Chapter 15. Network Management Protocols
This chapter covers the following subjects:
Simple Network Management Protocol
Other Network Management Protocols
This chapter introduces the following network management protocols and components: Simple Network Management Protocol (SNMP), Management Information Base (MIB), Remote Monitoring (RMON) protocol, Cisco Discovery Protocol (CDP), and the use of NetFlow and system logging (syslog).
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz helps you identify your strengths and deficiencies in this chapter’s topics.
The ten-question quiz, derived from the major sections in the “Foundation Topics” portion of the chapter, helps you determine how to spend your limited study time.
Table 15-1 outlines the major topics discussed in this chapter and the “Do I Know This Already?” quiz questions that correspond to those topics.
1. Which version of SNMP introduces security extensions for authentication and encryption?
a. SNMPv1
b. SNMPv2
c. SNMPv3
d. SNMPv4
2. SNMP runs over which protocol?
a. TCP
b. UDP
c. IP
d. MIB
3. Which SNMP component contains an agent?
a. Managed device
b. Agent
c. NMS manager
d. MIB
4. Which SNMP component is a collection of information that is stored on the local agent?
a. Managed device
b. Agent
c. NMS manager
d. MIB
5. CDP is an acronym for which Cisco function?
a. Collection Device Protocol
b. Cisco Device Protocol
c. Campus Discovery Protocol
d. Cisco Discovery Protocol
6. Which SNMP operation obtains full table information from an agent?
a. Get
b. GetNext
c. GetBulk
d. Inform
7. RMON1 provides information at what levels of the OSI model?
a. Data link and physical
b. Network, data link, physical
c. Transport and network
d. Application to network
8. Which of the following is not an SNMP operation?
a. Get
b. Community
c. Set
d. Trap
9. Which solution gathers information that can be used for accounting and billing applications?
a. RMON
b. NetFlow
c. CDP
d. Syslog
10. What is CDP?
a. Client/server protocol
b. Hello-based protocol
c. Network management agent
d. Request-response protocol
Foundation Topics
After a new network is designed, installed, and configured, it must be managed by the operations team. Network management tools are used to gather operating statistics and to manage devices. Statistics are gathered on WAN bandwidth utilization, router CPU and memory utilization, and interface counters. Configuration changes are also made through network management tools such as Cisco Prime. The ISO defines five types of network management processes that are commonly known as FCAPS. These processes are as follows:
![]() Fault management: Refers to detecting and correcting network fault problems
Fault management: Refers to detecting and correcting network fault problems
![]() Configuration management: Refers to baselining, modifying, and tracking configuration changes
Configuration management: Refers to baselining, modifying, and tracking configuration changes
![]() Accounting management: Refers to keeping track of circuits for billing of services
Accounting management: Refers to keeping track of circuits for billing of services
![]() Performance management: Measures the network’s effectiveness at delivering packets
Performance management: Measures the network’s effectiveness at delivering packets
![]() Security management: Tracks the authentication and authorization information
Security management: Tracks the authentication and authorization information
Network management is supported by the elements listed in Table 15-2.

The protocols and tools described in this chapter perform some of these functions. SNMP is the underlying protocol used for network management. Agents are configured in managed devices (routers) that allow the NMS to manage the device. RMON is used for advanced monitoring of routers and switches. CDP is a Cisco proprietary protocol that allows the discovery of Cisco devices. NetFlow is a network monitoring solution that allows for greater scalability than RMON. Syslog allows system messages and error events to be gathered for review.
Simple Network Management Protocol

Simple Network Management Protocol (SNMP) is an IP application layer protocol that has become the standard for the exchange of management information between network devices. SNMP was initially described in RFC 1157. It is a simple solution that requires little code to implement, which allows vendors to build SNMP agents on their products.
SNMP runs over User Datagram Protocol (UDP) and therefore does not inherently provide for sequencing and acknowledgment of packets, but it still reduces the amount of overhead used for management information.
SNMP Components
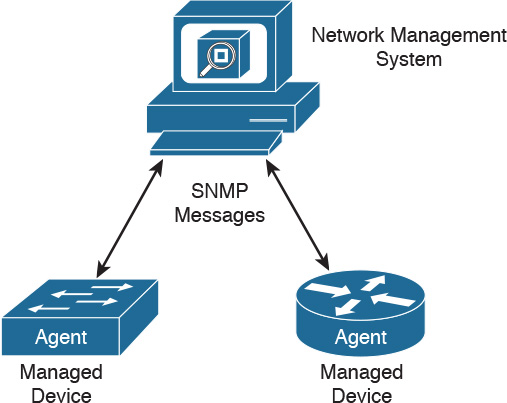
SNMP has three network-managed components:
![]() The managed devices
The managed devices
![]() The agent that resides on the managed device
The agent that resides on the managed device
![]() The NMS
The NMS
Figure 15-1 shows the relationship between these components.
A managed device is a router or LAN switch or any other device that contains an SNMP agent. These devices collect and store management information and make this information available to the NMS. SNMP community strings (passwords) are configured on routers and switches to allow for SNMP management.
The agent is the network management software that resides in the managed device. The agent gathers the information and puts it in SNMP format. It responds to the manager’s request for information and also generates traps.
The NMS has applications that are used to monitor and configure managed devices. It is also known as the manager. The NMS provides the bulk of the processing resources used for network management. It polls agents on the network and correlates and displays the management information.
MIB
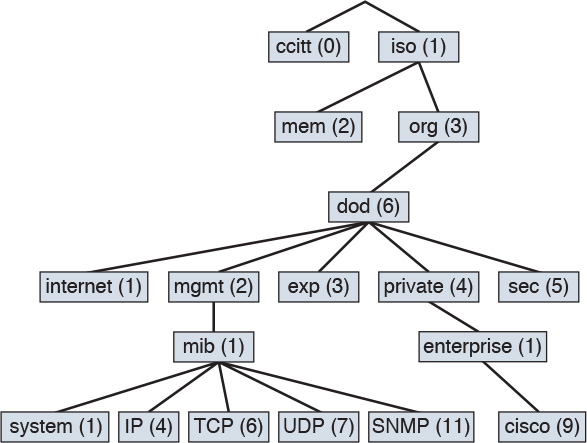
A Management Information Base (MIB) is a collection of information that is stored on the local agent of the managed device. MIBs are organized hierarchically and are accessed by the NMS. MIBs are databases of objects organized in a tree-like structure, with each branch containing similar objects. Each object has an object identifier (number) that uniquely identifies the managed object of the MIB hierarchy. Read and write community strings are used to control access to MIB information.
The top-level MIB object IDs belong to different standards organizations, and lower-level object IDs are allocated to associated organizations. Standard MIBs are defined by RFCs. Vendors define private branches that include managed objects for their products. Figure 15-2 shows a portion of the MIB tree structure. RFC 1213 describes the MIBs for TCP/IP. Cisco defines the MIBs under the Cisco head object. For example, a Cisco MIB can be uniquely identified by either the object name, iso.org.dod.private.enterprise.cisco, or the equivalent object descriptor, 1.3.6.1.4.1.9.
Each individual manageable feature in the MIB is called an MIB variable. The MIB module is a document that describes each manageable feature that is contained in an agent. The MIB module is written in Abstract Syntax Notation 1 (ASN.1). Three ASN.1 data types are required: name, syntax, and encoding. The name serves as the object identifier. The syntax defines the object’s data type (integer or string). The encoding data describes how information associated with a managed object is formatted as a series of data items for transmission on the network. Some examples of standard managed objects that can be obtained from the MIB tree follow:
![]() Interfaces
Interfaces
![]() Buffers
Buffers
![]() Memory
Memory
![]() Standard protocols
Standard protocols
From the Cisco private tree, you can obtain the following additional information:
![]() Small, medium, large buffers
Small, medium, large buffers
![]() Primary and secondary memory
Primary and secondary memory
![]() Proprietary protocols (Enhanced Interior Gateway Routing Protocol [EIGRP]), for example)
Proprietary protocols (Enhanced Interior Gateway Routing Protocol [EIGRP]), for example)
You can find more specific information about Cisco MIBs at www.cisco.com/public/sw-center/netmgmt/cmtk/mibs.shtml.
SNMP Message Versions
SNMPv1 was initially defined by RFC 1157. Since then, SNMP has evolved with a second and third version, each adding new message types. The CCDA should understand each message type and the version associated with each.
SNMPv1
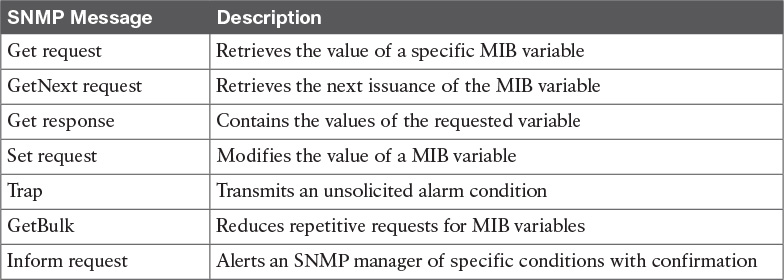
SNMPv1 is defined by RFC 1157. It is a simple request-and-response protocol. The NMS manager issues a request, and managed devices return responses. The data types are limited to 32-bit values. SNMPv1 uses four protocol operations, with five message types to carry out the communication:
![]() Get request: Retrieves the value of a specific MIB variable.
Get request: Retrieves the value of a specific MIB variable.
![]() GetNext request: Retrieves the next instance of the MIB variable.
GetNext request: Retrieves the next instance of the MIB variable.
![]() Get response: Contains the values of the requested variable.
Get response: Contains the values of the requested variable.
![]() Set request: This is a request from the manager to the agent to set a MIB variable. It can be used to modify the agent’s configuration.
Set request: This is a request from the manager to the agent to set a MIB variable. It can be used to modify the agent’s configuration.
![]() Trap: Transmits an unsolicited alarm condition.
Trap: Transmits an unsolicited alarm condition.
Figure 15-3 shows the SNMPv1 message types.
The NMS manager uses the Get operation to retrieve the value-specific MIB variable from an agent. The GetNext operation is used to retrieve the next object instance in a table or list within an agent. The Get Response contains the value of the requested variable.
The NMS manager uses the Set operation to set values of the object instance within an agent. For example, the Set operation can be used to set an IP address on an interface or to bring an interface up or down. Agents use the Trap operation to inform the NMS manager of a significant alarm event. For example, a trap is generated when a WAN circuit goes down.
SNMPv2
SNMPv2 is an evolution of the initial SNMPv1 and is defined in RFCs 1901 and 1902. SNMPv2 offers improvements to SNMPv1, including additional protocol operations. The Get, GetNext, and Set operations used in SNMPv1 are exactly the same as those used in SNMPv2. The SNMP Trap operation serves the same function as in SNMPv1, but it uses a different message format.
SNMPv2 defines two new protocol operations:
![]() GetBulk: Reduces repetitive requests for MIB variables
GetBulk: Reduces repetitive requests for MIB variables
![]() Inform request: Alerts an SNMP manager of specific conditions with confirmation
Inform request: Alerts an SNMP manager of specific conditions with confirmation
The NMS manager uses the GetBulk operation to retrieve large blocks of data, such as multiple rows in a table. This is more efficient than repeating GetNext commands. If the agent responding to the GetBulk operation cannot provide values for all the variables in a list, it provides partial results. The Inform operation allows one NMS manager to send trap information to other NMS managers and to receive information. Another improvement is that data type values can be 64 bits.
Table 15-3 summarizes SNMP message types.

SNMPv3
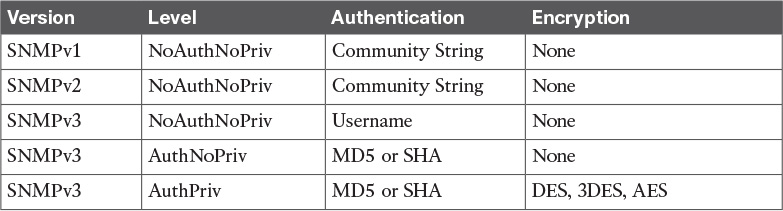
SNMPv3 was developed to correct several deficiencies in the earlier versions of SNMP, security being a primary reason. SNMPv3 is defined in RFCs 3410 through 3415. SNMPv3 provides authentication and privacy via usernames and access control by using key management. Security levels are implemented to determine which devices a user can read, write, or create. SNMPv3 also verifies each message to ensure that it has not been modified during transmission. SNMPv3 removes the use of community-based authentication strings, which were sent in cleartext over the network. It is recommended that SNMPv1 and SNMPv2 be used only for read-only access, whereas SNMPv3 be used with read-write access.
SNMPv3 introduces three levels of security:
![]() noAuthNoPriv: No authentication and no encryption
noAuthNoPriv: No authentication and no encryption
![]() authNoPriv: Authentication and no encryption
authNoPriv: Authentication and no encryption
![]() authPriv: Authentication and encryption
authPriv: Authentication and encryption
The noAuthNoPriv level provides no authentication and no privacy (encryption). At the authNoPriv level, authentication is provided but not encryption. The authPriv level provides authentication and encryption.
Authentication for SNMPv3 is based on Hash-based Message Authentication Code–Message Digest 5 (HMAC-MD5) or HMAC – Secure Hash (HMAC-SHA) algorithms. The Cipher Block Chaining–Data Encryption Standard (CBC-DES) standard is used for encryption.
Table 15-4 summarizes SNMP security levels.

Other Network Management Technologies
This section covers RMON, NetFlow, CDP, LLDP, and syslog technologies used to gather network information.
RMON

RMON is a standard monitoring specification that enables network monitoring devices and console systems to exchange network monitoring data. RMON provides more information than SNMP, but more sophisticated data collection devices (network probes) are needed. RMON looks at MAC-layer data and provides aggregate information on the statistics and LAN traffic.
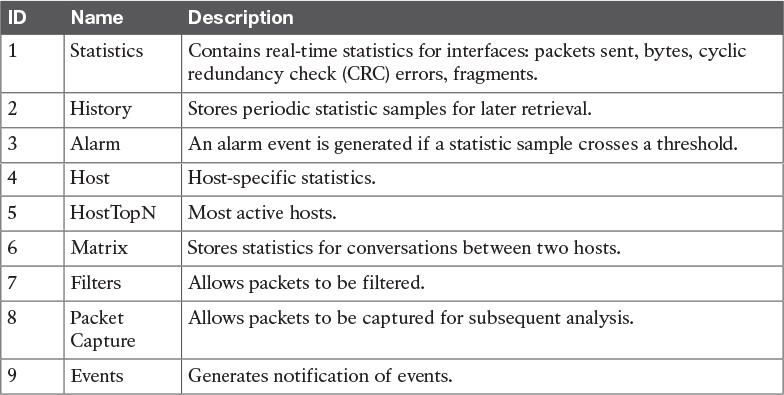
Enterprise networks deploy network probes on several network segments; these probes report back to the RMON console. RMON allows network statistics to be collected even if a failure occurs between the probe and the RMON console. RMON1 is defined by RFCs 1757 and 2819, and additions for RMON2 are defined by RFC 2021.
The RMON MIB is located at iso.org.dod.internet.mgt.mib.rmon or by the equivalent object descriptor, 1.3.6.1.2.1.16. RMON1 defines nine monitoring groups; each group provides specific sets of data. One more group is defined for Token Ring. Each group is optional, so vendors do not need to support all the groups in the MIB. Table 15-5 shows the RMON1 groups.
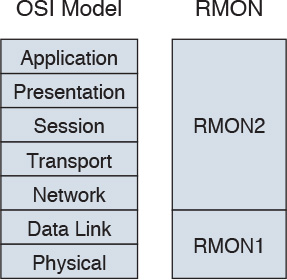
RMON2
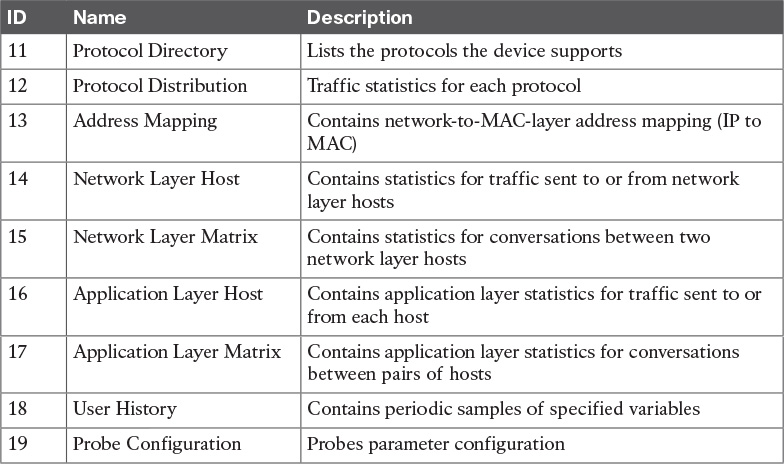
RMON1 is focused on the data link and physical layers of the OSI model. As shown in Figure 15-4, RMON2 provides an extension for monitoring upper-layer protocols.
Defined by RFC 2021, RMON2 extends the RMON group with the MIB groups listed in Table 15-6.
NetFlow

Cisco NetFlow allows the tracking of IP flows as they are passed through routers and multilayer switches. An IP flow is a set of IP packets within a specific timeslot that share a number of properties, such as the same source address, destination address, type of service, and protocol number. NetFlow information is forwarded to a network data analyzer, network planning tools, RMON applications, or accounting and billing applications. NetFlow allows for network planning, traffic engineering, usage-based network billing, accounting, Denial of Service monitoring capabilities, and application monitoring. One big benefit is that NetFlow provides the necessary data for billing of network usage. The most recent version of NetFlow is NetFlow Version 9, which is defined in RFC 3954. The NetFlow protocol itself has been superseded by Internet Protocol Flow Information eXport (IPFIX). Based on the NetFlow Version 9 implementation, IPFIX is on the IETF standards track with RFCs 7011 and 7015.
As shown in Figure 15-5, NetFlow consists of three major components:
![]() NetFlow accounting: Collects IP data flows entering router or switch interfaces and prepares data for export. It enables the accumulation of data on flows with unique characteristics, such as IP addresses, application, and class of service (CoS).
NetFlow accounting: Collects IP data flows entering router or switch interfaces and prepares data for export. It enables the accumulation of data on flows with unique characteristics, such as IP addresses, application, and class of service (CoS).
![]() Flow collector engines: Captures exported data from multiple routers and filters and aggregates the data according to customer policies, and then stores this summarized or aggregated data. Examples of collectors are Cisco NetFlow Collector, SolarWinds, and CA NetQoS.
Flow collector engines: Captures exported data from multiple routers and filters and aggregates the data according to customer policies, and then stores this summarized or aggregated data. Examples of collectors are Cisco NetFlow Collector, SolarWinds, and CA NetQoS.
![]() Network data analyzers: Displays a graphical user interface (GUI) and analyzes NetFlow data collected from flow collector files. This allows users to complete near-real-time visualization or trending analysis of recorded and aggregated flow data. Users can specify the router and aggregation scheme and the desired time interval.
Network data analyzers: Displays a graphical user interface (GUI) and analyzes NetFlow data collected from flow collector files. This allows users to complete near-real-time visualization or trending analysis of recorded and aggregated flow data. Users can specify the router and aggregation scheme and the desired time interval.
The benefits of using NetFlow include the following:
![]() Ability to obtain detailed information with minimal impact to the network devices
Ability to obtain detailed information with minimal impact to the network devices
![]() Ability to customize the data captures for each interface
Ability to customize the data captures for each interface
![]() Ability to include data timestamping across a large number of devices
Ability to include data timestamping across a large number of devices
![]() Ability to meter network traffic providing data for billing based on network usage
Ability to meter network traffic providing data for billing based on network usage
![]() Used to detect and mitigate threats
Used to detect and mitigate threats
Routers and switches are the network accounting devices that gather the statistics. These devices aggregate data and export the information. Each unidirectional network flow is identified by both source and destination IP addresses and transport layer port numbers. NetFlow can also identify flows based on IP protocol number, type of service, and input interface. NetFlow data records contain the following information:
![]() Source and destination IP address
Source and destination IP address
![]() Source and destination TCP/UDP ports
Source and destination TCP/UDP ports
![]() Type of service (ToS)
Type of service (ToS)
![]() Packet and byte counts
Packet and byte counts
![]() Start and end timestamps
Start and end timestamps
![]() Input and output interface numbers
Input and output interface numbers
![]() TCP flags and encapsulated protocol (TCP/UDP)
TCP flags and encapsulated protocol (TCP/UDP)
![]() Routing information (next-hop address, source and destination autonomous system number, destination prefix mask)
Routing information (next-hop address, source and destination autonomous system number, destination prefix mask)
![]() Data analyzers
Data analyzers
The NetFlow export or transport mechanism sends the NetFlow data to a collection engine or network management collector. Flow collector engines perform data collection and filtering. They aggregate data from several devices and store the information. Different NetFlow data analyzers can be used based on the intended purpose. NetFlow data can be analyzed for the following key applications:
![]() Accounting and billing: Used by service providers for charging based on bandwidth and application usage and quality of service (QoS).
Accounting and billing: Used by service providers for charging based on bandwidth and application usage and quality of service (QoS).
![]() Network planning and analysis: Link and router capacity.
Network planning and analysis: Link and router capacity.
![]() Network and security monitoring: Visualize real-time traffic patterns.
Network and security monitoring: Visualize real-time traffic patterns.
![]() Application monitoring and profiling: Time-based view of application usage.
Application monitoring and profiling: Time-based view of application usage.
![]() User monitoring and profiling: Identifies customer and user network utilization and resource application.
User monitoring and profiling: Identifies customer and user network utilization and resource application.
![]() NetFlow data warehousing and mining: NetFlow data can be warehoused for later retrieval and analysis.
NetFlow data warehousing and mining: NetFlow data can be warehoused for later retrieval and analysis.
Looking ahead, Cisco has introduced Flexible NetFlow as the next generation in flow technology. Flexible NetFlow has many benefits beyond the Cisco traditional NetFlow functionality available for years in Cisco hardware and software.
The key advantages to using Flexible NetFlow are as follows:
![]() Flexibility, scalability of flow data beyond traditional NetFlow
Flexibility, scalability of flow data beyond traditional NetFlow
![]() The ability to monitor a wider range of packet information to produce new information about network behavior not available previously
The ability to monitor a wider range of packet information to produce new information about network behavior not available previously
![]() Enhanced network anomaly and security detection
Enhanced network anomaly and security detection
![]() User configurable flow information to perform customized traffic identification and the ability to focus and monitor specific network behavior
User configurable flow information to perform customized traffic identification and the ability to focus and monitor specific network behavior
![]() Convergence of multiple accounting technologies into one accounting mechanism
Convergence of multiple accounting technologies into one accounting mechanism
Flexible NetFlow is an integral part of Cisco IOS Software that collects and measures data, allowing all routers or switches in the network to become a source of telemetry and a monitoring device. Flexible NetFlow allows extremely granular and accurate traffic measurements and high-level aggregated traffic collection. Because it is part of Cisco IOS Software, Flexible NetFlow enables Cisco product-based networks to perform traffic flow analysis without external probes being purchased, thus making traffic analysis economical for large IP networks.
Flexible NetFlow can track the following packet information for Layer 2, IPv4, and IPv6 flows:
![]() Source and destination MAC addresses
Source and destination MAC addresses
![]() Source and destination IPv4 or IPv6 addresses
Source and destination IPv4 or IPv6 addresses
![]() Source and destination TCP/User Datagram Protocol (UDP) ports
Source and destination TCP/User Datagram Protocol (UDP) ports
![]() Type of service (ToS)
Type of service (ToS)
![]() DSCP
DSCP
![]() Packet and byte counts
Packet and byte counts
![]() Flow timestamps
Flow timestamps
![]() Input and output interface numbers
Input and output interface numbers
![]() TCP flags and encapsulated protocol (TCP/UDP) and individual TCP flags
TCP flags and encapsulated protocol (TCP/UDP) and individual TCP flags
![]() Sections of packets for deep packet inspection
Sections of packets for deep packet inspection
![]() All fields in the IPv4 header, including IP-ID, TTL, and others
All fields in the IPv4 header, including IP-ID, TTL, and others
![]() All fields in the IPv6 header, including Flow Label, Option Header, and others
All fields in the IPv6 header, including Flow Label, Option Header, and others
![]() Routing information such as next-hop address, source autonomous system (AS) number, destination AS number, source prefix mask, destination prefix mask, BGP Next Hop, and BGP Policy Accounting traffic index
Routing information such as next-hop address, source autonomous system (AS) number, destination AS number, source prefix mask, destination prefix mask, BGP Next Hop, and BGP Policy Accounting traffic index
NetFlow Compared to RMON and SNMP
NetFlow enables you to gather more statistical information than RMON with fewer resources. It provides greater detail of the collected data, with date- and timestamping. NetFlow has greater scalability and does not require network probes. As compared with SNMP, NetFlow reports on traffic statistics and is push based, whereas SNMP reports primarily on device statistics and is poll based.
NetFlow can be configured on individual Layer 3 interfaces on routers and Layer 3 switches. NetFlow provides detailed information on the following:
![]() Source and destination IP addresses
Source and destination IP addresses
![]() Source and destination interface identifiers
Source and destination interface identifiers
![]() TCP/UDP source and destination port numbers
TCP/UDP source and destination port numbers
![]() Number of bytes and packets per flow
Number of bytes and packets per flow
![]() Source and destination autonomous system numbers
Source and destination autonomous system numbers
![]() IP type of service (ToS)
IP type of service (ToS)
CDP

Cisco Discovery Protocol (CDP) is a Cisco-proprietary protocol that can be used to discover only Cisco network devices. CDP is media and protocol independent, so it works over Ethernet, Frame Relay, ATM, and other media. The requirement is that the media support Subnetwork Access Protocol (SNAP) encapsulation. CDP runs at the data link layer of the OSI model. CDP uses hello messages; packets are exchanged between neighbors, but CDP information is not forwarded. In addition to routers and switches, IP phones and Cisco Unified Communication Manager (CUCM) servers also advertise CDP information.
Being protocol and media independent is CDP’s biggest advantage over other network management technologies. CDP provides key information about neighbors, including platforms, capabilities, and IP addresses, which is significant for network discovery. It is useful when SNMP community strings are unknown when performing a network discovery.
When displaying CDP neighbors, you can obtain the following information:
![]() Local interface: Local interface that is connected to the discovered neighbor
Local interface: Local interface that is connected to the discovered neighbor
![]() Device ID: Name of the neighbor device and MAC address or serial number
Device ID: Name of the neighbor device and MAC address or serial number
![]() Device IP address: IP address of the neighbor
Device IP address: IP address of the neighbor
![]() Hold time: How long (seconds) to hold the neighbor information
Hold time: How long (seconds) to hold the neighbor information
![]() Device capabilities: Type of device discovered: router, switch, transparent bridge, host, IGMP, or repeater
Device capabilities: Type of device discovered: router, switch, transparent bridge, host, IGMP, or repeater
![]() Version: IOS or switch OS version
Version: IOS or switch OS version
![]() Platform: Router or switch model number
Platform: Router or switch model number
![]() Port ID: Interface of the neighboring device
Port ID: Interface of the neighboring device
Network management devices can obtain CDP information for data gathering. CDP should be disabled on untrusted interfaces, such as those that face the Internet, third-party networks, or other secure networks. CDP works only on Cisco devices.
Note
Disable CDP on interfaces for which you do not want devices to be discovered, such as Internet connections.
LLDP

The Link Layer Discovery Protocol (LLDP), defined in the IEEE 802.1AB (LLDP) specification, is an option of discovering network devices in multivendor networks. LLDP performs functions similar to CDP. With LLDP, devices send information at a fixed interval from each of their interfaces in the form of an Ethernet frame with an Ethertype of 0x88CC. The information shared includes the following:
![]() System name and description
System name and description
![]() Port name and description
Port name and description
![]() VLAN name
VLAN name
![]() IP management address
IP management address
![]() System capabilities
System capabilities
![]() MAC/PHY layer information
MAC/PHY layer information
![]() Link aggregation
Link aggregation
Syslog
The syslog protocol is defined in RFC 3164. Syslog transmits event notification messages over the network. Network devices send the event messages to an event server for aggregation. Network devices include routers, servers, switches, firewalls, and network appliances. Syslog operates over UDP, so messages are not sequenced or acknowledged. The syslog messages are also stored on the device that generates the message and can be viewed locally.
Syslog messages are generated in many broad areas. These areas are called facilities. Cisco IOS has more than 500 facilities. Common facilities include
![]() IP
IP
![]() CDP
CDP
![]() OSPF
OSPF
![]() TCP
TCP
![]() Interface
Interface
![]() IPsec
IPsec
![]() SYS operating system
SYS operating system
![]() Security/authorization
Security/authorization
![]() Spanning Tree Protocol (STP)
Spanning Tree Protocol (STP)
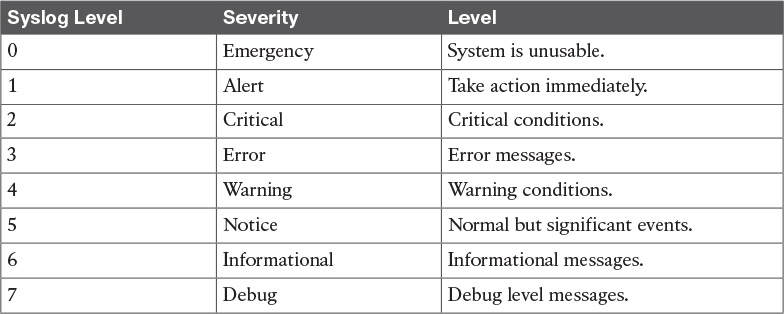
Each syslog message has a level. The syslog level determines the event’s criticality. Lower syslog levels are more important. Table 15-7 lists the syslog levels.

Common syslog messages are interface up and down events. Access lists can also be configured on routers and switches to generate syslog messages when a match occurs. Each syslog message includes a timestamp, level, and facility. Syslog messages have the following format:
mm/dd/yy:hh/mm/ss:FACILITY-LEVEL-mnemonic:description
Syslog messages can create large amounts of network bandwidth. It is important to enable only syslog facilities and levels that are of particular importance.
Table 15-8 summarizes some of the protocols just covered in this section.

References and Recommended Reading
NetFlow Performance Analysis, www.cisco.com/en/US/tech/tk812/technologies_white_paper0900aecd802a0eb9.shtml.
NetFlow Version 9, www.cisco.com/en/US/products/ps6645/products_ios_protocol_option_home.html.
Cisco IOS Netflow Data Sheet, http://www.cisco.com/c/en/us/products/collateral/ios-nx-os-software/ios-netflow/product_data_sheet0900aecd80173f71.html.
Tutorial on Link Layer Discovery Protocol, http://www.eetimes.com/document.asp?doc_id=1272069.
MIBs Supported by Product, http://tools.cisco.com/ITDIT/MIBS/servlet/index.
RFC 1157: A Simple Network Management Protocol (SNMP).
RFC 1441: Introduction to Version 2 of the Internet-Standard Network Management Framework.
RFC 1757: Remote Network Monitoring Management Information Base.
RFC 1901: Introduction to Community-Based SNMPv2.
RFC 1902: Structure of Management Information for Version 2 of the Simple Network Management Protocol (SNMPv2).
RFC 2021: Remote Network Monitoring Management Information Base Version 2 Using SMIv2.
RFC 2576: Coexistence Between Version 1, Version 2, and Version 3 of the Internet Standard Network Management Framework.
RFC 3164: The BSD Syslog Protocol.
RFC 3410: Introduction and Applicability Statements for Internet Standard Management Framework.
RFC 3411: An Architecture for Describing Simple Network Management Protocol (SNMP) Management Frameworks.
RFC 3412: Message Processing and Dispatching for the Simple Network Management Protocol (SNMP).
RFC 3414: User-Based Security Model (USM) for Version 3 of the Simple Network Management Protocol (SNMPv3).
RFC 3415: View-Based Access Control Model (VACM) for the Simple Network Management Protocol (SNMP).
RFC 3416: Protocol Operations for SNMPv2.
RFC 3418: Management Information Base for SNMPv2.
RFC 3954: Cisco Systems NetFlow Services Export Version 9.
RFC 5103: Bidirectional Flow Export Using IP Flow Information Export (IPFIX).
RFC 7011: Specification of the IP Flow Information Export (IPFIX) Protocol for the Exchange of Flow Information.
RFC 7015: Flow Aggregation for the IP Flow Information Export (IPFIX) Protocol.
Cisco IOS Flexible http://www.cisco.com/c/en/us/products/collateral/ios-nx-os-software/flexible-netflow/product_data_sheet0900aecd804b590b.html.
Exam Preparation Tasks
Review All Key Topics
Review the most important topics in the chapter, noted with the Key Topics icon in the outer margin of the page. Table 15-9 lists a reference of these key topics and the page numbers on which each is found.

Complete Tables and Lists from Memory
Print a copy of Appendix D, “Memory Tables” (found on the CD), or at least the section for this chapter, and complete the tables and lists from memory. Appendix E, “Memory Tables Answer Key,” also on the CD, includes completed tables and lists to check your work.
Define Key Terms
Define the following key terms from this chapter, and check your answers in the glossary:
Q&A
The answers to these questions appear in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes and Q&A Questions.” For more practice with exam format questions, use the exam engine on the CD.
1. What does the acronym FCAPS stand for?
2. CDP runs at what layer of the OSI model?
3. Syslog level 5 is what level of severity?
4. True or false: RMON provides more scalability than NetFlow.
5. True or false: NetFlow provides detailed information on the number of bytes and packets per conversation.
6. What information can be obtained from a neighbor using CDP?
7. What SNMP message is sent by an agent when an event occurs?
a. Get
b. Set
c. GetResponse
d. Trap
8. What SNMP message is sent to an agent to obtain an instance of an object?
a. Get
b. Set
c. GetResponse
d. Trap
9. What SNMP message is used to configure a managed device?
a. Get
b. Set
c. GetResponse
d. Trap
10. About how many facilities are available for syslog in Cisco routers?
a. 25
b. 100
c. 500
d. 1000
11. Which SNMPv3 level provides authentication with no encryption?
a. authPriv
b. authNoPriv
d. noauthPriv
12. What encryption standard does SNMPv3 use?
a. 3DES
b. CBC-DES
c. HMAC-MD5
d. MD5
13. Which technologies can you use to assess a network and create documentation? (Select two.)
a. RMON
b. MIB
c. CDP
d. NetFlow
14. Which of the following are true about CDP? (Select three.)
a. It uses UDP.
b. It is a data-link protocol.
c. It provides information on neighboring routers and switches.
d. It is media and protocol independent.
e. It uses syslog and RMON.
15. RMON2 provides information at what levels of the OSI model?
a. Data link and physical
b. Network, data link, and physical
c. Transport and network only
d. Network to application
16. Which network management technology operates over TCP?
a. SNMP
b. RMON
c. NetFlow
d. None of the above
17. Which statement is correct?
a. SNMPv1 uses GetBulk operations and 32-bit values.
b. SNMPv2 uses 32-bit values, and SNMPv3 uses 64-bit values.
c. SNMPv1 uses 32-bit values, and SNMPv2 uses 64-bit values.
d. SNMPv1 uses GetBulk operations, and SNMPv2 uses Inform operations.
18. Which SNMPv3 level provides authentication and privacy?
a. authPriv
b. authNoPriv
c. noAuthNoPriv
d. noauthPriv
19. Match the RMON group with its description.
i. Statistics
ii. Matrix
iii. Application-Layer Host
iv. Protocol Directory
a. Stores statistics for conversations between two hosts
b. Lists the protocols that the device supports
c. Contains real-time statistics for interfaces: packets sent, bytes, CRC errors, fragments
d. Contains application layer statistics for traffic sent to or from each host
20. What is the most critical syslog priority level?
a. 0
b. 1
c. 6
d. 7
21. Which management protocol will help a company concentrate on Layer 4 monitoring and gain information to assist in long-term trending analysis?
a. SNMPv3
b. RMON2
c. NetFlow
d. CDP
e. MIB
22. Which management protocol performs network traffic analysis?
a. SNMPv3
b. RMON2
c. NetFlow
d. CDP
e. MIB
23. What virtual information store is used by SNMP?
a. SNMPv3
b. RMON2
c. ASN.1
d. CDP
e. MIB
24. What standard language is used by SNMP?
a. SNMPv3
b. RMON2
c. ASN.1
d. CDP
e. MIB
25. Which SNMPv3 method provides authentication but no encryption?
a. noAuthNoPriv
b. authPriv
c. authNoPriv
d. noauthPriv
26. Which is not an SNMP operation?
a. GetNext
b. Trap
c. Inform Request
d. Community
e. GetBulk
27. Which protocol allows for vendor-specific information?
a. SNMPv3
b. RMON2
c. ASN.1
d. CDP
e. MIB
28. Which protocol allows for ISPs to bill its customers for network usage?
a. SNMPv3
b. RMON2
c. NetFlow
d. CDP
e. MIB
29. Which solution can be customized in each interface to include data timestamping across a large number of interfaces?
a. SNMPv3
b. RMON2
c. NetFlow
d. CDP
e. MIB
30. Cisco NetFlow consists of which components? (Select three.)
a. NetFlow Accounting
b. FlowCollector
c. NetFlow Billing Server
d. Network Data Analyzer
e. NetFlow Traffic Generator Tool
31. You are performing a manual network discovery using CDP when you encounter non-Cisco network devices. What options do you have to continue the manual discovery?
a. Continue to use CDP; it discovers non-Cisco devices.
b. Use CDP non-Cisco command options.
c. Use LLDP.