19. Security System Integration
Chapter objectives
1. Understand Why Security Systems Should Be Integrated
2. Discover Security System Integration Concepts
3. Understand the Benefits of System Integration
4. Learn about Types of Integration
5. Study Some Examples of Security System Integration
6. Pass a Quiz on Security System Integration
CHAPTER OVERVIEW
While Alarm/Access Control Systems, Security Video Systems, and Security Intercom Systems all are powerful tools to help manage risk for an organization, they become even more powerful when integrated together into a single, comprehensive security system.
Security Systems should be integrated in order to help the security program operators minimize the organization's risk. Benefits of Security System integration include a more complete awareness of the security conditions across the organization, faster and more effective detection of inappropriate behavior, more rapid and accurate assessment and filtering of actual threats vs. nuisance alarms, the ability to delay aggressors both coming into and on their way out of the organization's facilities, better coordinated responses to security events, and the ability to gather coordinated evidence of security events.
We will also discuss types of system integration and look at some examples of effective system integration.
Alarm/Access Control Systems, Security Video Systems, and Security Intercom Systems all are powerful tools to help manage risk for an organization, but they become even more powerful when integrated together into a single, comprehensive security system.
Security Systems should be integrated in order to help the security program operators minimize the organization's risk. Benefits of Security System integration include a more complete awareness of the security conditions across the organization, faster and more effective detection of inappropriate behavior, more rapid and accurate assessment and filtering of actual threats versus nuisance alarms, the ability to delay aggressors both coming into and on their way out of the organization's facilities, better coordinated responses to security events, and the ability to gather coordinated evidence of security events.
The types of system integration are discussed and some examples of effective system integration are reviewed.
Keywords: Access Control, Alarm, Behavior, Detection, Integrated, Intercom, Nuisance, Threat, Video
Author Information:
Thomas L. Norman, CPP, PSP, CSC, Executive Vice President, Protection Partners International
Why Security Systems Should Be Integrated
In order to talk about why security systems should be integrated, we need to first understand the theory of protecting organizations' assets.
Every organization begins with a mission. The organization develops programs in support of its mission. If the organization's mission is banking, depending on the country, they may develop programs to include retail branch banks, a credit card program, loan programs, investment banking program, a real-estate management program, currency, oil or stock trading, and so forth. As they develop programs, the organization will acquire assets in support of its programs. These assets always include:
• People
• Employees
• Contractors
• Vendors
• Visitors
• Customers
• Property
• Real Property (Land and Buildings)
• Fixtures, Furnishings, and Equipment
• Proprietary Information
• Vital Records
• Patents, Formulas, etc.
• Customer Lists
• Accounting Records, etc.
• The Organization's Business Reputation
These assets have appropriate and inappropriate users. Appropriate users include those who use the assets for the benefit of and with permission by the organization. Inappropriate users are those who seek to use the organization's assets for their own benefit rather than for the benefit of the organization, or in some cases the assets are used against the benefit of the organization.
Inappropriate users can include employees using a Social Network Web site on company time, too many purchases and returns from some customers, or something more serious. “Threat Actors” are a category of inappropriate users who present a criminal or terroristic threat to the welfare of the organization and they act on that threat. Threat actors include:
• Terrorists
• Violent Criminals
• Economic Criminals
• Petty Criminals
Organizations must protect their assets from Threat Actors or face serious reductions in their ability to meet their mission. The role of an organization's Security Program is to improve the likelihood of appropriate use of its assets and reduce the potential for inappropriate use of the organization's assets. They do that by analyzing the risk they face and developing appropriate security countermeasures to balance the risk.
In its simplest form, Risk is a combination of the existence of an active threat actor interested in the organization's assets (probability, P), exploitable vulnerabilities (V), and the degree of consequences (C) of that threat scenario being carried out or R = (P*V*C).
A high probability of a scenario coupled with high vulnerabilities that could result in high consequences represents a high risk. A low probability with low vulnerabilities, resulting in low consequences, represents a low risk. All other things being equal, Threat Scenarios with Low Probability and High Consequences should receive a higher risk score than those with Higher Probability and Low Consequences. For this reason I recommend that one consider risk as R = (P*V), prioritized by Consequences. While similar, the second simple risk formula results in a more accurate risk assessment.
Once risks are assessed, security countermeasures should be developed. These should always begin with a Comprehensive set of Security Policies and Procedures, upon which all other countermeasures are built. This is to ensure that all countermeasures have a practical basis in security policy.
Good Security Programs include all three types of security countermeasures:
• Hi-Tech
• Lo-Tech
• No-Tech
Hi-Tech Countermeasures include electronic systems: Alarm/Access Control, Digital Video, Security Intercoms, 2-way Radio, X-ray and Metal Screening, and so forth. Lo-Tech Countermeasures include Locks, Barriers, Lighting, and Signage, and No-Tech Countermeasures include Policies and Procedures, Security Staffing, Dogs, Law Enforcement Liaison Programs, and Security Awareness Programs. These three types of countermeasures should always be used together in a layered approach to reduce risk.
All security countermeasures are intended to
• Deter Unwanted Behavior
• Detect Inappropriate Behavior
• Help Assess what has been Detected
• Help Security Staff Respond to Security Events
• Delay Intrusions and Exits of Offenders
• Gather Evidence of Security Events for Prosecution and Training
Since Deterrence varies substantially depending on the commitment of the Threat Actor, it cannot be accurately calculated, so you should not factor Deterrence into the Countermeasure Balancing formula. Remember, all security programs should be layered such that the most valuable assets are protected by multiple layers of Detection, Assessment, Delay, and Response. That is, a Threat Actor should have to go through multiple rings of detection and barriers to get to an asset and to get that asset back out of the organization's possession, encountering delaying mechanisms along the way in and out. At all times, the Security System should be gathering Evidence.
Designing an effective Electronic Security System is a challenging task. But Electronic Security Systems do their job better when their various components are “integrated” into a single, comprehensive system allowing each part of the overall system to “feed” information to and draw from the other parts of the system to enhance functions and effectiveness.
A well-designed security system should filter unnecessary information; present relevant information in a quick, easy-to-understand format; and provide the Security Console Officer and Supervisor with quick and relevant options to defend the organization's assets.
Integration Concepts
Security is not a challenge of technology; it is a challenge of imagination. The challenge of Security System Integration is also a challenge of imagination more than technology. When thinking about integrating systems, you must ask yourself the following questions:
• If I eliminated all of the technology and had a highly qualified guard at the location in question, what tasks would I want to perform?
• What information would I need to make decisions?
• What resources would I like to have to be able to carry out those tasks?
Let the integration begin…
• Suppose that you are at a Security Console and there is an alarm in a weapons storage facility.
• If I eliminated all of the technology and had a highly qualified guard at the location in question, what tasks would I want to perform?
- Confirm the alarm (an intruder, not a newspaper blowing across the field of view of a camera)
- Determine what the intentions of the intruder were and what weapons or tools he might have or be using
- Know where the intruder is going while a response is on its way
- Delay the intruder's progress
- Intersect and disorient the intruder, stop the intrusion, and apprehend the intruder
• What Information would I need to make decisions?
- Confirm that there is in fact an intrusion
- Confirm the description of the intruder
- Confirm the direction, path, and speed of the intruder
- Determine what weapons and tools the intruder is using and to the extent possible the aggressiveness of the intruder
• What resources would I like to have to be able to carry out those tasks?
- Alarm System
- Digital Video System Cameras at the point of entry and along the path of the intruder
- Graphical User Interface (GUI) Maps showing locations of the Alarm and Cameras
- Remotely Deployable Barriers
- Remotely Controllable Lighting
- Communications to Responding Guards
• What resources are available to integrate?
• Alarm/Access Control System
• Digital Video System
• Deployable Barriers
• Remotely Controllable Lighting
• 2-way Radio System
• Armed Security Guards each with a GPS-enabled mobile phone
• How would we integrate these systems?
• Alarm/Access Control System notifies Main Console on a GUI Map, displaying the location of the alarm.
• Alarm/Access Control System also notifies Digital Video System, which displays an array of video cameras inside and outside of the alarmed perimeter door.
• The area was also pre-recorded so the Console Operator can also see the area of the alarmed door in the time leading up to the alarm.
• The Console Operator can witness the description of the intruder and note the tools he is using and that he is carrying a sidearm.
• Zooming out slightly on the Console GUI Map, the Console Officer can see the locations of Roving Armed Guards on the Compound.
• The Console Officer notifies the three nearest guards of the alarm and vectors them to the alarmed door, while giving them a description of the intruder and instructing the guards that he is carrying a sidearm.
• During this time, the Console Operator follows the intruder on the Digital Video system and GUI Map and releases held-open fire doors in the path of the intruder and engages electric locks on those doors, delaying the intruder at each door.
• The Console Officer notifies the Police Emergency number and Police respond to the site of the Weapons Storage Compound.
• As the armed guards combine forces at the point of entry door, the Console Officer relays the location of the intruder.
• Armed Guards converge on the intruder who places his weapon on the floor when confronted by multiple armed guards.
• The intruder is apprehended and handed over to Police by the armed guards.
Benefits of System Integration
This section is largely derived from my 2007 book Integrated Security Systems Design.
Operational Benefits
Uniform Application of Security Policies: To get consistent results, it is imperative to use consistent processes and procedures. Imagine how chaotic it would be for a multi-national corporation to allow each department at each site in each business unit to perform their accounting using their own choice of different software programs and different accounting techniques. It would be very difficult for the organization's management to consolidate all of these different reports into a single cohesive picture of the organization's finances, and that could easily result in corporate losses and intense scrutiny by regulatory bodies and shareholders. So it is also unwise for any organization to allow its business units and individual sites to establish their own individual security policies and procedures, guard-force standards, and so forth, which results in the potential for legal liability where different standards are applied at different business units. Enterprise-class Security Systems provide the platform for the uniform application of Enterprise Security Policies across the entire organization. They can also provide visibility into how other company policies are being applied and followed. What follows can be better managed when that information is made available to management in a cohesive way.
Force Multipliers: Integrated Security Systems are force multipliers; that is, they can expand the reach of a security staff by extending the eyes, ears, and voice of the console officer into the depths of the facility where he could not otherwise reach. The use of video guard tours enhances patrol officers so that many more guard tours can be made than with patrol staff alone. Detection and surveillance systems alert security staff of inappropriate or suspicious behaviors and voice communications systems allow console officers to talk with subjects at a building in another state or nation while their behavior is observed onscreen.
Multiple Systems: The integration of alarm, access control, security video, and security voice communications into a single hardware/software platform permit much more efficient use of security manpower. Enterprise-class security systems are force multipliers. The better the system integration, the better use the organization has of its security force.
Multiple Buildings: When Security Systems span multiple buildings across a campus, the use of a single security system to monitor multiple buildings further expands the force multiplication factor of the system. The more buildings monitored the more value the system has.
Multiple Sites: Like multiple buildings on a single site, the monitoring of multiple sites further expands the system's ability to yield value. It is at this point that a true Enterprise-class Security System is truly required, because monitoring multiple sites requires the use of network or Internet resources. Monitoring multiple sites can get a little tricky due to network bandwidth. We will discuss how to get the most out of network bandwidth later in Chapter 21–Related Security Systems, see the section titled “Security Architecture Models for Campuses and Remote Sites”.
Multiple Business Units: Some large organizations also have multiple business units. For example, a petrochemical company may have Drilling, Transportation, Refining, Terminaling, and Retailing. Each of these can benefit by inclusion in an Enterprise-wide security program by consistent application of Security Policies across the multiple business units.
Improved System Performance: Enterprise-class systems also provide significantly improved system performance. The integration of multiple systems at multiple sites into a cohesive user interface allows for simple straightforward command and control. Gigantic systems become manageable.
Improved Monitoring: System monitoring is usually dramatically improved over non-enterprise systems. The integration of alarms, access control, and video and voice communications across the platform provide the console officer with coherent and timely information about ongoing events and trends. In elegantly designed systems, when a visitor at a remote site presses an intercom call button and identifies him/herself as an authorized user who has forgotten his/her access card, the console officer can pull up the record for that user quickly and confirm both the identity of the person at the intercom as well as their validity for that door. In an elegantly designed system, the system knows the user, the door, and the date and time. As the console officer drops the person's icon onto the door icon, the system either grants or denies access to the door, based on the person's authorization for that door for that time. (This application requires a relatively simple custom script at the time this was written.)
Reduced Training: Enterprise-class security systems also require less training. The most basic console operator functions for a truly well-designed Enterprise-class system can be learned in just a few minutes (answering alarms, viewing associated video, and answering the intercom). Because the interface is standardized across the Enterprise, cross-training between buildings and facilities is practical, and, operators from one site can provide support for a console officer or guard at another.
Better Communications: The system also provides for better communications. Imagine a single software platform that integrates Security Intercoms, Telephones, and Cell Phones with integral walkie-talkie functions, 2-way Radios, and Paging all into one easy-to-manage platform. Imagine a console officer who can wear a wireless headset, a wired headset, or use the computer's microphone and speakers, who can trigger the push-to-talk button with a footswitch or a mouse press. Imagine how much better it is when the system queues the intercom automatically when a camera is called. The more the system presents the console operator with the tools to act as though he/she were there at the scene, the better the system serves its security purpose. (This function is performed by GUI systems' interface management software in addition to conventional integrated security system software.)
Cost Benefits
Improved Labor Efficiency: For many of the reasons stated earlier, Enterprise-class security systems enhance labor efficiencies: fewer consoles, fewer guards, redundant monitoring, nighttime live monitoring where it was not cost-effective before, mutual-aid between sites and buildings. All of these factors free up guards to be on patrol and in live communication with the central console.
Reduced Maintenance Costs: Enterprise-class Security Systems are generally built on the use of a common technology across the entire platform. Counterintuitively, they are also generally built on simpler technology than less sophisticated systems. The key to success is often the elegant combination of simple technologies into a highly refined system. This inherent architectural simplicity often also results in lower maintenance costs. While the results are elegant and sophisticated, the underlying technology is actually simpler than in times past. The key is to combine simple Boolean algebra logical functions (and, or, not, counting, timing, etc.) in elegant ways.
Improved System Longevity: Security systems are notoriously short-lived. Contemporary security systems are comprised of numerous delicate components that either fail mechanically or are unable to upgrade as the system scales. Thus, when upgrades are necessary, it is often necessary to throw out components that are only a few years old because they are not compatible with newer technologies. This in-built obsolescence has a long tradition in security systems and it drives building owners and consultants totally nuts! Most building systems are expected to last 15 to 20 years. Some building systems including the basic electrical infrastructure are expected to last the life of the building. I find it shocking that most electronic security systems made by major manufacturers and installed by major integrators last less than seven years. A well-designed Enterprise-class Security System should last 10 to 15 years between major architectural upgrades. This is achievable using the principles taught in this book.
Types of Integration
What can be integrated and how? Virtually every system can be integrated with others one way or another. Integration opportunities fall into the following broad categories:
• Dry Contact Integration
• Wet Contact Integration
• Serial Port Integration
• TCP/IP Integration
• Database Integration
Dry Contact Integration
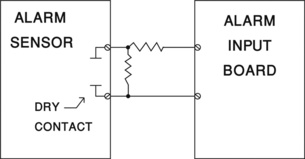
A Dry Contact is a switch or relay point that is not a source of power. When an alarm panel is connected to a Door Position Switch (DPS), that switch is a Dry Contact because it is not a source of power. The DPS is “dry.” The power source is the sensing input. A resistor is typically used in series with the Dry Contact to limit current through the sensing input (Figure 19.1).
When an Alarm/Access Control System provides relay points to signal a Video System to display a camera in response to an alarm, that relay is a Dry Contact to the Video System.
Dry contact connections are common between systems to signal a binary change in state in one system, a logical 1 or 0, such as on/off. These are typically used to signal an infrequent and relatively constant change of state such as alarm on, alarm off.
Wet Contact Integration
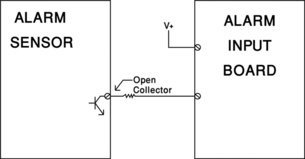
A Wet Contact is a connection point that is a source power that is used as a signal to another circuit. When an Alarm/Access Control System Lock Relay switches power on to a door lock, it does so through a Wet Contact. In this case, the Wet Contact is a Lock Power Relay to which a Lock Power Supply has provided power. The Lock Relay completes the circuit to the Lock when the relay closes.
A Wet Contact can also be the connection point to a Transistor, Silicon-Controlled Rectifier (SCR), Triac, or other electronic component. A typical Transistor connection can provide either an “Open Collector or Open Emitter” connection (Figure 19.2).
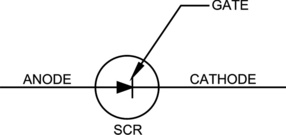
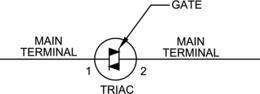
An SCR may provide either an Open Anode or Open Cathode connection and a Triac may provide a Main Terminal 1 (MT1) or Main Terminal 2 (MT2) connection. An SCR is similar to a transistor except that power can only flow in one direction. When power is applied to its Gate it causes power to flow in one direction only through the SCR (Figure 19.3). SCRs are often used to provide a connection to ground. A Triac is like two SCRs back to back with a common terminal in between (like the Gate on the SCR; Figure 9.4).
Serial Data Integration
Many systems use Serial Data to communicate. Serial Data is a data connection in which there is a single flow of data bits presented serially (one after the other) rather than parallel (eight bits with one byte at a time).
Whereas Dry and Wet Contacts communicate a simple change of state, Serial Data communication is often used to communicate instructions from one system to another, such as a command (Figure 19.5).
Common serial communications pass simple commands between systems, for example, which floor on an elevator was selected after a valid card was presented. These may be connected via RS-232 or Universal Serial Bus (USB) connections.
TCP/IP Integration
Increasingly, Ethernet TCP/IP connections are used to communicate large amounts of data or data across large distances. In particular, as Enterprise Class systems are being integrated (across many campuses, buildings, etc.) TCP/IP is the preferred communications method because there is usually already a Business Information Technology (IT) connection between the sites that can be used to transmit Security System Integration information as well.
Database Integration
When TCP/IP Integration is used, it can transmit parallel data, database records and fields, and complicated Structured Query Language (SQL) commands. SQL is coupled with an SQL database at both ends to synchronize databases and create compound command instructions.
System Integration Examples
The examples in this section are by no means a complete picture of what you can do with systems integration, but hopefully this will give you several ideas of how systems integration can be used to improve effectiveness and reduce the costs of a security program.
Basic System Integration
• Systems Integrated:
• Alarm/Access Control System
• Digital Video System
• Security Intercom System
• Functions Achieved:
• See and acknowledge alarms on a single Map-based GUI
• See and answer Intercom Calls on the Map-based GUI
• Open Vehicle Gates and Remote Doors in response to Intercom Calls from those locations directly from the Map-based GUI
• Benefits Derived:
• Less technology to interact with for basic functions for all three systems; only one GUI for all three systems
• Less Training needed for Console Guards
• Faster Response to Alarm and Access Control Incidents
More Advanced System Integration
• Systems Integrated:
• Alarm/Access Control System
• Digital Video System
• Security Intercom System
• Building Automation System
• Stairwell Pressurization System
• Functions Achieved:
• Daytime (Work Schedule):
- Fire Stairwell Landing next to Employee Parking Lot is also an Exit Passageway from Ground Floor Corridor to Lobby
- Smokers gather outside Stairwell Door for smoke break, smoker forgets access card so he props the door open, causing air to leak from pressurized fire stairwell
- Door Position Switch on Alarm triggers a propped door alarm after 20-second time-out, alarm is audible at door, not transmitted to security console
- Smoker ignores alarm at door, 30-second timer counts down
- After 30 seconds of alarm at door, alarm is announced on GUI at Security Console, video camera at door is displayed
- Console Officer views video at door, sees smokers ignoring alarm
- Console Officer announces to smokers to close door through intercom at door, stating that this is a pressurized fire stairwell and door must be kept closed, advises smokers to carry access cards, remotely unlocks door to allow smokers entry via intercom after smoking
• Nighttime Schedule:
- Door is broken into by intruder, when door opens…
- Local Alarm sounds, Alarm is sent immediately to Security Console (no delay), GUI shows location of alarm
- Up to 8 cameras surrounding area of door (inside, outside, and in stairwell) are displayed, showing intruder, who appears to be armed
- Console Officer follows intruder as he makes his way up stairwell to 6th floor and breaks into 6th floor stairwell door
- Console Officer notifies Police who respond to site
- Console Officer advises police over telephone of location of intruder
- Police capture and arrest intruder with help of Console Officer's guidance
• Benefits Derived:
• Case 1:
- Stairwell pressurization is not violated
- Console Officer is not notified if door is closed by nearby persons upon sounding of local alarm at door
- Console Officer is notified only after alarm is ignored
- Smokers are advised to carry access cards
- Console Officer can remotely unlock door for authorized users
• Case 2:
- Immediate notification of intrusion to Console Officer
- Video System provides all relevant cameras on alarm
- Console Officer can follow intrusion on Video System
- Console Officer is not compelled to confront armed intruder
- Police receive assistance from Console Officer as to location of intruder, assisting in his arrest
Advanced System Integration
• Systems Integrated:
• Alarm/Access Control Systems
• Digital Video Systems
• Fire Alarm Systems
• Emergency Gas Pump Shut-off System
• 2-way Audio System
• Business IT System
• Functions Achieved:
• Remote Monitoring of all Branches of a chain of Convenience Stores/Gas Stations from a single proprietary Central Station location
• Remote Monitoring of Fire Alarms/Intrusion Alarms/Duress Alarms
• Case 1 — Store Robbery:
- Robber approaches a Store Cashier with gun, aggressively demands money — Robber appears very threatening to Cashier
- Cashier triggers Silent Alarm while opening Cash Register
- Alarm is sent via Business IT System to Proprietary Central Station
- Alarm rings at Central Station on GUI showing location of Store on Map
- Video from the Store is displayed at Central Station GUI along with Audio from Microphone above the Cash Counter at the Store
- GUI displays location and Police/Fire/Emergency numbers next to location on GUI Map
- Central Station Operator Clicks on Police Emergency Number (which dials Police and uses recorded message to announce In-Progress Robbery and Store Location), announces that that following audio is one way from the store location and that store cannot hear police, then opens audio panel so that police can monitor audio from the store
- Central Station Operator announces to Robber over loudspeaker above Cash Counter that he is under observation and that the robbery is being recorded for prosecution (describes the offender so he knows he is under observation), says that police are en route and urges him to leave the store before he is caught by Police
- Robber takes small amount of cash in drawer (policies state large bills must be emptied every hour) and runs out without further aggression, hoping to get away from Police and not be seen on video assaulting the Cashier
• Case 2 — Fire:
- Person pumping gas is smoking cigarette, ignites gas vapors, and fire erupts from gas tank of vehicle
- Intelligent Video System sees fire and rings alarm at the Store and alarm is sent via Business IT System to Proprietary Central Station
- Alarm rings at Central Station on GUI showing location of Store on Map
- Video from the Store is displayed at Central Station GUI along with Audio from Microphone above the Cash Counter at the Store, one camera shows fire and smoke at Gas Pumps
- GUI displays location and Police/Fire/Emergency numbers next to location on GUI Map
- Central Station Operator directs Store Personnel to evacuate store through overhead speaker
- Cashier moves everyone out of the store to safety, in the excitement, he forgets to shut off power to Gas Pumps
- Central Station Operator shuts off gas to Gas Pumps by hitting Emergency Pump Shut-Off button on GUI
- Central Station Operator clicks on Fire Emergency Number (which dials Local Fire Department and uses recorded message to announce Fire at Store Location), then connects Central Station Operator with Fire Department Emergency Number for further description of the fire
- Central Station Operator instructs all persons on Gas Plaza to evacuate to a safe distance by using microphone at Central Station and loudspeakers at Gas Plaza
- Fire Department arrives, puts out fire
• Benefits Derived:
• Case 1: Life possibly saved, minimal cash lost
• Case 2: Lives possibly saved, minimal loss to fire
Chapter Summary
1. In order to talk about why security systems should be integrated, we need to first understand the theory of protecting an organization's assets.
2. Every organization begins with a mission.
3. The organization develops programs in support of its mission.
4. As they develop programs, the organization will acquire assets in support of its programs.
5. These assets always include:
• People
• Property
• Proprietary Information
• Business Reputation
6. These assets have appropriate and inappropriate users.
7. Appropriate users include those who use the assets for the benefit of and with permission by the organization.
8. Inappropriate users are those who seek to use the organization's assets for their own benefit rather than for the benefit of the organization, or in some cases the assets are used against the benefit of the organization.
9. Threat actors include:
• Terrorists
• Violent Criminals
• Economic Criminals
• Petty Criminals
10. Organizations must protect their assets from Threat Actors or face serious reductions in their ability to meet their mission.
11. In its simplest form, Risk is a combination of the existence of an active threat actor interested in the organization's assets (probability, P), exploitable vulnerabilities (V), and the degree of consequences (C) of that threat scenario being carried out or R = (P*V*C).
12. Once risks are assessed, security countermeasures should be developed.
13. These should always begin with a Comprehensive set of Security Policies and Procedures, upon which all other countermeasures are built.
14. Good Security Programs include all three types of security countermeasures:
• Hi-Tech
• Lo-Tech
• No-Tech
15. Hi-Tech Countermeasures include electronic systems including Alarm/Access Control, Digital Video, Security Intercoms, etc.
16. Lo-Tech Countermeasures include Locks, Barriers, Lighting, Signage, etc.
17. No-Tech Countermeasures include Policies and Procedures, Security Staffing, Dogs, Law Enforcement Liaison Programs, Security Awareness Programs, etc.
18. These three types of countermeasures should always be used together in a layered approach to reduce risk.
19. Since Deterrence varies substantially depending on the commitment of the Threat Actor, it cannot be accurately calculated.
20. A well-designed security system should filter unnecessary information; present relevant information in a quick, easy-to-understand format; and provide the Security Console Officer and Supervisor with quick and relevant options to defend the organization's assets.
21. Electronic Security Systems do their job better when their various components are “integrated” into a single, comprehensive system allowing each part of the overall system to “feed” information to and draw from the other parts of the system to enhance functions and effectiveness.
22. Integration benefits include:
• Operational Benefits
- Uniform Application of Security Policies
- Force Multipliers
- Multiple Systems
- Multiple Buildings
- Multiple Sites
- Multiple Business Units
- Improved System Performance
- Improved Monitoring
- Reduced Training
- Better Communications
• Cost Benefits
- Improved Labor Efficiency
- Reduced Maintenance Costs
- Improved System Longevity
23. Types of integration include:
• Dry Contact Integration
• Wet Contact Integration
• Serial Port Integration
• TCP/IP Integration
• Database Integration
1) While Alarm/Access Control Systems, Security Video Systems, and Security Intercom Systems all are powerful tools to help manage risk for an organization, they become
a. Less powerful in the hands of inexperienced operators
b. Even more powerful when integrated together into a single, comprehensive security system
c. Essential methods in the control of terrorism
d. None of the above
2) Every organization has four kinds of assets. These include:
a. Employees, Contractors, Vendors, and Visitors
b. People, Property, Proprietary Information, and Business Reputation
c. People, Fixtures, Furnishings, and Equipment
d. Customers, Real Property, Fixtures, and Furnishings
3) Threat Actors can include:
a. Employees, Contractors, Vendors, and Visitors
b. Employees, Contractors, Visitors, and Customers
c. Terrorists, Violent Criminals, Economic Criminals, and Petty Criminals
d. Terrorists, Eco-Terrorists, Animal-Rights Terrorists, and Bugs Bunny
4) Good Security Programs include only the following types of countermeasures:
a. Hi-Tech, Lo-Tech, and No-Tech
b. Electronics, Operations, and Investigations
c. Electronics, Operations, and Dogs
d. Electronics, Policies, and Procedures
5) All security countermeasures are intended to
a. Deter unwanted behavior
b. Detect inappropriate behavior
c. Help assess what has been detected
d. All of the above
6) All security countermeasures are intended to
a. Help Security Staff Respond to Security Events
b. Delay Intrusions and Exits of Offenders
c. Gather Evidence of Security Events for Prosecution and Training
d. All of the above
7) Security is not a challenge of technology; it is a challenge of
a. Imagination
b. Understanding
c. Apprehension
d. Arrest
8) When thinking to integrate systems you must ask yourself
a. If I eliminated all the technology and had a highly qualified guard at the location in question, what tasks would I want to perform?
b. What information would I need to make decisions?
c. What resources would I like to have to be able to carry out those tasks?
d. All of the above
9) Benefits of System Integration include:
a. Operational Benefits
b. Cost Benefits
c. Neither a nor b
d. Both a and b
10) Operational Benefits may include:
a. Uniform application of Security Policies
b. Force Multipliers
c. Both a and b
d. Neither a nor b
11) Cost Benefits may include:
a. Improved system longevity
b. Improved use of dogs
c. Improved use of drugs
d. None of the above
12) Types of Integration may include:
a. Dry Contact Integration
b. Wet Contact Integration
c. Serial Port Integration
d. All of the above
13) Types of Integration may include:
a. TCP/IP Integration
b. Database Integration
c. Both a and b
d. Neither a nor b
Answers: 1) b, 2) b, 3) c, 4) a, 5) d, 6) d, 7) a, 8) d, 9) d, 10) c, 11) a, 12) d, 13) c
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.