Chapter 13. Security Solutions
This chapter covers the following subjects:
Trust and Identity Technologies
Detecting and Mitigating Threats
Security Management Applications
Integrating Security into Network Devices
This chapter covers Cisco Security Architecture for the Enterprise (SAFE), security technologies, and design options for securing the enterprise. The CCDA candidate can expect many questions related to integrating security technologies and mitigating security exposures. This chapter also focuses on how to integrate security into existing network devices and security platforms throughout your network. Furthermore, the CCDA must understand the different types of security features available and where to deploy them.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” helps you identify your strengths and deficiencies in this chapter’s topics.
The ten-question quiz, derived from the major sections in the “Foundation Topics” portion of the chapter, helps you determine how to spend your limited study time.
Table 13-1 outlines the major topics discussed in this chapter and the “Do I Know This Already?” quiz questions that correspond to those topics.
1. Which of the following are secure domains of the Cisco SAFE architecture? (Select all that apply.)
a. Segmentation
b. Compliance
c. Management
d. Data center
2. What network security platform combines a high-performance firewall with an IPS, antivirus, IPsec, and an SSL VPN in a single unified architecture?
a. Integrated Services Routers
b. Cisco Catalyst switches
c. Adaptive Security Appliances
d. Cisco ISE
3. Which media-level access control standard developed by IEEE permits and denies access to the network and applies traffic policy based on identity?
a. AES
b. 802.1X
c. Cisco ISE
d. ASA SM
4. What mechanism protects networks from threats by enforcing security compliance on all devices attempting to access the network?
a. Cisco ISE
b. SNMP
c. ASDM
d. 3DES
5. Which of the following can be used to perform firewall filtering with the use of ACLs? (Select all that apply.)
a. ASA
b. IPS
c. ASA SM
d. All of the above
6. What Cisco security appliance acts as an SMTP gateway for the enterprise?
a. Cisco ISE
b. Cisco ESA
c. Cisco ASA
d. Cisco WSA
7. Which security management solution integrates the configuration management of firewalls, VPNs, routers, switch modules, and IPS devices?
a. CSM
b. Cisco ISE
c. ASDM
d. ACS
8. When you’re integrating security into the network devices, which of the following can be used? (Select all that apply.)
a. RMON
b. ASA
c. Cisco IOS IPS
d. Syslog
9. Which of the following technologies is used to detect and mitigate threats in network traffic?
a. 802.1X
b. NetFlow
c. ASDM
d. SSH
10. What Cisco security management platform is used to control the TACACS and RADIUS protocols?
a. SSH
b. IPS
c. ACS
d. IDM
Foundation Topics
This chapter covers security topics that you need to master for the CCDA exam. It begins with a discussion of the Cisco SAFE architecture and then covers the strategy for identifying and responding to security threats. Next, the “Trust and Identity Technologies” section discusses the technologies and services used on network security devices such as routers and firewalls. Then the “Detecting and Mitigating Threats” section covers the technologies that support threat defense, such as intrusion prevention systems (IPSs), Adaptive Security Appliances (ASAs), and Cisco Identity Services Engine (ISE).
Furthermore, the “Security Management Applications” section describes the Cisco security management products designed to support the Cisco SAFE architecture. Next, the “Integrating Security into Network Devices” section covers the security features integrated into Cisco network devices, such as routers, firewalls, IPS, endpoint security, and Catalyst service modules. To wrap up, the “Securing the Enterprise” section reviews the places in the network (PINs) used to deploy security devices and solutions in the enterprise, data center, and the enterprise edge.
Cisco SAFE Architecture
Cisco Security Architecture for the Enterprise (SAFE) is a secure architectural framework that simplifies the complexity of security and focuses on the areas in the network that a company needs to secure. Part of the SAFE architecture discusses organizing complexity into places in the network (PINs) along with secure domains. PINs consist of the places in the network such as branch, campus, cloud, data center, edge, Internet, and WAN. Secure domains are the functional areas used to protect the places in the network. Because enterprise networks are key enablers of business, networks must be designed with integrated security in mind to ensure confidentiality, integrity, and availability of network resources, especially those networks that support critical business activity.
One key principle of Cisco SAFE architecture relates to the need for deep security and protection from both the inside and outside of the organization. Cisco SAFE provides guidelines for handling today’s threats and the capabilities needed to secure the network against those threats. The Cisco SAFE approach allows for the analysis of expected threats and supports the design of the network security strategy. In addition, the modular nature of Cisco SAFE allows for the security system to be expanded and scaled as the business grows.
The secure domains of Cisco SAFE are as follows:

![]() Secure Services provides access control, VPNs, and encryption. It protects insecure services such as applications and wireless networking.
Secure Services provides access control, VPNs, and encryption. It protects insecure services such as applications and wireless networking.
![]() Compliance covers policies both internal and external, including PCI DSS, HIPAA, and SOX.
Compliance covers policies both internal and external, including PCI DSS, HIPAA, and SOX.
![]() Threat Defense provides visibility for cyber-threats and uses network traffic telemetry, reputation, and contextual information. It also includes the assessment of risks due to suspicious activities and provides next steps.
Threat Defense provides visibility for cyber-threats and uses network traffic telemetry, reputation, and contextual information. It also includes the assessment of risks due to suspicious activities and provides next steps.
![]() Security Intelligence provides detection and aggregation of malware and threats. It enables the network to enforce policy dynamically as reputations are updated when new threats emerge.
Security Intelligence provides detection and aggregation of malware and threats. It enables the network to enforce policy dynamically as reputations are updated when new threats emerge.
![]() Segmentation creates boundaries for both users and data. Manual segmentation uses VLANs, network addressing, and firewalling for policy enforcement. Advanced segmentation uses identity-aware infrastructure to enforce policies automatically.
Segmentation creates boundaries for both users and data. Manual segmentation uses VLANs, network addressing, and firewalling for policy enforcement. Advanced segmentation uses identity-aware infrastructure to enforce policies automatically.
![]() Management provides services for devices and systems for consistent policy deployment, workflow-based change management, patch management, and alerting.
Management provides services for devices and systems for consistent policy deployment, workflow-based change management, patch management, and alerting.
The benefits of Cisco SAFE include the following:
![]() SAFE is the basis for the design of highly available secure networks.
SAFE is the basis for the design of highly available secure networks.
![]() SAFE provides for an open, modular, and expandable structure.
SAFE provides for an open, modular, and expandable structure.
![]() SAFE facilitates the development, implementation, and management of secure networks.
SAFE facilitates the development, implementation, and management of secure networks.
Figure 13-1 shows Cisco SAFE PINs and the secure domains.
Network Security Platforms
Network security starts with having a secure underlying network. The underlying network provides an ideal place to implement core and advanced security solutions. The center of these secure network solutions consists of the Adaptive Security Appliances (ASAs), Integrated Services Routers (ISRs), and Cisco Catalyst switches that have integrated security features. These are intelligent network security devices with many built-in security features that provide a framework for incorporating security throughout the network. Here is a description of some important security device platforms:
![]() ASA is a high-performance firewall appliance with IPS, antivirus, IPsec, and Secure Sockets Layer (SSL) virtual private network (VPN) technologies integrated into a single unified architecture. ASA also has support for FirePOWER IPS module capabilities.
ASA is a high-performance firewall appliance with IPS, antivirus, IPsec, and Secure Sockets Layer (SSL) virtual private network (VPN) technologies integrated into a single unified architecture. ASA also has support for FirePOWER IPS module capabilities.
![]() ISR G2 combines IOS firewall, VPN, and IPS services across the router portfolio, enabling new security features on existing routers. Supported VPNs include IPsec VPN, Dynamic Multipoint VPN (DMVPN), and SSL VPN.
ISR G2 combines IOS firewall, VPN, and IPS services across the router portfolio, enabling new security features on existing routers. Supported VPNs include IPsec VPN, Dynamic Multipoint VPN (DMVPN), and SSL VPN.
![]() Cisco Catalyst switches include denial of service (DoS) and man-in-the-middle attack mitigations and integration with service modules that provide firewall and VPN capabilities providing for secure connectivity. Unique security zones can be set up along with the virtualization of firewalls.
Cisco Catalyst switches include denial of service (DoS) and man-in-the-middle attack mitigations and integration with service modules that provide firewall and VPN capabilities providing for secure connectivity. Unique security zones can be set up along with the virtualization of firewalls.
Cisco Security Control Framework
The Cisco Security Control Framework (SCF) is a security framework that provides a foundation for securing networks based on proven industry best practices and security architecture principles. Cisco SCF is designed to address current threats and threats that are still evolving by using common and comprehensive security solutions. The Cisco SAFE architecture uses SCF to develop secure network designs that ensure high availability of network services. Cisco SCF influences security product selection and helps guide network implementations to allow for better visibility and control.
SCF assumes the presence of security policies derived from threat and risk assessments that complement the goals of the business. Security policies and guidelines define the acceptable-use policy for the secure use of network services and devices in the organization. The security policies should also determine the process and procedures for handling security events, which help define the security operations. To achieve business goals, it is critical to businesses that security policy and procedures empower the business rather than prevent access.

Total visibility and complete control are two of the main components of SCF. Network security is a function of visibility and control. Without visibility, there is a lack of control, and without control, you are missing key elements of security. The success of a security policy depends on solid visibility and control. Within SCF, there are six security actions used to enforce security policy and allow for visibility and control. Visibility is improved with identify, monitor, and correlate security actions; and control is enhanced through the harden, isolate, and enforce security actions. Each of these security actions is further defined in the SCF model.
Figure 13-2 describes of components of the Cisco SCF model.
Trust and Identity Technologies

Trust and identity technologies are security controls that enable network traffic security. The following are examples of technologies used to support trust and identity management:
![]() Access control lists (ACL): ACLs are used on routers, switches, and firewalls to control access. For example, ACLs are commonly used to restrict traffic on the ingress or egress of an interface by a wide variety of methods, such as using IP addresses and TCP or User Datagram Protocol (UDP) ports.
Access control lists (ACL): ACLs are used on routers, switches, and firewalls to control access. For example, ACLs are commonly used to restrict traffic on the ingress or egress of an interface by a wide variety of methods, such as using IP addresses and TCP or User Datagram Protocol (UDP) ports.
![]() Firewall: A security device designed to permit or deny network traffic based on source address, destination address, protocol, and port. The firewall enforces security by using the access and authorization policy to determine what is trusted and untrusted. The firewall also performs stateful packet inspection (SPI), which keeps track of the state of each TCP/UDP connection. SPI permits ingress traffic if the traffic originated from a higher security interface, such as the inside.
Firewall: A security device designed to permit or deny network traffic based on source address, destination address, protocol, and port. The firewall enforces security by using the access and authorization policy to determine what is trusted and untrusted. The firewall also performs stateful packet inspection (SPI), which keeps track of the state of each TCP/UDP connection. SPI permits ingress traffic if the traffic originated from a higher security interface, such as the inside.
![]() Port security: Port security is a security technique used on switch ports to limit MAC addresses permitted on a switch port. It can be used to define specific MAC addresses or limit the number of MAC addresses allowed on the switch port.
Port security: Port security is a security technique used on switch ports to limit MAC addresses permitted on a switch port. It can be used to define specific MAC addresses or limit the number of MAC addresses allowed on the switch port.
![]() 802.1X: An IEEE media-level access control standard that permits and denies admission to the network and applies traffic policy based on user or machine identity. 802.1X is used to control access to wired and wireless networks by allowing only authorized users and devices on the network.
802.1X: An IEEE media-level access control standard that permits and denies admission to the network and applies traffic policy based on user or machine identity. 802.1X is used to control access to wired and wireless networks by allowing only authorized users and devices on the network.
![]() Cisco Identity Services Engine (ISE): Cisco ISE is a security policy management platform that automates access control by enforcing compliance, increasing network security, and improving operations. Cisco ISE provides accurate identification of users and devices on the network, including easy provisioning of all devices. ISE collects rich contextual data about the connected users and devices and can provide policy enforcement and security compliance before the device is even authorized to access the network.
Cisco Identity Services Engine (ISE): Cisco ISE is a security policy management platform that automates access control by enforcing compliance, increasing network security, and improving operations. Cisco ISE provides accurate identification of users and devices on the network, including easy provisioning of all devices. ISE collects rich contextual data about the connected users and devices and can provide policy enforcement and security compliance before the device is even authorized to access the network.
The following sections cover some of these trust and identity technologies in more detail.
Firewall Fundamentals
A firewall is a security device that is responsible for enforcing the configured access control policy between network segments. Firewalls can be implemented with hardware appliances or with software-based solutions. The most important function for firewalls is preventing undesirable traffic on the outside of the firewall from accessing the internal network segments or DMZs on the inside. Because these network segment boundaries are so important, firewalls must adhere to some common functions. For example, if a software vulnerability were exploited in the firewall and became compromised, then the firewall would no longer be able to enforce the configured access control policy. Therefore, firewalls need to be resistant to attacks such as these.
For the firewall to create proper network segment boundaries, traffic needs to be pushed through the firewall so that the access control policy can be enforced. If there are alternate network paths, the traffic could flow around the firewall, thus bypassing the access control policy. Therefore, if there are redundant or additional paths in the network, firewalls should be used to enforce the firewall policy.
The access control policy defines the security rules about what traffic is allowed or blocked based on the company’s business requirements and objectives. These security rules build the basis for the documented firewall security policy. These security rules should then be implemented on firewalls enforcing the company’s access control policy.
Types of Firewalls

Today, there are many options when it comes to firewalls, each with its own capabilities and methods of implementing security services. Traditional firewall types include the following:
![]() Packet filtering firewalls use access control lists to permit or deny traffic and are sometimes referred to as stateless firewalls. The access control lists filter based on source and destination IP addresses, TCP/UDP port numbers, TCP flags, and ICMP types. As traffic flows through the ACL on the firewall, if traffic is matched by an ACL, then the action is taken without regard to any kind of state of the traffic flow. The packet filtering is actually occurring based on the information found in each packet that flows through the ACL. Packet filtering is typically used on routers and Layer 3 switches to restrict traffic flows and reduce the amount of traffic that needs to be further inspected.
Packet filtering firewalls use access control lists to permit or deny traffic and are sometimes referred to as stateless firewalls. The access control lists filter based on source and destination IP addresses, TCP/UDP port numbers, TCP flags, and ICMP types. As traffic flows through the ACL on the firewall, if traffic is matched by an ACL, then the action is taken without regard to any kind of state of the traffic flow. The packet filtering is actually occurring based on the information found in each packet that flows through the ACL. Packet filtering is typically used on routers and Layer 3 switches to restrict traffic flows and reduce the amount of traffic that needs to be further inspected.
![]() Stateful firewalls use stateful packet inspection (SPI) when evaluating traffic that passes through the firewall using a state table of existing traffic flows. As traffic enters the firewall, the traffic flow information is put into a state table to record the traffic flow. Then, as the return traffic comes back through the firewall, if a firewall record exists in the state table, the traffic is permitted back through. If the traffic flow does not exist in the state table, the traffic must be explicitly permitted by an ACL to be allowed through the firewall. A stateful firewall monitors the traffic from an initiating state, transferring state, or a terminating state. Most firewalls today are SPI firewalls.
Stateful firewalls use stateful packet inspection (SPI) when evaluating traffic that passes through the firewall using a state table of existing traffic flows. As traffic enters the firewall, the traffic flow information is put into a state table to record the traffic flow. Then, as the return traffic comes back through the firewall, if a firewall record exists in the state table, the traffic is permitted back through. If the traffic flow does not exist in the state table, the traffic must be explicitly permitted by an ACL to be allowed through the firewall. A stateful firewall monitors the traffic from an initiating state, transferring state, or a terminating state. Most firewalls today are SPI firewalls.
The two main advantages that SPI firewalls have over traditional packet filtering firewalls include the following:
![]() The use of a state table where all of the firewall connections are tracked as they flow through the firewall
The use of a state table where all of the firewall connections are tracked as they flow through the firewall
![]() Capability to recognize the applications that use dynamic ports for additional connections during the communication between hosts
Capability to recognize the applications that use dynamic ports for additional connections during the communication between hosts
![]() Application level gateways work up to Layer 7 of the OSI model and are sometimes referred to as proxy firewalls. These proxy firewalls run software that acts as a proxy between the source clients and destination servers. As traffic flows through the proxy firewall, source client connections are terminated and new connections are originated to the destination servers. The application-level gateway sits in the middle and controls the connections between the client and the server, allowing very granular policy to be applied to the traffic flows.
Application level gateways work up to Layer 7 of the OSI model and are sometimes referred to as proxy firewalls. These proxy firewalls run software that acts as a proxy between the source clients and destination servers. As traffic flows through the proxy firewall, source client connections are terminated and new connections are originated to the destination servers. The application-level gateway sits in the middle and controls the connections between the client and the server, allowing very granular policy to be applied to the traffic flows.
![]() Host-based firewalls consist of firewall software running on clients and/or servers protecting traffic on ingress or egress network interfaces.
Host-based firewalls consist of firewall software running on clients and/or servers protecting traffic on ingress or egress network interfaces.
![]() Transparent mode firewalls can be the same SPI firewalls as mentioned previously but are implemented as a bump in the wire at Layer 2. Transparent mode firewalls use L2 bridged interfaces and enforce policy using ACLs consisting of IP and TCP/UDP port information.
Transparent mode firewalls can be the same SPI firewalls as mentioned previously but are implemented as a bump in the wire at Layer 2. Transparent mode firewalls use L2 bridged interfaces and enforce policy using ACLs consisting of IP and TCP/UDP port information.
![]() Hybrid firewalls are firewalls that include functions of multiple firewall types such as a stateful firewall with application-level gateway capabilities.
Hybrid firewalls are firewalls that include functions of multiple firewall types such as a stateful firewall with application-level gateway capabilities.
Next-Gen Firewalls

Next-generation firewalls (NGFWs) are the most recent generation of firewalls. They combine traditional firewall functionality with additional security technologies, including the following:
![]() Application filtering with deep packet inspection using application signatures.
Application filtering with deep packet inspection using application signatures.
![]() Intrusion prevention system (IPS) inspects content passing through a firewall and compares it against known malicious signatures. Matched signatures can drop the affected packets or the entire session. Zero-day attacks can also be detected by executing suspicious code using cloud services and mitigated using new IPS signatures based on the suspicious code.
Intrusion prevention system (IPS) inspects content passing through a firewall and compares it against known malicious signatures. Matched signatures can drop the affected packets or the entire session. Zero-day attacks can also be detected by executing suspicious code using cloud services and mitigated using new IPS signatures based on the suspicious code.
![]() User Identification allows integration with LDAP or Microsoft Active Directory and can be used to apply security policy based on users or groups.
User Identification allows integration with LDAP or Microsoft Active Directory and can be used to apply security policy based on users or groups.
![]() Decryption of encrypted traffic provides visibility into SSL protected traffic. When decryption is enabled, the NGFW acts as a proxy by terminating the client SSL session on the firewall, and then it creates its own SSL session with the server. This allows for SSL traffic to be inspected.
Decryption of encrypted traffic provides visibility into SSL protected traffic. When decryption is enabled, the NGFW acts as a proxy by terminating the client SSL session on the firewall, and then it creates its own SSL session with the server. This allows for SSL traffic to be inspected.
![]() Antivirus and antimalware inspection provides protection against viruses and malware.
Antivirus and antimalware inspection provides protection against viruses and malware.
![]() URL filtering provides comprehensive alerting and control over suspicious web traffic.
URL filtering provides comprehensive alerting and control over suspicious web traffic.
NAT Placement
We need to use NAT because of the exhaustion of IPv4 public address space. Today, NAT is used extensively to enable Internet access on firewalls. In addition, port address translation (PAT) enables us to use many internal private addresses and translate them into a single public address. For servers that are public facing on the Internet, we need to use public IPv4 addressing. Either we can assign the server a public address without the need for NAT or we can assign the server a private address and have the firewall translate the address from public to private.
Using public IPv4 addressing simplifies the addressing and avoids NAT altogether; however, public IPv4 address blocks are very limited, and you might run out of space without being able to get more addresses assigned.
Another approach is to use NAT along with private addressing for your public-facing servers. This design allows you to use a firewall to handle the address translations between the public and private network segments. Firewall DMZs are typically used to place your public-facing servers into, and the firewall can use either static NAT or PAT to translate the addressing. With PAT, you can use a single public address on the firewall to translate traffic with different port numbers tied to different public-facing servers in the DMZ.
![]() Position firewalls at key network locations such as between the Internet and the inside network.
Position firewalls at key network locations such as between the Internet and the inside network.
![]() Firewalls should be the primary security enforcement point, but not the only one. Consider other security devices such as IPS and email security appliances.
Firewalls should be the primary security enforcement point, but not the only one. Consider other security devices such as IPS and email security appliances.
![]() Firewalls should be deployed with redundancy in mind, such as in an Active/Standby or Active/Active failover pair.
Firewalls should be deployed with redundancy in mind, such as in an Active/Standby or Active/Active failover pair.
![]() A closed security model is more secure and preferred over an open security model. Closed security refers to denying everything by default and then adding permit statements as exceptions. An open security model is the opposite. It allows all traffic by default and then deny statements are added as exceptions, which is less secure.
A closed security model is more secure and preferred over an open security model. Closed security refers to denying everything by default and then adding permit statements as exceptions. An open security model is the opposite. It allows all traffic by default and then deny statements are added as exceptions, which is less secure.
![]() Firewall features should be used as needed, such as dynamic NAT/PAT for Internet traffic along with stateful packet inspection (SPI).
Firewall features should be used as needed, such as dynamic NAT/PAT for Internet traffic along with stateful packet inspection (SPI).
![]() Secure physical and management access points in locations with locks or badge readers. Enforce management access with authorized users using separate authentication servers.
Secure physical and management access points in locations with locks or badge readers. Enforce management access with authorized users using separate authentication servers.
![]() Analyze and monitor the firewall’s events and logs. Look for anomalies and messages that might indicate further examination.
Analyze and monitor the firewall’s events and logs. Look for anomalies and messages that might indicate further examination.
![]() Use change management to document the firewall change and the associated back-out plan should something go wrong during the change window.
Use change management to document the firewall change and the associated back-out plan should something go wrong during the change window.
Firewall ACLs
Firewalls control access to and from the Internet and provide interaction with customers, suppliers, and employees. But because the Internet is unsecure, firewalls need to use ACLs to permit and deny traffic flowing through it. Firewalls use security zones to define trust levels that are associated with the firewall’s interfaces. For example, the trusted zone is associated with an interface connected to the internal network, and the untrusted zone is associated with an interface connected to outside of the firewall. Common security zones include the inside, outside, and demilitarized zone (DMZ), but others can be created as needed.
Figure 13-3 shows an ASA firewall with three zones and the permitted policy and flow of the traffic.
The policy for the firewall shown in Figure 13-3 includes the following:
![]() Allow HTTP and HTTPS to the Internet
Allow HTTP and HTTPS to the Internet
![]() Allow HTTPS and FTP to the public web and FTP server
Allow HTTPS and FTP to the public web and FTP server
![]() Allow HTTPS to the public e-commerce server
Allow HTTPS to the public e-commerce server
Cisco Identity-Based Network Services
The Cisco Identity-Based Network Services solution is a way to authenticate host access based on policy for admission to the network. IBNS supports identity authentication, dynamic provisioning of VLANs on a per-user basis, guest VLANs, and 802.1X with port security.
The 802.1X protocol is a standards-based protocol for authenticating network clients by permitting or denying access to the network. The 802.1X protocol operates between the end-user client seeking access and an Ethernet switch or wireless access point (AP) providing the connection to the network. In 802.1X terminology, clients are called supplicants, and switches and APs are called authenticators. A back-end Remote Authentication Dial-In User Service (RADIUS) server such as a Cisco Identity Services Engine (ISE) provides the user account database used to apply authentication and authorization.
With an IBNS solution, the host uses 802.1X and Extensible Authentication Protocol over LANs (EAPoL) to send the credentials and initiate a session to the network. After the host and switch establish LAN connectivity, username and password credentials are requested. The client host then sends the credentials to the switch, which forwards them to the RADIUS service running on Cisco ISE.
The RADIUS service performs a lookup on the username and password to determine the credentials’ validity. If the username and password are correct, an accept message is sent to the switch or AP to allow access to the client host. If the username and password are incorrect, the server sends a message to the switch or AP to block the host port.
Figure 13-4 illustrates the communication flow of two hosts using 802.1X and EAPoL with the switch, AP, and back-end Cisco ISE server running RADIUS.
Identity and Access Control Deployments
Validating user authentication should be implemented as close to the source as possible, with an emphasis on strong authentication for access from untrusted networks. Access rules should enforce policy deployed throughout the network with the following guidelines:
![]() Source-specific rules with any type destinations should be applied as close to the source as possible.
Source-specific rules with any type destinations should be applied as close to the source as possible.
![]() Destination-specific rules with any type sources should be applied as close to the destination as possible.
Destination-specific rules with any type sources should be applied as close to the destination as possible.
![]() Mixed rules integrating both source and destination should be used as close to the source as possible.
Mixed rules integrating both source and destination should be used as close to the source as possible.
An integral part of identity and access control deployments is to allow only the necessary access. Highly distributed rules allow for greater granularity and scalability but, unfortunately, increase the management complexity. On the other hand, centralized rule deployment eases management but lacks flexibility and scalability.
Figure 13-5 shows the importance of the authentication databases and how many network components in the enterprise rely on them for authentication services.
Detecting and Mitigating Threats

The use of threat detection and mitigation techniques enables early detection of and notifications about unwanted malicious traffic. The goals are to detect, notify, and help stop unforeseen and unauthorized traffic. These techniques help increase the network’s availability, particularly against unidentified and unexpected attacks. Threat detection and mitigation solutions include the following:
![]() Endpoint protection: Viruses and worms can create havoc by propagating infections from host to host throughout the network. Antivirus services can help hosts detect and remove infections based on known virus pattern markings.
Endpoint protection: Viruses and worms can create havoc by propagating infections from host to host throughout the network. Antivirus services can help hosts detect and remove infections based on known virus pattern markings.
![]() Application security and content security defense: Several new application layer network products have been released that help address new classes of threats, such as spam, phishing, spyware, packet abuse, and unauthorized point-to-point file sharing. Content security products such as Cisco WSA Appliances provide comprehensive antivirus, antispyware, file-blocking, antispam, URL blocking, and content-filtering services. These products supplement traditional firewalls and intrusion prevention system (IPS) solutions with more granular traffic inspection services, thereby quarantining traffic so that it does not propagate throughout the network.
Application security and content security defense: Several new application layer network products have been released that help address new classes of threats, such as spam, phishing, spyware, packet abuse, and unauthorized point-to-point file sharing. Content security products such as Cisco WSA Appliances provide comprehensive antivirus, antispyware, file-blocking, antispam, URL blocking, and content-filtering services. These products supplement traditional firewalls and intrusion prevention system (IPS) solutions with more granular traffic inspection services, thereby quarantining traffic so that it does not propagate throughout the network.
![]() Infection containment: The Cisco ASA, ASA Services Module, and IOS firewalls protect the network by creating security zones that partition the network into separate segments. The firewall services provide perimeter network security but do not eliminate the need for continuous network monitoring. As part of the Cisco SAFE architecture, Cisco ISE can be used in the perimeter to perform policy-based admission control, thus reducing potential threats.
Infection containment: The Cisco ASA, ASA Services Module, and IOS firewalls protect the network by creating security zones that partition the network into separate segments. The firewall services provide perimeter network security but do not eliminate the need for continuous network monitoring. As part of the Cisco SAFE architecture, Cisco ISE can be used in the perimeter to perform policy-based admission control, thus reducing potential threats.
![]() Inline IPS: Cisco has innovated in the area of IPS by being the first to incorporate IPS into the IOS on routing and switching platforms. In addition, IPS solutions have inline filtering features that can remove unwanted traffic with programmable features that classify traffic patterns. The Cisco IOS IPS can identify, analyze, and stop unwanted traffic from flowing on the network.
Inline IPS: Cisco has innovated in the area of IPS by being the first to incorporate IPS into the IOS on routing and switching platforms. In addition, IPS solutions have inline filtering features that can remove unwanted traffic with programmable features that classify traffic patterns. The Cisco IOS IPS can identify, analyze, and stop unwanted traffic from flowing on the network.
IPS/IDS Fundamentals
Intrusion prevention and intrusion detection systems are network security devices that proactively identify and block security threats. Today’s security threats are far too complex to be secured by a single security device. Although security techniques such as access control, firewall services, and device hardening help secure the network from attacks, they cannot provide adequate protections from fast moving malware or zero-day attacks. Network security must adapt to these threats, and new network designs should include IDS and IPS that have features that can detect and block these new and evolving threats.
Both IPS and IDS look at packet payloads and compare these against security signatures that they know about.
Intrusion prevention systems are classified into two categories:

![]() Intrusion detection systems (IDSs) are passive devices that monitor traffic and generate alerts or logs when suspicious traffic is detected from attacks such as reconnaissance or DoS attacks. Since IDS devices are only analyzing traffic flows, there is no impact at all to network performance.
Intrusion detection systems (IDSs) are passive devices that monitor traffic and generate alerts or logs when suspicious traffic is detected from attacks such as reconnaissance or DoS attacks. Since IDS devices are only analyzing traffic flows, there is no impact at all to network performance.
![]() Intrusion prevention systems (IPSs) are active devices that not only can detect but also block malicious traffic from coming into the network. For the IPS to actually block traffic, it has to be deployed in inline mode, where traffic is forced through the IPS. That way, the IPS can detect and prevent suspicious traffic in real time from accessing the internal network.
Intrusion prevention systems (IPSs) are active devices that not only can detect but also block malicious traffic from coming into the network. For the IPS to actually block traffic, it has to be deployed in inline mode, where traffic is forced through the IPS. That way, the IPS can detect and prevent suspicious traffic in real time from accessing the internal network.
IPS/IDS technologies are commonly deployed as sensors, and they are available in many options. IPS sensors can be deployed on dedicated hardware appliances or using IPS software on routers, switches, or firewall modules. Both IPS and IDS technologies need to be able to detect malicious traffic, which has unique characteristics identified through the use of signatures. A signature is a set of rules that IPS/IDS sensors use to detect suspicious activity during network attacks. Signatures can detect viruses, malware, and protocol anomalies. Sensors are tuned to detect irregular traffic patterns or viruses by matching a signature.
Both IPS and IDS can be used together to increase security by providing extra visibility into the traffic flows. Because an IDS has zero impact on the network, it can be used to do deeper packet inspections in more areas within the network, and the IPS can be used for the most critical parts of the network.
Table 13-2 outlines the pros and cons of IDS and IPS devices.

IPS/IDS Guidelines
Here are some recommended guidelines to consider when deploying IPS/IDS services:
![]() Place IPS sensor appliances behind the firewall so that you only see traffic that has been filtered by the firewall policy
Place IPS sensor appliances behind the firewall so that you only see traffic that has been filtered by the firewall policy
![]() Review the traffic load that it will need to handle as part of proper capacity planning for sizing the IPS sensors. Consider the performance impacts of enabling IPS features.
Review the traffic load that it will need to handle as part of proper capacity planning for sizing the IPS sensors. Consider the performance impacts of enabling IPS features.
![]() Tune default signatures to reduce false positives. Monitor traffic for the first 30 days and tune the signatures afterwards to filter out noisy signatures.
Tune default signatures to reduce false positives. Monitor traffic for the first 30 days and tune the signatures afterwards to filter out noisy signatures.
![]() Develop an update schedule for downloading signatures near the release time of the new signatures. Tune the new signatures if needed.
Develop an update schedule for downloading signatures near the release time of the new signatures. Tune the new signatures if needed.
![]() Monitor network events on a daily basis and look for malicious traffic patterns by correlating the events through a central monitoring system.
Monitor network events on a daily basis and look for malicious traffic patterns by correlating the events through a central monitoring system.
Figure 13-6 illustrates the recommended IPS placement behind the firewall.
Threat Detection and Mitigation Technologies
Here are some examples of Cisco threat-detection and threat-mitigation technologies:
![]() ASA Service Module: Catalyst 6500 ASA Services Module
ASA Service Module: Catalyst 6500 ASA Services Module
![]() ASA: Adaptive Security Appliance (robust firewall)
ASA: Adaptive Security Appliance (robust firewall)
![]() IOS firewall: Cisco IOS software feature set
IOS firewall: Cisco IOS software feature set
![]() FirePOWER IPS: Module for ASA appliance
FirePOWER IPS: Module for ASA appliance
![]() FirePOWER Next-Gen IPS appliances
FirePOWER Next-Gen IPS appliances
![]() IPS: Intrusion prevention system (IOS feature)
IPS: Intrusion prevention system (IOS feature)
![]() Cisco Web Security Appliance (Cisco WSA)
Cisco Web Security Appliance (Cisco WSA)
![]() Cisco Email Security Appliance (Cisco ESA)
Cisco Email Security Appliance (Cisco ESA)
![]() Network management protocols and solutions:
Network management protocols and solutions:
![]() NetFlow: Stats on packets flowing through router (IOS feature)
NetFlow: Stats on packets flowing through router (IOS feature)
![]() Syslog: Logging data (IOS feature)
Syslog: Logging data (IOS feature)
![]() SNMP: Simple Network Management Protocol (IOS feature)
SNMP: Simple Network Management Protocol (IOS feature)
Threat-Detection and Threat-Mitigation Solutions
Threat-detection and threat-mitigation solutions are deployed throughout the network and can serve as an effective layered defense for secure network communications. For example, suppose your network is being attacked from the Internet (for example, via a worm or virus outbreak). The Internet WAN routers are your first line of protection and can be used to spot increasing network load or suspicious NetFlow data. After some information has been collected, you can use specific granular ACLs to further identify the attack.
Firewalls can perform stateful packet inspections and can ultimately block unwanted network traffic in the event of an attack. However, it is preferable to engage the ISP and have them block the attack from even entering your network.
To successfully detect threats and mitigate them, it is important to understand where to look for potential threats. The following are good sources of information for detecting and mitigating threats:
![]() NetFlow
NetFlow
![]() Syslog
Syslog
![]() Remote Monitor (RMON) events
Remote Monitor (RMON) events
![]() Simple Network Management Protocol (SNMP) thresholds and traps
Simple Network Management Protocol (SNMP) thresholds and traps
![]() CPU and interface statistics
CPU and interface statistics
Figure 13-7 depicts an attacker sourcing from the Internet and targeting the internal network and how to detect and mitigate the threat.
FirePOWER IPS
The growth of data center resources along with increased security policy complexity are driving the need for next-generation security services. A comprehensive set of security capabilities is needed in order to combat advanced data security threats in addition to firewall security services. Cisco ASA clustering along with FirePOWER service modules provides increased security capabilities and simplicity to help mitigate these challenges.

FirePOWER module features and benefits for Cisco ASA appliances include the following:
![]() Next-generation intrusion prevention system (NGIPS): Provides threat protection and contextual awareness
Next-generation intrusion prevention system (NGIPS): Provides threat protection and contextual awareness
![]() URL filtering: Provides over 80 categories and millions of URLs for filtering
URL filtering: Provides over 80 categories and millions of URLs for filtering
![]() Application Visibility and Control (AVC): Provides over 3000 application layer and risk-based controls
Application Visibility and Control (AVC): Provides over 3000 application layer and risk-based controls
![]() Advanced Malware Protection (AMP): Provides malware detection and blocking
Advanced Malware Protection (AMP): Provides malware detection and blocking
Cisco ESA
Cisco Email Security Appliances (ESAs) are designed to protect networks from today’s and tomorrow’s email threats. Cisco ESA is a firewall and threat-monitoring appliance for SMTP-based traffic (on TCP port 25). Cisco ESAs are available as physical hardware appliances or as virtual Cisco ESA appliances. In the email delivery process, ESA acts as an SMTP gateway firewall for the enterprise. One of the advantages of using Cisco EAS for your MTA in the message transfer chain is that ESA can determine the source IP address and query that against the Cisco SenderBase to get the sender’s reputation score. Cisco ESA uses the reputation score to stop spam, viruses, and malware from arriving in users’ mailboxes.
Multiple deployment options are available depending on the number of interfaces used. It is generally recommended to place the ESA appliance close to the Internet firewall. The most common deployment option uses a single physical interface inserted in a dedicated or shared DMZ firewalled network segment. An alternative approach is to use two interfaces, one to send and receive email traffic located in the DMZ and another interface connected to an inside network to deliver mail to internal mail servers. With either approach, it is recommended to use a static Network Address Translation (NAT) on the Internet firewall to translate the public address into a private address located in the DMZ.
Cisco WSA
The Cisco Web Security Appliance (WSA) is designed to monitor and mitigate abnormal web traffic between users and the public Internet. WSA appliances provide web filtering, malware protection, identity-based polices, and SSL offload services. Cisco WSAs are available as physical hardware appliances or as virtual Cisco WSA appliances. The WSA acts as a web proxy for the corporate users residing on the internal network segments and is logically placed in the path between the users and the Internet. There are three ways to implement the WSA, two of which require Internet browser customizations.
Table 13-3 describes the Cisco WSA mode options.
It is recommended to use explicit mode with PAC files for testing and then transition to WCCP for final implementation. The PAC file implementation is much easier to deploy during testing than WCCP because you just need to modify the test browser proxy settings; however, the WCCP mode is much more elegant in the long run because you do not need to modify all the users’ browsers settings.
Security Management Applications
Security management applications consolidate network management and monitoring, which allows more secure control of the network. Security management provides several functions:
![]() Central repository for collecting network information for further analysis of security-related events. In addition, many applications have reporting capabilities to help network managers’ present technical information to upper management. Some examples include authentication, authorization, and accounting (AAA) with TACACS and RADIUS servers, Cisco ISE, and syslog servers.
Central repository for collecting network information for further analysis of security-related events. In addition, many applications have reporting capabilities to help network managers’ present technical information to upper management. Some examples include authentication, authorization, and accounting (AAA) with TACACS and RADIUS servers, Cisco ISE, and syslog servers.
![]() Allows for easier deployment of security policies into the security devices via graphical user interface (GUI) tools. These tools help you maintain the consistency of the security policies across a broad spectrum of network device types.
Allows for easier deployment of security policies into the security devices via graphical user interface (GUI) tools. These tools help you maintain the consistency of the security policies across a broad spectrum of network device types.
![]() Role-based access control for all accounts to separate administrative tasks and user functions.
Role-based access control for all accounts to separate administrative tasks and user functions.
Security implementations need to be planned properly using the security policies governed by the organization to make good use of the security applications. From time to time, audits are necessary, which requires updates to the security policy and related security management applications. A major risk to security implementations is policy error. Management needs to be cognizant of the security policy and know how to manage incidents properly.
Security Platform Solutions

Cisco has a variety of security management products and technologies that allow scalable administration and enforcement of security policy for the Cisco SCF architecture. These solutions reduce the operational management and automate many of the common tasks, including configuration, analysis, incident response, and reporting. Security management platforms include the following:
![]() Cisco Security Manager (CSM) is an integrated solution for GUI configuration management of firewall, VPN, and IPS policies on Cisco security appliances, firewalls, routers, and switch modules. CSM has capabilities for security policies to be deployed by device, by group, or globally for all devices.
Cisco Security Manager (CSM) is an integrated solution for GUI configuration management of firewall, VPN, and IPS policies on Cisco security appliances, firewalls, routers, and switch modules. CSM has capabilities for security policies to be deployed by device, by group, or globally for all devices.
![]() Cisco Secure Access Control Server (ACS) provides centralized control for administrative access to Cisco devices and security applications. ACS provides for AAA security services and supports routers, switches, VPN services, and ASAs. In addition, Cisco ACS also supports back-end directory integration with Lightweight Directory Access Protocol (LDAP) and Microsoft Active Directory (AD) for authentication services.
Cisco Secure Access Control Server (ACS) provides centralized control for administrative access to Cisco devices and security applications. ACS provides for AAA security services and supports routers, switches, VPN services, and ASAs. In addition, Cisco ACS also supports back-end directory integration with Lightweight Directory Access Protocol (LDAP) and Microsoft Active Directory (AD) for authentication services.
![]() Cisco Identity Services Engine (ISE): Cisco ISE is a security policy management platform that automates access control by enforcing compliance, increasing network security, and improving operations. Cisco ISE provides accurate identification of users and devices on the network including easy provisioning of all devices. ISE collects rich contextual data about the connected users and devices and can provide policy enforcement and security compliance before the device is even authorized to access the network.
Cisco Identity Services Engine (ISE): Cisco ISE is a security policy management platform that automates access control by enforcing compliance, increasing network security, and improving operations. Cisco ISE provides accurate identification of users and devices on the network including easy provisioning of all devices. ISE collects rich contextual data about the connected users and devices and can provide policy enforcement and security compliance before the device is even authorized to access the network.
![]() System Administration Jump Host provides a centralized host used to stage configuration, software images, and implement network changes.
System Administration Jump Host provides a centralized host used to stage configuration, software images, and implement network changes.
![]() Network Time Protocol (NTP) server provides time synchronization to NTP clients such as routers and switches. Time synchronization is crucial in the analysis of event correlations.
Network Time Protocol (NTP) server provides time synchronization to NTP clients such as routers and switches. Time synchronization is crucial in the analysis of event correlations.
![]() Configuration and Software Archive Host serves as a repository to backup device configurations and software images.
Configuration and Software Archive Host serves as a repository to backup device configurations and software images.
Security Management Network
The SAFE architecture design incorporates a management network module dedicated to carrying network management and control plane traffic such as NTP, SSH, SNMP, TACACS, VPN, syslog, and NetFlow reporting. Two primary technologies are used in the management module: Cisco IOS routers acting as terminal servers and a management VLAN or separate network segment. Together, these technologies provide configuration management to nearly all network devices. The management VLAN provides the primary access method for devices using SSH and HTTPS. Hardened terminal servers provide console access and command-line interface (CLI) using reverse Telnet functions. It is a best practice to configure your network devices to send network management traffic such as NTP, SSH, SNMP, TACACS, syslog, and NetFlow traffic back to the dedicated network management VLAN.
Network management can be implemented in both in-band (IB) management and out-of-band (OOB) management configurations designed to provide secure management of network devices within the enterprise. OOB management is typically located at the headquarters and uses dedicated Ethernet ports on the devices connected to the OOB VLAN or network segment. These Ethernet ports are intended to be used for management and monitoring functions of the network devices. The OOB management network can be a separate LAN or by using an isolated VLAN. The in-band management is used for remote devices such as branch site routers and the access is provided through a firewalled data path through the core network.
In some cases, console access to the network equipment is needed, and that functionality can be provided using an OOB console server.
Figure 13-8 illustrates the security management network using both IB and OOB networks for carrying control and management plane traffic. The firewall controls the security between the IB and OOB networks.
Integrating Security into Network Devices

It is crucial to integrate security into all network devices throughout your network. Common device types include
![]() IOS routers and switches
IOS routers and switches
![]() Adaptive Security Appliances (ASAs)
Adaptive Security Appliances (ASAs)
![]() Intrusion Prevention Systems (IPSs)
Intrusion Prevention Systems (IPSs)
![]() Catalyst 6500 service modules
Catalyst 6500 service modules
![]() Endpoint security
Endpoint security
The following sections discuss device security integration in more detail.
IOS Security
Cisco has developed many security features that are integrated into the IOS base software or security-specific feature sets. Here are some of the major areas of security focus that have been included with IOS releases:
![]() Cisco IOS firewall is a security-specific option that provides stateful firewall functionality for perimeter IOS routers. Cisco IOS firewall provides effective control of application traffic flowing through the network. Key benefits of IOS firewall include protecting networks from network and application layer attacks, improving uptime, and offering policy enforcement for internal and external connections.
Cisco IOS firewall is a security-specific option that provides stateful firewall functionality for perimeter IOS routers. Cisco IOS firewall provides effective control of application traffic flowing through the network. Key benefits of IOS firewall include protecting networks from network and application layer attacks, improving uptime, and offering policy enforcement for internal and external connections.
![]() Cisco IOS IPS offers inline deep packet inspection to successfully diminish a wide range of network attacks. IOS IPS can identify, classify, and block malicious traffic in real time. IOS IPS operates by loading attack signatures on the router and then matching the attacks based on signatures. Cisco also provides prebuilt signature definition files (SDF) that contain high-fidelity signatures that are based on the memory available on the router.
Cisco IOS IPS offers inline deep packet inspection to successfully diminish a wide range of network attacks. IOS IPS can identify, classify, and block malicious traffic in real time. IOS IPS operates by loading attack signatures on the router and then matching the attacks based on signatures. Cisco also provides prebuilt signature definition files (SDF) that contain high-fidelity signatures that are based on the memory available on the router.
![]() Cisco IOS IPsec encrypts data at the IP packet level using a set of standards-based protocols. IPsec provides data authentication, anti-replay, and data confidentially, and is the preferred method of securing VPNs.
Cisco IOS IPsec encrypts data at the IP packet level using a set of standards-based protocols. IPsec provides data authentication, anti-replay, and data confidentially, and is the preferred method of securing VPNs.
![]() Cisco IOS Trust and Identity is a set of core technologies that enables network traffic security. Technologies include the following:
Cisco IOS Trust and Identity is a set of core technologies that enables network traffic security. Technologies include the following:
![]() AAA: Framework and mechanisms for controlling device access
AAA: Framework and mechanisms for controlling device access
![]() Secure Shell (SSH): Used for encrypted access between applications and routers
Secure Shell (SSH): Used for encrypted access between applications and routers
![]() Secure Socket Layer (SSL): Secure web application access
Secure Socket Layer (SSL): Secure web application access
![]() PKI (Public Key Infrastructure): Strong authentication for e-commerce applications
PKI (Public Key Infrastructure): Strong authentication for e-commerce applications
Table 13-4 describes the Cisco IOS integrated security features.

ISR G2 Security Hardware Options
The Cisco G2 ISRs have additional hardware options that enhance the routers’ security capabilities. Here are some of the available hardware options:
![]() Built-In VPN Acceleration is hardware-based encryption that offloads VPN processing from the router’s internal CPU to improve VPN throughput.
Built-In VPN Acceleration is hardware-based encryption that offloads VPN processing from the router’s internal CPU to improve VPN throughput.
![]() High-Performance Advanced Integration Module (AIM) is a VPN encryption advanced integration module used to terminate large numbers of VPN tunnels such as with Dynamic Multipoint VPN (DMVPN). The module supports Triple Digital Encryption Standard (3DES) and Advanced Encryption Standard (AES), which increases the router’s encryption and compression performance.
High-Performance Advanced Integration Module (AIM) is a VPN encryption advanced integration module used to terminate large numbers of VPN tunnels such as with Dynamic Multipoint VPN (DMVPN). The module supports Triple Digital Encryption Standard (3DES) and Advanced Encryption Standard (AES), which increases the router’s encryption and compression performance.
![]() IPS Enhanced Network Module (IPS NME) provides technologies to prevent a large range of security threats using hardware-based intrusion prevention. Cisco IPS NME can identify, classify, and stop unwanted traffic, including spyware, malware, network viruses, and worms. The IPS NME can monitor up to 75 Mbps of traffic and supports T1/E1 and T3 WAN interfaces.
IPS Enhanced Network Module (IPS NME) provides technologies to prevent a large range of security threats using hardware-based intrusion prevention. Cisco IPS NME can identify, classify, and stop unwanted traffic, including spyware, malware, network viruses, and worms. The IPS NME can monitor up to 75 Mbps of traffic and supports T1/E1 and T3 WAN interfaces.
![]() Universal serial bus (USB) port and removable credentials: G2 ISRs were designed with onboard USB 1.1 ports, enabling security and storage capabilities. The USB ports allow for storing removable credentials for establishing IPsec VPN connections, configuration files, and software images.
Universal serial bus (USB) port and removable credentials: G2 ISRs were designed with onboard USB 1.1 ports, enabling security and storage capabilities. The USB ports allow for storing removable credentials for establishing IPsec VPN connections, configuration files, and software images.
![]() Secure Voice: Referred to as digital signal processor (DSP) slots on the ISR for use with packet voice/fax DSP modules (PVDMs). These offer capabilities such as conferencing and transcoding. In addition, Secure Real-time Transport Protocol (SRTP) protects the entire voice payload by encryption, except for the header, which remains in clear text to support QoS.
Secure Voice: Referred to as digital signal processor (DSP) slots on the ISR for use with packet voice/fax DSP modules (PVDMs). These offer capabilities such as conferencing and transcoding. In addition, Secure Real-time Transport Protocol (SRTP) protects the entire voice payload by encryption, except for the header, which remains in clear text to support QoS.
Note
For a complete ISR G2 series comparison, go to www.cisco.com/en/US/products/ps10536/prod_series_comparison.html.
Cisco Security Appliances

Cisco security appliances provide robust security services and protection for firewalling, VPN services, content defenses, intrusion prevention services, and network access control. The following is an overview of Cisco security appliances:
![]() Adaptive Security Appliance (ASA): The ASA is a high-performance, multifunction security appliance that offers a comprehensive set of services for securing network environments. The services are customized through product editions tailored for firewall, IPS, anti-virus, and VPN. The ASA is a critical component of the Cisco SAFE architecture that provides proactive threat mitigation, controls application data flows, and delivers flexible VPN and IPS services. In addition, the ASA is very cost-effective and easy to manage, and offers advanced integration modules that enhance the processing capabilities. ASA also has support for FirePOWER IPS module capabilities.
Adaptive Security Appliance (ASA): The ASA is a high-performance, multifunction security appliance that offers a comprehensive set of services for securing network environments. The services are customized through product editions tailored for firewall, IPS, anti-virus, and VPN. The ASA is a critical component of the Cisco SAFE architecture that provides proactive threat mitigation, controls application data flows, and delivers flexible VPN and IPS services. In addition, the ASA is very cost-effective and easy to manage, and offers advanced integration modules that enhance the processing capabilities. ASA also has support for FirePOWER IPS module capabilities.
![]() ASAs for VPNs: The Cisco ASAs provide businesses with IPsec and SSL VPN connectivity. ASAs are flexible and offer many deployment scenarios. Although they are commonly used to terminate VPN sessions for remote-access connections, ASAs can also be used to terminate site-to-site tunnels with other ASAs, routers, or even non-Cisco firewalls. The centralized architecture and web-based management ease the administrative burden and consolidate the VPN connectivity for the enterprise.
ASAs for VPNs: The Cisco ASAs provide businesses with IPsec and SSL VPN connectivity. ASAs are flexible and offer many deployment scenarios. Although they are commonly used to terminate VPN sessions for remote-access connections, ASAs can also be used to terminate site-to-site tunnels with other ASAs, routers, or even non-Cisco firewalls. The centralized architecture and web-based management ease the administrative burden and consolidate the VPN connectivity for the enterprise.
![]() Cisco Identity Services Engine (ISE): Cisco ISE is a security policy management platform that automates access control by enforcing compliance, increasing network security, and improving operations. Cisco ISE provides accurate identification of users and devices on the network, including easy provisioning of all devices. ISE collects rich contextual data about the connected users and devices, and can provide policy enforcement and security compliance before a device is even authorized to access the network.
Cisco Identity Services Engine (ISE): Cisco ISE is a security policy management platform that automates access control by enforcing compliance, increasing network security, and improving operations. Cisco ISE provides accurate identification of users and devices on the network, including easy provisioning of all devices. ISE collects rich contextual data about the connected users and devices, and can provide policy enforcement and security compliance before a device is even authorized to access the network.
Catalyst 6500 Service Modules

The Catalyst 6500 switching platform supports additional security services and functionality through the use of service modules. Several service module options extend the capabilities of security-related services with the Cisco Catalyst 6500 platform. Many environments now combine many of these service modules together to form what is now referred to as services switches.
Catalyst 6500 security-related service modules include the following:
![]() ASA Services Module is a high-speed firewall module for use in the Cisco Catalyst 6500 and Cisco 7600 series routing platforms. Up to four ASA Service Modules can be installed in a single chassis, providing 20 Gbps of throughput performance per module. For service provider and large enterprise environments, the ASA Service Module supports advanced features such as multiple security contexts for both routed and transparent firewall modes. Running multiple contexts on the same firewall hardware is a technique used to virtualize the ASA into multiple firewalls, each with its own configuration and firewall policy.
ASA Services Module is a high-speed firewall module for use in the Cisco Catalyst 6500 and Cisco 7600 series routing platforms. Up to four ASA Service Modules can be installed in a single chassis, providing 20 Gbps of throughput performance per module. For service provider and large enterprise environments, the ASA Service Module supports advanced features such as multiple security contexts for both routed and transparent firewall modes. Running multiple contexts on the same firewall hardware is a technique used to virtualize the ASA into multiple firewalls, each with its own configuration and firewall policy.
![]() IPsec VPN SPA enables cost-effective and scalable VPN services using the Cisco Catalyst 6500 series switches and Cisco 7600 series routing platforms. The module does not have any interfaces, but instead uses the other LAN and WAN interfaces that are available on the chassis. Using the SPA Carrier-400, each slot of the Cisco Catalyst 6500 or Cisco 7600 router can support up to two Cisco IPsec VPN SPAs.
IPsec VPN SPA enables cost-effective and scalable VPN services using the Cisco Catalyst 6500 series switches and Cisco 7600 series routing platforms. The module does not have any interfaces, but instead uses the other LAN and WAN interfaces that are available on the chassis. Using the SPA Carrier-400, each slot of the Cisco Catalyst 6500 or Cisco 7600 router can support up to two Cisco IPsec VPN SPAs.
![]() WebVPN Services Module is a high-speed integrated SSL VPN Services Module for support of large-scale remote-access VPN deployments. The WebVPN Services Module supports up to 32,000 SSL VPN users, and up to 4 modules can be used in a single chassis.
WebVPN Services Module is a high-speed integrated SSL VPN Services Module for support of large-scale remote-access VPN deployments. The WebVPN Services Module supports up to 32,000 SSL VPN users, and up to 4 modules can be used in a single chassis.
![]() Network Analysis Module 3 provides packet-capture capabilities and visibility into all the layers of the network data flows, including overlay technologies such as CAPWAP and VXLAN. You can analyze application traffic between hosts, networks, and servers. The NAM supports L4-7 visibility using Cisco Network-based Application Recognition 2 (NBAR2).
Network Analysis Module 3 provides packet-capture capabilities and visibility into all the layers of the network data flows, including overlay technologies such as CAPWAP and VXLAN. You can analyze application traffic between hosts, networks, and servers. The NAM supports L4-7 visibility using Cisco Network-based Application Recognition 2 (NBAR2).
Endpoint Security
Endpoint security solutions protect server and desktop endpoints from the latest threats caused by malicious network attacks. Endpoint security solutions can identify and prevent network attacks that are considered unknown or “day-zero”-type threats. Cisco ISE enables the network to enforce security policies on both wired and wireless devices seeking access to the network infrastructure. Cisco ISE protects data and prevents unauthorized network access by initially confirming a user’s identity before allowing access. Cisco ISE also provides posture assessment to reduce the risks associated with noncompliant devices by not allowing network access until the device is compliant with the configured policy.
Securing the Enterprise
The Cisco SAFE architecture provides the most comprehensive security systems for securing the enterprise network from the threats of today and tomorrow.
Each location in the enterprise network has unique security requirements because concerns are different and vary by location. In most cases, however, customizing network security solutions by functional area offers the best protection for the enterprise network.
The following sections examine some ways to use Cisco security solutions in the campus, data center, and enterprise edge.
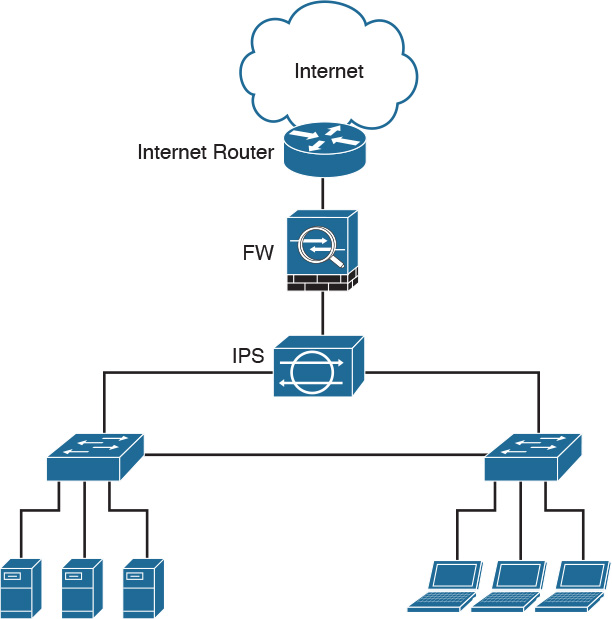
Implementing Security in the Campus
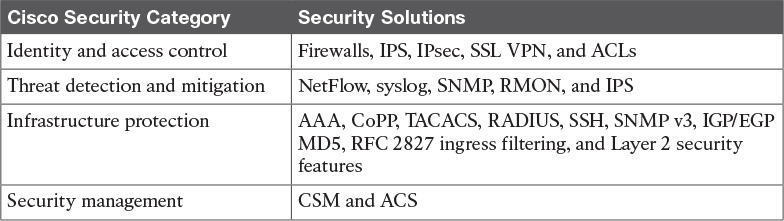
Security for the campus begins with remembering that you need to implement security throughout your network. Several technologies, protocols, solutions, and devices work together to provide the secure campus. Network security should be implemented in the core, distribution, and access layers and can be grouped into four broad categories, as described in Table 13-5.

Figure 13-9 illustrates an enterprise campus security scenario and shows where security technologies, protocols, and mechanisms can be deployed in the enterprise campus.
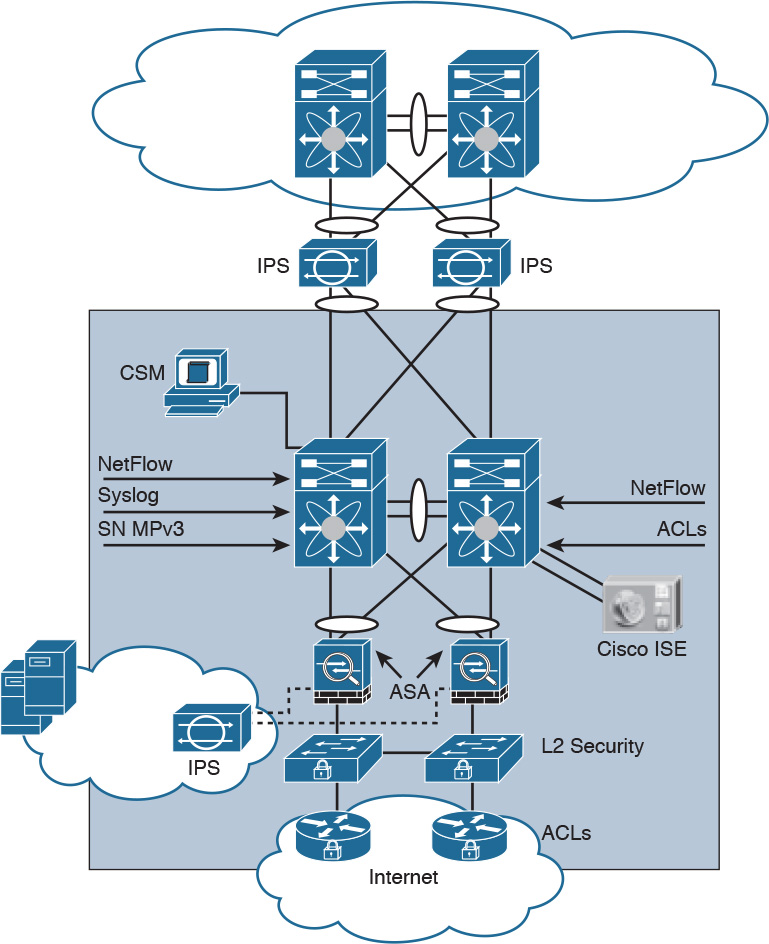
Implementing Security in the Data Center
The enterprise data center hosts critical servers and applications for the main campus and the branch offices. Many of the servers require high availability because of the importance of the information and the high volume of users they serve. Several of the servers may contain sensitive information that is crucial to the business and therefore cannot become compromised. Therefore, it needs to be highly secured. Network performance is another area that is critically important, which can limit the choice of protection mechanisms and technologies. Here are some of the risks inherent with enterprise data centers:
![]() Compromised applications and unauthorized access to critical information
Compromised applications and unauthorized access to critical information
![]() Exploiting different servers in the business by launching an attack from the compromised servers
Exploiting different servers in the business by launching an attack from the compromised servers
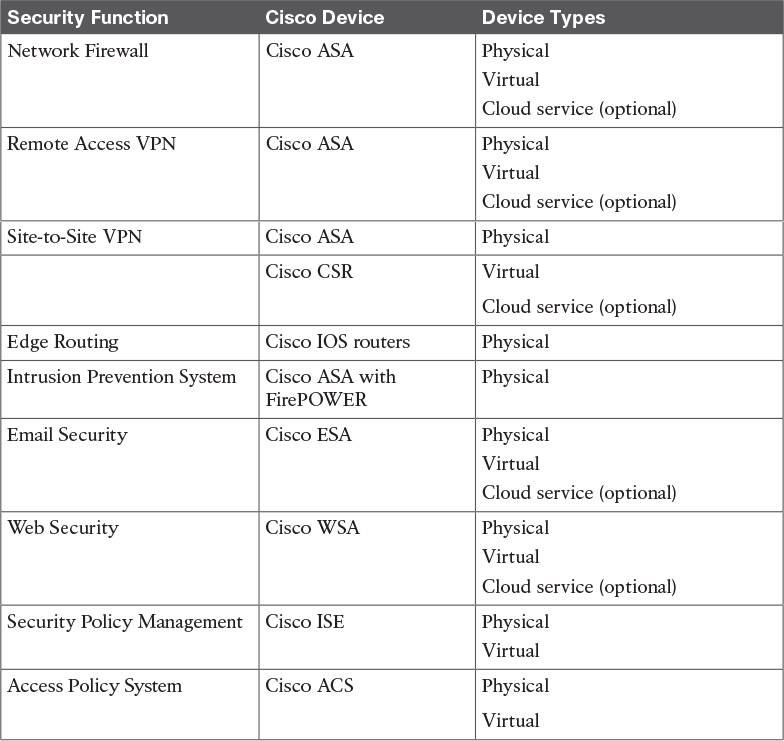
To provide adequate security protection, organizations can implement the network security solutions described in Table 13-6.
Figure 13-10 illustrates an enterprise data center security scenario and shows where security technologies, protocols, and mechanisms can be deployed in the enterprise data center.
Implementing Security in the Enterprise Edge
The enterprise edge provides connectivity to other parts of your network over insecure public networks. It is important to consider the available security options when transferring data between locations over Internet transports.
When you’re selecting devices for the enterprise edge, design choices need to be factored in for levels of granularity of services per device. There are choices between all-in-one devices and dedicated device-per-service models. The all-in-one devices can simplify management and lower cost, but may lack some advanced features and increase the risk of exposure. The dedicated device per service, on the other hand, can enable increased levels of performance and security overall, but can add in more CAPEX and OPEX. Device types available include physical appliances, virtual appliance, or a cloud-based service for most of the security devices.
Integrated multiple services on Cisco routers and Cisco ASAs are as follows:
![]() Cisco routers: Provide VRFs to enable isolation at the router layer and can be stitched together over Layer 3 hops in the network.
Cisco routers: Provide VRFs to enable isolation at the router layer and can be stitched together over Layer 3 hops in the network.
![]() Cisco ASAs: Feature virtual contexts that allow multiple firewall instances to be run on the same hardware; however, not all features are available in context mode.
Cisco ASAs: Feature virtual contexts that allow multiple firewall instances to be run on the same hardware; however, not all features are available in context mode.
The design choices need to consider business factors such as security and performance characteristics, security risks to the business, and cost when determining the appropriate solution. There may be different levels of security available when evaluating the use of a public cloud service versus an on-premises private cloud option. Performance aspects need to be considered regarding the use of virtual workloads with dependencies on underlying server hardware or physical appliances with known performance characteristics. In addition, upgrades to virtual workloads are software- and license-based, whereas physical appliances require new purchases along with the install of new hardware and licensing. The virtualization layer can also add in redundancy for the virtual appliances without the typical cost of additional hardware. Security risks for cloud services are normally higher than with on-premises private cloud-based options. Then there is the cost evaluation for CAPEX and OPEX for the security solution.
Table 13-7 lists the device components with the device types of physical, virtual, or cloud service if the service provider has the offering available.

Keep in mind the following potential risk areas when moving data between locations:
![]() Attackers obtain access to the network and compromise the confidentiality and integrity of sensitive information with eavesdropping or data manipulation.
Attackers obtain access to the network and compromise the confidentiality and integrity of sensitive information with eavesdropping or data manipulation.
![]() Misconfiguration of the enterprise edge devices could cause inappropriate device configurations and unwanted connectivity.
Misconfiguration of the enterprise edge devices could cause inappropriate device configurations and unwanted connectivity.
To provide adequate security protection between locations, organizations can implement the security solutions described in Table 13-8.

Figure 13-11 illustrates the use of enterprise edge and where security technologies, protocols, and mechanisms can be deployed in the enterprise edge.
References and Recommended Readings
The Cisco ASA 5500 as a Superior Firewall Solution, www.cisco.com/c/en/us/products/collateral/security/asa-5500-series-next-generation-firewalls/prod_white_paper0900aecd8058ec85.html.
Cisco SAFE Solution Overview, www.cisco.com/en/US/docs/solutions/Enterprise/Security/SAFESolOver.html.
SAFE Poster, www.cisco.com/c/dam/en/us/solutions/collateral/enterprise/design-zone-security/safe-poster-components.pdf.
Module 4 (Enterprise Network Design), Designing for Cisco Internetwork Solution Course (DESGN) 3.0.
Cisco Security Control Framework (SCF) Model, www.cisco.com/en/US/docs/solutions/Enterprise/Security/CiscoSCF.html.
RFC 2827: Network Ingress Filtering: Defeating Denial of Service Attacks Which Employ IP Source Address Spoofing, www.faqs.org/rfcs/rfc2827.html.
Cisco Identity Services Engine Data Sheet, www.cisco.com/c/en/us/products/collateral/security/identity-services-engine/data_sheet_c78-656174.html.
Exam Preparation Tasks
Review All Key Topics
Review the most important topics in the chapter, noted with the Key Topic icon in the outer margin of the page. Table 13-9 lists a reference of these key topics and the page numbers on which each is found.

Complete Tables and Lists from Memory
Print a copy of Appendix D, “Memory Tables” (found on the book website), or at least the section for this chapter, and complete the tables and lists from memory. Appendix E, “Memory Tables Answer Key,” also on the website, includes completed tables and lists to check your work.
Define Key Terms
Define the following key terms from this chapter, and check your answers in the glossary:
Adaptive Security Appliance (ASA)
Integrated Services Router (ISR) G2
Cisco Identity-Based Network Services (IBNS)
Cisco Secure Access Control Server (ACS)
Cisco Adaptive Security Device Manager (ASDM)
Q&A
The answers to these questions appear in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes and Q&A Questions.” For more practice with exam format questions, use the exam engine on the CD.
1. What security device combines IOS firewall with VPN and IPS services?
a. ASA
b. ISR
c. Cisco Catalyst switches
d. IPS
2. Which of the following is a standards-based protocol for authenticating network clients?
a. Cisco ISE
b. PoE
c. 802.1X
d. CSM
3. The Cisco ________ is an integrated solution led by Cisco that incorporates the network infrastructure and third-party software to impose security policy on attached endpoints.
a. ASA
b. CSM
c. ISR
d. ISE
4. What software-based solution can network security administrators use to configure standalone ASA firewalls? (Select the best answer.)
a. ISR
b. Cisco ISE
c. ASDM
d. IDM
5. Cisco IOS Trust and Identity has a set of services that includes which of the following? (Select all that apply.)
a. 802.1X
b. SSL
c. AAA
d. ASDM
6. Cisco IOS ______________ offers data encryption at the IP packet level using a set of standards-based protocols.
a. IPS
b. IPsec
c. L2TP
d. L2F
7. What provides hardware VPN encryption for terminating a large number of VPN tunnels for ISRs?
a. ASA SM
b. WebVPN Services Module
c. Network Analysis Module 3
d. High-Performance AIM
8. What are two ways to enhance VPN performance on Cisco ISR G2s?
a. SSL Network Module
b. IDS Network Module
c. Built-In Hardware VPN Acceleration
d. High-Performance AIM
9. Which Cisco security solution can prevent noncompliant devices from accessing the network until they are compliant?
a. IPsec
b. ASA Service module
c. ACS
d. Cisco ISE
10. Which of the following service modules do Cisco Catalyst 6500 switches support? (Select all that apply.)
a. ASA SM
b. Network Analysis Module 3
c. High-Performance AIM
d. FirePOWER IPS
11. What provides packet capture capabilities and visibility into all layers of network data flows?
a. Network Analysis Module 3
b. ASA Services Module
c. WebVPN Services Module
d. IPsec VPN SPA
12. Which of the following are identity and access control protocols and mechanisms? (Select all that apply.)
a. 802.1X
b. ACLs
d. NetFlow
13. Which two of the following are Cisco security management tools?
a. CSM
b. IDS module
c. ACS
d. Cisco ISE
14. True or false: NetFlow is used for threat detection and mitigation.
15. True or false: Cisco ASAs, ASA SM, and IOS firewall are part of infection containment.
16. What IOS feature offers inline deep packet inspection to successfully diminish a wide range of network attacks?
a. IOS SSH
b. IOS SSL VPN
c. IOS IPsec
d. IOS IPS
17. The Cisco ___________ IPS Module for ASA can identify, analyze, and block unwanted traffic from flowing on the network.
18. What provides centralized control for administrative access to Cisco devices and security applications?
a. CSM
b. ACS
c. NetFlow
d. ASDM
19. Which of the following are PINs in the Cisco SAFE architecture?
a. Core
b. Data Center
c. Telecommuter
d. Distribution
20. Match each protocol, mechanism, or feature with its security grouping:
i. CSM
ii. IGP/EGP MD5
iii. NetFlow
iv. Cisco ISE
a. Identity and access control
b. Threat detection and mitigation
c. Infrastructure protection
d. Security management