Chapter 25
Configure and Verify Access Control Lists
The access control list (ACL) is a critical component of security in the Cisco world and beyond. Keep in mind that an ACL has other uses in Cisco networking, in addition to permitting or denying traffic through an interface for security reasons. For example, you might need to use an ACL to identify certain traffic forms on which you want to perform quality of service (QoS). Also keep in mind ACLs are used in many other forms of technology. For example, in AWS, you work with network ACLs (NACLs), which permit or deny traffic between subnets in your Virtual Private Cloud (VPC). This chapter is therefore very important when studying for the CCNA 200-301 exam.
This chapter covers the following essential terms and components:
▸ Access control list (ACL)
▸ Numbered ACL
▸ Named ACL
▸ Standard ACL
▸ Extended ACL
▸ Wildcard (inverse) mask
▸ Implicit deny all
Topic: Configure, verify, and troubleshoot IPv4 standard numbered and named access lists for routed interfaces
CramSaver
If you can correctly answer these CramSaver questions, save time by skimming the ExamAlerts in this section and then completing the CramQuiz at the end of this section and the Review Questions at the end of the chapter. If you are in doubt at all, read everything in this chapter!
1. What are the ranges possible for a standard numbered access control list (ACL)?
_________
2. What is implied at the end of every ACL?
_________
3. Examine the topology and configurations shown here. Why is R3 unable to ping R1? Be as specific as possible.
_________
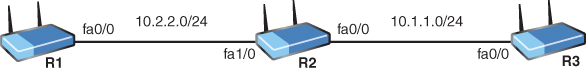
R1# show running-config ... ! hostname R1 ... ! interface FastEthernet0/0 ip address 10.2.2.1 255.255.255.0 ip access-group 1 in duplex half ! ! interface FastEthernet1/0 no ip address shutdown duplex auto speed auto! ! interface FastEthernet1/1 no ip address shutdown duplex auto speed auto ! ! router rip version 2 network 10.0.0.0 no auto-summary ! ... ! access-list 1 permit 10.1.1.0 0.0.0.255 access-list 1 permit 10.2.2.0 0.0.0.255 no cdp log mismatch duplex ! ... ! line con 0 exec-timeout 0 0 privilege level 15 logging synchronous stopbits 1 line aux 0 exec-timeout 0 0 privilege level 15 logging synchronous stopbits 1 line vty 0 4 login ! end R1# R2# show running-config ... ! hostname R2 ! ... ! interface FastEthernet0/0 ip address 10.1.1.2 255.255.255.0 ip access-group 1 in ! ! interface FastEthernet1/0 ip address 10.2.2.2 255.255.255.0 duplex auto speed auto ! ! interface FastEthernet1/1 no ip address shutdown duplex auto speed auto ! ! router rip version 2 network 10.0.0.0 no auto-summary ! ... ! access-list 1 deny 10.1.1.3 access-list 1 permit any no cdp log mismatch duplex ! ... ! line con 0 exec-timeout 0 0 privilege level 15 logging synchronous stopbits 1 line aux 0 exec-timeout 0 0 privilege level 15 logging synchronous stopbits 1 line vty 0 4 login ! end R2# R3# show running-config ... ! hostname R3 ! ... ! interface FastEthernet0/0 ip address 10.1.1.3 255.255.255.0 duplex half ! ! interface FastEthernet1/0 no ip address shutdown duplex auto speed auto ! ! interface FastEthernet1/1 no ip address shutdown duplex auto speed auto ! ! router rip version 2 network 10.0.0.0 no auto-summary ! ... ! line con 0 exec-timeout 0 0 privilege level 15 logging synchronous stopbits 1 line aux 0 exec-timeout 0 0 privilege level 15 logging synchronous stopbits 1 line vty 0 4 login ! end R3#
4. Create a numbered access control entry (ACE) that permits Telnet traffic sourced from a server on network 10.10.10.0/24 destined for network 192.168.1.0/24. Use ACL 101.
_________
Answers
1. Numbered standard ACLs use 1–99 or 1300–1999.
2. An implicit deny all ends an ACL.
3. There is an inbound ACL on R2 Fa0/0 explicitly denying traffic sourced from 10.1.1.3, which is R3’s Fa0/0 interface. Unless R3 uses a loopback interface to source the ping to R1, it will use the Fa0/0 IP address as the source address.
4. access-list 101 permit tcp 10.10.10.0 0.0.0.255 eq 23 192.168.1.0 0.0.0.255
Access control lists (ACLs) are powerful tools for identifying traffic. This chapter examines a specific use of ACLs, based on the CCNA 200-301 exam blueprint: applying ACLs as a security filter to a routed interface.
There are two types of ACLs you need to be aware of:
▸ Standard ACLs: These lists can be named or numbered for identification. If numbered, you must use 1–99 or 1300–1999. Standard ACLs can only match on source IP address. As a result of this very limited matching criterion, Cisco recommends that, in general, standard ACLs be placed as close to the destination of the filtered traffic as possible.
▸ Extended ACLs: These lists can be named or numbered. If numbered, you must use 100–199 or 2000–2699. Extended ACLs can match on a wide variety of criteria, including source and destination IP addresses, protocol type, and specific port numbers. Because there are so many possible filtering criteria, Cisco recommends that, in general, extended ACLs be placed as close to the source of traffic as possible.
Entries in an ACL are called access control entries (ACEs). The order of these entries is critical because packets are processed in a top-down fashion, with a match resulting in the processing of the permit or deny action and the termination of further processing. Example 25.1 shows an example of the construction of a standard ACL that would function as desired if properly assigned to a routed interface. (This configuration is demonstrated later in this section.)
Example 25.1 Building a Standard Numbered ACL
R1#s R1# configure terminal Enter configuration commands, one per line. End with CNTL/Z. R1(config)# access-list 1 deny host 172.16.1.100 R1(config)# access-list 1 deny host 172.16.1.101 R1(config)# access-list 1 permit 172.16.1.0 0.0.0.255 R1(config)# end R1#
Notice in Example 25.1 that the more specific entries are located above the more general entry, so the desired effect of blocking these two specific host source addresses would be achieved by the filter. Notice also the use of a wildcard (or inverse) mask in an access control list. This functions as the opposite of a subnet mask. So, in the entry access-list 1 permit 172.16.1.0 0.0.0.255, you match on the 172.16.1 portion of the address, and any value can appear in the fourth octet.
Notice the use of the keyword host in Example 25.1. This eliminates the requirement for the longer entry access-list 1 deny 172.16.1.100 0.0.0.0. Another shortcut keyword you can use is any. This eliminates entries such as access-list 1 permit 0.0.0.0 255.255.255.255; typing access-list 1 permit any is much easier.
ExamAlert
Every ACL ends with an implicit deny all entry that you cannot see. For this reason, when using an ACL as a routing interface filter, you must have at least one permit statement. Notice also in Example 25.1 that traffic sourced from 10.10.10.1 would be denied as a result of this implicit deny all entry that truly ends the ACL. You are likely to see the deny any log entry used to end an ACL. An administrator uses this entry to track how many packets are reaching the end of the ACL.
Verifying the creation of your ACL is simple, as you can see in Example 25.2.
Example 25.2 Verifying a Standard ACL
R1# R1# show access-list Standard IP access list 1 20 deny 172.16.1.101 10 deny 172.16.1.100 30 permit 172.16.1.0, wildcard bits 0.0.0.255 R1#
Note
You see from the output in Example 25.2 that the Cisco router numbers the entries for you, even though you did not specify sequence numbers during the ACL’s construction. This makes it easier for you to potentially edit an ACL.
Example 25.3 demonstrates the configuration of a standard named ACL.
Example 25.3 Configuring a Standard Named ACL
R1# R1# configure terminal Enter configuration commands, one per line. End with CNTL/Z. R1(config)# ip access-list standard MYACL R1(config-std-nacl)# deny 10.0.0.0 0.255.255.255 R1(config-std-nacl)# permit 192.168.1.0 0.0.0.255 R1(config-std-nacl)# end R1#
Well-constructed ACLs are wonderful, but they’re useless as routing filters unless they are applied to an interface. Example 25.4 demonstrates the assignment of numbered and named ACLs to interfaces.
Example 25.4 Assigning Standard ACLs to Interfaces
R1# R1# configure terminal Enter configuration commands, one per line. End with CNTL/Z. R1(config)# interface fa0/0 R1(config-if)# ip access-group 1 in R1(config-if)# exit R1(config)# interface fa1/0 R1(config-if)# ip access-group MYACL out R1(config-if)# end R1#
As shown in Example 25.4, the ip access-group command is key, regardless of named or numbered ACL assignment. Notice that you must assign the filter for inbound traffic or for outbound traffic on the interface.
ExamAlert
By default, an ACL does not impact traffic generated by the local router. So even if you place an ACL outbound on an interface, by default that ACL does not process or filter locally generated packets such as routing protocol updates. Remember that it is other devices’ routed traffic, moving through a router, that ACLs can filter.
Is there a verification command you can use to see if an ACL is applied to an interface (other than show run, of course)? There is, as demonstrated in Example 25.5.
Example 25.5 Verifying ACL Interface Assignment
R1# R1# show ip interface fa0/0 FastEthernet0/0 is up, line protocol is up Internet address is 10.1.1.1/24 Broadcast address is 255.255.255.255 Address determined by setup command MTU is 1500 bytes Helper address is not set Directed broadcast forwarding is disabled Outgoing access list is not set Inbound access list is 1 Proxy ARP is enabled Local Proxy ARP is disabled ...
In Example 25.5, the show ip interface command verifies that there is an inbound access list set numbered 1. (The rest of this command’s output was trimmed for the sake of brevity.)
Although Example 25.5 is great, what about verifying that an ACL is actually filtering traffic? This is possible with the show access-list command after the filter is assigned to an interface. Example 25.6 shows this. Notice that matches are being logged.
Example 25.6 Using show access-list to Verify Matches
R2#
R2# show access-list
Standard IP access list 1
10 deny 10.1.1.3 (10 matches)
20 permit any
R2#ExamAlert
Even though this topic deals with the specific case of ACLs used as filters, remember that you also used ACLs in Chapter 18, “Configure and Verify Inside Source NAT.” In the case of NAT, ACLs are used to simply identify traffic, not filter it. As stated earlier in this chapter, there are many additional uses for ACLs that are not covered on the CCNA 200-301 exam.
Thanks to extended access control lists, there are many parameters you can match, including the following:
▸ Source IP address
▸ Destination IP address
▸ Protocol
▸ Source port
▸ Destination port
Example 25.7 demonstrates the configuration of an extended ACL.
Example 25.7 Configuring an Extended ACL
R1# R1# configure terminal Enter configuration commands, one per line. End with CNTL/Z. R1(config)# access-list 101 permit tcp 10.10.10.0 0.0.0.255 192.168.1.0 0.0.0.255 eq 23 R1(config)# access-list 101 permit tcp 10.10.10.0 0.0.0.255 192.168.1.0 0.0.0.255 eq 80 R1(config)# access-list 101 permit tcp 10.10.10.0 0.0.0.255 192.168.1.0 0.0.0.255 eq 21 R1(config)# interface gi0/1 R1(config-if)# ip access-group 101 in R1(config-if)# exit R1(config)# exit R1# R1# show access-list Extended IP access list 101 10 permit tcp 10.10.10.0 0.0.0.255 192.168.1.0 0.0.0.255 eq telnet 20 permit tcp 10.10.10.0 0.0.0.255 192.168.1.0 0.0.0.255 eq www 30 permit tcp 10.10.10.0 0.0.0.255 192.168.1.0 0.0.0.255 eq ftp R1#
CramQuiz
1. What ACL correctly denies traffic from 192.168.1.1 while permitting all other traffic?
![]() A. access-list 1 permit 192.168.1.1 0.0.0.0
A. access-list 1 permit 192.168.1.1 0.0.0.0
access-list 1 permit 192.168.1.0 0.0.0.255
![]() B. access-list 1 deny 192.168.1.1 0.0.0.0
B. access-list 1 deny 192.168.1.1 0.0.0.0
access-list 1 permit 192.168.1.0 0.0.0.255
![]() C. access-list 1 deny 192.168.1.1 0.0.0.0
C. access-list 1 deny 192.168.1.1 0.0.0.0
access-list 1 permit any
![]() D. access-list 1 permit any
D. access-list 1 permit any
access-list 1 deny host 192.168.1.1
2. What command would you use to see the matches that an ACL would have?
![]() A. show ip interface
A. show ip interface
![]() B. show ip interface brief
B. show ip interface brief
![]() C. show access-list hits
C. show access-list hits
![]() D. show access-list
D. show access-list
3. What keyword can you use in place of a four-zeros wildcard mask?
![]() A. device
A. device
![]() B. system
B. system
![]() C. host
C. host
![]() D. entry
D. entry
4. What does eq indicate in an ACL?
![]() A. You are matching a port or ports.
A. You are matching a port or ports.
![]() B. You are using a standard ACL in place of an extended ACL.
B. You are using a standard ACL in place of an extended ACL.
![]() C. You are only using one ACE in the ACL.
C. You are only using one ACE in the ACL.
![]() D. Your ACL is not a traffic filter.
D. Your ACL is not a traffic filter.
CramQuiz Answers
1. C is correct. The first entry denies 192.168.1.1, and the second ACE permits all other traffic.
2. D is correct. The show access-list command displays matches once the filter is in place.
3. C is correct. The host keyword allows you to eliminate the wildcard mask entry 0.0.0.0.
4. A is correct. eq is used to match port numbers.
Review Questions
1. What field can a standard ACL filter on?
![]() A. Protocol
A. Protocol
![]() B. Port
B. Port
![]() C. Destination IP
C. Destination IP
![]() D. Source IP
D. Source IP
2. Why might deny any log appear at the end of an ACL?
![]() A. It is used to track traffic that matches no previous ACL entries.
A. It is used to track traffic that matches no previous ACL entries.
![]() B. It is required as the final ACE.
B. It is required as the final ACE.
![]() C. It ensures fast packet processing.
C. It ensures fast packet processing.
![]() D. It is used to send emails to security team members.
D. It is used to send emails to security team members.
3. What command assigns a standard ACL for filtering on an interface?
![]() A. ip access-group in|out
A. ip access-group in|out
![]() B. ip access-bind in|out
B. ip access-bind in|out
![]() C. ip access-list in|out
C. ip access-list in|out
![]() D. ip access-track in|out
D. ip access-track in|out
4. What command permits you to verify that an access list is assigned to an interface in a specific direction?
![]() A. show access-list
A. show access-list
![]() B. show access-list interface
B. show access-list interface
![]() C. show ip interface
C. show ip interface
![]() D. show access-list assign
D. show access-list assign
Answers to Review Questions
1. D is correct. A standard ACL can filter on source IP address only.
2. A is correct. This is matched before the implicit deny all. An explicit deny all is used for tracking entries that match the end of the list.
3. A is correct. You use the ip access-group command in this case.
4. C is correct. You use show ip interface to verify assignment of ACLs to interfaces.
Hands-On Lab Practice Assignment
Configuring ACLs
To complete this Hands-On Lab Practice Assignment, download the assigned Packet Tracer file from the book’s companion website and perform the lab on your locally installed version of Packet Tracer. For instructions on how to download and use the Packet Tracer files, see “Packet Tracer Hands-On Lab Practice Assignments” in the Introduction of this book.
Additional Resources
How to Configure Extended ACL Cisco
https://www.youtube.com/watch?v=OD0y4YJGFcQ
Configuring IP Access Lists
https://www.cisco.com/c/en/us/support/docs/security/ios-firewall/23602-confaccesslists.html?referring_site=RE&pos=2&page=http://www.cisco.com/c/en/us/td/docs/ios/12_2/security/configuration/guide/fsecur_c/scfreflx.html
