Chapter 2. Introducing the Enterprise Mobility Suite
In the previous chapter, you had the opportunity to learn about enterprise mobility and how to embrace a mobile workforce. Microsoft offers a suite of cloud services called Enterprise Mobility Suite (EMS) to address the enterprise mobility challenges. The plan is to help organizations enable their users to be productive on the devices they love while protecting company data. This chapter describes EMS and each of its three cloud services, as well as the considerations for implementing each service.
Understanding the EMS solution
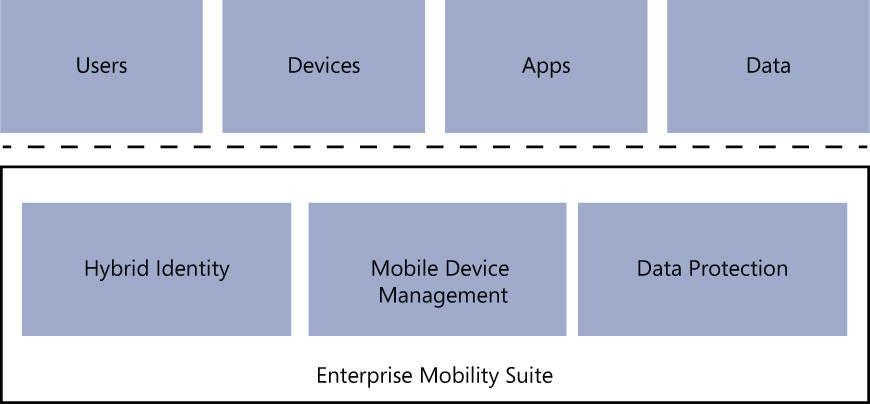
Chapter 1 introduced the four elements (users, devices, apps, and data) involved in the enterprise mobility strategy. These elements will be used as examples throughout the book. Knowing that the core of your enterprise mobility solution must include these four elements will make it easier for you to understand how EMS can enable organizations to embrace a mobile workforce. EMS has three “pillars” that support the EMS elements (see Figure 2-1):
![]() Hybrid identity
Hybrid identity
![]() Mobile Device Management (MDM)
Mobile Device Management (MDM)
![]() Data protection
Data protection
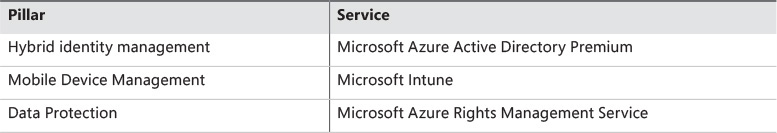
These pillars are essential pieces of the enterprise mobility solution. For each pillar, EMS a cloud service that provides the capabilities that are required to achieve the demands established by each pillar. These pillars and the related cloud service for each are shown in Table 2-1.
Establishing a hybrid identity
It is fundamentally important to mobile users that they have access to what they need to perform their work, regardless of where they might be located. However, it is also fundamentally important for the IT department to understand who is trying to access the information and to validate the level of authorization necessary to access the information. This is where identity becomes one of the most important aspects in an enterprise mobility solution.
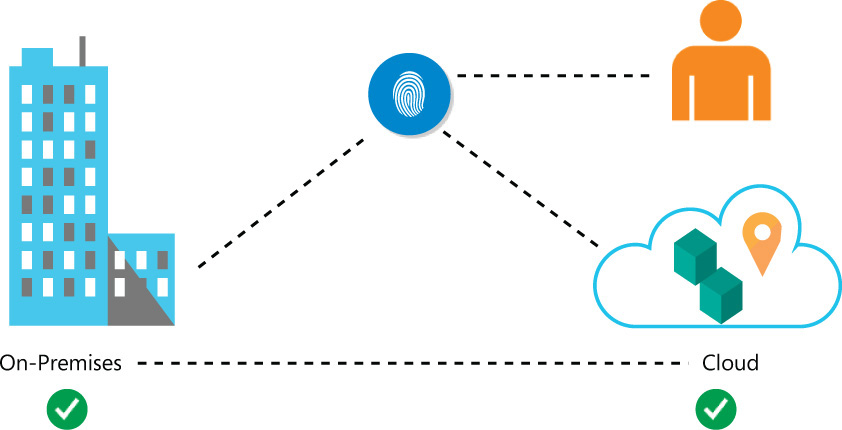
In addition, it is important to allow users to consume cloud-based Software as a Service (SaaS) apps approved by the company without requiring users to memorize multiple credentials. As you know, increasing the number of credentials (usernames and passwords) leads to problems for the users. They might forget one credential or they might start using weak passwords to access other apps, which can lead to a security breach. Figure 2-2 shows how a common identity can be important to maintaining a seamless experience across on-premises and cloud resources.
FIGURE 2-2 Enterprise mobility enables users to use a single identity to access on-premises and cloud resources
Not every company has a robust infrastructure to keep remote access on-premises. Most of the time, the budget needs to include funding for more than just the maintenance of remote access or of a VPN appliance; your budget also has to include an IT team prepared to maintain this infrastructure. In this scenario, cloud computing can be a vital asset for the company. Even if the organization doesn’t plan to fully migrate to a cloud environment, it can realize the benefits of adopting a hybrid solution. An IT administrator responsible for maintaining a hybrid environment should be able to manage resources located on-premises and in the cloud while preserving a seamless user-authentication experience. For this reason, EMS uses the Hybrid Identity model, which enables organizations to leverage their current investments in identity management located on-premises to authenticate and authorize access to users while those users have the capability to integrate with a cloud-based identity directory.
While these are foundational aspects of an identity solution for an enterprise mobility strategy, the following items are other key requirements that must be fulfilled in any identity solution:
![]() Organizations need to enable users to use a single set of identity on their devices of choice to access resources in the cloud and on-premises.
Organizations need to enable users to use a single set of identity on their devices of choice to access resources in the cloud and on-premises.
![]() Organizations that are not going to fully migrate to the cloud require a hybrid environment in order to leverage cloud-computing capabilities while keeping their sensitive data on-premises.
Organizations that are not going to fully migrate to the cloud require a hybrid environment in order to leverage cloud-computing capabilities while keeping their sensitive data on-premises.
![]() Organizations need to enhance their security by implementing multi-factor authentication (MFA) for users accessing resources from the cloud.
Organizations need to enhance their security by implementing multi-factor authentication (MFA) for users accessing resources from the cloud.
![]() Organizations need to be able to manage their user’s identity-to-identity suspicious activities.
Organizations need to be able to manage their user’s identity-to-identity suspicious activities.
The EMS service responsible for addressing these requirements is called Microsoft Azure Active Directory Premium. Chapter 3 covers the Azure AD Premium capabilities and Chapter 4 covers how to implement some of these capabilities.
It is important to identify which options meet the requirements for your organization to implement hybrid identity. When deciding which option your organization should use, ensure that the option that you choose can evolve as new requirements arise. Even if your organization does not have a hybrid IT environment, the solution that will be implemented should be flexible enough to meet the requirements when it is necessary to integrate the business with cloud services.
More Info
For a list of advantages and disadvantages to using each identity option, read section 4.3.3 of the BYOD Design Considerations Guide at http://aka.ms/byodcg.
Managing mobile devices
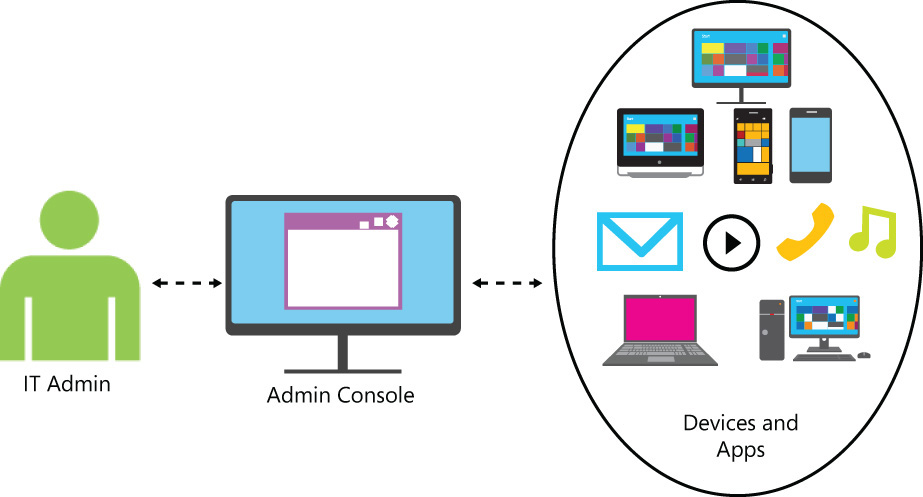
Another EMS pillar is Mobile Device Management. This pillar has direct correlation to how your organization will administer mobile devices, deploy apps, and help secure organizational data. Organizations that are planning to embrace mobility need to enable IT to view and manage PCs, mobile devices, servers, and virtual machines that are both corporate-connected and cloud-based connected. It is also imperative that the management platform is capable of performing inventory, applying policies, and distributing software to a wide range of devices across multiple platforms. Figure 2-3 illustrates the challenge for IT admins, where they need to be able to manage all these devices from a single location.
FIGURE 2-3 IT admins need to manage multiple devices and apps across multiple platforms from a single location
Device management requirements
As discussed in Chapter 1, BYOD is one vital scenario in the enterprise mobility space. To securely embrace this solution, management must enable IT to define and deploy configuration policies specific to each mobile device platform that will help meet compliance requirements and at the same time protect employee privacy and data. Mobile users will use a variety of devices to consume data and apps that are controlled by the organization. The management platform must enable IT to publish or deploy applications to users’ corporate or personal devices based on pre-defined policies. Ideally the management platform should be as unobtrusive to the user as possible. The IT administrator needs to empower users to be productive without impeding their ability to perform their work. IT administrators must be able to perform the following device management tasks:
![]() Manage updates
Manage updates
![]() Monitor and trigger alerts proactively
Monitor and trigger alerts proactively
![]() Perform hardware and software inventory
Perform hardware and software inventory
![]() Set security policies
Set security policies
![]() Distribute software
Distribute software
![]() Provide remote assistance
Provide remote assistance
![]() Help protect PCs from malware
Help protect PCs from malware
![]() Remotely wipe and selectively wipe mobile devices
Remotely wipe and selectively wipe mobile devices
As you can see, device management is an important part of your enterprise mobility strategy and there are many requirements that must be fulfilled. Within EMS, Microsoft Intune is responsible for addressing these requirements. Chapter 5 covers the Microsoft Intune capabilities and Chapter 6 covers how to implement some of these capabilities.
Device management considerations
You need to ensure that the device management option you select meets the requirements for your organization before you implement the device management solution. By default, Microsoft Intune is the option available with EMS. However, you must evaluate the following approaches to device management and define your approach before you implement it:
![]() Unify the on-premises device management solution with the cloud-based management solution
Unify the on-premises device management solution with the cloud-based management solution
![]() Manage the mobile devices separately from the on-premises devices using the cloud-based device management solution
Manage the mobile devices separately from the on-premises devices using the cloud-based device management solution
If your organization decides to unify the management environment, you must evaluate this integration prior to implementing it. A different set of designing and planning options must be reviewed before you can properly deploy this solution according to the organization’s business requirements.
More Info
For a list of advantages and disadvantage to using each device management option, read section 4.4 of the BYOD Design Considerations Guide at http://aka.ms/byodcg.
Protecting data
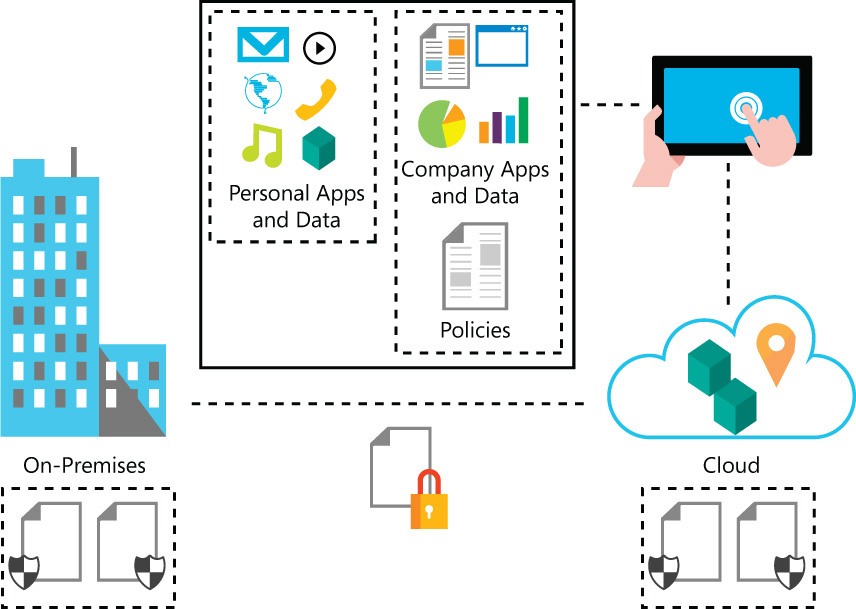
As part of creating your enterprise mobility strategy, policies and data classifications must be defined as part of the overall data protection solution. Once IT validates the users’ identities, the next step is to apply additional conditions to the types of devices that are able to access the information and apps provided by the organization. Organizations that are planning to embrace mobility need to ensure that their data is protected no matter where the data is located (on-premises, in the cloud, or on the user’s device). Ideally, corporate files should be protected even when you copy them to another folder or device or when you share the folder in which the files are located. Figure 2-4 illustrates the many areas where data must be protected.
As shown in Figure 2-4, data protection must be applied on-premises, in transit (usually done by using encryption), in the cloud, and at the user’s device. The important aspect of data protection at the user’s device is the isolation of personal data from the organization’s data. IT admins must be able to, at any moment, remove the organization’s apps and data from the user’s device without harming the user’s personal files and apps.
Mitigating risk
Many organizations are concerned about embracing mobility because their perception is that the likelihood that data leakage will occur will increase. While this is a fair assumption, the enterprise mobility strategy must mitigate this potential risk by ensuring that the data protection solution is able to:
![]() Protect all file types
Protect all file types
![]() Protect files sent via email
Protect files sent via email
![]() Protect data located in all commonly used devices, not just Windows computers
Protect data located in all commonly used devices, not just Windows computers
![]() Support data protection for on-premises services as well as in the cloud (SaaS such as Office 365)
Support data protection for on-premises services as well as in the cloud (SaaS such as Office 365)
![]() Scale across your organization as needed
Scale across your organization as needed
![]() Adhere to regulatory requirements
Adhere to regulatory requirements
![]() Allow IT to keep control of the data
Allow IT to keep control of the data
![]() Maintain the users’ abilities to interact and protect their own documents
Maintain the users’ abilities to interact and protect their own documents
EMS addresses these requirements through the Azure Rights Management Services (RMS). Chapter 7 covers Azure RMS capabilities and Chapter 8 covers how to implement some of these capabilities.
Data protection considerations
While Azure RMS specifically addresses data protection, there are other capabilities distributed among the other pillars (hybrid identity and device management) that are all part of the data protection solution. Remember, data is the core of your solution; therefore you should apply the defense-in-depth approach to add multiple layers of security to ensure total protection of the data. Defense-in-depth should leverage not only the data protection capabilities offered by EMS but also the built-in capabilities available from each platform, such as the Windows operating system.
Table 2-2 shows the different layers of security that are involved before the user accesses the data. Security considerations for each layer are part of the defense-in-depth strategy to protect the data itself.
EMS activation process
While EMS is a solution for enterprise mobility adoption, this solution is the aggregation of separate cloud services (Azure AD Premium, Microsoft Intune, and Azure Rights Management). Therefore, there is no procedure to install EMS; what you will do is a single activation process. Once action is completed, the additional steps to configure each part of the solution are unique to each cloud service. The EMS activation process can be summarized in three steps:
1. Sign up for EMS.
2. Activate the license plan.
3. Activate access.
For more details about each step, you can download the EMS Activation Guide at http://aka.ms/emsaguide.
More Info
To see the latest information about EMS Licensing options, go to http://www.microsoft.com/en-us/server-cloud/products/enterprise-mobility-suite/buy.aspx
Embracing a mobile workforce scenario
To help you understand how each EMS service will be used as part of the enterprise mobility solution, the following scenario will be used throughout this book. Each implementation chapter will reference this scenario and will implement one or more of the requirements that are described in this section. At the end of this book you will have the completed solution implemented and all requirements for the fictitious organization shown in Figure 2-5 will be fulfilled.
Blue Yonder Airlines has made a recent acquisition and is in the process of expanding its business throughout different regions of the country. As result of the acquisition, many of the new employees will be working remotely from multiple time zones and they will be changing geographic locations. With so many employees traveling throughout the world, it is becoming an overwhelming challenge for the centralized IT staff to manage access to organizational resources.
In addition, many of the new Blue Yonder Airlines employees are complaining that it takes too long to obtain the security access to apps that they need to use in order to be productive or that they simply cannot access the app on their devices. When IT investigated these issues, they discovered that more and more Blue Yonder Airlines employees are accessing their corporate email, company applications, and company data from many different types of personal devices (rather than from company-owned computers). Recently, one employee’s unmanaged personal device became compromised with malware and this malware infected a file located at the corporate office, causing a potential data breach. Fortunately, IT was able to contain the issue and clean the file system before any harm was done. However, it alerted the organization to the fact that it needs to resolve its resource access and device management problems as soon as possible in order to keep its employees productive and organization’s data secure.
After researching BYOD trends and user productivity studies, the leadership team at Blue Yonder Airlines concluded that it needs to embrace BYOD and implement an enterprise mobility management solution as soon as possible. The team knows it must first draft a BYOD policy and ensure employees are aware of the policy before employees use their personal devices to access company data. However, in addition to creating the BYOD policy, the leadership team must also meet several business requirements.
Currently, Blue Yonder Airlines has the following infrastructure on-premises:
![]() Active Directory is running on-premises with hundreds of users authenticating on a daily basis
Active Directory is running on-premises with hundreds of users authenticating on a daily basis
![]() Exchange Server 2013 is running with users accessing their mailboxes via Outlook client, mobile devices (ActiveSync) and Outlook Web App (OWA)
Exchange Server 2013 is running with users accessing their mailboxes via Outlook client, mobile devices (ActiveSync) and Outlook Web App (OWA)
![]() There is no Systems Management technology implemented on-premises
There is no Systems Management technology implemented on-premises
![]() The current security policies do not cover BYOD scenarios
The current security policies do not cover BYOD scenarios
Blue Yonder Airlines’ goals with this project are to enable enterprise mobility to ensure that its employees are more productive and that they can work from anywhere using the devices of their choice while also protecting company data and resources. Blue Yonder Airlines established the following requirements in order to consider this project successful:
![]() Leverage its on-premises investment in Windows Server Active Directory and Azure to deliver a hybrid identity that enables users to be productive while leaving IT in control
Leverage its on-premises investment in Windows Server Active Directory and Azure to deliver a hybrid identity that enables users to be productive while leaving IT in control
![]() Implement SSO so that users need only one name and one password to access both on-premises and cloud-based software and services
Implement SSO so that users need only one name and one password to access both on-premises and cloud-based software and services
![]() Enable a seamless user experience for users transitioning from on-premises to the cloud by providing a consistent look and feel across all managed websites and services.
Enable a seamless user experience for users transitioning from on-premises to the cloud by providing a consistent look and feel across all managed websites and services.
![]() Require users to register information that is required to enable MFA before getting access to company resources
Require users to register information that is required to enable MFA before getting access to company resources
![]() Require users to register devices before accessing company resources
Require users to register devices before accessing company resources
![]() Enable users to access and use centrally managed SaaS apps from a secure location
Enable users to access and use centrally managed SaaS apps from a secure location
![]() Enable user self-service to reduce help-desk calls and empower users to manage their profiles, passwords, and delegated Azure AD group memberships
Enable user self-service to reduce help-desk calls and empower users to manage their profiles, passwords, and delegated Azure AD group memberships
![]() Enable IT to easily monitor and protect access to organizational resources
Enable IT to easily monitor and protect access to organizational resources
![]() Manage MFA for mobile users who are accessing company resources
Manage MFA for mobile users who are accessing company resources
![]() Ensure that all major platforms (Windows, Android, and iOS) are managed and supported by the company
Ensure that all major platforms (Windows, Android, and iOS) are managed and supported by the company
![]() Ensure that policy enforcement is available for company-owned devices as well as user-owned devices (BYOD)
Ensure that policy enforcement is available for company-owned devices as well as user-owned devices (BYOD)
![]() Ensure that data is protected and classified
Ensure that data is protected and classified
![]() Establish ways to mitigate issues related to data leakage on mobile devices
Establish ways to mitigate issues related to data leakage on mobile devices
![]() Minimize investment in implementing an on-premises infrastructure
Minimize investment in implementing an on-premises infrastructure
![]() Implement EMS with as little administrative overhead as possible while still enabling centralized reporting to monitor organizational activity and services.
Implement EMS with as little administrative overhead as possible while still enabling centralized reporting to monitor organizational activity and services.