2. Foundational Security and Access Control Concepts
Chapter objectives
1. Understand Risk and How to Manage Risk
2. Understand Types of Countermeasures
3. Understand Access Control System Principles
CHAPTER OVERVIEW
Access Control Systems are electronic systems that facilitate automated approval for authorized personnel to enter through a Security Portal without the need for a security officer to review and validate the authorization of the person entering the portal, typically by using a credential to present to the system to verify their authorization. A Security Portal is a door or passageway that creates an entry point in a security boundary. Common Security Portals include standard doors (such as shown inFigure 2.1using an HID Global Corporation reader), vestibules, revolving doors, and vehicle entry barriers.
Access Control Systems are electronic systems that facilitate automated approval for authorized personnel to enter through a Security Portal. This is done without the need for a security officer to review and validate the authorization of the person entering the portal, typically by using a credential to present to the system to verify their authorization. A Security Portal is a door or passageway that creates an entry point in a security boundary. Common Security Portals include standard doors, vestibules, revolving doors, and vehicle entry barriers.
Keywords: Access Control, Approval, Authorized, Automated, Door, Electronic, Entry Point, Passageway, Personnel, Portal
Author Information:
Thomas L. Norman, CPP, PSP, CSC, Executive Vice President, Protection Partners International
Access Control Systems are an important part of an overall Security Program that is designed to deter and reduce both criminal behavior and violations of an organization's security policies. But it is important to remember that it is only a part.
First, it is important to understand that Access Control is not an element of security; it is a concession that security programs make to daily operational necessities. Perfect security involves perfect Access Control. By that, I mean that in a perfect security environment, not one person can enter who is not absolutely known without question to be an ardent supporter of the security portion of the overall mission of the organization. In a real organization, that virtually never happens. Access Control Systems are an automated method to allow “presumed” friendlies to enter controlled, restricted, and secured areas of a facility with only minimal vetting at the Access Control Portal. Indeed, Access Control Portals are doorways through a security perimeter in which the entrants are “assumed” to be friendly, due to their status as an employee, contractor, or softly vetted visitor.
Understanding this, a new light is shed on the role of Access Control Systems. They are a vulnerability that exists right in the heart of the security system. As such, one can now understand why one must understand Risk, Managing Risk, and Types of Countermeasures to understand how to properly utilize Access Control Systems. One must also completely understand Access Control System principles so as not to create unseen vulnerabilities in the heart of the Security Program.
Understanding Risk
Types of Organization Assets
Every organization begins with a mission, which may be healthcare, mercantile, financial, education or something else. Each organization establishes programs in support of its mission. If healthcare, it may establish a hospital, outpatient clinics, and a pharmacy. If financial, it may establish a retail bank, investment bank, or stock brokerage. Each type of mission produces different types of programs in support of the mission.
Once the mission and programs are determined, the organization will set about to acquire assets to support the programs. There are only four types of assets (Figure 2.2) common to all types of organizations, missions, and programs:
• People
• Property
• Proprietary Information
• Business Reputation
People include employees, contractors, vendors, and visitors. Property may include real estate, fixtures, furnishings, and equipment. Proprietary Information is information that is unique to the organization and necessary for it to function and is not common to other organizations. This may include information such as the formula for Coca-Cola, vital records, customer lists, and accounting records. Finally, the organization will establish and try to grow its Business Reputation. Indeed, its future is tied intrinsically to the success of this effort, for any organization that loses its Business Reputation is going to suffer badly, almost always in ways that fundamentally affect its ability to carry out its core mission. Every organization of every type has these four types of assets, and they are what the security program is designed to protect.
The organization's assets become the targets of those who oppose the organization's mission.
Types of Users
Each organization has three types of users (people who use the facility). In the first category are people who intrinsically share and support the mission of the organization. In the second category are people who oppose the mission of the organization. In the third category are people who sometimes work in support of the mission and sometimes work in opposition to the mission of the organization.
The smallest number of users is those who either totally support or totally oppose the mission of the organization. Those who totally support the mission typically include shareholders, founders, and owners. Those who oppose typically include competitors, predatory criminals, and so forth. By far the largest segment among these is the third — those who sometimes work in support of and sometimes work in opposition to the mission of the organization.
This typically includes almost all employees, contractors, vendors, and visitors. As long as the mission of the organization aligns (in that moment) with the needs of the individual, then the individual supports the organization's mission. Where there is no alignment, the individual does not support the mission.
It is this vast third group that comprises most of the people who occupy the organization's facilities. Security Programs must effectively allow the normal operation of the organization and deal effectively with those who oppose (however temporarily) the mission's organization.
The purpose of the Security Program is to help ensure that all activity within the organization's facilities supports the organization's mission to the greatest extent possible, and works in opposition to the mission to the smallest extent possible.
Types of Threat Actors
A threat is any person who can create a man-made danger to the organization's security. A hazard is a natural or man-made equivalent of a threat where there is no intent to do harm, but harm nonetheless can result. Hazards include storms, earthquakes, fires, and safety risks. Threats include bombings, weapons usage, theft, diversion of assets, and undermining the organization's Business Reputation.
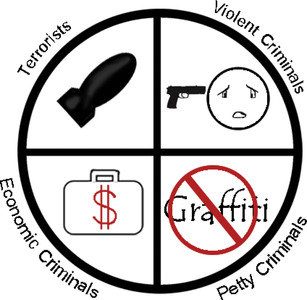
There exist only four types of security threat actors (Figure 2.3):
• Terrorists
• Violent Criminals
• Economic Criminals
• Petty Criminals
Terrorists are at the extreme end of the spectrum and have the greatest capacity to harm life and property. Although the probability of a terrorist event is very low, the consequences are high. Terrorists do not care about being quiet; quite the opposite. They often do not care about escaping with their lives. They only care about inflicting the maximum amount of death, injury, and damage possible at the least financial cost to themselves. Their only real concern is about not succeeding in their attack. Terrorism typically involves substantial planning; acquisition of weapons, chemicals, or explosives; and conducting surveillance. Sometimes there is a practice run and then the terrorists go operational.
Violent Criminals want to inflict control, injury, and/or death on their victims. If they care at all about economic benefit, then their violence is seen as a means to control their victims. Those with a tendency toward violence often prefer confrontation to a quiet economic crime. Violent criminals may be controlled or emotionally erratic. They may incorporate planning or spontaneously combust into violence without apparent reason or in response to an innocent comment or minor insult. Once violence ensues, all participants tend toward emotional responses. As emotional responses are not conducive to carrying out a plan, plans often go awry and the situation escalates. Escape may or may not be a part of the violent criminal's plan, and his actions may or may not allow for escape.
Economic Criminals are after money or goods. They do not want to be caught, and they place this goal above all others. Economic criminals may be strategic (planning, acquisition of tools and weapons, conduct surveillance, plan their escape, perhaps a practice run and then they go operational), or they may be opportunistic, striking when the opportunity presents itself. Many economic criminals do not put much effort into planning. Only a few are strategic and methodical. Generally, the higher the risks, the greater the planning. Relatively few economic criminals are strategic enough to fully plan a crime from inception to escape in any methodical way. Economic criminals may work alone or in a group. Better group criminals have an established hierarchy of leadership that is followed unquestionably. Most groups are haphazard and members of the group will quickly turn on the others when their own life or freedom is at risk. Some economic criminals are also violent criminals. In such cases their “lean” may be either toward a successful economic crime or their violent side may prevail such that they will quickly abandon the economic crime and go to violence when confronted. Many economic criminals do not want to encounter anyone in the commission of their crime. However, a significant number of economic criminals intentionally encounter victims and often use violence to control their victims to get them to comply with their directions. In such cases, some intend to leave their victims alive and others wish to leave no witnesses.
Petty Criminals are individuals who commit petty crimes such as graffiti, drunken disturbances, loud behavior, and prostitution. Petty criminals reduce the attractiveness of the environment to normal behavior and create an environment that encourages unacceptable behavior.
It is important to understand how each type of potential threat actor can affect the facility to be protected. One must develop scenarios for each type of threat actor and evaluate vulnerabilities and develop countermeasures based on such scenarios. Effective security managers understand threat scenarios and run them through their heads effortlessly. It is a good skill to develop as a form of very practical and effective game theory.
Understanding Criticalities and Consequences
Not all assets are equal. Some are more critical to the operation of the facility than others. Entire factory operations have stopped because of the failure of a 25 cent part. Such assets are called critical assets. A critical asset is any asset that is critical to the flow of operations or down-line operations. Factors affecting criticality include the importance of its role in the operation of the organization and whether or not it is deployed in a non-redundant manner and also how difficult or time-consuming is it to repair or replace the asset to get the operation going again. Criticality assessment is the skill of assessing how critical assets are to the mission of the organization. Similarly, the loss of some assets has a higher consequence than others. The loss of any human is devastating, but the loss of the person with the necessary skills to maintain the organization's viability is a greater loss and therefore more consequential. The loss of a critical asset is more consequential than the loss of a non-critical asset.
The loss of some assets may present a higher consequence to the organization or to the community than others; for example, an accident in the manufacture or storage of methyl isocyanate gas represents a very high consequence not only to the organization but to the community where it might occur. 1 Many organizations have fallen due to the loss of their Business Reputation. Most of those organizations did not consider their Business Reputation to be either critical or of significant consequence before the event. Consequence analysis is the skill of determining which assets have the greatest potential for consequence.
1In the world's worst industrial catastrophe, a leak of methyl isocyanate gas and other chemicals at the Union Carbide plant at Bhopal, Madhya Pradesh, India, resulted in an immediate death of 3,787 people and ultimately claimed over 15,000 lives.
Security Programs should be designed to protect those assets with the greatest consequence first.
Understanding Vulnerability
A vulnerability is an attribute of a facility that a threat actor can exploit to carry out a threat action. Vulnerabilities may include opportunities for entry, for access to assets, for concealment of activities or staging of stolen items prior to taking from the facility, for diversion of attention, for taking control of an area, or for escape. Vulnerabilities may be physical or procedural. Vulnerabilities exist in every facility and every security system and cannot be completely eliminated; however, it is imperative to mitigate vulnerabilities that could be easily exploited.
Vulnerabilities can be mitigated through physical, procedural, or electronic measures, or a combination of these. Vulnerability equals opportunity.
Understanding Probability
Probability is the likelihood of an event occurring. Probability is a key factor in determining risk, and equally it is a key factor in determining how best to mitigate risk. Probability can be affected by the number of employees, contractors, vendors, and visitors; by the frequency of occurrence of an action such as an access control event; by the number of items affected; and by the environment.
Probability and consequence often go hand in hand. High-probability, low-consequence events present relatively minor risk whereas low-probability, high-consequence events may present very high risk.
Factors affecting probability include:
• Interest level including the value of assets to potential threat actors
• Opportunities available to exploit
• Number of potential threat actors who might be interested in carrying out a threat scenario
• Effectiveness of existing security countermeasures (what is the risk to potential threat actors)
What Is Risk?
Risk is the potential for a threat action to occur. Risk factors include Probability, Vulnerability, and Consequences. Risk is the final calculation taking into concern the potential threat actors, their potential interest, and available vulnerabilities to exploit. Risk works both ways. An organization can be at risk of theft of an asset and the thief can be at risk of not succeeding or being discovered and prosecuted.
A key factor in the risk formula is consequences. The higher the possible consequences, the higher the risk. Thus, low-probability, high-consequence threat scenarios rank higher on risk than high-probability, low-consequence threat scenarios. Although terrorism is low in probability, its consequences make it a higher risk.
See the author's earlier book Risk Analysis and Security Countermeasure Selection for a complete discussion on risk.
Managing Risk
Methods of Managing Risk
Risk can be managed by reducing the potential number of threat actors who have access to a given asset, reducing the vulnerabilities related to the asset, or reducing the potential consequences of the asset being attacked. Risk may also be reduced by increasing the risk to the potential threat actor. These may be achieved by modifying the physical, electronic, or procedural environment.
For example, by placing an asset in a more physically protected environment, risk is reduced. By requiring greater scrutiny of persons entering the area of the asset to be certain that they do not pose a threat, risk is reduced. By placing video cameras along the pathway to and from the asset and around the asset and recording those cameras, risk is reduced because it creates a higher risk to potential threat actors and provides evidence for investigations and prosecution if the asset is taken or damaged.
How Security and Access Control Programs Help Manage Risk
Organizations develop Security Programs to manage risk in an organized and methodical way. By assigning a manager who is competent in security matters and also a competent personnel manager, the organization can organize the security process into a business process that supports the goal of protecting the assets of the organization while not interfering with the natural business of the organization.
Effective Security Programs use a layered approach to protecting the organization's assets. The most critical and consequential assets are the most protected, and a threat actor must engage multiple layers of physical, procedural, and electronic security measures to acquire such assets.
A good security manager will develop a Security Program that:
• Maintains focus on the mission of the organization at all times
• Supports the natural activities of the organization's programs and the business culture
• Is aware of all of the assets of the organization and has prioritized the assets by criticality and consequences
• Has analyzed risk comprehensively
• Has developed a set of security policies and procedures to address the risks in conformance with the business culture
• Utilizes a layered approach to security countermeasures
• Engages local, state, and federal law enforcement appropriately
• Trains the security force, employees, and visitors as needed to achieve compliance with the organization's security policies
• Continuously evaluates its own effectiveness and continuously improves the effectiveness of the program
Security Program Elements
A good Security Program will include all of the following elements:
• The program will be based on a comprehensive Risk Analysis
• The program will be based on a set of Security Policies and Procedures (Security Plan) that addresses all of the elements of the Risk Analysis
• The program will include:
• An Access Control element
• Physical Security elements
• Intrusion Detection elements
• Security Communications
• Coordination and Response elements
• Evidence Gathering and Analysis elements
• Investigation capabilities
• Continuous Program Effectiveness Analysis and Improvement
The Importance of a Qualified Risk Analysis
It is surprising how many Security Programs are developed and run without a comprehensive Risk Analysis. Any Security Program that is not based on a comprehensive Risk Analysis will have unknown vulnerabilities. Unknown vulnerabilities present unknown risk that can be easily exploited by a thoughtful threat actor.
Security Programs that are not based on a proper Risk Analysis are virtually certain to cost more and be less effective than programs based on a proper Risk Analysis.
Running a Security Program without a proper Risk Analysis is analogous to running a business without an accounting system or audit. The business will go broke, and the Security Program will fall victim to security exploits.
The Importance of Security Policies and Procedures
It is equally surprising how many Security Programs are run haphazardly without a formal set of Security Policies and Procedures. Security Policies and Procedures are the foundation documents of a good Security Program. Without Policies and Procedures, the program will necessarily be haphazard and disorganized. Without policies, every response is spontaneous and based solely on the judgment of the individual security officer or manager. There is no continuity. Such programs are a wellspring of litigation opportunities, because there is no consistency and the judgment of individual security officers is rarely based on criminal law or company policy.
Further, the lack of security policies and procedures is a vulnerability due to the uneven approach of patrols, investigations (if any), and enforcement. In such cases the program generally swings toward accommodating employees and visitors to the detriment of the security of the organization, because individuals' complaints against individual security officers cannot be refuted.
Such programs often depend heavily on electronic systems to “enforce” security, and such systems are developed to address the most urgent security issues without regard to dozens or hundreds of other vulnerabilities that remain unaddressed. Thus money spent on electronics is money wasted.
No Security Program can succeed without proper Security Policies and Procedures.
Types of Countermeasures
There are three types of Security Countermeasures: Hi-Tech, Lo-Tech, and No-Tech. These three must be used in combination to create a layered and effective security program. No single security countermeasure is effective against all threat scenarios. Access Control Systems, in particular, are a type of “controlled vulnerability” as each access control portal is a hole in the security boundary.
Hi-Tech
Hi-Tech systems include all electronic systems. Typically these include Alarm/Access Control Systems, Video Systems, Communications Systems, Integrated Security Systems, Specialized Detection Systems, and Computerized Systems.
Hi-Tech systems serve to automate repetitive functions, monitor continuously without error, and report to and facilitate communication and coordinated response by security staff.
Increasingly, Hi-Tech systems are used to handle vast amounts of information that could never be handled cost-effectively by humans. Examples of these include intelligent video analytics that analyze a video scene evaluating human activity for unwanted behaviors and integrated systems that use multiple credential methods (such as a card reader and facial recognition), automated weapons screening, and package X-ray screening to allow entry to a high security area via an automated portal.
Although there is an increasing focus on Hi-Tech systems in Security Programs, they should be the last element considered. Lo-Tech and No-Tech elements form the basis for an effective Security Program and Hi-Tech elements amplify the capabilities of the Lo-Tech and No-Tech elements. No matter how elegant an Integrated Electronic Security System may be, they cannot substitute for a solid security program based upon physical (Lo Tech) and procedural (No Tech) countermeasures.
Lo-Tech
Lo-Tech elements are physical security elements that are usually among the most cost-effective security measures any organization can employ. Lo-Tech elements include such things as Locks and Barriers, Lighting, Fencing, Signage, Other Physical Barriers, and Crime Prevention Through Environmental Design (CPTED) measures. CPTED is an architectural discipline that involves creating architectural spaces that encourage appropriate behavior and discourage inappropriate behavior. It comprises three basic elements:
• Territorial Reinforcement
• Natural Surveillance
• Natural Access Control
Lo-Tech elements are effective because in most cases they represent a single one-time investment that works daily without fail. Lo-Tech elements can be used to funnel people to controlled access points, alert visitors to security policies, prevent entry to unauthorized people, provide a deterrent, and stop intruders cold with unexpected barriers.
No-Tech
No-Tech elements are those security elements that have no technology:
• A Comprehensive Risk Analysis
• Policies and Procedures
• Security Guard Programs
• Security Awareness and Training
• Law Enforcement Liaison
• Investigations
• Dogs and other non-technology related programs
No-Tech elements are among the most effective due primarily to their active nature. No-Tech elements are the parts of the security program that users notice most. Every interaction with a Security Officer is somehow memorable; the same cannot be said for every interaction with a card reader. Users are more likely to criticize or complain to or about their interactions with Security Officers than their interactions with technology.
Mixing Approaches
Successful Security Programs mix Hi-Tech, Lo-Tech, and No-Tech countermeasures to achieve an effective and cost-effective program. Each element has its strengths and weaknesses, and each element has its own effect on the organization's business culture. By mixing Hi-Tech, Lo-Tech, and No-Tech approaches, a security program is more likely to achieve repeatable desired results.
Layering Security Countermeasures
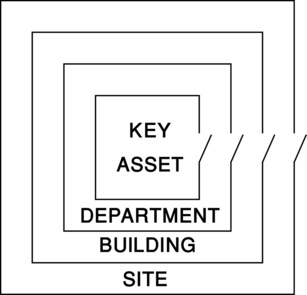
Layering means that an asset is protected by multiple layers of countermeasures from the outside in. To get to a valuable asset such as the Information Technology Server Room, a threat actor must encounter a number of security elements, each one a risk to his success. The more layers, the less likely it is that a threat action will succeed.
Layers should use mixed technology approaches. At the outside, the threat actor encounters the outer fence, then lights, then perimeter sensors, then cameras, then the building boundary, then door/window detection, then more cameras, then motion alarms, then the department perimeter with its alarms and access control and cameras, and finally, the controls in the Server Room. The threat actor will encounter all of these countermeasures on the way out as well, further reducing the likelihood of a successful exit and unnoticed escape (Figure 2.4).
Access Control System Concepts
Access control is all around us. From the lock on your front door or car door to the Personal Identification Number (PIN) for your Automated Teller Machine (ATM) card, we encounter access control systems every day. Even with the club doorman at the velvet rope looking down his nose at eager young club-goers, access control is everywhere. Access Control Systems are designed to help ensure that only authorized or qualified people are allowed to enter an exclusive space.
Electronic Access Control Systems utilize a computer, credential, credential reader, and door lock to control access electronically. Elements at the door also include an alarm point to tell if the door has opened without authorization and a request-to-exit sensor to allow the door to unlock for those inside to exit without setting off an alarm. The access control portal is coupled with a wall or fence to prevent going around the portal.
Credentials: Access control systems rely on credentialed users. Credentials may be something you have, something you know, or something about you that is unique. Something you have might be an access card, something you know might be a keypad code, and something about you that is unique might be your fingerprint.
Credential Readers: The system combines the credential with a credential reader (card reader, keypad, or biometric reader) to send a code to the computer where it is compared to a database of codes. If a match is found, the computer orders the portal to unlock the door and allow your entry (accompanied by a green light on the credential reader). It also makes an entry into a data log to record the entry. If no match is found, it rejects your entry attempt (buzzer at the door accompanied by a red light on the credential reader) and it enters an entry into the log recording the improper attempt including the card number or improper keypad code.
Who, Where, and When: Electronic Access Control Systems focus on who, where, and when, and access is granted on a “Who, Where, and When” formula. Each authorized user (Who) is valid for given portals (Where) and on a certain authorized schedule (When) — who is allowed to enter, where can they enter, and when are they allowed to enter or exit. Historically, this was handled by keys and mechanical locks. Authorized users were given a key for each lock, and the keys were good at any time. This resulted in many keys and when a key was lost, the lock had to be re-keyed and all key holders had to be issued a new key. This was not practical for large facilities and did not provide for time-sensitive access control. With Electronic Access Control Systems, each user is given only one key (like an access card) and the Access Control System database records where and when the card is valid. If the user loses his card, the card is voided in the database and a new card is issued. No other cardholders are affected, and no locks must be re-keyed.
Two-Factor Authorization: Additional security can be ensured by using two-factor authorization. In this case, access to a critical area such as a server room or vault requires the presentation of two credentials in a short period of time, typically one from an employee and one from a manager. Another form of two-factor authorization is created by requiring the user to present two factors such as a card and a keycode, or a card and a biometric credential such as a fingerprint.
Employee and Visitor Access Control: Cards are typically issued to employees and worn on their clothes by means of a clip or lanyard. Access Control Systems in facilities that receive visitors can be set up with a special visitor card to allow for contractors, vendors, and visitors to have access to certain designated areas. Typically, the Visitor Access Control system operates as a subsystem of the Access Control System and works with either a temporary paper access card or with a conventional access card specially marked to show that the cardholder is a visitor.
Photo Identification: Most Electronic Access Control Systems utilize access cards that bear the photo and name of the cardholder. This aids in identification of users and helps ensure that the cardholder is indeed the valid user of that specific card.
Alarms: Most Access Control Systems incorporate an alarm monitoring element. This allows intrusion detection to the facility or zones within the facility. The Access Control System will also record the event into a log file. Many if not most Security Portals utilize an alarm sensor to detect if the portal has been forced open or left (propped) open. The software for a portal is intrinsically capable of managing the Security Portal alarm. Those alarms are also bypassed (ignored) automatically when the door is opened legally to enter or to exit.
Events: The concept of Events is central to the real power of advanced Alarm/Access Control Systems. An Event is an automatic action that can be taken by the system in response to a stimulus. Examples of events are as simple as unlocking a door in response to a valid card or as complex as turning on after-hours path lights from the parking garage to a worker's office space while simultaneously starting up the air conditioning system for his office and warming up the coffee pot. Advanced systems allow for complex events that take multiple conditions and logic into consideration; for example, changing what a guard will see on a workstation in response to the time of day and the Department of Homeland Security threat level.
Video System Integration: In response to an alarm or an unauthorized access attempt (and many other kinds of events), the Alarm/Access Control System can cause the Security Video System to display one or more video cameras that are related to the event. This can help security staff to quickly assess the nature and seriousness of the security incident and to coordinate an appropriate response.
Security Intercom System Integration: Security Intercoms can be interfaced with the Alarm/Access Control System to perform two important functions:
• Make the Intercom Call an Event in the system's database
• Cause the Access Control System to display and record appropriate video cameras in response to an Intercom call
Guard Tours: Access Control Systems can also be used to ensure that security staff is conducting a scheduled guard tour of the facility several times each night; many Access Control Systems can be programmed to require the tour guard to use access card readers as the checkpoints for his/her guard tour. These are sequenced and timed to ensure that each guard tour stop is checked in an appropriate time window.
Anti-Passback: As with many things, there is always somebody who tries to cheat the system. This is also true for Access Control Systems. One common method is a technique called “Passback.” This occurs when a valid access card holder uses his card to allow entry to one or more unauthorized persons who are with him. This happens often at Parking Access Control Systems when a valid card holder uses his card to allow entry to the employee parking garage for his own card, but he has a visitor in the car behind him who is not allowed to park in the employee garage. As the parking gate rises, the valid card holder leaves his card on top of the card reader pedestal and then he drives into the garage. The visitor enters the gate area, rolls down his window, and picks up the card that has been left on top of the card reader pedestal and presents the card to the parking garage card reader. The Access Control System sees that the card is valid and opens the gate again for the same person who has already entered. Access Control Systems with an Anti-Passback feature require that each card leave the garage before they can re-enter.
Roll Call Reports, Mustering, and De-Mustering: A roll call report is a function that can display all users in (or out) or a certain alarm zone at a given time (manually or automatically). The Mustering feature is used to gather users in a safe area during an emergency and to account for their presence. When the emergency is over, users may be required to return to their work area. A roll call report can then verify that all users are back at their work areas.
Occupancy Restrictions and N-Man Rules: Organizations can limit access to an access zone to a designated minimum or maximum number of users. This can help ensure that fire code occupancy rules are obeyed. The N-Man Rule ensures that a minimum number of people are present before entry is allowed, such as ensuring that four bank employees are present before opening the external employee entry door in order to deter robberies.
Escorted Visitors: Some systems can enforce the Escorted Visitor Rule, which ensures that all escorted visitors must be associated with a valid user before entering a given access zone.
Types of Users
Typical Access Control System users include management, employees, contractors, vendors, and visitors. Each of these is given access to areas as they are needed and for times as may be appropriate.
Types of Areas/Groups
Most Access Control Systems define access portals according to a logical grouping. This might include grouping by departments, buildings, or functions (janitorial employees). Thus, a janitorial employee might have access to all floors and the service lift of the building to which he/she is assigned. Certain users may be authorized for all areas.
User Schedules
Most access credentials are authorized on a schedule. The schedule may correlate to the user's working hours or some other reasonable program. Certain employees (management, maintenance, etc.) may be authorized for all hours.
Schedules may also include holiday and special events schedules. Most systems accommodate seven-day schedules and are programmed around the annual calendar. Some systems are also flexible enough to handle special schedules; for example, offshore oil rigs may work on a ten day on/ten day off schedule.
Portal Programming
Typically each portal is assigned to an Access Group, such as a department or an elevator bank.
Credential Programming
Typically each user's credential is assigned to a user group. This simplifies programming so that each user does not have to be assigned to individual doors and schedules.
Group and Schedule Programming
Access Portals and Users can be assigned to Access Portal Groups or Access User Groups, the combination of which allows for simplified system programming. Otherwise, every user would have to be programmed for access to each individual portal on individual schedules.
Chapter Summary
1. Every organization begins with a mission and develops programs to support its mission. These programs acquire assets to support the programs, and those assets become targets of users who oppose the mission of the organization.
2. Every organization has only four types of assets: People, Property, Proprietary Information, and the organization's Business Reputation.
3. There are three types of users of every facility: those who support the organization's mission, those who oppose the mission, and those who sometimes support and sometimes work in opposition to the organization's mission.
4. The purpose of the Security Program is to help ensure that all activity within the organization's facilities is in support of the organization's mission to the greatest extent possible, and works in opposition to the mission to the smallest extent possible.
5. Potential Threat Actors include terrorists, violent criminals, economic criminals, and petty criminals.
6. Some assets are more critical than others to the operation of the organization and the loss of some assets presents a higher potential for consequences to the organization and the community than others.
7. Vulnerabilities are any condition that can be exploited by a threat actor to carry out a threat action.
8. Probability is the likelihood of a security event occurring.
9. Risk is the potential for a threat action to occur. Risk factors include Probability, Vulnerability, and Consequences.
10. Risk can be managed by reducing the potential number of threat actors who have access to a given asset, reducing the vulnerabilities related to the asset or reducing the potential consequences of the asset being attacked.
11. Effective Security Programs use a layered approach to protecting the organization's assets.
12. Any Security Program that is not based on a comprehensive Risk Analysis will have unknown vulnerabilities.
13. Security Policies and Procedures are the foundation documents of a good Security Program. Without Policies and Procedures, the program will be haphazard and disorganized.
14. There are three types of Security Countermeasures: Hi-Tech, Lo-Tech, and No-Tech.
15. Hi-Tech countermeasures are electronic systems such as alarm/access control, CCTV, and communications systems.
16. Lo-Tech countermeasures include locks, lighting, security landscaping, and CPTED.
17. No-Tech countermeasures include the Risk Analysis, Policies and Procedures, Guards, Dogs, Security Awareness Programs, and Law Enforcement Liaison.
18. Security Countermeasures should be layered for complete protection. Layering means that an asset is protected by multiple layers of countermeasures from the outside in.
19. Electronic Access Control Systems utilize a computer, credential, credential reader, and door lock to control access electronically.
20. Access credentials may be something you have, something you know, or something about you that is unique.
21. Credential readers read credentials and send identity data to an access controller that verifies the data against a database of authorized users.
22. Access is granted on a “Who, Where, and When” formula. Each authorized user (Who) is valid for given portals (Where) and on a certain authorized schedule (When).
23. Higher security portals may use “Two-Factor” authorization.
24. Larger systems often use both employee and visitor access control systems.
25. Users include employees, contractors, vendors, and visitors.
26. Most Access Control Systems define access portals according to a logical grouping such as departments, floors, and elevator banks.
27. Most access credentials are authorized on a schedule. Users can also be assigned to a group that includes a schedule.
28. Many portals are also part of a group, such as doors in a department.
1) What is access control?
a. Element of security
b. A concession that security programs make to daily operational necessities
c. An organization's security program
d. All of the above
2) The four types of assets in organizations are
a. Employees, Equipment, Proprietary Information, Business Reputation
b. Employees, Property, Accounting Records and Customer Lists, Business Reputation
c. People, Property, Accounting Records and Customer Lists, Business Reputation
d. People, Property, Proprietary Information, Business Reputation
3) Types of users who use the facility
a. People who intrinsically share and support the mission of the organization
b. People who oppose the mission of the organization
c. People who sometimes work in support of the mission and sometimes work in opposition to the mission of the organization
d. All of the above
4) Who are the terrorists?
a. Incorporate planning or spontaneously combust into violence without apparent reason, or in response to an innocent comment or minor insult
b. Care about inflicting the maximum amount of death, injury, and damage possible at the least financial cost to themselves
c. Are after money or goods
d. Reduce the attractiveness of the environment to normal behavior and create an environment that encourages unacceptable behavior
5) Who are the Violent Criminals?
a. Incorporate planning or spontaneously combust into violence without apparent reason, or in response to an innocent comment or minor insult
b. Care about inflicting the maximum amount of death, injury, and damage possible at the least financial cost to themselves
c. Are after money or goods
d. Reduce the attractiveness of the environment to normal behavior and create an environment that encourages unacceptable behavior
6) Who are the Economic Criminals?
a. Incorporate planning or spontaneously combust into violence without apparent reason, or in response to an innocent comment or minor insult
b. Care about inflicting the maximum amount of death, injury, and damage possible at the least financial cost to themselves
c. Are after money or goods
d. Reduce the attractiveness of the environment to normal behavior and create an environment that encourages unacceptable behavior
7) Who are the Petty Criminals
a. Incorporate planning or spontaneously combust into violence without apparent reason, or in response to an innocent comment or minor insult
b. Care about inflicting the maximum amount of death, injury, and damage possible at the least financial cost to themselves
c. Are after money or goods
d. Reduce the attractiveness of the environment to normal behavior and create an environment that encourages unacceptable behavior
8) A critical asset is
a. Any asset that presents a lower consequence to the organization or to the community than others
b. Loss of any person with the necessary skills
c. Any asset that is not critical to the flow of operations or down-line operations
d. Any asset with medium importance of its role in the operation of the organization
9) What is vulnerability?
a. An attribute of a facility that a threat actor can exploit to carry out a threat action
b. Any asset that is critical to the flow of operations or down-line operations.
c. Can be completely eliminated
d. All of the above
10) Factors affecting probability include:
a. Interest level including the value of assets to potential threat actors
b. Opportunities available to exploit
c. Number of potential threat actors who might be interested in carrying out a threat scenario
d. All of the above
11) Risk can be managed by
a. Reducing the potential number of threat actors who have access to a given asset
b. Reducing the vulnerabilities related to the asset or reducing the potential consequences of the asset being attacked
c. Increasing the risk to the potential threat actor
d. All of the above
12) Security Countermeasures come in these types:
a. Hi-Tech, Lo-Tech
b. Hi-Tech, No-Tech
c. Hi-Tech, Lo-Tech, No-Tech
d. Hi-Tech, Me-Tech, No-Tech
Answers: 1) b, 2) a, 3) d, 4) b, 5) a, 6) c, 7) d, 8) b, 9) a, 10) d, 11) d, 12) c
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.