Chapter 15. The Incident Response Process
This chapter covers the following topics related to Objective 4.1 (Explain the importance of the incident response process) of the CompTIA Cybersecurity Analyst (CySA+) CS0-002 certification exam:
• Communication plan: Describes the proper incident response processes for communication during an incident, which includes limiting communications to trusted parties, disclosing based on regulatory/legislative requirements, preventing inadvertent release of information, using a secure method of communication, and reporting requirements
• Response coordination with relevant entities: Describes the entities with which coordination is required during an incident, including legal, human resources, public relations, internal and external, law enforcement, senior leadership, and regulatory bodies
• Factors contributing to data criticality: Identifies factors that determine the criticality of an information resource, which include personally identifiable information (PII), personal health information (PHI), sensitive personal information (SPI), high value asset, financial information, intellectual property, and corporate information
The incident response process is a formal approach to responding to security issues. It attempts to avoid the haphazard approach that can waste time and resources. This chapter and the next chapter examine this process.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz enables you to assess whether you should read the entire chapter. If you miss no more than one of these six self-assessment questions, you might want to skip ahead to the “Exam Preparation Tasks.” Table 15-1 lists the major headings in this chapter and the “Do I Know This Already?” quiz questions covering the material in those headings so that you can assess your knowledge of these specific areas. The answers to the “Do I Know This Already?” quiz appear in Appendix A.
Table 15-1 “Do I Know This Already?” Foundation Topics Section-to-Question Mapping

1. Which of the following is false with respect to the incident response communication plan?
a. Organizations in certain industries may be required to comply with regulatory or legislative requirements with regard to communicating data breaches.
b. Content of these communications should include as much information as possible.
c. All responders should act to prevent the disclosure of any information to parties that are not specified in the communication plan.
d. All communications that takes place between the stakeholders should use a secure communication process.
2. Which of the following HIPAA rules requires covered entities and their business associates to provide notification following a breach of unsecured PHI?
a. Breach Notification Rule
b. Privacy Rule
c. Security Rule
d. Enforcement Rule
3. Which of the following is responsible for reviewing NDAs to ensure support for incident response efforts?
a. Human resources
b. Legal
c. Management
d. Public relations
4. Which of the following is responsible for developing all written responses to the outside world concerning an incident and its response?
a. Human resources
b. Legal
c. Management
d. Public relations
5. Which of the following is any piece of data that can be used alone or with other information to identify a single person?
a. Intellectual property
b. Trade secret
c. PII
d. PPP
6. Which of the following is not intellectual property?
a. Patent
b. Trade secret
c. Trademark
d. Contract
Foundation Topics
Communication Plan
Over time, best practices have evolved for handling the communication process between stakeholders. By following these best practices, you have a greater chance of maintaining control of the process and achieving the goals of incident response. Failure to follow these guidelines can lead to lawsuits, the premature alerting of the suspected party, potential disclosure of sensitive information, and, ultimately, an incident response process that is less effective than it could be.
Limiting Communication to Trusted Parties
During an incident, communications should take place only with those who have been designated beforehand to receive such communications. Moreover, the content of these communications should be limited to what is necessary for each stakeholder to perform his or her role.
Disclosing Based on Regulatory/Legislative Requirements
Organizations in certain industries may be required to comply with regulatory or legislative requirements with regard to communicating data breaches to affected parties and to those agencies and legislative bodies promulgating these regulations. The organization should include these communication types in the communication plan.
Preventing Inadvertent Release of Information
All responders should act to prevent the disclosure of any information to parties that are not specified in the communication plan. Moreover, all information released to the public and the press should be handled by public relations or persons trained for this type of communication. The timing of all communications should also be specified in the plan.
Using a Secure Method of Communication
All communications that take place between the stakeholders should use a secure communication process to ensure that information is not leaked or sniffed. Secure communication channels and strong cryptographic mechanisms should be used for these communications. The best approach is to create an out-of-band method of communication, which does not use the regular methods of corporate e-mail or VoIP. While personal cell phones can be a method for voice communication, file and data exchange should be through a method that provides end-to-end encryption, such as Off-the-Record (OTR) Messaging.
Reporting Requirements
Beyond the communication requirements within the organization, there may be legal obligations to report to agencies or governmental bodies during and following a security incident. Especially when sensitive customer, vendor, or employee records are exposed, organizations are required to report this is a reasonable time frame.
For example, in the healthcare field, the HIPAA Breach Notification Rule, 45 CFR §§ 164.400-414, requires HIPAA covered entities and their business associates to provide notification following a breach of unsecured protected health information (PHI). As another example, all 50 states, the District of Columbia, Guam, Puerto Rico, and the Virgin Islands have enacted legislation requiring private or governmental entities to notify individuals of security breaches of information involving personally identifiable information (PII). PHI and PII are described in more detail later in this chapter.
Response Coordination with Relevant Entities
During an incident, proper communication among the various stakeholders in the process is critical to the success of the response. One key step that helps ensure proper communication is to select the right people for the incident response (IR) team. Because these individuals will be responsible for communicating with stakeholders, communication skills should be a key selection criterion for the IR team. Moreover, this team should take the following steps when selecting individuals to represent each stakeholder community:

• Select representatives based on communication skills.
• Hold regular meetings.
• Use proper escalation procedures.
The following sections identify these stakeholders, discuss why the communication process is important, describe best practices for the communication process, and list the responsibilities of various key roles involved in the response.
Legal
The role of the legal department is to do the following:

• Review nondisclosure agreements (NDAs) to ensure support for incident response efforts.
• Develop wording of documents used to contact possibly affected sites and organizations.
• Assess site liability for illegal computer activity.
Human Resources
The role of the HR department involves the following responsibilities in response:

• Develop job descriptions for those persons who will be hired for positions involved in incident response.
• Create policies and procedures that support the removal of employees found to be engaging in improper or illegal activity.
For example, HR should ensure that these activities are spelled out in policies and new hire documents as activities that are punishable by firing. This can help avoid employment disputes when the firing occurs.
Public Relations
The role of public relations is managing the dialog between the organization and the outside world. One person should be designated to do all talking to the media so as to maintain a consistent message. Responsibilities of the PR department include the following:

• Handling all press conferences that may be held
• Developing all written response to the outside world concerning the incident and its response
Internal and External
Most of the stakeholders will be internal to the organization but not all. External stakeholders (law enforcement, industry organizations, and media) should be managed separately from the internal stakeholders. Communications to external stakeholders may require a different and more secure medium.
Law Enforcement
Law enforcement may become involved in many incidents. Sometimes they are required to become involved, but in many instances, the organization is likely to invite law enforcement to get involved. When making a decision about whether to involve law enforcement, consider the following factors:

• Law enforcement will view the incident differently than the company security team views it. While your team may be more motivated to stop attacks and their damage, law enforcement may be inclined to let an attack proceed in order to gather more evidence.
• The expertise of law enforcement varies. While contacting local law enforcement may be indicated for physical theft of computers and similar incidents, involving law enforcement at the federal level, where greater skill sets are available, may be indicated for more abstract crimes and events. The USA PATRIOT Act enhanced the investigatory tools available to law enforcement and expanded their ability to look at e-mail communications, telephone records, Internet communications, medical records, and financial records, which can be helpful.
• Before involving law enforcement, try to rule out other potential causes of an event, such as accidents and hardware or software failure.
• In cases where laws have obviously been broken (child pornography, for example), immediately get law enforcement involved. This includes any felonies, regardless of how small the loss to the company may have been.
Senior Leadership
The most important factor in the success of an incident response plan is the support, both verbal and financial (through the budget process), of senior leadership. Moreover, all other levels of management should fall in line with support of all efforts. Specifically, senior leadership’s role involves the following:

• Communicate the importance of the incident response plan to all parts of the organization.
• Create agreements that detail the authority of the incident response team to take over business systems if necessary.
• Create decision systems for determining when key systems must be removed from the network
Regulatory Bodies
Earlier in this chapter you learned that there are reporting requirements to certain governmental bodies when a data breach occurs. This makes these agencies external stakeholders. Be aware of reporting requirements based on the industry in which the organization operates. An incident response should be coordinated with any regulatory bodies that regulate the industry in which the organization operates.
Factors Contributing to Data Criticality
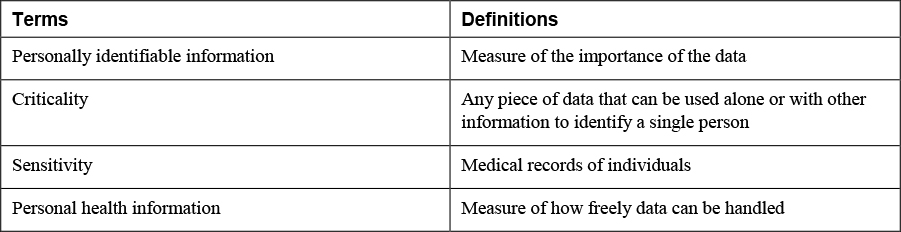
Sensitivity is a measure of how freely data can be handled. Some data requires special care and handling, especially when inappropriate handling could result in penalties, identity theft, financial loss, invasion of privacy, or unauthorized access by an individual or many individuals. Some data is also subject to regulation by state or federal laws and requires notification in the event of a disclosure.
Data is assigned a level of sensitivity based on who should have access to it and how much harm would be done if it were disclosed. This assignment of sensitivity is called data classification.
Criticality is a measure of the importance of the data. Data considered sensitive may not necessarily be considered critical. Assigning a level of criticality to a particular data set must take into consideration the answer to a few questions:

• Will you be able to recover the data in case of disaster?
• How long will it take to recover the data?
• What is the effect of this downtime, including loss of public standing?
Data is considered critical when it is essential to the organization’s business. When essential data is not available, even for a brief period of time, or its integrity is questionable, the organization is unable to function. Data is considered critical when it is important to the organization but organizational operations can continue for a predetermined period of time even if the data is not available. Data is considered nonessential if the organization is able to operate without it during extended periods of time.
Once the sensitivity and criticality of data are understood and documented, the organization should work to create a data classification system. Most organizations use either a commercial business classification system or a military and government classification system.
To properly categorize data types, a security analyst should be familiar with some of the most sensitive types of data that the organization may possess.
When responding to an incident the criticality of the data at risk should be a prime consideration when assigning resources to the incident. When the data at risk is more critical, the more resources should be assigned to the issue, because it becomes more important that time is of the essence to identify and correct any settings or policies that are implicated in the incident.
Personally Identifiable Information (PII)
When considering technology and its use today, privacy is a major concern of users. This privacy concern usually involves three areas: which personal information can be shared with whom, whether messages can be exchanged confidentially, and whether and how one can send messages anonymously. Privacy is an integral part of any security measures that an organization takes.

As part of the security measures that organizations must take to protect privacy, personally identifiable information (PII) must be understood, identified, and protected. PII is any piece of data that can be used alone or with other information to identify a single person. Any PII that an organization collects must be protected in the strongest manner possible. PII includes full name, identification numbers (including driver’s license number and Social Security number), date of birth, place of birth, biometric data, financial account numbers (both bank account and credit card numbers), and digital identities (including social media names and tags).
Keep in mind that different countries and levels of government can have different qualifiers for identifying PII. Security professionals must ensure that they understand international, national, state, and local regulations and laws regarding PII. As the theft of this data becomes even more prevalent, you can expect more laws to be enacted that will affect your job. Figure 15-1 shows examples of PII.
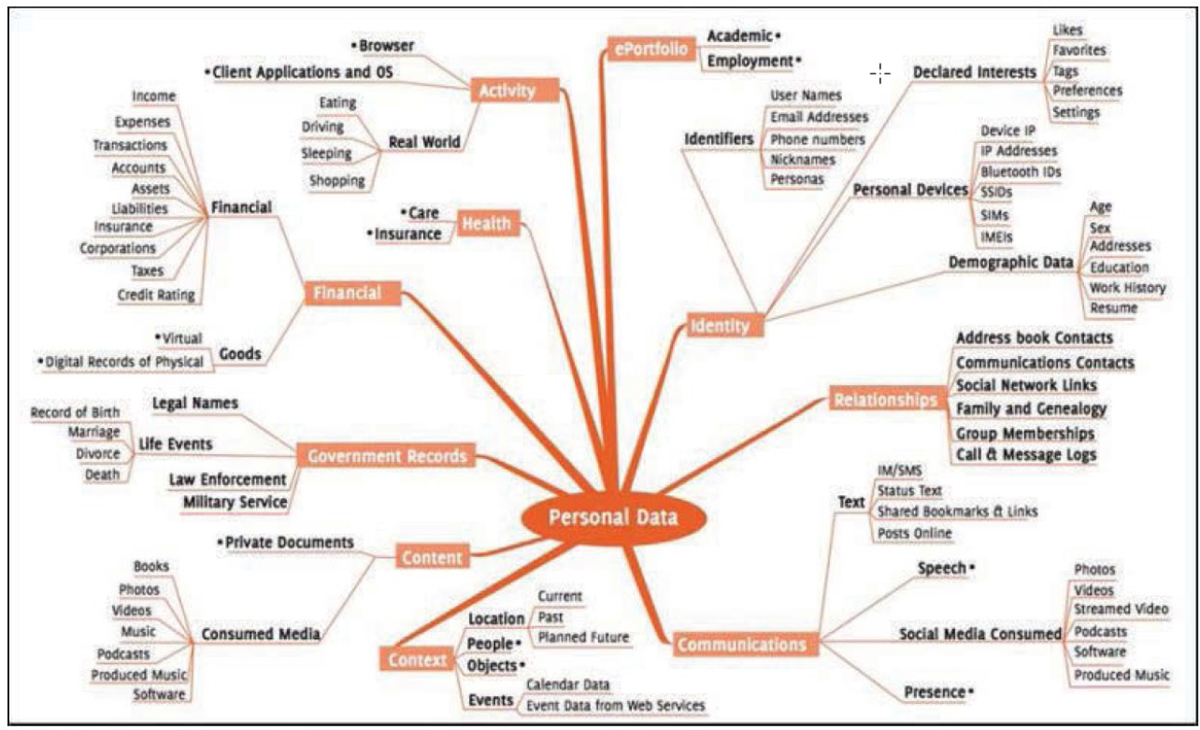
Figure 15-1 Personally Identifiable Information
The most obvious reaction to the issue of privacy is the measures in the far-reaching EU General Data Protection Regulation (GDPR) The GDPR aims primarily to give control to individuals over their personal data and to simplify the regulatory environment for international business by unifying the regulation within the EU.
Personal Health Information (PHI)
One particular type of PII that an organization might possess is personal health information (PHI). PHI includes the medical records of individuals and must be protected in specific ways, as prescribed by the regulations contained in the Health Insurance Portability and Accountability Act of 1996 (HIPAA). HIPAA, also known as the Kennedy-Kassebaum Act, affects all healthcare facilities, health insurance companies, and healthcare clearinghouses. It is enforced by the Office for Civil Rights (OCR) of the Department of Health and Human Services (HHS). It provides standards and procedures for storing, using, and transmitting medical information and healthcare data. HIPAA overrides state laws unless the state laws are stricter. Additions to this law now extend its requirements to third parties that do work for covered organizations in which those parties handle this information.
Note
Objective 4.1 of the CySA+ exam refers to PHI as personal health information, whereas HIPAA refers to it as protected health information.
Sensitive Personal Information (SPI)
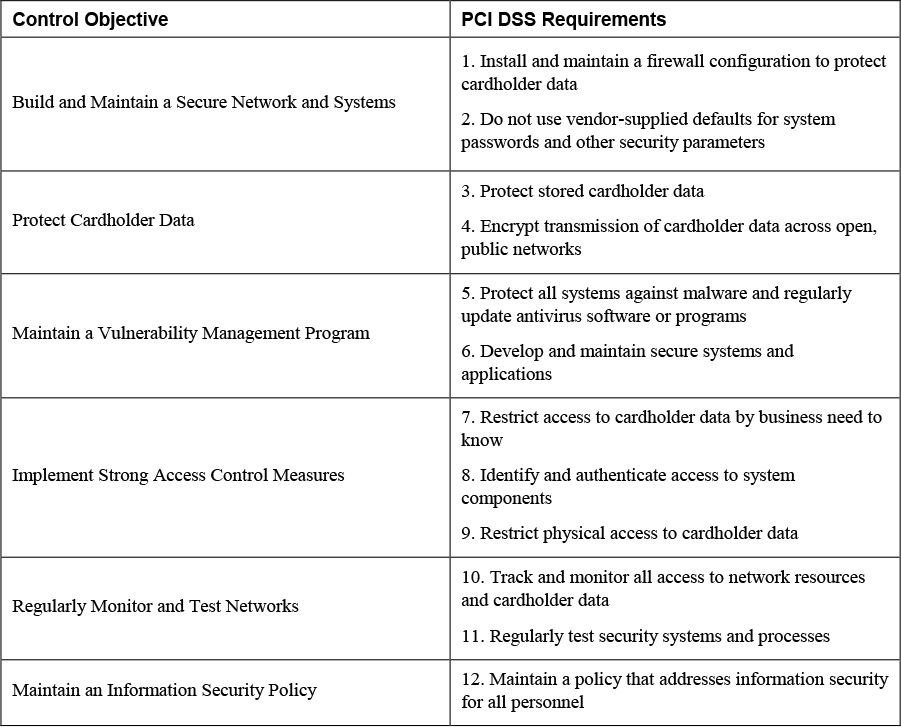
Some types of information should receive special treatment, and certain standards have been designed to protect this information. This type of data is called sensitive personal information (SPI). The best example of this is credit card information. Almost all companies possess and process credit card data. Holders of this data must protect it. Many of the highest-profile security breaches that have occurred have involved the theft of this data. The Payment Card Industry Data Security Standard (PCI DSS) affects any organizations that handle cardholder information for the major credit card companies. The latest version at the time of writing is 3.2.1. To prove compliance with the standard, an organization must be reviewed annually. Although PCI DSS is not a law, this standard has affected the adoption of several state laws. PCI DSS specifies 12 requirements, listed in Table 15-2.

Table 15-2 Control Objectives of PCI DSS
High Value Asset
Some assets are not actually information but systems that provide access to information. When these systems or groups of systems provide access to data required to continue to do business, they are called critical systems. While it is somewhat simpler to arrive at a value for physical assets such as servers, routers, switches, and other devices, in cases where these systems provide access to critical data or are required to continue a business-critical process, their value is more than the replacement cost of the hardware. The assigned value should be increased to reflect its importance in providing access to data or its role in continuing a critical process.
Financial Information
Financial and accounting data in today’s networks is typically contained in accounting information systems (AISs). While these systems offer valuable integration with other systems, such as HR and customer relationship management systems, this integration comes at the cost of creating a secure connection between these systems. Many organizations are also abandoning legacy accounting software for cloud-based vendors to maximize profit. Cloud arrangements bring their own security issues, such as the danger of data comingling in the multitenancy environment that is common in public clouds. Moreover, considering that a virtual infrastructure underlies these cloud systems, all the dangers of the virtual environment come into play.
Considering the criticality of this data and the need of the organization to keep the bulk of it confidential, incidents that target this type of information or the systems that provide access to this data should be given high priority. The following steps should be taken to protect this information:

• Always ensure physical security of the building.
• Ensure that a firewall is deployed at the perimeter and make use of all its features, such as URL and application filtering, intrusion prevention, antivirus scanning, and remote access via virtual private networks and TLS/SSL encryption.
• Diligently audit file and folder permissions on all server resources.
• Encrypt all accounting data.
• Back up all accounting data and store it on servers that use redundant technologies such as RAID.
Intellectual Property
Intellectual property is a tangible or intangible asset to which the owner has exclusive rights. Intellectual property law is a group of laws that recognize exclusive rights for creations of the mind. The intellectual property covered by this type of law includes the following:

• Patents
• Trade secrets
• Trademarks
• Copyrights
The following sections explain these types of intellectual properties and their internal protection.
Patent
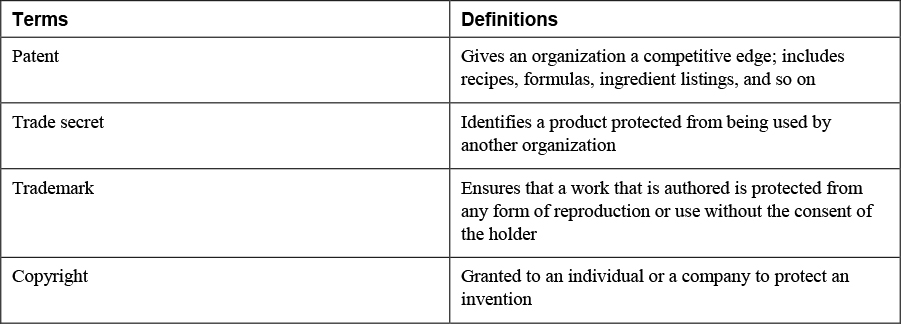
A patent is granted to an individual or a company to protect an invention that is described in the patent’s application. When the patent is granted, only the patent owner can make, use, or sell the invention for a period of time, usually 20 years. Although a patent is considered one of the strongest intellectual property protections available, the invention becomes public domain after the patent expires, thereby allowing any entity to manufacture and sell the product.
Patent litigation is common in today’s world. You commonly see technology companies, such as Apple, HP, and Google, filing lawsuits regarding infringement on patents (often against each other). For this reason, many companies involve a legal team in patent research before developing new technologies. Being the first to be issued a patent is crucial in today’s highly competitive market.
Any product that is produced and is currently undergoing the patent application process is usually identified with the Patent Pending seal, shown in Figure 15-2.

Figure 15-2 Patent Pending Seal
Trade Secret
A trade secret ensures that proprietary technical or business information remains confidential. A trade secret gives an organization a competitive edge. Trade secrets include recipes, formulas, ingredient listings, and so on that must be protected against disclosure. After a trade secret is obtained by or disclosed to a competitor or the general public, it is no longer considered a trade secret. Most organizations that have trade secrets attempt to protect them by using nondisclosure agreements (NDAs). An NDA must be signed by any entity that has access to information that is part of a trade secret. Anyone who signs an NDA will suffer legal consequences if the organization is able to prove that the signer violated it.
Trademark
A trademark ensures that a symbol, a sound, or an expression that identifies a product or an organization is protected from being used by another organization. A trademark allows a product or an organization to be recognized by the general public. Most trademarks are marked with one of the designations shown in Figure 15-3. If a trademark is not registered, an organization should use a capital TM. If the trademark is registered, an organization should use a capital R that is encircled.

Figure 15-3 Trademark Designations
Copyright
A copyright ensures that a work that is authored is protected from any form of reproduction or use without the consent of the copyright holder, usually the author or artist who created the original work. A copyright lasts longer than a patent.
Although the U.S. Copyright Office has several guidelines to determine the amount of time a copyright lasts, the general rule for works created after January 1, 1978, is the life of the author plus 70 years. In 1996, the World Intellectual Property Organization (WIPO) standardized the treatment of digital copyrights. Copyright management information (CMI) is licensing and ownership information that is added to any digital work. In this standardization, WIPO stipulated that CMI included in copyrighted material cannot be altered. The [cw] symbol denotes a work that is copyrighted.
Securing Intellectual Property
Intellectual property of an organization, including patents, copyrights, trademarks, and trade secrets, must be protected, or the business loses any competitive advantage created by such properties. To ensure that an organization retains the advantages given by its IP, it should do the following:

• Invest in well-written NDAs to be included in employment agreements, licenses, sales contracts, and technology transfer agreements.
• Ensure that tight security protocols are in place for all computer systems.
• Protect trade secrets residing in computer systems with encryption technologies or by limiting storage to computer systems that do not have external Internet connections.
• Deploy effective insider threat countermeasures, particularly focused on disgruntlement detection and mitigation techniques.
Corporate Information
Corporate confidential data is anything that needs to be kept confidential within the organization. This can include the following:

• Plan announcements
• Processes and procedures that may be unique to the organization
• Profit data and estimates
• Salaries
• Market share figures
• Customer lists
• Performance appraisal
Exam Preparation Tasks
As mentioned in the section “How to Use This Book” in the Introduction, you have several choices for exam preparation: the exercises here, Chapter 22, “Final Preparation,” and the exam simulation questions in the Pearson Test Prep Software Online.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 15-3 lists a reference of these key topics and the page numbers on which each is found.

Table 15-3 Key Topics
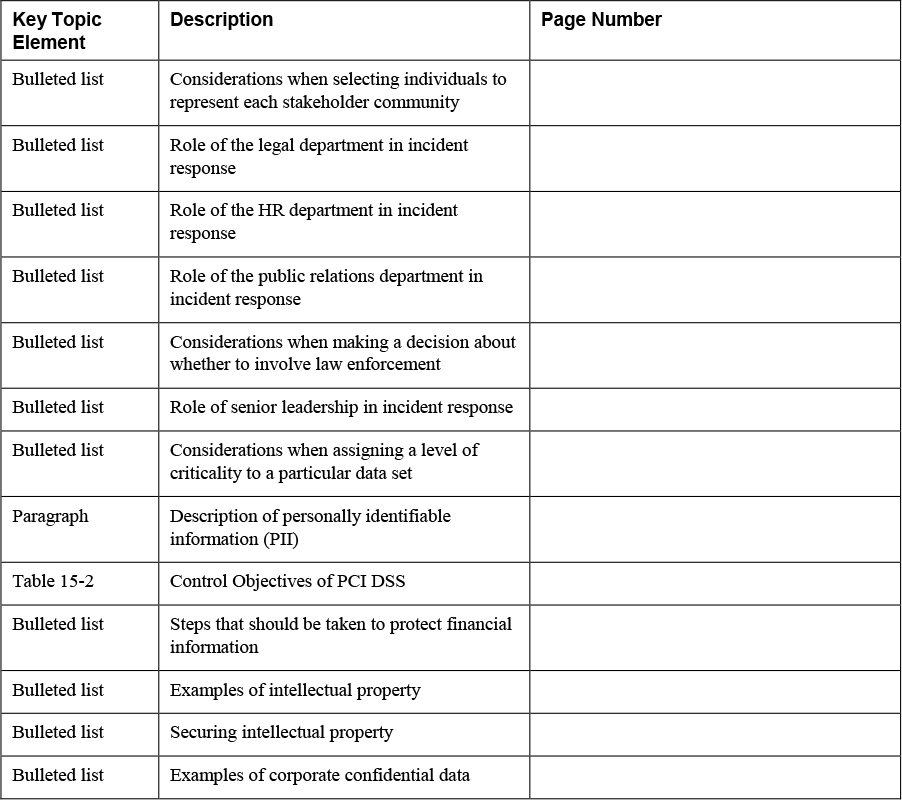
Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
HIPAA Breach Notification Rule
personally identifiable information (PII)
personal health information (PHI)
sensitive personal information (SPI)
Payment Card Industry Data Security Standard (PCI DSS)
Review Questions
1. After a breach, all information released to the public and the press should be handled by _________________.
2. List at least one job of the human resources department with regard to incident response.
3. Match the following terms with their definitions
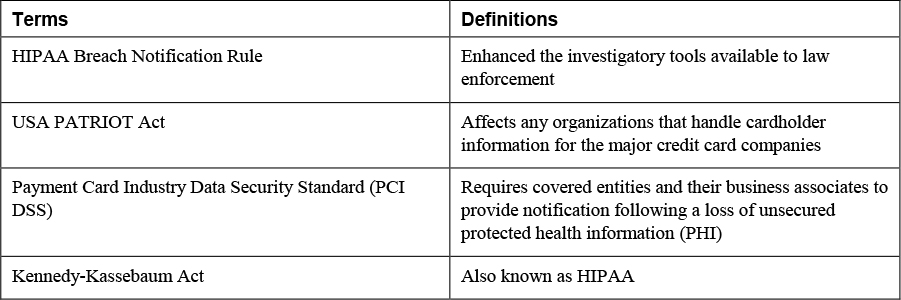
4. It is the role of ____________________ to develop job descriptions for those persons who will be hired for positions involved in incident response.
5. List at least one of the roles of senior leadership in incident response.
6. Match the following terms with their definitions.
7. The most important factor in the success of an incident response plan is the support, both verbal and financial (through the budget process), of ________________
8. List at least one consideration when assigning a level of criticality.
9. Match the following terms with their definitions.
10. Salaries of employees is considered ______________________________________________
