Chapter 21. The Importance of Frameworks, Policies, Procedures, and Controls
This chapter covers the following topics related to Objective 5.3 (Explain the importance of frameworks, policies, procedures, and controls) of the CompTIA Cybersecurity Analyst (CySA+) CS0-002 certification exam:
• Frameworks: Covers both risk-based and prescriptive frameworks
• Policies and procedures: Includes code of conduct/ethics, acceptable use policy (AUP), password policy, data ownership, data retention, account management, continuous monitoring, and work product retention
• Category: Describes the managerial, operational, technical categories
• Control type: Covers the preventative, detective, corrective, deterrent, compensating, and physical control types
• Audits and assessments: Discusses regulatory and compliance audits
Organizations use policies, procedures, and controls to implement security. Policies are broad statements that define what the aim of the security measure is, while procedures define how to carry out the measures. Controls are countermeasures or mitigations that are used to prevent breaches. Creating and implementing policies, procedures, and controls can be a challenge. Help is available, however, from security frameworks created by various entities. Help is available through templates, examples, and other documents that organizations can use to ensure that they have covered all bases. This chapter explains what policies, procedures, and controls are and describes how security frameworks can be used to create them.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz enables you to assess whether you should read the entire chapter. If you miss no more than one of these eight self-assessment questions, you might want to move ahead to the “Exam Preparation Tasks.” Table 21-1 lists the major headings in this chapter and the “Do I Know This Already?” quiz questions covering the material in those headings so you can assess your knowledge of these specific areas. The answers to the “Do I Know This Already?” quiz appear in Appendix A.
Table 21-1 “Do I Know This Already?” Foundation Topics Section-to-Question Mapping

1. Which of the following is not one of the four interrelated domains of the Open Group Architecture Framework (TOGAF) four interrelated domains?
a. Business architecture
b. Data architecture
c. Security architecture
d. Technology architecture
2. Which of the following is not one of the classes of controls described by NIST SP 800-53 Rev 4?
a. Access Control
b. Awareness and Training
c. Contingency Planning
d. Facility Security
3. Which of the following policies is intended to demonstrate a commitment to ethics?
a. Non-compete
b. Non-disclosure
c. Expectation of privacy
d. Code of conduct
4. Which of the following consists of single words that often include a mixture of upper- and lowercase letters?
a. Standard word passwords
b. Complex passwords
c. Passphrase passwords
d. Cognitive passwords
5. Which of the following controls are implemented to administer the organization’s assets and personnel and include security policies, procedures, standards, baselines, and guidelines that are established by management?
a. Managerial
b. Physical
c. Technical
d. Logical
6. Which operational control type would include security guards?
a. Detective
b. Preventative
c. Deterrent
d. Directive
7. Which of the following reports on internal controls over financial reporting?
a. SOC 1
b. SOC 2
c. SOC 3
d. SOC 4
8. Which of the following standards verifies the controls and processes and requires a written assertion regarding the design and operating effectiveness of the controls being reviewed?
a. SSAE
b. HIPAA
c. GLBA
d. CFAA
9. When you implement a new password policy what category of control have you implemented?
a. Managerial
b. Operational
c. Technical
d. Preventative
10. Which of the following controls is a directive control?
a. A new firewall
b. A policy forbidding USB drives
c. A No Admittance sign at the server room door
d. A biometric authentication system
Foundation Topics
Frameworks
Many organizations have developed security management frameworks and methodologies to help guide security professionals. These frameworks and methodologies include security program development standards, enterprise and security architect development frameworks, security control development methods, corporate governance methods, and process management methods. The following sections discuss the major frameworks and methodologies and explain where they are used.
Risk-Based Frameworks
Some frameworks are designed to help organizations organize their approach and response to risk. Frameworks in this section are risk-based.
National Institute of Standards and Technology (NIST)
NIST SP 800-53 Rev 4 is a security controls development framework developed by the NIST body of the U.S. Department of Commerce. Table 21-2 lists the NIST SP 800-53 Rev 44 control families.

Table 21-2 NIST SP 800-53 Rev 4 Control Families

NIST SP 800-55 Rev 1 is an information security metrics framework that provides guidance on developing performance measuring procedures with a U.S. government viewpoint.
COBIT
The governance and management objectives in COBIT 2019 are grouped into five domains. The domains have names with verbs that express the key purpose and areas of activity of the objectives contained in them. The five domain are
• Evaluate, Direct, and Monitor (EDM)
• Align, Plan, and Organize (APO)
• Build, Acquire, and Implement (BAI)
• Deliver, Service, and Support (DSS)
• Monitor, Evaluate, and Assess (MEA)
The Cobit 2019 Goals Cascade (shown in Figure 21-1) supports translation of enterprise goals into priorities for alignment goals.

Figure 21-1 The Cobit 2019 Goals Cascade
The Open Group Architecture Framework (TOGAF)
The Open Group Architecture Framework (TOGAF), another enterprise architecture framework, helps organizations design, plan, implement, and govern an enterprise information architecture. The latest version, TOGAF 9.2, was launched in 2018. TOGAF is based on

• Business architecture: Business strategy, governance, organization, and key business processes
• Application architecture: Individual systems to be deployed, interactions between the application systems, and their relationships to the core business processes
• Data architecture: Structure of an organizations logical and physical data assets
• Technology architecture: Hardware, software, and network infrastructure
The Architecture Development Method (ADM), as prescribed by TOGAF, is applied to develop an enterprise architecture that meets the business and information technology needs of an organization. Figure 21-2 shows the process, which is iterative and cyclic. Each step checks with requirements.


Figure 21-2 TOGAF ADM Model
Prescriptive Frameworks
Some frameworks are designed to provide organizations with a list of activities that comprise a prescription for handling certain security issues common to all. The frameworks described in this section are prescriptive.
NIST Cybersecurity Framework Version 1.1
NIST created the Framework for Improving Critical Infrastructure Cybersecurity, or simply the NIST Cybersecurity Framework version 1.1, in 2018. It focuses exclusively on IT security and is composed of three parts:

• Framework Core: The core presents five cybersecurity functions, each of which is further divided into categories and subcategories. It describes desired outcomes for these functions. As you can see in Figure 21-3, each function has informative references available to help guide the completion of that subcategory of a particular function.
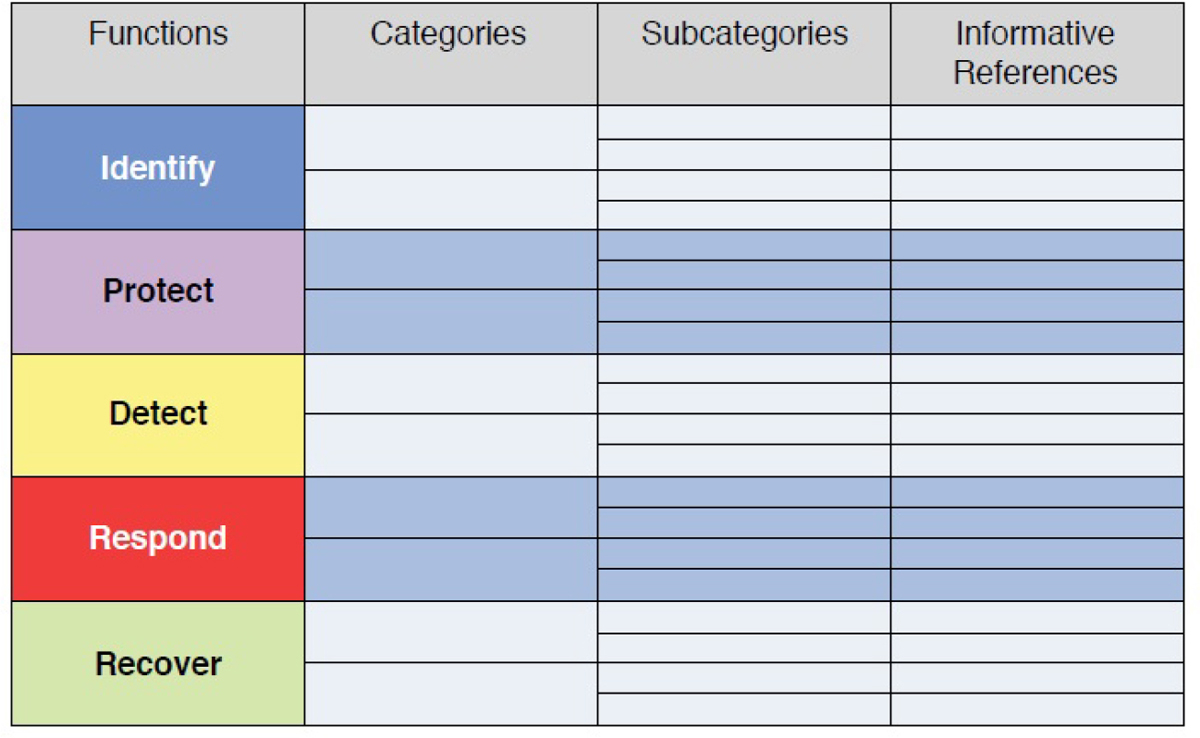
Figure 21-3 Framework Core Structure
• Implementation Tiers: These tiers are levels of sophistication in the risk management process that organizations can aspire to reach. These tiers can be used as milestones in the development of an organization’s risk management process. The four tiers, from least developed to most developed, are Partial, Risk Informed, Repeatable, and Adaptive.
• Framework Profiles: Profiles can be used to compare the current state (or profile) to a target state (profile). This enables an organization to create an action plan to close gaps between the two.
ISO 27000 Series
The International Organization for Standardization (ISO), often incorrectly referred to as the International Standards Organization, joined with the International Electrotechnical Commission (IEC) to standardize the British Standard 7799 (BS7799) to a new global standard that is now referred to as the ISO/IEC 27000 Series. ISO/IEC 27000 is a security program development standard on how to develop and maintain an information security management system (ISMS).
The 27000 Series includes a list of standards, each of which addresses a particular aspect of ISMS. These standards are either published or in development. The following standards are included as part of the ISO/IEC 27000 Series at this writing:

• 27000: Published overview of ISMS and vocabulary
• 27001: Published ISMS requirements
• 27002: Published code of practice for information security controls
• 27003: Published ISMS implementation guidelines
• 27004: Published ISMS measurement guidelines
• 27005: Published information security risk management guidelines
• 27006: Published requirements for bodies providing audit and certification of ISMS
• 27007: Published ISMS auditing guidelines
• 27008: Published auditor of ISMS guidelines
• 27010: Published information security management for inter-sector and interorganizational communications guidelines
• 27011: Published telecommunications organizations information security management guidelines
• 27013: Published integrated implementation of ISO/IEC 27001 and ISO/IEC 20000-1 guidance
• 27014: Published information security governance guidelines
• 27015: Published financial services information security management guidelines
• 27016:TR 27016 Information security economics
• 27017: In-development cloud computing services information security control guidelines based on ISO/IEC 27002
• 27018: Published code of practice for protection of personally identifiable information (PII) in public clouds acting as PII processors
• 27019: Published energy industry process control system ISMS guidelines based on ISO/IEC 27002
• 27021: Published competence requirements for information security management systems professionals
• 27023: Published mapping the revised editions of ISO/IEC 27001 and ISO/ IEC 27002
• 27031: Published information and communication technology readiness for business continuity guidelines
• 27032: Published cybersecurity guidelines
• 27033-1: Published network security overview and concepts
• 27033-2: Published network security design and implementation guidelines
• 27033-3: Published network security threats, design techniques, and control issues guidelines
• 27033-4: Published securing communications between networks using security gateways
• 27033-5: Published securing communications across networks using virtual private networks (VPN)
• 27033-6: In-development securing wireless IP network access
• 27034-1: Published application security overview and concepts
• 27034-2: In-development application security organization normative framework guidelines
• 27034-3: In-development application security management process guidelines
• 27034-4: In-development application security validation guidelines
• 27034-5: In-development application security protocols and controls data structure guidelines
• 27034-6: In-development security guidance for specific applications
• 27034-7: In-development guidance for application security assurance prediction
• 27035: Published information security incident management guidelines
• 27035-1: In-development information security incident management principles
• 27035-2: In-development information security incident response readiness guidelines
• 27035-3: In-development computer security incident response team (CSIRT) operations guidelines
• 27036-1: Published information security for supplier relationships overview and concepts
• 27036-2: Published information security for supplier relationships common requirements guidelines
• 27036-3: Published information and communication technology (ICT) supply chain security guidelines
• 27036-4: In-development guidelines for security of cloud services
• 27037: Published digital evidence identification, collection, acquisition, and preservation guidelines
• 27038: Published information security digital redaction specification
• 27039: Published intrusion detection systems (IDS) selection, deployment, and operations guidelines
• 27040: Published storage security guidelines
• 27041: Published guidance on assuring suitability and adequacy of incident investigative method
• 27042: Published digital evidence analysis and interpretation guidelines
• 27043: Published incident investigation principles and processes
• 27044: In-development security information and event management (SIEM) guidelines
• 27050: In-development electronic discovery (eDiscovery) guidelines
• 27799: Published information security in health organizations guidelines
These standards are developed by the ISO/IEC bodies, but certification or conformity assessment is provided by third parties.
SABSA
SABSA is an enterprise security architecture framework that uses the six communication questions (What, Where, When, Why, Who, and How) that intersect with six layers (operational, component, physical, logical, conceptual, and contextual). It is a risk-driven architecture. See Table 21-3.

Table 21-3 SABSA Framework Matrix

IITIL
ITIL is a process management development standard developed by the Office of Management and Budget in OMB Circular A-130 and owned by AXELOS since 2013. ITIL has five core publications: ITIL Service Strategy, ITIL Service Design, ITIL Service Transition, ITIL Service Operation, and ITIL Continual Service Improvement. These five core publications contain 26 processes. Although ITIL has a security component, it is primarily concerned with managing the service-level agreements (SLAs) between an IT department or organization and its customers. An independent review of security controls should be performed every three years. Table 21-4 shows the ITIL v4 key components, ITIL service value system (SVS), and the four dimensions model.

Table 21-4 ITIL Version 4 Service Value System

Maturity Models
Organizations are not alone in the wilderness when it comes to developing processes for assessing vulnerability, selecting controls, adjusting security policies and procedures to support those controls, and performing audits. As describe in the sections that follow, several publications and process models have been developed to help develop these skills. Maturity models are used to determine where you are in the continual improvement process as it relates to security and offer help in reaching a higher level of improvement.
CMMI
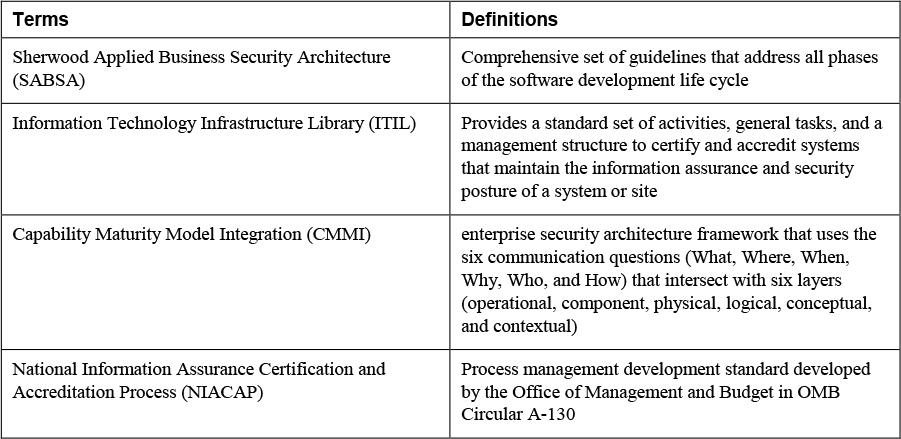
The Capability Maturity Model Integration (CMMI) is a comprehensive set of guidelines that address all phases of the software development life cycle. It describes a series of stages, or maturity levels, that a development process can advance through as it goes from the ad hoc (Initial) model to one that incorporates a budgeted plan for continuous improvement. Figure 21-4 shows its five maturity levels.


Figure 21-4 CMMI Maturity Levels Certification
Although the terms are used as synonyms in casual conversation, accreditation and certification are two different concepts in the context of assurance levels and ratings. However, they are closely related. Certification evaluates the technical system components, whereas accreditation occurs when the adequacy of a system’s overall security is accepted by management.
ISO/IEC 27001
ISO/IEC 27001:2013 is the current version of the 27001 standard, and it is one of the most popular standards by which organizations obtain certification for information security. It is covered in Chapter 20.
Policies and Procedures
Policies are broad statements of intent, while procedures are details used to carry out that intent. Both mechanisms are used to guide an organization’s effort with regard to security or any activity over which the organization wishes to gain control. A security policy should cover certain items, and it should be composed of a set of documents that ensure that key components are secured. The following sections cover the key policies and procedures that should be created and included in a security policy.
Code of Conduct/Ethics
A code of conduct/ethics policy is one intended to demonstrate a commitment to ethics in the activities of the principles. It is typically a broad statement of commitment that is supported by detailed procedures designed to prevent unethical activities. For example, the statement might be “We commit to the highest ethical standards in our dealings with others.” Supporting this would be a procedure that prohibits the acceptance or offer of gifts during a sales negotiation.
Personnel hiring procedures should include signing all the appropriate documents, including government-required documentation, no expectation of privacy statements, and non-disclosure agreements (NDAs). Organizations usually have a personnel handbook and other hiring information that must be communicated to the employee. The hiring process should include a formal verification that the employee has completed all the training. Employee IDs and passwords are issued at this time.
Code of conduct, conflict of interest, and ethics agreements should also be signed at this time. Also, any non-compete agreements should be verified to ensure that employees do not leave the organization for a competitor. Employees should be given guidelines for periodic performance reviews, compensation, and recognition of achievements.
Acceptable Use Policy (AUP)
An acceptable use policy (AUP) is used to inform users of the actions that are allowed and those that are not allowed. It should also provide information on the consequences that may result when these policies are violated. This document should be reviewed and signed by each user during the employee orientation phase of the employment process. The following are examples of the many issues that may be addressed in an AUP:

• Proprietary information stored on electronic and computing devices, whether owned or leased by company, the employee, or a third party, remains the sole property of company.
• The employee has a responsibility to promptly report the theft, loss, or unauthorized disclosure of proprietary information.
• Access, use, or sharing of proprietary information is allowed only to the extent that it is authorized and necessary to fulfill assigned job duties.
• Employees are responsible for exercising good judgment regarding the reasonableness of personal use.
• Authorized individuals in the company may monitor equipment, systems, and network traffic at any time.
• The company reserves the right to audit networks and systems on a periodic basis to ensure compliance with this policy.
• All mobile and computing devices that connect to the internal network must comply with the company access policy.
• System-level and user-level passwords must comply with the password policy.
• All computing devices must be secured with a password-protected screensaver.
• Postings by employees from a company e-mail address to newsgroups should contain a disclaimer stating that the opinions expressed are strictly their own and not necessarily those of company.
• Employees must use extreme caution when opening e-mail attachments received from unknown senders, which may contain malware.
Password Policy
Password authentication is the most popular authentication method implemented today. But often password types can vary from system to system. Before we look at potential password policies, it is vital that you understand all the types of passwords that can be used. Some of the types of passwords that you should be familiar with include the following:

• Standard word passwords: As the name implies, these passwords consist of single words that often include a mixture of upper- and lowercase letters. The advantage of this password type is that it is easy to remember. A disadvantage of this password type is that it is easy for attackers to crack or break, resulting in compromised accounts.
• Combination passwords: These passwords, also called composition passwords, use a mix of dictionary words, usually two that are unrelated. Like standard word passwords, they can include upper- and lowercase letters and numbers. An advantage of this password type is that it is harder to break than a standard word password. A disadvantage is that it can be hard to remember.
• Static passwords: This password type is the same for each login. It provides a minimum level of security because the password never changes. It is most often seen in peer-to-peer networks.
• Complex passwords: This password type forces a user to include a mixture of upper- and lowercase letters, numbers, and special characters. For many organizations today, this type of password is enforced as part of the organization’s password policy. An advantage of this password type is that it is very hard to crack. A disadvantage is that it is harder to remember and can often be much harder to enter correctly.
• Passphrase passwords: This password type requires that a long phrase be used. Because of the password’s length, it is easier to remember but much harder to attack, both of which are definite advantages. Incorporating upper- and lowercase letters, numbers, and special characters in this type of password can significantly increase authentication security.
• Cognitive passwords: This password type is a piece of information that can be used to verify an individual’s identity. The user provides this information to the system by answering a series of questions based on her life, such as favorite color, pet’s name, mother’s maiden name, and so on. An advantage of this type is that users can usually easily remember this information. The disadvantage is that someone who has intimate knowledge of the person’s life (spouse, child, sibling, and so on) may be able to provide this information as well.
• One-time passwords (OTPs): Also called a dynamic password, an OTP is used only once to log in to the access control system. This password type provides the highest level of security because it is discarded after it is used once.
• Graphical passwords: Also called CAPTCHA passwords (an acronym for Completely Automated Public Turing test to tell Computers and Humans Apart), this type of password uses graphics as part of the authentication mechanism. One popular implementation requires a user to enter a series of characters that appear in a graphic. This implementation ensures that a human, not a machine, is entering the password. Another popular implementation requires the user to select the appropriate graphic for his account from a list of graphics.
• Numeric passwords: This type of password includes only numbers. Keep in mind that the choices of a password are limited by the number of digits allowed. For example, if all passwords are four digits, then the maximum number of password possibilities is 10,000, from 0000 through 9999. Once an attacker realizes that only numbers are used, cracking user passwords is much easier because the attacker knows the possibilities.
The simpler types of passwords are considered weaker than passphrases, one-time passwords, token devices, and login phrases. Once an organization has decided which type of password to use, the organization must establish its password management policies. Password management considerations include, but may not be limited to, the following:

• Password life: How long a password will be valid. For most organizations, passwords are valid for 60 to 90 days.
• Password history: How long before a password can be reused. Password policies usually remember a certain number of previously used passwords.
• Authentication period: How long a user can remain logged in. If a user remains logged in for the specified period without activity, the user will be automatically logged out.
• Password complexity: How the password will be structured. Most organizations require upper- and lowercase letters, numbers, and special characters. The following are some recommendations:
• Passwords shouldn’t contain the username or parts of the user’s full name, such as his first name.
• Passwords should use at least three of the four available character types: lowercase letters, uppercase letters, numbers, and symbols.
• Password length: How long the password must be. Most organizations require 8 to 12 characters.
As part of password management, an organization should establish a procedure for changing passwords. Most organizations implement a service that allows users to automatically reset a password before the password expires. In addition, most organizations should consider establishing a password reset policy that addresses situations in which users forget their passwords or their passwords are compromised. A self-service password reset approach allows users to reset their own passwords, without the assistance of help desk employees. An assisted password reset approach requires that users contact help desk personnel for help changing passwords.
Password reset policies can also be affected by other organizational policies, such as account lockout policies. Account lockout policies are security policies that organizations implement to protect against attacks carried out against passwords. Organizations often configure account lockout policies so that user accounts are locked after a certain number of unsuccessful login attempts. If an account is locked out, the system administrator may need to unlock or reenable the user account. Security professionals should also consider encouraging organizations to require users to reset their passwords if their accounts have been locked. For most organizations, all the password policies, including account lockout policies, are implemented at the enterprise level on the servers that manage the network.
Depending on which servers are used to manage the enterprise, security professionals must be aware of the security issues that affect user accounts and password management. Two popular server operating systems are Linux and Windows.
For Linux, passwords are stored in the /etc/passwd or /etc/shadow file. Because the /etc/passwd file is a text file that can be easily accessed, you should ensure that any Linux servers use the /etc/shadow file, where the passwords in the file can be protected using a hash. The root user in Linux is a default account that is given administrative-level access to the entire server. If the root account is compromised, all passwords should be changed. Access to the root account should be limited only to system administrators, and root login should be allowed only via a system console.
Data Ownership
A data ownership policy is closely related to a data classification policy (covered in Chapter 13, “The Importance of Proactive Threat Hunting”), and often the two policies are combined. This is because typically the data owner is tasked with classifying the data. Therefore, the data ownership policy covers how the owner of each piece of data or each data set is identified. In most cases, the creator of the data is the owner, but some organizations may deem all data created by a department to be owned by the department head. Another way a user may become the owner of data is by introducing into the organization data the user did not create. Perhaps the data was purchased from a third party. In any case, the data ownership policy should outline both how data ownership occurs and the responsibilities of the owner with respect to determining the data classification and identifying those with access to the data.
Data Retention
A data retention policy outlines how various data types must be retained and may rely on the data classifications described in the data classification policy. Data retention requirements vary based on several factors, including data type, data age, and legal and regulatory requirements. Security professionals must understand where data is stored and the type of data stored. In addition, security professionals should provide guidance on managing and archiving data securely. Therefore, each data retention policy must be established with the help of organizational personnel.
A data retention policy usually identifies the purpose of the policy, the portion of the organization affected by the policy, any exclusions to the policy, the personnel responsible for overseeing the policy, the personnel responsible for data destruction, the data types covered by the policy, and the retention schedule. Security professionals should work with data owners to develop the appropriate data retention policy for each type of data the organization owns. Examples of data types include, but are not limited to, human resources data, accounts payable/receivable data, sales data, customer data, and e-mail.
To design a data retention policy, an organization should answer the following questions:
• What are the legal/regulatory requirements and business needs for the data?
• What are the types of data?
• What are the retention periods and destruction needs of the data?
The personnel who are most familiar with each data type should work with security professionals to determine the data retention policy. For example, human resources personnel should help design the data retention policy for all human resources data. While designing a data retention policy, the organization must consider the media and hardware that will be used to retain the data. Then, with this information in hand, the data retention policy should be drafted and formally adopted by the organization and/or business unit.
Once a data retention policy has been created, personnel must be trained to comply with it. Auditing and monitoring should be configured to ensure data retention policy compliance. Periodically, data owners and processors should review the data retention policy to determine whether any changes need to be made. All data retention policies, implementation plans, training, and auditing should be fully documented.
Remember that for most organizations, a one-size-fits-all solution is impossible because of the different types of data. Only those most familiar with each data type can determine the best retention policy for that data. While a security professional should be involved in the design of the data retention policies, the security professional is there to ensure that data security is always considered and that data retention policies satisfy organizational needs. The security professional should only act in an advisory role and should provide expertise when needed.
Account Management
The account management policy helps guide the management of identities and accounts. Identity and account management is vital to any authentication process. As a security professional, you must ensure that your organization has a formal procedure to control the creation and allocation of access credentials or identities. If invalid accounts are allowed to be created and are not disabled, security breaches will occur. Most organizations implement a method to review the identification and authentication process to ensure that user accounts are current. Answering questions such as the following is likely to help in the process:
• Is a current list of authorized users and their access maintained and approved?
• Are passwords changed at least every 90 days[md]or earlier, if needed?
• Are inactive user accounts disabled after a specified period of time?
Any identity management procedure must include processes for creating (provisioning), changing and monitoring (reviewing), and removing users from the access control system (revoking). This is referred to as the access control provisioning life cycle. When initially establishing a user account, new users should be required to provide valid photo identification and should sign a statement regarding password confidentiality. User accounts must be unique. Policies should be in place to standardize the structure of user accounts. For example, all user accounts should be firstname.lastname or some other structure. This ensures that users in an organization will be able to determine a new user’s identification, mainly for communication purposes.
After creation, user accounts should be monitored to ensure that they remain active. Inactive accounts should be automatically disabled after a certain period of inactivity, based on business requirements. In addition, any termination policy should include formal procedures to ensure that all user accounts are disabled or deleted. Elements of proper account management include the following:
• Establish a formal process for establishing, issuing, and closing user accounts.
• Periodically review user accounts.
• Implement a process for tracking access authorization.
• Periodically rescreen personnel in sensitive positions.
• Periodically verify the legitimacy of user accounts.
User account reviews are a vital part of account management. User accounts should be reviewed for conformity with the principle of least privilege. This principle specifies that users should only be given the rights and permission required to do their job and no more. User account reviews can be performed on an enterprise wide, systemwide, or application-by-application basis. The size of the organization greatly affects which of these methods to use. As part of user account reviews, organizations should determine whether all user accounts are active.
Continuous Monitoring
To support the enforcement of a security policy and its various parts, operations procedures should be defined and practiced on a daily basis. One of the most common operational procedures that should be defined is continuous monitoring. Before continuous monitoring can be successful, an organization must ensure that operational baselines are captured. After all, an organization cannot recognize abnormal patterns or behavior if it doesn’t know what “normal” is. These baselines should also be revisited periodically to ensure that they have not changed. For example, if a single web server is upgraded to a web server farm, a new performance baseline should be captured.
Security analysts must ensure that the organization’s security posture is maintained at all times. This requires continuous monitoring. Auditing and security logs should be reviewed on a regular schedule. Performance metrics should be compared to baselines. Even simple acts such as normal user login/logout times should be monitored. If a user suddenly starts logging in and out at irregular times, the user’s supervisor should be alerted to ensure that the user is authorized. Organizations must always be diligent in monitoring the security of the enterprise.
An example of a continuous monitoring tool is Security Compliance Toolkit (SCT). This tool can be used to monitor compliance with a baseline. It works with two other Microsoft tools: Group Policy and Microsoft Endpoint Configuration Manager (MESCM).
Work Product Retention
Work product is anything you complete for a person or business that has hired you. Organizations need a clear work product retention policy that defines all work product as property of the organization and not of the worker who created the product. This requires employers to sign an agreement to that effect at time of employment.
Category
Control categories refer to how the control responds to the issue, while the control type refers to how the control is implemented. There are three control categories, managerial (or administrative), operational, and technical. Control types are covered in the following “Control Type” section.
Managerial
Managerial controls (also called administrative controls) are implemented to administer the organization’s assets and personnel and include security policies, procedures, standards, baselines, and guidelines that are established by management. These controls are commonly referred to as soft controls. Specific examples are personnel controls, data classification, data labeling, security awareness training, and supervision.
Security awareness training is a very important administrative control. Its purpose is to improve the organization’s attitude about safeguarding data. The benefits of security awareness training include reduction in the number and severity of errors and omissions, better understanding of information value, and better administrator recognition of unauthorized intrusion attempts. A cost-effective way to ensure that employees take security awareness seriously is to create an award or recognition program.
Operational
Operational controls are measures that are made part of the organizational security stance day to day. These controls include the following control types:
• Directive controls: Specify acceptable practice within an organization. They are in place to formalize an organization’s security directive mainly to its employees. The most popular directive control is an acceptable use policy (AUP), which lists proper (and often examples of improper) procedures and behaviors that personnel must follow. Any organizational security policies or procedures usually fall into this access control category. You should keep in mind that directive controls are efficient only if there is a stated consequence for not following the organization’s directions.
• Deterrent controls: Deter or discourage an attacker. Via deterrent controls, attacks can be discovered early in the process. Deterrent controls often trigger preventive and corrective controls. Examples of deterrent controls include user identification and authentication, fences, lighting, and organizational security policies, such as an NDA.
Technical
Technical controls (also called logical controls) are software or hardware components used to restrict access. Specific examples of logical controls are firewalls, IDSs, IPSs, encryption, authentication systems, protocols, auditing and monitoring, biometrics, smart cards, and passwords.
An example of implementing a technical control is adopting a new security policy that forbids employees from remotely configuring the e-mail server from a third party’s location during work hours.
Although auditing and monitoring are logical controls and are often listed together, they are actually two different controls. Auditing is a one-time or periodic event to evaluate security. Monitoring is an ongoing activity that examines either the system or users.

Control Type
Controls are implemented as countermeasures to identified vulnerabilities. Control mechanisms are divided into six types, as explained in this section. Control type refers to how the control is implemented.
Preventative
Preventative controls (or preventive controls) prevent an attack from occurring. Examples of preventive controls include locks, badges, biometric systems, encryption, IPSs, antivirus software, personnel security, security guards, passwords, and security awareness training.
Detective
Detective controls are in place to detect an attack while it is occurring to alert appropriate personnel. Examples of detective controls include motion detectors, IDSs, logs, guards, investigations, and job rotation.
Corrective
Corrective controls are in place to reduce the effect of an attack or other undesirable event. Using corrective controls fixes or restores the entity that is attacked. Examples of corrective controls include installing fire extinguishers, isolating or terminating a connection, implementing new firewall rules, and using server images to restore to a previous state.
Deterrent
Deters or discourages an attacker. Via deterrent controls, attacks can be discovered early in the process. Deterrent controls often trigger preventive and corrective controls. Examples of deterrent controls include user identification and authentication, fences, lighting, and organizational security policies, such as an NDA.
Directive
Specifies acceptable practice within an organization. They are in place to formalize an organization’s security directive mainly to its employees. The most popular directive control is an acceptable use policy (AUP), which lists proper (and often examples of improper) procedures and behaviors that personnel must follow. Any organizational security policies or procedures usually fall into this access control category. You should keep in mind that directive controls are efficient only if there is a stated consequence for not following the organization’s directions.
Physical
Physical controls are implemented to protect an organization’s facilities and personnel. Personnel concerns should take priority over all other concerns. Specific examples of physical controls include perimeter security, badges, swipe cards, guards, dogs, mantraps, biometrics, and cabling.
Audits and Assessments
Assessing vulnerability, selecting controls, and adjusting security policies and procedures to support those controls without performing verification and quality control are somewhat like driving without a dashboard. Just as you would have no information about the engine temperature, speed, and fuel level, you would be unable to determine whether your efforts are effective.
Audits differ from internal assessments in that they are usually best performed by a third party. An organization should conduct internal and third-party audits as part of any security assessment and testing strategy. An audit should test all security controls that are currently in place. Some guidelines to consider as part of a good security audit plan include the following:
• At minimum, perform annual audits to establish a security baseline.
• Determine your organization’s objectives for the audit and share them with the auditors.
• Set the ground rules for the audit before the audit starts, including the dates/ times of the audit.
• Choose auditors who have security experience.
• Involve business unit managers early in the process.
• Ensure that auditors rely on experience, not just checklists.
• Ensure that the auditor’s report reflects risks that your organization has identified.
• Ensure that the audit is conducted properly.
• Ensure that the audit covers all systems and all policies and procedures.
• Examine the report when the audit is complete.
Audits and assessments can fall into two categories, which are covered in the following sections.
Regulatory
Many regulations today require that audits occur. Organizations used to rely on Statement on Auditing Standards (SAS) 70, which provided auditors information and verification about data center controls and processes related to the data center user and financial reporting. In 2011, the Statement on Standards for Attestation Engagements (SSAE) No. 16 took the place of SAS 70 as the authoritative standard for auditing service organizations and was subsequently updated to verify 18.These audits verify that the controls and processes set in place by a data center are actually followed. The Statement on Standards for Attestation Engagements (SSAE) 18 is a standard that verifies the controls and processes and also requires a written assertion regarding the design and operating effectiveness of the controls being reviewed.
An SSAE 18 audit results in a Service Organization Control (SOC) 1 report. This report focuses on internal controls over financial reporting. There are two types of SOC 1 reports:
• SOC 1, Type 1 report: Focuses on the auditors’ opinion of the accuracy and completeness of the data center management’s design of controls, system, and/or service.
• SOC 1, Type 2 report: Includes Type 1 and an audit on the effectiveness of controls over a certain time period, normally between six months and a year.
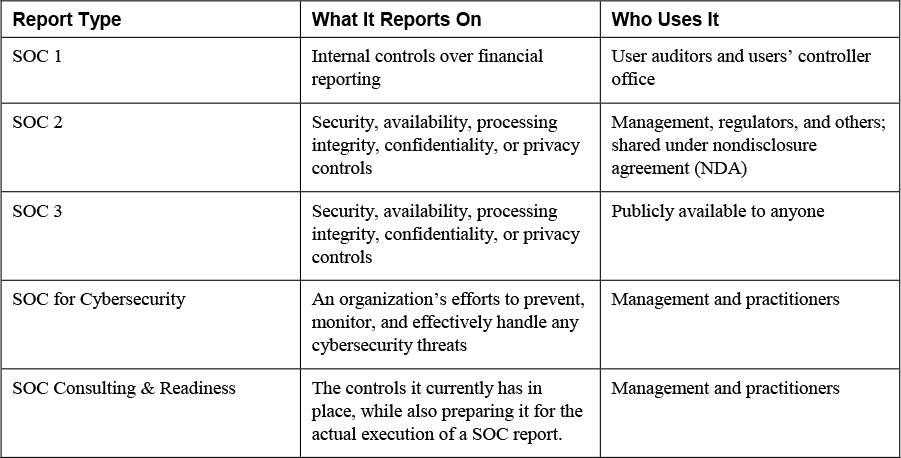
Two other report types are also available: SOC 2 and SOC 3. Both of these audits provide benchmarks for controls related to the security, availability, processing integrity, confidentiality, or privacy of a system and its information. A SOC 2 report includes service auditor testing and results, and a SOC 3 report provides only the system description and auditor opinion. A SOC 3 report is for general use and provides a level of certification for data center operators that assures data center users of facility security, high availability, and process integrity. Table 21-5 briefly compares the three types of SOC reports. Included in the table are two new report types as well.

Table 21-5 SOC Report Comparison Chart
Compliance
No organization operates within a bubble. All organizations are affected by laws, regulations, and compliance requirements. Security analysts must understand the laws and regulations of the country or countries they are working in and the industry within which they operate. In many cases, laws and regulations prescribe how specific actions must be taken. In other cases, laws and regulations leave it up to the organization to determine how to comply. Significant pieces of legislation that can affect an organization and its security policy are covered in Chapter 19.
Exam Preparation Tasks
As mentioned in the section “How to Use This Book” in the Introduction, you have several choices for exam preparation: the exercises here, Chapter 22, “Final Preparation,” and the exam simulation questions in the Pearson Test Prep Software Online.
Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topics icon in the outer margin of the page. Table 21-6 lists a reference of these key topics and the page numbers on which each is found.

Table 21-6 Key Topics in Chapter 21

Define Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
The Open Group Architecture Framework (TOGAF)
NIST Cybersecurity Framework version 1.1
Capability Maturity Model Integration (CMMI)
National Information Assurance Certification and Accreditation Process (NIACAP)
managerial (administrative type) controls
Review Questions
1. ________________ is a security controls development framework developed by NIST.
2. List the family and class of at least two of the NIST SP 800-53 control families.
3. Match the following terms with their definitions.

4. List at least two guidelines to consider as part of a good security audit plan.
5. List at least one SOC report, including what it reports on and who uses it.
6. Match the following terms with their definitions.

7. _______________________ controls are software or hardware components used to restrict access.
8. List and define at least two password policies.
9. Match the following terms with their definitions.
10. A(n) ______________________ policy is one intended to demonstrate a commitment to ethics in the activities of the principles.
