Chapter 13
Regulatory Compliance for Financial Institutions
Chapter Objectives
After reading this chapter and completing the exercises, you will be able to do the following:
Understand different financial institution cybersecurity regulatory compliance requirements.
Understand the components of a GLBA-compliant information security program.
Examine other financial services regulations, such as the New York Department of Financial Services (DFS) Cybersecurity Regulation.
Prepare for a regulatory examination.
Understand data privacy and new trends in international regulatory compliance.
Financial services institutions such as banks, credit unions, and lending institutions provide an array of solutions and financial instruments. You might think that money is their most valuable asset. On the other hand, the reality is that customer and transactional information is the heart of their business. Financial assets are material and can be replaced. Protection of customer information is necessary to establish and maintain trust between the financial institution and the community it serves. More specifically, institutions have a responsibility to safeguard the privacy of individual consumers and protect them from harm, including fraud and identity theft. On a broader scale, the industry is responsible for maintaining the nation’s financial services critical infrastructure.
This chapter examines different examples of regulations applicable to the financial sector, focusing on the following topics:
Title 5 Section 501(b) of the Gramm-Leach-Bliley Act (GLBA) and the corresponding interagency guidelines
Federal Financial Institutions Examination Council (FFIEC)
Federal Trade Commission (FTC) Safeguards Act, and Financial Institution Letters (FILs).
New York’s Department of Financial Services Cybersecurity Regulation (23 NYCRR Part 500)
Compliance with regulations such as the NYCRR and GLBA is mandatory. Noncompliance has significant penalties, including being forced to cease operations. As we examine the various regulations, we will look at how examiners assess compliance. We will conclude the chapter with a look at the most significant financial security issue of our time—personal and corporate identity theft—and the regulations that address this ever-growing problem.
The Gramm-Leach-Bliley Act
In a response to the massive bank failures of the Great Depression, the Banking Act of 1933 prohibited national and state banks from affiliating with securities companies. The specific provision is often referred to as the Glass-Steagall Act. Similar to the Glass-Steagall Act, the Bank Holding Company Act of 1956 prohibited banks from controlling a nonbank company. This act was amended by Congress in 1982 to further forbid banks from conducting general insurance underwriting or agency activities.
On November 11, 1999, the Glass-Steagall Act was repealed and the Gramm-Leach-Bliley Act (GLBA) was signed into law by President Bill Clinton. Also known as the Financial Modernization Act of 1999, GLBA effectively repealed the restrictions placed on banks during the six preceding decades, which prevented the merger of banks, stock brokerage companies, and insurance companies.
What Is a Financial Institution?
GLBA defines a financial institution as “Any institution the business of which is significantly engaged in financial activities as described in Section 4(k) of the Bank Holding Company Act (12 U.S.C. § 1843(k).” GLBA applies to all financial services organizations, regardless of size. This definition is important to understand, because these financial institutions include many companies that are not traditionally considered to be financial institutions, such as the following:
Check cashing businesses
Payday lenders
Mortgage brokers
Nonbank lenders (automobile dealers providing financial services)
Technology vendors providing loans to their clients
Educational institutions providing financial aid
Debt collectors
Real-estate settlement service providers
Personal property or real-estate appraisers
Retailers that issue branded credit cards
Professional tax preparers
Courier services
The law also applies to companies that receive information about customers of other financial institutions, including credit reporting agencies and ATM operators.
The Federal Trade Commission (FTC) is responsible for enforcing GLBA as it pertains to financial firms that are not covered by federal banking agencies, the SEC, the Commodity Futures Trading Commission, and state insurance authorities, which include tax preparers, debt collectors, loan brokers, real estate appraisers, and nonbank mortgage lenders.
Prior to GLBA, the insurance company that maintained health records was by law unrelated to the bank that financed mortgages and the brokerage house that traded stocks. Once merged, however, companies would have access to a cross-section of personal information. Using data-mining techniques, it is possible to build detailed customer and prospect profiles. Because of the potential for misuse of information, Title 5 of GLBA specifically addresses protecting both the privacy and the security of nonpublic personal information (NPPI).
GLBA’s information protection directive is composed of the three main components shown in Figure 13-1.

FIGURE 13-1 GLBA’s Information Protection Directive Components
The following are the components illustrated in Figure 13-1:
The Privacy Rule limits a financial institution’s disclosure of nonpublic personal information (NPPI) to unaffiliated third parties, such as by selling the information to unaffiliated third parties. Subject to certain exceptions, the Privacy Rule prohibits disclosure of a consumer’s NPPI to a nonaffiliated third party unless certain notice requirements are met and the consumer does not elect to prevent, or opt out of, the disclosure. The Privacy Rule requires that privacy notices provided to customers and consumers describe the financial institution’s policies and practices to protect the confidentiality and security of that information. It does not impose any other obligations with respect to safeguarding customers or their information.
The Safeguards Rule addresses the protection of the confidentiality and security of customer NPPI and ensuring the proper disposal of customer NPPI. It is directed toward preventing or responding to foreseeable threats to, or unauthorized access or use of, that information.
Pretexting is also referred to as social engineering. It is a methodology by which an individual impersonates someone else to extract sensitive information from unsuspecting victims. GLBA encourages organizations to implement robust employee training programs to combat social engineering. One of the main entry points to cybersecurity breaches is by leveraging social engineering. Threat actors often impersonate legitimate customers of a financial institution to get more information about the customer they’re pretending to be.
In addition, nonpublic personal information (NPPI) includes (but is not limited to) names, addresses, and phone numbers when linked to bank and credit card account numbers, income and credit histories, and social security numbers (SSNs). Regulatory language uses the terms sensitive customer information and NPPI interchangeably.
Regulatory Oversight
All financial institutions that conduct business in the United States are subject to GLBA. The regulation gives authority to various agencies to administer and enforce the privacy and security provisions. Table 13.1 lists the agencies, their charges, and the applicable public law. By law, the agencies are required to work together to issue consistent and comparable rules to implement the act’s privacy provision. In contrast, the agencies are tasked with independently establishing minimum-security standards, as well as determining the type and severity of the penalties. Figure 13-2 lists several publications of standards and guidelines that have been published by different government agencies.
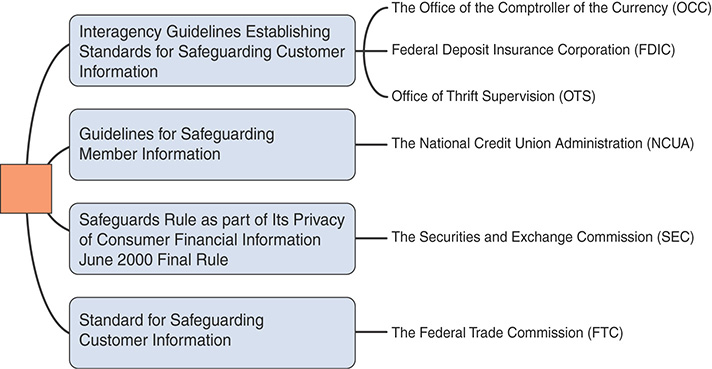
FIGURE 13-2 Publications by Federal Agencies Around the Safeguarding of Customer Information
Table 13-1 provides the GLBA regulatory agencies and their respective rules.
TABLE 13-1 GLBA Regulatory Agencies and Rules
Regulatory Agency |
Institution Type |
GLBA Rule Federal Register Designation |
|---|---|---|
Federal Reserve Board (FRB) |
Bank holding companies and member banks of the Federal Reserve System (FRS) |
12 C.F.R. § 216 |
Office of the Comptroller of the Currency (OCC) |
National banks, federal savings associations, and federal branches of foreign banks |
12 C.F.R. § 40 |
Federal Deposit Insurance Corporation (FDIC) |
State-chartered banks (that are not members of the FRS) |
12 C.F.R. § 332 |
National Credit Union Administration (NCUA) |
Federally chartered credit unions |
NCUA: 12 C.F.R. § 716 |
Securities and Exchange Commission (SEC) |
Securities brokers and dealers as well as investment companies |
17 C.F.R. § 248 |
Commodity Futures Trading Commission (CFTC) |
Futures and option markets |
CFTC: 17 C.F.R. § 160 |
Federal Trade Commission (FTC) |
Institutions not covered by the other agencies |
16 C.F.R. § 313 |
FYI: What Is the Federal Register?
Published by the Office of the Federal Register, National Archives and Records Administration (NARA), the Federal Register is the official daily publication for rules, proposed rules, and notices of federal agencies and organizations, as well as executive orders and other presidential documents. It is updated daily by 6 a.m. and is published Monday through Friday, except on federal holidays. The official home page of the Federal Register is www.federalregister.gov.
The Federal Trade Commission (FTC) Safeguards Act
As noted earlier, a variety of companies are subject to GLBA regulations. Banks, credit unions, insurance agencies, and investment firms are subject to regulatory oversight by the agency that charters or licenses them. The FTC has jurisdiction over individuals or organizations that are significantly engaged in providing financial products or services to consumers and are not subject to regulatory oversight. Many of these organizations are small businesses. The FTC’s implementation is known as the Safeguards Act. Overall, the requirements of the Safeguards Act are not as stringent as the Interagency Guidelines. The primary requirements are that covered entities must do the following:
Designate the employee or employees to coordinate the safeguards.
Identify and assess the risks to customer information in each relevant area of the company’s operation, and evaluate the effectiveness of current safeguards for controlling these risks.
Design a safeguards program, and detail the plans to monitor it.
Select appropriate service providers and require them (by contract) to implement the safeguards.
Evaluate the program and explain adjustments in light of changes to its business arrangements or the results of its security tests.
The FTC does not conduct regulatory compliance audits. Enforcement is complaint-driven. Consumers can file a complaint with the FTC. The FTC analyzes the complaints and if it detects a pattern of wrongdoing, it will investigate and prosecute, if appropriate. The FTC does not resolve individual consumer complaints.
The FTC has undertaken substantial efforts to promote cybersecurity in the private sector through the following:
Civil law enforcement
Business outreach and consumer education
Policy initiatives
Recommendations to Congress to enact legislation
Section 5 of The Federal Trade Commission (FTC) Safeguards Act is the primary enforcement tool that is used to prevent deceptive and unfair business practices. The FTC has been working with NIST and is aligning its practices with the NIST Cybersecurity Framework. FTC officials explain how the NIST Cybersecurity Framework relate to the FTC’s work on data security on a blog posted at https://www.ftc.gov/news-events/blogs/business-blog/2016/08/nist-cybersecurity-framework-ftc.
As FTC officials describe in their blog and website:
“The types of things the Framework calls for organizations to evaluate are the types of things the FTC has been evaluating for years in its Section 5 enforcement to determine whether a company’s data security and its processes are reasonable. By identifying different risk management practices and defining different levels of implementation, the NIST Framework takes a similar approach to the FTC’s long-standing Section 5 enforcement.”
What Are the Interagency Guidelines?
As noted earlier, the financial services oversight agencies were tasked with independently establishing minimum-security standards as well as determining the type and severity of the penalties. Banks are subject to the “Interagency Guidelines Establishing Standards for Safeguarding Customer Information,” and credit unions are subject to the “Guidelines for Safeguarding Member Information.” In this section, we will refer to them collectively as the Interagency Guidelines.
The Interagency Guidelines require every covered institution to implement a comprehensive written information security program that includes administrative, technical, and physical safeguards appropriate to the size and complexity of the bank or credit union and the nature and scope of its activities. To be in compliance, the information security program must include policies and processes that require institutions to perform the steps illustrated in Figure 13-3.

FIGURE 13-3 Policies and Processes Required for Compliance
It is up to each institution to develop a program that meets these objectives. The ISO 27002:2013 standard provides an excellent framework to develop a GLBA-compliant information security program.
In Practice
Regulatory Language Definitions
To understand the scope and mandate of the information security regulations, we need to start with the terminology. The following definitions apply to all versions of the Interagency Guidelines. Note that with the exception of credit unions, the user of services is referred to as a customer (in the case of credit unions, they are referred to as members).
Consumer information means any record about an individual, whether in paper, electronic, or other form, that is a consumer report or is derived from a consumer report and that is maintained or otherwise possessed by or on behalf of the institution for a business purpose. The term does not include any record that does not personally identify an individual.
Customer or member information means any record containing NPPI, about a customer or member, whether in paper, electronic, or other form, that is maintained by or on behalf of the financial institution.
Customer or member information system means any method used to access, collect, store, use, transmit, protect, or dispose of customer or member information.
Service provider means any person or entity that maintains, processes, or otherwise is permitted access to customer information through its provision of services directly to the financial institution.
Administrative safeguards are defined as governance, risk management, oversight, policies, standards, processes, programs, monitoring, and training designed and implemented with the intent of establishing and maintaining a secure environment.
Technical safeguards are defined as controls that are implemented or enforced by technological means.
Physical safeguards are defined as controls designed to protect systems and physical facilities from natural threats and/or man-made intrusions.
Involve the Board of Directors
The Interagency Guidelines require that the Board of Directors or an appropriate committee of the Board approve the bank’s written information security program. The Board is also tasked with overseeing the development, implementation, and maintenance of the information security program, including assigning specific responsibility for its implementation and reviewing reports from management. As corporate officials, directors have a fiduciary and legal responsibility. For example, financial institutions that do not comply with the GLBA are subject to civil penalties of $100,000 per violation. Officers and directors of that institution can be held personally liable as well, with penalties of $10,000 per violation.
Board members are generally chosen for their experience, business acumen, and standing in the community. It can be assumed that they understand business goals, processes, and inherent risks. Even experienced professionals, however, do not always have an in-depth natural understanding of information security issues. Institutions are expected to provide their Boards with educational opportunities to become and remain proficient in the area. Recognizing that this is a specialized body of knowledge, the Interagency Guidelines include the provision for delegation and distribution of responsibilities.
Examples of delegation include the following:
Delegating Board oversight to a subcommittee whose members include directors and representatives of the financial institution, such as a Chief Information Security Officer (CISO) or Chief Risk Officer (CRO)
Assigning information security management program oversight and management to a CISO or CRO
Assigning implementation and maintenance of administrative controls to the Information Security Officer
Assigning implementation and maintenance of technical controls to the Director of Information Technology
Assigning implementation and maintenance of physical controls to the facilities manager
Assigning design and delivery of information security training and awareness programs to the training department
Assigning verification of controls to the internal audit department
Assigning risk evaluation to the risk management committee
Assigning the evaluation of technology initiatives to the technology steering committee
Creating a multidisciplinary information security advisory committee that includes the representatives of all the aforementioned roles and departments
Information security crosses many boundaries and involves multiple domains. Experience has shown us that institutions that have adopted a cross-functional multidisciplinary approach, as shown in Figure 13-4, have a stronger and more successful information security program.
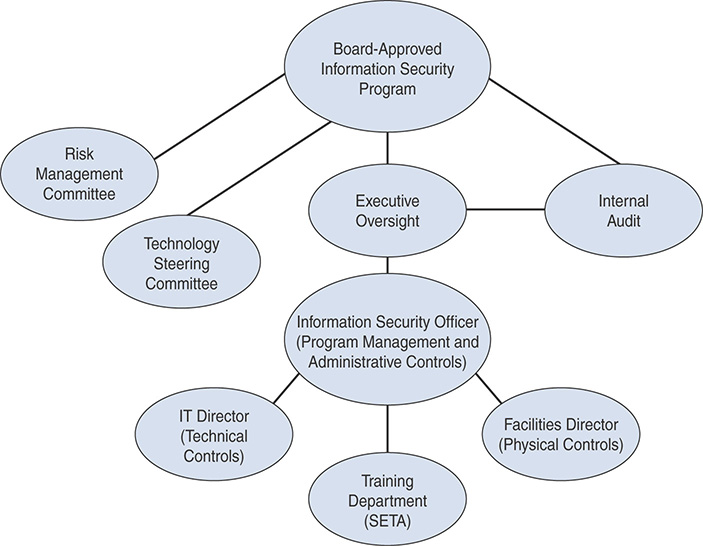
FIGURE 13-4 A Cross-functional Multidisciplinary Approach
In Practice
GLBA Section III-A: Involve the Board of Directors
The Board of Directors or an appropriate committee of the Board of each bank or credit union shall:
Approve the written information security program.
Oversee the development, implementation, and maintenance of the information security program, including assigning specific responsibility for its implementation and reviewing reports from management.
Assess Risk
Financial institutions are expected to take a risk-based approach to information security. The process begins with identifying threats. Threats are defined as potential dangers that have the capacity to cause harm. It is incumbent upon each institution to continually engage in a threat assessment, which is the identification of the types of threats and attacks that may affect the institution’s condition and operations or may cause data disclosures that could result in substantial harm or inconvenience to customers. A threat assessment must take into consideration a number of factors, including the size and type of the institution, services offered, geographic location, experience of personnel, infrastructure design, operating systems, vulnerability of applications, and cultural attitudes and norms. At a minimum, financial institutions must address the threats of unauthorized access, unauthorized data modification, system infiltration, malware, destruction of data or systems, and denial of service (DoS).
The systematic rating of threats based on level of impact and likelihood sans controls is used to determine the inherent risk. A risk assessment is used to evaluate the corresponding safeguards to calculate residual risk, which is defined as the level of risk after controls have been implemented. The Federal Financial Institutions Examination Council (FFIEC) recommends using the NIST risk management framework and methodology as described in Special Publication 800-53 to calculate residual risk. Multiple categories of risk are defined by the FDIC as relevant for financial institutions, including strategic, reputational, operational, transactional, and compliance:
Strategic risk is the risk arising from adverse business decisions, or the failure to implement appropriate business decisions in a manner that is consistent with the institution’s strategic goals.
Reputational risk is the risk arising from negative public opinion.
Operational risk is the risk of loss resulting from inadequate or failed internal processes, people, and systems or from external events.
Transactional risk is the risk arising from problems with service or product delivery.
Compliance risk is the risk arising from violations of laws, rules, or regulations, or from noncompliance with internal policies or procedures or with the institution’s business standards.
Risk assessments and corresponding risk management decisions must be documented and reported to the Board of Directors or designee. The reports are used by both independent auditors and regulators to evaluate the sufficiency of the institution’s risk management program.
In Practice
GLBA Section III-B: Assess Risk
Each bank or credit union shall:
Identify reasonably foreseeable internal and external threats that could result in unauthorized disclosure, misuse, alteration, or destruction of customer information or customer information systems.
Assess the likelihood and potential damage of these threats, taking into consideration the sensitivity of customer information.
Assess the sufficiency of policies, procedures, customer information systems, and other arrangements in place to control risks.
Manage and Control Risk
The Interagency Guidelines require that financial institutions design their information security programs to control the identified risks, commensurate with the sensitivity of the information as well as the complexity and scope of their activities. The agencies recommend using the ISO standards as the framework for financial institution information security programs. Table 13-2 maps the GLBA information security objectives and the ISO security domains.
TABLE 13-2 GLBA Requirement ISO 27002:2013 Cross-Reference
GLBA Requirement |
Corresponding ISO 27002:2013 Domain |
|---|---|
II. Standards for Safeguarding Customer Information |
|
A. Information Security Program Requirements |
Information Security Policies Compliance Management |
III. Development and Implementation of Information Security Program |
|
A. Involve the Board of Directors |
Organization of Information Security |
B. Assess Risk |
Refer to ISO 27005: Risk Management |
C1. Manage and Control Risk |
Asset Management Human Resources Security Physical and Environmental Security Communications Security Operations Security Access Control Information Systems Acquisition, Development, and Maintenance Information Security Incident Management Business Continuity |
C2. Train Staff |
Human Resources Security |
C3. Test Key Controls |
Communications Security Operations Security Information Systems Acquisition, Development, and Maintenance Information Security Incident Management Business Continuity |
C4. Properly Dispose of Information |
Asset Management |
D. Oversee Service Provider Arrangements |
Communications Security Operations Security |
E. Adjust the Program |
Information Security Policies Compliance Management |
F. Report to the Board |
Organization of Information Security |
Supplement A to Appendix B to Part 364 Interagency Guidance on Response Programs for Unauthorized Access to Customer Information and Customer Notice |
Information Security Incident Management |
Federal Financial Institutions Examination Council (FFIEC) Information Technology Examination Handbook (IT Handbook)
A must-read supporting resource is Federal Financial Institutions Examination Council (FFIEC) Information Technology Examination Handbook (IT Handbook). The FFIEC is an interagency body empowered to prescribe uniform principles, standards, and report forms for the federal examination of financial institutions by the Board of Governors of the Federal Reserve System (FRB), the FDIC, the NCUA, the OCC and the Consumer Financial Protection Bureau (CFPB), and to make recommendations to promote uniformity in the supervision of financial institutions. The IT InfoBase spans a number of topics, including Information Security, IT Audit, Business Continuity Planning, Development and Acquisition, Management, Operations, and Outsourcing Technology Services.
The FFIEC InfoBase is the de facto guide for a financial institution that wants to ensure it has a GLBA-compliant information security program that meets regulatory expectations. Resources include explanatory text, guidance, recommended examination procedures and work papers, presentations, and resource pointers. The InfoBase can be accessed from the FFIEC home page (www.ffiec.gov).
FFIEC Cybersecurity Assessment Tool
The FFIEC developed the Cybersecurity Assessment Tool to help financial institutions identify their risks and assess their cybersecurity maturity. The Cybersecurity Assessment Tool is aligned with the principles of the FFIEC Information Technology Examination Handbook (IT Handbook) and the NIST Cybersecurity Framework.
The FFIEC Cybersecurity Assessment Tool can be accessed at https://www.ffiec.gov/cyberassessmenttool.htm.
The FFIEC Cybersecurity Assessment Tool addresses two main topics:
The Inherent Risk Profile: Categorizes the institution’s inherent risk before implementing controls.
The Cybersecurity Maturity: Contains domains, assessment factors, components, and individual declarative statements across five maturity levels to identify specific controls and practices that are in place.
To complete the cybersecurity assessment, the executive team first assesses the organization’s inherent risk profile based on the five categories shown in Figure 13-5.
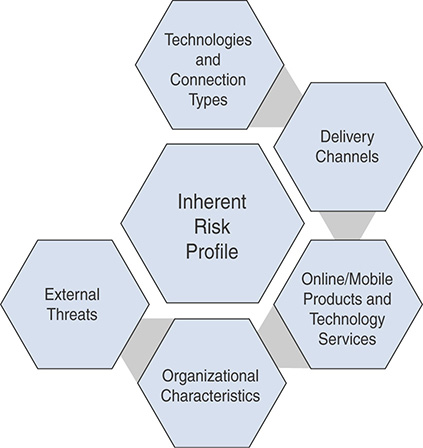
FIGURE 13-5 Inherent Risk Profile
The organization’s executives evaluate the overall cybersecurity maturity level for the domains shown in Figure 13-6.
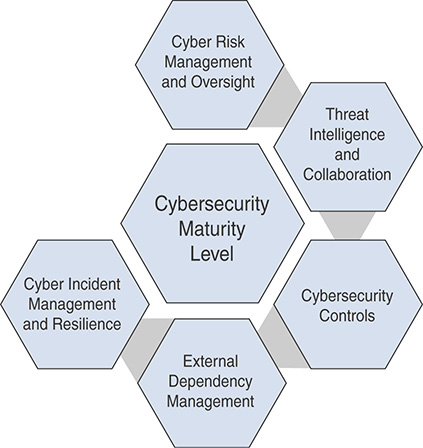
FIGURE 13-6 Evaluating the Overall Cybersecurity Maturity
Training
The Interagency Guidelines require institutions to implement an ongoing information security awareness program, to invest in training, and to educate executive management and directors.
The National Initiative for Cybersecurity Education (NICE), led by the National Institute of Standards and Technology (NIST), establishes a taxonomy and common lexicon that describes cybersecurity work and workers. The NICE Framework is documented in the NIST Special Publication 800-181. It is intended to be applied in the public, private, and academic sectors. Many organizations, including financial services institutions, use the NICE Framework to categorize the skills and training necessary for their cybersecurity workforce.
The goal of education is to explain why, and the anticipated outcome is insight and understanding. The goal of training is to explain how, and the anticipated outcome is knowledge and skill. Last, the goal of awareness is to explain what, and the anticipated outcome is information and awareness. The impact of education is long term, the impact of training is immediate, and the impact of awareness is short term.
At a minimum, financial institutions are expected to deliver and document annual enterprisewide training. The training can be instructor-led or online. Recommended topics include an overview of state and federal regulatory requirements, an explanation of user-focused threats, such as malware and social engineering, and a discussion of best practices and information resources acceptable use. It is commonplace for institutions to coordinate the distribution and signing of the acceptable use agreement with the annual training.
A popular concept that allows you to provide performance-based learning and assessment is the concept of cyber ranges. Cyber ranges are interactive, virtual representations of your organization’s network, systems, and applications in order to provide a safe, legal environment to gain hands-on cyber skills and a secure environment for product development and security posture testing. You can use physical hardware or a combination of actual and virtual components.
In Practice
GLBA Section IIIC-2: Training
Train staff to implement the bank’s information security program.
Note: Many organizations are leveraging the National Initiative for Cybersecurity Education (NICE) framework to develop security training for their employees.
Testing
Safeguards are meaningful only if they perform as anticipated. The regulatory agencies expect institutions to regularly test key controls and safeguards at a frequency that takes into account the rapid evolution of threats. High-risk systems should be subject to independent testing at least once a year. Independent testing means that the in-house or outsourced personnel who perform and report on the testing have no relationship to the design, installation, maintenance, and operation of the targeted system, or the policies and procedures that guide its operation. They should also be protected from undue influence or retaliatory repercussions.
The tests and methods utilized should be sufficient to validate the effectiveness of the security process in identifying and appropriately controlling security risks. The three most commonly used testing methodologies are audit, assessment, and assurance:
An audit is an evidence-based examination that compares current practices against a specific internal (for example, policy) or external (for example, regulations or audit standard such as Control Objectives for Information and Related Technology [COBIT]) criteria.
An assessment is a focused privileged inspection to determine condition, locate weakness or vulnerabilities, and identify corrective actions.
An assurance test measures how well the control or safeguard works generally by subjecting the system or device to an actual attack, misuse, or an accident. Assurance tests can be black box, meaning with no prior knowledge of the system or process being tested, or white box, meaning with knowledge of the system or process being tested.
Because testing may uncover nonpublic customer information, appropriate safeguards to protect the information must be in place. Contracts with third parties that provide testing services should require that the third parties implement appropriate measures to meet the objectives of the Interagency Guidelines and that any exposure of NPPI be reported immediately.
In Practice
GLBA Section IIIC-3: Testing
Regularly test the key controls, systems, and procedures of the information security program. The frequency and nature of such tests should be determined by the bank’s risk assessment. Tests should be conducted or reviewed by independent third parties or staff independent of those that develop or maintain the security programs.
Oversee Service Provider Arrangements
A third-party service provider relationship is broadly defined by the regulatory agencies to include all entities that have entered into a business relationship with a financial institution. This includes parties that perform functions on behalf of the institution, provide access to products and services, or perform marketing, monitoring, or auditing functions.
The Interagency Guidelines require financial institutions to ensure that service providers have implemented security controls in accordance with GLBA requirements. In June 2008, the Financial Institution Letter FIL-44-2008 “Guidance for Managing Third-Party Risk” made clear that an “institution can outsource a task, but it cannot outsource the responsibility.” It is up to the institution to ensure that the controls and safeguards designed, managed, and maintained by third parties are equivalent to or exceed internal policies and standards.
Recommended service provider oversight procedures include the following:
Conducting a risk assessment to ensure that the relationship is consistent with the overall business strategy and to ensure that management has the knowledge and expertise to provide adequate oversight
Using appropriate due diligence in service provider research and selection
Implementing contractual assurances regarding security responsibilities, controls, and reporting
Requiring nondisclosure agreements (NDAs) regarding the institution’s systems and data
Providing a third-party review of the service provider’s security though appropriate audits and tests
Coordinating incident response policies and contractual notification requirements
Reviewing at least annually significant third-party arrangements and performance
The Bank Service Company Act (BSCA), 12 USC 1861-1867, gives federal financial regulators statutory authority to regulate and examine the services a technology service provider (TSP) performs for FDIC-insured financial institutions. According to the FFIEC Outsourcing Technology Services Handbook, TSP relationships should be subject to the same risk management, security, privacy, and other internal controls and policies that would be expected if the financial institution were conducting the activities directly. To maintain an accurate database of TSPs, BSCA requires insured financial institutions to notify their appropriate federal banking agency in writing of contracts or relationships with third parties that provide certain services to the institution. Selected TSPs are examined on a 24-, 36-, or 48-month cycle. Distribution of the exam results is restricted to financial institutions that have signed a contract with the TSP. Ironically, this means that the findings are not available during the initial due-diligence phase.
In Practice
GLBA Section III-D: Oversee Service Provider Relationships
Each bank shall:
Exercise appropriate due diligence in selecting its service providers.
Require its service providers by contract to implement appropriate measures designed to meet the objectives of these guidelines.
Where indicated by the bank’s risk assessment, monitor its service providers to confirm that they have satisfied their obligations as required by paragraph D.2. As part of this monitoring, a bank should review audits, summaries of test results, or other equivalent evaluations of its service providers.
Adjust the Program
A static information security program provides a false sense of security. Threats are ever increasing. Organizations are subject to change. Monitoring the effectiveness of the security program and personnel is essential to maintaining a secure environment, protecting customer information, and complying with regulatory objectives. Evaluation results should be carefully analyzed and, as appropriate, adjustments to the information security program implemented. At a minimum, the information security policy should be reviewed annually. Modifications to policy must be communicated to the Board of Directors. It is the responsibility of the Board of Directors to annually reauthorize the information security policy and, by extension, the information security program.
In Practice
GLBA Section III-E: Adjust the Program
Each bank shall monitor, evaluate, and adjust, as appropriate, the information security program in light of any relevant changes in technology, the sensitivity of its customer information, internal or external threats to information, and the bank’s own changing business arrangements, such as mergers and acquisitions, alliances and joint ventures, outsourcing arrangements, and changes to customer information systems.
Report to the Board
Throughout the year, the Board of Directors or designated committee should receive information security program updates and be immediately apprised of any major issue. Additionally, the Interagency Guidelines require each institution to provide an annual Information Security and GLBA Compliance report to the Board of Directors or designated committee. The report should describe the overall status of the information security program and the bank’s compliance with the Interagency Guidelines. The report should detail the following:
Regulatory examination results and post-examination follow-up.
Security incidents that occurred in the previous 12 months, including a synopsis of response and impact.
Major IT and security initiatives completed in the previous 12 months, in progress and scheduled.
Information security program–related governance activities, including a synopsis of roles, responsibilities, and significant decisions.
Independent audit and testing conducted in the previous 12 months. The description should include type of test, date of test, tester, test objective, test results, recommendations, follow-up, and, if applicable, remediation plan.
Risk assessments conducted in the previous 12 months. The description should include methodology, focus areas, results, follow-up, and, if applicable, remediation plan.
Service provider oversight activities. The description should include due diligence, contract updates, monitoring, and, if applicable, identified issues and remediation plan.
Employee training conducted in the previous 12 months. The description should include the type of training, conduct, participation, and evaluation.
Updates to and testing of the incident disaster recovery, public health emergency, and business continuity plan.
Updates to and testing of the incident response plan and procedures.
Recommended changes to the information security program or policy that require Board approval or authorization.
The final section of the report should be management’s opinion of the institution’s compliance with information security–related state and federal regulations and guidance. Conversely, if in management’s opinion the institution does not comply with applicable regulations or guidance, the issues should be fully documented and a remediation plan presented.
New York’s Department of Financial Services Cybersecurity Regulation (23 NYCRR Part 500)
The New York Department of Financial Services (DFS) created a regulation that took effect on March 1, 2017, and that is designed to promote the protection of customer information as well as the information technology systems of regulated entities. This regulation requires any individual or organization operating under or required to operate under a license, charter, certificate, permit, accreditation, or similar authorization under the banking law, insurance law, or the financial services law that do business in the state of New York to assess their cybersecurity risk profile and design a solid program to address such cybersecurity risks. The NY DFS Cybersecurity Regulation can be accessed at www.dfs.ny.gov/legal/regulations/adoptions/dfsrf500txt.pdf; the key parts are as follows:
Section 500.00 is an introduction to the rule, and Section 500.01 defines the terms used throughout the rule.
Section 500.02 states that “each Covered Entity shall maintain a cybersecurity program designed to protect the confidentiality, integrity and availability of the Covered Entity’s Information Systems.”
Section 500.03 dictates that “each Covered Entity shall implement and maintain a written policy or policies, approved by a Senior Officer or the Covered Entity’s board of directors (or an appropriate committee thereof) or equivalent governing body, setting forth the Covered Entity’s policies and procedures for the protection of its Information Systems and Nonpublic Information stored on those Information Systems.”
The NY DFS Cybersecurity Regulation states in Section 500.04 that “each Covered Entity shall designate a qualified individual responsible for overseeing and implementing the Covered Entity’s cybersecurity program and enforcing its cybersecurity policy (for purposes of this Part, “Chief Information Security Officer” or “CISO”). The CISO may be employed by the Covered Entity, one of its Affiliates or a Third-Party Service Provider.”
Section 500.05 requires the covered entity to perform security penetration testing and vulnerability assessments on an ongoing basis. The cybersecurity program needs to include monitoring and testing, developed in accordance with the Covered Entity’s Risk Assessment, designed to assess the effectiveness of the Covered Entity’s cybersecurity program. The regulation dictates that “the monitoring and testing shall include continuous monitoring or periodic Penetration Testing and vulnerability assessments.” The organization must conduct an annual security penetration test and a biannual vulnerability assessment.
Section 500.06 specifies that each covered entity shall securely maintain an audit trail of supported systems.
Section 500.07 specifies that “each Covered Entity shall limit user access privileges to Information Systems that provide access to Nonpublic Information and shall periodically review such access privileges.”
Additionally, Section 500.08 states that the institution’s application security “procedures, guidelines and standards shall be periodically reviewed, assessed and updated as necessary by the CISO (or a qualified designee) of the Covered Entity.” As such, when Covered Entities are acquiring or merging with a new company, Covered Entities will need to do a factual analysis of how these regulatory requirements apply to that particular acquisition. Some important considerations include, but are not limited to, what business the acquired company engages in, the target company’s risk for cybersecurity, including its availability of PII, the safety and soundness of the Covered Entity, and the integration of data systems. The Department emphasizes that Covered Entities need to have a serious due diligence process, and cybersecurity should be a priority when considering any new acquisitions.
Section 500.09 states that the “Risk Assessment shall be updated as reasonably necessary to address changes to the Covered Entity’s Information Systems, Nonpublic Information or business operations.”
Similar to GLBA, the NY DFS Cybersecurity Regulation specifies (in Section 500.10) that each covered entity needs to provide cybersecurity personnel “with cybersecurity updates and training sufficient to address relevant cybersecurity risks; and verify that key cybersecurity personnel take steps to maintain current knowledge of changing cybersecurity threats and countermeasures.” Section 500.11 addresses third-party service provider security policies.
Section 500.12 specifies that each covered entity shall use multifactor authentication.
Section 500.13 strictly specifies that “each Covered Entity shall include policies and procedures for the secure disposal on a periodic basis of any Nonpublic Information identified in section 500.01(g)(2)-(3) of this Part that is no longer necessary for business operations or for other legitimate business purposes of the Covered Entity, except where such information is otherwise required to be retained by law or regulation, or where targeted disposal is not reasonably feasible due to the manner in which the information is maintained.”
Section 500.14 covers training and monitoring.
Section 500.15 mandates encryption of nonpublic information.
Section 500.16 mandates that each Covered Entity “shall establish a written incident response plan designed to promptly respond to, and recover from, any Cybersecurity Event materially affecting the confidentiality, integrity or availability of the Covered Entity’s Information Systems or the continuing functionality of any aspect of the Covered Entity’s business or operations.”
Section 500.17 requires each Covered Entity to annually submit to the Superintendent a written statement covering the prior calendar year by February 15, certifying that the Covered Entity is in compliance with the requirements stated in the regulation. In addition, it dictates that the Covered Entity needs to maintain all records, schedules, and data supporting the certificate for a period of five years. The Superintendent also needs to be notified within 72 hours from the determination of the occurrence of a Cybersecurity Event impacting the Covered Entity.
An important element to point out about the NY DFS Cybersecurity Regulation is that it overlaps with the guidance and requirements for entities that are already in compliance with the GLBA or have met the FFIEC standards outlined in their IT Handbook. Most financial organizations that are considered covered entities under the NY DFS Cybersecurity Regulation will have already addressed some requirements outlined in GLBA or FFIEC IT Handbook. However, it is important to know that while there is overlap in the requirements, there are also some substantial differences needing to be addressed to comply with the NY DFS Cybersecurity Regulation. Understanding these differences will help you leverage existing investments in security and develop a plan of action to address any gaps.
What Is a Regulatory Examination?
The regulatory agencies are responsible for oversight and supervision of financial institutions. Included in this charge is ensuring that the financial institutions soundly manage risk; comply with laws and regulations, including GLBA, the NY DFS Cybersecurity Regulation, and others; and, as appropriate, take corrective action. Representatives of the regulatory agencies examine their respective banks and credit unions. Depending on size, scope, and previous examination findings, exams are conducted every 12 to 18 months. Included in the exam is an evaluation of policies, processes, personnel, controls, and outcomes.
Examination Process
GLBA security is included in the Information Technology Examination. Institutions are given 30- to 90-days’ notice that an examination is scheduled. An Information Technology Officer’s questionnaire is sent to the institution with the expectation that the institution will complete and return the questionnaire and supporting documentation (including Board reports, policies, risk assessments, test results, and training materials) prior to the examination date. The length of the exam and number of on-site examiners depends on the complexity of the environment, previous findings, and examiner availability. The examination begins with an entrance meeting with management. The agenda of the entrance meeting includes explaining the scope of the examination, the role of each examiner, and how the team will conduct the exam. During the exam, the examiners will request information, observe, and ask questions. At the end of the exam, an exit meeting is held to discuss findings and potential solutions. Post-examination, the regulatory agency will issue a draft report for management’s review for accuracy. Taking into consideration management’s response, the agency will issue a written report to the Board of Directors, which includes the examination ratings, any issues that have been identified, recommendations, and, if required, supervisory action.
The NY DFS Cybersecurity Regulation mandates that “each Covered Entity shall maintain for examination by the Department all records, schedules and data supporting this certificate for a period of five years.” It also specifies that each Covered Entity is to annually submit to the Superintendent, by February 15, a written statement covering the prior calendar year, certifying that the Covered Entity is in compliance with the requirements stated in the regulation. In addition, it dictates that the Covered Entity needs to maintain all records, schedules, and data supporting the certificate for a period of five years. The Superintendent also needs to be notified within 72 hours from the determination of the occurrence of a Cybersecurity Event impacting the Covered Entity.
Examination Ratings
The Uniform Rating System for Information Technology (URSIT) is used to uniformly assess financial institutions. The rating is based on a scale of 1 to 5, in ascending order of supervisory concern, with 1 representing the best rating and least degree of concern, and 5 representing the worst rating and highest degree of concern. URSIT is part of the FFIEC.
Per URSIT standards:
Financial institutions that are rated as a “1” exhibit strong performance in every respect. Weaknesses in IT are minor in nature and are easily corrected during the normal course of business. Risk management processes provide a comprehensive program to identify and monitor risk relative to the size, complexity, and risk profile of the entity.
Financial institutions rated as a “2” exhibit safe and sound performance but may demonstrate modest weaknesses in operating performance, monitoring, management processes, or system development. Generally, senior management corrects weaknesses in the normal course of business. Risk management processes adequately identify and monitor risk relative to the size, complexity, and risk profile of the entity. As a result, supervisory action is informal and limited.
Financial institutions and service providers rated composite “3” exhibit some degree of supervisory concern because of a combination of weaknesses that may range from moderate to severe. If weaknesses persist, further deterioration in the condition and performance of the institution or service provider is likely. Risk management processes may not effectively identify risks and may not be appropriate for the size, complexity, or risk profile of the entity. Formal or informal supervisory action may be necessary to secure corrective action.
Financial institutions and service providers rated composite “4” operate in an unsafe and unsound environment that may impair the future viability of the entity. Operating weaknesses are indicative of serious managerial deficiencies. Risk management processes inadequately identify and monitor risk, and practices are not appropriate given the size, complexity, and risk profile of the entity. Close supervisory attention is necessary and, in most cases, formal enforcement action is warranted.
Financial institutions and service providers rated composite “5” exhibit critically deficient operating performance and are in need of immediate remedial action. Operational problems and serious weaknesses may exist throughout the organization. Risk management processes are severely deficient and provide management little or no perception of risk relative to the size, complexity, and risk profile of the entity. Ongoing supervisory attention is necessary.
Supplemental to the rating, if violations of any law or regulations are identified, the agency must provide detailed information, including legal numerical citations and name, a brief description of the law or regulation (or portion of it) that is in violation, a description of what led to the violation, and corrective action taken or promised by management.
Personal and Corporate Identity Theft
Personal and corporate identity theft is one of the fastest growing crimes worldwide. Personal identity theft occurs when a criminal fraudulently uses a name, address, SSN, bank account or credit card account number, or other identifying information without consent to commit a crime.
Corporate identity theft occurs when criminals attempt to impersonate authorized employees, generally for the purpose of accessing corporate bank accounts to steal money. This type of attack is known as a corporate account takeover. Using specially crafted malware, criminals capture a business’s online banking credentials or compromise the workstation used for online banking. The criminals then access online accounts and create fraudulent ACH or wire transfers. The transfers are directed “money mules” who are waiting to withdraw the funds and send the money overseas. Once the funds are offshore, it is very difficult for law enforcement to recover them.
What Is Required by the Interagency Guidelines Supplement A?
Supplement A, “Interagency Guidance on Response Programs for Unauthorized Access to Customer Information and Customer Notice,” describes response programs, including customer notification procedures, that a financial institution should develop and implement to address unauthorized access to or use of customer information that could result in substantial harm or inconvenience to a customer. The guidance enumerates a number of security measures that each financial institution must consider and adopt, if appropriate, to control risks stemming from reasonably foreseeable internal and external threats to the institution’s customer information. The guidance stresses that every financial institution must develop and implement a risk-based response program to address incidents of unauthorized access to customer information. The response program should be a key part of an institution’s cybersecurity program. Supplement A emphasizes that an institution’s response program should contain procedures for the following:
Assessing the nature and scope of an incident, and identifying what customer information systems and types of customer information have been accessed or misused.
Notifying its primary federal regulator as soon as possible when the institution becomes aware of an incident involving unauthorized access to or use of sensitive customer information.
Being consistent with the agencies’ Suspicious Activity Report (SAR) regulations, notifying appropriate law enforcement authorities in addition to filing a timely SAR in situations involving federal criminal violations requiring immediate attention, such as when a reportable violation is ongoing.
Taking appropriate steps to contain and control the incident to prevent further unauthorized access to or use of customer information—for example, by monitoring, freezing, or closing affected accounts—while preserving records and other evidence.
Requiring its service providers by contract to implement appropriate measures designed to protect against unauthorized access to or use of customer information that could result in substantial harm or inconvenience to any customers.
Notifying customers when warranted.
The guidance emphasizes notification requirements. When a financial institution becomes aware of an incident of unauthorized access to sensitive customer information, the institution is required to conduct a reasonable investigation to promptly determine the likelihood that the information has been or will be misused. If the institution determines that misuse of its information about a customer has occurred or is reasonably possible, it must notify its regulatory agency and affected customers as soon as possible. Customer notice may be delayed if an appropriate law enforcement agency determines that notification will interfere with a criminal investigation and provides the institution with a written request for the delay. In this case, the institution should notify its customers as soon as notification will no longer interfere with the investigation. When customer notification is warranted, an institution may not forgo notifying its customers of an incident because the institution believes that it may be potentially embarrassed or inconvenienced by doing so.
Compliance with the Supplement A, “Interagency Guidance on Response Programs for Unauthorized Access to Customer Information and Customer Notice,” is included in the FFIEC Information Technology Examination.
Identity Theft Data Clearinghouse
Although the FTC does not have criminal jurisdiction, it supports the identity theft criminal investigation and prosecution through its Identity Theft Data Clearinghouse. The Clearinghouse is the nation’s official repository for identity theft complaints and a part of the FTC’s Consumer Sentinel complaint database. In addition to housing more than a million ID theft complaints, Sentinel offers participating law enforcement agencies a variety of tools to facilitate the investigation and prosecution of identity theft. These include information to help agencies coordinate effective joint action, sample indictments, tools to refresh investigative data through programmed data searches, and access to “hot address” databases.
What Is Required by the Supplement to the Authentication in an Internet Banking Environment Guidance?
In response to the alarming rate of successful corporate account takeover attacks, the financial losses being sustained by both financial institutions and customers, and the impact on public confidence in the online banking system, in October 2011, the regulatory agencies issued updated guidance related to Internet banking safeguards. The FFIEC issued a supplement to the Authentication in an Internet Banking Environment Guidance, which stressed the need for performing risk assessments, implementing effective strategies for mitigating identified risks, and raising customer awareness of potential risks. In a departure from other guidance, the supplement was specific in its requirements and opinion of various authentication mechanisms.
Requirements include the following:
Financial institutions are required to review and update their existing risk assessments as new information becomes available, prior to implementing new electronic financial services, or at least every 12 months.
Financial institutions are required to implement a layered security model. Layered security is characterized by the use of different controls at different points in a transaction process so that a weakness in one control is generally compensated for by the strength of a different control.
Financial institutions are required to offer multifactor authentication to their commercial cash management (ACH and wire transfer) customers. Because the frequency and dollar amounts of these transactions are generally higher than consumer transactions, they pose a comparatively increased level of risk to the institution and its customer.
Financial institutions are required to implement authentication and transactional fraud monitoring.
Financial institutions are required to educate their retail and commercial account holders about the risks associated with online banking. Commercial customers must be notified that their funds are not covered under Regulation E and that they may incur a loss. It is strongly recommended that the awareness programs include risk reduction and mitigation recommendations.
Compliance with the Supplement to the Authentication in an Internet Banking Environment Guidance has been added to the Information Technology Examination. Anecdotal evidence suggests that the guidance has had an impact because losses associated with corporate account takeover are declining.
FYI: Corporate Account Takeover Fraud Advisory
The United States Secret Service, the Federal Bureau of Investigation, the Internet Crime Complaint Center (IC3), and the Financial Services Information Sharing and Analysis Center (FSISAC) jointly issued a Fraud Advisory for Business: Corporate Account Takeover, with the intent of warning business about this type of crime. The advisory noted that cybercriminals are targeting nonprofits, small and medium-sized businesses, municipalities, and school districts across the country. Using malicious software (malware), cybercriminals attempt to capture a business’s online banking credentials, take over web sessions, or even remotely control workstations. If the criminal gains access to online bank account login credentials or can take over an online banking session, it is possible for him to initiate and authorize ACH or wire funds transfers. Generally, the criminal will create numerous smaller transactions and send them to domestic “money mules,” who are waiting to withdraw the funds and send the money overseas. Once the funds are offshore, it is very difficult for law enforcement to recover them. To make matters worse, financial institutions are not required to reimburse for fraud-related losses associated with commercial accountholder computers or networks. Nor are these losses covered by FDIC insurance.
The information contained in the advisory is intended to provide basic guidance and resources for businesses to learn about the evolving threats and to establish security processes specific to their needs. The advisory and related resources are available at the NACHA Corporate Account Takeover Resource Center website at www.nacha.org/Corporate_Account_Takeover_Resource_Center. Security journalist Brian Krebs has been reporting on the impact of corporate account takeovers on small business for years! For current and archived reports, visit his blog at http://krebsonsecurity.com/category/smallbizvictims.
Summary
Federal law defines a financial institution as “any institution the business of which is significantly engaged in financial activities….” This broad definition includes banks, credit unions, investment firms, and businesses such as automobile dealers, check-cashing businesses, consumer reporting agencies, credit card companies, educational institutions that provide financial aid, financial planners, insurance companies, mortgage brokers and lenders, and retail stores that issue credit cards.
Congress enacted legislation requiring all financial institutions that do business in the United States to protect the privacy and security of customer nonpublic personal information (NPPI). The Gramm-Leach-Bliley Act (GLBA) required that appropriate privacy and security standards be developed and enforced, and assigned this task to various federal agencies. The agencies that regulate banks and credit unions collaborated and in 2001 published the Interagency Guidelines Establishing Standards for Safeguarding Customer Information and the Guidelines for Safeguarding Member Information, respectively. The Federal Trade Commission (FTC) was charged with developing standards for nonregulated businesses that provide financial services, and in 2003 published the Standards for Safeguarding Customer Information, also known as the Safeguards Act. Due to the type of business the regulations apply to, the requirements of the Safeguards Act are not as stringent as the Interagency Guidelines. The FTC does not conduct compliance examinations. The basis for investigation and enforcement actions are consumer complaints.
The Interagency Guidelines Establishing Standards for Safeguarding Customer Information and the Guidelines for Safeguarding Member Information, collectively referred to as the Interagency Guidelines, define cybersecurity program objectives and requirements for banks and credit unions. It is up to each covered entity to implement a comprehensive written cybersecurity program that includes administrative, technical, and physical safeguards appropriate to the size and complexity of the institution and the nature and scope of its activities. To be in compliance, the cybersecurity program must include policies and processes that require institutions to do the following:
Involve the Board of Directors
Assess risk
Manage and control risk
Oversee service provider arrangements
Adjust the program
Report to the Board
It is up to each institution to develop a program that meets these objectives. The NIST Cybersecurity Framework and the ISO 27002:2013 standard provide a good foundation for a regulatory-compliant cybersecurity program.
Financial institutions are expected to take a risk-based approach to cybersecurity. The process begins with identifying threats. Threats are defined as potential dangers that have the capacity to cause harm. It is incumbent upon each institution to continually engage in a threat assessment. A threat assessment is the identification of the types of threats and attacks that may affect the institution’s condition and operations or may cause data disclosures that could result in substantial harm or inconvenience to customers. At a minimum, financial institutions must address the threats of unauthorized access, unauthorized data modification, system infiltration, malware, destruction of data or systems, and DoS. The systematic rating of threats based on level of impact and likelihood sans controls is used to determine the inherent risk. A risk assessment is used to evaluate the corresponding safeguards in order to calculate residual risk. Residual risk is defined as the level of risk after controls and safeguards have been implemented. The Federal Financial Institutions Examination Council (FFIEC) recommends using the NIST risk management framework and methodology as described in Special Publication 800-53 to calculate residual risk. Multiple categories of risk are defined by the FDIC as relevant for financial institutions, including strategic, reputational, operational, transactional, and compliance.
Controls and safeguards can be circumvented by users. Although these actions may be deliberate or accidental, they are often intentionally malicious. To mitigate the risk of circumvention, it is critical that users understand the threat environment, learn best practices, and agree to acceptable use of information and information systems. To this end, institutions are expected to have a security awareness program and to provide annual enterprisewide training.
Controls and safeguards are useful only if they perform as expected. Scheduled testing should be conducted by personnel that are independent of the targeted system. The tests and methods utilized should be sufficient to validate the effectiveness of the controls and safeguards. The three most common testing methodologies are audit, assessment, and assurance.
The Interagency Guidelines require financial institutions to ensure that service providers have implemented security controls in accordance with GLBA requirements. Financial Institution Letter FIL-44-2008, “Third-Party Risk Guidance for Managing Third-Party Risk,” clearly states that an institution can outsource a task, but it cannot outsource the responsibility. It is up to the institution to ensure that the controls and safeguards designed, managed, and maintained by third parties comply with the Interagency Guidelines and are equivalent to or exceed internal policies and standards.
The financial institutions’ Board of Directors is ultimately responsible for oversight of the cybersecurity program and for compliance with all applicable state and federal regulations. Throughout the year, board members should receive cybersecurity program updates and be immediately apprised of all major security issues. Decisions that may significantly affect the risk profile of the institution must be authorized by the Board. The Interagency Guidelines require each institution to provide a comprehensive annual Cybersecurity and GLBA Compliance report to the Board of Directors or designated committee.
In response to the problem of personal and corporate identity threat, in 2005 the regulatory agencies issued Supplement A, “Interagency Guidance on Response Programs for Unauthorized Access to Customer Information and Customer Notice,” and in 2011, “Supplement to the Authentication in an Internet Banking Environment Guidance.” Both supplements focus on threats related to unauthorized access to or use of customer information as well as corresponding controls, including education, incident response programs, and notification procedures.
To ensure compliance with GLBA Interagency Guidelines and supplemental guidance, financial institutions are subject to regulatory examinations. Depending on size, scope, and previous examination findings, exams are conducted every 12 to 18 months. Included in the exam is an evaluation of policies, processes, personnel, controls, and outcomes. The outcome of the examination is a rating based on a scale of 1 to 5, in ascending order of supervisory concern (1 representing the best rating and least degree of concern, and 5 representing the worst rating and highest degree of concern), supervisory comments, and recommendations. Financial institutions that are found not in compliance with regulatory requirements and do not remediate examination findings within an agreed-upon time frame can be subject to closure.
Test Your Skills
Multiple Choice Questions
1. Which of the following statements best defines the type of organizations that are subject to GLBA regulations?
A. GLBA applies only to banks and credit unions.
B. GLBA applies only to check cashing businesses.
C. GLBA applies to any business engaged in financial services.
D. GLBA applies only to institutions licensed to offer depository services.
2. The Financial Modernization Act of 1999 __________________.
A. prevented the merger of banks, stock brokerage companies, and insurance companies
B. mandated use of computers in all branch offices
C. allowed the merger of banks, stock brokerage companies, and insurance companies
D. introduced the new cybersecurity framework
3. Which of the following agencies is responsible for enforcing GLBA?
A. The U.S. Department of Commerce
B. NIST
C. Federal Trade Commission (FTC)
D. None of the above
4. Which of the following is not considered NPPI?
A. SSN
B. The physical address of a company or a bank
C. Checking account number
D. PIN or password associated with a financial account or payment card
5. The Interagency Guidelines Establishing Standards for Safeguarding Customer Information was jointly developed by the _____________________________.
A. Federal Deposit Insurance Corporation (FDIC)
B. Office of the Comptroller of the Currency (OCC), Federal Reserve System (FRS), and FDIC
C. Securities and Exchange Commission (SEC) and FDIC
D. National Credit Union Administration (NCUA) and FDIC
6. Which of the following is not a requirement of the Safeguards Act?
A. Designate the employee or employees to coordinate the safeguards.
B. Design a safeguards program, and detail the plans to monitor it.
C. Select appropriate service providers and require them (by contract) to implement the safeguards.
D. Enforce the adoption and improvement of the NIST Cybersecurity Framework.
7. Which of the following statements is false about the FTC Safeguards Act?
A. The FTC does not conduct regulatory compliance audits.
B. Enforcement is complaint-driven.
C. Consumers can file a complaint with the FTC.
D. Consumers can only file a complaint with the respective financial institution.
8. What is the Federal Register?
A. A series of legal safeguards
B. A series of physical safeguards
C. The official daily publication for rules, proposed rules, and notices of federal agencies
D. A series of technical safeguards
9. The Interagency Guidelines require every covered institution to implement which of the following?
A. A cybersecurity framework for business partners
B. A comprehensive written information security program that includes administrative, technical, and physical safeguards appropriate to the size and complexity of the organization
C. A comprehensive written information security program that includes administrative, technical, and physical safeguards appropriate to the size and complexity of the business partners
D. A comprehensive written information security program excluding administrative, technical, and physical safeguards
10. Financial institutions are expected to take an _________ approach to cybersecurity.
A. threat-based
B. risk-based
C. audit-based
D. management-based
11. Which of the following terms describes a potential danger that has the capacity to cause harm?
A. Risk
B. Threat
C. Variable
D. Vulnerability
12. Which of the following statements best describes a threat assessment?
A. A threat assessment identifies the types of threats that may affect the institution or customers.
B. A threat assessment is a systematic rating of threats based on level of impact and likelihood.
C. A threat assessment is an audit report.
D. A threat assessment is a determination of inherent risk.
13. Which of the following risk types is defined as a level of risk after controls and safeguards have been implemented?
A. Ongoing risk
B. Residual risk
C. Acceptable risk
D. Inherent risk
14. Which of the following risk-management frameworks is recommended by the FFIEC?
A. FAIR Institute
B. COBIT
C. NIST
D. FDIC
15. Which of the following statements is true?
A. Strategic risk is the risk of loss resulting from inadequate or failed internal processes, people, and systems or from external events.
B. Reputational risk is the risk of loss resulting from inadequate or failed internal processes, people, and systems or from external events.
C. Transactional risk is the risk of loss resulting from inadequate or failed internal processes, people, and systems or from external events.
D. Operational risk is the risk of loss resulting from inadequate or failed internal processes, people, and systems or from external events.
16. The risk arising from problems with service or product delivery is known as ________________.
A. strategic risk
B. reputational risk
C. transactional risk
D. operational risk
17. Which of the following defines strategic risk?
A. The risk arising from negative public opinion
B. The risk arising from negative government regulations
C. The risk arising from adverse business decisions, or the failure to implement appropriate business decisions in a manner that is consistent with the institution’s strategic goals
D. The risk arising from noncompliant business partners
18. A security awareness and training program is considered which type of control?
A. Administrative control
B. Physical control
C. Technical control
D. Contractual control
19. Which of the following statements best describes a cyber range?
A. An enterprisewide security penetration testing program including continuous monitoring and vulnerability management.
B. Interactive, virtual representations of your organization’s network, systems, and applications in order to provide a safe, legal environment to gain hands-on cyber skills and a secure environment for product development and security posture testing.
C. An enterprisewide security penetration testing program excluding continuous monitoring and vulnerability management.
D. Independent testing is testing performed by certified professionals.
20. Which of the following test methodologies is a privileged inspection to determine condition, locate weakness or vulnerabilities, and identify corrective actions?
A. Audit
B. Assessment
C. White box
D. Black box
21. Which of the following is true about “black box” testing?
A. The individual conducting the testing had prior knowledge of the system and underlying source code of an application.
B. The individual conducting the testing only had prior knowledge and access to the underlying source code of an application running on the system.
C. The individual conducting the testing didn’t have prior knowledge of the system and underlying source code of an application.
D. The individual conducting the testing is also the developer of the application running on the system.
22. Per the Interagency Guidance, which of the following entities is responsible for oversight of a financial institution’s Cybersecurity Program?
A. Chief Technology Officer (CTO)
B. Chief Information Security Officer (CISO)
C. Board of Directors
D. Regulatory Agencies
23. Which of the following is true about the Uniform Rating System for Information Technology (URSIT)?
A. URSIT is a rating based on a scale of 1 to 5, in ascending order of supervisory concern, with 1 representing the best rating and least degree of concern, and 5 representing the worst rating and highest degree of concern.
B. URSIT is a rating based on a scale of 1 to 10, in ascending order of supervisory concern, with 10 representing the best rating and least degree of concern, and 1 representing the worst rating and highest degree of concern.
C. URSIT is a rating based on a scale of 1 to 5, in ascending order of supervisory concern, with 5 representing the best rating and least degree of concern, and 1 representing the worst rating and highest degree of concern.
D. None of the above.
24. Which of the following statements is true about the New York Department of Financial Services (DFS) Cybersecurity Regulation?
A. All financial institutions in New York, New Jersey, and New England are subject to a three-year examination schedule.
B. All financial institutions in New York and New Jersey are subject to a three-year examination schedule.
C. Requires financial services companies that do business in the state of New York to assess their cybersecurity risk profile and design a solid program to address such cybersecurity risks.
D. Requires financial services companies to have a CISO in New York, and the company cannot hire an affiliate or a third-party service provider.
25. Which of the following statements is not true about the NY DFS Cybersecurity Regulation?
A. The organization must conduct an annual security penetration test and a biannual vulnerability assessment.
B. The organization must conduct a security penetration test every two years and an annual vulnerability assessment.
C. The cybersecurity procedures, guidelines and standards shall be periodically reviewed, assessed, and updated as necessary by the CISO (or a qualified designee) of the covered entity.
D. The financial institution needs to provide cybersecurity personnel with cybersecurity updates and training sufficient to address relevant cybersecurity risks, and verify that key cybersecurity personnel take steps to maintain current knowledge of changing cybersecurity threats and countermeasures.
26. Which of the following is not an example of multifactor authentication?
A. Password and smart token
B. Password and username
C. Password and SMS (text) message
D. Password and out-of-band via a mobile device app
27. Which of the following is not true about controls and safeguards?
A. Controls and safeguards are useful only if they perform as expected.
B. Controls and safeguards can be circumvented by users.
C. The tests and methods utilized should be sufficient to validate the effectiveness of the controls and safeguards.
D. Controls and safeguards cannot be circumvented by users.
28. Which of the following statements is true?
A. When a financial institution chooses to outsource a banking function, it must conduct a due-diligence investigation.
B. When a financial institution chooses to outsource a banking function, it must report the relationship to its regulatory agency.
C. When a financial institution chooses to outsource a banking function, it must require the service provider to have appropriate controls and safeguards.
D. All of the above.
29. Which of the following is not a requirement by the Supplement to the Authentication in an Internet Banking Environment Guidance?
A. Financial institutions are required to educate their retail and commercial account holders about the risks associated with online banking.
B. Financial institutions are required to educate their retail and commercial account holders about the risks associated with a cyber range.
C. Financial institutions are required to implement a layered security model. Layered security is characterized by the use of different controls at different points in a transaction process so that a weakness in one control is generally compensated for by the strength of a different control.
D. Financial institutions are required to implement authentication and transactional fraud monitoring.
30. The FTC does not have criminal jurisdiction; it supports the identity theft criminal investigation and prosecution through which of the following?
A. FTC Consumer Protection Partners
B. FTC Identity Theft Data Clearinghouse
C. NIST Identity Theft Data Clearinghouse
D. NIST Cybersecurity Framework
Exercises
Exercise 13.1: Identifying Regulatory Relationships
Access the official websites of the Federal Reserve Board (FRB), the Federal Deposit Insurance Corporation (FDIC), the National Credit Union Administration (NCUA), and the Office of the Comptroller of the Currency (OCC) and write a brief synopsis of the mission of each agency.
For each agency, identify at least one financial institution (within a 50-mile radius of your location) that it regulates.
In matters of cybersecurity, should it matter to consumers who regulates the financial institution they use? Why or why not?
Exercise 13.2: Researching the FTC
Visit the official FTC website and write a brief synopsis of its mission.
Prepare a summary of FTC cybersecurity resources for business.
Prepare a summary of an FTC GLBA-related enforcement action.
Exercise 13.3: Understanding the Federal Register
Locate a Federal Register copy of the Interagency Guidelines Establishing Standards for Safeguarding Customer Information.
Highlight the actual regulations.
Prepare a brief explaining the other sections of the document.
Exercise 13.4: Assessing GLBA Training
Go online and find publicly available GLBA-related cybersecurity training.
Go through the training and make a list of the key points.
Did you find the training effective? Why or why not?
Exercise 13.5: Researching Identity Theft
Document the steps consumers should take if they have been or suspect they have been the victims of identity theft.
Document how a consumer reports identity theft to your local or state police.
Document how a consumer files an identity theft complaint with the FTC.
Projects
Project 13.1: Educational Institutions and GLBA
Educational institutions that collect, process, store, and/or transmit nonpublic personal student information, including financial records and SSNs, are subject to GLBA regulations.
Locate documents published by your school that relate to compliance with GLBA. If you are not a student, choose a local educational institution. GLBA compliance documentation is generally published on an institution’s website.
Evaluate the documentation for clarity (for example, is it written in plain language? is it easy to understand and relate to?) and content (does it address the objectives of the Safeguards Act?). Make suggestions for improvement.
Prepare a training session for new faculty and administration that describes the school’s GLBA compliance policy and standards. Include an explanation of why it is important to safeguard NPPI.
Project 13.2: Exploring the FFIEC Cybersecurity Assessment Tool
The FFIEC developed the Cybersecurity Assessment Tool to help financial institutions identify their risks and assess their cybersecurity maturity. The Cybersecurity Assessment Tool is aligned with the principles of the FFIEC Information Technology Examination Handbook (IT Handbook) and the NIST Cybersecurity Framework.
Access and review the FFIEC Cybersecurity Assessment Tool at https://www.ffiec.gov/cyberassessmenttool.htm.
Explain how a financial institution must demonstrate its cybersecurity maturity.
Explain and provide five examples of how the FFIEC Cybersecurity Assessment Tool maps to the NIST Cybersecurity Framework.
Project 13.3: Assessing Risk Management
According to the FFIEC Cybersecurity InfoBase Handbook (Appendix A), the initial step in a regulatory Information Technology Examination is to interview management and review examination information to identify changes to the technology infrastructure, new products and services, or organizational structure.
Explain how changes in network topology, system configuration, or business processes might increase the institution’s cybersecurity-related risk. Provide examples.
Explain how new products or services delivered to either internal or external users might increase the institution’s cybersecurity-related risk. Provide examples.
Explain how loss or addition of key personnel, key management changes, or internal reorganizations might increase the institution’s cybersecurity-related risk. Provide examples.
Case Study
The Equifax Breach
The Equifax breach was one of the most catastrophic cybersecurity breaches in recent history. This is because if you are a United States citizen and have a credit report, there’s a good chance that you’re one of the 143 million American consumers whose sensitive personal information was exposed. Equifax is one of the three major credit reporting agencies in the United States.
The breach lasted from mid-May through July 2017.
Threat actors exploited a vulnerability in Apache Struts (CVE-2017-5638) disclosed and fixed several months prior to the attack.
Threat actors accessed people’s names, social security numbers, birth dates, addresses and, in some instances, driver’s license numbers. The Federal Trade Commission (FTC) confirmed that the threat actors also stole credit card numbers for about 209,000 people and dispute documents with personal identifying information for about 182,000 people. Nonpublic information of individuals in the UK and Canada was also compromised.
Equifax created a website to guide their customers and help them assess if they have been impacted at https://www.equifaxsecurity2017.com.
What guidance and requirements from the regulations described in this chapter could’ve prevented this breach?
References
Regulations Cited
“12 U.S.C. Chapter 18: Bank Service Companies, Section 1867 Regulation and Examination of Bank Service Companies,” accessed 06/2018, https://www.gpo.gov/fdsys/pkg/USCODE-2010-title12/html/USCODE-2010-title12-chap18-sec1867.htm.
“Standards for Safeguarding Customer Information; Final Rule - 16 CFR Part 314” accessed 06/2018, https://www.ftc.gov/policy/federal-register-notices/standards-safeguarding-customer-information-final-rule-16-cfr-part.
“Appendix B to Part 364: Interagency Guidelines Establishing Information Security Standards,” accessed 06/2018, https://www.fdic.gov/regulations/laws/rules/2000-8660.html.
“Financial Institution Letter (FIL-49-99), Bank Service Company Act,” accessed 06/2018, https://www.fdic.gov/news/news/financial/1999/fil9949.html.
“Financial Institution Letter (FIL-44-2008), Third-Party Risk Guidance for Managing Third-Party Risk,” accessed 06/2018, https://www.fdic.gov/news/news/financial/2008/fil08044.html.
“Supplemental Guidance on Internet Banking Authentication, June 28, 2011,” official website of the FFIEC, accessed 06/2018, https://www.ffiec.gov/press/pr062811.htm.
Other References
“Start with Security: A Guide for Business,” The Federal Trade Commission, accessed 06/2018, https://www.ftc.gov/startwithsecurity.
Financial Services Information Sharing and Analysis Center (FS-ISAC), accessed 06/2018, https://www.fsisac.com.
“FFIEC Cybersecurity Assessment General Observations,” accessed 06/2018, https://www.ffiec.gov/press/PDF/FFIEC_Cybersecurity_Assessment_Observations.pdf.
FFIEC IT Booklets and Handouts, accessed 06/2018, https://ithandbook.ffiec.gov/it-booklets.aspx.
FFIEC Cybersecurity Assessment Tool Frequently Asked Questions, accessed 06/2018, https://www.ffiec.gov/pdf/cybersecurity/FFIEC_CAT%20FAQs.pdf.
“Consumer Information—Identity Theft,” official website of the Federal Trade Commission, accessed 06/2018, www.consumer.ftc.gov/features/feature-0014-identity-theft.
“FFIEC Information Technology Examination Handbook: Information Security,” September 2016, Federal Financial Institutions Examination Council, accessed 06/2018, https://ithandbook.ffiec.gov/ITBooklets/FFIEC_ITBooklet_InformationSecurity.pdf.
“The NIST Cybersecurity Framework and the FTC”, Federal Trade Commission video, accessed 06/2018, https://www.ftc.gov/news-events/blogs/business-blog/2016/08/nist-cybersecurity-framework-ftc.
“Fraud Advisory for Business: Corporate Account Takeover,” U.S. Secret Service, FBI, IC3, and FS-ISAC, accessed 06/2018, https://www.nacha.org/content/current-fraud-threats-resource-center.
“Reporting Identity Theft,” official website of the Federal Trade Commission, accessed 06/2018, https://www.identitytheft.gov.
Gross, Grant, “Banks Crack Down on Cyber-based Account Takeovers,” IDG News Service, January 9, 2013, accessed 06/2018, www.networkworld.com/news/2013/010913-banks-crack-down-on-cyber-based-265685.html.
“Identity Theft Impacts,” State of California Department of Justice, Office of the Attorney General, accessed 06/2018, https://oag.ca.gov/idtheft.
FTC Complaint Assistant, accessed 06/2018, https://www.ftccomplaintassistant.gov.
“Equifax Twice Missed Finding Apache Struts Vulnerability Allowing Breach to Happen,” SC Magazine, accessed 06/2018, https://www.scmagazine.com/equifax-twice-missed-finding-apache-struts-vulnerability-allowing-breach-to-happen/article/697693.
“The Equifax Data Breach: What to Do,” the Federal Trade Commission, accessed 06/2018, https://www.consumer.ftc.gov/blog/2017/09/equifax-data-breach-what-do.
“Equifax Says Hackers Stole More Than Previously Reported,” CNN, accessed 06/2018, http://money.cnn.com/2018/03/01/technology/equifax-impact-more-customers/index.html.
