

Cloud enabling your CICS TS applications
IBM Customer Information Control System (CICS) Transaction Server (CICS TS) for z/OS is the premier application hosting platform for IBM z/OS for high-volume updates to shared data. It is designed to enable customers to create and maintain a competitive advantage by building custom, differentiated CICS TS applications.
For many decades, IBM has continuously delivered market-leading CICS TS technologies that companies have built upon to differentiate themselves in the marketplace. As technology has evolved to deliver increasingly complex, interconnected, and distributed services, the industry has developed new approaches to building these solutions.
The introduction of service-oriented architectures (SOA) laid the foundation for what has become the next transformational era in technology, as businesses around the world seek to deliver solutions based on the principles of cloud computing. CICS TS V5 takes the concepts and values promised by cloud computing, and provides new cloud capabilities designed to increase operational efficiency and service agility without going off-premise.
This IBM Redbooks publication introduces the concepts that form the foundations of the cloud capabilities in CICS TS. It also provides real examples of how to take an existing CICS TS topology and application and apply these capabilities to it, using the General Insurance Application (GENAPP) support pack.
1.1 Did you know?
CICS TS is used by businesses around the world to deliver mission-critical applications and services. With a heritage that spans over 40 years, CICS TS is unparalleled in the industry, delivering a mixed-language transaction processing and application hosting platform.
Although it might have been around longer than most, CICS TS is no stranger to new technologies, offering users the following advantages:
•Multiple languages
– Java
– C++
– Common Business Oriented Language (COBOL)
– PHP
•A broad range of connectivity and integration options
– Web services
– Representational State Transfer (RESTful) web services
– Database connectivity
– Messaging integration
•Security
•An advanced multi-threaded run time (with transaction isolation and storage protection)
•Event processing
•Exceptional scalability (customers regularly drive 1 billion+ transactions per-day)
•Integration with the broad range of IBM application development and lifecycle management tools
In the era of cloud and mobile, CICS TS delivers the essential services necessary to build robust, mission-critical applications. The cloud capabilities introduced in CICS TS V5 are the next logical step in the evolution of the CICS Transaction Server, offering increased efficiency and agility to the enterprise.
1.2 Business value
CICS Transaction Server V5 has been designed to address the following main challenges that customers are facing today:
•Ongoing operational pressure to drive down costs and improve efficiency
•Increased business pressure to deliver faster and with greater agility
•The ability to manage and use the rapidly changing technology landscape
Cloud computing, although it is a relatively new concept, offers many values that existing CICS TS users claim to enjoy already, so why introduce new cloud-style concepts into CICS TS today? At a high level, these concepts are being introduced because cloud is more than just a technology.
Cloud offers a conceptual shift in how a business delivers services. It promises increased operational efficiency over the management and operation of these services, and increased agility when developing and deploying them. By introducing cloud capabilities, CICS TS enables both new and existing customers to gain the benefits offered by cloud computing, while maintaining the solid foundation that CICS TS offers.
Specifically, CICS TS provides the following cloud capabilities and benefits:
•Platforms as first-class entities
First-class platforms enable the creation of agile service delivery runtimes. CICS TS regions can be grouped as platforms for rapid application deployments, decoupling applications from the underlying topology, which increases flexibility.When regions within a platform are started, applications are deployed to them, without any further interaction from a system administrator. In turn, reliability is increased by automatic resource validation, provisioning, and de-provisioning. Platforms can be managed dynamically by applying policies during run time.
•Applications as first-class entities
First-class applications enable the creation of agile services from new or existing assets. Disparate application resources can be combined and managed as a single entity, which can be versioned and rapidly moved through the development, test, and production lifecycle. Using applications improves dependency management, and entire applications can be measured for resource usage and internal billing. Applications can be managed dynamically by applying policies during run time.
•Policy-based operations
Automated control over critical system resources can now be managed using policies. Task thresholds can be set for data access requests, storage usage, program loops, and processor time used. Policy breaches can be managed by issuing messages, using tasks to cause an abnormal end (abend), or emitting events that can trigger further actions. Policies can be applied dynamically during runtime operation.
These three capabilities, when combined with the existing features of CICS Transaction Server, provide the building blocks to enable you to transform your existing CICS TS topologies and applications into cloud-style platforms and services.
1.3 Solution overview
This IBM Redbooks publication begins by examining the National Institute of Standards and Technology (NIST, part of the US Department of Commerce) Special Publication (SP) 800-145 recommendations, which represent the widely accepted definition of cloud computing:
This book compares these recommendations to the existing features and capabilities that CICS TS offers. As you will see, the strong heritage that CICS TS has, positions it extremely well as a cloud platform.
Having understood how CICS TS relates to the concepts of cloud, this book proceeds to look at each of the features introduced in CICS TS V5 that support its cloud capabilities:
•Chapter 2, “GENAPP introduction” on page 15 introduces the GENAPP in detail, covering the application’s current topology and architecture. This application is the bedrock for all later chapters in this book, and is used to demonstrate how existing applications can quickly benefit from the additional offerings provided by the CICS TS cloud.
•Chapter 3, “Creating a platform” on page 25 introduces the platform concept, describing the role of platforms as a host for applications and provider of application services. This chapter also details the components of the platform, then provides an introduction to the concept of a development platform. It also provides a step-by-step guide to define, deploy, and install this platform.
•Chapter 4, “Creating an application” on page 51 introduces the application concept, and explores the business value of, and the components that make up, an application. This chapter also provides a step-by-step guide to define, deploy, and install an application. The created application is built around GENAPP, introduced in Chapter 2, “GENAPP introduction” on page 15.
•Chapter 5, “Applying a policy” on page 97 introduces the new policy capabilities, and how these can be applied to provide more efficient operation in the CICS TS cloud. This chapter also provides a step-by-step guide to define, deploy, and add your policies to both platforms and applications.
•Chapter 6, “Packaging an application for multiversion deployment” on page 127 expands on the application defined in Chapter 4, “Creating an application” on page 51, and introduces the concept of application multi-versioning. This chapter walks you through the process of repackaging your application resources, and of rolling out a new version while the previous version is still active.
•Chapter 7, “Measurement by application” on page 175 explains how to take advantage of the application context for performance monitoring and chargeback. This chapter describes the improvements over traditional techniques, and provides examples using the application introduced in Chapter 2, “GENAPP introduction” on page 15.
•Chapter 8, “Managing by policy” on page 181 looks again at policies in more detail from a cloud perspective. This chapter examines the types of policies, and the actions that can be taken when a policy rule is breached. It looks at scoping policies for platforms and applications, and provides good usage scenarios.
•Chapter 9, “Application lifecycle management” on page 193 provides information about application versioning in more detail. This chapter explains semantic versioning, and takes the application introduced in Chapter 2, “GENAPP introduction” on page 15 through various upgrade scenarios, from releasing a new application version to version backout.
1.4 Cloud computing in a CICS TS context
When planning and implementing CICS Transaction Server for z/OS, version 5.1, the CICS TS design and development team used many different sources to establish and validate the new features that make cloud computing real to customers embracing the product. This included other IBM product and solution experts, industry experts outside of IBM, IBM Business Partners, and clients.
This provided a tremendous amount of insight into what the generally accepted principles of cloud computing are, and also validated that existing CICS TS capabilities were an excellent foundation on which to build additional new features that would transform the CICS TS application-management and system-management facilities to meet the expectations of a cloud computing platform.
During this design process, NIST issued its definition of cloud computing.
This document recommends five essential characteristics, three service models, and four deployment models related to cloud computing. These recommendations are aimed at an audience of system planners, program managers, technologists, and others adopting cloud computing as consumers or providers of cloud services. They provide a reference point for discussion of CICS TS V5.1 cloud enablement features.
The NIST Special Publication acknowledges that cloud computing is an evolving paradigm, and does not intend to prescribe or constrain any particular method of deployment, service delivery, or business operation.
Cloud computing essential characteristics
As CICS TS V3 did for service orientation and the IBM SOA reference architecture, CICS TS V5 takes accepted principles and enables them to be realized in a manner suited to the existing business application assets and system deployment styles used across thousands of CICS TS installations. The aim is to enable the positive outcomes associated with cloud computing to be gained in an incremental and easily managed fashion, minimizing cost
and disruption.
and disruption.
The five essential characteristics recommended by NIST provide a good basis to evaluate how CICS TS V5 enables these outcomes:
•On-demand self service
•Broad network access
•Resource pooling
•Rapid elasticity
•Measured service
|
Definition: The following definition is the first essential characteristic from the NIST SP 800-145 recommendations:
On-demand self-service A consumer can unilaterally provision computing capabilities, such as server time and network storage, as needed automatically without requiring human interaction with each service provider.
|
In a CICS TS context, the processes used to provision services vary widely from installation to installation. It is overwhelmingly common that business stability, audit, and other regulatory requirements demand highly stringent testing and validation of both application and system changes before they are deployed into production.
However, there are competing demands on skills and cycle times that are motivating a need to enable more rapid deployment of new or modified services, or additional system capacity in simplified and more responsive ways. Some installations have very mature and responsive processes to satisfy these needs, while others suffer from bottlenecks in processes, or are constrained in other resources, such as skilled staff.
An outcome enabled by CICS TS V5 is a simpler, more repeatable, and more controlled deployment process that provides a balance between the demands for business agility and the real demands for resilience and stability. New first-class management objects for application assets and system resources enable a more effective separation of concerns between application developers, deployers, and system provisioning and operations staff.
Consumers benefiting from such features might be application developers who require the provisioning of systems for development and unit-test activities, or line-of-business consumers requiring new or changed services to be rolled out to end-users.
|
Definition: The following definition is the second essential characteristic from the NIST SP 800-145 recommendations:
Broad network access Capabilities are available over the network and accessed through standard mechanisms that promote use by heterogeneous thin or thick client platforms (e.g., mobile phones, tablets, notebooks, and workstations).
|
Recent versions of CICS TS, especially version 3 and later, have greatly expanded the range of protocols and formats that can be used to expose business services from the application assets that it hosts. Service-enablement options have been heavily used by most customers, commonly using synchronous request-reply styles over Transmission Control Protocol/Internet Protocol (TCP/IP) or message-based asynchronous styles with IBM WebSphere MQ.
Services to clients can be made available using structured payloads, such as SOAP, according to tightly specified definitions, such as Web Services Description Language (WSDL). These services are subject to rigorous governance using service registries, or more informally provided using the principles of the RESTful style. Another outcome enabled by CICS TS V5 is that the development and deployment process for service enablement to achieve broader network access is simplified as application assets become better defined, with a better managed lifecycle and explicit versioning.
|
Definition: The following definition is the third essential characteristic from the NIST SP 800-145 recommendations:
Resource pooling The provider’s computing resources are pooled to serve multiple consumers using a multi-tenant model, with different physical and virtual resources dynamically assigned and reassigned according to consumer demand. There is a sense of location independence in that the customer generally has no control or knowledge over the exact location of the provided resources but may be able to specify location at a higher level of abstraction (e.g., country, state, or datacenter). Examples of resources include storage, processing, memory, and network bandwidth.
|
The invention of the class of platform known as a transaction processor was to provide more efficient use of precious computing resources, and to scale to meet the demands of global enterprises. CICS TS, the z/OS operating system, and IBM System z hardware practically define the gold standard for a mission-critical, mixed-workload application hosting platform.
The concept of a CICS TS transaction and its context has been an effective declaration of an application as a tenant in a multi-tenant environment from the inception of CICS TS. Within
a single server, CICS TS has control of the dispatching and resource allocation to tasks running the transaction. Features, such as hardware-mediated transaction isolation, support the requirements for multiple requests to share resources without the risk of compromising each other.
a single server, CICS TS has control of the dispatching and resource allocation to tasks running the transaction. Features, such as hardware-mediated transaction isolation, support the requirements for multiple requests to share resources without the risk of compromising each other.
The adoption of the CICS TS Open Transaction Environment (OTE) style of execution, which enables workloads to scale more effectively with the hardware cores provided by System z and z/OS, has meant that single CICS TS regions can provide many more millions of instructions per second (MIPS) to any given workload. Recent use of the expanded storage available to a region in the 64-bit address space means that those MIPS can be used to serve the ever-growing storage needs of today’s applications.
CICS TS exploitation of z/OS Parallel Sysplex topologies has meant that it can support very large workloads with stringent high-availability (HA) requirements. IBM CICSPlex System Manager (CICSPlex SM) works in partnership with z/OS Workload Manager (WLM) to achieve both efficient use of resources for workloads classified as the most critical, and continuation of service during planned or unplanned outages of processing resources.
Although the exploitation of OTE and Sysplex-enablement features is a partnership between CICS TS and the applications, the results are immediate benefits to the service consumers. There is no need for a consumer to be aware of their request being one of a few hundred or thousand such requests per day, or one of a billion or so.
CICS TS V5.1 provides new policy-based control of these resources in terms of the applications running on platforms. This enables the outcome of improved control of pooled resources, such as processing power and storage. For example, 24-bit storage is often a constraint on the workload that an individual region can support. Programming standards can be in place to restrict or prohibit use of this type of storage, but old applications might not have been modified to eliminate its use.
It is possible to define a policy that tracks and limits 24-bit storage on a task-by-task basis. Older applications might need to be enabled to have a limited amount of such storage, but new or well-maintained applications could be banned from allocating any. It is also possible to associate different threshold policies with each application to accommodate their varying demands.
|
Definition: The following definition is the fourth essential characteristic from the NIST SP 800-145 recommendations:
Rapid elasticity Capabilities can be elastically provisioned and released, in some cases automatically, to scale rapidly outward and inward commensurate with demand. To the consumer, the capabilities available for provisioning often appear to be unlimited and can be appropriated in any quantity at any time.
|
With today’s demand for 24 x 7 availability, and the exposure of services to ever-wider groups of consumers to use as and when they expect to use the service, the need to be ready for a workload spike is a common requirement.
The ability for regions to scale, and for workload management to prioritize critical requests to maintain service levels, is provided by the resource pooling capabilities of CICS TS. However, long-term capacity management will inevitably demand a more dynamic environment, with the number of regions growing and shrinking to match demand.
In the past, an installation’s capacity could largely be measured by the number of regions employed. Region usage and topology patterns could also be a measure of the resilience and sophistication of the design of the applications and infrastructure.
As a consequence of regions as the unit-of-scale in infrastructure terms, it is not surprising that in many cases it is a region-centric view of capacity that dominates, and decisions to provision and decommission regions are inelastic. This can lead to suboptimal infrastructure deployments and inefficiencies.
By creating a new management object (a platform) over the individual regions, but one
which fully embraces the reality of the structure of types of regions within the platform topology, CICS TS V5 is anticipating a future where regions or entire platforms are more actively managed on a day-by-day basis according to need, but without requiring a large provisioning effort.
which fully embraces the reality of the structure of types of regions within the platform topology, CICS TS V5 is anticipating a future where regions or entire platforms are more actively managed on a day-by-day basis according to need, but without requiring a large provisioning effort.
A common example where more dynamic management of regions and platforms has a positive outcome is the provisioning of development and test regions. If an infrastructure process makes it burdensome to request resources for each project to use for development and test, projects are likely to retain those resources for longer than is optimal.
Alternatively, a more dynamic environment promotes flexibility to give up under-utilized resources on the understanding that they can be easily reacquired when necessary. This leads to a net reduction in the overall resource consumption, while maintaining an agile development environment.
|
Definition: The following definition is the fifth essential characteristic from the NIST SP 800-145 recommendations:
Measured service Cloud systems automatically control and optimize resource use by leveraging a metering capability at some level of abstraction appropriate to the type of service (e.g., storage, processing, bandwidth, and active user accounts). Resource usage can be monitored, controlled, and reported, providing transparency for both the provider and consumer of the utilized service.
|
As noted previously, the measurement and reporting on a transaction-oriented basis has long been a strength of CICS TS. However, as the transaction view of the world has been superseded by a service-oriented view, there has been a need to deal in more expressive terms than a four-character transaction name.
In recent releases, CICS TS has improved the transaction-tracking capabilities for both monitoring and problem resolution purposes. Now with CICS TS V5.1, the application provides a context that is a better reflection of the business view of the application.
Every release brings new metrics for resource usage or time spent in certain functions. For example, in CICS TS V5.1, new data is available to account for time spent running on a general-purpose processor versus time on a specialty engine for each task in the CICS TS monitoring records. This is a finer-grained accounting than was previously possible with the address space IBM z/OS Resource Measurement Facility™ (RMF™) data.
Comparing with other cloud solutions
Many other cloud technologies currently do not support the same granularity of provisioning. They commonly define entire virtualized application stacks, including operating system (OS), middleware, database, and application, as a single deployable package.
This use case is valid, because applications are defined on virtualized UNIX or Windows servers. However, it does not match the long-established, mixed-workload efficiency design point of the z/OS operating system and CICS TS.
The platform and application specifications that are provided by CICS TS V5.1 enable the existing system programmers to own, structure and maintain platforms, with the applications owned and maintained separately. All such assets are appropriate for formal maintenance using your source code change management tools and processes.
The move to more clearly differentiate platforms from the applications that are hosted on them can provide motivation for more clearly differentiated roles for staff involved in the creation, deployment, maintenance, and operation of the platforms and applications.
It can be common for the staff maintaining the CICS TS system infrastructure to be closely involved in the design and deployment of applications. In addition, application developers are relatively unfamiliar with some of the important resource usage and binding concerns that are resolved as the application is deployed.
A better distinction between these concerns is being enabled with the platform and application patterns implemented in CICS TS V5.1. Existing system programmers would likely be ideal candidates to own platforms, but the ownership of applications should be more closely aligned with the application development team.
However, it is not proposed that every application developer needs to become an expert in the definition of the new resources or the new threshold policies. The distinct role of application deployment, especially to production platforms, might be best given to staff in a newly identified role of Application Deployer. Of course, in some cases this might just be formalizing an informal but well-understood role that exists in your organization.
1.5 Overview of the cloud-enabling technologies in CICS TS V5
As explained previously, in many respects deploying CICS TS platforms and applications is an evolution of the existing leading practices enhanced with new management objects (namely platforms, applications, and policies). This evolution has been achieved by building on some solid foundations.
Platforms have been created by employing the foundations of CICSPlex SM topology definitions, such as System Groups (CSYSGRP), and the operations to deploy and manage both platforms and applications built on the single-point-of-control capabilities of CICSPlex SM. It is a prerequisite to deploy CICSPlex SM to fully use the cloud enablement features of CICS TS V5.
The rich objects introduced in CICS TS V5.1 demand the facilities of a similarly rich user experience, such as that provided by the IBM CICS Explorer and CICS Explorer® software development kit (SDK). Applications, platforms, and policies are defined using Extensible Markup Language (XML) files, of a similar style to those already used for bundle-based deployment of web services and event processing in Version 3 and Version 4.
The CICS Explorer SDK provides wizards for creation, editors for easy maintenance of the assets, and export capabilities that simplify the deployment of the assets into a runtime environment.
1.5.1 Platform overview
Platforms are a prerequisite for hosting applications, providing well-defined scopes called region types, for the installation of application resources. Platforms can additionally host policies and services, or declare dependencies for existing services. They also provide a single point of reference for status about system activity and services.
Figure 1-1 shows an existing three-tier CICS TS region topology managed by a CICS TS platform. Superficially, this does not look much different from an existing CICSPlex management structure. However, the difference becomes apparent when we start to appreciate how CICS TS can use these artifacts to simplify the management of both the CICS TS regions and the applications that run within them.
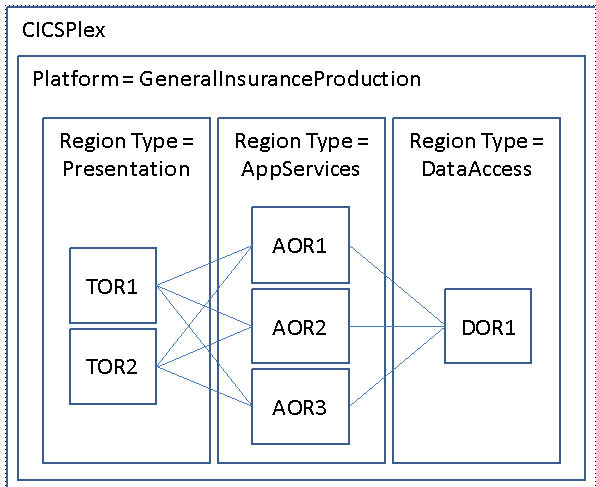
Figure 1-1 Conceptual diagram of existing CICS TS region topology managed by a CICS TS platform
The most obvious new element in Figure 1-1, aside from the platform itself, is the region type. A region type is a logical grouping of a collection of CICS regions that share common characteristics. In the example here, we have defined three region types to represent the three-tier nature of our application:
•Presentation
•Application logic
•Data
How you choose to define a region type is up to you, so you might also choose to have a region type of PayrollApplication, or perhaps to represent different geographical areas. There is a great deal of flexibility about how you define a region type, and we explain this in detail in Chapter 2, “GENAPP introduction” on page 15.
One of the powerful features of the platforms becomes apparent when you enable or disable the platform resource. When a platform is enabled, CICS TS automatically enables any bundle resources that were installed with the platform, for example, policies across the CICS TS regions in the appropriate region type. We look at policies in more detail in Chapter 4, “Creating an application” on page 51.
1.5.2 Application overview
Applications provide a powerful and capable container around CICS TS bundled resources. These resources track the application lifecycle, from installation to eventual discard. They can host resources, application dependencies, and policies. The overall health of these can be tracked using the application’s status.
The application can additionally provide entry points, whose declared operations, for example QueryCustomer or AuthorisePayment, can be used for simple and accurate resource monitoring and billing through System Management Facilities (SMF) records. Policies can also be deployed as part of an application to take effect only on those tasks related to specific operations. Finally, applications support advanced multi-versioning, enabling the user to simultaneously run current and newly patched versions of the same application.
Figure 1-2 shows an example application and an accompanying binding. The application is itself a collection of CICS TS bundles, each of which define or import a set of resources. Imported resources enable the application to declare a dependency on a specific resource that is not defined by this application, for example a file that is shared by multiple applications.
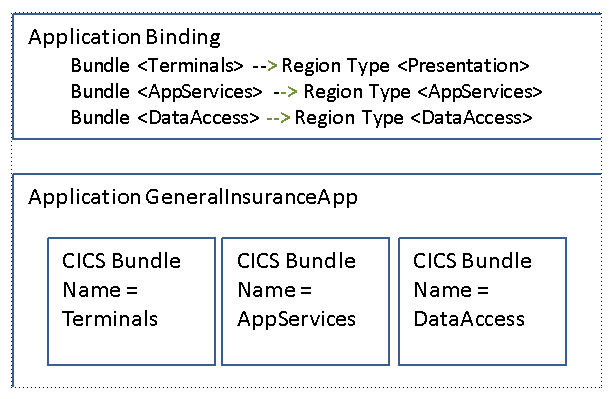
Figure 1-2 Conceptual diagram of an application and application binding
The application binding is used by CICS TS when an application is deployed onto a platform. It enables CICS TS to manage the installation of the application’s resources into the appropriate CICS TS regions managed by the platform. As you can see, the binding represents the mapping of an application component, for example Terminals, to the associated region type, in this case Presentation.
When an application is installed onto a platform, CICS TS ensures that all of the resources that the application depends upon (imports) are available in the regions of the target region type. If a resource cannot be located, the application reports a failure.
Chapter 4, “Creating an application” on page 51 explains applications in more detail.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
