CHAPTER 10
Asset Management
The fundamental objective of an information assurance management program is to protect the confidentiality, integrity, and availability of an organization’s assets throughout the life cycle in accordance with the MSR model. A best-practice security risk assessment exercise begins with an identification of the assets, followed by an evaluation of the asset sensitivity and criticality. This ensures that asset protection is proportional to the asset value.
In Chapter 2, when discussing the IAMS, we noted that each information asset has its life cycle. At any stage of the life cycle, the asset is constantly at risk. In fact, asset management is among the early activities in the IAMS.
This chapter explores the broad area of information assets. It first explains the types of assets and discusses the various responsibilities associated with them. The rest of the chapter focuses on information classification, handling, and labeling, which are core activities in asset management.
Types of Assets
Assets are tangible or intangible. Tangible assets range from data files to physical assets, such as computer peripherals, while intangible assets include the image and reputation of the organization, general utilities, and skill sets of a workforce. As mentioned in the ISO/IEC 27000 family of standards, assets can be categorized as shown in Table 10-1.
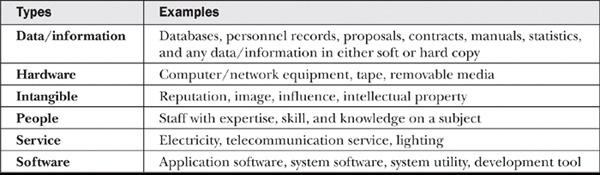
Table 10-1 Types of Assets
Tangible asset values can be quantified for the organization. For example, a server has a certain monetary replacement cost. This cost is part of its value. Next, the server is critical for providing e-commerce billing services to an organization’s web site. If it is down, the organization loses money for every missed sale. This is also a quantifiable value and can be added to the server’s total value. Finally, the configuration of the server may be proprietary or an industry trade secret. While the research used to develop the server configuration has a cost, if the proprietary configuration were stolen, the impact to the company because of increased competition could be immeasurable or extremely hard to quantify and therefore intangible.
Responsibilities for Assets
The objective of assigning responsibilities for assets is to assure adequate levels of protection. The responsibility of controlling an asset should be assigned to an identified individual or entity within an organization. This assignment is both risk management and security responsibilities. Asset responsibility provides accountability for the protection of the assets under the individual’s control. Protection includes appropriate information assurance and access control failures resulting in unauthorized access to and use of the assets.
Three controls are required to assign responsibility: inventory of assets, ownership of assets, and acceptable use of assets (see ISO/IEC 27002). Collectively or individually, implementation of these controls allows an organization to establish a suitable asset protection process.
Inventory of Assets
The organization establishes a baseline by identifying and recording important information about assets such as their location, license information, and security classification or categorization. Placing data into categories is the core of the asset management process, which ensures that movement of assets and changes to its information are documented and updated regularly. Following this process ensures that important information about the asset is available readily.
Ownership of Assets
It is important to establish that each asset has an assigned owner. An owner can be an individual or a functional role (for example, the head of finance). Designation as an “owner” means that the individual or party is responsible for the security of the asset and assigns ultimate accountability. The owner ensures that assets are classified properly and asset use authorizations are reviewed periodically. The owner can delegate the implementation of information assurance to someone else; however, the overall accountability remains with the owner.
Acceptable Use of Assets
To protect organizational assets, develop and document policy and guidelines for acceptable asset use. Ensure that the policy is endorsed by senior management. The policy elaborates on the rules and responsibilities of asset usage by internal and external parties in accordance with the security classification of the asset. Groups of assets with similar categorizations may be covered by a similar policy. For example, several different assets categorized as sensitive and mission critical may be covered by the same policies and associated procedures. Additionally, disclosure and release of information should be defined in policies and procedures. The use of nondisclosure agreements and information disclosure processes should be cited in asset use policies. The data owner recommends the parameters of acceptable use for their assets based on the services from the MSR model.
Information Classification and Handling
![]()
The rationale behind information classification (categorization) is to organize information according to its sensitivity and criticality of its loss, disclosure, modification, and unavailability. Once information is classified based on its value or impact to the organization, decide on the controls to be implemented to protect it. In addition, information classification is to indicate the level of confidentiality, integrity, and availability required for information protection. Protecting information assets is resource intensive; ensure the investment made is cost-beneficial to the organization. Conducting an information classification exercise ensures that data is protected cost-effectively. To achieve these objectives, two controls should be in place, namely, classification guidelines and information labeling and handling.
Classification Guidelines
Establishing an information classification system in an organization based on information needs and the impact in case of an information security breach or compromise is essential.
When developing and maintaining information, consider security classification and information assurance requirements from the organization perspective. Above all, identify information owners and involve them in providing input about the value or impact of the information. Business, industry, and legal requirements are other important decision criteria that should be supported by professional legal advice. Consider the organizational culture to allow effective implementation of the information classification policies and guidelines.
The originator of the information is responsible for classifying (categorizing) the information and protecting it according to the organization’s policy and procedures. There are also cases where the information assurance unit is tasked to classify the information. Information should be made available only to those authorized individuals.
Organizations must perform the classification process on a regular basis to take into account the life cycle of the information and its application. The life cycle shown in Figure 10-1 starts from the creation of information, implementation of the access control, method of processing, and eventually information disposal. The access control associated with the classification should comply with the access control policy of the organization.
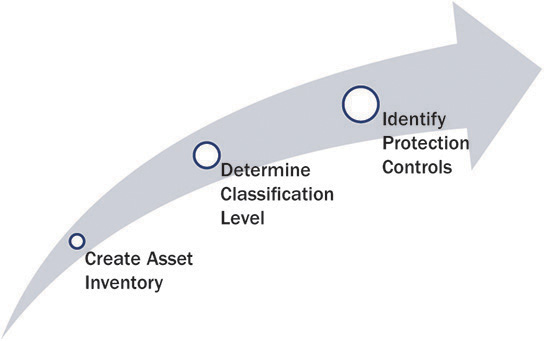
Figure 10-1 Information classification steps
Information Labeling and Handling
The sharing of information among organizations and individuals has become critical for the success of today’s businesses. Therefore, a proper and structured labeling scheme and handling mechanism is essential to secure and preserve an organization’s information assets. Information may be handled between different organizations, different components within an organization, or even different security levels within a system.
An organization should develop detailed information handling procedures derived from the organization’s policy on classification. For confidentiality, most organizations have adopted four levels of information classification: secret, confidential, restricted, and public. Other classifications are used for integrity and availability. The definitions of the classification and methods of processing, transmission, storage, accessibility, and disposal have to be documented by the organization. The procedure should cover physical assets and information kept or transferred in electronic formats such as e-mails and paper documents. Properly labeled assets encourage better handling and management by employees and partners.
In the U.S. government, the importance of information assurance in government operations is described at length in the Federal Information Security Management Act (FISMA). According to the act, measures should be taken to ensure the confidentiality, integrity, and availability of information. These measures are necessary to raise the confidence of the public and to promote usage of IT in industries such as commerce, healthcare, education, and public sector. The following example shows how information classification (categorization) is performed for civilian systems in the U.S. government.
Information Classification (Categorization) Example
It is useful to categorize assets so management can focus on protecting the most important ones. This process of categorization is often called classification. One best-practice example comes from the United States, where civilian agencies are required to adhere to the Federal Information Security Management Act. This law directs the U.S. National Institutes of Standards and Technology (NIST) to develop standards and guidelines for U.S. civilian agencies to follow. These standards cover the life cycle of information and the systems that are processing, storing, and transmitting information on behalf of the U.S. government. NIST has standards and guidelines specifically developed for information categorization and control selection. It is important to note that NIST uses the term categorization in lieu of classification. In the United States, classification is usually reserved for systems related to national security. While the terminology differs, the process is the same.
The NIST standards and guidelines are freely available online (http://csrc.nist.gov/publications/PubsFIPS.html). These standards and guidelines may be adopted in whole or partially by any organization at no cost, but they are mandatory for U.S. civilian agencies. The following example will use a sample of fictional information and explain how the categorization system operates.
Assume an information system is being designed for basic human resources (HR) functionality. This system will perform the following HR functions:
• Offboarding (removing employees from system)
• Onboarding (enrolling new employees into system)
• Payroll
• Personnel actions (including discipline)
• Suitability decision retention
• Time and attendance
According to FISMA, U.S. agencies must use Federal Information Processing Standard (FIPS) 199 to determine the categorization of the information. You can find the standard at http://csrc.nist.gov/publications/fips/fips199/FIPS-PUB-199-final.pdf.
In addition, agencies must use NIST Special Publication (SP) 800-60 to categorize their information. SP 800-60 contains numerous types of information and provides provisional impact (value) levels for each type. You can find SP 800-60 at http://csrc.nist.gov/publications/nistpubs/800-60-rev1/SP800-60_Vol1-Rev1.pdf.
Using SP 800-60 Vol. 2: (http://csrc.nist.gov/publications/nistpubs/800-60-rev1/SP800-60_Vol2-Rev1.pdf), the information owner or the information assurance support team determines the following information types are being processed, stored, and transmitted by the information system:
• Compensation management information
• Employee performance management information
• Financial reporting and information
• Organization and position information management
• Separation management information
• Staff acquisition information
When using NIST SP 800-60 and FIPS-199, the information assurance team must understand that the “impact” has been calibrated to the U.S. government. Therefore, a “high” impact means a loss of confidentiality, integrity, or availability would have catastrophic impact to the U.S. government. This means lives are at risk or the government is at risk of failure. Organizations must understand the impact in terms of their own mission and adjust accordingly. The process is diagramed in Figure 10-2.
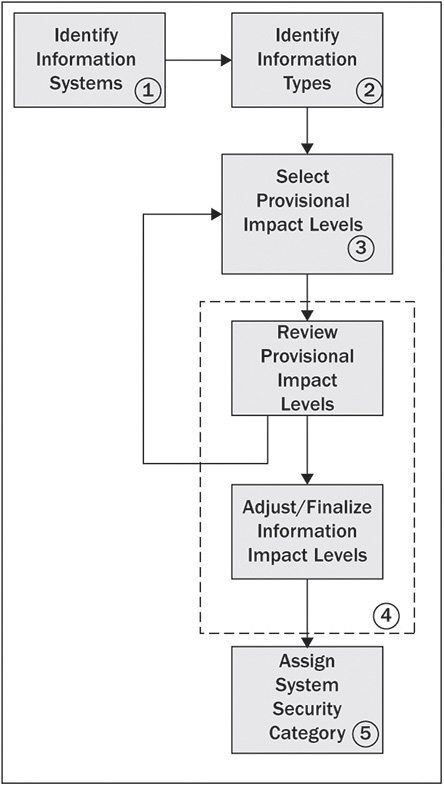
Figure 10-2 NIST SP 800-60 categorization process
NIST SP 800-60 provides provisional impact ratings for confidentiality, integrity, and availability. The impact ratings are provisional because they can be modified depending on special factors. Per NIST’s example, “Accounting information may have a provisional impact rating of ‘moderate’; however, if the accounting information contains proprietary information about an organization’s research and development, it may be adjusted to ‘high.’” Table 10-2 explains the impact levels for each security objective based on U.S. law for U.S. civilian agencies.
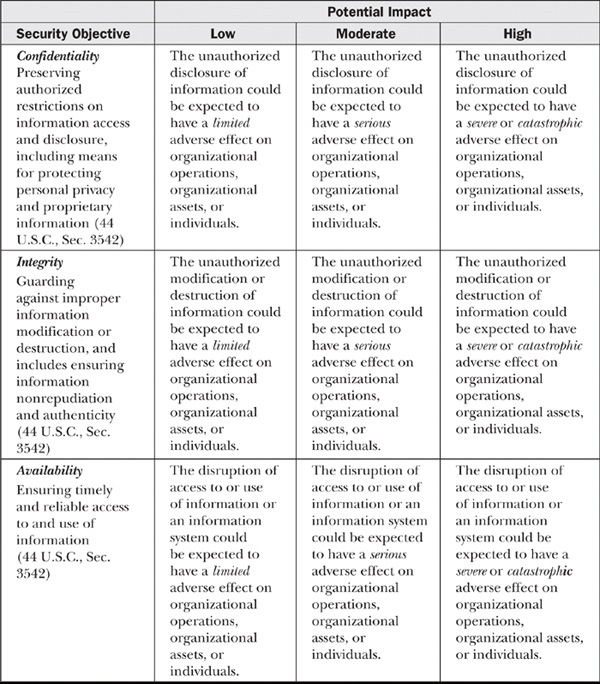
Table 10-2 Categorization of Information
Once types and impact values have been determined, using the provisional impact ratings for confidentiality, integrity, and availability, the information owner or the information assurance team builds an impact table for the information, as shown in Table 10-3.
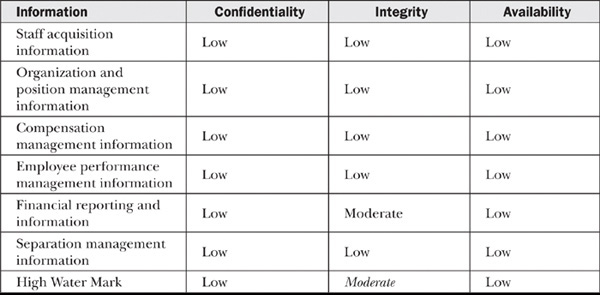
Table 10-3 Sample Categorization
The categorization indicates most of the information is of “low” impact to the U.S. government should there be a failure to ensure confidentiality, integrity, or availability. However, note there is a “moderate” impact if the integrity of financial reporting cannot be ensured. Therefore, the overall impact of a system which processes, stores, and transmits this information is “moderate.”
This categorization then drives the baseline control selection. This baseline establishes the minimum information assurance control requirements for the information system. Note that the majority of the information has a “low” impact, yet the entire system is being designed for moderate impact information. In these cases, the organization may want to determine whether the financial reporting information may be better processed, stored, and transmitted in another system with similar security requirements such as an organization’s accounting system. Good enterprise architecture can greatly decrease the cost of information assurance control implementation. Baseline information assurance controls for U.S. civilian agencies and organizations adopting NIST standards are determined using FIPS-200 (http://csrc.nist.gov/publications/fips/fips200/FIPS-200-final-march.pdf) and NIST SP 800-53 (http://csrc.nist.gov/publications/nistpubs/800-53-Rev3/sp800-53-rev3-final_updated-errata_05-01-2010.pdf).
Further Reading
• Federal Information Security Management Act of 2002 (Public Law 107-347, Title III). December 2002.
• International Organization Standardization and the International Electrotechnical Commission. Information Technology – Security Techniques – Information Security Management Systems –Requirements (ISO/IEC 27001). International Organization Standardization and the International Electrotechnical Commission, 2005.
• National Institute of Standards and Technology. Special Publication 800-60, Guide for Mapping Types of Information and Information Systems to Security Categories. June 2004.
• National Institute of Standards and Technology. Special Publication 800-53, Revision 4, Recommended Security Controls for Federal Information Systems and Organizations. DOC, April 2013.
• NIST FIPS 199, Standards for Security Categorization of Federal Information and Information Systems. DOC, February 2004.
• NIST FIPS 200, Minimum Security Requirements for Federal Information and Information Systems. DOC, March 2006.
• Schou, Corey D., and D.P. Shoemaker. Information Assurance for the Enterprise: A Roadmap to Information Security. McGraw-Hill Education, 2007.
• Tipton, Harold F., and S. Hernandez, ed. Official (ISC)2 Guide to the CISSP CBK 3rd edition. ((ISC)2) Press, 2012.
Critical Thinking Exercises
1. Within your organization, do you use marking methods to determine sensitive information or information critical to business? If so, what automated means do you have to ensure sensitive information is not leaked?
2. Consider the sensitive information in your organization and its life cycle. Where does the data reside at rest? On hard drives? In the cloud? Where does the data reside in transit? Over the mobile phone network? Over the open Internet? Over your network? What protections do you know are in place for each of the mediums you identified to protect sensitive information?
