Chapter 7
Physical and Environmental Security
Chapter Objectives
After reading this chapter and completing the exercises, you will be able to do the following:
Define the concept of physical security and how it relates to information security.
Evaluate the security requirements of facilities, offices, and equipment.
Understand the environmental risks posed to physical structures, areas within those structures, and equipment.
Enumerate the vulnerabilities related to reusing and disposing of equipment.
Recognize the risks posed by the loss or theft of mobile devices and media.
Develop policies designed to ensure the physical and environmental security of information, information systems, and information-processing and storage facilities.
In the beginning of the computer age, it was easy to protect the systems; they were locked away in a lab, weighed thousands of pounds, and only a select few were granted access. Today, computing devices are ubiquitous. We are tasked with protecting devices that range from massive cloud-based multiplex systems to tiny handheld devices. The explosion of both distributed and mobile computing means that computing devices can be located anywhere in the world and are subject to local law and custom. Possession requires that each individual user take responsibility for mobile device security.
Security professionals are often so focused on technical controls that they overlook the importance of physical controls. The simple reality is that physical access is the most direct path to malicious activity, including unauthorized access, theft, damage, and destruction. Protection mechanisms include controlling the physical security perimeter and physical entry, creating secure offices, rooms, and facilities, and implementing barriers to access, such as monitoring, and alerting. Section 11 of ISO 27002:2013 encompasses both physical and environmental security. Environmental security refers to the workplace environment, which includes the design and construction of the facilities, how and where people move, where equipment is stored, how the equipment is secured, and protection from natural and man-made disasters.
In previous chapters, you learned that to properly protect organizational information, we must first know where it is and how critical it is to the organization. Just as we shouldn’t spend as much money or resources to protect noncritical information as we would to protect critical information, so it goes that we shouldn’t spend the same amount to protect a broom closet as we should to protect information-processing facilities such as data centers, server rooms, or even offices containing client information.
Information security professionals rarely have the expertise to address this security domain on their own. It is critical to involve facilities and physical security personnel in strategic and tactical decisions, policies, and procedures. For example, the information security expert designs a server room with a double steel door, card-reading lock, and a camera outside the door. A facilities expert may question the construction of the walls, floor, vents, and ceilings, the capability of the HVAC and fire suppression systems, as well as the potential for a natural disaster, such as an earthquake, fire, or flood. A physical security expert may question the location, the topography, and even the traffic patterns of pedestrians, automobiles, and airplanes. Creating and maintaining physical and environmental security is a team effort.
In this chapter, we focus on design, obstacles, monitoring, and response as they relate to secure areas, equipment security, and environmental controls. We examine the security issues, related best practices, and of course, physical and environmental security policies.
FYI: ISO/IEC 27002:2013 and NIST Cybersecurity Framework
Section 11 of ISO 27002:2013 is dedicated to physical and environmental security, with the objective of maintaining a secure physical environment to prevent unauthorized access, damage, and interference to business premises. Special attention is paid to disposal and destruction.
The NIST Cybersecurity Framework addresses physical security in three areas:
Under the Protect Identity Management, Authentication and Access Control (PR.AC) Category stating that physical access to assets must be managed and protected
Under the Information Protection Processes and Procedures (PR.IP) Category stating that policy and regulations regarding the physical operating environment for organizational assets must be met
Under the Security Continuous Monitoring (DE.CM) Category stating that the physical environment needs to be monitored to detect potential cybersecurity events
Corresponding NIST guidance is provided in the following documents:
SP 800-12: “An Introduction to Computer Security—The NIST Handbook”
SP 800-14: “Generally Accepted Principles and Practices for Securing Information Technology Systems”
SP 800-88: “Guidelines for Media Sanitization”
SP 800-100: “Information Security Handbook: A Guide for Managers”
SP 800-116 Rev. 1: “A Recommendation for the Use of PIV Credentials in Physical Access Control Systems (PACS)”
SP 800-116: “A Recommendation for the Use of PIV Credentials in Physical Access Control Systems (PACS)”
SP 800-183: “Networks of ‘Things’”
Understanding the Secure Facility Layered Defense Model
The premise of a layered defense model is that if an intruder can bypass one layer of controls, the next layer of controls should provide additional deterrence or detection capabilities. Layered defense is both physical and psychological. The mere fact that an area appears to be secure is in itself a deterrent. Imagine the design of a medieval castle. The castle itself was built of stone. It was sited high on a hill within a walled property. There may have been a moat and an entry drawbridge. There were certainly lookouts and guards. For intruders to launch a successful attack, they had to overcome and penetrate each of these obstacles. The same concept is used in designing secure buildings and areas.
FYI: How Can You Ensure Physical Security of Assets When Your Data and Applications are in the Cloud?
Mature cloud providers such as Amazon Web Services (AWS) provide detailed explanations of their physical and operational security processes for the network and server infrastructure. These are the servers that will host your applications and data in the cloud that you do not have any control over. AWS details all their physical security practices at the following white paper:
https://d1.awsstatic.com/whitepapers/Security/AWS_Security_Whitepaper.pdf
The white paper details:
“AWS’s data centers are state of the art, utilizing innovative architectural and engineering approaches. Amazon has many years of experience in designing, constructing, and operating large-scale data centers. This experience has been applied to the AWS platform and infrastructure. AWS data centers are housed in nondescript facilities. Physical access is strictly controlled both at the perimeter and at building ingress points by professional security staff utilizing video surveillance, intrusion detection systems, and other electronic means.
Authorized staff must pass two-factor authentication a minimum of two times to access data center floors. All visitors and contractors are required to present identification and are signed in and continually escorted by authorized staff. AWS only provides data center access and information to employees and contractors who have a legitimate business need for such privileges. When an employee no longer has a business need for these privileges, his or her access is immediately revoked, even if they continue to be an employee of Amazon or Amazon Web Services. All physical access to data centers by AWS employees is logged and audited routinely.”
The paper describes their methodologies and capabilities for the following:
Fire detection and suppression systems to reduce risk of fire.
Data center electrical power systems are designed to be fully redundant and maintainable without impact to operations, 24 hours a day, and seven days a week. This includes the use of uninterruptible power supply (UPS) units to provide back-up power and the use of generators.
Climate and temperature control required to maintain a constant operating temperature for servers and other hardware.
Management and monitoring of electrical, mechanical, and life support systems and equipment so that any issues are immediately identified.
Storage device decommissioning when a storage device has reached the end of its useful life, to prevent customer data from being exposed to unauthorized individuals. AWS states that it follows the NIST SP 800-88 (“Guidelines for Media Sanitization”) as part of their decommissioning process.
How Do We Secure the Site?
Depending on the size of the organization, information-processing facilities can range from a closet with one server to an entire complex of buildings with several thousand or even hundreds of thousands of computers. In addressing site physical security, we need to think of the most obvious risks, such as theft and other malicious activity, but we also must consider accidental damage and destruction related to natural disasters.
Location
The design of a secure site starts with the location. Location-based threats that need to be evaluated include political stability, susceptibility to terrorism, the crime rate, adjacent buildings, roadways, flight paths, utility stability, and vulnerability to natural disasters. Historical and predictive data can be used to establish both criminal and natural disaster chronology for a geographic area. The outcome will influence the type of security measures that an organization should implement. Best practices dictate that critical information-processing facilities be inconspicuous and unremarkable. They should not have signage relating to their purpose, nor should their outward appearance hint at what may be inside.
FYI: Crime Prevention Through Environmental Design (CPTED)
CPTED (pronounced sep-ted) has as its basic premise that the proper design and effective use of the physical environment can lead to a reduction in the incidence and fear of crime. CPTED is a psychological and sociological method of looking at security based upon three constructs:
People protect territory they feel is their own, and people have a certain respect for the territory of others.
Intruders do not want to be seen.
Limiting access discourages intruders and/or marks them as intruders.
The International CPTED Association (ICA) is committed to creating safer environments and improving the quality of life through the use of CPTED principles and strategies. You can learn more about this design concept at www.cpted.net.
Perimeter Security
The three elements to security are obstacles that deter trivial attackers and delay serious ones, detection systems that make it more likely that the attack will be noticed, and a response capability to repel or catch attackers. Obstacles include physical elements such as berms, fences, gates, and bollards. Lighting is also a valuable deterrent. Entrances, exits, pathways, and parking lots should be illuminated. Fences should be at least eight feet in height, with a two-foot parameter of light used to illuminate along the top portion of the fence. The candlepower of the lighting must meet security standards. Detection systems include IP cameras, closed-circuit TV, alarms, motion sensors, and security guards. Response systems include locking gates and doors, on-site or remote security personnel notification, and direct communication with local, county, or state police.
In Practice
Physical Security Perimeter Policy
Synopsis: Securing the perimeter is the first line of defense against external physical attacks. Perimeter controls are required to prevent unauthorized access and damage to facilities.
Policy Statement:
The company will establish physical security perimeters around business premises.
An annual risk assessment of all existing business premises and information-processing facilities will be performed to determine the type and strength of the security perimeter that is appropriate and prudent.
A risk assessment must be conducted on all new sites under consideration prior to building plans being finalized.
The Office of Facilities Management in conjunction with the Office of Information Security will conduct the risk assessment.
Risk assessment results and recommendations are to be submitted to the Chief Operating Officer (COO).
The Office of Facilities Management is responsible for the implementation and maintenance of all physical security perimeter controls.
How Is Physical Access Controlled?
Our next area to consider is physical entry and exit controls. What does it take to get in and out? How is trouble detected and reported? Depending on the site and level of security required, a plethora of access controls are available, including cameras, security guards, mantraps, locks, barriers, metal detectors, biometric scanners, fire-resistant exterior walls that are solid and heavy, and unbreakable/shatterproof glass. The biggest challenge is authorized entry.
Authorizing Entry
How does a company identify authorized personnel, such as employees, contractors, vendors, and visitors? Of greatest concern are the fraudulent or forged credentials obtained through careful profiling or the carelessness of authenticated employees. One commonly used option is a badging system. Badges may also function as access cards. Visitors to secure areas should be credentialed and authorized. Tailgating is one of the most common physical security challenges of all time. In some cases, it might be done innocently by an authorized individual opening a door and holding it open for others, visitors without badges, or someone who looks to be an employee. A number of visitor management systems facilitate ID scanning and verification, photo storage, credentialing, check in and check out, notifications, and monitoring. Visitors should be required to wear some kind of identification that can be evaluated from a distance. For instance, we might choose to have three different colored badges for visitors, which tell our employees what level of supervision should be expected, even if they view the person from across a 100-foot room. If a blue badge denotes close supervision, and you see someone wearing a blue badge without any supervision, you would know immediately to report the visitor or perhaps activate a silent alarm without having to confront or even come within close proximity of the individual. You can install the most advanced security system in the industry, but your security measures will fail if your employees are not educated about the associated security risks. You need to create a secure building culture and good security awareness campaigns.
Background Checks
Your organization should also establish formal policies and procedures to delineate the minimum standards for logical and physical access to your premises and infrastructure hosts. Typically, enterprise organizations conduct criminal background checks, as permitted by law, as part of pre-employment screening practices for employees and matching with the employee’s position within the company and required level of access. The policies also identify functional responsibilities for the administration of physical access during working hours and after hours (including weekends and holidays).
In Practice
Physical Entry Controls Policy
Synopsis: Authorization and identification are required for entry to all nonpublic company locations.
Policy Statement:
Access to all nonpublic company locations will be restricted to authorized persons only.
The Office of Human Resources is responsible for providing access credentials to employees and contractors.
The Office of Facilities Management is responsible for visitor identification, providing access credentials, and monitoring access. All visitor management activities will be documented.
Employees and contractors are required to visibly display identification in all company locations.
Visitors are required to display identification in all nonpublic company locations.
Visitors are to be escorted at all times.
All personnel must be trained to immediately report unescorted visitors.
Securing Offices, Rooms, and Facilities
In addition to securing building access, the organization needs to secure the workspaces within the building. Workspaces should be classified based on the level of protection required. The classification system should address personnel security, information systems security, and document security. The security controls must take into consideration workplace violence, intentional crime, and environmental hazards.
Secure design controls for spaces within a building include (but are not limited to) the following:
Structural protection, such as full-height walls, fireproof ceilings, and restricted vent access
Alarmed solid, fireproof, lockable, and observable doors
Alarmed locking, unbreakable windows
Monitored and recorded entry controls (keypad, biometric, card swipe)
Monitored and recorded activity
In Practice
Workspace Classification
Synopsis: A classification system will be used to categorize workspaces. Classifications will be used to design and communicate baseline security controls.
Policy Statement:
The company will use a four-tiered workspace classification schema consisting of secure, restricted, nonpublic, and public.
The company will publish definitions for each classification.
The criteria for each level will be maintained by and available from the Office of Facilities Management.
All locations will be associated with one of the four data classifications. Classification assignment is the joint responsibility of the Office of Facilities Management and the Office of Information Security.
Each classification must have documented security requirements.
The COO must authorize exceptions.
Working in Secure Areas
It is not enough to just physically secure an area. Close attention must be paid to who is allowed to access the area and what they are allowed to do. Access control lists should be reviewed frequently. If the area is continually monitored, there should be guidelines specifying what is considered “suspicious” activity. If the area is videoed and not continually monitored, then there should be documented procedures regarding how often and by whom the video should be reviewed. Depending on the circumstances, it may be prudent to restrict cameras or recording devices, including smartphones, tablets, and USB drives, from being taken into the area.
In Practice
Working in Secure Areas Policy
Synopsis: Areas classified as “secure” will be continually monitored. Use of recording devices will be forbidden.
Policy Statement:
All access to areas classified as “secure” will be continually monitored.
All work in areas classified as “secure” will be recorded. The recordings will be maintained for a period of 36 months.
Mobile data storage devices are prohibited and may not be allowed in areas classified as “secure” without the authorization of the system owner or Information Security Officer (ISO).
Audio- and video-recording equipment is prohibited and may not be allowed in areas classified as “secure” without the authorization of the system owner or the Office of Information Security.
This policy is in addition to workspace classification security protocols.
Ensuring Clear Desks and Clear Screens
Documents containing protected and confidential information are subject to intentional or accidental unauthorized disclosure unless secured from viewing by unauthorized personnel when not in use. The same holds true for computer screens. Companies have a responsibility to protect physical and digital information both during the workday and during nonbusiness hours. All too often, organizations make it easy for unauthorized users to view information. Unauthorized access can be the result of viewing a document left unattended or in plain sight, removing (or reprinting) a document from a printer, copier, or fax machine, stealing digital media, such as a DVD or USB drive, and even shoulder surfing, which is the act of looking over someone’s shoulder to see what is displayed on a monitor or device.
Protected or confidential documents should never be viewable by unauthorized personnel. When not in use, documents should be locked in file rooms, cabinets, or desk drawers. Copiers, scanners, and fax machines should be located in nonpublic areas and require use codes. Printers should be assigned to users with similar access rights and permissions and located close to the designated users. Users should be trained to retrieve printed documents immediately. Monitors and device screens should be situated to ensure privacy. Password-protected screen savers should be set to engage automatically. Users should be trained to lock their screens when leaving devices unattended. Physical security expectations and requirements should be included in organizational acceptable use agreements.
In Practice
Clear Desk and Clear Screen Policy
Synopsis: User controls are required to prevent the unauthorized viewing or taking of information.
Policy Statement:
When left unattended during business hours, desks shall be clear of all documents classified as “protected” or “confidential.”
During nonbusiness hours, all documents classified as “protected” or “confidential” will be stored in a secure location.
While in use, device displays of any type must be situated to not allow unauthorized viewing.
When left unattended during business hours, device displays should be cleared and locked to prevent viewing.
Protected and confidential documents should be printed only to assigned printers. Print jobs should be retrieved immediately.
Scanners, copiers, and fax machines must be locked when not in use and require user codes to operate.
Protecting Equipment
Now that we have defined how facilities and work areas will be secured, we must address the security of the equipment within these facilities. Traditionally, protection controls were limited to company-owned equipment. This is no longer the case. Increasingly, organizations are encouraging employees and contractors to “bring your own device” to work (referred to as BYOD). These devices may store, process, or transmit company information. In developing policies, we need to consider how best to protect both company- and employee-owned equipment from unauthorized access, theft, damage, and destruction.
No Power, No Processing?
No power, no processing—it’s that simple. Long before computers took over the business world, organizations have been taking steps to ensure that power is available. Of course, it is now more important than ever. All information systems rely on clean, consistent, and abundant supplies of electrical power. Even portable devices that run on battery power require electricity for replenishment. Power is not free. Quite the contrary: Power can be very expensive, and excessive use has an environmental and geopolitical impact.
Power Protection
To function properly, our systems need consistent power delivered at the correct voltage level. Systems need to be protected from power loss, power degradation, and even from too much power, all of which can damage equipment. Common causes of voltage variation include lightning; damage to overhead lines from storms, trees, birds, or animals; vehicles striking poles or equipment; and load changes or equipment failure on the network. Heat waves can also contribute to power interruptions because the demand in electricity (that is, air conditioners) can sometimes exceed supply. The variation may be minor or significant.
Power fluctuations are categorized by changes in voltage and power loss. Figure 7-1 shows the difference between a power surge and a power spike.
FIGURE 7-1 Power Surge vs. Power Spike
Figure 7-2 shows the difference between a brownouts and a sag.
FIGURE 7-2 Brownout vs. Sag
Figure 7-3 shows the difference between a blackout and a fault.
FIGURE 7-3 Blackout vs. Fault
Companies can install protective devices to help guard their premises and assets, such as installing surge protection equipment, line filters, isolation transformers, voltage regulators, power conditioners, uninterruptible power supplies (UPSs), and back-up power supplies or generators. These power protection devices can condition the feed for consistency, provide continuous power for critical systems, and manage a controlled shutdown in the event of total loss of power.
In Practice
Power Consumption Policy
Synopsis: Power conditioning and redundancy protections must be in place to maintain the availability and performance of information systems and infrastructure. Power consumption should be minimized.
Policy Statement:
The company is committed to sustainable computing and the minimization of power consumption.
All computing devices purchased must be Energy Star (or equivalent)–certified.
All computing devices must be configured in power saver mode unless the setting degrades performance.
A biannual assessment must be conducted by the Office of Facilities Management to determine the best method(s) to provide clean, reliable data center power.
Data center equipment must be protected from damage caused by power fluctuations or interruptions.
Data center power protection devices must be tested on a scheduled basis for functionality and load capacity. A log must be kept of all service and routine maintenance.
Data center generators must be tested regularly according to manufacturer’s instructions. A log must be kept of all service and routine maintenance.
How Dangerous Is Fire?
Imagine the impact of a data center fire—equipment and data irrevocably destroyed, internal communications damaged, and external connectivity severed. On November 2017, Data Center Dynamics reported that a faulty battery in a UPS caused a fire in a health center in Cairns, Australia, causing two hospitals and several of the city’s health service systems to fail.
Fire protection is composed of the three elements shown in Figure 7-4.
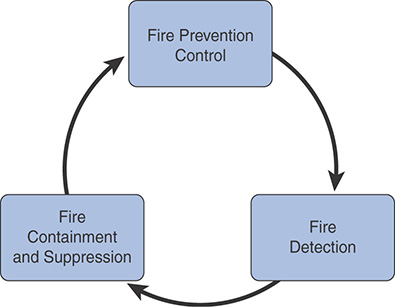
FIGURE 7-4 Fire Protection Elements
Active and passive fire prevention controls are the first line of defense. Fire prevention controls include hazard assessments and inspections, adhering to building and construction codes, using flame-retardant materials, and proper handling and storage procedures for flammable/combustible materials. Fire detection is recognizing that there is a fire. Fire detection devices can be smoke activated, heat activated, or flame activated. Fire containment and suppression involve actually responding to the fire. Containment and suppression equipment is specific to fire classification. Data center environments are typically at risk of Class A, B, or C fires:
Class A: Fire with combustible materials as its fuel source, such as wood, cloth, paper, rubber, and many plastics
Class B: Fire in flammable liquids, oils, greases, tars, oil-based paints, lacquers, and flammable gases
Class C: Fire that involves electrical equipment
Class D: Combustibles that involve metals
Facilities must comply with standards to test fire-extinguishing methods annually to validate full functionality.
The best-case scenario is that data centers and other critical locations are protected by an automatic fire-fighting system that spans multiple classes. Like all other major investments, it’s prudent to do a cost/benefit analysis before making a decision. In any emergency situation, human life always takes precedence. All personnel should know how to quickly and safely evacuate an area.
In Practice
Data Center and Communications Facilities Environmental Safeguards Policy
Synopsis: Data center and communications facilities must have controls designed to minimize the impact of power fluctuations, temperature, humidity, and fire.
Policy Statement:
Smoking, eating, and drinking are not permitted in data center and communications facilities.
Servers and communications equipment must be located in areas free from physical danger.
Servers and communications must be protected by uninterruptable power supplies and back-up power sources.
Appropriate fire detection, suppression, and fighting equipment must be installed and/or available in all data center and communications facilities.
Appropriate climate control systems must be installed in all data center and communications facilities.
Emergency lighting must engage automatically during power outages at all data center and communications facilities.
The Office of Facilities Management is responsible for assessing the data center and communications facilities environmental requirements and providing the recommendations to the COO.
The Office of Facilities Management is responsible for managing and maintaining the data center and communications facilities’ climate-control, fire, and power systems.
What About Disposal?
What do servers, workstations, laptops, tablets, smartphones, firewalls, routers, copiers, scanners, printers, memory cards, cameras, and flash drives have in common? They all store data that should be permanently removed before handing down, recycling, or discarding.
The data can be apparent, hidden, temporary, cached, browser-based, or metadata:
Apparent data files are files that authorized users can view and access.
Hidden files are files that the operating system by design does not display.
Temporary files are created to hold information temporarily while a file is being created.
A web cache is the temporary storage of web documents, such as HTML pages, images, and downloads.
A data cache is the temporary storage of data that has recently been read and, in some cases, adjacent data areas that are likely to be accessed next.
Browser-based data includes the following items:
Browsing history, which is the list of sites visited
Download history, which is the list of files downloaded
Form history, which includes the items entered into web page forms
Search bar history, which includes items entered into the search engines
Cookies, which store information about websites visited, such as site preferences and login status
Metadata is details about a file that describes or identifies it, such as title, author name, subject, and keywords that identify the document’s topic or contents.
Removing Data from Drives
A common misconception is that deleting a file will permanently remove its data. Deleting (or trashing) a file removes the operating system pointer to the file. Formatting a disk erases the operating system address tables. In both cases, the files still reside on the hard drive, and system recovery software can be used to restore the data. To give you an idea of how easy it is to recover information from a formatted hard drive, simply Google the phrase “data recovery” and see what comes back to you. Utilities are available for less than $50 that are quite capable of recovering data from formatted drives. Even if a drive has been formatted and a new operating system installed, the data is recoverable.
NIST Special Publication 800-88 Revision 1 defines data destruction as “the result of actions taken to ensure that media cannot be reused as originally intended and that information is virtually impossible to recover or prohibitively expensive.” There are two methods of permanently removing data from a drive—disk wiping (also known as scrubbing) and degaussing. The disk wiping process will overwrite the master boot record (MBR), partition table, and every sector of the hard drive with the numerals 0 and 1 several times. Then the drive is formatted. The more times the disk is overwritten and formatted, the more secure the disk wipe is. The government medium security standard (DoD 5220.22-M) specifies three iterations to completely overwrite a hard drive six times. Each iteration makes two write passes over the entire drive; the first pass inscribes ones (1) over the drive surface and the second inscribes zeros (0) onto the surface. After the third iteration, a government-designated code of 246 is written across the drive, and then it is verified by a final pass that uses a read-verify process. There are several commercially available applications that follow this standard. Disk wiping does not work reliably on solid-state drives, USB thumb drives, compact flash, and MMC/SD cards.
Degaussing is the process wherein a magnetic object, such as a computer tape, hard disk drive, or CRT monitor, is exposed to a magnetic field of greater, fluctuating intensity. As applied to magnetic media, such as video, audio, computer tape, or hard drives, the movement of magnetic media through the degaussing field realigns the particles, resetting the magnetic field of the media to a near-zero state, in effect erasing all the data previously written to the tape or hard drive. In many instances, degaussing resets the media to a like-new state so that it can be reused and recycled. In some instances, this simply wipes the media in preparation for safe and secure disposal. The National Security Agency (NSA) approves powerful degaussers that meet their specific standards and that in many cases utilize the latest technology for top-secret erasure levels.
Cryptographic Erase is a technique that uses the encryption of target data by enabling sanitization of the target data’s encryption key. This is done to leave only the cipher text on the media and preventing read-access, because no one should have the encryption key. It is common for storage manufacturers to include integrated encryption and access control capabilities, also known as self-encrypting drives (SEDs). SEDs feature always-on encryption that ensures that all data in the storage device is encrypted. In practice, cryptographic erase can be executed in a fraction of a second. This is a great benefit because nowadays other sanitization methods take more time in large storage devices. Cryptographic erase can also be used in addition to other data destruction methods. You should not use cryptographic erase to sanitize data if the encryption was enabled after sensitive data was stored on the device without having been sanitized first. In addition, you should not use cryptographic erase if you are not certain if sensitive data was stored on the device without being sanitized prior to encryption.
Destroying Materials
The objective of physical destruction is to render the device and/or the media unreadable and unusable. Devices and media can be crushed, shredded, or, in the case of hard drives, drilled in several locations perpendicular to the platters and penetrating clear through from top to bottom.
Cross-cut shredding technology, which reduces material to fine, confetti-like pieces, can be used on all media, ranging from paper to hard drives.
It is common for organizations to outsource the destruction process. Companies that offer destruction services often have specialized equipment and are cognizant of environmental and regulatory requirements. The downside is that the organization is transferring responsibility for protecting information. The media may be transported to off-site locations. The data is being handled by non-employees over whom the originating organization has no control. Selecting a destruction service is serious business, and thorough due diligence is in order.
Both in-house and outsourced destruction procedures should require that an unbroken predestruction chain of custody be maintained and documented and that an itemized post-destruction certificate of destruction be issued that serves as evidence of destruction in the event of a privacy violation, complaint, or audit. NIST Special Publication 800-88 Revision 1 mentions that destructive techniques also render a “device purged when effectively applied to the appropriate media type, including incineration, shredding, disintegrating, degaussing, and pulverizing.”
In Practice
Secure Disposal Policy
Synopsis: All media must be disposed of in a secure and environmentally sound manner.
Policy Statement:
The Office of Facilities Management and the Office of Information Security are jointly responsible for determining the disposal standards for each classification of information.
Devices or media containing “protected” or “confidential” information must not be sent off-site for repair and/or maintenance.
The standards for the highest classification must be adhered to when the device or media contains multiple types of data.
A chain of custody must be maintained for the destruction of “protected” and “confidential” information.
A certificate of destruction is required for third-party destruction of devices or media that contains “protected” and “confidential” information.
Disposal of media and equipment will be done in accordance with all applicable state and federal environmental disposal laws and regulations.
Stop, Thief!
According to the Federal Bureau of Investigation (FBI), on average, a laptop is stolen every 53 seconds, and one in ten individuals will have their laptop stolen at some point. The recovery statistics of stolen laptops is even worse, with only 3% ever being recovered. This means 97% of laptops stolen will never be returned to their rightful owners. The Ponemon Institute has conducted several studies and reported that almost half of laptops were lost or stolen off-site (working from a home office or hotel room) and one third were lost or stolen in travel or transit. The statistics for mobile phones and tablets is even worse.
The cost of lost and stolen devices is significant. The most obvious loss is the device itself. The cost of the device pales in comparison to the cost of detection, investigation, notification, after-the-fact response, and economic impact of lost customer trust and confidence, especially if the device contained legally protected information. The Ponemon Institute “2017 Cost of Data Breach Study: Global Overview” (https://www-01.ibm.com/common/ssi/cgi-bin/ssialias?htmlfid=SEL03130WWEN) calculated the average business cost of a breach in the United States to be $141 per record across all industries.
Consider this scenario: A laptop valued at $1,500 is stolen. A file on the laptop has information about 2,000 individuals. Using the Ponemon conclusion of $141 per record, the cost of the compromise would be $282,000! That cost doesn’t include potential litigation or fines.
Additional examples of things that are attractive to thieves are modern portable media theft, such as thumb or pen drives and SD cards. This is why it is important that you have a good asset inventory. In Chapter 5, “Asset Management and Data Loss Prevention,” you learned that asset management is crucial. In addition, you learned that every information asset must be assigned an owner. The success of an information security program is directly related to the defined relationship between the data owner and the information. In the best-case scenario, the data owner also functions as a security champion enthusiastically embracing the goals of confidentiality, integrity, and availability (CIA).
You should also have an established and effective process for individuals to report lost or stolen devices. Additionally, you should have mitigations in place in case of theft. These mitigations include encryption and remote wipe capabilities for mobile devices. Typically, remote wipe is a function of a mobile device management (MDM) application.
In Practice
Mobile Device and Media Security
Synopsis: Safeguards must be implemented to protect information stored on mobile devices and media.
Policy Statement:
All company-owned and employee-owned mobile devices and media that store or have the potential to store information classified as “protected” or “confidential” must be encrypted.
Whenever feasible, an antitheft technology solution must be deployed that enables remote locate, remote lock, and remote delete/wipe functionality.
Loss or theft of a mobile device or media must be reported immediately to the Office of Information Security.
FYI: Small Business Note
Two physical security issues are specific to small business and/or remote offices: location and person identification. A majority of small business and remote offices are located in multitenant buildings, where occupants do not have input into or control of perimeter security measures. In this case, the organization must treat their entry doors as the perimeter and install commensurate detective and preventative controls. Often, tenants are required to provide access mechanisms (for example, keys, codes) to building personnel, such as maintenance and security. Unique entry codes should be assigned to third-party personnel so that entry can be audited. Rarely are employee identification badges used in a small office. This makes it all the more important that visitors be clearly identified. Because there is little distinction between public and private spaces, visitors should be escorted whenever they need to go on the premises.
Summary
The objective of physical and environmental security is to prevent unauthorized access, damage, and interference to business premises and equipment. In this chapter, with a focus on the physical environment, we discussed the three elements to security—obstacles that deter trivial attackers and delay serious ones, detection systems that make it more likely that the attack will be noticed, and a response capability to repel or catch attackers. We began at the security perimeter, worked our way gradually inward to the data center, and then back out to mobile devices. Starting at the perimeter, we saw the importance of having a layered defense model as well as incorporating CPTED (crime prevention through environmental design) concepts. Moving inside the building, we looked at entry controls and the challenge of authorized access and identification. We acknowledged that not all access is equal. Workspaces and areas need to be classified so that levels of access can be determined and appropriate controls implemented. Equipment needs to be protected from damage, including natural disasters, voltage variations (such as surges, brownouts, and blackouts), fire, and theft. Purchasing Energy Star–certified equipment and proactively reducing energy consumption supports the long-term security principle of availability.
We explored the often-overlooked risks of device and media disposal and how important it is to permanently remove data before handing down, recycling, or discarding devices. Even the most innocuous devices or media may contain business or personal data in metadata, hidden or temporary files, web or data caches, or the browser history. Deleting files or formatting drives is not sufficient. DoD-approved disk-wiping software or a degaussing process can be used to permanently remove data. The most secure method of disposal is destruction, which renders the device and/or the media unreadable and unusable.
Mobile devices that store, process, or transmit company data are the newest challenge to physical security. These devices travel the world and in some cases are not even company-owned. Threats run the gamut from nosy friends and colleagues to targeted theft. The detection, investigation, notification, and after-the-fact response cost of a lost or stolen mobile device is astronomical. The economic impact of lost customer trust and confidence is long-lasting. Encryption and antitheft technology solutions that enable remote locate, remote lock, and remote delete/wipe functionality must be added to the protection arsenal.
Physical and environmental security policies include perimeter security, entry controls, workspace classification, working in secure areas, clean desk and clean screen, power consumption, data center and communications facilities environmental safeguards, secure disposal, and mobile device and media security.
Test Your Skills
Multiple Choice Questions
1. Which of the following groups should be assigned responsibility for physical and environmental security?
A. Facilities management
B. Information security management
C. Building security
D. A team of experts including facilities, information security, and building security
2. Physical and environmental security control decisions should be driven by a(n) ___________.
A. educated guess
B. industry survey
C. risk assessment
D. risk management
3. Which of the following terms best describes CPTED?
A. Crime prevention through environmental design
B. Crime prevention through environmental designation
C. Criminal prevention through energy distribution
D. Criminal prosecution through environmental design
4. The design of a secure site starts with the _________.
A. natural surveillance
B. territorial reinforcement
C. natural access control
D. location
5. Which of the following models is known as the construct that if an intruder can bypass one layer of controls, the next layer of controls should provide additional deterrence or detection capabilities?
A. Layered defense model
B. Perimeter defense model
C. Physical defense model
D. Security defense model
6. The mere fact that an area appears to be secure is in itself a ___________.
A. deterrent
B. layer
C. defense
D. signature
7. Best practices dictate that data centers should be _____________.
A. well marked
B. located in urban areas
C. inconspicuous and unremarkable
D. built on one level
8. Which of the following would be considered a “detection” control?
A. Lighting
B. Berms
C. Motion sensors
D. Bollards
9. Badging or an equivalent system at a secure facility should be used to identify ____________.
A. everyone who enters the building
B. employees
C. vendors
D. visitors
10. Which of the following statements best describes the concept of shoulder surfing?
A. Shoulder surfing is the use of a keylogger to capture data entry.
B. Shoulder surfing is the act of looking over someone’s shoulder to see what is on a computer screen.
C. Shoulder surfing is the act of positioning one’s shoulders to prevent fatigue.
D. None of the above.
11. The term BYOD is used to refer to devices owned by ____________.
A. the company
B. a vendor
C. the employee
D. a contractor
12. Which of the following statements is not true about data center best practices?
A. Data center equipment must be protected from damage caused by power fluctuations or interruptions.
B. Data center power protection devices must be tested on a scheduled basis for functionality and load capacity.
C. Data center generators must be tested regularly according to manufacturer’s instructions.
D. You can optionally log all service and routine maintenance.
13. Which of the following terms best describes a prolonged increase in voltage?
A. Power spike
B. Power surge
C. Power hit
D. Power fault
14. Common causes of voltage variations include ______________.
A. lightning, storm damage, and electric demand
B. using a power conditioner
C. turning on and off computers
D. using an uninterruptable power supply
15. Adhering to building and construction codes, using flame-retardant materials, and properly grounding equipment are examples of which of the following controls?
A. Fire detection controls
B. Fire containment controls
C. Fire prevention controls
D. Fire suppression controls
16. A Class C fire indicates the presence of which of the following items?
A. Electrical equipment
B. Flammable liquids
C. Combustible materials
D. Fire extinguishers
17. Confidential data can reside on which of the following items?
A. Smartphones
B. Cameras
C. Scanners
D. All of the above
18. Which of the following data types includes details about a file or document?
A. Apparent data
B. Hidden data
C. Metadata
D. Cache data
19. URL history, search history, form history, and download history are stored by the device ___________.
A. operating system
B. browser
C. BIOS
D. ROMMON
20. Which of the following statements about formatting a drive is not true?
A. Formatting a drive creates a bootable partition.
B. Formatting a drive overwrites data.
C. Formatting a drive fixes bad sectors.
D. Formatting a drive permanently deletes files.
Exercises
Exercise 7.1: Researching Data Destruction Services
Research companies in your area that offer data destruction services.
Document the services they offer.
Make a list of questions you would ask them if you were tasked with selecting a vendor for data destruction services.
Exercise 7.2: Assessing Data Center Visibility
Locate the data center at your school or workplace.
Is the facility or area marked with signage? How easy was it to find? What controls are in place to prevent unauthorized access? Document your findings.
Exercise 7.3: Reviewing Fire Containment
Find at least three on-campus fire extinguishers (do not touch them). Document their location, what class fire they can be used for, and when they were last inspected.
Find at least one fire extinguisher (do not touch it) in your dorm, off-campus apartment, or home. Document the location, what class fire it can be used for, and when it was last inspected.
Exercise 7.4: Assessing Identification Types
Document what type of identification is issued to students, faculty, staff, and visitors at your school. If possible, include pictures of these types of documentation.
Describe the process for obtaining student identification.
Describe the procedure for reporting lost or stolen identification.
Exercise 7.5: Finding Data
Access a public computer in either the library, a computer lab, or a classroom.
Find examples of files or data that other users have left behind. The files can be apparent, temporary, browser based, cached, or document metadata. Document your findings.
What should you do if you discover “personal” information?
Projects
Project 7.1: Assessing Physical and Environmental Security
You are going to conduct a physical assessment of a computing device you own. This could be a desktop computer, a laptop, a tablet, or a smartphone. Use the following table as a template to document your findings. You can add additional fields.
Device Description
Laptop Computer
Safeguard
Threats/Danger
Impact
Safeguard 1
Safeguard 2
Safeguard 3
Assessment
Recommendation
Initial Cost
Annual Cost
Cost/Benefit Analysis
Lost or forgotten
Need laptop for schoolwork
Pink case
Labeled with owner’s contact info
Inadequate
Install remote find software
$20.00
$20.00
$20 per year vs. the cost of replacing the laptop
Determine the physical and environmental dangers (threats); for example, losing or forgetting your laptop at school. Document your findings.
For each danger (threat), identify the controls that you have implemented; for example, your case is pink (recognizable) and the case and laptop are labeled with your contact information. It is expected that not all threats will have corresponding safeguards. Document your findings.
For threats that do not have a corresponding safeguard or ones for which you feel the current safeguards are inadequate, research the options you have for mitigating the danger. Based on your research, make recommendations. Your recommendation should include initial and ongoing costs. Compare the costs of the safeguard to the cost impact of the danger. Document your findings.
Project 7.2: Assessing Data Center Design
You have been tasked with recommending environmental and physical controls for a new data center to be built at your school. You are expected to present a report to the Chief Information Officer. The first part of your report should be a synopsis of the importance of data center physical and environmental security.
The second part of your report should address three areas: location, perimeter security, and power.
Location recommendations should include where the data center should be built and a description of the security of the surrounding area (for example, location-based threats include political stability, susceptibility to terrorism, the crime rate, adjacent buildings, roadways, pedestrian traffic, flight paths, utility stability, and vulnerability to natural disasters).
Access control recommendations should address who will be allowed in the building and how they will be identified and monitored.
Power recommendations should take into account power consumption as well as normal and emergency operating conditions.
Project 7.3: Securing the Perimeter
The security perimeter is a barrier of protection from theft, malicious activity, accidental damage, and natural disaster. Almost all buildings have multiple perimeter controls. We have become so accustomed to perimeter controls that they often go unnoticed (that is, security guards). Begin this project with developing a comprehensive list of perimeter controls.
Conduct a site survey by walking around your city or town. You are looking for perimeter controls. Include in your survey results the address of the building, a summary of building occupants, type(s) of perimeter controls, and your opinion as to the effectiveness of the controls. To make your survey valid, you must include at least 10 properties.
Choose one property to focus on. Taking into consideration the location, the depth of security required by the occupants, and the geography, comment in detail on the perimeter controls. Based on your analysis, recommend additional physical controls to enhance perimeter security.
Case Study
Physical Access Social Engineering
In your role of ISO at Anywhere USA University Teaching Hospital, you commissioned an independent security consultancy to test the hospital’s physical security controls using social engineering impersonation techniques. At the end of the first day of testing, the tester submitted a preliminary report.
Physical Access to Facilities
Dressed in blue scrubs, wearing a stethoscope, and carrying a clipboard, the tester was able to access the lab, the operating room, and the maternity ward. In one case, another staff member buzzed him in. In the two other cases, the tester walked in with other people.
Physical Access to the Network
Dressed in a suit, the tester was able to walk into a conference room and plug his laptop into a live data jack. Once connected, he was able to access the hospital’s network.
Physical Access to a Computer
Wearing a polo shirt with a company name, the tester was able to sit down at an unoccupied office cubicle and remove a hard disk from a workstation. When questioned, he answered that he had been hired by John Smith, IT Manager, to repair the computer.
Physical Access to Patient Files
Wearing a lab coat, the tester was able to walk up to a printer in the nursing station and remove recently printed documents.
Based on these findings, you request that the consultancy suspend the testing. Your immediate response is to call a meeting to review the preliminary report.
Determine who should be invited to the meeting.
Compose a meeting invitation explaining the objective of the meeting.
Prepare an agenda for the meeting.
Identify what you see as the most immediate issues to be remediated.
References
Regulations Cited
DoD 5220.22-M: National Industrial Security Program Operating Manual, February 28, 2006, revised March 28, 2013.
Other References
“About Energy Star,” Energy Star, accessed 04/2018, https://www.energystar.gov.
Amazon Web Services Physical Security Whitepaper, accessed 04/2018, https://d1.awsstatic.com/whitepapers/Security/AWS_Security_Whitepaper.pdf.
The Ponemon Institute, “2017 Cost of Data Breach Study: Global Overview,” accessed 04/2018, https://www-01.ibm.com/common/ssi/cgi-bin/ssialias?htmlfid=SEL03130WWEN.
Destruct Data, “Department of Defense (DoD) Media Sanitization Guidelines 5220.22M,” accessed 04/2018, http://www.destructdata.com/dod-standard/.
Bray, Megan, “Review of Computer Energy Consumption and Potential Savings,” December 2006, accessed 04/2018, www.dssw.co.uk/research/computer_energy_consumption.html.
“Efficiency: How We Do It,” Google, accessed 04/2018, https://www.google.com/about/datacenters/efficiency/internal/index.html#temperature.
“Facilities Services Sustainable Computing Guide,” Cornell University, accessed 04/2018, http://www.ictliteracy.info/rf.pdf/FSSustainableComputingGuide.pdf.
“Foundations Recovery Network Notifying Patients After a Laptop with PHI Was Stolen from an Employee’s Car,” PHIprivacy.net, June 24, 2013, accessed 04/2018, https://www.databreaches.net/foundations-recovery-network-notifying-patients-after-a-laptop-with-phi-was-stolen-from-an-employees-car/.
“Google Data Centers,” Google.com, accessed 04/2018, https://www.google.com/about/datacenters.
Jeffery, C. Ray. 1977. Crime Prevention Through Environmental Design, Second Edition, Beverly Hills: Sage Publications.
“Your Guide To Degaussers,” Degausser.com, accessed 04/2018, http://degausser.com/.
“Data Center Battery Incident Causes Fire in Australian Hospital,” Data Center Dynamics, accessed 04/2018, http://www.datacenterdynamics.com/content-tracks/security-risk/data-center-battery-incident-causes-fire-in-australian-hospital/99357.fullarticle.
