Chapter 18. Secure Sockets Layer VPN (SSL VPN)
The ubiquitous Internet fuels network access reachability and availability to users whenever and wherever needed.
Today’s VPN solutions offer state-of-the-art secure technologies that extend the reach of networks to anyone, anyplace, anytime.
Remote Access VPN technology is the logical solution for remote connectivity providing secure communications with access rights tailored to individual users.
SSL-based Remote Access VPN technology provides remote-access connectivity from any Internet-enabled computer through a standard web browser and its native SSL encryption.
SSL VPN solutions offer network access at any time and any place, thereby providing the possibility of increasing productivity. SSL VPN solutions also offer greater flexibility for the remote workforce.
This chapter provides a complete overview of the SSL-based Remote Access VPN technology, describing solution architecture, deployment, and implementation guidelines. The chapter also introduces the newly released Cisco AnyConnect VPN client solution.
Secure Sockets Layer (SSL) Protocol
SSL is an application layer (Layer 7) cryptographic protocol that provides secure communications over the Internet for web browsing, e-mail, instant messaging, and other data traffic.
SSL, which was originally developed by Netscape and released in 1996, later served as the foundation for the IETF standard—Transport Layer Security (TLS) protocol.
Although SSL and TLS vary in some respects and are not interoperable, the protocol architecture largely remains the same. The primary objective of both protocols is to provide data privacy and data integrity, thereby providing secure communications between applications. By default, SSL uses TCP port 443.
Note
TLS was originally documented in IETF RFC 2246—“The TLS Protocol Version 1.0,” and was made obsolete by IETF RFC 4346—“The Transport Layer Security (TLS) Protocol Version 1.1,” which, as of this writing, is the current approved TLS version.
SSL VPN Solution Architecture
VPN technologies in recent years have evolved and have been widely used to provide secure connectivity, extending the reach of networks. As discussed in Chapter 15, “IPsec VPN,” two primary methods are used to deploy Remote Access VPN technology:
• Remote Access: IPsec VPN (covered in Chapter 15)
• Remote Access: SSL VPN
Cisco IPsec VPN and SSL VPN are complementary technologies. Both solutions offer remote access connectivity and can be deployed together or individually to better address the deployment requirements. Selecting the appropriate method depends on the deployment requirements and the network architecture.
Table 18-1 shows a comparison summary between IPsec VPN and SSL VPN technologies that can assist you in evaluating the appropriate Remote Access VPN technology as needed.
Table 18-1. IPsec and SSL VPN Comparison Chart
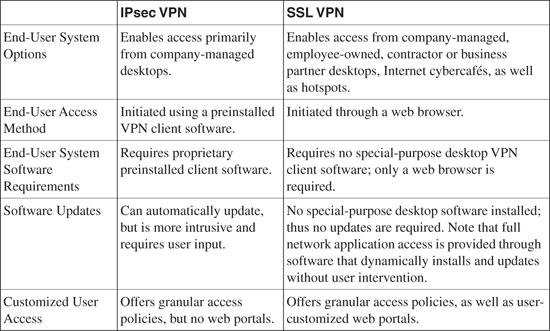
Note: The information in Table 18-1 is compiled from a Cisco white paper on “Remote Access VPN for Secure Communications” at http://www.cisco.com/en/US/netsol/ns340/ns394/ns171/ns125/networking_solutions_white_paper0900aecd804fb79a.shtml.
SSL VPN Overview
SSL VPN is an emerging technology offering a flexible, low-cost Internet-based remote solution by using the native SSL encryption of a web browser. SSL VPN does not require a special-purpose client software to be preinstalled on the system, thus enabling a user to connect from any computer, whether it is a company-managed or a non-company-managed system, such as a personal laptop, cybercafé, or home PC. SSL VPN sessions can be established from any Internet-enabled computer, thereby extending network access when and where required.
The Cisco SSL-based Remote Access VPN solution is a powerful tool that provides users with a virtual environment that emulates the working conditions of a main office with no geographical boundaries.
The Cisco Remote Access VPN solutions offer both IPsec VPN and SSL VPN technologies integrated on a single platform with unified management. The Cisco security solutions group offers the SSL VPN solution as part of the security products range. Examples include Cisco Integrated Services Routers (ISR), VPN Security, and Firewall Appliances.
Note
The Cisco SSL VPN solution is also commonly known as the Cisco WebVPN solution, and the two terms are interchangeably used in publications.
SSL VPN Features
SSL VPN technology offers a wide range of benefits. Key features include the following:
• Does not require special-purpose desktop VPN client software to be preinstalled on the system.
• Uses a standard web browser to establish a remote access VPN connection.
• Uses the native SSL encryption of a web browser to provide data confidentiality.
• Offers granular access control.
• Enables additional client-server applications to be downloaded dynamically with multiple delivery methods to help ensure transparent download and distribution with Java, ActiveX, or .exe files.
• Offers flexibility to establish VPN connections from any Internet-enabled system, be it a company-managed or non-company-managed system.
• Allows easy firewall and network traversal from any location.
• Allows transparent wireless roaming.
• Offers enhanced security using the integrated Cisco IOS Firewall feature.
Figure 18-1 illustrates the concept of SSL VPN and how a remote access user can access protected resources via the Internet over a secure encrypted channel.
Figure 18-1. Cisco SSL VPN Solution
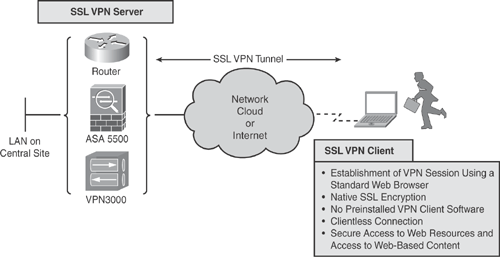
Note
As the industry leader in innovation, Cisco introduced the first-ever router platform to integrate the SSL VPN solution in Cisco IOS Software on Cisco Integrated Services Routers (ISR) series. The Cisco SSL VPN solution is also known as Cisco WebVPN.
SSL VPN Deployment Consideration
SSL VPN is an enhanced Cisco Remote Access VPN solution that offers data confidentiality by using the native SSL encryption technology within a web browser. Table 18-2 summarizes the characteristics that need to be considered when evaluating the SSL VPN deployment option.
Table 18-2. SSL VPN Deployment Consideration
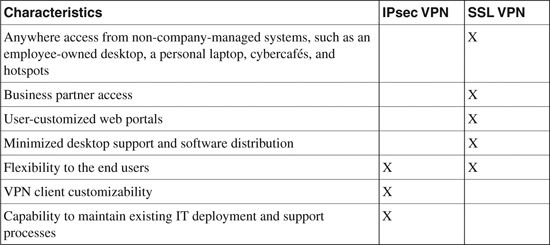
The information in Table 18-2 is compiled from the Cisco white paper on “Remote Access VPN for Secure Communications” at http://www.cisco.com/en/US/netsol/ns340/ns394/ns171/ns125/networking_solutions_white_paper0900aecd804fb79a.shtml.
SSL VPN Access Methods
SSL VPN can be deployed in one of the following three access modes, as illustrated in Figure 18-2:
• Clientless mode (Layer 7): Clientless mode provides secure access to web resources and access to web-based content. This mode is useful for accessing content that can be accessed in a web browser, such as Internet access, databases, and online web-based tools. Clientless mode can also offer remote file sharing by using the common Internet file system (CIFS) that provides a list of file server links in the web portal page, thereby allowing the remote user to browse listings of domains, servers, and directory folders, download a file, create a new file/directory, and so on. Clientless mode is limited to web-based content only.
• Thin client mode (Layer 7) (also known as port forwarding): Thin client mode provides remote access to TCP-based services such as Post Office Protocol (POP3), Simple Mail Transfer Protocol (SMTP), Internet Message Access Protocol (IMAP), Telnet, and Secure Shell (SSH) applications. The thin client is delivered via a Java applet that is dynamically downloaded from the SSL VPN appliance upon session establishment. This mode extends the capability of the cryptographic functions of the web browser.
• Thick client mode (Layer 3) (also known as tunnel mode or full tunneling client): The thick client mode provides remote access to an extensive array of application support and is delivered dynamically by downloading SSL VPN Client (SVC) software or the Cisco AnyConnect VPN client software from the VPN server appliance. This mode delivers a lightweight, centrally configured, and easy-to-support SSL VPN tunneling client that provides full network layer (Layer 3) access to virtually any application.
Figure 18-2 illustrates the basic SSL VPN access modes that were discussed previously.
Figure 18-2. SSL VPN Access Modes
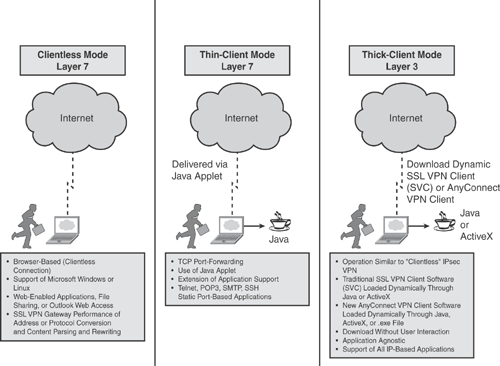
The information in Figure 18-2 is taken from the Cisco configuration guide on “Cisco IOS Software Releases 12.4T - SSL VPN” at http://www.cisco.com/en/US/products/ps6441/products_feature_guide09186a00805eeaea.html#wp1053878.
SSL VPN Citrix Support
The Cisco SSL VPN solution also offers clientless Citrix support that allows Citrix clients to use applications running on a remote Citrix server as if they were executed locally on the internal LAN.
Clientless SSL VPN is commonly used for remote access to Citrix applications. One of the major advantages of using the Cisco SSL VPN solution is that no additional helper applications are required for Citrix access over clientless SSL VPN, which helps ensure fast application initiation time and reduces the risk of desktop software conflicts. Many other SSL VPN solutions on the market require proprietary applets to be pushed down for Citrix to function.
Figure 18-3 illustrates Citrix support comparison with a traditional SSL VPN and the Cisco SSL VPN solution.
Figure 18-3. SSL VPN Citrix Support
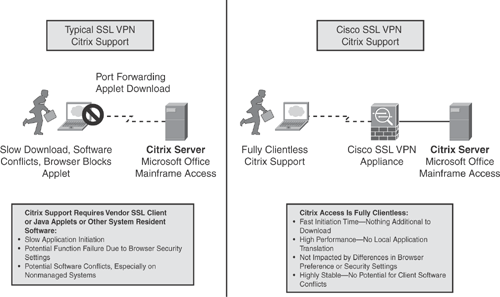
The information concept in Figure 18-3 is taken from the Cisco Networkers session presentation# SEC-2010 – “Deploying Remote Access IPSec and SSL VPNs.”
Implementing Cisco IOS SSL VPN
Based on Figure 18-2, the following configuration examples provide basic deployment guidelines for implementing the Cisco IOS SSL VPN solution on the Cisco Integrated Services Routers (ISR) series.
Note
The Cisco SSL VPN (WebVPN) feature was introduced in Cisco IOS Software Release 12.3(14)T supporting SSL Version 3.
Example 18-1 shows a generic SSL VPN gateway configuration that includes some of the common features available.
Caution
There is a slight variation in command syntax between Cisco IOS version 12.3T and 12.4T when you are configuring an SSL VPN. Example 18-1 is captured from a Cisco IOS version 12.4T-based router.
Example 18-1. Configuring Cisco IOS SSL VPN
hostname SSL-Gateway
!
aaa new-model
aaa authentication login default local group radius
!
crypto pki trustpoint Gateway
enrollment selfsigned
ip-address 192.168.1.1
revocation-check crl
rsakeypair keys 1024 1024
!
crypto pki certificate chain Gateway
certificate self-signed 02
!
interface Loopback0
ip address 10.10.10.1 255.255.255.0
!
interface GigabitEthernet0/1
ip address 192.168.1.1 255.255.255.0
!
ip local pool svc-pool 10.10.10.100 10.10.10.110
!
webvpn gateway ssl-vpn
ip address 192.168.1.1 port 443
ssl trustpoint Gateway
inservice
!
! The following line is required for SSLVPN Client.
webvpn install svc flash:/webvpn/svc.pkg
!
! The following line is required for Cisco Secure Desktop.
webvpn install csd flash:/webvpn/sdesktop.pkg
!
webvpn context ssl-vpn
ssl authenticate verify all
!
policy group default
! The following line enables SSLVPN Client.
functions svc-enabled
! The following line enables clientless Citrix.
citrix enabled
default-group-policy default
! The following line maps this context to the virtual gateway and defines the domain
to use.
gateway ssl-vpn domain sslvpn
! The following line enables Cisco Secure Desktop.
csd enable
inservice
!
<..>
Tip
Refer to the following Cisco technical documentation for further details on configuring Cisco IOS SSL VPN and various other parameters:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios123/123newft/123t/123t_14/g_sslvpn.htm
http://www.cisco.com/en/US/products/ps6441/products_feature_guide09186a00805eeaea.html#wp1356909
The following show and debug commands can be used to verify functionality on a Cisco router (SSL VPN gateway).
• show webvpn sessions
• show webvpn statistics
• show tcp brief all
• debug webvpn
Cisco AnyConnect VPN Client
The Cisco AnyConnect VPN Client is the newly introduced SSL-based VPN client, the next generation of SSL VPN client software. Cisco AnyConnect VPN client provides remote users with secure VPN connections by using the SSL protocol.
Cisco AnyConnect VPN Client solution is available on the following:
• Cisco ASA 5500 Series security appliance running software version 8.0 and later
• Cisco IOS Software Release 12.4(15)T and later
The Cisco AnyConnect is the next-generation SSL VPN Client, replacing the older SVC software.
When using Cisco IOS Software release prior to 12.4(15)T, you should be dynamically loading the older GUI of SVC software when establishing a web-based SSL connection to the SSL server.
However, when using Cisco IOS Software Release 12.4(15)T or later, you should be dynamically loading the newer GUI of Cisco AnyConnect VPN Client software when establishing the connection.
The AnyConnect client supports Microsoft Vista, Microsoft Windows XP, Microsoft Windows 2000, Linux, or Macintosh OS, providing all the benefits of a traditional SSL VPN client and extending enhanced functions support unavailable to a regular clientless SSL VPN connection. Most notably, the AnyConnect client supports the next-generation IPv6 protocol over an IPv4 network.
As illustrated in Figure 18-2, the AnyConnect software client can be automatically downloaded to remote users with any SSL-based browser and dynamically loaded using Java, ActiveX, or .exe files.
Tip
Refer to the following Cisco technical documentation for further details on configuring Cisco AnyConnect VPN Client:
Configuring AnyConnect VPN Client on Cisco IOS Router
http://www.cisco.com/en/US/products/ps6441/products_feature_guide09186a00805eeaea.html
http://www.cisco.com/en/US/products/ps6441/products_feature_guide09186a0080806b10.html
Configuring AnyConnect VPN Client on Cisco ASA Security Appliance
http://www.cisco.com/en/US/docs/security/asa/asa80/configuration/guide/svc.html
http://www.cisco.com/en/US/docs/security/asa/asa80/getting_started/asa5500/quick/guide/ssl_vpn.html
Summary
With the increasing demand of “anywhere” remote access connectivity, using Remote Access VPN technology is the logical solution for providing secure encrypted communications.
Cisco SSL VPN is one of the Remote Access VPN technologies that offers secure remote-access connectivity from any Internet-enabled computer through a standard web browser, thus allowing networks to extend beyond geographical boundaries and providing anytime, anyplace access to a corporate network.
This chapter explained the Cisco SSL VPN solution architecture and basic deployment and implementation guidelines. The chapter also introduced the newly released Cisco AnyConnect VPN Client software.
References
http://www.cisco.com/go/sslvpn
http://www.cisco.com/en/US/products/ps6657/products_ios_protocol_group_home.html
http://www.cisco.com/web/about/security/intelligence/05_08_SSL-VPN-Security.html
http://www.cisco.com/en/US/netsol/ns340/ns394/ns171/netbr09186a00801f0a72.html
http://www.cisco.com/en/US/products/ps6441/products_feature_guide09186a00805eeaea.html
http://www.cisco.com/en/US/products/ps6350/prod_bulletin09186a0080457a84.html#wp1028745
http://www.cisco.com/univercd/cc/td/doc/product/software/ios123/123newft/123t/123t_14/g_sslvpn.htm
http://www.cisco.com/go/iossslvpn
http://www.cisco.com/en/US/products/ps6657/products_data_sheet0900aecd80405e25.html
http://www.cisco.com/en/US/docs/security/vpn_client/anyconnect/anyconnect21/release/notes/anyconnect21.html
