CHAPTER 14
Advantages of Certification, Accreditation, and Assurance
In general, certification refers to a thorough assessment of a process, while accreditation is a formal declaration about the status of a process. In information assurance, certification and accreditation (C&A) are complex topics. In some economies, it is associated with government rules and regulations; however, the concept is much broader. It spans everything from compliance with an internationally recognized standard such as ISO 27001 to a more specifically focused audit to assure that management acknowledges and accepts the inherent risk in a system. In today’s fast-changing environment, where every new day brings new threats and vulnerabilities, information assurance is required for both technical as well as nontechnical operations.
Certification and accreditation (and its analogs) have long been staples in the U.S. government and other high assurance industries. When performed properly, C&A provides a level of assurance and due diligence with management and stakeholders. It provides a baseline of information assurance organization-wide and provides a focused baseline for the organization to identify areas for improvement or enhanced efficiency. C&A is ultimately about mature processes and policies being enacted by a capable workforce throughout the organization.
Certification and accreditation support information assurance. Certification, accreditation, and assurance are crucial elements to evaluate if security controls are implemented correctly, they are operated as expected, and residual risk is visible. C&A is a risk management tool that examines and reports on the effectiveness of controls in managing risks, as discussed in Chapters 11 and this chapter.
Providing assurance is never a one-time event; it is an ongoing exercise. Temporal, environmental, and organizationally defined events trigger a review and update of the C&A. Recalling the discussion in Chapter 6 about IAMS, managing security is a process that requires continuous review and improvement. In the context of the PDCA model, which is the most commonly used model in IAMS, perform this review during the Check phase. The improvement is identified in the Act phase. This chapter offers guidelines for a generalized process of certification and accreditation and discusses how these processes contribute to the assurance of the information system.
C&A of information systems supports senior management risk awareness, mitigation, avoidance, and acceptance. Certification and accreditation help achieve more secure information systems within an organization by doing the following:
• Enabling more consistent, comparable, and repeatable assessments of security controls in information systems
• Promoting a better understanding of organization-related mission risks resulting from the operation of information systems
• Creating more complete, reliable, and trustworthy information for accrediting officials—to facilitate more informed security accreditation decisions
Certification and accreditation are important activities that support a risk management process and are an integral part of an agency’s information assurance program. Accreditation is a risk-based decision made by senior management to authorize the operation of an information system and to accept the explicit risk based on the implemented security controls.
C&A of a system is a form of quality control and challenges the organization to implement the most effective security controls possible. A difficult task is made more complex since it is an analysis of not just a single system. Information assurance is a system of systems that must interoperate reliably while minimizing risk.
Concepts and Definitions
Certification evaluates a system against a set of criteria that demonstrates that the system is secure enough to be operated in a target environment. The objective of certification is the evaluation of the controls present within a system to ensure compliance with predefined functional and security requirements. The results of certification activity are the input for the accreditation process, which is the formal approval by management. Certification uses various techniques for evaluation purposes, such as risk analysis, validation, testing, control evaluation, and audit.
Accreditation, also known as authorization, is the official decision by management to operate a system (or system of systems). It is a formal acceptance of the adequacy of a system’s security to conform to operational requirements within an acceptable risk level. An accreditation exercise considers the following within an existing or proposed system:
• Acceptable risk level
• Defined interconnections to other systems
• Defined period of time and conditions
• Mechanism to counter identified threats and vulnerabilities with current or planned controls
• Operating with a set mode of security
• Prescribed set of security controls
Factors affecting the target system in its unique environment such as installed applications, operational security mode, sensitivity of the stored information, system setup, site location, and interconnections with other systems should be carefully considered.
Certification and accreditation are also closely related to risk management. The objective of risk management is to identify specific areas where safeguards are needed against security threats. Specific controls are applied to mitigate, eliminate, or acceptably reduce the identified risk. The results of this exercise provide critical information for making an accreditation decision.
The process of certification and accreditation is an ongoing one in line with the IAMS discussed in Chapter 6. Clearly, it should be a formal continuous process. Formal re-certification and re-accreditation should be mandatory when there are major changes to the system, when a major application is introduced, when the threat/risk environment changes, or when there are significant technological upgrades.
Purpose of Certification and Accreditation
There are many reasons for having management commit to a certification and accreditation exercise. In some cases, laws (U.S. government) require certification and accreditation; however, in the absence of law, there are other advantages to the organization.
• Certification and accreditation promote the importance of risk management in operating a system with appropriate management review and monitoring.
• Implementing and practicing a formal certification and accreditation process assist the organization in providing evidence that it has exercised due diligence if a security problem or incident arises.
• Management of an organization can obtain a higher level of assurance that its security systems are in fact configured and operated properly to secure assets instead of being victims of or unwitting contributors to their compromise. It is important that an organization has an appropriate level of security and trust of the system being used to safeguard its assets.
Primary Roles for Supporting Certification and Accreditation
Many roles are involved in the certification and accreditation exercise. The number of people involved in the exercise depends on the complexity of the system assessed. However, the functions remain the same. For the exercise to be effective, all parties need to work as a team to ensure success of the program. Table 14-1 provides an overview of the roles and associated responsibilities for supporting the certification and accreditation exercise.
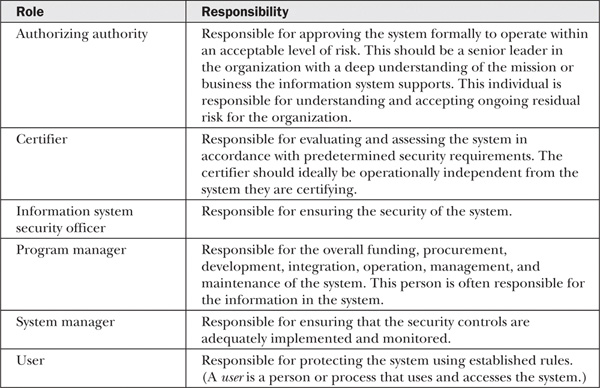
Table 14-1 Roles for Supporting Certification and Accreditation Exercise
Certification and Accreditation Process
The security certification and accreditation process consists of four phases. Figure 14-1 provides brief descriptions of the activities in each phase.
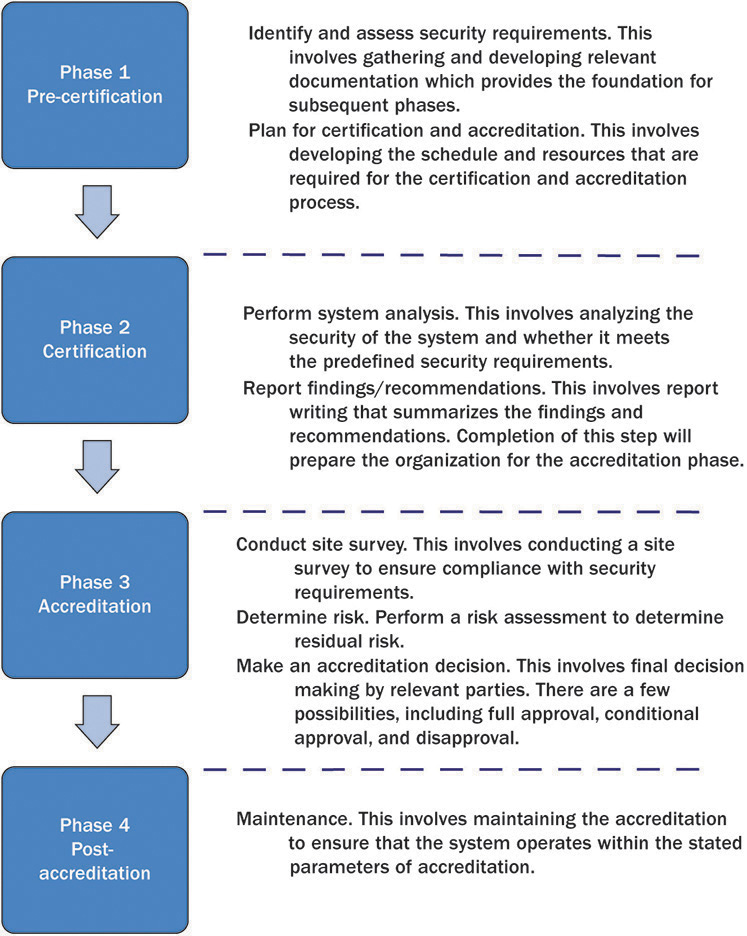
Figure 14-1 Certification and accreditation process flow
Certification Baselines
Certification is commonly derived from baselines. Organizations can save time and resources by determining standard information assurance baselines for their information systems based on the classification or categorization of the system. These baselines become the foundation for certification activities. In the United States, cloud service providers that are providing services to civilian departments and agencies must comply with FedRAMP baselines. The FedRAMP baselines provide minimum information assurance requirements that systems must comply with if they are to receive the FedRAMP certification called a provisional ATO. Figure 14-2 summarizes the baseline control requirements.
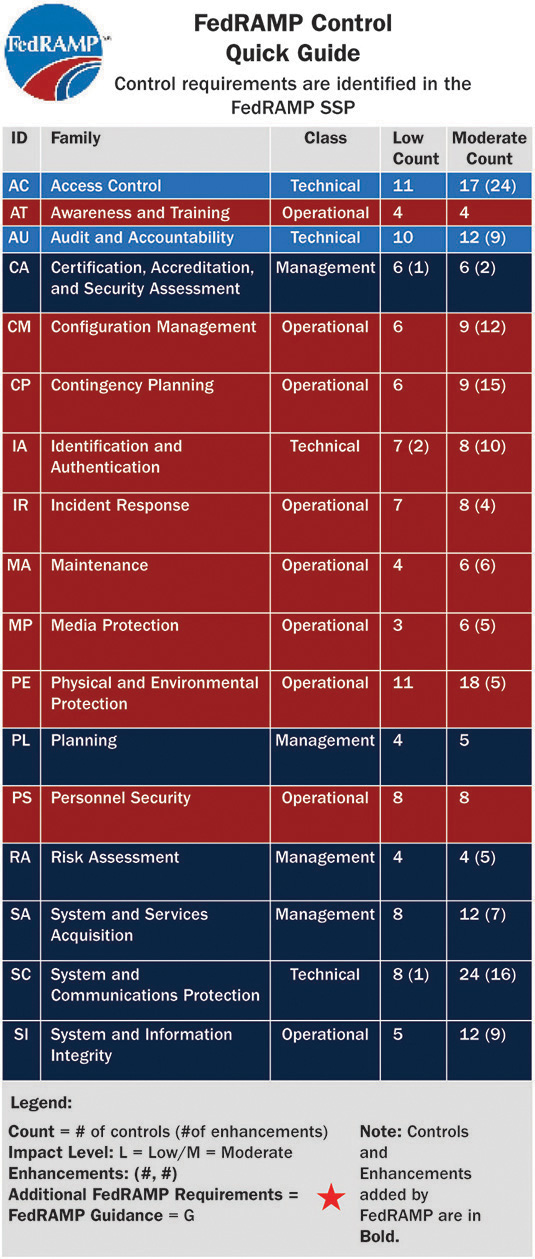
Figure 14-2 Sample baseline summary
Considerations for Product Evaluation, Certification, and Accreditation
![]()
To decide whether to embark on certification and accreditation exercises, an organization should take into account several factors. Since accreditation is about the acceptance and management of risk, organizations should weigh the appropriate factors and decide to either accept or reject the risk. To ensure that credible, risk-based decisions are made, the following points should be considered during the security certification and accreditation process:
• Effectiveness of security controls Do the security controls provide the appropriate and desired level of protection as required?
• Reasonable and acceptable risk Prior to the certification, are the risks established in the risk analysis real and reasonable? Would these risks be acceptable?
• Relevancy and benefits In what way would the certification be relevant and beneficial to the organization?
• Risk mitigation and control Are there any steps being taken or do any plans exist to rectify weaknesses or to remove known vulnerabilities arising in the security controls?
Security requirements that apply to a system differ considerably from one system to another. Every system’s security requirements are interpretations of generic requirements within the context of the system’s purpose, operational concept, and threat environment. Tailor certification and accreditation activities to address a system’s specific security requirements. In addition, evaluate the complexity and sensitivity of the system. For example, the depth of technical analysis required for a stand-alone computer that handles routine work is less when compared to a mission-critical system that handles multimillion-dollar transactions.
Further Reading
• National Institute of Standards and Technology. Special Publication 800-37, Revision 1, Guide for Applying the Risk Management Framework to Federal Information Systems: A Security Life Cycle Approach. February 2010.
• National Institute of Standards and Technology. Special Publication 800-39, Managing Information Security Risk: Organization, Mission, and Information System View. March 2011.
• Nichols, R., D. Ryan, and J. Ryan. Defending Your Digital Assets Against Hackers, Crackers, Spies, and Thieves, McGraw-Hill Education, 2000.
• Risk Management AS/NZS 4360:1999. Standards Association of Australia.
• Ross, R., et al. Guide for Assessing the Security Controls in Federal Information Systems, (Special Publication 800-53 Rev 1). NIST, 2008.
• Ross, R., et al. Recommended Security Controls for Federal Information Systems (Special Publication 800-53 Rev 1). NIST, 2006.
• Ross, R., M. Swanson, et al. Guide for the Security Certification and Accreditation of Federal Information Systems (Special Publication 800 37). NIST, 2007.
• Schmidt, Howard A. Larstan’s The Black Book on Government Security. Transition Vendor, 2006.
• Schou, Corey D., and D.P. Shoemaker. Information Assurance for the Enterprise: A Roadmap to Information Security. McGraw-Hill Education, 2007.
• The Common Criteria Evaluation and Validation Scheme. www.niap-ccevs.org/cc-scheme/.
• Tipton, Harold F., and S. Hernandez, ed. Official (ISC)2 Guide to the CISSP CBK 3rd edition. ((ISC)2) Press, 2012.
Critical Thinking Exercises
1. An organization chooses to have its CIO be the accreditation official for all its information systems. What are the strengths and weaknesses of this approach?
2. Within an organization, who is best suited to determine the independence of the certifier?
