network and Information Security Agency (ENISA) IT Continuity website and underlying resources. Its main goal is to “Promote Risk Assessment and Risk Management methods to enhance the capability of dealing with network and information security threats” [ENISA Regulation]. Additional information can be found at ENISA’s website at https://www.enisa.europa.eu/.
In Practice
Business Continuity Testing and Maintenance Policy
Synopsis: Codify testing and maintenance requirements and responsibility.
Policy Statement:
Reference to the business continuity plan is inclusive of plans, procedures, and ancillary documentation related to disaster preparation, response, contingency operations, recovery, resumption, training, testing, and plan maintenance.
The Chief Operating Officer or designee is responsible for maintenance of the business continuity plan.
The Chief Operating Officer or designee will conduct an annual review of the business continuity plan.
The Business Continuity Team is responsible for publishing an annual testing schedule and managing the test plan. The Chief Operating Officer will report the results to the Board of Directors.
Internal audit is tasked with managing and selecting an independent firm to conduct an annual audit of the business continuity plan. The independent audit firm will report the results to the Board of Directors or designated committee.
FYI: Small Business Note
A disaster situation can be particularly devastating to a small business, yet few are prepared. According to David Paulison, former executive director of the Federal Emergency Management Agency (FEMA), “Small businesses that don’t have a plan in place generally don’t survive after a disaster, whether it’s a flood or a tornado. We see that anywhere from 40–60 percent of those that are hit like that simply don’t come back to business.”
In response to the lack of preparedness, the Small Business Administration (SBA) has made available a number of general preparedness resources and specific disaster information designed to assist the small business community and support economic recovery.
General preparedness resources include an identifying critical business systems worksheet, creating a preparedness program template, and instructions on building a business disaster preparedness kit.
Specific disaster information includes hurricanes, winter weather, earthquakes, tornadoes, wildfires, floods, and cybersecurity.
The resources can be accessed at the following site: https://www.sba.gov/business-guide/manage/prepare-emergencies-disaster-assistance.
Summary
A disaster is an event that results in damage or destruction, loss of life, or drastic change to the environment. Preparing for a disaster can make the difference between life and death, success or failure. Preparedness is a regulatory requirement for industry sectors deemed critical to national security. Not investing the time and effort required to face disruptions is negligent and the consequences severe.
A resilient organization is one that has the ability to quickly adapt and recover from known or unknown changes to the environment. The objective of business continuity planning is to ensure that organizations have the capability to respond to and recover from disaster situations. Response plans focus on the initial and near-term response and include such elements as authority, plan activation, notification, communication, evacuation, relocation, coordination with public authorities, and security. Contingency plans focus on immediate, near-term, and short-term alternate workforce and business processes. Recovery plans focus on the immediate, near-term, and short-term recovery of information systems, infrastructure, and facilities. Resumption plans guide the organization back to normalcy. Taken as a whole, this is referred to as the business continuity plan (BCP) or as the continuity of operations plan (COOP). The discipline is referred to as business continuity management.
The precursor to developing a BCP is assessing the threat environment and organizational risk as well as determining essential business services and processes. A business continuity threat assessment identifies viable threats and predicts the likelihood of occurrence. Threat modeling takes into account historical and predictive geographic, technological, physical, environmental, third-party, and industry factors.
A business continuity risk assessment evaluates the sufficiency of controls to prevent the threat from occurring or to minimize its impact. A business impact assessment (BIA) identifies essential services/processes and recovery time frames. In BCP, essential means that the absence of, or disruption of, a service/process would result in significant, irrecoverable, or irreparable harm to the organization, employees, business partners, constituents, community, or country. The BIA process uses three prioritization metrics: MTD, recovery time objectives (RTOs), and recovery point objectives (RPOs). The MTD is the total length of time an essential business function can be unavailable without causing significant harm to the business. The RTO is the maximum amount of time a system resource can be unavailable before there is an unacceptable impact on other system resources or business process. The RPO represents the point in time, prior to a disruption or system outage, that data can be recovered; in other words, the acceptable data loss.
Business continuity management is a distributed responsibility. The Board of Directors or organizational equivalent is ultimately accountable for ensuring that the organization is prepared. It is the responsibility of executive management to ensure that threats are evaluated, impact to business processes recognized, and resources allocated. They are also charged with declaring a disaster and activating the BCP. The BCT, appointed by executive management, is expected to manage preparation and be the authoritative body in a declared disaster.
A BCP should be maintained in a state of readiness, which includes having personnel trained to fulfill their roles and responsibilities within the plan, having plans exercised to validate their content, and having systems and system components tested and audited to ensure their operability. The plan in its entirety should be reviewed on a scheduled basis. It should be reauthorized annually by the Board of Directors or organizational equivalent.
Business Continuity Management policies include Emergency Preparedness, Business Impact Assessment, Business Continuity Management, Emergency Response Plan, Operational Contingency Plan, Disaster Recovery Plan, and Business Continuity Testing and Maintenance.
Test Your Skills
Multiple Choice Questions
1. Which of the following terms best describes the primary objective of business continuity?
A. Assurance
B. Availability
C. Accounting
D. Authentication
2. Which of the following statements best describes a disaster?
A. A disaster is a planned activity.
B. A disaster is an isolated incident.
C. A disaster is a significant disruption of normal business functions.
D. A disaster is a change in management structure.
3. Flood, fire, and wind are examples of which type of threat?
A. Malicious act
B. Environmental
C. Logistical
D. Technical
4. Which of the following terms best describes the process of identifying viable threats and likelihood of occurrence?
A. Risk assessment
B. Threat assessment
C. Likelihood assessment
D. Impact assessment
5. Which of the following terms best describes the process of evaluating the sufficiency of controls?
A. Risk assessment
B. Threat assessment
C. Likelihood assessment
D. Impact assessment
6. Which of the following statements best describes the outcome of a BIA?
A. A BIA generates RTOs.
B. A BIA produces an organizational agreement on essential processes and services.
C. A BIA identifies the gap between current and desired recovery capabilities.
D. All of the above
7. An acceptable length of time a business function or process can be unavailable is known as _________________.
A. maximum unavailability (MU)
B. total acceptable time (TAT)
C. maximum tolerable downtime (MTD)
D. recovery time objective (RTO)
8. The recovery point objective (RPO) represents ____________.
A. acceptable data loss
B. acceptable processing time loss
C. acceptable downtime
D. None of the above
9. Recovery time objectives relate to which of the following?
A. The maximum amount of time a guest system can be unavailable
B. The maximum amount of time a system resource can be unavailable
C. The minimum amount of time a system resource can be unavailable
D. None of the above
10. Which of the following plans are included in a BCP?
A. Resumption plans
B. Response plans
C. Contingency plans
D. All of the above
11. Legal and regulatory accountability for an organization’s preparedness is assigned to _______________.
A. the BCT
B. regulators
C. the Board of Directors or organizational equivalent
D. service providers
12. The authority to declare an emergency and activate the plan is owned by ____________.
A. the BCT
B. executive management
C. the Board of Directors or organizational equivalent
D. service providers
13. Which of the following plans include evacuation and in-shelter procedures?
A. The fire drill plan
B. The occupant emergency plan
C. The business contingency plan
D. A FEMA directive
14. A __________ site is a backup facility that has power, HVAC, and secure access.
A. hot
B. cold
C. replica
D. mirror
15. ___________ are self-contained units. The units are provided by a third-party and generally arrive equipped with the required hardware, software, and peripherals. Data need to be restored.
A. Mobile sites
B. Hot sites
C. Cold sites
D. Mirrored sites
16. A _________ site is fully redundant with real-time replication from the production site.
A. mirrored
B. hot
C. cold
D. replica
17. A _______ site is based on a agreement to have access to/use of another organization’s facilities
A. mirrored
B. hot
C. cold
D. reciprocal
Exercises
Exercise 12.1: Assessing Threats
Based on historical occurrences, identify three environmental or location-based threats to your campus or workplace.
Choose one of the three threats and document how often the threat has occurred in the past 20 years.
Describe the factors you would take into consideration in predicting the likelihood of a reoccurrence within the next five years.
Exercise 12.2: Analyzing an Occupant Emergency Response Plan
Locate a copy of the occupant emergency response plan (note that it may go by a different name, such as evacuation plan) for your campus or workplace. If you cannot locate one, use the Internet to locate one from another school or organization.
When was the plan last updated?
Summarize the key components of the plan. In your opinion, does the plan provide adequate instructions?
Exercise 12.3: Assessing the Training and Testing of an Occupant Emergency Response Plan
Locate a copy of the occupant emergency response plan (note that it may go by a different name, such as evacuation plan) for your campus or workplace. If you cannot locate one, use the Internet to locate one from another school or organization. If you completed Exercise 12.2, you may use the same plan.
What type of exercises would you recommend to test the occupant emergency response plan?
What type of training would you recommend in order to educate personnel regarding the occupant emergency response plan?
If you were auditing the occupant emergency response plan, what questions would you ask?
Exercise 12.4: Researching Alternative Processing Sites
A number of companies specialize in offering hot site solutions. Locate at least three companies that offer this service.
Create a matrix comparing and contrasting options, such as technical support, available bandwidth, traffic redirection, managed security, and data center features (for example, power and connectivity and geographic location).
Recommend one of the sites. Be prepared to explain your recommendation.
Exercise 12.5: Researching the Federal Emergency Management Agency
Describe the FEMA resources available online to businesses to help them prepare for disasters.
Describe the FEMA resources available online to families to help them prepare for disasters.
What is FEMA Corps?
Exercise 12.6: Researching Similar Agencies or Programs in Europe, Canada, and Any Other Countries
Describe and compare non-U.S. programs and resources available to help businesses prepare and react for disasters.
What are the similarities with FEMA?
Projects
Project 12.1: Assessing Disruptions in Business Continuity
Disruption in service at a financial institution impacts both its customers and internal operations.
Listed here are various disruptions in banking service. Assign each event a rating of 1–5 (1 is the lowest, 5 is the highest) that best represents the impact on you (as the customer), and provide an explanation of your rating. Consider each event independently.
ATM system unavailable, branches open.
Closest local branch closed, others open.
Internet banking unavailable, branches open.
Core processing system unavailable, deposits accepted, withdrawals less than $100, other account information unavailable.
Communications capabilities between branches disrupted, tellers work in offline mode.
Listed here are the same disruptions in banking service. Assign each event a rating of 1–5 (1 is the lowest, 5 is the highest) that best represents the impact on the bank from a financial, operational, legal, or regulatory perspective, and provide an explanation. Consider each event independently.
ATM system unavailable, branches open.
Closest local branch closed, others open.
Internet banking unavailable, branches open.
Core processing system unavailable, deposits accepted, withdrawals less than $100, other account information unavailable.
Communications capabilities between branches disrupted, tellers work in offline mode.
Describe how business continuity planners should reconcile the differences in impact upon a business and its customers.
Project 12.2: Evaluating Business Continuity Plans
The objective of this project is to evaluate your school or employer’s BCP. You will need to obtain a copy of your school or employer’s BCP (it may be known as a disaster response plan). If you cannot locate a copy, use the Internet to locate one from another school or organization.
Identify the sections related to preparation, response, contingency, recovery, resumption, testing, and maintenance. Is anything missing?
Identify roles and responsibilities referenced in the plan.
Critique the plan in terms of clarity and ease of use.
Project 12.3: Assessing the Impact of the Cloud on Business Continuity
Infrastructure as a Service (IaaS) and Platform as a Service (PaaS) are changing how organizations design their technology environments.
How do IaaS and PaaS impact business continuity planning?
Have any of the cloud service providers (such as Google, Amazon, Rackspace, Savvis) experienced any major outages that would impact their customers?
Assuming an organization used the services of a cloud provider for business continuity services, explain the type of response, recovery, and continuity testing they could/should conduct.
Case Study
The Role of Social Media in a Disaster
Hurricane Maria is considered one of the worst natural disasters on record in Puerto Rico. Social media helped reunite families, friends, organize donation campaigns, and much more.
Document how social media was used as an emergency communication tool during the aftermath of Hurricane Maria.
Make a recommendation as to whether businesses should use social media as a communications tool during a disaster situation. Be sure to include both pros and cons.
Would your answer be different if the assignment was to make a recommendation as to whether colleges and universities should adopt social media for communicating about a disaster? Why or why not?
References
Regulations Cited
“16 CFR Part 314: Standards for Safeguarding Customer Information; Final Rule, Federal Register,” accessed 06/2018, https://www.gpo.gov/fdsys/pkg/CFR-2016-title16-vol1/xml/CFR-2016-title16-vol1-part314.xml.
“HIPAA Security Rule,” official website of the Department of Health and Human Services, accessed 06/2018, https://www.hhs.gov/hipaa/for-professionals/security/index.html.
Executive Orders Cited
“Federal Continuity Directives (FCD) 1 and 2,” accessed 06/2018, https://www.fema.gov/guidance-directives.
“Presidential Decision Directive 63, Critical Infrastructure Protection,” official website of the Government Printing Office, accessed 06/2018, https://www.gpo.gov/fdsys/granule/FR-1998-08-05/98-20865.
“Presidential Directive HSPD-7, Critical Infrastructure Identification, Prioritization, and Protection,” official website of the Department of Homeland Security, accessed 06/2018, https://www.dhs.gov/homeland-security-presidential-directive-7.
Other References
Bell, Michael, “The Five Principles of Organizational Resilience,” Gartner Group, January 7, 2002, accessed 06/2018, https://www.gartner.com/id=351410.
“Hurricane Maria News, Graphics, and Social Media”, accessed 06/2018, https://www.fema.gov/disaster/updates/hurricane-maria-news-graphics-and-social-media.
“Puerto Ricans Organize on Social Media to Send Aid Back Home,” accessed 06/2018, www.nola.com/hurricane/index.ssf/2017/09/puerto_rico_help_new_orleans_m.html.
“Business Testimonials: Aeneas,” FEMA Ready, accessed 06/2018, https://www.ready.gov/business/business-testimonials.
“Emergency Preparedness,” official website of the SBA, accessed 06/2018, https://www.sba.gov/business-guide/manage/prepare-emergencies-disaster-assistance.
