Appendix E. Memory Tables Answer Key
Chapter 1
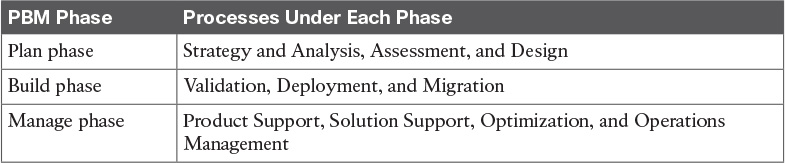
Table 1-3 PBM Network Lifecycle Phases
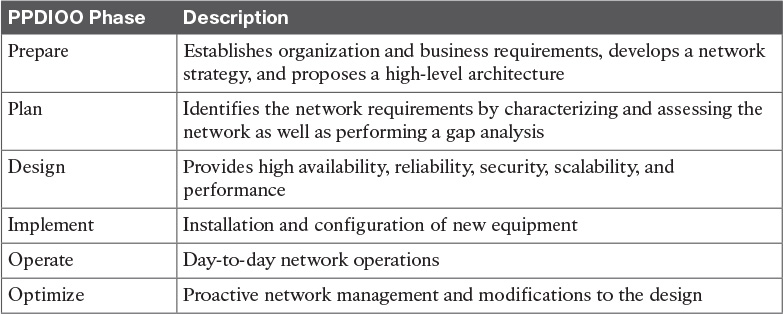
Table 1-8 PPDIOO Network Lifecycle Phases
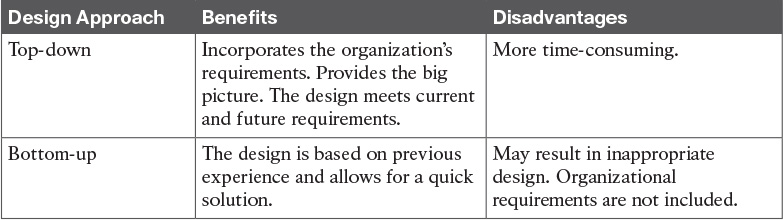
Table 1-11 Top-Down Design Compared to Bottom-Up Design
Chapter 2
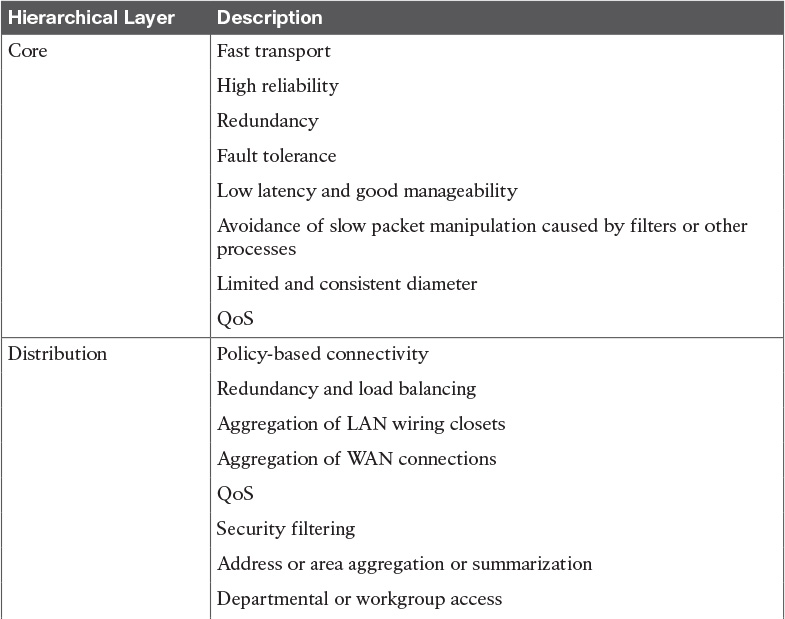
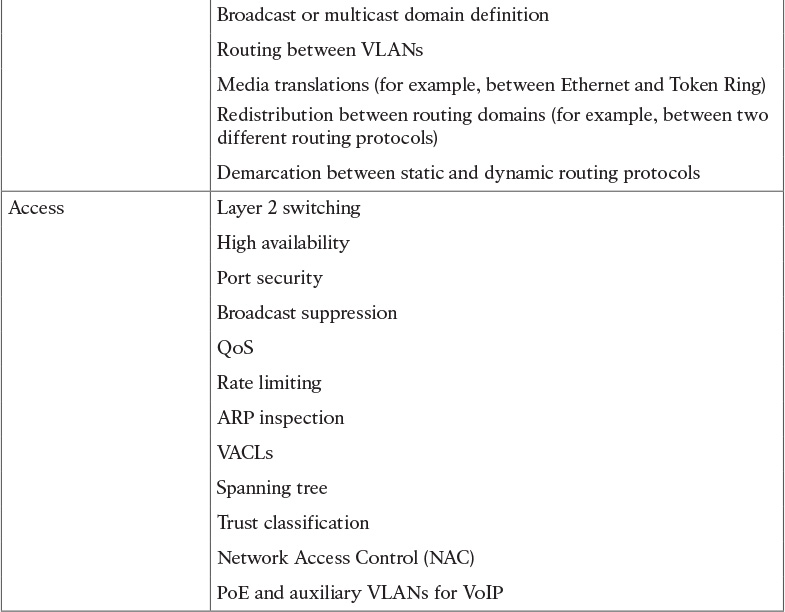
Table 2-2 Cisco Enterprise Architecture Model
Chapter 3
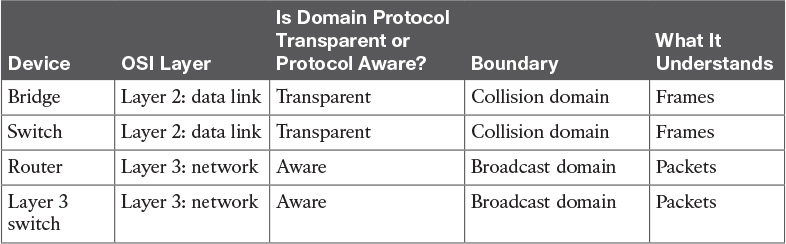
Table 3-6 LAN Device Comparison
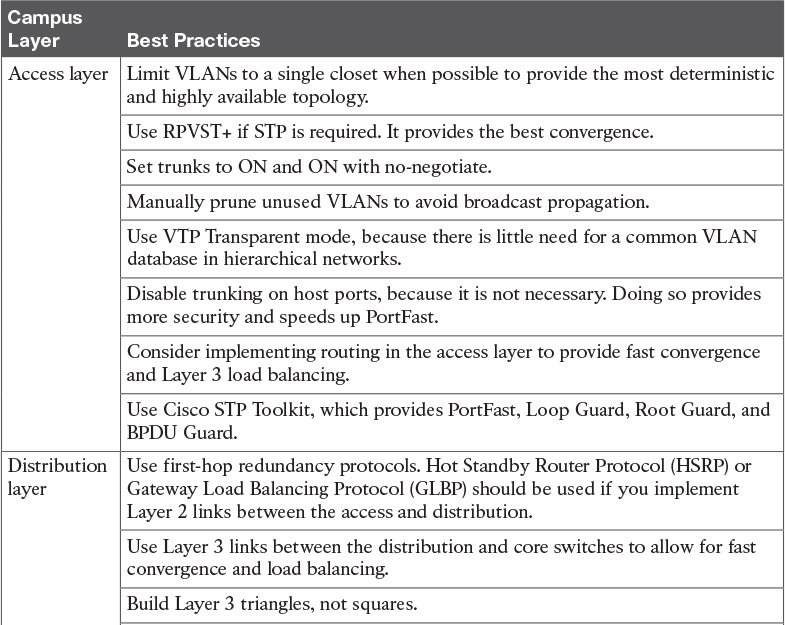
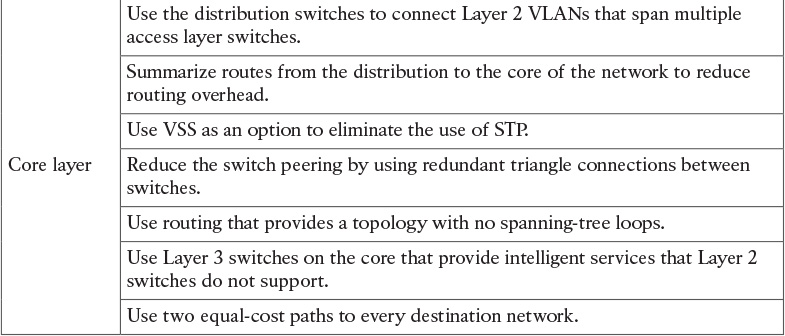
Table 3-9 Campus Layer Design Best Practices

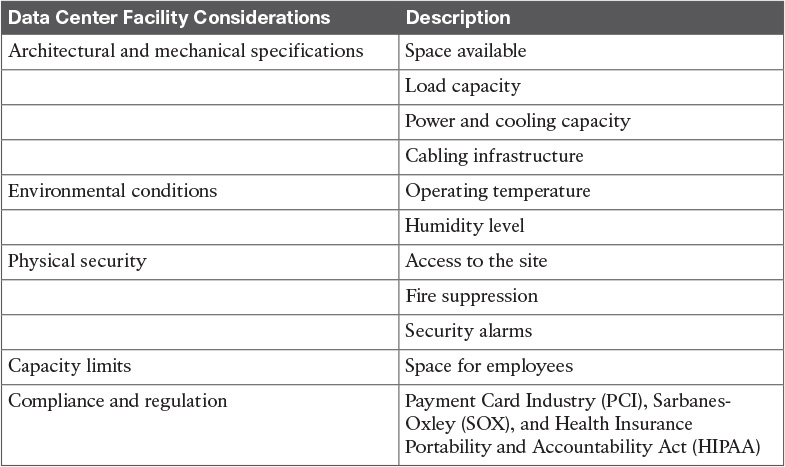
Table 4-3 Data Center Core Drivers
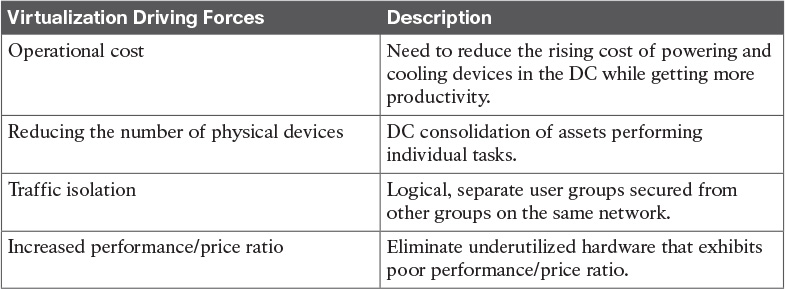
Table 4-4 Virtualization Key Drivers
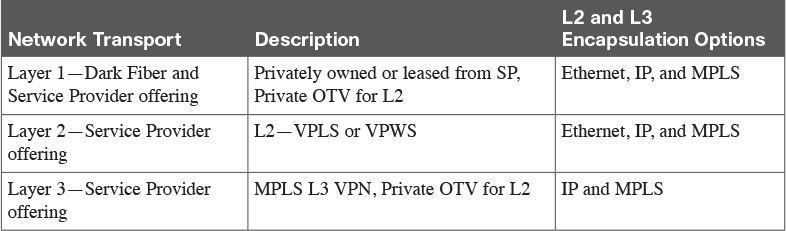
Table 4-6 DCI Transport Options
Chapter 5
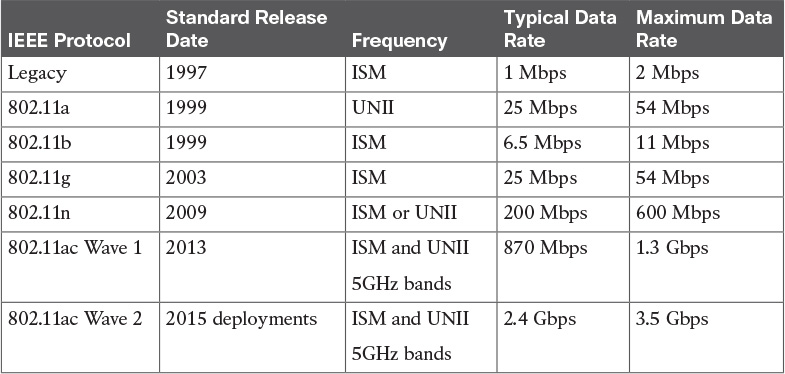
Table 5-2 WLAN Standards Summary

Table 5-5 Access Point Modes
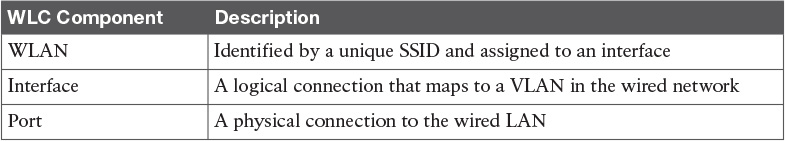
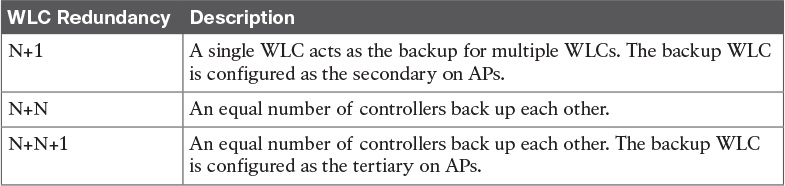
Table 5-7 WLC Components

Table 5-8 WLC Interface Types
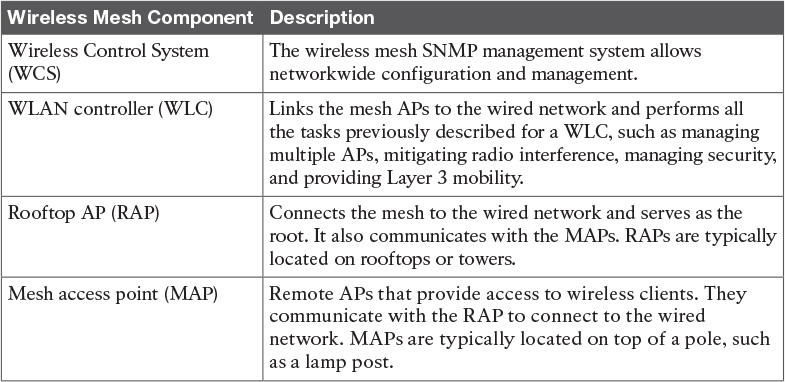
Table 5-11 Wireless Mesh Components
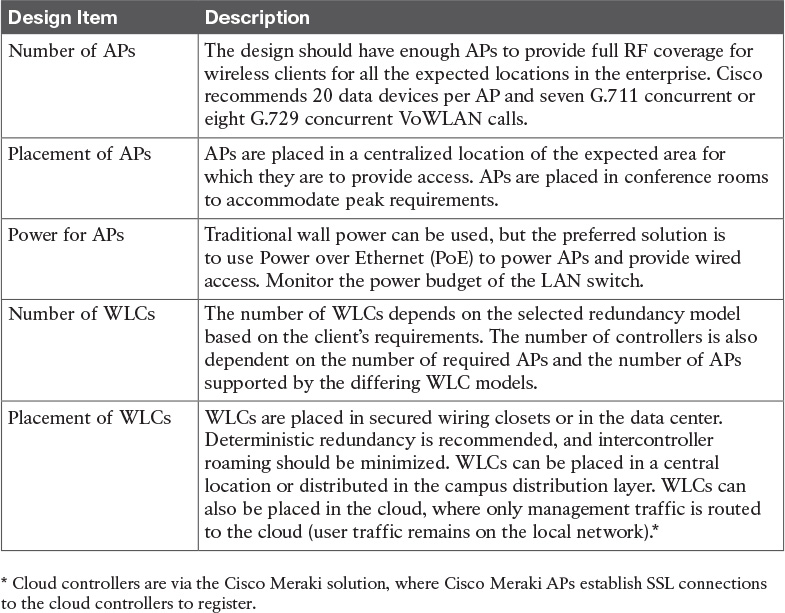
Table 5-12 WLAN Design Considerations

Table 6-3 Key Design Principles
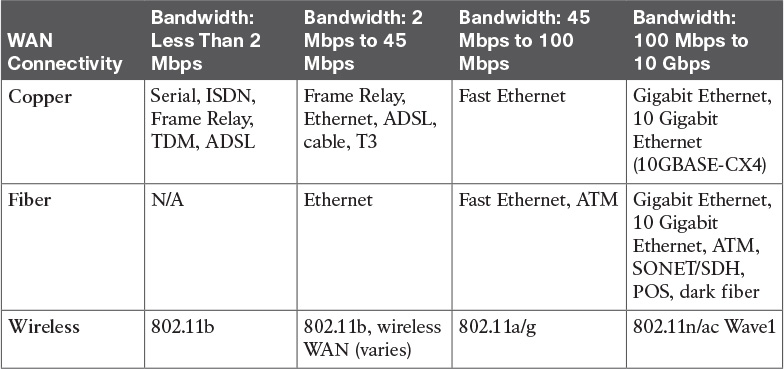
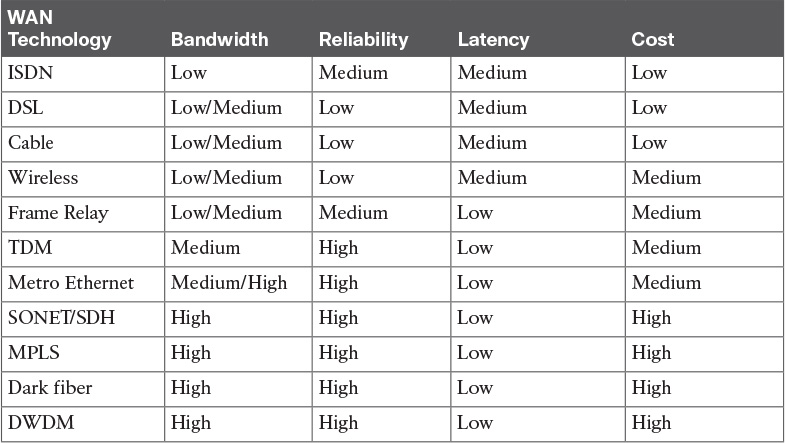
Table 6-5 Physical Bandwidth Comparison
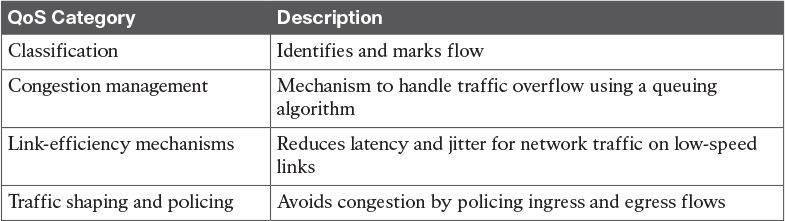
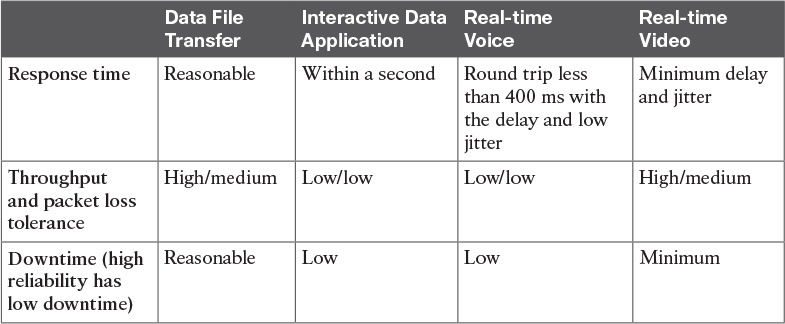
Table 6-7 QoS Considerations
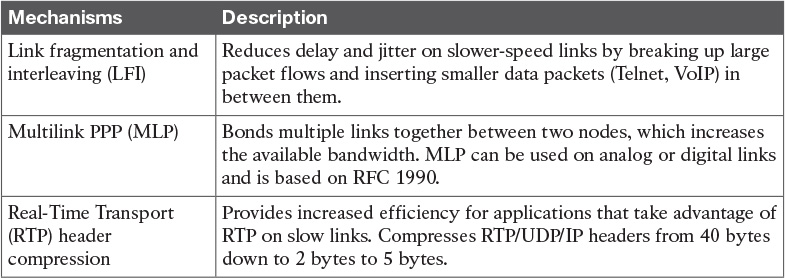
Table 6-8 Link-Efficiency Mechanisms
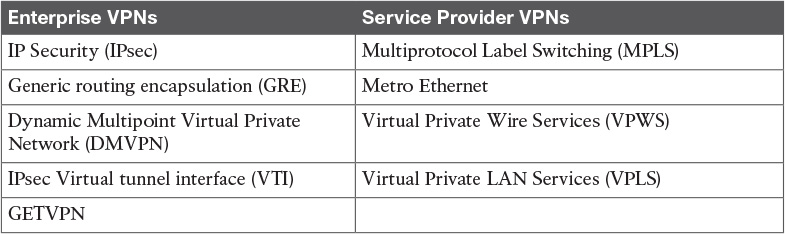
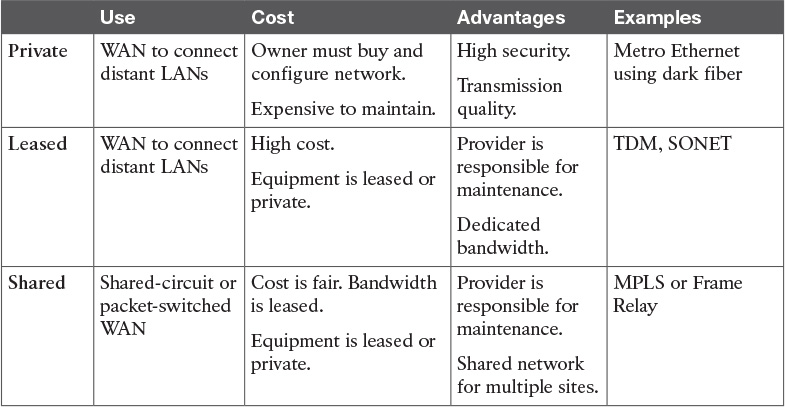
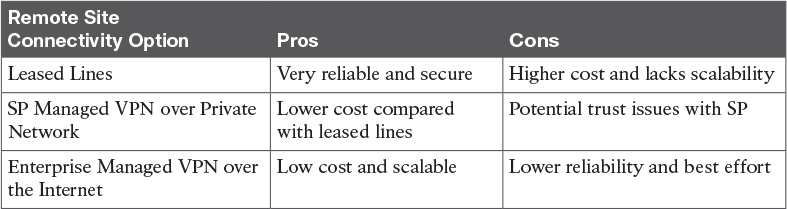
Table 7-3 VPNs Found in Enterprise and Service Provider Environments
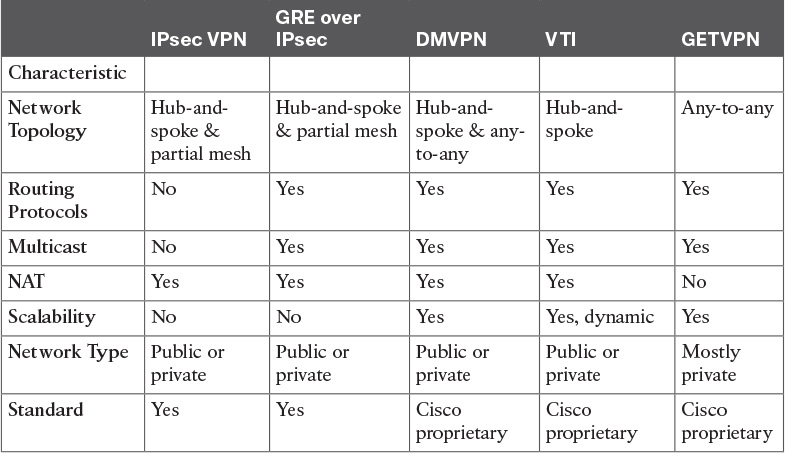
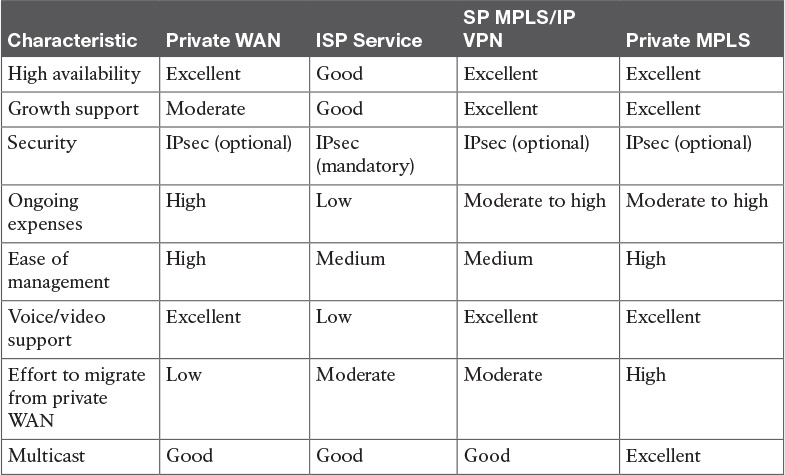
Table 7-4 Enterprise VPN Comparison
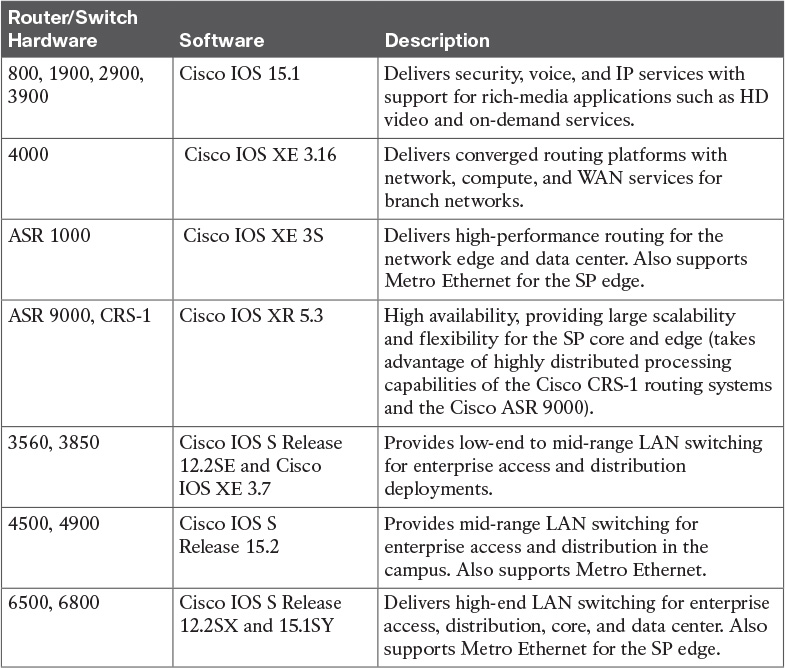
Table 7-7 Cisco Router/Switch Platform and Software Comparison
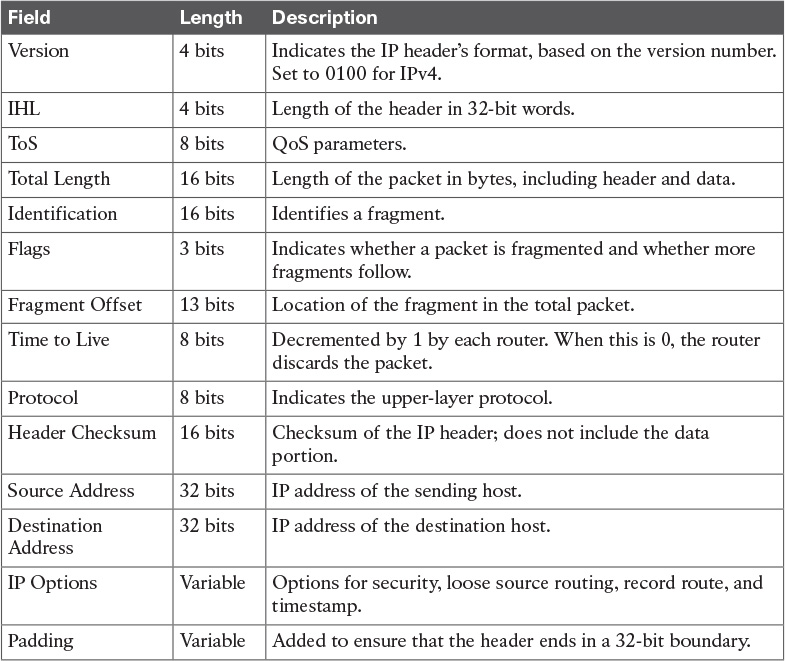
Table 8-3 IPv4 Header Fields
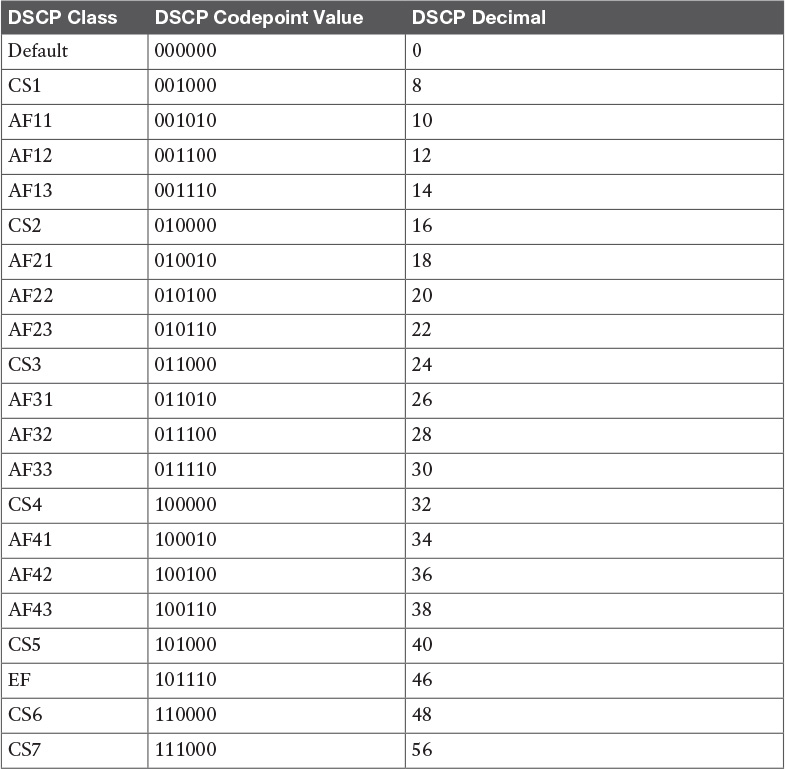
Table 8-8 IP DSCP Values
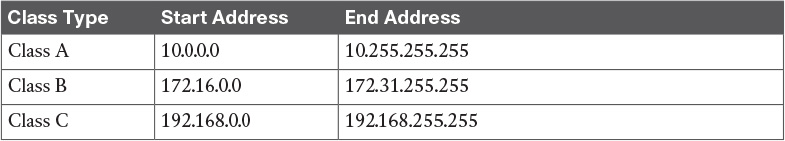
Table 8-12 IPv4 Private Address Space
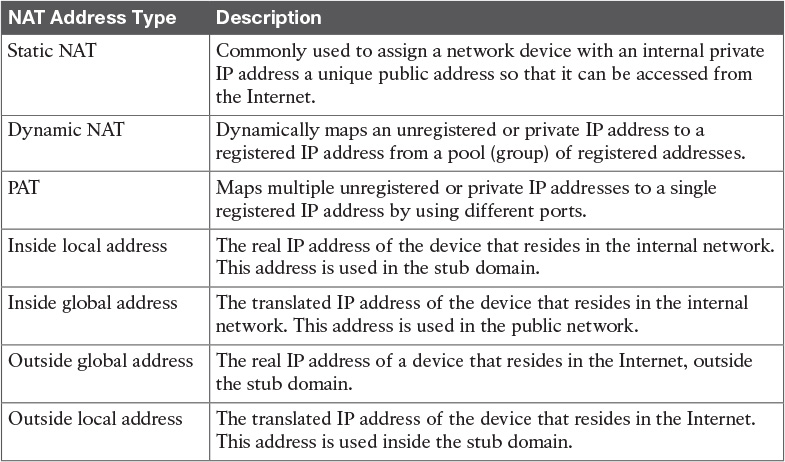
Table 8-13 NAT Concepts
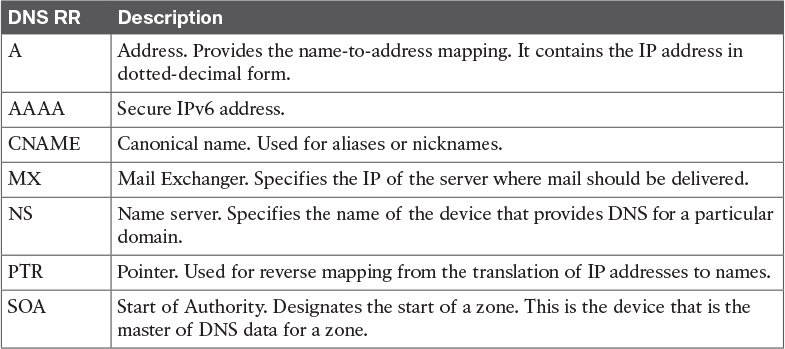
Table 8-31 DNS Resource Records
Chapter 9
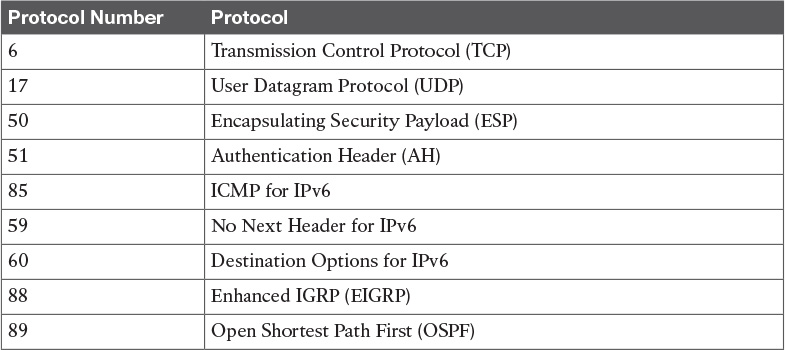
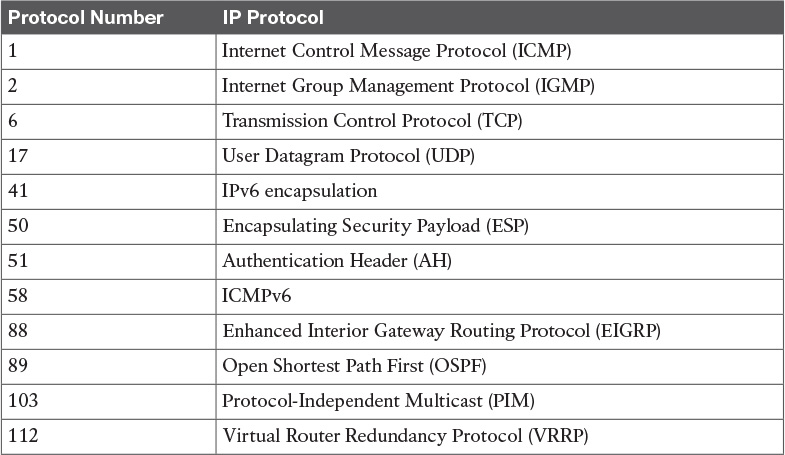
Table 9-2 IP Protocol Numbers
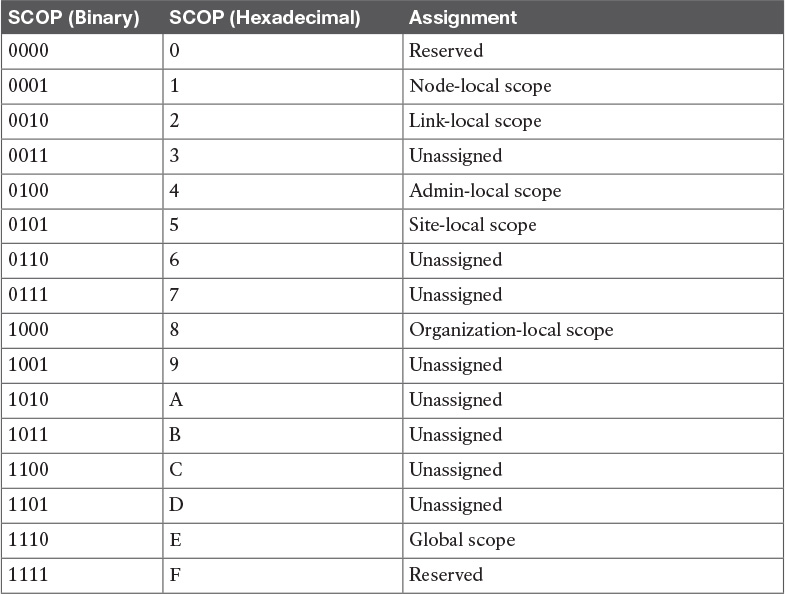
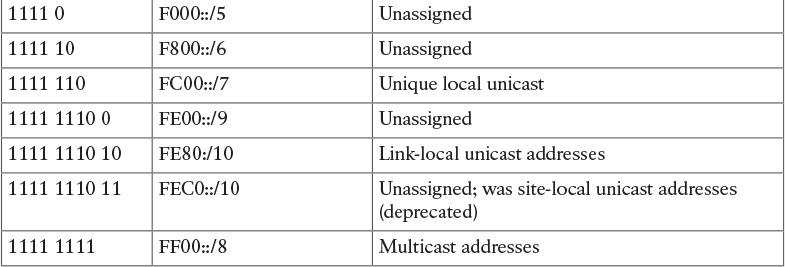
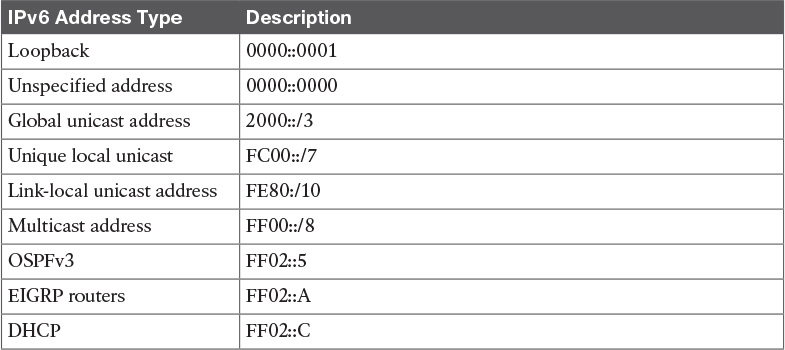
Table 9-4 Multicast Scope Assignments
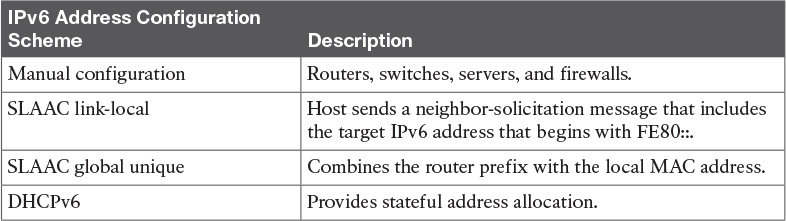
Table 9-8 IPv6 Address Autoconfiguration Scheme
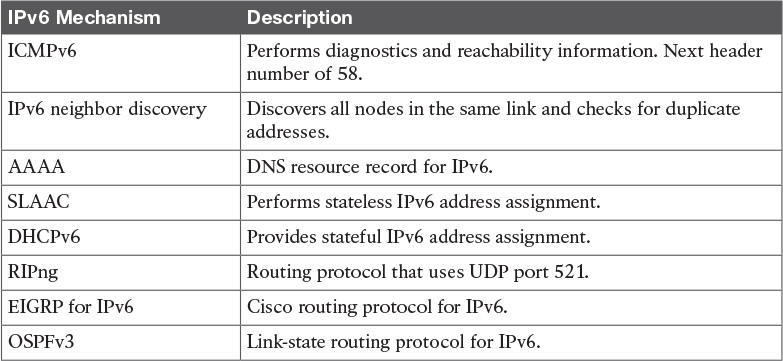
Table 9-9 IPv6 Mechanisms
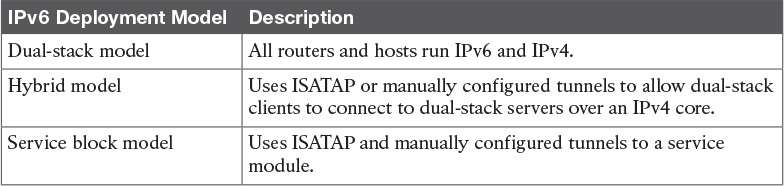
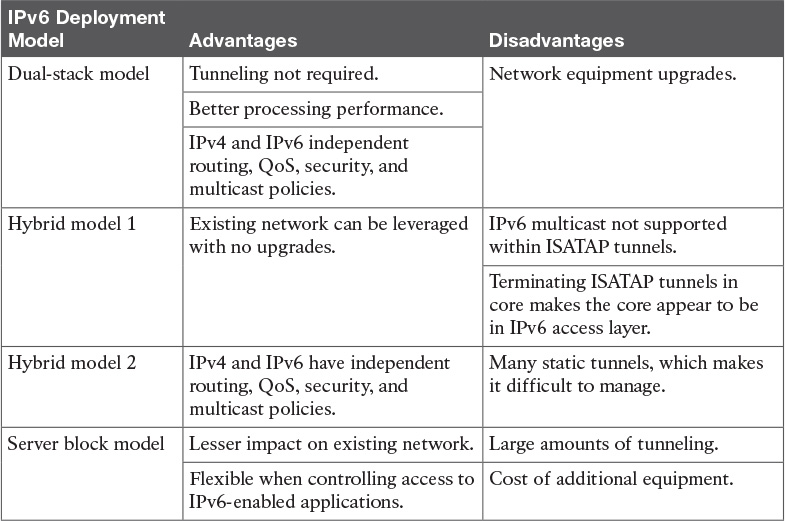
Table 9-13 IPv6 Deployment Models
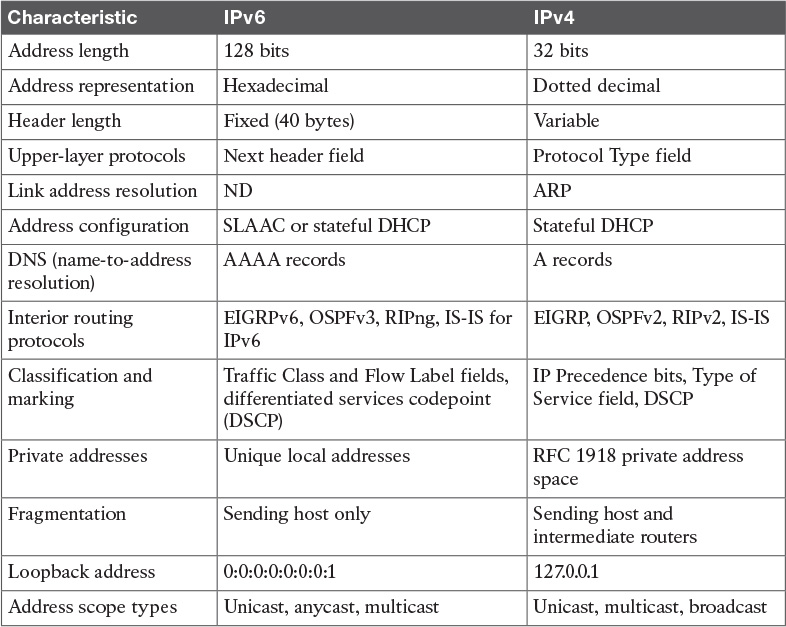
Table 9-14 IPv6 and IPv4 Characteristics
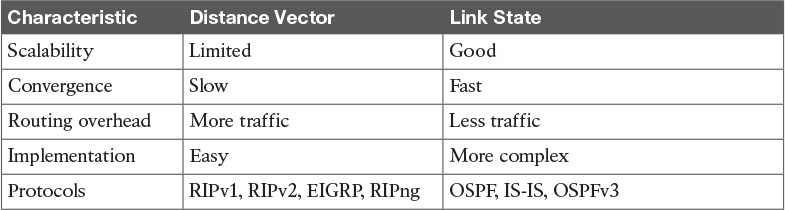
Table 10-3 Distance-Vector Versus Link-State Routing Protocols
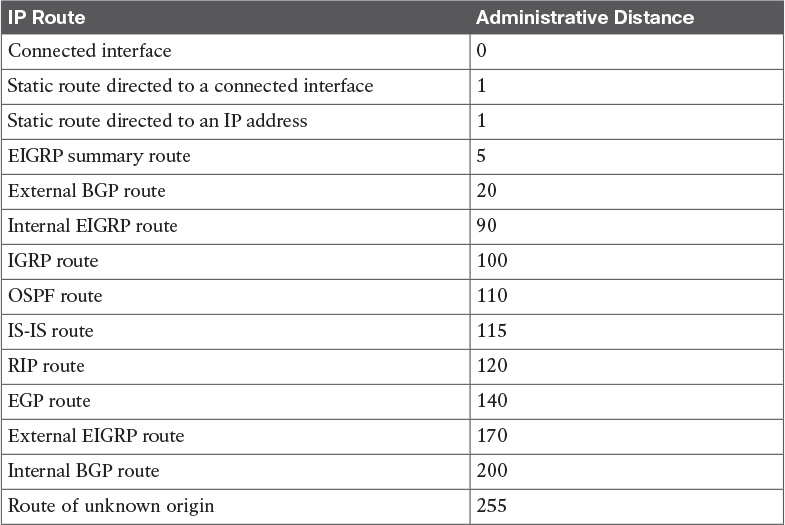
Table 10-5 Default Administrative Distances for IP Routes
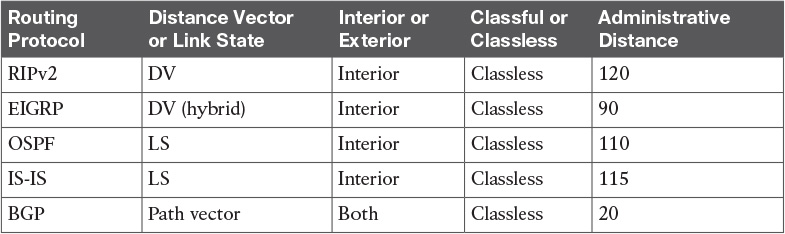
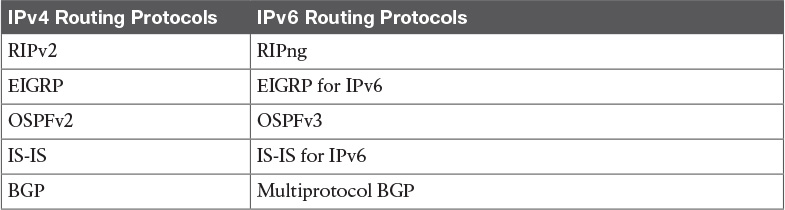
Table 10-6 Routing Protocol Characteristics
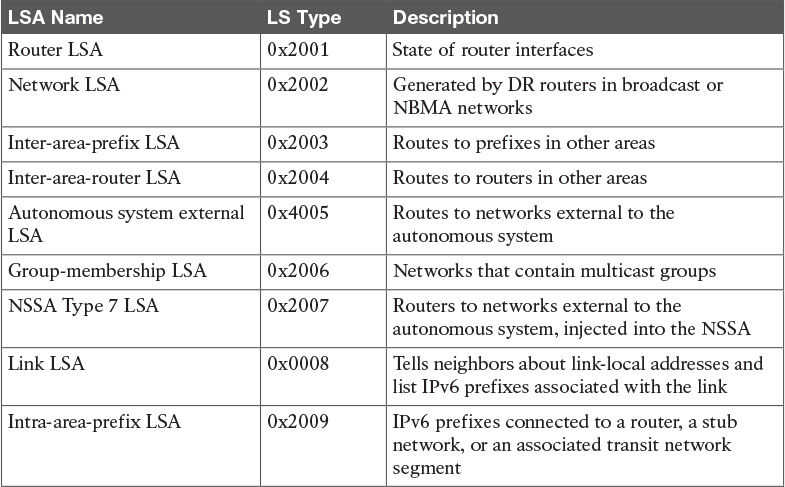
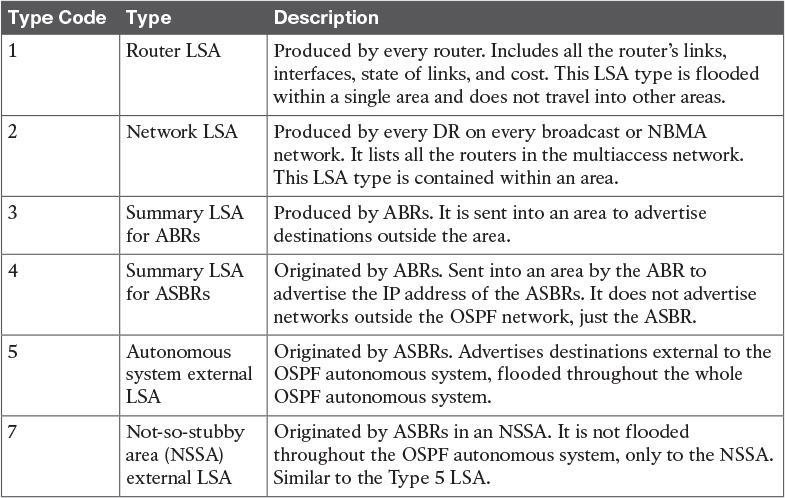
Table 11-6 OSPFv3 LSA Types
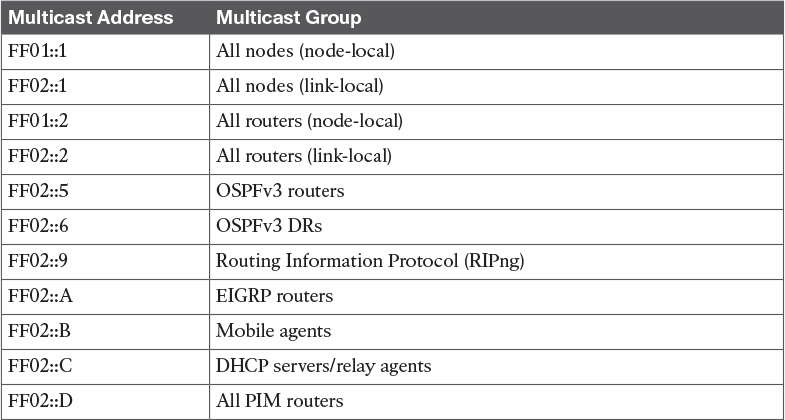
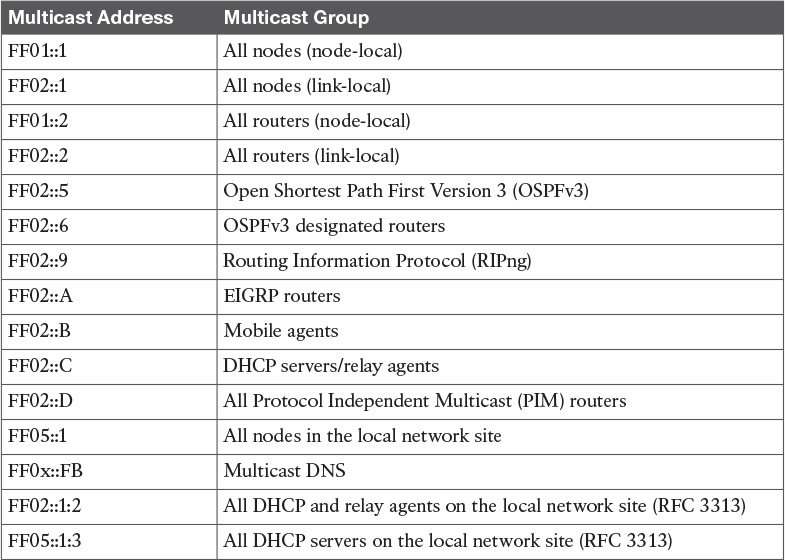
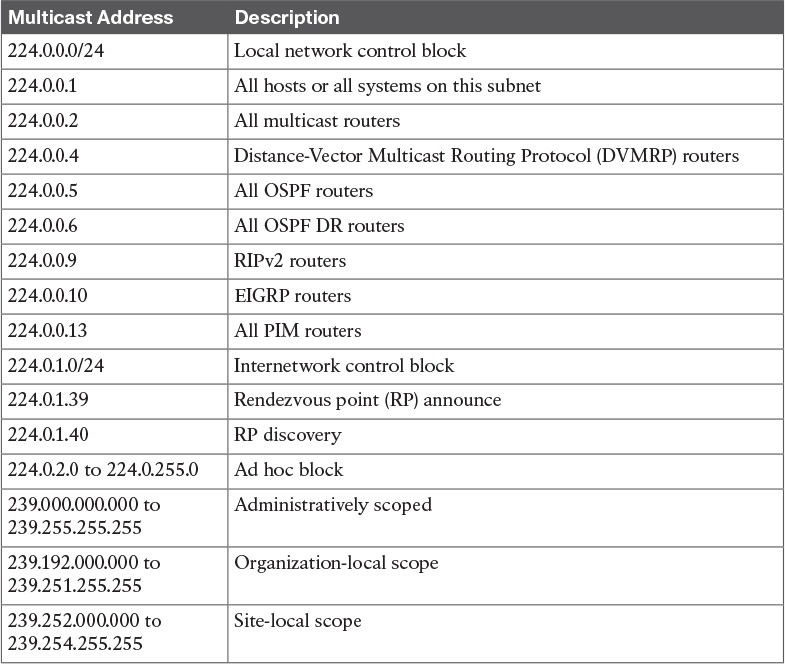
Table 11-11 Well-Known Multicast Addresses
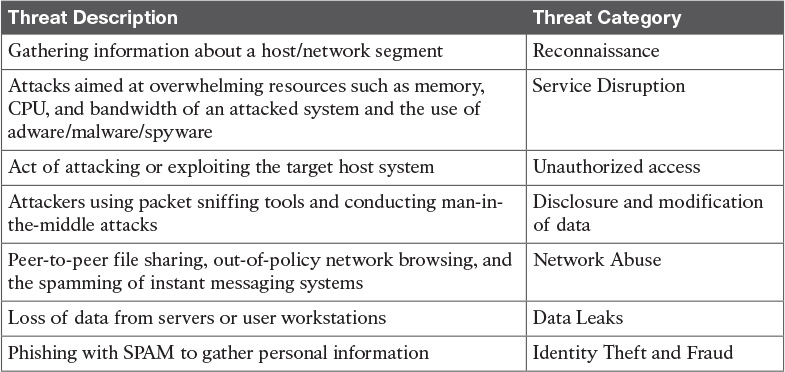
Table 12-3 Security Threats
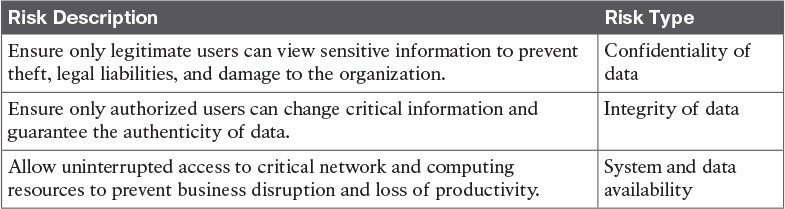
Table 12-4 Security Risks
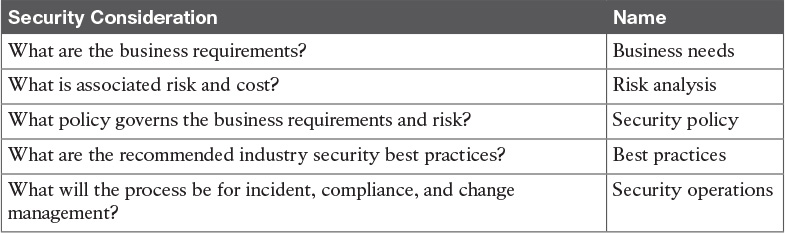
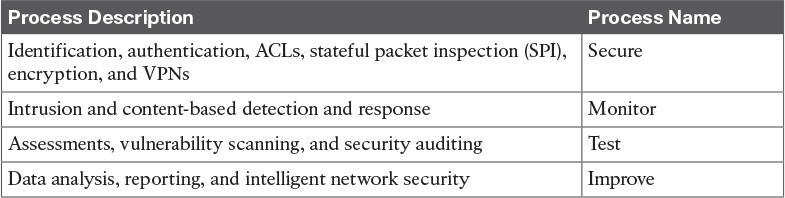
Table 12-6 Key Network Security Elements of the Network Security Lifecycle
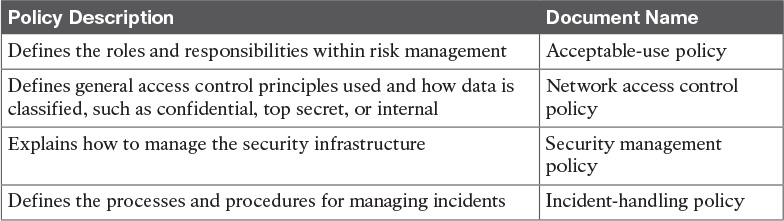
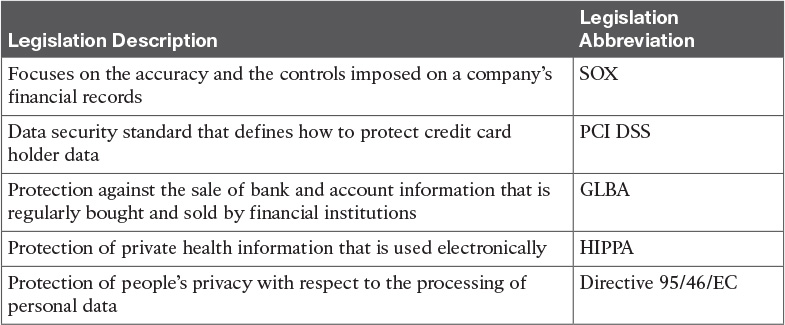
Table 12-7 Security Policy Documents
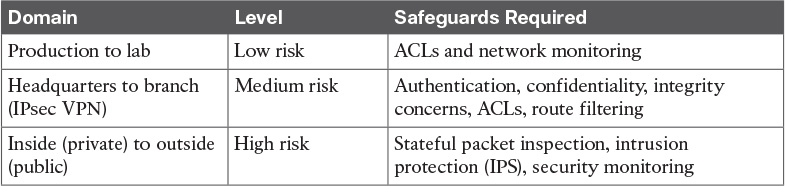
Table 12-10 Domains of Trust: Risks from Low to High
Chapter 13
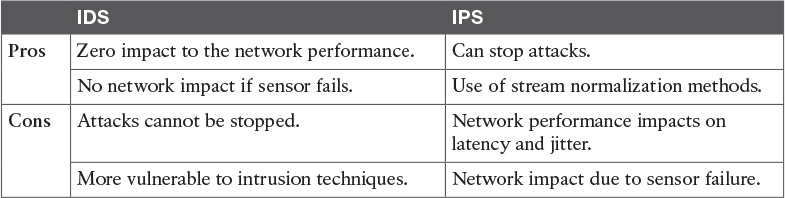
Table 13-2 IDS/IPS Pros and Cons
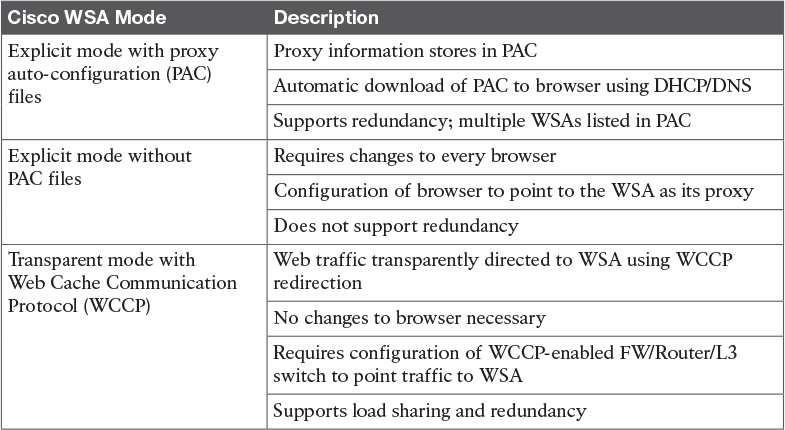
Table 13-3 Cisco WSA Modes

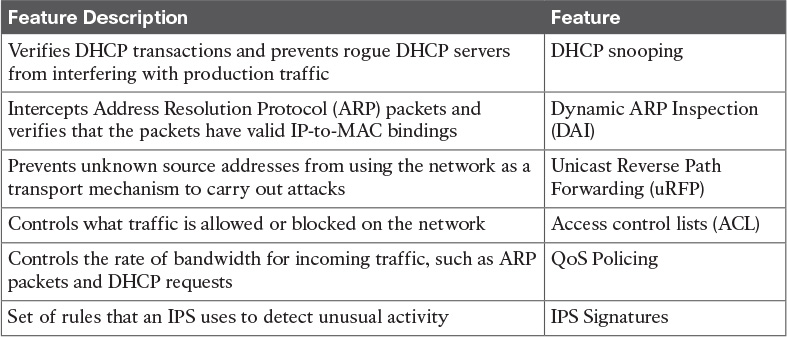
Table 13-5 Security in the Campus

Table 13-6 Security in the Data Center
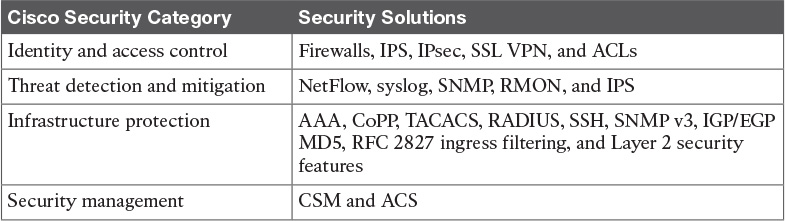
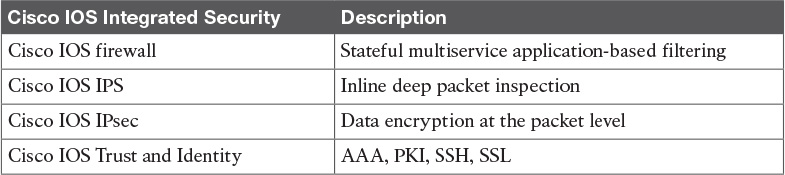
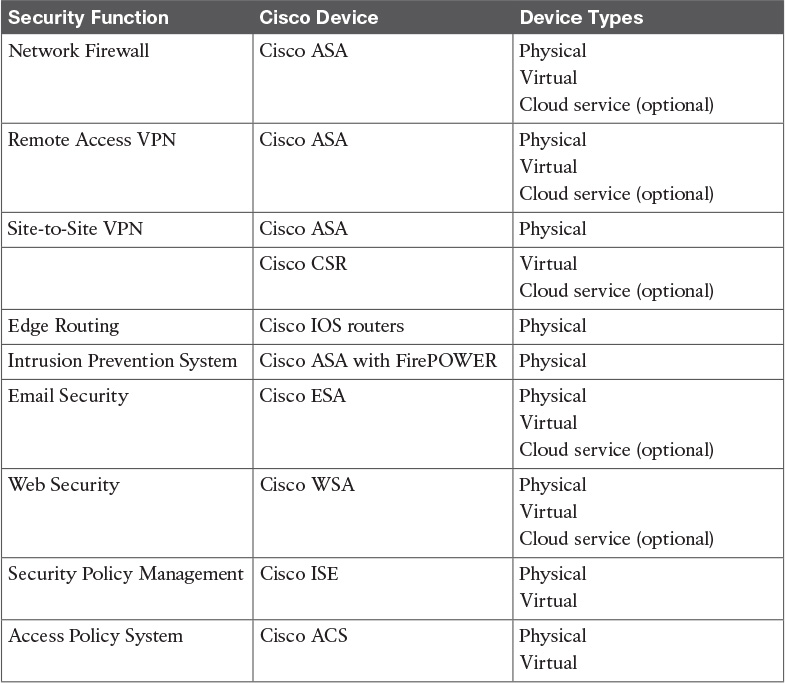
Table 13-8 Security in the Enterprise Edge
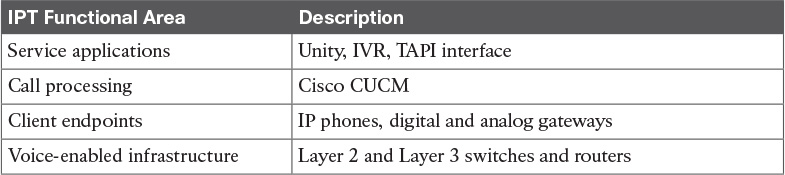
Table 14-5 IPT Functional Areas
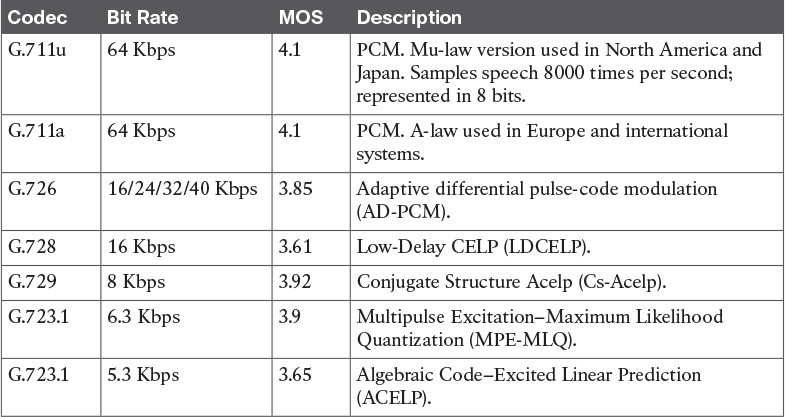
Table 14-8 Codec Standards
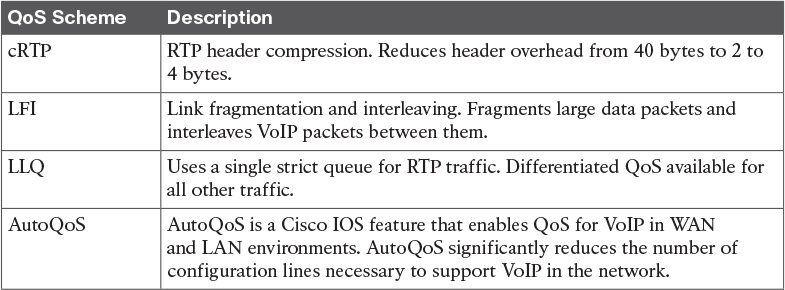
Table 14-14 QoS Scheme Summary
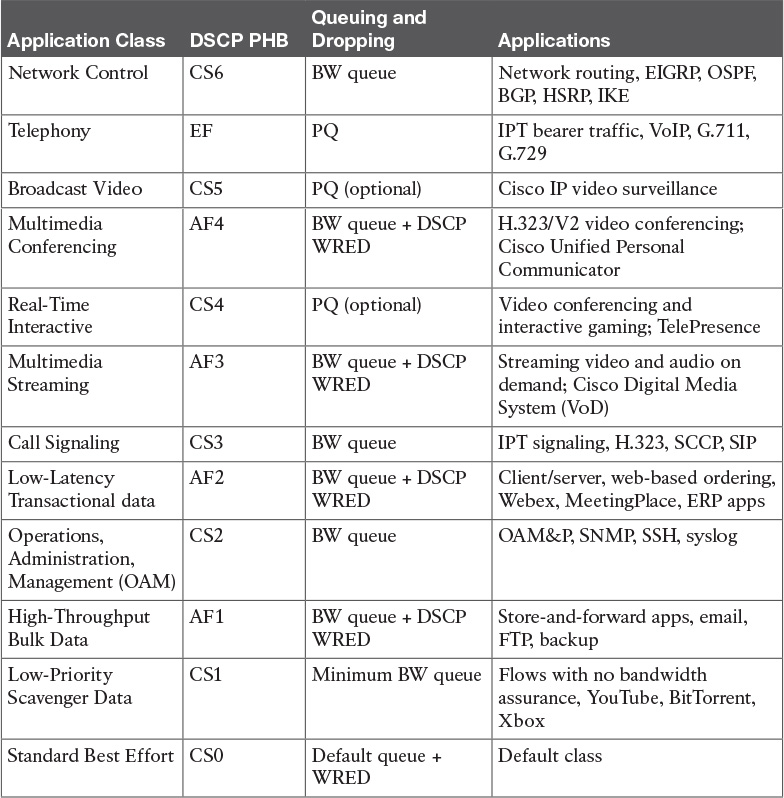
Table 14-15 Cisco Service Class PHB Recommendations
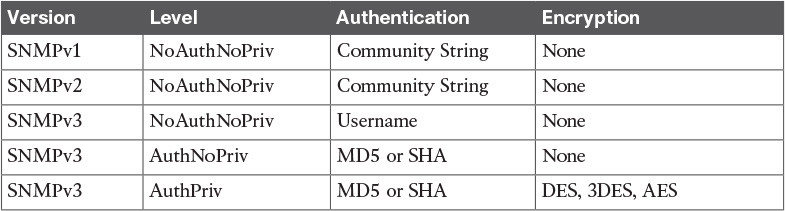
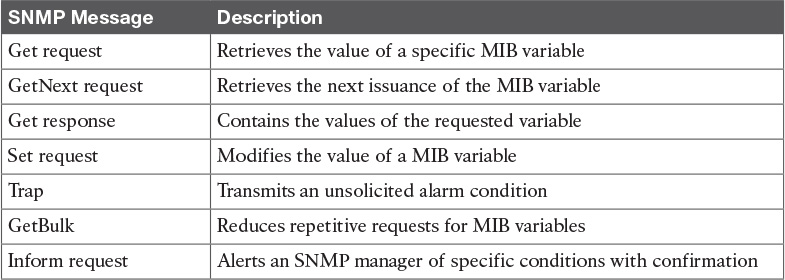
Table 15-4 SNMP Security Levels
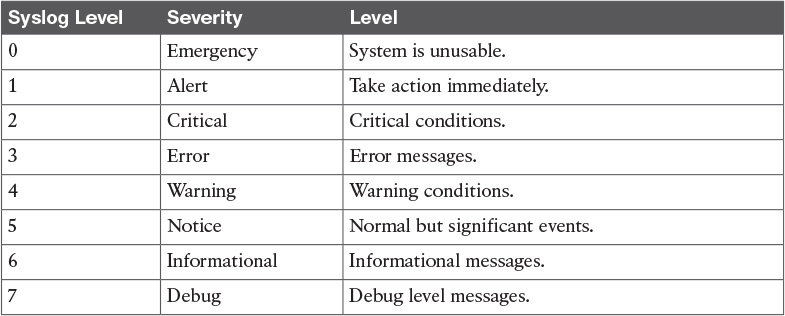
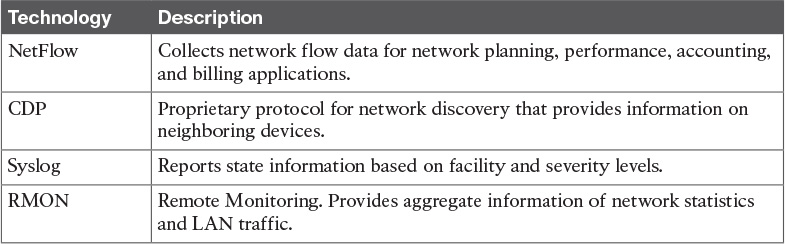
Table 15-7 Syslog Message Levels