

GENAPP introduction
The scenarios in this IBM Redbooks publication use a general insurance application available with IBM GENAPP SupportPac CB12, which can be found on the following website:
The General Insurance Application GENAPP is an IBM Customer Information Control System (CICS) Transaction Server (CICS TS) Common Business Oriented Language (COBOL) application that simulates transactions made by an insurance company to create and manage customer and insurance policy data. It provides sample data and an IBM 3270 interface for creating and inquiring on customers and insurance policy information.
This chapter introduces the components of the application and its topology. To install and set up the application, see Appendix A, “Setup and environment” on page 207.
This chapter contains the following topics:
2.1 CICS TS topology
GENAPP can be installed into a stand-alone CICS TS region System Management Single Server (SMSS) that is not managed using CICSPlex SM. However, the concepts of applications and platforms discussed in this IBM Redbooks publication require the region to be managed by IBM CICSPlex System Manager (CICSPlex SM). Therefore, all steps in the scenarios are applied to a single region, but it is still a part of a CICSPlex, and is referred to as a single managed region.
In addition, the scenarios separate the GENAPP application into a CICS TS topology consisting of three different types of CICS TS regions:
•Presentation
•Application services
•Data access
Chapter 3, “Creating a platform” on page 25 shows how to create a development platform, where all three region types are provided by a single managed region, and a test platform, where each region type has its own CICS TS region, connected using multiregion operation (MRO) or Internet Protocol interconnectivity (IPIC). One might imagine a production platform taking this a step further, and having multiple regions for each region type, with requests dynamically routed between the CICS TS regions.
Figure 2-1 shows the infrastructure of the example used in this IBM Redbooks publication, where the single managed region is used for development, the simple CICS TS topology for test, and the full CICSPlex SM topology in production.
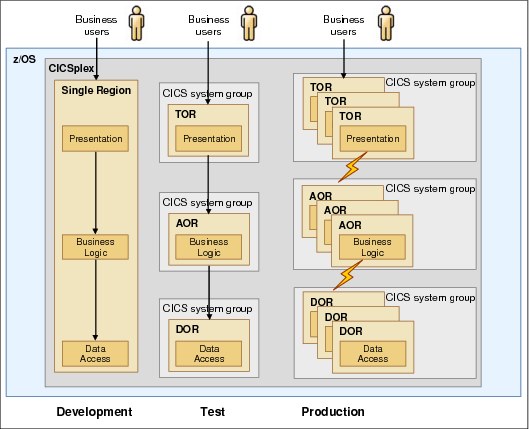
Figure 2-1 CICS TS environments used in this IBM Redbooks publication
|
Important: Although outlined in Figure 2-1 on page 16, this IBM Redbooks publication will not cover the production scenario. You will work with GENAPP in development and test.
In an actual environment, those different environments would not be part of the same CICSPlex.
|
To install GENAPP to a single managed region and a CICS TS topology, see Appendix A, “Setup and environment” on page 207.
If you follow the instructions described in Appendix A, “Setup and environment” on page 207, you will have defined some CICS TS system groups to logically group regions of the same type together in the CICSPlex, as shown in Figure 2-2:
•GENATOR
•GENAAOR
•GENADOR
•GENAALL
Chapter 3, “Creating a platform” on page 25, takes you through the process of adding more CICS TS system groups to enable a single managed region to be used as a development platform with three different region types, as shown in Figure 2-1 on page 16.

Figure 2-2 CICS TS system groups defined during the installation of GENAPP
2.2 Application architecture
This section describes the basic architecture of GENAPP as it has been used for this IBM Redbooks publication.
2.2.1 GENAPP in a single managed region
GENAPP can be divided into two different application parts:
•The customer application to inquire and add customers
•The insurance policy application to inquire, add, update, and delete policies
The scenarios in this book use the customer application part of GENAPP.
Figure 2-3 shows the architecture of this part of the application.
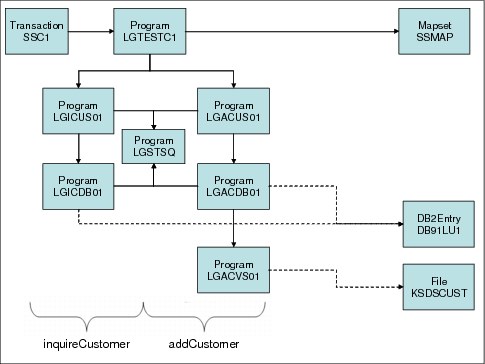
Figure 2-3 Customer application part of GENAPP
The following prefixes are used:
•LGI prefixes inquiry
•LGA prefixes add
LGSTSQ is a utility program used by most of the other programs. Figure 2-4 shows a part of a visualization from CICS Interdependency Analyzer (IBM CICS IA®) that collects information about the customer application part of GENAPP. The LGSTSQ program does not show up, because IA only collects programs that ran at run time. LGSTSQ is only called in case of
an error.
an error.
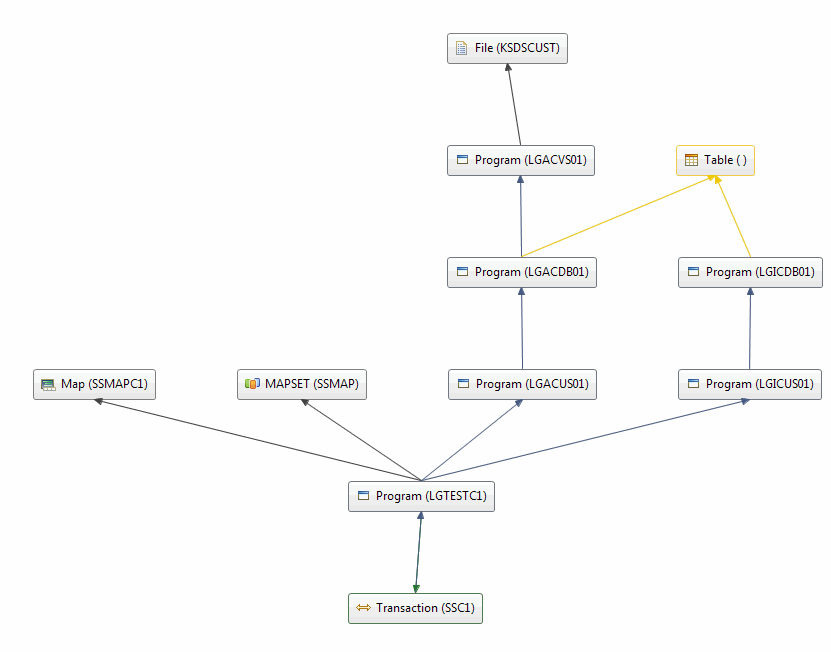
Figure 2-4 CICS IA visualization of GENAPP customer part
2.2.2 GENAPP in a CICS TS topology
Figure 2-5 shows GENAPP deployed across a test platform consisting of three different region types (where each region type consists of a single CICS TS region), as described in Chapter 3, “Creating a platform” on page 25. This strategy separates the different layers into unique address spaces:
•Presentation layer, or terminal-owning region (TOR)
•Application services (business logic) layer, or application-owning region (AOR)
•Data access layer, or data-owning region (DOR)
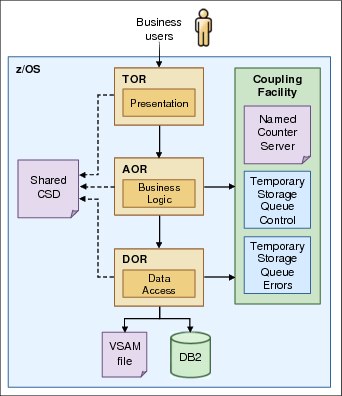
Figure 2-5 CICS TS topology connected by MRO
|
Remember: This scenario assumes that you are using a shared CICS system definition (CSD) data set as a repository, rather than CICSPlex SM Business Application Services (BAS) to define resources to CICS TS, but either approach is equally valid.
|
As outlined in Figure 2-6, the application design means that it can easily be separated into presentation, business, and data access logic.
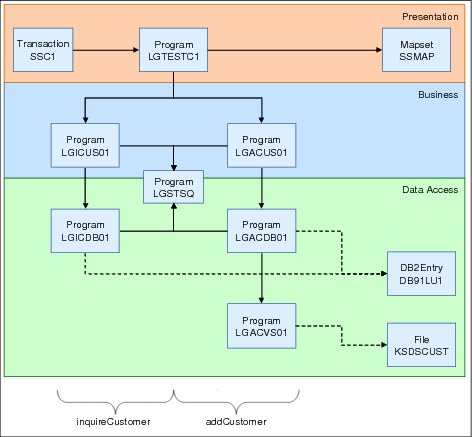
Figure 2-6 GENAPP customer application part: Separated
The GENAPP artifacts is distributed among those layers in the following ways:
•The presentation layer contains the following definitions:
– Transaction definitions
– Local program definitions for the presentation logic (LGTESTC1 and the BMS program SSMAP1)
– Remote program definitions to route work to the application services layer (LGICUS01, LGACUS01)
•The application (business) services layer contains the following definitions:
– Local program definitions for the business logic (LGICUS01, LGACUS01)
– Remote program definitions to route work to the data access layer (LGIDDB01, LGACDB01, LGACVS01)
•The data access layer contains the following definitions:
– Local program definitions for the data access logic (for example, LGIDDB01, LGACDB01, LGACVS01)
– Definitions for data to be accessed (VSAM file KSDSCUST, DB2Connection and DB2Entry)
|
Fast Path: The local program definitions can be omitted if the CICS TS autoinstall program function is enabled.
|
Figure 2-7 shows the topology in a CICSPlex SM context.

Figure 2-7 CICS TS topology in the context of CICSPlex SM
2.3 Limitations of the current design
This section provides information about some limitations in the current design of the GENAPP application, and how these can be addressed using CICS TS cloud capabilities.
2.3.1 Meaningful names
Strict naming conventions enable you to derive the functions of the programs, transactions, and other resources used in GENAPP. But eight characters (or even four, in the case of transactions) do not allow for much flexibility. For example, it would be much more meaningful to identify resources as part of the GeneralInsuranceCustomer application in SMF data, in addition to knowing that they ran under the SSC1 CICS TS transaction.
Chapter 4, “Creating an application” on page 51 addresses the concept of applications.
The same applies to the underlying CICS TS infrastructure, for example, it would be more meaningful to deploy part of the application onto the ApplicationServices regions rather than the CICSAAOR CPSM system group.
Chapter 3, “Creating a platform” on page 25 addresses the concept of platforms.
2.3.2 Taking the application through the lifecycle
From a CICS TS perspective, GENAPP currently consists of a load library and some CICS TS resources (programs, transactions, files, IBM DB2 connection, and entries). Although these CICS TS resources are organized in groups and lists, it is not possible to manage them as a single entity after installation.
A connection between resources can only be concluded manually from the carefully designed naming conventions (programs starting with LGIC belong to the customer application). This makes it a challenge to perform some tasks, such as removing the application from CICS TS.
Chapter 6, “Packaging an application for multiversion deployment” on page 127 describes how to package resources and code as an entity.
2.3.3 Managing updates to GENAPP
CICS TS resource names have historically had to be unique within a CICS TS region. This makes it impossible to run two versions of GENAPP on the same CICS TS region if they have the same named CICS TS programs and transactions. This in turn makes it difficult to update the application without affecting its availability to users. Sometimes, if a change is to a single CICS TS program, NEWCOPY can be used to update just that module, but when changes affect more than one resource, this approach can lead to inconsistent results.
Chapter 6, “Packaging an application for multiversion deployment” on page 127 describes how to package application resources, such that multiple versions of the application can be deployed into the same CICS TS regions.
Chapter 9, “Application lifecycle management” on page 193 provides information about the value in being able to deploy multiple versions of the same application.
2.3.4 Dependencies
Currently, there is no way to make the availability of a CICS TS program dependent on a CICS TS resource, such as a file or DB2 connection. Chapter 4, “Creating an application” on page 51 describes how to declare application dependencies.
2.3.5 Multiple region separation
As discussed in section 2.2.2, “GENAPP in a CICS TS topology” on page 19, it is a manual process to distribute the definitions among the different regions. This topology uses one single CSD that requires that different lists be maintained to separate resources dedicated to specific types of regions. This is addressed by the introduction of application bindings in Chapter 4, “Creating an application” on page 51.
2.3.6 Control of resource usage
The GENAPP application makes DB2 calls, and accesses a CICS TS Virtual Storage Access Method (VSAM) file. In addition, requests into GENAPP are from a user, who expects a response within a reasonable period of time. A sysprog might want to protect the CICS TS regions from changes to GENAPP that result in it making an excessive number of DB2 or FILE access calls, or using too much processor or elapsed time. Chapter 5, “Applying a policy” on page 97, demonstrates how this can be achieved using threshold policies.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
