20. Integrated Alarm System Devices
Chapter objectives
1. Learn the Basics in the Chapter Overview
2. Get to Know about Alarm Concepts
3. Discover Types of Alarm Sensors
4. Learn about Alarm System Application Rules
5. Looking beyond Alarm Detection
6. Answer Questions about Integrated Alarm Concepts and Devices
CHAPTER OVERVIEW
In Chapter 20, we will discuss Alarm Concepts (including how alarms are detected and initiated), Alarm States (including the difference between False Alarms and Nuisance Alarms), Filtering, Alarm Communication and Annunciation, Assessment, Response, and Evidence Gathering. We will examine a variety of types of alarm detection devices, and we will also look beyond Alarm Detection and learn how alarms can be used for Trend Analysis and Vulnerability Analysis.
In Chapter 20, Alarm Concepts (including how alarms are detected and initiated), Alarm States (including the difference between False Alarms and Nuisance Alarms), Filtering, Alarm Communication and Annunciation, Assessment, Response, and Evidence Gathering are all discussed. A variety of alarm detection devices are examined and the reader can also look beyond Alarm Detection and learn how alarms can be used for Trend Analysis and Vulnerability Analysis.
Keywords: Alarm, Alarm State, Assess, Concepts, Detect, Evidence, Filtering, Initiate, Response
Author Information:
Thomas L. Norman, CPP, PSP, CSC, Executive Vice President, Protection Partners International
Alarm Concepts
There is a lot more to an alarm system than most people think. There are many steps between “Bad Guy turns up in woods outside our weapons depot” and “Bad Guy arrested.” This section covers all of the basic concepts involved in alarms from detection to arrest.
Detection and Initiation
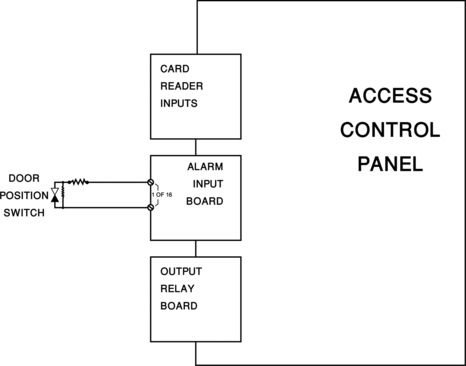
Alarm detection occurs when the alarm device is initiated by an intruder. Depending on the type of alarm detection device, initiation may be caused by opening a window, door, or gate (equipped with a window/door/gate position switch), breaking a window (acoustic glass break detector), walking or driving over underground seismic or energy field detectors, walking or driving through a beam (such as infrared or laser beams), or walking through a volumetric energy field (such as infrared or microwave detectors).
Alarm detection devices and their methods of detection are discussed at the end of this chapter.
Filtering and Alarm States
Before the alarm is reported to a Security Console Officer as an alarm, it may be filtered to reduce the potential for false or nuisance alarms.
• Alarm States: Alarm devices typically are connected to an alarm input panel and exist in one of four states:
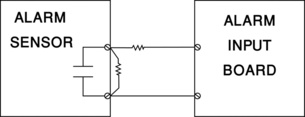
• Secure: The Secure alarm state means that the alarm detection device is connected and communicating properly and that there is nothing to report. The area is secure. Electrically, the alarm circuit is typically closed with a resistor in the circuit to limit the current from the alarm input board. When the Secure state is annunciated, the alarm point is typically shown as green (Figure 20.1).
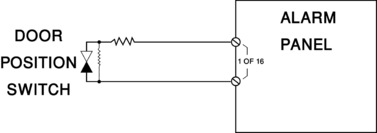
• Alarm: When an alarm detection device goes into the Alarm state, it is because the alarm detection device has been activated according to its detection technology (a door/window/gate has opened, a motion detector has seen a change in heat or motion, etc.; Figure 20.2). When the Alarm state is annunciated, the alarm point is typically shown flashing red. When the alarm changes from Secure to Alarm state, there is often also an audible annunciation to draw the Security Console Officer's attention to the alarm.
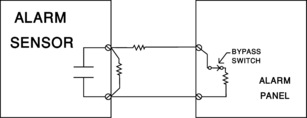
• Bypass: There are times when you do not want to receive any alarm even though the alarm detection device may be activated. For example, a motion detection alarm device in a theater hall would be bypassed when the theater is scheduled for activities. In such cases, the alarm detection device is placed into the “Bypass” state (Figure 20.3). Often the alarm is annunciated by a color change as it changes state, but instead of displaying green/red (secure/alarm) it may display green/yellow (secure/sensing but in bypass state). When bypassed, the alarm point shows the change of state but there is not audible alarm.
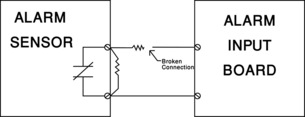
• Trouble: On rare occasion, there may be a problem with the alarm detection device wiring. When this happens, it can be sensed by the “Trouble” state (Figure 20.4). Typically the Trouble state is annunciated as a flashing yellow light, usually with no audible alarm. Although all alarm detection devices can be wired in a fashion that will not report the “Trouble” state when problems arise, they will likely be reported as an alarm. That is the definition of a “False Alarm.”
• Filtering: Alarms may also be filtered to help avoid “Nuisance Alarms.” A Nuisance Alarm is when an alarm detection device reports a valid detection, but it is an occurrence that has no security implication, such as when a dog leans against a fence.
Every alarm detection device has what are called “Exploit Modes.” This is important for system designers, installers, and maintenance technicians to understand. If the Exploit Mode is used inappropriately, then it will detect things that have nothing to do with security and drive Security Console Officers crazy. Most Console Operators deal with Nuisance Alarms by placing those alarm detection devices into “Permanent Bypass Mode.” Thereafter they do not cause Nuisance Alarms, but they also do not report real alarms. This leaves the facility vulnerable to the security event the Alarm Detection Device was installed to detect. The answer is to filter out Nuisance Alarms.
The most effective way to filter Nuisance Alarms is to
• First, understand the Exploit Modes of all Alarm Detection Devices (more on that later in this chapter).
• Second, use a second Alarm Detection Device for the same area that does not possess the same Exploit Mode as the first Alarm Detection Device; for example, use an infrared motion detection device along with a pair of infrared photo beams.
• Configure the circuit such that when either one trips, there is no alarm reported but when both circuits trip an alarm is reported.
Communication and Annunciation
Most alarms are communicated from the Alarm Detection Device to the Alarm Panel typically over a two-conductor twisted pair cable (typically UL Listed 20 gauge stranded, individually insulated with an overall sheath; Figure 20.5).
An alarm panel may be stand-alone (a complete alarm system to which all alarm detection devices connect directly), or it may be an Alarm Input Board, which is a small part of a much larger Alarm/Access Control System including many other Alarm Input Boards, Access Control Panels, and other electronic devices.
Alarm Input Boards communicate the alarm through the Access Control Panel, to the Host Server, and then to an Alarm/Access Control Workstation where it is often annunciated on a Map-based Graphical User Interface (GUI) that shows the location of the alarm as well as its alarm state (Figure 20.6).
When an alarm is annunciated, the Security Console Officer's attention is usually drawn to the alarm by an audible alarm. The Officer will “silence” the audible alarm and view the point in the Alarm state. If this is on a simple lamp-based panel, it will be the flashing red light. If this is on a scrolling screen, it will be the last one on the list, usually flashing red. If this is on a Map-based GUI, or Map-based Annunciating Panel it will be the red flashing icon overlaid onto the map showing the location of the alarm event.
Assessment
Once annunciated the alarm must be assessed; that is, the Security Console Officer must determine if the alarm is a valid “Security Event” or if the alarm detection device is reporting a “Nuisance Alarm.” This requires that
• A roving guard is sent to see the conditions at the alarm event location
• The Console Officer views a video camera showing the alarm event location
• A second alarm detection device in the alarm event location triggers, confirming the first alarm detection device
• The Console Officer listens to an audio source from the alarm event location, confirming inappropriate activity there
The fastest and most accurate way of assessment is to use video to assess the alarm. This provides the Console Officer with a wealth of additional information including but not necessarily limited to
• Is the alarm a real security event?
• How many offenders are there?
• What do the offenders look like? (Sex, Height, Weight, Hair, Clothing, etc.)
• Are the offenders using tools?
• Are the offenders carrying weapons?
• What direction are the offenders headed?
• Do the offenders appear organized or chaotic?
• How aggressive are the actions of the offenders?
All of this information helps the Console Officer and Supervisor organize an appropriate response plan.
Response
Alerted to intruders, the Console Officer and Supervisor must organize an appropriate response. Typically this may involve sending either Police or Roving Security Officers to confront the intruder, thus it is a good thing to know how many intruders there are and whether or not they are armed. For this, the Console Officer will either use the 2-way Radio to notify roving guards or telephone to notify Police.
During the pursuit, the Console Officer should monitor the movements of the intruders using the Digital Video System. This is best done with Video Pursuit scripting on Digital Video Software.
The “Video Pursuit Function” is a custom software script that can be overlaid on most Digital Video Systems. The concept was invented by the author to allow Console Officers to follow subjects easily through a complex facility equipped with a large video system. The Video Pursuit initiates with the alarm notification and the video system displaying up to nine relevant images, where the center image is the scene of the alarm event and all surrounding images are scenes of “egress paths” away from the alarm scene. Each surrounding image is a mouse button that can be triggered when the Console Officer “hovers” the mouse over the image. When the intruder exits the alarm scene and goes into the view of a surrounding camera, the Console Officer clicks on that image and it becomes the new “center focus tile” in a new array of up to cameras. Each movement of the “focus tile” issues a corresponding move on the Map-based GUI showing the new location of the subject as he moves. The Console Officer advises the responding officers of the change in location of the intruder as he moves. This operation repeats itself until the subject is apprehended by Police or Roving Security Officers. The Video Pursuit script can be implemented by competent Security System Integrators or by the Engineering Support Departments of most Digital Video System manufacturers.
Evidence
One of the most important functions of alarm systems is to gather evidence of a crime or misbehavior. Alarm/Access Control Systems keep logs of all activity, and one of those logs is the “Alarm Event Log.” This is legal evidence in a court of law, civil proceeding, or employment hearing that an event occurred. When the event can be tied to the offender using other evidence such as video, audio, or witness testimony, a case against the offender can be established.
Types of Alarm Sensors
Alarm sensors can be categorized into several broad areas as follows:
• Outer Perimeter Detection Systems
• Building Perimeter Detection Systems
• Interior Volumetric Detection Systems
• Interior Point Detection Systems
• Intelligent Video Detection Systems
Outer Perimeter Detection Systems
Outer Perimeter Detection Systems are designed to alert whenever a human or vehicle breaches an outer perimeter such as a fence line, gate, or invisible border. Outer Perimeter Detection Systems can also be used along campus boundaries and even national borders.
• Gate Breach Detection System
• Application: Gate Breach Detectors are typically in the form of magnetic switches that are applied to gates instead of interior doors. They may be configured to work on swing, sliding, or overhead gates. They work by maintaining a magnetic switch in the closed position as long as the switch is held next to the magnet. The magnet is mounted on the gate and the switch is mounted on the adjacent fence. When the gate opens, the switch will change state and send an alarm.
• Advantages: These switches are generally very reliable. For the highest reliability they should be balanced-bias (wherein the switch exists in a field of several magnets, one on the gate and the others within the switch) so that if anyone tries to place a magnet next to the switch, this act alone will cause an alarm.
• Disadvantages: As the gate ages, the switch may not align properly with the switch, causing nuisance alarms. Wide gap switches are necessary to accommodate the natural loose fitting of gates.
• Exploits: Climb over the fence or tunnel below the fence.
• Seismic Detection Systems
• Application: Seismic detectors are essentially rugged waterproof microphones, typically in the form of spikes that are driven into the ground. They are connected by cables (or sometimes radio frequency) to a detection circuit that helps to filter out nuisance alarms.
• Advantages: Very good at detecting vehicles and footsteps on solid ground.
• Disadvantages: Do not work well in soft ground such as sandy soil and they cannot be used in areas of routine high traffic, such as next to a freeway, as the noise of large vehicles drowns out any nearby footsteps.
• Exploits: Knowledgeable Threat Actors use continuous loud sounds such as construction equipment to swamp the detectors so that they cannot hear footsteps.
• Fiber-Optic Detection Systems
• Application: Fiber-optic cables may be attached to fences to detect climbing or cutting of the fence fabric. Better systems can pinpoint the exact location of the fence breach down to about a couple of meters. Some sensors also provide audio so that the Console Officer can hear the fence being cut or climbed in order to help verify the alarm.
• Advantages: Highly reliable when correctly installed on a good quality fence. They also can detect for very long distances as compared to other types of fence detectors and use fewer electronic modules than most other types, thus reducing their costs on long fence lines. One manufacturer claims to be able to operate a single zone of up to 60 miles (100 km) with a detection accuracy of ± 1.5 m.
• Disadvantages: Correct installation is critical and the fence must be kept in very good condition.
• Exploits: Exploits include cutting the line in advance of the actual intrusion and making entry before repairs can be conducted, down-line of the cut.
• Capacitance Detection Systems
• Application: These are typically in the form of two cables placed near each other that set up a capacitive field between the two cables. These can be mounted on a fence, used as a fence topper, or buried underground. Depending on the type and the installation method, these systems can be very good at detecting intruders near the capacitive field. They sense by sensing the water content of human bodies, which disrupts a tuned radio-frequency field between the two cables, changing its frequency. When installed correctly, and in combination with its integral detection filtering equipment, the sensors can detect with relative accuracy the location of an intruder even standing nearby outside the fence.
• Advantages: These systems are reliable except during rain. They require relatively little maintenance and are much less sensitive to fence fabric maintenance than fiber-optic detection systems.
• Disadvantages: Unreliable during rain unless carefully monitored and tuned for such. They cannot be used underground in areas of standing water and are less reliable on fences near standing water such as puddles after a rainstorm.
• Exploits: Knowledgeable Threat Actors have used heavy rainstorms to mask their entry. The lines can also be cut before an intrusion, with the actual intrusion occurring before repairs can be made. Well-organized security programs place additional patrols or sensor layers when lines are cut to avoid this exploit.
• Leaky-Coax Cable
• Application: A Leaky-coax system comprises a radio-frequency coaxial cable, similar to a television cable, on which the outer braid is designed to be incomplete (about 50% coverage instead of 100%) in order to “leak” their Radio Frequency (RF) signal outside the cable. When the RF signal is interrupted by the presence of a human body with its mass of water, this de-tunes the system to provide for detection. Leaky-coax systems can be buried or placed on fences. Unlike the Capacitance System, the Leaky-coax system requires only a single cable.
• Advantages: Work well on fences and underground. When underground, like the Capacitance Systems, they are invisible to the offender.
• Disadvantages: Do not work well near standing water or in rainstorms.
• Exploits: Knowledgeable Threat Actors have used the slow-move approach (less than 1 foot every 10 minutes) to avoid detection and depending on the area, detection may be avoided during a heavy rainstorm if the detector is fence mounted.
• Infrared and Laser Detection Systems
• Application: Infrared Beams are configured as an infrared light source and a photoelectric detector placed some distance apart. For perimeter use, these are used in vertical arrays so that a person cannot climb over or step under a single beam. To prevent a false light source from being used, they are configured at a specific infrared frequency and are pulsed so that the detector is expecting to see that specific light frequency and pattern, if not, detection occurs. If the beam is broken, detection occurs; if a false beam is placed on the detector providing an improper frequency of pattern of flashes, detection occurs. Lasers may be used instead of infrared light beams. Detection beams can span short distances or distances up to several hundred meters. All Infrared and Laser Detection Beams are line-of-sight and cannot contour to hills and valleys except by placing additional beams at the vector locations (edges) of hills and valleys. Thus they work best on land with little change in elevation.
• Advantages: Very reliable in all weather.
• Disadvantages: Detection Beams sense anything interrupting the beams including animals, blowing newspaper, leaves, and so forth. This can be mitigated by configuring the beams so that two or more beams must be broken in order to yield detection (alarm filtering).
• Exploits: Knowledgeable Threat Actors cause many false alarms before the actual event so that detection is ignored by the security officer.
• Outdoor Passive Infrared Detectors
• Application: Although Passive Infrared (PIR) Detectors are usually used indoors, there are a few Outdoor PIRs available. Outdoor PIRs are equipped with hardened rain-proof enclosures and are designed to work in moderate temperature environments (from somewhat above freezing to about 95 °F). They use circuitry that filters the PIR signals to look for human infrared signatures outdoors and avoid common nuisances such as blowing leaves, changes in air temperatures, and so forth.
• Advantages: Relatively low cost, work well at short ranges, and their mere presence may serve as a deterrent.
• Disadvantages: Do not work at all in high-temperature environments and have difficulty in extreme low-temperature environments because humans bundled up to stay warm so they mask their normal infrared signature.
• Exploits: Knowledgeable Threat Actors can avoid detection by moving very slowly (less than 1 foot per ten minutes).
• Pneumatic Underground Detection Systems
• Application: The most familiar example of a Pneumatic Detection System is the old-fashioned gas station bell. This comprised a flexible tube (looking sort of like a garden hose) that was stretched across the gas station driveway. When a car drove over the hose, a change in air pressure inside the tube caused the bell to ring. A similar system is available for direct burial and is capable of detecting vehicles or pedestrians across solid ground. The tubes are usually buried just below the surface of the ground with a sensor nearby.
• Advantages: Accommodate uneven ground and work well in remote areas without quality roads. The detector is invisible as it is buried so detection of the alarm by an intruder is less likely. These are also somewhat less expensive than some other long-line outdoor detectors.
• Disadvantages: The detection zone is not very precise. Only the entire zone is detected, so it is not possible to pinpoint where along the line the intrusion has occurred. This means that smaller detection zones are necessary. The line has to maintain a constant pressure so the detection circuitry includes pressurization equipment, requiring more power than some other systems. Burrowing animals such as moles have been known to chew through the Pneumatic Hose, causing it to fail. When this happens, the entire line must be searched to find the leak and fix it.
• Exploits: If a knowledgeable Threat Actor could find it, he could cut the hose, disabling the entire line until maintenance can occur.
• Microwave Detection Systems
• Types: Available in either Monostatic or Bistatic versions. Monostatic detectors use a single device that transmits and receives (a transceiver), whereas Bistatic detectors use a pair where one is the transmitter and the other is the receiver.
• Monostatic Microwave Detection Systems
- Application: Monostatic detectors fill a volume (detection zone) with microwave energy and detect the echo of that energy. When a person or object enters the detection zone the quiescent echo is changed and that is detected.
- Advantages: Quite reliable for short ranges.
- Disadvantages: Care must be taken when used near buildings because they can sense through many types of walls. Close proximity to fluorescent lights can cause false alarms. They are sensitive to blowing objects such as leaves, newspapers, wind ripples on a mud puddle, small animals, and so forth.
- Exploits: Cause numerous false alarms so that the guard force will ignore the actual intrusion.
• Bistatic Microwave Detection Systems
- Application: A detection zone is set up between the transmitter and receiver, with its widest portion in the exact middle of the zone.
- Advantages: Accurately detect any movement between the transmitter and receiver.
- Disadvantages: Nuisance alarms are a problem. They detect literally everything that goes on between the transmitter and receiver including rain, snow, wind-driven leaves and dust, newspapers, and ripples on a puddle. Everything! Bistatic Microwave Detectors should always be used with a confirming detector of another technology.
- Exploits: Enter during a rainstorm. The unit is effectively blind because it is in constant detection.
• Ground-Based Radar
• Application: This is a short-range version of long-range marine radar designed to sense vehicles, vessels, and objects close-in (typically less than 2 to 8 miles).
• Advantages: It can track multiple vehicles, moving objects, and people simultaneously and “paint” their location on a Map-based screen.
• Disadvantages: It does not work well in close proximity to train tracks and roadways where constant movement can confuse the radar with reflections of other objects. This is one of the most expensive detection technologies.
• Exploits: Knowledgeable Threat Actors can confuse radar with other radar noise on the same frequency.
Building Perimeter Detection Systems
• Balanced-Biased Door Position Switches
• Application: Like Gate Position Switches, Door Position Switches work by using magnets and a magnetic sensitive switch. A magnet is placed in the top of the door and the switch is placed in the door frame. When the door is closed, the switch rests in a “balanced-bias” magnetic field of several magnets (including the magnet on the door and others within the switch). When the door opens, this unstable magnetic field is disrupted, closing the switch. The switch can also be activated by placing another magnet near the switch, in an effort to bypass the magnet on the door. Thus, the very act of trying to bypass the switch can set it off. Other versions of this switch are available for overhead and roll-up doors and for windows.
• Advantages: Very reliable detection.
• Disadvantages: It is best to conceal the switch and magnet in the frame and top of door. Surface mounting can be used on “back-of-house” doors in rough finish areas.
• Exploits: Saw through the door, leaving the magnetic switch in place. This is a common exploit for roll-up vehicle doors.
• Photoelectric Beam Detectors
• Application: Indoor version of the Outdoor Infrared Beam Detectors. The beams are pulsed infrared, just like their outdoor cousins, and they sense objects moving between the beams. They are ideal to span a large expanse of doors, and are often used in a warehouse or industrial setting to span up to a dozen vehicle and pedestrian doors.
• Advantages: The beam detectors sense entry of an intruder cutting through a warehouse roll-up door, attempting to bypass a Door Position Switch.
• Disadvantages: In most installations, beam installation is obvious so they are not often covert.
• Exploits: Leave an object blocking the beams, thus putting the alarm zone into the “trouble” state.
• Glass Break Detectors
• Application: Available in both acoustic and vibration sensitive versions. Older glass break detectors (no longer in use) used foil tape on glass that broke when the glass was broken. Acoustic detectors listen for the distinctive sound of breaking glass. These are usually placed on the ceiling, centrally above several windows. Vibration detectors are small adhesive disks placed on each window which sense the vibration caused when the glass breaks.
• Advantages: Very reliable detection of glass breakage.
• Disadvantages: Older acoustic detectors were known to detect the sound of vacuum cleaners and sometimes jingling keys.
• Exploits: Find another entry point other than through the glass. These detectors will even detect when glass cutters are used.
• Seismic Detectors
• Application: An indoor version of the Outdoor Seismic Detector, these are used to detect hammering or drilling into walls. They are common on interior vault walls.
• Advantages: It is virtually impossible to drill or hammer into a room equipped with seismic detectors.
• Disadvantages: Sensitivity must be set to accommodate all kinds of traffic vibrations, so that only a real intrusion is sensed. Unless this is done properly, nuisance alarms are common.
• Exploits: Set off a number of false alarms so that the detectors are ignored.
Interior Volumetric Sensors
• Microwave Detection Systems
• Application: Interior Microwave Sensors are Monostatic and are often used to sense activity in stairwells. Because they sense reflected motion, they can sense movement a floor above or below the floor where they are located. I have used these every third floor to sense stairwell motion.
• Advantages: Very sensitive to motion, and are particularly sensitive to motion coming toward or going away from the detector. They are less sensitive to detection across their detection zone, but still quite useable for that purpose.
• Disadvantages: These detectors are able to see through walls, detecting activity on the other side of a wall. So they must be placed with care, respecting construction materials and normal activity. Microwave sensors can detect plasma moving within fluorescent lights, so they should not be used near them.
• Exploits: Create nuisance alarms hoping that the security staff will ignore the alarm. Extremely slow movement can also defeat these detectors.
• Infrared Detection Systems
• Application: Infrared Detectors create a series of “fingers” and are most sensitive to human movement across their detection zone (the opposite of Microwave sensors). The detectors can also create a “curtain” across which motion is detected. They also sense a change in heat across the curtain or fingers in their detection pattern.
• Advantages: Provide reliable detection in normal building temperatures and when installed correctly (respecting their limitations).
• Disadvantages: Detectors do not work above about 95 °F. Heat sources in the detection field such as heating ducts can cause nuisance alarms. These detectors are least sensitive to bodies moving toward the detector. They are designed to detect bodies moving across their detection field.
• Exploits: Extremely slow movement can sometimes defeat these in high-temperature areas. Knowledgeable Threat Actors have defeated Infrared detectors by covering their body with a heavy blanket, masking their body heat.
• Dual-Technology Detection Systems
• Application: Dual-technology Detectors combine the best of both Infrared and Microwave detectors, using both technologies to create a single reliable detector. Both microwave and infrared sensors must trip for the detector to signal an alarm.
• Advantages: Sensitive to motion both across and toward the detector. They are far less prone to false alarms than either type of detector alone.
• Disadvantages: None
• Exploits: None.
• Ultrasonic Detection Systems
• Application: Ultrasonic detectors are acoustical microphones and detection circuits that listen for sounds in the ultrasonic frequency range (about 50 to 100 kHz). Ultrasonic detectors are available in either Passive or Active versions. Passive detectors listen for sounds in the ultrasonic frequencies whereas Active detectors work like bats, emitting ultrasonic frequencies and listening for changes in the frequency caused by objects reflecting back (a bit like Monostatic Microwave Detectors).
• Advantages: None.
• Disadvantages: Ultrasonic detectors are less reliable than microwave. Jingling keys, vacuum cleaners, flying insects, and nearby airports and construction zones can all confuse Ultrasonic detectors.
• Exploits: Many as stated earlier. In one case, an intruder reportedly released a swarm of bees into the room.
• Thermal Imaging Detection Systems
• Application: Thermal Imaging Cameras can sense body heat against the background.
• Advantages: Provide very reliable detection and also provide an image of the intruder, showing his location in the room or corridor.
• Disadvantages: Thermal Imaging Detectors are very expensive.
• Exploits: Cannot penetrate glass, and high ambient temperature near 98 °F can mask an intruder.
Interior Point Detection Systems
• Duress Alarms
• Application: Duress Alarms (also called Panic Alarms) are a detection switch that is activated by a human in response to a security concern. Common forms include switches under a counter or on a wall tripped by hand, a switch on the floor tripped by lifting one's foot up under a paddle, and cash drawer bill traps. Unlike all other alarms discussed here that are designed to be tripped by an unwitting offender, Duress Alarms rely on an authorized person to intentionally trip the alarm when they are concerned about a security event. Thus these are the highest priority alarms in the system. Typically there is a violent event occurring when a Duress Alarm is tripped.
• Types of Duress Switches:
- Wall-Mounted Duress Switch: May be placed on a train platform or other public or semi-public area for concerned persons to signal Security or Police when they are concerned about being attacked.
- Two-finger Switches: Requires the user to push two buttons simultaneously in order to signal an alarm. The use of two buttons helps ensure that the alarm is intentional and is not being triggered by something bumping against the switch. Commonly used under a desk or cash counter.
- Shroud Switches: A single switch enclosed by a shroud to keep objects from pushing on the switch.
- Pull Switches: Requires the user to pull a plunger out from its off position, usually also shrouded to allow fingers to enter between the shroud and the switch but keeping out objects that could accidentally trigger the alarm.
- Foot Switches: The user places his/her foot under a paddle and lifts the foot, triggering the switch. These allow the user to have both hands above the desk or counter and are often preferred for their discreet nature.
- Bill Traps: When the last bill in a cash drawer is pulled out, a clip over the last bill makes electrical contact with a steel plate below the bill, tripping the alarm. Thus the very action of pulling out all of the cash from a drawer sets off a silent alarm.
- Audio/Video Verification: All Duress Switches should be used with audio and video to verify the alarm. These tools allow the Security Console Officer to determine the number of aggressors, their actions, their weapons, and how much of a force is needed to quell the event and to protect the innocent people involved.
• Advantages: An essential tool to allow persons at risk to signal for help.
• Disadvantages: If not designed or installed correctly, they can cause nuisance alarms.
• Exploits: The offender may try to defeat the alarm communications so that it will not send an alarm (by cutting a telephone line for example) or try to convince the person under attack not to trigger a Duress Alarm, usually by threat of force.
• Explosives Detection Methods and Systems
• Types: Explosives detection can be accommodated by a variety of methods and detection technologies including Dogs, X-rays, Millimeter Wave Scanners, Spectrographic Detection, and Visual Detection.
• Visual Inspection Approaches
- Application: Visual Inspection of packages by trained guards is a common and often effective means of deterrence and detection. A package is opened by hand and inspected for suspicious contents by a trained guard.
- Advantages: Can be very thorough. Allows a trained guard time with a subject to analyze his/her behavior, thus detecting suspicious persons by their behavior as well as by the package itself.
- Disadvantages: Most guards are either poorly trained or unconcerned with conducting a thorough search. Most searches are very poor.
- Exploits: Of all of the methods of explosives detection, if I were carrying explosives, I would most hope to encounter a visual inspection. Explosives can usually be easily packaged into the container in a manner that evades visual inspection. Also, most visual inspections are profoundly cursory, often missing obvious briefcase pockets and so forth. In almost all inspections I have undergone, my packages were not fully inspected. Also, one could use an accomplice to create a distraction at the time of the hand search.
• Dogs
- Application: Trained dogs are arguably the most reliable explosives detection method. They can detect minute amounts of virtually every explosive compound. Terrorists fear dogs more than any other detection methodology.
- Advantages: Dogs are very efficient when properly trained and used. In many countries, people find the use of dogs to be engaging rather than off-putting. This is not the case in Muslim countries where the use of dogs can be offensive. For some reason, persons carrying explosives also have an aversion to sniffer dogs. Dogs will work for dog food and the love of their handlers.
- Disadvantages: Cannot be used in Muslim countries due to cultural norms. Dogs cannot work effectively for more than about 20 minutes, requiring frequent breaks. Thus multiple dogs are needed for a single checkpoint. When used for multiple checkpoints the cost of training and handlers can become expensive. Dogs' training must be constant for them to be reliable. This is also expensive due to the cost of trainers.
- Exploits: Package explosives hermetically. No other exploits for a well-trained dog.
• Package X-Ray Scanners
- Application: There are two types: transmission and backscatter. These can image the interior of packages and cargo, including entire vehicles, trailers, and trucks.
- Advantages: Accurately detect most contraband materials including most explosives, drugs, and weapons. Thus, these are among the most versatile Explosives Detectors.
- Disadvantages: Can miss some substances. The technician must be well trained and continually alert.
- Exploits: Objects can be placed inside the package or container in a manner that is less obvious to a less-well trained operator. For example, a gun can be placed upright against the side of a suitcase instead of flat, where its outline would be obvious.
• Personnel X-Ray Scanners
- Application: All use backscatter technology. These create a “naked” image of the person scanned showing anatomical features and many kinds of objects placed against the body.
- Advantages: Backscatter imagers can sense weapons, drugs, explosives, and other contraband such as packages of money on the person.
- Disadvantages: Increasingly, these are seen as culturally offensive by all cultures, but especially in Asian and Muslim cultures because they show all anatomy. News stories of TSA agents gleefully selecting attractive women for inspection and horror stories of medical survivors having breast implants or colostomy bags have outraged the public. There continues to be outrage against these machines, so they are rarely used except at transportation facilities, where their use is detested, but mandatory. Accordingly these are entirely impractical for commercial use.
- Exploits: Certain substances are virtually undetected by these scanners, but many TSA tests have successfully gotten handguns past the detectors.
• Millimeter Wave Scanners
- Application: These are somewhat similar to backscatter X-ray technology, but work from a distance and provide a visual (not X-ray vision) image of the person, showing the location of the detected objects that the person has over the image of the person. Some versions show a quasi-X-ray image of the person with less definition than backscatter X-rays machines.
- Advantages: Good imaging under ideal environments (no heavy clothing, no significant heat, no rain-wetted clothes, etc.)
- Disadvantages: Rain, heat, and heavy clothes obscure the image.
- Exploits: Enter when there is a heavy rain or wear heavy clothes.
• Spectrographic Detection Systems
- Application: A variety of electronic tools use spectrum analysis to “sniff” for explosives. Some are configured as wipes that are wiped on a package and then the wipe is placed into the detector, while others are handheld and sniff the article directly.
- Advantages: Very reliable detection, not quite as good as dogs. The very best can be swiped across a car door, steering wheel, or trunk lid and will detect minute traces of common explosives.
- Disadvantages: Only detect explosives leaving residue of vapor.
- Exploits: These are a very good deterrent. Very difficult to beat. However, certain explosive compounds are very difficult to detect, so be certain what you have to detect before relying on these alone.
• Radiological Detection Systems
• Standard Gamma Ray Detectors
- Application: Handheld and fixed gamma ray detectors sense gamma rays given off by most radiological compounds.
- Advantages: Relatively inexpensive.
- Disadvantages: Can be fooled by common articles such as crockery, bananas, and so forth, which naturally give off gamma rays.
- Exploits: Sufficient lead packaging, although this is very difficult to achieve.
• Video Gamma Ray Detectors
- Application: These are very rare, but effective. All solid-state video sensors are also sensitive to gamma rays and can thus be used with specialized software to detect gamma rays on a person, in a vehicle, or in a container.
- Advantages: Can use existing video camera as a sensor. Immediate identification of the suspicious person, vehicle, or object by the video camera.
- Disadvantages: Can be fooled by common articles such as crockery, bananas, and so forth, which naturally give off gamma rays.
- Exploits: Sufficient lead packaging, although this is very difficult to achieve.
Intelligent Video Analytics Sensors
• Types
• Video cameras can be embedded or used with intelligent video software to detect specific or abnormal behaviors that other sensors would not detect.
• Common detection algorithms include:
- Direction of travel (entry into an exit area)
- Crossing a virtual line (such as a person falling into a subway rail from a platform)
- Left Object detection (briefcase left)
- Placed Object detection (briefcase placed by a bench)
- Removed Object detection (painting on a wall)
- Lack of movement (person floating in a pool)
- Loitering behavior of one person among a crowd of people or one person alone in an area like a subway platform
- Crowd gathering
• Edge Sensors
• Application: Video cameras equipped with a Digital Signal Processing CPU inside the camera so that the processing is conducted “at the edge” rather than centrally at a server.
• Advantages: Scalable system. Costs of the system are gradual as you add more cameras. These require fewer servers and the cameras use less network bandwidth than some other systems.
• Disadvantages: The camera will process only the algorithms it is programmed to perform and no others.
• Exploits: One must know that a camera is intelligent and what algorithms it is processing.
• Conventional Central Processing Sensors
• Application: A normal digital video stream is decoded by a special server operating designated video motion algorithms.
• Advantages: Can detect many activities and behaviors that other sensors would not see or notice.
• Disadvantages: The system will process only the algorithms it is programmed to perform.
• Exploits: One must know that a video system is intelligent and what algorithms it is processing.
• Learning Algorithm Systems
• Application: Edge Sensors and Conventional Central Processing Sensors both require that a computer programmer design a specific algorithm to detect a specific unwanted behavior. There is another type called Learning Algorithm systems (such as BRS Labs) in which the system is completely ignorant out of the package, but “learns” over time what is normal in the field of view of the camera. These are Central Processing Systems that respond to any out of the ordinary behavior. They will, for example, equally detect a person carrying an M-16 into an airport or a person carrying a Banjo into the airport. Both are uncommon sights to the system.
• Advantages: These systems are very good at detecting almost any type of unwanted behavior and they get better over time at determining what is unusual but acceptable and what is unusual and unwanted.
• Disadvantages: No more costly than other Central Processing Intelligent Video systems.
• Exploits: Absolutely none. (Cloak of invisibility, maybe?)
Complex Alarm Sensing
Combinations of sensors should be used together to minimize nuisance alarms, for example, outdoor sensors used with video motion detection or beam detectors used with roll-up door position switches. Any combination of sensors that combines the abilities of both to make the exploit of the other impossible to use is a good design. Combinations can be used to verify alarms or as an “and” type logic cell to trigger only when both detectors alarm.
Beyond Alarm Detection
Alarms can be used for more than alerting. They can also be used to detect trends and patterns that would otherwise not be possible and to assist in vulnerability detection and analysis.
Trend Analysis
Trend Analysis is the art of determining if there is a trend developing or occurring around a specific type of alarm event. For example, does the same alarm always trigger whenever a train goes by or does the same alarm always trigger when it rains? Is there an instance of crowds gathering too near the edge of a subway platform at afternoon rush hour?
Trend Analysis can be conducted by hand or with specialized software. Common software includes PPM-2000, which can be interfaced with the Alarm/Access Control System and is capable of spotting trends that you otherwise might never notice.
Vulnerability Analysis
When a trend spots a common nuisance alarm condition, such as whenever a train goes by or when it is raining or snowing, this points out a vulnerability that should be covered by additional security countermeasures.
Chapter Summary
1. Basic alarm concepts include:
• Detection and Alarm Initiation
• Alarm States
- Secure
- Alarm
- Bypass
- Trouble
• Alarm Filtering (usually by using two or more sensors)
• Communications and Annunciation
• Alarm Assessment
• Response
• Evidence Gathering
2. Alarm sensors can be categorized into several broad areas:
• Outer Perimeter Detection Systems
• Building Perimeter Detection Systems
• Interior Volumetric Detection Systems
• Interior Point Detection Systems
• Intelligent Video Analytic Sensors
3. Outer Perimeter Detection Systems include:
• Gate Breach Detection System
• Seismic Detection Systems
• Fiber-optic Detection Systems
• Capacitance Detection Systems
• Leaky-coax Cable Systems
• Infrared and Laser Detection Systems
• Outdoor Passive Infrared Detectors
• Pneumatic Underground Detection Systems
• Microwave Detection Systems
- Monostatic Systems
- Bistatic Systems
• Ground-based Radar
4. Common Building Perimeter Detection Systems include:
• Balanced-biased Door Position Switches
• Photoelectric Beam Detectors
• Glass Break Detectors
• Seismic Detectors
5. Common Interior Volumetric Sensors include:
• Microwave Detection Systems
• Infrared Detection Systems
• Dual-technology Detection Systems
• Ultrasonic Detection Systems
• Thermal Imaging Systems
6. Common Interior Point Detection Sensors include:
• Duress Alarms
• Explosive Detection Methods and Systems
- Visual Inspection Approaches
- Dogs
- Package X-ray Scanners
- Personnel X-ray Scanners
- Millimeter X-ray Scanners
- Spectrographic Detection Systems
- Radiological Detection Systems
- Standard Gamma Ray Detectors
- Video Gamma Ray Detectors
7. Types of Intelligent Video Analytics Sensors include:
• Dedicated (specific) Algorithm Systems
- Edge Sensors (in the camera)
- Conventional Central Processing sensors (in a server)
• Learning Algorithm Systems
8. Combinations of sensors should be used together to minimize nuisance alarms, for example, outdoor sensors used with video motion detection or beam detectors used with roll-up door position switches.
9. Alarms can be used for more than alerting. They can also be used to detect trends and patterns that would otherwise not be possible and to assist in vulnerability detection and analysis.
10. Trend Analysis is the art of determining if there is a trend developing or occurring around a specific type of alarm event.
11. When a trend spots a common nuisance alarm condition, such as whenever a train goes by or when it is raining or snowing, this points out a vulnerability that should be covered by additional security countermeasures.
1) Basic Alarm Concepts include:
a. Detection and Initiation
b. Filtering and Alarm States
c. Communications and Annunciation
d. All of the above
2) Basic Alarm Concepts include:
a. Assessment
b. Response
c. Both a and b
d. Neither a nor b
3) Types of Alarm Sensors include:
a. Outdoor Perimeter Detection Systems
b. Building Perimeter Detection Systems
c. Interior Volumetric Detection Systems
d. All of the above
4) Types of Alarm Sensors include:
a. Interior Point Detection Systems
b. Intelligent Video Detection Systems
c. Neither a nor b
d. Both a and b
5) Which type of detection system can detect vehicles and footsteps from their sound?
a. Seismic Detection System
b. Capacitance Detection System
c. Infrared and Laser Detection System
d. None of the above
6) Which type of detection system uses radio frequency?
a. Seismic Detection System
b. Infrared and Laser Detection System
c. Leaky-coax Detection System
d. None of the above
7) Which of the following are valid alarm states?
a. Secure, Alarm, Bypass, and Enable
b. Secure, Alarm, Bypass, and Trouble
c. Unsecure, Alarm, Bypass, and Enable
d. Unsecure, Alarm, Bypass, and Trouble
8) Alarm Filtering helps avoid
a. Nuisance Alarms
b. False Alarms
c. Remotely Triggered Alarms
d. All alarms
9) Assessment is used to ensure that the alarm is
a. Invalid
b. Valid
c. Not a Security Event
d. Reported to the console
10) Response may typically involve sending either _______ or _______ to confront the intruder.
a. Police or Police Dogs
b. Patrol Car or Military
c. Police or Roving Security Officers
d. None of the above
11) One of the logs in an Alarm/Access Control System that keeps evidence is
a. The Evidence Log
b. The Alarm Event Log
c. The Alarm Action Log
d. None of the above
12) Building Perimeter Detection Systems may include:
a. Balanced-biased Door Position Switches
b. Photoelectric Beam Detectors
c. Glass Break Detectors
d. All of the above
13) Interior Volumetric Sensors may include:
a. Microwave Detection Systems
b. Infrared Detection Systems
c. Dual-technology Detection Systems
d. All of the above
14) Interior Point Detection Systems may include:
a. Duress Alarms
b. Explosives Detection Methods and Systems
c. Radiological Detection Systems
d. All of the above
15) Intelligent Video Analytics Sensors include:
a. Conventional Central Processing Sensors
b. Learning Algorithm Sensors
c. Both a and b
d. Neither a nor b
16) Alarms can also be used to conduct
a. Trend Analysis
b. Vulnerability Analysis
c. Both a and b
d. Neither a nor b
Answers: 1) d, 2) c, 3) d, 4) d, 5) a, 6) c, 7) b, 8) a, 9) b, 10) c, 11) d, 12) d, 13) d, 14) d, 15) c, 16) c
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.