Chapter 12. Managing Security
This chapter covers the following subjects:
This chapter discusses network security in terms of security management and policy. Network security topics examined include security threats, risks, policy compliance, and securing network connectivity. The chapter then goes on to explain how network security management and policy provide a framework for secure networks. The chapter also explores trust and identity management, which defines how network access can occur, and threat defense, which adds increased levels of security into network endpoints.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz helps you identify your strengths and deficiencies in this chapter’s topics.
The ten-question quiz, derived from the major sections in the “Foundation Topics” portion of the chapter, helps you determine how to spend your limited study time.
Table 12-1 outlines the major topics discussed in this chapter and the “Do I Know This Already?” quiz questions that correspond to those topics.
1. Which of the following security legislation applies protection for credit card holder data?
a. SOX
b. GLBA
c. HIPAA
d. PCI DSS
2. What classification of security threat gathers information about the target host?
a. Unauthorized access
b. Reconnaissance
c. Denial of service
d. None of the above
3. What type of security threat works to overwhelm network resources such as memory, CPU, and bandwidth?
a. Denial of service
b. Reconnaissance
c. Unauthorized access
d. NMAP scans
4. What is it called when attackers change sensitive data without proper authorization?
a. VLAN filtering
b. ACLs
c. Integrity violation
d. Loss of availability
5. What security document focuses on the processes and procedures for managing network events in addition to emergency-type scenarios?
c. Network access control policy
6. Which of the following should be included in a security policy? (Select all that apply.)
a. Identification of assets
b. Definition of roles and responsibilities
c. Description of permitted behaviors
d. All of the above
7. Authentication of the identity is based on what attributes? (Select all that apply.)
a. Something the subject knows
b. Something the subject has
c. Something the subject is
d. All of the above
8. What VPN protocol uses encrypted point-to-point GRE tunnels?
a. GRE-based VPN
b. Cisco IPsec VPN
c. Cisco GET VPN
d. Cisco DMVPN
9. What are some physical security guidelines to consider for a secure infrastructure? (Select all that apply.)
a. Evaluate potential security breaches.
b. Use physical access controls such as locks or alarms.
c. Assess the impact of stolen network resources and equipment.
d. Use Syslog and SNMP analysis.
10. Which of the following benefits does a security management solution provide?
a. SAINT scans
b. Provisions network security policies for deployment
c. Prevents unauthorized access
d. NMAP scans
Foundation Topics
This chapter examines security management topics that you need to master for the CCDA exam. It begins by explaining reasons for network security and some techniques that can be used to prevent attacks. Next, the chapter describes the types of attacks that can compromise network security and classifies security threats. It goes on to cover the risks inherent in network security, along with a series of risk examples that illustrate how attacks can occur. The chapter then looks at what a “security policy” is and how it is used as a framework for network security.
In addition, this chapter explores ways to control and permit network access at any point within the network and discusses enabling security in network equipment by using traffic-isolation techniques. The chapter wraps up with examining some security management solutions.
Network Security Overview
For many years, networks were designed to be fairly open in nature and did not require much security. The greatest area of concern was physical access. Over time, networks grew in size, and complexity of attacks increased the need for network security. For today’s businesses and organizations, security is now a mandatory part of designing IT systems, because the risks are too high if critical data is tampered with or lost. Security teams within organizations must provide adequate levels of protection for the business to conduct its operations.
Network security is used to prevent unauthorized access and defend against network attacks from intruders. In addition, network security protects data from manipulation and theft. Businesses today also need to comply with company policy and security legislation that is in place to help protect data and keep it private.
Here are some key security goals to think about when integrating security into the network:
![]() High availability and resiliency of the infrastructure
High availability and resiliency of the infrastructure
![]() Preventing unauthorized access, intrusions, network abuse, data leaks, theft, and fraud
Preventing unauthorized access, intrusions, network abuse, data leaks, theft, and fraud
![]() Protecting the end users and infrastructure
Protecting the end users and infrastructure
![]() Ensuring data confidentiality and integrity
Ensuring data confidentiality and integrity
Network security also needs to be transparent to the end users and should also be designed to prevent attacks by
![]() Blocking external attackers from accessing the network
Blocking external attackers from accessing the network
![]() Permitting access to only authorized users
Permitting access to only authorized users
![]() Preventing attacks from sourcing internally
Preventing attacks from sourcing internally
![]() Supporting different levels of user access
Supporting different levels of user access
![]() Safeguarding data from tampering or misuse
Safeguarding data from tampering or misuse
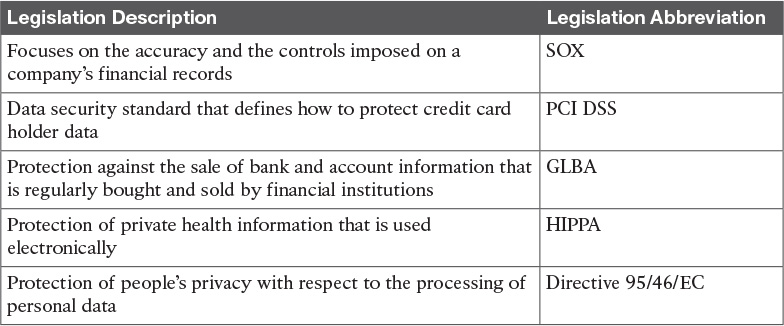
Security Legislation
A number of legislative bodies along with the public have insisted that security controls be in place to protect private information and make certain that it is handled properly. These legislative bodies influence network security by imposing mandates with which organizations are required to comply. These requirements might include protecting customer information with regards to privacy and, in some cases, requiring encryption of the data.
The United States has a growing body of security legislation that you need to be aware of:
![]() U.S. Public Company Accounting Reform and Investor Protection Act of 2002 (Sarbanes-Oxley or SOX): Focuses on the accuracy and controls imposed on a company’s financial records. This U.S. federal law was passed because of a number of corporate and accounting scandals that took place.
U.S. Public Company Accounting Reform and Investor Protection Act of 2002 (Sarbanes-Oxley or SOX): Focuses on the accuracy and controls imposed on a company’s financial records. This U.S. federal law was passed because of a number of corporate and accounting scandals that took place.
![]() Payment Card Industry (PCI) Data Security Standard (DSS): PCI is a data security standard that defines how to protect credit card holder data, including the storage and transfer of credit card holder information. Many retailers that accept credit cards have to meet PCI DSS standards or pay stiff penalties and are subject to regular and rigorous audits for PCI DSS compliance.
Payment Card Industry (PCI) Data Security Standard (DSS): PCI is a data security standard that defines how to protect credit card holder data, including the storage and transfer of credit card holder information. Many retailers that accept credit cards have to meet PCI DSS standards or pay stiff penalties and are subject to regular and rigorous audits for PCI DSS compliance.
![]() Gramm-Leach-Bliley Financial Services Modernization Act of 1999 (GLBA): Provides protection against the sale of bank and account information that is regularly bought and sold by financial institutions. GLBA also guards against the practice of obtaining private information through false pretenses.
Gramm-Leach-Bliley Financial Services Modernization Act of 1999 (GLBA): Provides protection against the sale of bank and account information that is regularly bought and sold by financial institutions. GLBA also guards against the practice of obtaining private information through false pretenses.
![]() U.S. Health Insurance Portability and Accountability Act (HIPAA): Applies to the protection of private health information that is used electronically. The purpose is to enable better access to health information, reduce fraud, and lower the cost of health care in the United States.
U.S. Health Insurance Portability and Accountability Act (HIPAA): Applies to the protection of private health information that is used electronically. The purpose is to enable better access to health information, reduce fraud, and lower the cost of health care in the United States.
![]() EU Data Protection Directive 95/46/EC: Calls for the protection of people’s right to privacy with respect to the processing of personal data.
EU Data Protection Directive 95/46/EC: Calls for the protection of people’s right to privacy with respect to the processing of personal data.
Table 12-2 describes the security legislation and identifies its abbreviation.

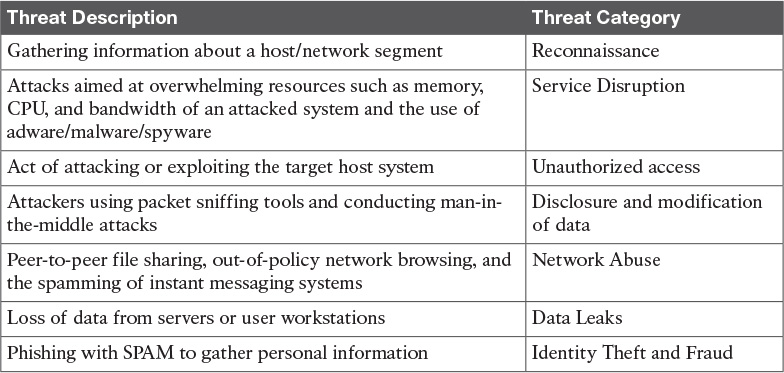
Security Threats
It is important to be aware of the different types of attacks that can impact the security of IT systems. Security threats can be classified into the following categories:
![]() Reconnaissance: The goal of reconnaissance is to gather as much information as possible about the target host/network. Generally, this type of information gathering is done before an attack is carried out.
Reconnaissance: The goal of reconnaissance is to gather as much information as possible about the target host/network. Generally, this type of information gathering is done before an attack is carried out.
![]() Unauthorized access: Refers to the act of attacking or exploiting the target system or host. Operating systems, services, and physical access to the target host have known system vulnerabilities that the attacker can take advantage of and use to increase his or her privileges. Social engineering is another technique for obtaining confidential information from employees by manipulation. As a result of the attacker exploiting the host, can read, change, or delete information from the system causing interruption of service and/or data loss in some cases.
Unauthorized access: Refers to the act of attacking or exploiting the target system or host. Operating systems, services, and physical access to the target host have known system vulnerabilities that the attacker can take advantage of and use to increase his or her privileges. Social engineering is another technique for obtaining confidential information from employees by manipulation. As a result of the attacker exploiting the host, can read, change, or delete information from the system causing interruption of service and/or data loss in some cases.
![]() Service disruption: Attacks aimed at disrupting normal infrastructure services. The disruption can be caused by the following:
Service disruption: Attacks aimed at disrupting normal infrastructure services. The disruption can be caused by the following:
![]() Denial of service (DoS) attacks: DoS attacks aim to overwhelm resources such as memory, CPU, and bandwidth that impact the target system and deny legitimate user’s access. Distributed DoS (DDoS) attacks involve multiple sources working together to deliver the coordinated attack.
Denial of service (DoS) attacks: DoS attacks aim to overwhelm resources such as memory, CPU, and bandwidth that impact the target system and deny legitimate user’s access. Distributed DoS (DDoS) attacks involve multiple sources working together to deliver the coordinated attack.
![]() Adware: Automatic ads used to generate revenue for the hackers that are seeking monetary gains.
Adware: Automatic ads used to generate revenue for the hackers that are seeking monetary gains.
![]() Malware: Hostile software used to gain access, gather information, or disrupt normal operations.
Malware: Hostile software used to gain access, gather information, or disrupt normal operations.
![]() Spyware: Software that is used to obtain covert information secretly.
Spyware: Software that is used to obtain covert information secretly.
![]() Disclosure and modification of data: As data is in transit, an attacker can use packet-sniffing tools to read data on the wire while it is in flight. Man-in-the-middle attacks can also be used to inject new information into the data packets.
Disclosure and modification of data: As data is in transit, an attacker can use packet-sniffing tools to read data on the wire while it is in flight. Man-in-the-middle attacks can also be used to inject new information into the data packets.
![]() Network abuse: The network can be abused from peer-to-peer file sharing, out-of-policy network browsing, and access to forbidden content on the network. Instant messaging systems can be a potential target for spammers to send unsolicited messages.
Network abuse: The network can be abused from peer-to-peer file sharing, out-of-policy network browsing, and access to forbidden content on the network. Instant messaging systems can be a potential target for spammers to send unsolicited messages.
![]() Data leaks: The loss of data from servers or users’ workstations while in transit or at rest. To prevent loss of data, data loss prevention (DLP) software can help to control what data users can transfer.
Data leaks: The loss of data from servers or users’ workstations while in transit or at rest. To prevent loss of data, data loss prevention (DLP) software can help to control what data users can transfer.
![]() Identity theft and fraud: Would-be attackers use phishing techniques such as email spam to gather personal information such as usernames, passwords, and credit card accounts by posing as a person who can be trusted.
Identity theft and fraud: Would-be attackers use phishing techniques such as email spam to gather personal information such as usernames, passwords, and credit card accounts by posing as a person who can be trusted.
Table 12-3 outlines the categorized security threats.
Reconnaissance and Port Scanning
Reconnaissance network tools are used to gather information from the hosts attached to the network. They have many capabilities, including identifying the active hosts and which services the hosts are running. In addition, these tools can find trust relationships, determine OS platforms, and identify user and file permissions.
Some of the techniques that these scanning tools use include TCP connects (open), TCP SYNs (half open), ACK sweeps, Internet Control Message Protocol (ICMP) sweeps, SYN sweeps, and Null scans. Listed here are some of the more popular port-scanning tools and their uses:
![]() NMAP (Network Mapper) is designed to scan large networks or even a single host. It is an open source utility used for network exploration and security audits.
NMAP (Network Mapper) is designed to scan large networks or even a single host. It is an open source utility used for network exploration and security audits.
![]() NetscanTools is a collection over 40 network utilities designed for Windows machines. It includes tools for DNS, ping, traceroute, and port scanning.
NetscanTools is a collection over 40 network utilities designed for Windows machines. It includes tools for DNS, ping, traceroute, and port scanning.
![]() NetStumbler identifies wireless networks using 802.11a/b/g wireless LAN (WLAN) standards with or without the service set identifier (SSID) being broadcast. NetStumbler runs on Microsoft Windows–based platforms, including Windows Mobile.
NetStumbler identifies wireless networks using 802.11a/b/g wireless LAN (WLAN) standards with or without the service set identifier (SSID) being broadcast. NetStumbler runs on Microsoft Windows–based platforms, including Windows Mobile.
![]() Kismet is an 802.11 wireless sniffer and intrusion detection system (IDS) application that can collect traffic from 802.11a/b/g/n networks. Kismet collects packets and detects wireless networks even when they are hidden.
Kismet is an 802.11 wireless sniffer and intrusion detection system (IDS) application that can collect traffic from 802.11a/b/g/n networks. Kismet collects packets and detects wireless networks even when they are hidden.
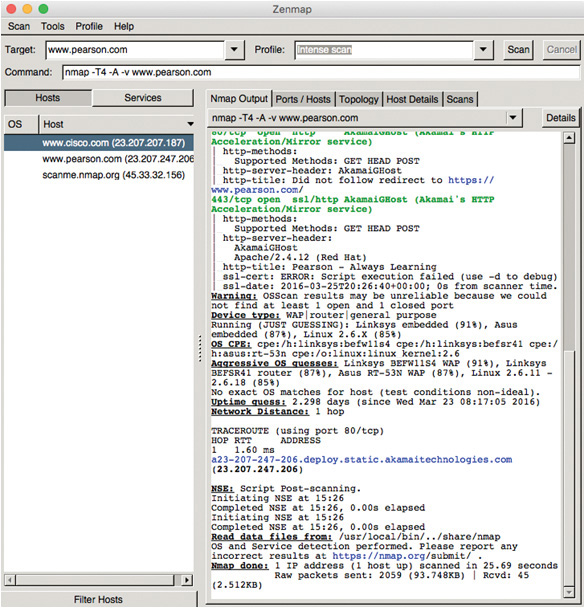
Figure 12-1 shows NMAP scanning several hosts that have different operating systems. This particular scan displays the IP address, open ports, services, device type, uptime, OS details, and traceroute information.
Vulnerability Scanners
Vulnerability scanners determine what potential exposures are present in the network. Passive scanning tools are used to analyze the traffic flowing on the network. Active testing injects sample traffic onto the network. Here are some online resources for published vulnerability information:
![]() CERT CC: cert.org
CERT CC: cert.org
![]() MITRE: cve.mitre.org
MITRE: cve.mitre.org
![]() Microsoft: technet.microsoft.com/en-us/security
Microsoft: technet.microsoft.com/en-us/security
![]() Cisco Security Notices: tools.cisco.com/security/center/
Cisco Security Notices: tools.cisco.com/security/center/
Here are some tools used for vulnerability scanning:
![]() Nessus is designed to automate the testing and discovery of known vulnerabilities. Nessus is an open source tool that runs natively on various operating systems, including Linux, Apple Mac OS, and Microsoft Windows-based operating systems.
Nessus is designed to automate the testing and discovery of known vulnerabilities. Nessus is an open source tool that runs natively on various operating systems, including Linux, Apple Mac OS, and Microsoft Windows-based operating systems.
![]() SAINT (Security Administrator’s Integrated Network Tool) is a vulnerability-assessment application that runs on Linux and Apple Mac OS hosts.
SAINT (Security Administrator’s Integrated Network Tool) is a vulnerability-assessment application that runs on Linux and Apple Mac OS hosts.
![]() MBSA (Microsoft Baseline Security Analyzer) is used to scan systems and identify whether patches are missing for Windows products such as operating systems, Internet Information Services (IIS), Structured Query Language (SQL), Exchange Server, Internet Explorer, Systems Management Server (SMS), and Microsoft Office applications. MBSA also alerts you if it finds any known security vulnerabilities such as weak or missing passwords and other common security issues.
MBSA (Microsoft Baseline Security Analyzer) is used to scan systems and identify whether patches are missing for Windows products such as operating systems, Internet Information Services (IIS), Structured Query Language (SQL), Exchange Server, Internet Explorer, Systems Management Server (SMS), and Microsoft Office applications. MBSA also alerts you if it finds any known security vulnerabilities such as weak or missing passwords and other common security issues.
The MBSA security report in Figure 12-2 displays several security issues on this host. Issues found include: Automatic updates is not configured to start automatically, some user account passwords have blank or missing passwords, and the Windows Firewall has some exceptions.
Unauthorized Access
Attackers use several techniques to gain unauthorized system access. One approach is when unauthorized people use usernames and passwords to escalate the account’s privilege levels. Furthermore, some system user accounts have default administrative username and password pairings that are common knowledge, which makes them very unsecure. The trust relationships inherit between systems, and applications are yet another way unauthorized access takes place.
Social engineering is yet another method used to gain unauthorized access. Social engineering is the practice of acquiring confidential information by manipulating legitimate users. Actually, the most confidential information such as badges, usernames, and passwords can be uncovered just by walking around an organization. Many security items can be found unsecured in offices and cubicles. For example, it is not uncommon to find passwords written on notes or badges and keys left on tops of desks or in unlocked drawers. Another way of gaining confidential information is the pyschological method of social engineering. For example, someone pretending to be from the IT department calls a user and asks for his or her account information to maintain or correct an account discrepancy.
In addition to these approaches, hackers can obtain account information by using password-cracking utilities or by capturing network traffic.
Security Risks
To protect network resources, processes, and procedures, technology needs to address several security risks. Important network characteristics that can be at risk from security threats include system availability, data integrity, and data confidentiality:
![]() System availability should ensure uninterrupted access to critical network and computing resources to prevent service disruption and loss of productivity.
System availability should ensure uninterrupted access to critical network and computing resources to prevent service disruption and loss of productivity.
![]() Data integrity should ensure that only authorized users can change critical information and guarantee the authenticity of data.
Data integrity should ensure that only authorized users can change critical information and guarantee the authenticity of data.
![]() Data confidentiality should ensure that only legitimate users can view sensitive information to prevent theft, legal liabilities, and damage to the organization.
Data confidentiality should ensure that only legitimate users can view sensitive information to prevent theft, legal liabilities, and damage to the organization.
In addition, the use of redundant hardware and encryption can significantly reduce the risks associated with system availability, data integrity, and data confidentiality.
Table 12-4 summarizes security risks types with descriptions.

Targets
Given the wide range of potential threats, just about everything in the network has become vulnerable and is a potential target. Ordinary hosts top the list as the favorite target, especially for worms and viruses. After a host has been compromised, it is frequently used as a new attack point. (A collection of such hosts is referred to as a botnet.)
Other high-value targets include devices that support the network. Here is a list of some network devices, servers, and security devices that stand out as potential targets:
![]() Infrastructure devices: Routers, switches
Infrastructure devices: Routers, switches
![]() Security devices: Firewalls, intrusion prevention systems (IPS)
Security devices: Firewalls, intrusion prevention systems (IPS)
![]() Network services: Dynamic Host Configuration Protocol (DHCP) and Domain Name System (DNS) servers
Network services: Dynamic Host Configuration Protocol (DHCP) and Domain Name System (DNS) servers
![]() Endpoints: Management stations and IP phones
Endpoints: Management stations and IP phones
![]() Infrastructure: Network throughput and capacity
Infrastructure: Network throughput and capacity
Loss of Availability
Denial of service (DoS) attacks try to block or deny access to impact the availability of network services. These types of attacks can interrupt business transactions, cause considerable loss, and damage the company’s reputation. DoS attacks are fairly straightforward to carry out, even by an unskilled attacker. Distributed DoS (DDoS) attacks are initiated by multiple source locations within the network to increase the attack’s size and impact.
DDoS attacks occur when the attacker takes advantage of vulnerabilities in the network/host. Here are some common failure points:
![]() A network, host, or application fails to process large amounts of data sent to it, which crashes or breaks communication ability.
A network, host, or application fails to process large amounts of data sent to it, which crashes or breaks communication ability.
![]() A host or application is unable to handle an unexpected condition, such as improperly formatted data and memory or resource depletion.
A host or application is unable to handle an unexpected condition, such as improperly formatted data and memory or resource depletion.
![]() Nearly all DoS attacks are carried out with spoofing and flooding methods.
Nearly all DoS attacks are carried out with spoofing and flooding methods.
Table 12-5 lists some DoS-mitigating IOS software features.

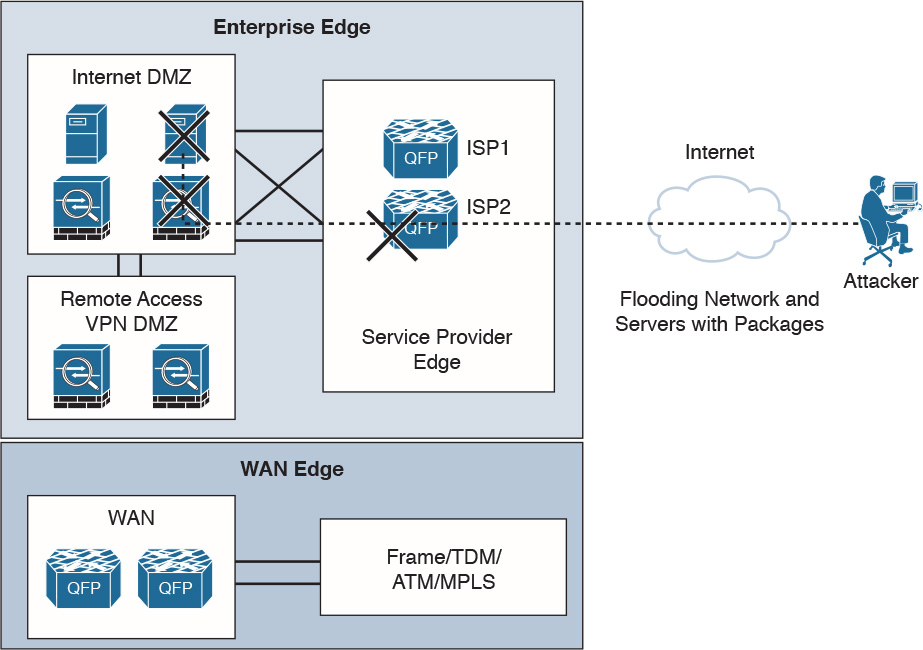
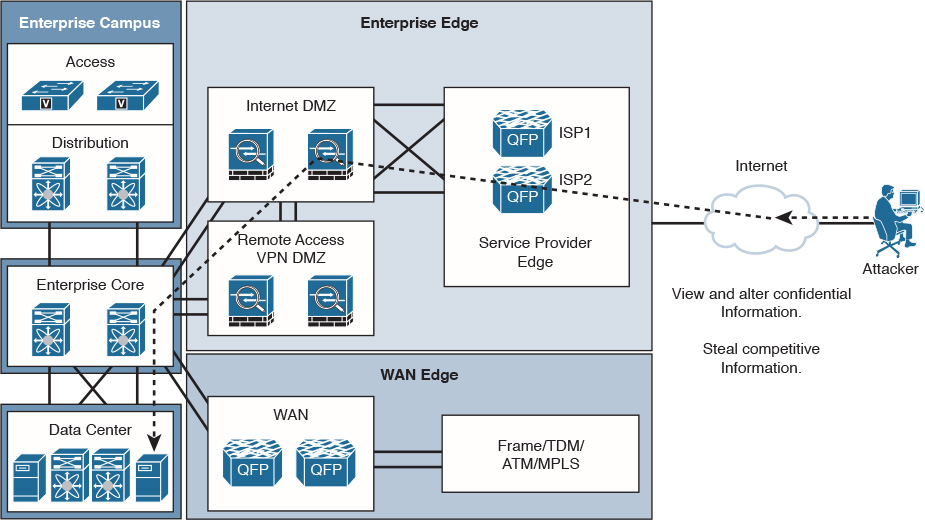
Figure 12-3 shows a DoS threat on availability. The attacker is performing a DoS attack on the network and servers using a flood of packets. Keep in mind that this is an external attack; however, an internal attack is also certainly possible.
Integrity Violations and Confidentiality Breaches
When attackers change sensitive data without the proper authorization, this is called an integrity violation. For example, an attacker might access financial data and delete critical information. The effect of this change might not be felt for some time or until a significant loss has occurred. Integrity attacks like this are considered by many companies to be one of the most serious threats to their business. Furthermore, identifying these attacks can be difficult, and the effects can be devastating.
Confidentiality breaches occur when the attacker attempts to read sensitive information. It is difficult to detect these types of attacks, and loss of data can happen without the owner’s knowledge.
It is important to use restrictive access controls to prevent integrity violations and confidentiality attacks. Here are some ways to enforce access control to reduce the risks:
![]() Restrict access by separating networks (VLANs) and by using stateful packet inspection firewalls.
Restrict access by separating networks (VLANs) and by using stateful packet inspection firewalls.
![]() Restrict access with OS-based controls in both Windows and Linux.
Restrict access with OS-based controls in both Windows and Linux.
![]() Limit user access by using user profiles for different departmental roles.
Limit user access by using user profiles for different departmental roles.
![]() Use encryption techniques to secure data or digitally sign data.
Use encryption techniques to secure data or digitally sign data.
Figure 12-4 shows an attacker viewing, altering, and stealing competitive information. Pay particular attention to the obstacles the attacker must go through to get to the data.
Security Policy and Process
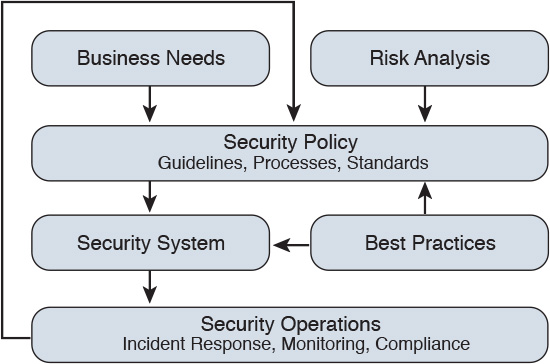
To provide the proper levels of security and increase network availability, a security policy is a crucial element in providing secure network services. This is an important concept to understand, and such business requirements should be considered throughout the system lifecycle. Business requirements and risk analysis are used in the development of a security policy. It is often a balance between ease of access versus the security risk and cost of implementing the security technology.
In terms of network security in the system lifecycle, the business needs are a key area to consider. Business needs define what the business wants to do with the network.
Risk analysis is another part of the system lifecycle. It explains the security risks and their associated costs. The business needs and the risk assessment feed information into the security policy.
The security policy describes the organization’s processes, procedures, guidelines, and standards. Furthermore, industry and security best practices are leveraged to provide well-known processes and procedures.
Finally, an organization’s security operations team needs to have processes and procedures defined. This information helps explain what needs to happen for incident response, security monitoring, system maintenance, and managing compliance.
Table 12-6 outlines key network security considerations.

Figure 12-5 shows the flow of the network security lifecycle.
Security Policy Defined
RFC 2196 says, “A security policy is a formal statement of the rules by which people who are given access to an organization’s technology and information assets must abide.” When you are developing security policies for an organization, RFC 2196 can serve as a guide for developing security processes and procedures. This RFC lists issues and factors that an organization must consider when setting its policies. Organizations need to make many decisions and come to agreement when creating their security policy.
Basic Approach of a Security Policy
To help create a security policy, here is a generally accepted approach from RFC 2196:
Step 1. Identify what you are trying to protect.
Step 2. Determine what you are trying to protect it from.
Step 3. Determine how likely the threats are.
Step 4. Implement measures that protect your assets in a cost-effective manner.
Step 5. Review the process continuously, and make improvements each time a weakness is found.
Purpose of Security Policies
One of the main purposes of a security policy is to describe the roles and requirements for securing technology and information assets. The policy defines the ways in which these requirements will be met.
There are two main reasons for having a security policy:
![]() It provides the framework for the security implementation:
It provides the framework for the security implementation:
![]() Identifies assets and how to use them
Identifies assets and how to use them
![]() Defines and communicates roles and responsibilities
Defines and communicates roles and responsibilities
![]() Describes tools and procedures
Describes tools and procedures
![]() Clarifies incident handling of security events
Clarifies incident handling of security events
![]() It creates a security baseline of the current security posture:
It creates a security baseline of the current security posture:
![]() Describes permitted and unpermitted behaviors
Describes permitted and unpermitted behaviors
![]() Defines consequences of asset misuse
Defines consequences of asset misuse
![]() Provides cost and risk analysis
Provides cost and risk analysis
Here are some questions you might need to ask when developing a security policy:
![]() What data and assets will be included in the policy?
What data and assets will be included in the policy?
![]() What network communication is permitted between hosts?
What network communication is permitted between hosts?
![]() How will policies be implemented?
How will policies be implemented?
![]() What happens if the policies are violated?
What happens if the policies are violated?
![]() How will the latest attacks impact your network and security systems?
How will the latest attacks impact your network and security systems?
Security Policy Components
A security policy is divided into smaller parts that help describe the overall risk management policy, identification of assets, and where security should be applied. Other components of the security policy explain how responsibilities related to risk management are handled throughout the enterprise.
Further documents concentrate on specific areas of risk management:
![]() Acceptable-use policy is a general end-user document that is written in simple language. This document defines the roles and responsibilities within risk management and should have clear explanations to avoid confusion.
Acceptable-use policy is a general end-user document that is written in simple language. This document defines the roles and responsibilities within risk management and should have clear explanations to avoid confusion.
![]() Network access control policy defines general access control principles used in the network and how data is classified, such as confidential, top secret, or internal.
Network access control policy defines general access control principles used in the network and how data is classified, such as confidential, top secret, or internal.
![]() Security management policy explains how to manage the security infrastructure.
Security management policy explains how to manage the security infrastructure.
![]() Incident-handling policy defines the processes and procedures for managing security incidents, including the handling of emergency scenarios.
Incident-handling policy defines the processes and procedures for managing security incidents, including the handling of emergency scenarios.
Several other documents supplement these; they vary depending on the organization. The security policy requires the acceptance and support of all employees to make it successful. All the key stakeholders or business leaders, including members of senior management, should have input into the development of the security policy. In addition, key stakeholders should continue to participate in the ongoing maintenance and updates to the security policy in order to keep it up to date.
Table 12-7 summarizes additional security policy documents.

Risk Assessment
Within network security, proper risk management is a technique used to lower risks to within acceptable levels. A well thought-out plan for network security design implements the components that are part of the security policy. The security policies that an organization employs use risk assessments and cost-benefit analysis to reduce security risks.
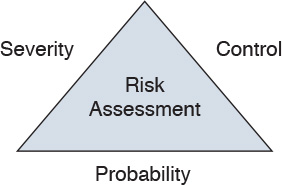
Figure 12-6 shows the three major components of risk assessment. Control refers to how you use the security policy to minimize potential risks. Severity describes the level of the risk to the organization, and probability is the likeliness that an attack against the assets will occur.
Risk assessments should explain the following:
![]() What assets to secure
What assets to secure
![]() The monetary value of the assets
The monetary value of the assets
![]() The actual loss that would result from an attack
The actual loss that would result from an attack
![]() The severity and the probability that an attack against the assets will occur
The severity and the probability that an attack against the assets will occur
![]() How to use security policy to control or minimize the risks
How to use security policy to control or minimize the risks
In many cases, security costs can be justified by describing the loss of productivity or revenue that could occur during security incidents.
Generally, network systems are built with just enough security to reduce potential losses to a reasonable level. However, some organizations have higher security requirements, such as complying with PCI DSS, SOX or HIPAA regulations, so they need to employ stronger security mechanisms.
Risk Index
A risk index is used to consider the risks of potential threats. The risk index is based on risk assessment components (factors):
![]() Severity of loss if the asset is compromised
Severity of loss if the asset is compromised
![]() Probability of the risk actually occurring
Probability of the risk actually occurring
![]() Ability to control and manage the risk
Ability to control and manage the risk
One approach to determining a risk index is to give each risk factor a value from 1 (lowest) to 3 (highest). For example, a high-severity risk would have a substantial impact on the user base and/or the entire organization. Medium-severity risks would have an effect on a single department or site. Low-severity risks would have limited impact and would be relatively straightforward to mitigate.
The risk index is calculated by multiplying the severity times the probability factor, and then dividing by the control factor:
Risk index = (severity factor * probability factor) / control factor
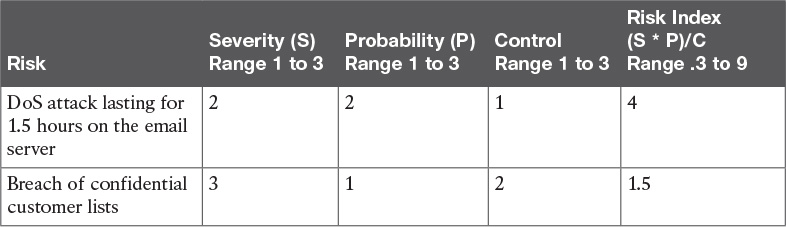
Table 12-8 shows a sample risk index calculation for a typical large corporation facing a couple of typical risks. If the risk index number calculated is high, there is more risk and therefore more impact to the organization. The lower the index number calculated means that there is less risk and less impact to the organization.
Continuous Security
As requirements change and new technology is developed, the network security policy should be updated to reflect the changes. Here are four steps used to facilitate continuing efforts in maintaining security policies:
Step 1. Secure: Identification, authentication, ACLs, stateful packet inspection (SPI), encryption, and VPNs
Step 2. Monitor: Intrusion and content-based detection and response
Step 3. Test: Assessments, vulnerability scanning, and security auditing
Step 4. Improve: Data analysis, reporting, and intelligent network security
Figure 12-7 shows the four-step process that updates and continues the development of security policies.
Table 12-9 lists the steps for continuous security.
Integrating Security Mechanisms into Network Design
Today’s network designs demonstrate an increased use of security mechanisms and have become more tightly integrated with network design. Many security services such as IPS, firewalls, and IPsec virtual private network (VPN) appliances now reside within the internal network infrastructure. It is recommended that you incorporate network security during the network design planning process. This requires close coordination between the various engineering and operations teams.
Trust and Identity Management
Trust and identity management is crucial for the development of a secure network system. Trust and identity management defines who and what can access the network, and when, where, and how that access can occur. Access to the business applications and network equipment is based on the user-level rights that are granted and assigned by the administrators. Trust and identity management also attempts to isolate and keep infected machines off the network by enforcing access control. The three main components of trust and identity management are trust, identity, and access control, as shown in Figure 12-8. The following sections cover these components in detail.
Trust
Trust is the relationship between two or more network entities that are permitted to communicate. Security policy decisions are largely based on this premise of trust. If you are trusted, you are allowed to communicate as needed. However, sometimes security controls need to apply restraint to trust relationships by limiting or preventing access to the designated privilege level. Trust relationships can be explicit or implied by the organization. Some trust relationships can be inherited or passed down from one system to another. However, keep in mind that these trust relationships can also be abused.
Domains of Trust
Domains of trust are a way to group network systems that share a common policy or function. Network segments have different trust levels, depending on the resources they are securing. When applying security controls within network segments, it is important to consider the trust relationships between the segments. Keep in mind that customers, partners, and employees each have their own unique sets of requirements from a security perspective that can be managed independently with “domains of trust” classifications. When domains of trust are managed in this way, consistent security controls within each segment can be applied.
Figure 12-9 shows two examples of trust domains with varying levels of trust segmented. The lighter shading indicates an internal environment with higher security, and the darker areas represent less-secure areas with lower security.
Trust levels such as the internal network can be very open and flexible, whereas the outside needs to be considered unsafe and therefore needs strong security to protect the resources. Table 12-10 shows different levels of trust, from low to high.

Identity
Identity is the “who” of a trust relationship. This can be users, devices, organizations, or all of the above. Network entities are validated by credentials. Authentication of the identity is based on the following attributes:
![]() Something the subject knows: Knowledge of a secret, password, PIN, or private key
Something the subject knows: Knowledge of a secret, password, PIN, or private key
![]() Something the subject has: Possession of an item such as a software token, token card, smartcard, or hardware key
Something the subject has: Possession of an item such as a software token, token card, smartcard, or hardware key
![]() Something the subject is: Human characteristics, such as a fingerprint, retina scan, or voice recognition
Something the subject is: Human characteristics, such as a fingerprint, retina scan, or voice recognition
Generally, identity credentials are checked and authorized by requiring passwords, pins, tokens, or certificates.
Passwords
Passwords are used to give users access and allow them to access network resources. Passwords are an example of the authentication attribute called “something you know.” Typically, users do not want to use strong passwords; they usually prefer to use passwords that are easy to remember. Users present a weakness in password security that requires increased enforcement of the organization’s password policy. Passwords should be valid for a limited amount of time and employ some password complexity such as upper/lowercase, numeric, and non-alphanumeric characters. Passwords should never be shared, use common dictionary words, or be posted on computer monitors.
Tokens
Tokens represent a way to increase security by requiring “two-factor authentication.” This type of authentication is based on “something you know” and “something you have.” For example, one factor may be a four-digit PIN, and another is the six-digit code on the physical token. The code on the tokens changes frequently, and it is not useful without the PIN. The code plus the PIN is transmitted to the authentication server for authorization. Then the server permits or denies access based on the user’s predetermined access level. Some token-based systems even require a password instead of a pin and code from the token. This is known as two-factor authentication.
Figure 12-10 shows two-factor authentication using a username and password, along with a token access code.
Certificates
Certificates are used to digitally prove your identity or right to access information or services. Certificates, also known as digital certificates, bind an identity to a pair of electronic keys that can be used to encrypt and sign digital information. A digital certificate is signed and issued by a certification authority (CA) with the CA’s private key. A digital certificate contains the following:
![]() Owner’s public key
Owner’s public key
![]() Owner’s name
Owner’s name
![]() Expiration date of the public key
Expiration date of the public key
![]() Name of the certificate authority
Name of the certificate authority
![]() Serial number
Serial number
![]() Digital signature of the CA
Digital signature of the CA
Certificates can be read or written by an application conforming to the X.509 CCITT international standard and are typical when deploying server applications based on Secure Sockets Layer (SSL).
Network Access Control
Network access control is a security mechanism for controlling admission to networks and resources. These controls enforce the security policy and employ rules about which resources can be accessed. Network access control ensures the confidentiality and integrity of the network resources.
The core of network access control forms the AAA framework, which consists of the following:
![]() Authentication establishes the user’s identity and access to the network resources.
Authentication establishes the user’s identity and access to the network resources.
![]() Authorization describes what can be done and what can be accessed.
Authorization describes what can be done and what can be accessed.
![]() Accounting provides an audit trail of activities by logging the actions of the user.
Accounting provides an audit trail of activities by logging the actions of the user.
Authentication, authorization, and accounting (AAA) are the network security services that help manage the network access control on your network equipment. AAA provides you with methods to secure access to network devices based on more granular techniques than just IP addressing information. For example, you might have a requirement to control access for a group of users regardless of their IP location. With AAA, you can integrate user directories such as LDAP and AD so that groups of users can have the same access levels decoupled from IP location. The implementation of AAA services requires authentication; however, authorization and accounting are optional services.
Secure Services
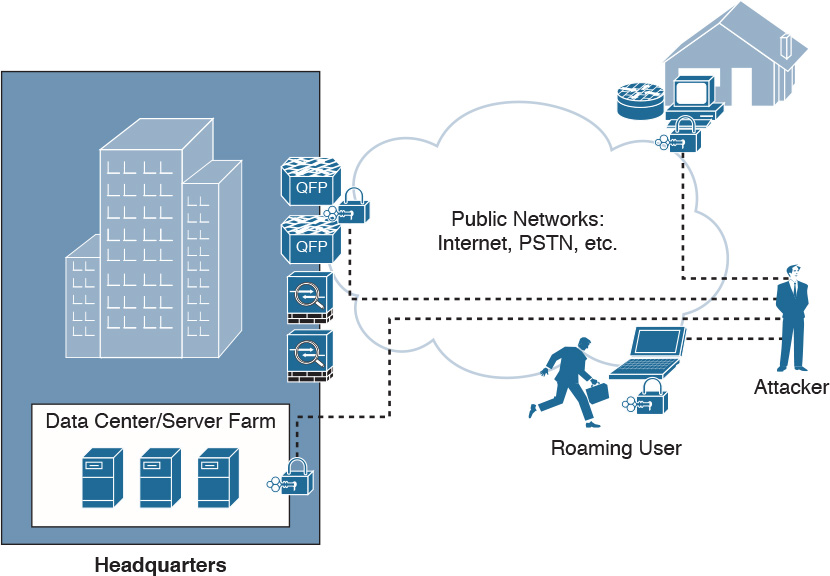
Secure Services is a component of the Cisco SAFE security reference architecture. This component of SAFE aims to protect the integrity and privacy of organizations’ sensitive information. With increased security risks on the rise, it is critical that security be implemented within today’s network environments. Consider, for example, the increased use of the Internet as a transport for extranet and teleworker connectivity via always-on broadband connectivity. Internal network segments have traditionally been considered trusted, but now require higher levels of network security. However, internal threats are now more than ten times more expensive and destructive than external threats. Data that flows across the network needs to be secured so that its privacy and integrity are preserved. These are important concepts to keep in mind when making business decisions about securing connectivity.
The Cisco Secure Services provides secure transport for data and applications using encryption and authentication techniques. Many security technologies exist for securing data, voice, and video traffic using wired, wireless, or remote access connectivity methods. Regardless of how the users connect to the network, they should have access to the applications and data that they are authorized to access.
Security technologies include
![]() IP Security (IPsec)
IP Security (IPsec)
![]() Secure Shell (SSH)
Secure Shell (SSH)
![]() Secure Sockets Layer (SSL)
Secure Sockets Layer (SSL)
![]() MPLS VPNs with IPsec
MPLS VPNs with IPsec
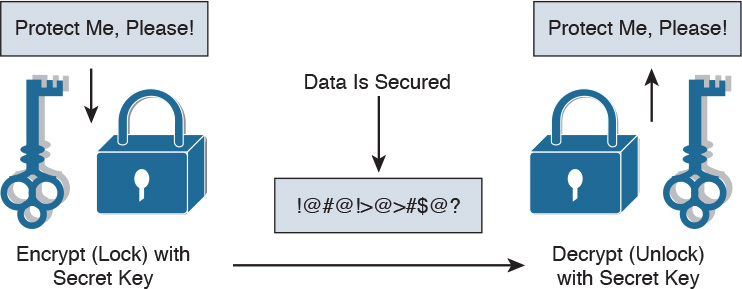
Encryption Fundamentals
Cryptography uses encryption to keep data private, thus protecting its confidentiality. The encapsulated data is encrypted with a secret key that secures the data for transport. When the data reaches the other side of the connection, another secret key is used to decrypt the data and reveal the message transmitted. The encryption and decryption can be used only by authorized users. Most encryption algorithms require the user to have knowledge of the secret keys. IPsec is an example of a security protocol framework that uses encryption algorithms to hide the IP packet payload during transmission.
Encryption Keys
An encryption session between two endpoints needs a key to encrypt the traffic and a key to decrypt the traffic at the remote endpoint. There are two ways to send a key to the remote endpoint:

![]() Shared secrets
Shared secrets
![]() Both sides can use the same key or use a transform to create the decryption key.
Both sides can use the same key or use a transform to create the decryption key.
![]() The key is placed on the remote endpoint out of band.
The key is placed on the remote endpoint out of band.
![]() This is a simple mechanism, but it has security issues because the key does not change frequently enough.
This is a simple mechanism, but it has security issues because the key does not change frequently enough.
![]() PKI
PKI
![]() It relies on asymmetric cryptography, which uses two different keys for encryption.
It relies on asymmetric cryptography, which uses two different keys for encryption.
![]() Public keys are used to encrypt and private keys to decrypt.
Public keys are used to encrypt and private keys to decrypt.
![]() PKI requires a certificate to be issued by a certificate authority (CA) and is used by many e-commerce sites on the Internet.
PKI requires a certificate to be issued by a certificate authority (CA) and is used by many e-commerce sites on the Internet.
Figure 12-11 shows what occurs during the encryption process using shared secret keys.
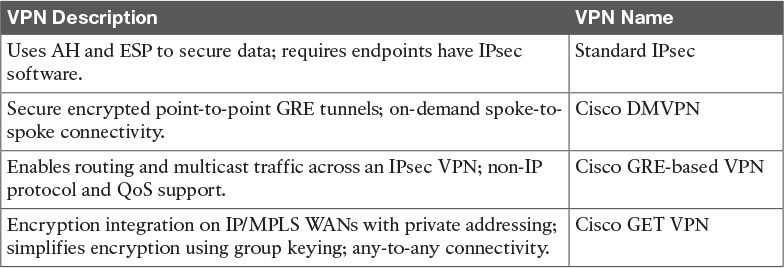
VPN Protocols
There are several VPN protocols to choose from, each with varying benefits and uses:

![]() Standard IPsec
Standard IPsec
![]() Uses Authentication Header (AH) and Encapsulating Security Payloads (ESP) to secure data.
Uses Authentication Header (AH) and Encapsulating Security Payloads (ESP) to secure data.
![]() Uses Internet Key Exchange (IKE) for dynamic key exchange.
Uses Internet Key Exchange (IKE) for dynamic key exchange.
![]() Endpoints require IPsec software.
Endpoints require IPsec software.
![]() Choose when multivendor interoperability support is required.
Choose when multivendor interoperability support is required.
![]() Cisco Dynamic Multipoint Virtual Private Network (DMVPN)
Cisco Dynamic Multipoint Virtual Private Network (DMVPN)
![]() Secure encrypted point-to-point generic routing encapsulation (GRE) tunnels.
Secure encrypted point-to-point generic routing encapsulation (GRE) tunnels.
![]() Provides on-demand spoke-to-spoke connectivity.
Provides on-demand spoke-to-spoke connectivity.
![]() Routing, multicast, and quality of service (QoS) support.
Routing, multicast, and quality of service (QoS) support.
![]() Choose when simplified hub-and-spoke VPNs are needed.
Choose when simplified hub-and-spoke VPNs are needed.
![]() Cisco GRE-based VPN
Cisco GRE-based VPN
![]() Enables routing and multicast traffic across a VPN (IPsec is optional).
Enables routing and multicast traffic across a VPN (IPsec is optional).
![]() Non-IP protocol and QoS support.
Non-IP protocol and QoS support.
![]() Choose when more detailed configuration than DMVPN is required.
Choose when more detailed configuration than DMVPN is required.
![]() Cisco GET VPN
Cisco GET VPN
![]() Encryption integration on IP and MPLS WANs using private addressing.
Encryption integration on IP and MPLS WANs using private addressing.
![]() Simplifies encryption management using group keying.
Simplifies encryption management using group keying.
![]() Any-to-any connectivity.
Any-to-any connectivity.
![]() Support for routing, multicast, and QoS.
Support for routing, multicast, and QoS.
![]() Choose when adding encryption to IP or MPLS WANs while allowing any-to-any connectivity.
Choose when adding encryption to IP or MPLS WANs while allowing any-to-any connectivity.
Table 12-11 describes key features of VPN security protocols.
IPsec comes in two forms: IP ESP and IP AH, which use protocol numbers 50 and 51, respectively. ESP is defined in RFC 2406, and AH is defined in RFC 2402. ESP provides confidentiality, data-origin authentication, integrity, and anti-replay service. AH allows for connectionless integrity, origin authentication, and anti-replay protection. These protocols can be used together or independently. Most IPsec-enabled clients or routers use IKE to exchange keys and ESP to encrypt the traffic.
Another type of VPN technology is SSL VPNs, which have become increasingly popular because of their clientless nature. The client only needs a standard web browser and a connection to the SSL VPN host, usually via the Internet.
Transmission Confidentiality
To ensure that data is kept private over unsecure networks such as the Internet, transmission confidentiality is used. Because the Internet is a public network, ordinary access control mechanisms are unavailable. Therefore, you need to encrypt the data before transporting over any untrusted network such as the Internet.
To provide transmission confidentiality, IPsec VPNs that support encryption can create a secure tunnel between the source and destination. As packets leave one site, they are encrypted; when they reach the remote site, they are decrypted. Eavesdropping on the Internet can occur, but with IPsec-encrypted packets, it is much more difficult.
IPsec VPNs commonly use well-known algorithms to perform the confidentiality treatment for packets. The well-known cryptographic algorithms include Triple Data Encryption Standard (3DES), Advanced Encryption Standard (AES), and Rivest Cipher 4 (RC4). These algorithms are thoroughly tested and checked and are considered trusted. However, keep in mind that cryptography can pose some performance problems, depending on the network’s state. That is why it is important to carefully analyze the network before deploying VPNs with IPsec.
Data Integrity
Cryptographic protocols protect data from tampering by employing secure fingerprints and digital signatures that can detect changes in data integrity.
Secure fingerprints function by appending a checksum to data that is generated and verified with the secret key. Only those who are authorized also know the secret key. An example of secure fingerprints is Hash-based Message Authentication Code (HMAC), which maintains packet integrity and the authenticity of the data protected.
Digital signatures use a related cryptography method that digitally signs the packet data. A signer creates the signature using a key that is unique and known only to the original signer. Recipients of the message can check the signature by using the signature verification key. The cryptography inherent in digital signatures guarantees accuracy and authenticity because the originator signed it. Financial businesses rely on digital signatures to electronically sign documents and also to prove that the transactions did in fact occur.
Keep in mind the following data integrity guidelines:
![]() Analyze the need for transmission integrity.
Analyze the need for transmission integrity.
![]() Factor in performance, but use the strongest cryptography.
Factor in performance, but use the strongest cryptography.
![]() Always use well-known cryptographic algorithms.
Always use well-known cryptographic algorithms.
Threat Defense
As part of the Cisco SAFE security reference architecture, threat defense enhances the security in the network by adding increased levels of security protection on network devices, appliances, and endpoints. Both internal and external threats have become much more destructive than in the past. DoS attacks, man-in-the-middle attacks, and Trojan horses have the potential to severely impact business operations. The Cisco Threat Defense System (Cisco TDS) provides a strong defense against these internal and external threats.
Threat defense has three main areas of focus:
![]() Enhancing the security of the existing network: Preventing loss of downtime, revenue, and reputation
Enhancing the security of the existing network: Preventing loss of downtime, revenue, and reputation
![]() Adding full security services for network endpoints: Securing mobile devices and desktop endpoints with Cisco Identity Services Engine (ISE)
Adding full security services for network endpoints: Securing mobile devices and desktop endpoints with Cisco Identity Services Engine (ISE)
![]() Enabling integrated security in routers, switches, and appliances: Security techniques enabled throughout the network, not just in point products or locations
Enabling integrated security in routers, switches, and appliances: Security techniques enabled throughout the network, not just in point products or locations
Physical Security
During your security implementations, it is essential to incorporate physical security to increase the strength of the overall security design. Physical security helps protect and restrict access to network resources and physical network equipment. Sound security policies must defend against potential attacks that can cause loss of uptime, reputation, or even revenue impacts.
Here are some considerations for potential physical threats:
![]() Attackers having unauthorized physical access can result in a full compromise of the IT asset.
Attackers having unauthorized physical access can result in a full compromise of the IT asset.
![]() Vulnerabilities inherent in systems can be exploited by attackers when they access the hardware directly or through untrusted software.
Vulnerabilities inherent in systems can be exploited by attackers when they access the hardware directly or through untrusted software.
![]() Physical access to the network, allowing attackers to capture, alter, or remove data flowing in the network.
Physical access to the network, allowing attackers to capture, alter, or remove data flowing in the network.
![]() Attackers may use their own hardware, such as a laptop or router, to inject malicious traffic onto the network.
Attackers may use their own hardware, such as a laptop or router, to inject malicious traffic onto the network.
Keep in mind these physical security guidelines when designing physical security architectures:
![]() Use physical access controls such as card readers, retina scans, locks, or alarms.
Use physical access controls such as card readers, retina scans, locks, or alarms.
![]() Ensure network devices have the proper environmental conditions that have controls for temperature, humidity, and fire suppression, and are free of magnetic interference.
Ensure network devices have the proper environmental conditions that have controls for temperature, humidity, and fire suppression, and are free of magnetic interference.
![]() Incorporate UPS units to reduce the possibility of loss of power to devices.
Incorporate UPS units to reduce the possibility of loss of power to devices.
![]() Evaluate potential security breach attack points.
Evaluate potential security breach attack points.
![]() Assess the impact of stolen network resources and equipment.
Assess the impact of stolen network resources and equipment.
![]() Use controls such as cryptography to secure traffic flowing on networks outside your control.
Use controls such as cryptography to secure traffic flowing on networks outside your control.
Figure 12-12 shows some physical security threat locations that an attacker could potentially exploit.
Infrastructure Protection

The infrastructure needs to be protected using security features and services to meet the growing needs of business without disruption. Infrastructure protection is the process of taking steps to reduce the risks and threats to the network infrastructure and to maintain the integrity and high availability of network resources.
By using best practices and a security policy, you can secure and harden the infrastructure equipment to prevent potential attacks. To combat network threats, Cisco has enhanced Cisco IOS and IOS XE with security features to support the secure infrastructure and increase the network’s availability.
Here are some recommended best practices for infrastructure protection:
![]() Use an out-of-band (OOB) management network to separate management-related traffic from production network traffic.
Use an out-of-band (OOB) management network to separate management-related traffic from production network traffic.
![]() Access network equipment remotely with SSH rather than with Telnet.
Access network equipment remotely with SSH rather than with Telnet.
![]() In network switching infrastructure, use BPDU Guard, Root Guard, and VLAN Trunking Protocol (VTP) with mode Transparent.
In network switching infrastructure, use BPDU Guard, Root Guard, and VLAN Trunking Protocol (VTP) with mode Transparent.
![]() In network switching infrastructure, use ARP inspection and DHCP snooping.
In network switching infrastructure, use ARP inspection and DHCP snooping.
![]() In network switching infrastructure, use Control Plane Policing (CoPP).
In network switching infrastructure, use Control Plane Policing (CoPP).
![]() Use AAA for authenticating administrative access, authorizing privileges, and logging all user sessions. Multiple AAA servers can also be used to increase fault tolerance of AAA services.
Use AAA for authenticating administrative access, authorizing privileges, and logging all user sessions. Multiple AAA servers can also be used to increase fault tolerance of AAA services.
![]() Enable syslog collection; review the logs for further analysis.
Enable syslog collection; review the logs for further analysis.
![]() Use Simple Network Management Protocol Version 3 (SNMPv3) for its security and privacy features.
Use Simple Network Management Protocol Version 3 (SNMPv3) for its security and privacy features.
![]() Disable unused network services, such as tcp-small-servers and udp-small-servers.
Disable unused network services, such as tcp-small-servers and udp-small-servers.
![]() Use SFTP rather than TFTP to manage images.
Use SFTP rather than TFTP to manage images.
![]() Use access classes to restrict access to management and the command-line interface (CLI).
Use access classes to restrict access to management and the command-line interface (CLI).
![]() Enable routing protocol authentication when available, such as Enhanced Interior Gateway Routing Protocol (EIGRP), Open Shortest Path First (OSPF) protocol, Intermediate System-to-Intermediate System (IS-IS), and Border Gateway Protocol (BGP).
Enable routing protocol authentication when available, such as Enhanced Interior Gateway Routing Protocol (EIGRP), Open Shortest Path First (OSPF) protocol, Intermediate System-to-Intermediate System (IS-IS), and Border Gateway Protocol (BGP).
![]() Use unused VLANs for the native VLAN on trunk ports. Do not use VLAN1.
Use unused VLANs for the native VLAN on trunk ports. Do not use VLAN1.
Security Management Solutions
Security management solutions are used to monitor, control, and support the network infrastructure. These same tools can be helpful during network audits and can save administrators a considerable amount of time.
Security management solutions provide the following:

![]() Collects, interprets, and presents information
Collects, interprets, and presents information
![]() Provisions network security policies for deployment
Provisions network security policies for deployment
![]() Maintains consistency by tracking policy changes
Maintains consistency by tracking policy changes
![]() Monitors account activity and provides role-based access control (RBAC)
Monitors account activity and provides role-based access control (RBAC)
A strong security implementation is only as good as the policies that are used. One of the biggest risks with a good security implementation is policy error. The network operations personnel need to fully understand the security policies, processes, and tools so that they can respond quickly when a security incident arises.
References and Recommended Readings
SecTools.org: Network Security Tools, sectools.org.
IANA protocol numbers, www.iana.org/assignments/protocol-numbers.
Module 4, “Enterprise Network Design,” Designing for Cisco Internetwork Solution Course (DESGN) v3.0.
Safe Simplifies Security, http://www.cisco.com/c/dam/en/us/solutions/collateral/enterprise/design-zone-security/safe-poster-components.pdf
Cisco SAFE Solution Overview, www.cisco.com/en/US/docs/solutions/Enterprise/Security/SAFESolOver.html.
RFC 2196: Site Security Handbook, www.ietf.org/rfc/rfc2196.txt.
RFC 2402: IP Authentication Header, www.ietf.org/rfc/rfc2402.txt.
RFC 2406: IP Encapsulating Security Payload (ESP), www.ietf.org/rfc/rfc2406.txt.
Exam Preparation Tasks
Review All Key Topics
Review the most important topics in the chapter, noted with the Key Topic icon in the outer margin of the page. Table 12-12 lists a reference of these key topics and the page numbers on which each is found.

Complete Tables and Lists from Memory
Print a copy of Appendix D, “Memory Tables” (found on the book website), or at least the section for this chapter, and complete the tables and lists from memory. Appendix E, “Memory Tables Answer Key,” also on the website, includes completed tables and lists to check your work.
Define Key Terms
Define the following key terms from this chapter, and check your answers in the glossary:
U.S. Public Company Accounting Reform and Investor Protection Act of 2002
Gramm-Leach-Bliley Financial Services Modernization Act of 1999 (GLBA)
U.S. Health Insurance Portability and Accountability Act (HIPAA)
EU Data Protection Directive 95/46/EC
Adaptive Security Appliance (ASA)
Q&A
The answers to these questions appear in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes and Q&A Questions.” For more practice with exam format questions, use the exam engine on the CD.
1. What technique can be used to protect private information that is transported over the Internet between the headquarters and branch office? (Select the best answer.)
a. Authentication
b. Log all data
c. Encryption
d. Accounting
2. What would be recommended to protect database servers connected to or accessible from the Internet?
a. Firewall
b. Server load balancing (SLB)
c. Syslog
d. SPAN
3. What network security issue does 3DES encryption aim to solve?
a. Data integrity
b. User authentication
c. Data authentication
d. Data confidentiality
4. Users are reporting a DoS attack in the DMZ. All the servers have been patched, and all unnecessary services have been turned off. What else can you do to alleviate some of the attack’s effects? (Select all that apply.)
a. Police traffic on the firewall’s ingress.
b. Use ACLs to let only allowed traffic into the network.
c. Block all TCP traffic from unknown sources.
d. Perform DHCP snooping for the DMZ segment.
5. You are a network engineer for ABC Corp. You need to bring your coworkers up to date on network security threats. What would you discuss with them? (Select all that apply.)
a. Reconnaissance and unauthorized access
b. DHCP snooping
c. DMZ security
d. DoS
6. True or false: IPsec can ensure data integrity and confidentiality across the Internet.
7. What focuses on the accuracy and controls imposed on a company’s financial records?
a. HIPAA
b. GLBA
c. SOX
d. EU Data Protection Directive
8. What are components of managing the security infrastructure? (Select all that apply.)
a. Security management policy
b. Incident-handling policy
c. Network access control policy
d. None of the above
9. Which security legislative body calls for the protection of people’s privacy?
a. HIPAA
b. GLBA
c. EU Data Protection Directive
d. SOX
10. How can attackers obtain sensitive account information? (Select all that apply.)
a. Password-cracking utilities
b. Capturing network traffic
c. Social engineering
d. All of the above
11. What best describes how to protect data’s integrity?
a. System availability
b. Data confidentiality
c. Ensuring that only legitimate users can view sensitive data
d. Allowing only authorized users to modify data
12. What provides an audit trail of network activities?
a. Authentication
b. Accounting
c. Authorization
d. SSHv1
13. What authenticates valid DHCP servers to ensure unauthorized host systems are not interfering with production systems?
a. DHCP options
b. ARP inspection
c. DHCP snooping
d. DHCP reservations
14. What contains the organization’s procedures, guidelines, and standards?
a. Security policy
b. Acceptable use policy
c. Procedure handling
d. Process handling
15. How can you enforce access control? (Select all that apply.)
a. Restrict access using VLANs
b. Restrict access using OS-based controls
c. Use encryption techniques
d. All of the above
16. What is a general user document that is written in simple language to describe the roles and responsibilities within risk management?
a. Security policy
b. Acceptable-use policy
c. Procedure handling
d. Process handling
17. True or false: The network access control policy defines the general access control principles used and how data is classified, such as confidential, top secret, or internal.
18. What are the four steps used to facilitate continuing efforts in maintaining security policies?
a. Secure, monitor, maintain, close out
b. Monitor, test, evaluate, purchase
c. Improve, test, purchase, evaluate
d. Secure, monitor, test, improve
19. Match the encryption keys and VPN protocols with their definitions.
i. IPsec
ii. SSL
iii. Shared secret
iv. PKI
a. Both sides use the same key.
b. Uses AH and ESP.
c. Web browser TCP port 443.
d. Asymmetric cryptography.
20. What does Cisco recommend as the foundation of any deployed security solution?
a. Customer requirements
b. Security audit
c. SLA policy
d. Security policy
21. Which of the following protocols are used for IP security?
a. SSH and EIGRP
b. BGP and TCP
c. AH and ESP
d. SSH and RIP
22. Which security solution best meets requirements for confidentiality, integrity, and authenticity when using the public network such as the Internet?
a. Cisco IOS firewall
b. Intrusion prevention
c. Secure Services
d. AAA
e. Traffic Guard Protector
23. What uses security integrated into routers, switches, and appliances to defend against attacks?
a. Trust and identity management
b. Threat defense
c. Secure Services
d. Cisco SAFE
e. Secure firewalling
24. Encryption and authentication are used to provide secure transport across untrusted networks by providing ________________.
a. Trust and identity management
b. Threat defense
c. Secure Services
d. Cisco SAFE
e. Secure firewalling