The Linux books flooding your local bookstore are replete with installation chapters. If you're using Linux, you've probably already read a few. (I've read a dozen or so myself.) With that in mind, is an installation chapter really necessary?
I thought so, for several reasons. First, most installation primers don't focus on security. Second, many folks will buy this book prior to establishing their Linux network. And third, Linux security starts at installation, or even before.
However, instead of an installation how-to, this chapter focuses on installation issues that can affect your security:
At least 15 Linux distributions exist, and more will undoubtedly crop up by this book's release. These distributions all share some common characteristics: the same kernel releases, the same basic applications, and, with few exceptions, the same core source code.
This might persuade you that all Linux distributions are identical. Not true. Subtle differences do exist:
Different Linux distributions have different installation tools, and their functionality may vary. Some installation tools automatically specify which network servers activate on boot, and some don't. Others ask you.
Some installation tools drill down into individual packages so you can choose precisely what software is installed. Other installation tools offer less incisive scope, such as asking you which sets of software you'd like to install rather than which individual applications.
If you're new to Linux, these variables can affect your system's security. Frankly, you may end up with innumerable software packages and servers installed that you know nothing about.
This is a major problem facing Linux newcomers, and the publishing field hasn't helped. Although there are countless Linux primer books, few of them contain comprehensive lists of installable software. This leaves newbies in an odd position. Faced with choosing individual applications or installing the entire distribution, most will choose the latter.
Note
Older distributions, like early SlackWare, worked differently. The installation tool, based on shell scripts with a dialog front-end, paused at every application and utility, forcing you to choose whether to install it or not. Each dialog displayed the application's description per its Linux Software Map entry. This allowed you to ascertain each program's purpose and whether you needed it or not. Naturally, this made installation tiresome, but also far more incisive and informative.
Is it really so important that you understand precisely what you're installing? Yes, and here's why: Linux markedly differs from other operating systems in that no single entity controls development and testing. When you venture beyond Linux's kernel (the system's heart), Linux is composed of several thousand different tools, modules, libraries, and so forth.
Many of these components are derived from third-party, academic, freelance, and commercial developers all around the world. Each developer is responsible for their application's quality control, and hence your mileage may greatly vary. To understand why, please examine Figure 3.1.
Figure 3.1 shows various types of Linux software and an admittedly generalized critique of quality control at each level. Here's what it shows:
The Linux kernel and must-have tools have been rigorously tested for common programming errors that could potentially threaten system security. The folks doing this testing have a lot of experience and are familiar with Linux source and development history, particularly from a security standpoint.
Semi-commercial tools are tools that would be commercial on any other platform. Recently, there's been a huge influx of such tools as large corporate vendors move into Linux territory. These tools may have excellent security, but many probably don't. Porting complex commercial applications to Linux, a relatively new and unfamiliar operating system, is an error-prone enterprise. Furthermore, some vendors view Linux ports as policy decisions (testing the water) and allocate less time and effort to analyzing their port's security status, unless the application is specifically related to security.
Finally, beyond core Linux code and semi-commercial contributions lie freelance, beta, and other tools. This category already makes up a substantial portion of Linux and is growing rapidly. Testing here varies. Many new Linux tools are the result of the well-intentioned, enthusiastic efforts of budding programmers. Some have long UNIX experience and are well aware of security issues. Others may be just starting out.
As you move farther from Linux's basic core, you may reap increasingly disparate results—with the notable exception of security tools. Some Linux security tools have reached levels of excellence equaled only in high-performance, commercial security applications.
If you're using Linux for personal use, you can install the entire distribution without worry. Just employ good security practices, back up often, and be prepared to learn through trial and error.
However, if you're using Linux for enterprise or mission-critical tasks, and therefore cannot tolerate error, take a different approach:
Before employing Linux in your enterprise environment, learn a bit about software packages, what they do, how long they've been around, and whether you actually need them. For this, I recommend visiting the Linux Software Map at http://www.boutell.com/lsm/. The LSM is searchable, which is nice because there are currently about 3,000 entries.
If your Linux distribution includes proprietary tools, investigate their utility and security track record. See Appendix D, "Sources for More Information," for more information about each distribution (bug lists, revision tracking sites, bulletins, vendor advisories, and so on).
Beyond these steps, try adhering to this cardinal rule: Less is more. Try installing only what you need.
This can be difficult, especially if you've just discovered Linux. Linux offers a wide range of applications and multiple subsets within each application type. Thus, in addition to the dozen text editors available on your distribution's CD-ROM, there are probably 25 Linux text editors. That's a lot of choices.
In particular, be extremely careful when you're choosing networked applications (anything that relies on a daemon). If a networked application has flaws, it can expose your system to remote attack. No other operating system offers as many networked applications as Linux. Indeed, Linux developers have gone hog-wild, networking everything from CD players to scribble pads. If it can be networked at all, Linux surely has networked it.
In short, before you install Linux in an enterprise environment, take the time to read about it. It's worth the effort, and you'll find your research interesting and enlightening. Linux is an operating system that's rich with possibilities and that supports truly amazing applications. For example, do you need DNA-sequencing tools or a means to view molecular structures? No problem. Go to http://SAL.KachinaTech.COM/index.shtml.
Finally, I should point out that even given all this, when Linux is properly installed and maintained, it offers excellent security. You simply need a Linux security overview, which is what this book is for, after all. Let's get started.
During installation, Linux will prompt you to partition your hard drive. This section will examine how your partitioning approach can affect your security.
Partitions are areas on your hard drive that are reserved for file systems. Let's look at their relationship to your hard drive at large.
Hard drives are composed of one or more layers called platters. Older SCSI drives, in particular, often house multiple platters. Please see Figure 3.2.
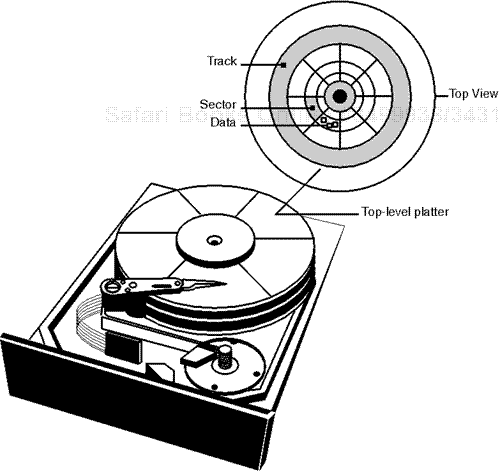
Each platter's surface vaguely resembles the surface of a vinyl record. Please see Figure 3.3.
As depicted in Figure 3.3, platters are covered by groove-like structures, circles that get increasingly smaller as they get closer to the center. The spaces between these circles are tracks. Tracks are divided into smaller units called sectors, which contain even smaller units that record data bits.
The total number of tracks that occupy the same region on all platters form a cylinder. Please see Figure 3.4.
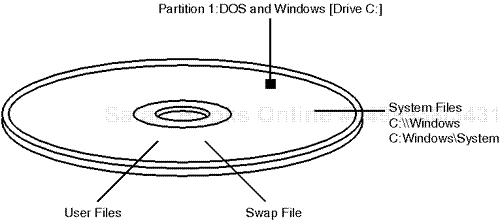
Partitions are composed of a user-specified range of contiguous cylinders. With DOS and Windows 3.11 in days of old (or even Windows 95's early release), users needed only one partition. This occupied virtually the entire disk and contained system files, user files, and swap files. Please see Figure 3.5.
Note
As hard drives larger than 2 gigabytes have become more affordable, this has changed. DOS/Windows and the first release of Windows 95 could only handle 2GB or less. Hence, to accommodate a large disk, you had to format it in 2GB partition increments, where your first partition would be Drive C:, your second partition would be Drive D:, and so on. Later releases of Windows 95 and Windows NT impose no such restriction.
In Linux, it's more common to have multiple partitions, primarily to maintain strict control over where data ends up. Normally, when you use only a single partition (as you would with DOS), your operating system writes data arbitrarily wherever it finds suitable space, and so do users. Eventually, your data becomes spread out, unmanageable, and disorganized.
In contrast, things are a bit more orderly when you create multiple partitions. For example, you can separate swap files from your live file system. Each partition exclusively owns a specific disk area. Figure 3.6 depicts a fairly common partitioning scenario.
Another common scenario is when you install two or more operating systems on the same disk drive but different partitions, and they can coexist problem-free.
Linux supports a wide range of partition types. Table 3.1 lists a few of the more interesting ones.
Table 3.1. Various Partition Types Supported by Linux
| Number | Partition Type |
|---|---|
| 2 | XENIX root, an antiquated, UNIX-based operating system for PCs that is rarely used today. It has a long history. Originally based on UNIX version 7, later incorporating features from BSD 4.1, and finally conforming to SYS V, XENIX has been marketed by many companies, including Microsoft and the Santa Cruz Operation (SCO). |
| 7 | The High Performance File System or HPFS, a fault-tolerant system that incorporates advanced caching, long filenames, and support for traditionally incompatible file structures. It is the basis for the OS/2 system. Learn more about HPFS at http://www.cs.wisc.edu/~bolo/shipyard/hpfs.html. |
| 8 | AIX (IBM UNIX). |
| 40 | Venix 80286, a System V-compatible version of UNIX from VentureCom. |
| 63 | GNU HURD, which hails from the Free Software Foundation and will eventually be a replacement for the UNIX kernel. To learn more about HURD, go to http://www.gnu.org/software/hurd/hurd.html. |
| 64 | Novell NetWare. |
| 81 | Minix. |
| 82 | Linux swap partition. |
| 83 | Linux nativepartition. |
| 93 | Amoeba, a distributed operating system that runs on SPARCstations (Sun4c and Sun4m), as well as the 386/486, 68030, Sun 3/50, and Sun 3/60. Amoeba is used to pool the power of multiple workstations into one powerful block of computing power. Learn more about Amoeba at http://www.cs.vu.nl/pub/amoeba/. |
Linux supports more partitions than those listed here. For a complete list, go to http://linuxclub.mnf.nu/lsa/lsg18.htm#E69E130. Also, for a complete list of all PC partition types (including those Linux does not support), go to http://www.win.tue.nl/math/dw/personalpages/aeb/linux/partitions/partition_types-1.html.
Many folks install both DOS/Windows and Linux on the same hard drive, on separate partitions. This offers them latitude and flexibility. They can learn Linux while still relying on Windows, and enjoy at least one-way compatibility. Please see Figure 3.7.
Although DOS and Windows cannot access the Linux partition, Linux can access the DOS partition, thereby allowing you to copy files back and forth across file systems.
Note
During installation, Linux asks you to specify additional or foreign file systems that you'd like to access. Linux mounts those file systems in the directory of your choice. A typical configuration would be to mount the DOS file system from Linux in /dos.
Linux newcomers often use the configurations depicted in Figures 3.6 and 3.7 because they're easy to implement. Many new Linux users are satisfied if they can just complete the installation with no problems, so they're apt to avoid more complicated partitioning schemes. Moreover, few installation routines highlight the relationship between partitioning and security, and give no hint that such configurations are risky. In fact, the scenarios depicted in Figures 3.6 and 3.7 expose your system to attack and hinder your ability to exercise effective system administration.
First, you should never put root and user file systems on the same Linux partition. If you do so, you increase the chance that attackers can exploit SUID programs to access restricted areas.
Note
SUID files are special in that they always execute with owner privileges, no matter who runs them. For example, if root owns a SUID program, that program will execute with root privileges and have considerable power to access, alter, and overwrite files that might otherwise be unreachable. If an attacker can exploit weaknesses in SUID programs, he can threaten the system at large. (Learn more about SUID programs in Chapter 4, "Basic Linux System Administration.")
Additionally, lumping Linux into a single native partition makes your life as a system administrator difficult. For example, it may hinder your ability to incisively update or back up individual packages or file systems. And when the full Linux system occupies one partition, even limited file corruption can cause systemic problems (meaning that one corrupted directory hierarchy can affect others). You may even have to reinstall.
To avoid these problems, create a separate partition for each major file system. Figure 3.8 depicts one possible configuration.
This enhances security and makes backups and recovery manageable. You can specify different backup schedules for different partitions, system files are separated from data files, and so on. This approach also allows you to exercise more stringent control over each file system and how it is mounted.
Note
The term mount refers to how Linux makes different file systems available to you. When Linux mounts a local or foreign file system, it attaches the system to a local device and/or directory. This gives you an access point. For example, to grant you access to your CD-ROM, Linux associates the CD-ROM drive with the device /dev/cdrom (usually), and you must specify a directory as the mount point (typically /mnt/cdrom or /cdrom). From that point on, your CD-ROM's top-level directory is accessible in /cdrom and its subdirectories are available beneath it (/cdrom/docs, /cdrom/install, /cdrom/source, and so on).
At system startup, Linux mounts all available file systems per the specifications set forth in /etc/fstab. You can use /etc/fstab to incisively control how users and the system access your partitions. Let's quickly cover /etc/fstab now.
/etc/fstab is the plain text file in which you specify file system mount options. Each line addresses one file system. For example, the following entry specifies mount options for an MSDOS file system mountable in /dos:
/dev/hda4 /dos msdos defaults 1 1
The line consists of six fields:
The file system specification—Here you specify either the block device or file system to be mounted—in this case, partition 4 on the first drive. This is what Linux will mount.
The file system file location—This is the mount point—in this case it's
/dos, a common naming for a DOS file system mount point, as discussed earlier.The file system type—In this field, you describe the file system's type—Minix, extended, DOS, HPFS, iso9660/CDROM, Network File System (NFS), or swap.
The file system mount options—Here you specify the level of access that users and the system will have on this mounted file system. Here's where security comes in. Your choices are as follows:
defaultsEverything (quota, read-write, and suid). noquotaNo quotas, generally. nosuidNo SUIDaccess.quotaQuotas are active. roRead-only. rwRead-write. suidSUIDaccess is okay.File system dump parameters—This is a numerical value to flag file systems that need to be dumped (backed up).
File system check sequence number—Here you specify the file system's priority for integrity checks performed by
fsck. (fsckis a file system integrity checker that examines file systems at boot by default.)
Where should you force a nosuid mount? Anywhere that local or remote users might be up to no good. For example, suppose that you anticipate providing anonymous FTP services (not a great idea). If so, consider creating a separate partition for this and have Linux mount it nosuid. This still allows data to be written but addresses the SUID problem.
So, multiple partitions offer you at least four advantages:
Easy backup and upgrade management
Faster booting (in some cases)
The ability to control how each file system is mounted
Protection against renegade
SUIDprograms
There are other advantages. One is that the multi-partition approach prevents accidental denial of service and shields your root file system from overflow. For example, /var stores logging information. If you have just a single partition containing root, /usr, /var, and /tmp, logs in /var can potentially flood your entire file system (and users can too).
As noted, new users sometimes shy away from multiple partitions (beyond swap and root). That's because creating multiple partitions forces you to make some hard choices. For example, just how large should each partition be? Unfortunately, there's no definite answer to this question except when you're dealing with swap and root partitions. Swap partitions should be 128MB or less, and root should have 64MB minimum, (although I allocate 100MB).
In respect to other file systems, you'll make your choices depending on different factors. One factor is what you intend to do with your Linux box. On a multi-user system, you'll want to give your users at least 20MB each (and probably more). Hence, for 10 users, you'll need a /home partition of at least 210MB.
Some of these values are interdependent. For example, if you're accommodating many users and providing mail and news services, your /var and /home partitions will need to be substantial. Unless, of course, users use third-party mail and news solutions. In that case, their messages will be stored in their /home/user directory, e.g. /home/user/.netscape/.
If you run a firewall, you'll need a large log directory hierarchy, and this should have its own partition. In fact, you may be forced to put this partition on a separate disk drive. That way you'll avoid losing valuable audit information if the primary file system is corrupted.
However, in most cases your largest partitions will house the /usr and /home directories. Let's look at a conservative example. Here's a df report from a 1.6MB IDE hard drive with a 128MB swap partition that isn't visible from the df query:
Filesystem 1024-blocks Used Available Capacity Mounted on /dev/hda2 66365 17160 45778 27% / /dev/hda5 373695 1549 352845 0% /home /dev/hda6 703417 344725 322356 52% /usr /dev/hda7 127816 21235 99981 18% /var /dev/hda8 123919 22 117498 0% /tmp
Here's the fstab information immediately after installation:
/dev/hda2 / ext2 defaults 0 1 /proc /proc proc defaults 0 0 /dev/hda1 none swap defaults 0 0 /dev/hda5 /home ext2 defaults 0 2 /dev/hda6 /usr ext2 defaults 0 2 /dev/hda7 /var ext2 defaults 0 2 /dev/hda8 /tmp ext2 defaults 0 2 # /dev/fd0 /mnt/floppy ext2 defaults,noauto 0 0 # /dev/hdb /mnt/cdrom iso9660 ro,noauto 0 0
Note partitions 5, 6, 7, and 8. These are logical partitions. You're allowed only four primary partitions in the Intel world, or three primary partitions, one extended partition, and multiple logical partitions. To create additional partitions, first establish an extended partition and then slice this into logical partitions using either fdisk or, if you have Red Hat, Disk Druid.
Caution
Some distributions offer user-friendly installation routines that automatically suggest disk layout (much like Sun's Solaris does). These routines are convenient, but think carefully before accepting such a partitioning scheme. Here's why: although you can incisively reformat separate partitions without affecting the entire system, once your partitions have all been sized, you cannot resize them. The exception to this is when additional, unpartitioned space still exists. However, from the outset you should create your partitions in sequential order with no gaps in between, unless you have a very good reason not to.
Although you've probably used fdisk already, some folks that have purchased this book may not have installed Linux yet. For their benefit, I'll briefly address fdisk here.
fdisk is a partition manipulator for Linux. During your installation, Linux will move you from a semi-graphical environment to a command-line interface so that you can partition your disks. At that point, you'll almost certainly be dealing with fdisk.
fdisk's initial prompt will look much like this:
Using /dev/hda as default device! The number of cylinders for this disk is set to 1579. This is larger than 1024, and may cause problems with: 1) software that runs at boot time (e.g., LILO) 2) booting and partitioning software from other OSs (e.g., DOS FDISK, OS/2 FDISK) Command (m for help):
Before continuing, if you're using fdisk for the first or even the fifth time, review the list of valid commands. That way, you can familiarize yourself with each one and reduce the chance of error. To view the complete command set, type m and press Enter. In response, fdisk will print a help menu:
Command action a toggle a bootable flag d delete a partition l list known partition types m print this menu n add a new partition p print the partition table q quit without saving changes t change a partition's system id u change display/entry units v verify the partition table w write table to disk and exit x extra functionality (experts only)
Also, examine the current partition table before you make any changes. That way, you can verify if any partitions already exist. To do so, type p and press Enter. If you're working with an unpartitioned disk, fdisk will print a blank table:
Disk /dev/hda: 32 heads, 63 sectors, 1579 cylinders Units = cylinders of 2016 * 512 bytes Device Boot Start End Blocks Id System Command (m for help):
Now you're ready to begin creating your partitions.
From here on, I'll stick with the values from the preceding partitioning example. You'll need to adjust partition sizes according to your own needs. This is merely a walkthrough that demonstrates how to create an extended partition and logical partitions within it. Few Linux how-to books address this issue. (Most such books focus on Red Hat installations. Red Hat includes Disk Druid, a semi-graphical tool that simplifies the process for you. However, you may be installing another distribution, one with command-line fdisk. If so, this next section will illustrate the steps required when you're creating such partitions by hand.)
First, you'll need to create your swap and root partitions. In this example, I'll assume that you're installing to a new hard drive, with no other existing file systems previously installed.
To create a new partition, type n and press Enter. In response, fdisk will ask you what style of partition you want. Type p and press Enter for primary:
Command Action
e extended
p primary partition (1-4)
p
fdisk will then ask you to number the new partition. This is your first primary partition and will house your swap file, so choose 1:
Partition Number (1-4): 1
Next, fdisk will ask you to specify where the partition starts. This is your first partition and you want to write it from the first cylinder onward, so choose 1:
First cylinder: (1-1579) 1
Finally, to complete the cycle, fdisk will ask you to size the partition. Swap file size is a matter of personal preference. In past years, Linux tutorials prescribed a ratio approach: "If you have 8MB of RAM, you'll need a 16MB swap file, minimum." Today, RAM is so inexpensive and folks have so much of it that this is unnecessary and, in many cases, impossible. Currently, Linux supports swap files of 128MB or less.
As per the preceding example, choose 128MB:
Last cylinder or +size or +sizeM or +sizek (1-1579): +128M
After you create each partition, reexamine the fdisk partition table. This way, if you make typographical errors, you can catch them before writing changes to disk. Here's what the updated table will look like after you create the first partition:
Command (m for help): p Disk /dev/hda: 32 heads, 63 sectors, 1579 cylinders Units = cylinders of 2016 * 512 bytes Device Boot Start End Blocks Id System /dev/hda1 1 130 131008+ 83 Linux native
Note that the partition is type 83 (Linux native). You need to change this. This partition is a swap partition, and you must manually designate it as such. To do so, type t and press Enter:
Command (m for help): t
In response, fdisk will prompt you for the partition number. Choose 1:
Partition number (1-4):1
Finally, fdisk will ask which partition type you want. Choose 82 to convert the partition to a Linux swap:
Hex Code (L to list): 82
When you reexamine the partition table, fdisk will reflect the changes:
Command (m for help): p Disk /dev/hda: 32 heads, 63 sectors, 1579 cylinders Units = cylinders of 2016 * 512 bytes Device Boot Start End Blocks Id System /dev/hda1 1 130 131008+ 82 Linux swap
Next, create the root partition. Here again, size is a matter of personal preference. You should allocate at least 32MB to root, although I've seen people make this partition as large as 100MB. In any case, the procedure is precisely the same. You start by creating a new partition. Type n and press Enter. Then fdisk will ask what style of partition you'd like. Again, type p and press Enter for primary:
Command Action
e extended
p primary partition (1-4)
p
Then fdisk will ask you to number the new partition. This will be your second primary partition, so choose 2:
Partition Number (1-4): 2
In response, fdisk will ask you to specify where the partition starts:
First cylinder: (131-1579)
Note that the first valid starting cylinder is now 131. That's because your swap partition occupies cylinders 1 through 130. Therefore, you'll start your root partition at cylinder 131:
First cylinder: (1-1560) 131
And finally, fdisk will ask you to size the partition. For this example, allocate 64MB:
Last cylinder or +size or +sizeM or +sizek (131-1579):+64M
The results show a Linux (type 82) swap partition and a root (type 83) partition:
The next step is to create an extended partition that will occupy the remaining disk space. To create an extended partition, type n and press Enter (new), and then choose e for extended:
Command Action
e extended
p primary partition (1-4)
e
Here, fdisk will ask you to specify the extended partition's first cylinder. In this case, the first available cylinder is 199, so choose that:
First cylinder: (199-1579):199
Finally, fdisk will ask you to specify the extended partition's last cylinder. In general, you should go with the very last cylinder. That way, the extended partition occupies the remaining disk space. However, you choose to leave some space at the end of the disk, so specify cylinder 1560:
Last cylinder or +size or +sizeM or +sizek (199-1579): 1560
Here are the results:
Command (m for help): p Disk /dev/hda: 32 heads, 63 sectors, 1579 cylinders Units = cylinders of 2016 * 512 bytes Device Boot Start End Blocks Id System /dev/hda1 1 130 131008+ 82 Linux swap /dev/hda2 131 198 68544 83 Linux native /dev/hda3 199 1560 1372896 5 Extended
The table now shows one Linux swap, one Linux native, and one Linux extended partition. Your remaining task is to allocate several logical partitions.
Now that fdisk is aware of an extended partition, the fdisk menu will change. To create your first logical partition (for /home), type n and press Enter. In response, fdisk offers a new menu. Here, choose l for logical:
Command Action
l logical (5 or over)
p primary partition (1-4)
l
Then fdisk will ask you to specify the new logical partition's first cylinder. Note that the first available cylinder is 199, which is the same first available cylinder that you specified for the extended partition. That's because your logical partitions will lie on top of the extended partition. So choose 199:
First cylinder: (199-1579):199
Finally, fdisk will ask you to specify this logical partition's last cylinder. To give /home 370MB, choose 581:
Last cylinder or +size or +sizeM or +sizek (199-1579): 581
Here are the results so far:
Command (m for help): p Disk /dev/hda: 32 heads, 63 sectors, 1579 cylinders Units = cylinders of 2016 * 512 bytes Device Boot Start End Blocks Id System /dev/hda1 1 130 131008+ 82 Linux swap /dev/hda2 131 198 68544 83 Linux native /dev/hda3 199 1560 1372896 5 Extended /dev/hda5 199 581 386032+ 83 Linux native
You add the remaining partitions, /usr, /var, and /tmp, in the same fashion. Here's the sequence for /usr:
Command Action l logical (5 or over) p primary partition (1-4) l First cylinder: (582-1579):582 Last cylinder or +size or +sizeM or +sizek (581-1579): 1302
Here's the sequence for /var:
Command Action l logical (5 or over) p primary partition (1-4) l First cylinder: (1303-1579):1303 Last cylinder or +size or +sizeM or +sizek (1303-1579): 1433
And finally, the sequence for /tmp:
Command Action l logical (5 or over) p primary partition (1-4) l First cylinder: (1433-1579):1303 Last cylinder or +size or +sizeM or +sizek (1433-1579): 1560
When you view the final results, fdisk will reflect the following changes:
Command (m for help): p Disk /dev/hda: 32 heads, 63 sectors, 1579 cylinders Units = cylinders of 2016 * 512 bytes Device Boot Start End Blocks Id System /dev/hda1 1 130 131008+ 82 Linux swap /dev/hda2 131 198 68544 83 Linux native /dev/hda3 199 1560 1372896 5 Extended /dev/hda5 199 581 386032+ 83 Linux native /dev/hda6 582 1302 726736+ 83 Linux native /dev/hda7 1303 1433 132016+ 83 Linux native /dev/hda8 1434 1560 127984+ 83 Linux native
Once you've achieved and verified your desired results, choose w. This will exit fdisk and permanently commit these changes to disk. Linux will then return you to the main installation program.
Note
Some Linux installation programs won't force a reboot after fdisk changes. I strongly recommend that you force a reboot on your own to ensure that changes are properly written to disk. To be extra careful, also consider verifying that the changes were actually committed to disk, even after rebooting.
Not every Linux installation program directs you to fdisk for partitioning. Instead, you may end up working with cfdisk or Disk Druid. These tools are much easier to use.
cfdisk is a Curses-based partition manipulator for Linux.
Note
Curses is a development package for creating menu-based programs on UNIX terminals. Curses applications vaguely resemble old DOS programs, in that you can navigate menu choices by using arrow keys. Traditional Curses applications have a black background and white foreground. Menu choices appear in white until highlighted with a white bar, at which point the highlighted text turns black. Learn more about Curses programming at http://aotech1.tuwien.ac.at/~dusty/ncurses-intro.html.
cfdisk presents a comfortable and easy-to-navigate interface. Please see Figure 3.9.
For the most part, you'll have no trouble navigating cfdisk using arrow keys—the program provides ample help along the way. However, I've provided a summary of important cfdisk keystrokes and their functions in Table 3.2. This is in the event that on your first installation, you're forced to use cfdisk but have little or no accompanying documentation—a common problem.
Table 3.2. Keystroke Commands in cfdisk
Disk Druid, common to Red Hat installation as a fdisk alternative, is even easier to use. The application is entirely graphical. Please see Figure 3.10.
To add your partitions, highlight the Add button and press Enter. In response, Disk Druid displays a dialog box with all the options you'll ever need. Please see Figure 3.11.
Because partitioning has a strong bearing on your system security, you should carefully weigh your options before installation. Making your final decisions will never be easy.
Balancing disk load is probably the most challenging aspect of partitioning, particularly with smaller disks. By creating multiple partitions, you limit each file system's ability to grow. In certain instances, of course, that's exactly what you want. However, it's irritating to later discover that you failed to allocate adequate disk space.
One thing that can help is to know each major file system's purpose. Here they are, in short order:
Disk balancing also gets easier if you develop policies for a consistent application set. For example, perhaps you limit third-party software to Netscape Communicator, StarOffice, and Corel WordPerfect. This eliminates the need for a large /var partition and gives you a ballpark figure on how large /opt has to be.
Of course, there's no law mandating that you create a dozen partitions. The partition parameters in the preceding examples are for demonstration purposes only. You can get along nicely with just three partitions, especially if only a few trusted users have access to your Linux system. Only you can accurately assess how many partitions you'll need and which file systems to segregate.
Here are some closing tips:
You may prefer fewer partitions, or you may want to prioritize file systems that must or should be segregated. If so, the important file systems to house on separate partitions are root (
/),/var, and/tmpfrom a security viewpoint, or root (/),/var, and/usrfrom an administrative viewpoint. At bare minimum, I strongly advise housing root on its own partition.If you allocate partitions to non-Linux operating systems, carefully consider how you want Linux to mount them. For example, suppose you have a small Windows partition at the beginning of the disk. If you use this partition almost exclusively when in Windows, consider having Linux mount it read-only or not at all. That way, you protect it from either accidental or intentional damage.
If you're running a firewall, sniffer, or other network-monitoring device, funnel logs to their own partition (preferably on another disk).
Exercise care when setting partition mount options. Sometimes, restrictive policies can lead to administrative headaches. For example, suppose you decide to lump contributed binaries into
/usr/localand have Linux mount/usr/localread-only. Later, this may hamper your ability to perform upgrades without first redefining the mount option.
Finally, here are some resources for more information on partitioning:
Debian Linux Installation & Getting Started by Boris D. Beletsky (
[email protected]). The author takes you through each step of installation, with special focus on disk partitioning. Find it at http://www.ssc.com/lg/issue15/debian.html.Linux Installation and Getting Started by Matt Welsh. Although slanted heavily toward SlackWare, this document is superb, stepping through every aspect of installation and partitioning in excruciating detail. Find it at http://durak.org/sean/pubs/ligs-slackware/node1.html.
The Linux Disk HOWTO by Stein Gjoen (
[email protected]). The author discusses drive geometry and structure, disk layout, partitioning, and so forth, in great detail. Find it at http://www.memphisonline.com/linux/mirror/HOWTO/Disk-HOWTO.html#toc18.The Linux Partition HOWTO by Kristan Koehntopp (
[email protected]). The author discusses important issues about disk balancing, partition sizes, and so on. Find it at http://sunflower.man.poznan.pl/LDP/HOWTO/mini/Partition.html.White Paper for PartitionMagic 3.0 Optimizing Hard Drives with Partitions, PowerQuest Corporation. The authors discuss partitioning related to security and disk management. Find it at http://support.powerquest.com/white1.html.
As noted earlier, Linux supports many network services. Your job is determining which ones you need. Network services come in two basic flavors:
Services that deliver information to clients for human consumption. For example, a Web server, which allows users to download documents and media.
Services that deliver information to clients or hosts for network and operational purposes. For example, Dynamic Host Configuration Protocol, which automatically sets up clients' network configuration.
Network services that provide people with data or functionality are generally not essential. Instead, they are privileges and niceties that you afford your users, and you'd profit by viewing them that way. Indeed, because almost every service you run will complicate system administration and security, the fewer you allow the better. Here are some non-essential services that provide people with data or functionality:
bootpd—A server that can implement the bootstrap protocol, which allows you to boot diskless clients from a server. During startup, a diskless client queries the server and discovers its IP address. It also loads any files specified by the server. (Typically, the server forwards a boot program.) Don't runbootpdif you don't need it.fingerd—Thefingerserver, which gathers personal information on specified users, including their username, real name, shell, directory, and office telephone number (if available). On request,fingerdforwards this information to anyone using afingerclient. Here's an example of whatfingerdreturns:Login name: unowen In real life: U. N. Owen Directory: /home/unowen Shell: /sbin/sh On since Feb 3 18:13:14 on pts/15 from ppp-208-19-49-133.samshacker.net Mail last read Wed Feb 3 18:01:12 1999
This isn't essential by any means. In fact, it may expose your users and your Linux server to unwanted invasions of privacy. Disable
fingerdunless you have a good reason not to. To do so, comment it out in/etc/inet.dby placing a # symbol at the beginning of the finger definition line).ftpd—File Transfer Protocol (FTP), which provides standard file transfer over internetworks. Today, there's less reason to run an FTP server. The WWW has made it easy to distribute files using HTTP, which most users are more familiar with anyhow. If you are going to provide FTP services, see Chapter 11, "FTP Security."gopherd—Gopher server. Gopher, developed at the University of Minnesota, is a document distribution system and the Web's predecessor. Gopher servers are often used to distribute textual information. However, many modern Web browsers support Gopher protocols, so you can use Gopher to distribute other media too. You'll probably never use Gopher, though, so you might want to give it a pass.httpd—The Hypertext Transfer Protocol server. This is your Web server. Without a doubt, you'll want to provide at least limited Web services. Check Chapter 14, "Web Server Security," for ways to tighten access control and general Web security.nfs—Network File System, a system that allows you to transparently import files from or export file systems to remote hosts. These files appear and act as though they were installed on your local machine. NFS is useful in many situations. For example, if you're hosting Web servers for third parties (running a Web farm), you can run exports to a RAID server. That way, all user Web directories are actually stored on a single server, redundant and prepared for possible individual host failures. To users, who maintain their own Web pages, everything appears to be local when they telnet or FTP into their co-located box.NFS has many other uses, too. However, if you don't need it, don't install or enable it. NFS has some security issues, even though secure NFS systems do exist. Learn more in Chapter 15, "Secure Protocols."
nntpd—Network News Transfer Protocol server. This is the Usenet news server. Today, most people get Usenet news from their ISP's feed, so there's little reason to run NNTP yourself.rlogind—Therlogin(remote login) server.rloginis anrservice that allows users to conduct remote terminal sessions, much like telnet does. A major difference betweenrloginand telnet is thatrloginallows users to set up passwordless access on trusted hosts with trusted users. You probably don't want this.rshd—The remote shell (rsh) server.rshallows users to execute commands on remote hosts runningrshd. This is a member of therservices family (rsh,rlogin, and so on), which is a notorious security hazard. Carefully consider whether you need to provide such services.talkd—Thetalkserver.talkis an interactive chatting system for Linux that splits each user's screen in half. The top half echoes the requesting party's keystrokes, and the bottom echoes the responding party's keystrokes. Is this essential? Hardly. However, if your system is in-house (not wired to the Net), you might want to keeptalkfor quick interdepartmental communication.telnetd—The telnet server. Although telnet can increase risk, it is indispensable for some administrative tasks, so you'll probably want it. Check Chapter 13, "Telnet Security," for ways to lock down telnet and keep it useful but safe.tftp—Trivial File Transfer Protocol (TFTP). TFTP is an antiquated means of transferring files. You probably don't need it.
These are just a few examples. A default installation could result in many more non-essential services cluttering up your system and eroding its security. For this reason, whenever possible, you should run a verbose installation and explicitly reject packages that you don't need.
Boot loaders are small programs that manage the boot process. If you've worked with Windows NT, you've had some experience with a boot loader. At startup, NT's boot loader asks what operating system you'd like to boot to.
In Linux, the most commonly used boot-loading tool is LILO, the Linux Loader. During installation (typically at the very end), Linux will generate LILO values and ask you to verify them. At that time, you are given the opportunity to insert additional LILO boot options. For example, perhaps you have additional partitions and operating systems you'd like to add. This way, during system startup you can choose which operating system to use for that session.
LILO reads its options from /etc/lilo.conf, the LILO configuration file. /etc/lilo.conf provides an option for a boot password. Let's quickly cover that now.
After installation, your /etc/lilo.conf will contain values for boot images, target drives, and the root partition. Here's the /etc/lilo.conffrom the drive partitioned in the preceding example:
#
# general section
#
boot = /dev/hda
install = /boot/boot.b
message = /boot/message
prompt
# wait 20 seconds (200 10ths) for user to select the entry to load
timeout = 200
#
# default entry
#
image = /vmlinuz
label = linux
root = /dev/hda2
read-only
#
# additional entries
#
Let's quickly familiarize you with /etc/lilo.conf and its contents. This way, when you edit it, you'll feel confident that you're making the right changes. Table 3.3 lists some commonly used options for /etc/lilo.conf.
Table 3.3. Commonly used /etc/lilo.conf options
To add a password to your /etc/lilo.conf, insert a line like this:
password=123456
This will prevent local users from booting Linux without a password. Note that the password will not be encrypted. Therefore, ensure that /etc/lilo.conf is owned by root and set to mode 600. If you don't, malicious users may later obtain your LILO password.
You may later decide not to use LILO. After all, it's not the only boot manager out there. Consult your boot loader documentation to see whether it also supports password protection. Every layer counts.
And finally, note that the /etc/lilo.conf password option does not prevent attackers from booting with a floppy. If your BIOS/PROM offers an option to disable floppy diskette boots, use it.
Try to tailor your installation to meet your Linux server's essential needs, and discard the rest. There is no prescribed set of rules for this. Ascertaining those needs is an undertaking that demands skill, organization, and clear goals. Particularly when you're employing Linux in enterprise environments, you should outline how the server will be used, who will use it, and what data it will serve.
The next chapter departs from preliminary security measures (physical security, installation, and so on) in favor of old–fashioned system administration.