Chapter 17
Common Types of Attacks
It's true … you're not paranoid if they really are out to get you. Although “they” probably aren't after you personally, your network—no matter the size—is seriously vulnerable, so it's wise to be very concerned about keeping it secure. Unfortunately, it's also true that no matter how secure you think your network is, it's a good bet that there are still some very real threats out there that could breach its security and totally cripple your infrastructure!
I'm not trying to scare you; it's just that networks, by their very nature, are not secure environments. Think about it—the whole point of having a network is to make resources available to people who aren't at the same physical location as the network's resources.
Because of this, it follows that you've got to open access to those resources to users you may not be able to identify. One network administrator I know referred to a server running a much-maligned network operating system as “a perfectly secure server until you install the NIC.” You can see the dilemma here, right?
Okay, with all this doom and gloom, what's a network administrator to do? Well, the first line of defense is to know about the types of threats out there because you can't do anything to protect yourself from something you don't know about. But once you understand the threats, you can begin to design defenses to combat bad guys lurking in the depths of cyberspace just waiting for an opportunity to strike.
I'm going to introduce you to some of the more common security threats and teach you about the ways to mitigate them. I'll be honest—the information I'll be giving you in this chapter is definitely not exhaustive. Securing computers and networks is a huge task and there are literally hundreds of books on this subject alone. To operate securely in a network environment, one must understand how to speak the language of security. As in any field there is specific terminology.
In this chapter you will learn the common types of attacks that all network professionals should understand to secure an enterprise network.
Technology-Based Attacks
Technology-based attacks are those that take advantage of weaknesses in software and the protocols that systems use to communicate with one another. This is in contrast to attacks that target environmental or human weaknesses (covered later in this chapter). In the following sections, you'll learn about attacks that target technologies.
Denial of Service (DoS)/Distributed Denial of Service (DDoS)
A denial of service (DoS) attack does exactly what it sounds like it would do—it prevents users from accessing the network and/or its resources. Today, DoS attacks are commonly launched against a major company's intranet and especially its websites. “Joe the Hacker” (formerly a plumber) thinks that if he can make a mess of, say, Microsoft's or Amazon's website, he's done that company some serious damage. And you know what?
He's right!
Even though DoS attacks are nasty, strangely, hackers don't respect other hackers who execute them because they're really easy to deploy. It's true—even a pesky little 10-year-old can execute one and bring you to your knees. (That's just wrong!) This means that “real” bad guys have no respect for someone who uses DoS attacks, and they usually employ much more sophisticated methods of wreaking havoc on you instead. I guess it comes down to that “honor among thieves” thing. Still, know that even though a DoS-type attack won't gain the guilty party any esteemed status among “real” hackers, it's still not exactly a day at the beach to deal with.
Worse, DoS attacks come in a variety of flavors. Let's talk about some of them now.
The Ping of Death
Ping is primarily used to see whether a computer is responding to IP requests. Usually, when you ping a remote host, what you're really doing is sending four normal-sized Internet Control Message Protocol (ICMP) packets to the remote host to see if it's available. But during a Ping of Death attack, a humongous ICMP packet is sent to the remote host victim, totally flooding the victim's buffer and causing the system to reboot or helplessly hang there, drowning. It's good to know that patches are available for most operating systems to prevent a Ping of Death attack from working.
Distributed DoS (DDoS)
Denial of service attacks can be made more effective if they can be amplified by recruiting helpers in the attack process. In the following sections, some terms and concepts that apply to a distributed denial of service attack are explained.
Botnet/Command and Control
A botnet is a group of programs connected on the Internet for the purpose of performing a task in a coordinated manner. Some botnets, such as those created to maintain control of Internet Relay Chat (IRC) channels, are legal, while others are illegally created to foist a DDoS. An attacker can recruit and build a botnet to help amplify a DoS attack, as illustrated in Figure 17.1.

FIGURE 17.1 Botnet
The steps in the process of building a botnet are as follows:
- A botnet operator sends out viruses or worms whose payloads are malicious applications, the bots, infecting ordinary users' computers.
- The bots on the infected PCs log into a server called a command and control (C&C) server under the control of the attacker.
- At the appropriate time, the attacker, through the C&C server, sends a command to all bots to attack the victim at the same time, thereby significantly amplifying the effect of the attack.
Traffic Spike
One of the hallmarks of a DDoS attack is a major spike in traffic in the network as bots that have been recruited mount the attack. For this reason, any major spike in traffic should be regarded with suspicion. A network intrusion detection system (IDS) can recognize these traffic spikes and may be able to prevent them from growing larger or in some cases prevent the traffic in the first place.
Some smaller organizations that cannot afford some of the pricier intrusion prevention systems (IPSs) or IDSs make use of features present on their load balancers. Many of these products include DDoS mitigation features such as the TCP SYN cookie option. This allows the load balancer to react when the number of SYN requests reaches a certain point. At that point, the device will start dropping requests when the SYN queue is full.
Coordinated Attack
Another unmistakable feature of a DDoS attack is the presence of a coordinated attack. As shown in Figure 17.1 and as just described in the section “Botnet/Command and Control,” to properly amplify the attack, the bots must attack the victim at the same time. The coordination of the bots is orchestrated by the command and control server depicted in Figure 17.1. If all the bots can be instructed to attack at precisely the same second, the attack becomes much more dangerous to the victim.
Friendly/Unintentional DoS
An unintentional DoS attack (also referred to as attack from “friendly fire”) is not one that is not caused by malicious individuals; instead, it's a spike in activity to a website or resource that overpowers its ability to respond. In many cases, it is the result of a relatively unknown URL suddenly being shared in a larger medium such as a popular TV or news show. For example, when Michael Jackson died, the amount of Twitter and Google traffic spiked so much that at first it was thought that an automated attack was under way.
Physical Attack
Physical attacks are those that cause hardware damage to a device. These attacks can be mitigated, but not eliminated, by preventing physical access to the device. Routers, switches, firewalls, servers, and other infrastructure devices should be locked away and protected by strong access controls. Otherwise, you may be confronted with a permanent DoS, which is discussed next.
Permanent DoS
A permanent DoS attack is one in which the device is damaged and must be replaced. It requires physical access to the device, or does it? Actually, it doesn't! An attack called a phlashing denial of service (PDoS) attacks the firmware located in many systems. Using tools that fuzz (introduce errors) the firmware, attackers cause the device to be unusable.
Another approach is to introduce a firmware image containing a Trojan or other types of malware.
Smurf
Smurfs are happy little blue creatures that like to sing and dance, but a Smurf attack is far more nefarious. It's a version of a DoS attack that floods its victim with spoofed broadcast ping messages. I'll talk about spoofing in more detail later; for now, understand that it basically involves stealing someone else's IP address.
Here's how it works: The bad guy spoofs the intended victim's IP address and then sends a large number of pings (IP echo requests) to IP broadcast addresses. The receiving router responds by delivering the broadcast to all hosts in the subnet, and all the hosts respond with an IP echo reply—all of them at the same time. On a network with hundreds of hosts, this results in major network gridlock because all the machines are kept busy responding to each echo request. The situation is even worse if the routers have not been configured to keep these types of broadcasts confined to the local subnet (which thankfully they are by default!). Figure 17.2 shows a Smurf attack in progress.
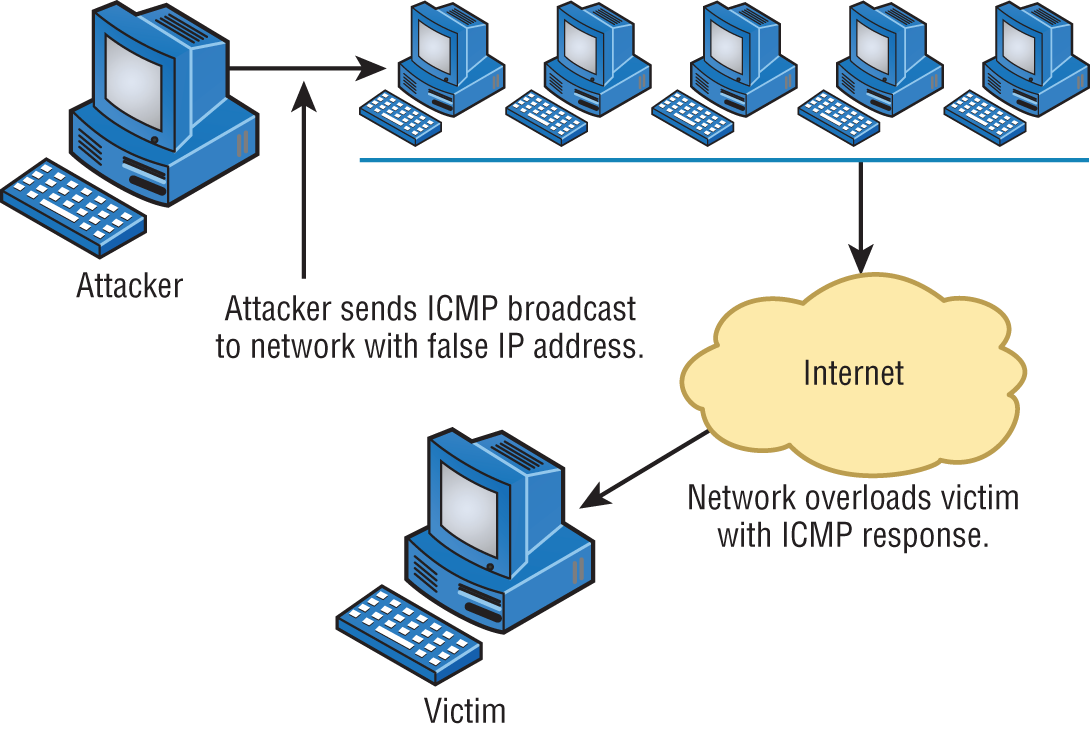
FIGURE 17.2 Smurf attack
Fortunately, Smurf attacks aren't very common anymore because most routers are configured in a way that prevents them from forwarding broadcast packets to other networks. Plus, it's really easy to configure routers and hosts so they won't respond to ping requests directed toward broadcast addresses.
SYN Flood
A SYN flood is also a DoS attack that inundates the receiving machine with lots of packets that cause the victim to waste resources by holding connections open. In normal communications, a workstation that wants to open a Transmission Control Protocol/Internet Protocol (TCP/IP) communication with a server sends a TCP/IP packet with the SYN flag set to 1. The server automatically responds to the request, indicating that it's ready to start communicating with a SYN-ACK. In the SYN flood, the attacker sends a SYN, the victim sends back a SYN-ACK, and the attacker leaves the victim waiting for the final ACK. While the server is waiting for the response, a small part of memory is reserved for it. As the SYNs continue to arrive, memory is gradually consumed.
Figure 17.3 shows an example of a simple DoS/SYN flood attack.
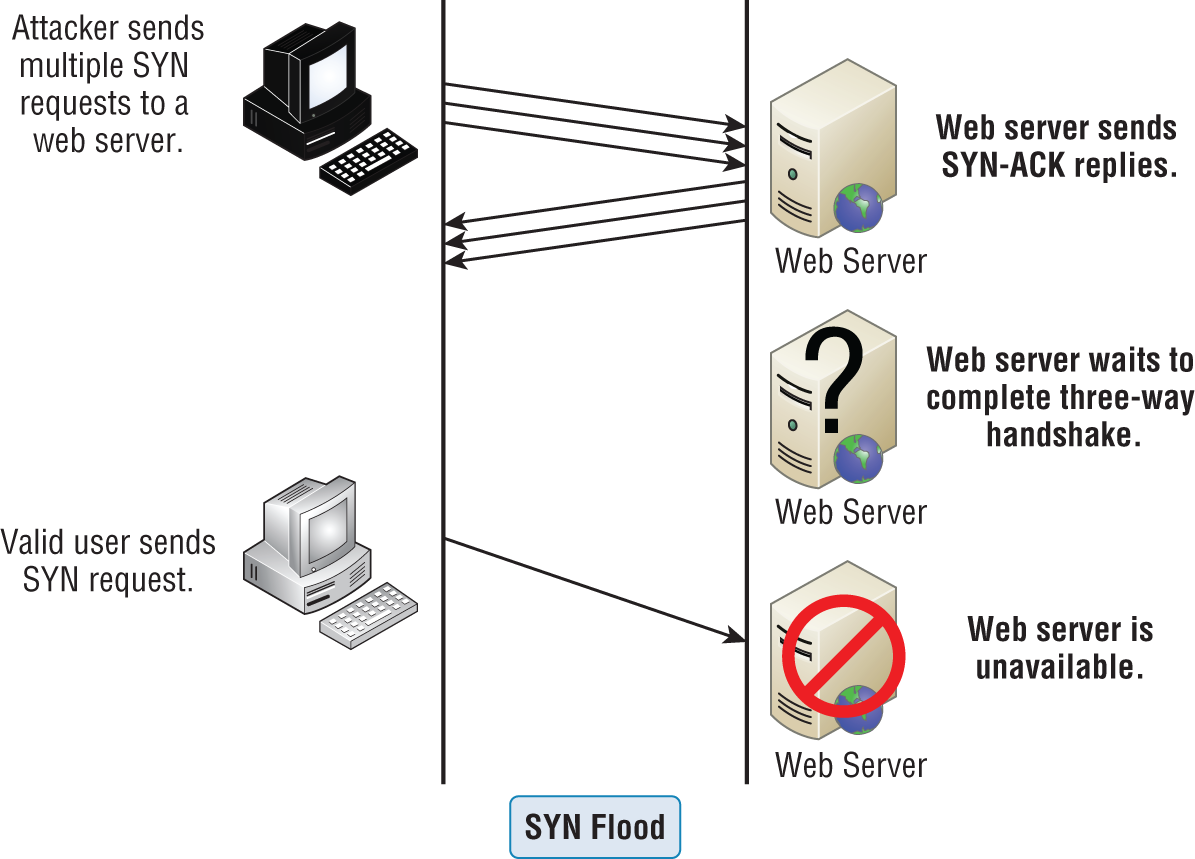
FIGURE 17.3 SYN flood
You can see that the preyed-upon machine can't respond to any other requests because its buffers are already overloaded, and it therefore rejects all packets requesting connections, even valid ones, which is the idea behind the attack. The good news is that patches to help guard against this type of attack are available for the various network operating systems today.
Reflected/Amplified Attacks
Reflected or amplified attacks increase the effectiveness of a DoS attack. Two of the more effective of these types of attacks involve leveraging two functions that almost all networks use, DNS and NTP. In the next two sections these attacks are described.
DNS
A DNS amplification attack is a form of reflection attack in that the attacker delivers traffic to the victim by reflecting it off a third party. Reflection conceals the source of the attack. It relies on the exploitation of publicly accessible open DNS servers to deluge victims with DNS response traffic.
The attacker sends a small DNS message using the victim's IP address as the source to an open resolver. The type of request used returns all known information about the DNS zone, which allows for the maximum level of response amplification directed to the victim's server. The attack is magnified by recruiting a botnet to send the small messages to a large list of open resolvers (DNS servers). The response from the DNS server overwhelms the victim, as shown in Figure 17.4.
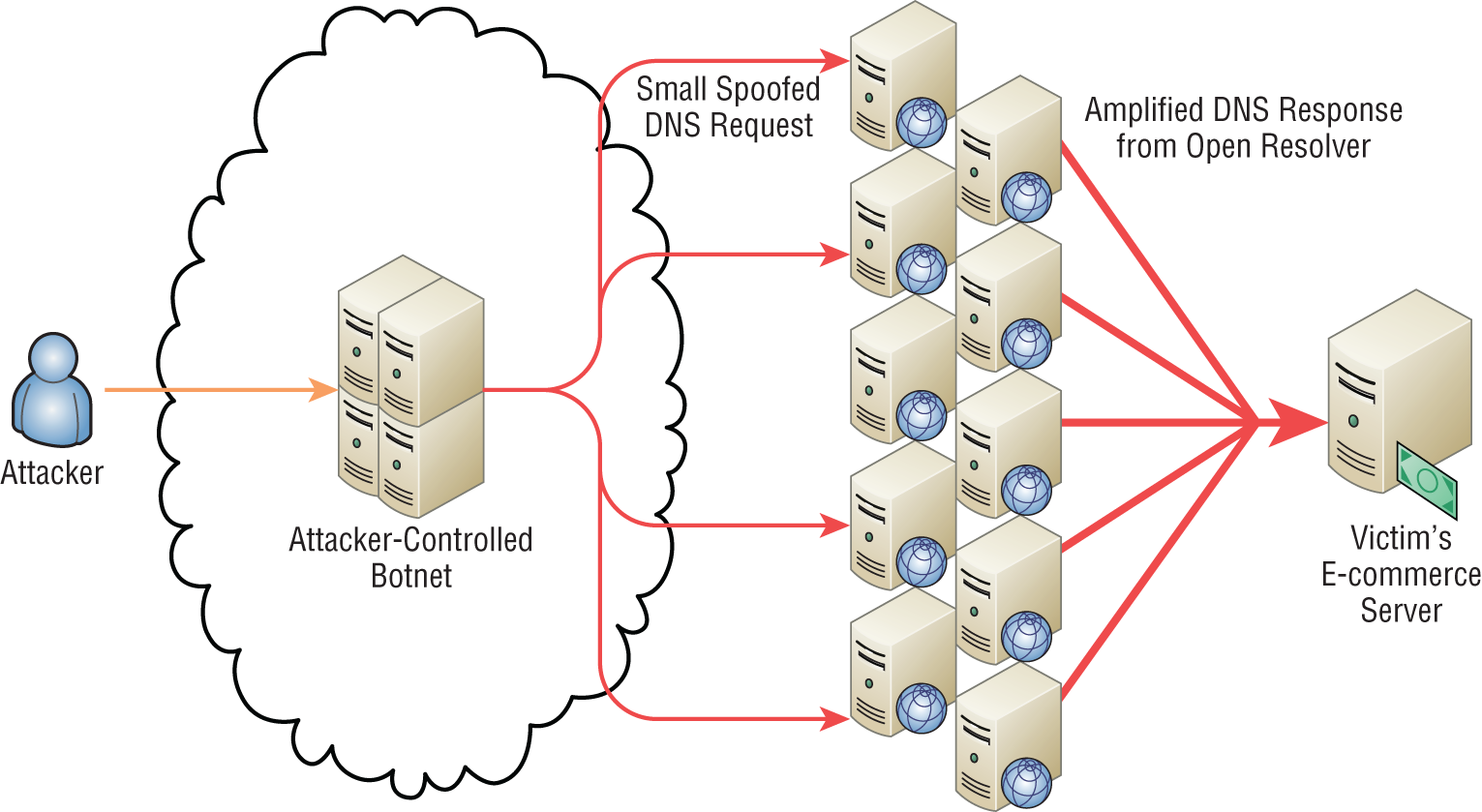
FIGURE 17.4 DNS amplification attack
NTP
While NTP refection attacks use the same process of recruiting bots to aid the attack, the attacks are not reflected off DNS servers; they are instead reflected off Network Time Protocol (NTP) servers. These servers are used to maintain time synchronization between devices in a network.
The attacker (and his bots) sends a small spoofed 8-byte UDP packet to vulnerable NTP servers that requests a large amount of data (megabytes worth of traffic) to be sent to the DDoS's target IP address. The attackers use the monlist command, a remote command in older versions of NTP, that sends the requester a list of the last 600 hosts who have connected to that server. This attack can be prevented by using at least the NTP version 4.2.7 (which was released in 2010).
On-Path Attack (Previously Known as Man-in-the-Middle Attack)
Interception! But it's not a football, it's a bunch of your network's packets—your precious data. An on-path attack (previously known as a man-in-the-middle attack) happens when someone intercepts packets intended for one computer and reads the data. A common guilty party could be someone working for your very own ISP using a packet sniffer and augmenting it with routing and transport protocols. Rogue ATM machines and even credit-card swipers are tools that are also increasingly used for this type of attack. Figure 17.5 shows an on-path/man-in-the-middle attack.
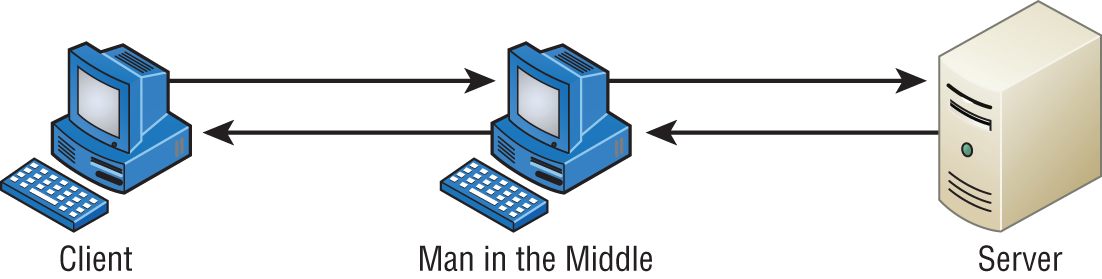
FIGURE 17.5 On-path attack
DNS Poisoning
DNS clients send requests for name to IP address resolution (called queries) to a DNS server. The search for the IP address that goes with a computer or domain name usually starts with a local DNS server that is not authoritative for the DNS domain in which the requested computer or website resides. When this occurs, the local DNS server makes a request of the DNS server that does hold the record in question. After the local DNS server receives the answer, it returns it to the local DNS client. After this, the local DNS server maintains that record in its DNS cache for a period called the time to live (TTL), which is usually an hour but can vary.
In a DNS cache poisoning attack, the attacker attempts to refresh or update that record when it expires with a different address than the correct address. If the attacker can convince the DNS server to accept this refresh, the local DNS server will then be responding to client requests for that computer with the address inserted by the attacker. Typically, the address they now receive is for a fake website that appears to look in every way like the site the client is requesting. The hacker can then harvest all the name and password combinations entered on his fake site.
To prevent this type of attack, the DNS servers should be limited in the updates they accept. In most DNS software, you can restrict the DNS servers from which a server will accept updates. This can help prevent the server from accepting these false updates.
VLAN Hopping
VLANs, or virtual LANs, are layer 2 subdivisions of the ports in a single switch. A VLAN may also span multiple switches. When devices are segregated into VLANs, access control lists (ACLs) can be used in a router to control access between VLANs in the same way it is done between real LANs. When VLANs span switches, the connection between the switches is called a trunk link, and it carries the traffic of multiple VLANs. Trunk links are also used for the connection from the switch to the router.
A VLAN hopping attack results in traffic from one VLAN being sent to the wrong VLAN. Normally, this is prevented by the trunking protocol placing a VLAN tag in the packet to identify the VLAN to which the traffic belongs. The attacker can circumvent this by a process called double tagging, which is placing a fake VLAN tag into the packet along with the real tag. When the frame goes through multiple switches, the real tag is taken off by the first switch, leaving the fake tag. When the frame reaches the second switch, the fake tag is read and the frame is sent to the VLAN to which the hacker intended the frame to go.
This process is shown in Figure 17.6.
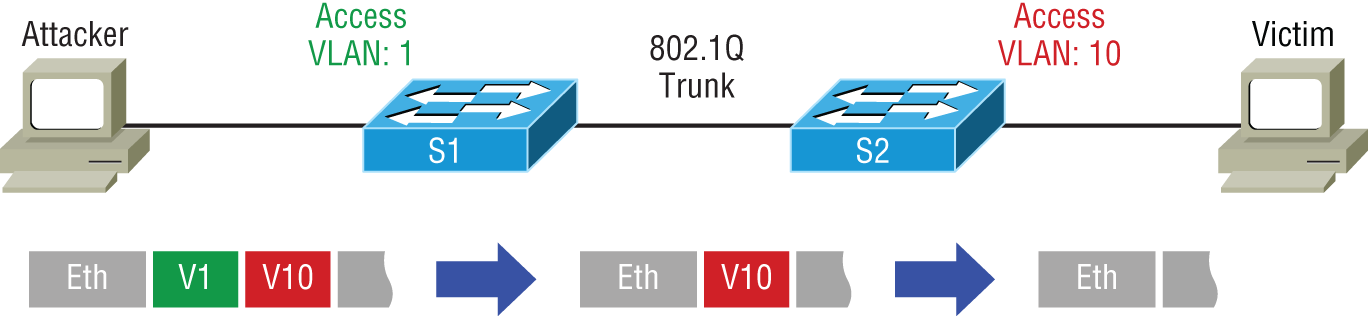
FIGURE 17.6 VLAN hopping
ARP Spoofing
ARP spoofing is the process of adopting another system's MAC address for the purpose of receiving data meant for that system. It usually also entails ARP cache poisoning. ARP cache poisoning is usually a part of an on-path/man-in-the middle attack. The ARP cache contains IP address–to–MAC address mappings that a device has learned through the ARP process. One of the ways this cache can be poisoned is by pinging a device with a spoofed IP address. In this way, an attacker can force the victim to insert an incorrect IP address–to–MAC address mapping into its ARP cache. If the attacker can accomplish this with two computers having a conversation, they can effectively be placed in the middle of the transmission. After the ARP cache is poisoned on both machines, they will be sending data packets to the attacker, all the while thinking they are sending them to the other member of the conversation.
Rogue DHCP
Dynamic Host Configuration Protocol (DHCP) is used to automate the process of assigning IP configurations to hosts. When configured properly, it reduces administrative overload, reduces the human error inherent in manual assignment, and enhances device mobility. But it introduces a vulnerability that when leveraged by a malicious individual can result in an inability of hosts to communicate (constituting a DoS attack) and peer-to-peer attacks.
When an illegitimate DHCP server (called a rogue DHCP server) is introduced to the network, unsuspecting hosts may accept DHCP Offer packets from the illegitimate DHCP server rather than the legitimate DHCP server. When this occurs, the rogue DHCP server will not only issue the host an incorrect IP address, subnet mask, and default gateway address (which makes a peer-to-peer attack possible), it can also issue an incorrect DNS server address, which will lead to the host relying on the attacker's DNS server for the IP addresses of websites (such as those resembling major banks' websites) that lead to phishing attacks. An example of how this can occur is shown in Figure 17.7.
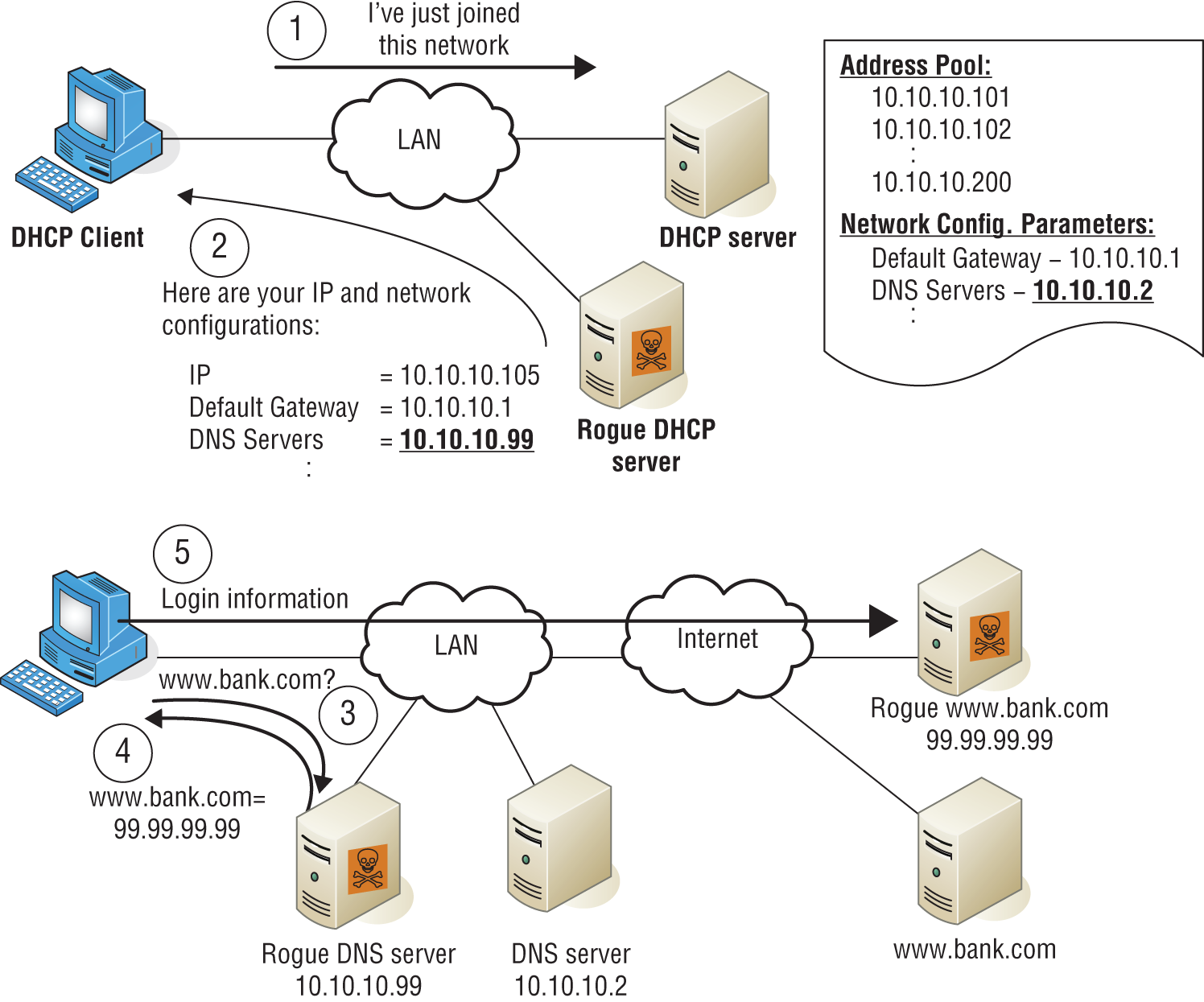
FIGURE 17.7 Rogue DHCP
In Figure 17.7, after receiving an incorrect IP address, subnet mask, default gateway, and DNS server address from the rogue DHCP server, the DHCP client uses the attacker's DNS server to obtain the IP address of his bank. This leads the client to unwittingly connect to the attacker's copy of the bank's website. When the client enters his credentials to log in, the attacker now has the client's bank credentials and can proceed to empty out his account.
Rogue Access Point (AP)
These are APs that have been connected to your wired infrastructure without your knowledge. The rogue AP may have been placed there by a determined hacker who snuck into your facility and put it in an out-of-the-way location or, more innocently, by an employee who just wants wireless access and doesn't get just how dangerous doing this is. Either way, it's just like placing an open Ethernet port out in the parking lot with a sign that says “Corporate LAN access here—no password required!”
Clearly, the worst type of rogue AP is the one some hacker has cleverly slipped into your network. It's particularly nasty because the bad guy probably didn't do it to simply gain access to your network. Nope—the hacker likely did it to entice your wireless clients to disastrously associate with their rogue AP instead! This ugly trick is achieved by placing their AP on a different channel from your legitimate APs and then setting its SSID in accordance with your SSID. Wireless clients identify the network by the SSID, not the MAC address of the AP or the IP address of the AP, so jamming the channel that your AP is on will cause your stations to roam to the bad guy's AP instead. With the proper DHCP software installed on the AP, the hacker can issue the client an address, and once that's been done, the bad guy has basically “kidnapped” your client over to their network and can freely perform a peer-to-peer attack. Believe it or not, this can all be achieved from a laptop while Mr. Hacker simply sits in your parking lot, because there are many types of AP software that will run on a laptop—yikes!
Mitigation
But you're not helpless—one way to keep rogue APs out of the wireless network is to employ a wireless LAN controller (WLC) to manage your APs. This is a nice mitigation technique because APs and controllers communicate using Lightweight Access Point Protocol (LWAPP) or the newer CAPWAP, and it just so happens that one of the message types they share is called Radio Resource Management (RRM). Basically, your APs monitor all channels by momentarily switching from their configured channel and by collecting packets to check for rogue activity. If an AP is detected that isn't usually managed by the controller, it's classified as a rogue, and if a wireless control system is in use, that rogue can be plotted on a floor plan and located. Another great benefit of this mitigation approach is that it enables your APs to also prevent workstations from associating with the newly exposed rogue.
Evil Twin
An evil twin is an AP that is not under your control but is used to perform a hijacking attack. A hijacking attack is one in which the hacker connects one or more of your users' computers to their network for the purpose of a peer-to-peer attack.
The attack begins with the introduction of an access point that is under the hacker's control. This access point will be set to use the same network name or SSID your network uses, and it will be set to require no authentication (creating what is called an open network).
Moreover, this access point will be set to use a different channel than the access point under your control.
To understand how the attack works, you must understand how wireless stations (laptops, tablets, and so on) choose an access point with which to connect. It is done by SSID and not by channel. The hacker will “jam” the channel on which your access point is transmitting. When a station gets disconnected from an access point, it scans the area for another access point with the same SSID. The stations will find the hacker's access point and will connect to it.
Once the station is connected to the hacker's access point, it will receive an IP address from a DHCP server running on the access point and the user will now be located on the same network as the hacker. At this point, the hacker is free to commence a peer-to-peer attack.
Ransomware
Ransomware is a class of malware that prevents or limits users from accessing their information or systems. In many cases the data is encrypted and the decryption key is only made available to the user when the ransom has been paid.
Password Attacks
Password attacks are one of the most common attacks there are. Cracked or disclosed passwords can lead to severe data breaches. The end game of a phishing attack is often to learn a password. In the following sections, you'll learn about the two major approaches to cracking a password.
Brute-Force
A brute-force attack is a form of password cracking. The attacker attempts every possible combination of numbers and letters that could be in a password. Theoretically, given enough time and processing power, any password can be cracked. When long, complex passwords are used, however, it can take years.
Setting an account lockout policy is the simplest mitigation technique to defeat brute-force attacks. With such a policy applied, the account becomes locked after a set number of failed attempts.
Dictionary
Similar to a brute-force attack, a dictionary attack uses all the words in a dictionary until a key is discovered that successfully decrypts the ciphertext. This attack requires considerable time and processing power and is very difficult to complete. It also requires a comprehensive dictionary of words.
An automated program uses the hash of the dictionary word and compares this hash value to entries in the system password file. Although the program comes with a dictionary, attackers also use extra dictionaries that are found on the Internet.
To protect against these attacks, you should implement a security rule that says that a password must not be a word found in the dictionary. You can also implement an account lockout policy so that an account is locked out after a certain number of invalid login attempts.
MAC Spoofing
MAC spoofing is the assumption of another system's MAC address for the following purposes:
- To pass through a MAC address filter
- To receive data intended for another system
- To impersonate a gateway (router interface) for the purpose of receiving all data leaving a subnet.
MAC spoofing is the reason we don't rely solely on security at layer 2 (MAC address filters), while best practices call for basing access on user accounts rather than device properties such as IP addresses or MAC addresses.
IP Spoofing
IP spoofing is the process of changing a source IP address so that one computer appears to be a different computer. It's usually done to get traffic through a firewall that would normally not be allowed. It may also be used to access a server to which the hacker would normally be disallowed access by their IP address.
Deauthentication
A wireless deauthentication attack is a form of a DoS attack in which the attacker sends a large number of management packets called deauthentication frames on the WLAN, causing stations to be disconnected from the access point.
Malware
Malicious software (or malware) is a term that describes any software that harms a computer, deletes data, or takes actions the user did not authorize. There is a wide array of malware types, including ones you have probably heard of, like viruses. Some types of malware require the assistance of a user to spread, while others do not.
A worm is a type of malware that can spread without the assistance of the user. A worm is a small program that, like a virus, is used to deliver a payload. One way to help mitigate the effects of worms is to place limits on sharing, writing, and executing programs.
However, the real solution is to deploy antivirus and antimalware software to all devices in the network. This software is designed to identify viruses, Trojans, and worms and delete them, or at least quarantine them until they can be removed.
Viruses
Viruses with catchy names like Chernobyl, Michelangelo, Melissa, I Love You, and Love Bug are probably the best-known threats to your computer's security because they get a lot of media coverage as they proliferate and cause tons of damage to legions of people. In their simplest form, viruses are basically little programs that cause a variety of very bad things to happen on your computer, ranging from merely annoying to totally devastating. They can display a message, delete files, or even send huge amounts of meaningless data over a network to block legitimate messages. A key trait of viruses is that they can't replicate themselves to other computers or systems without a user doing something like opening an executable attachment in an email to propagate them. Figure 17.8 shows how fast a virus can spread through an email system.
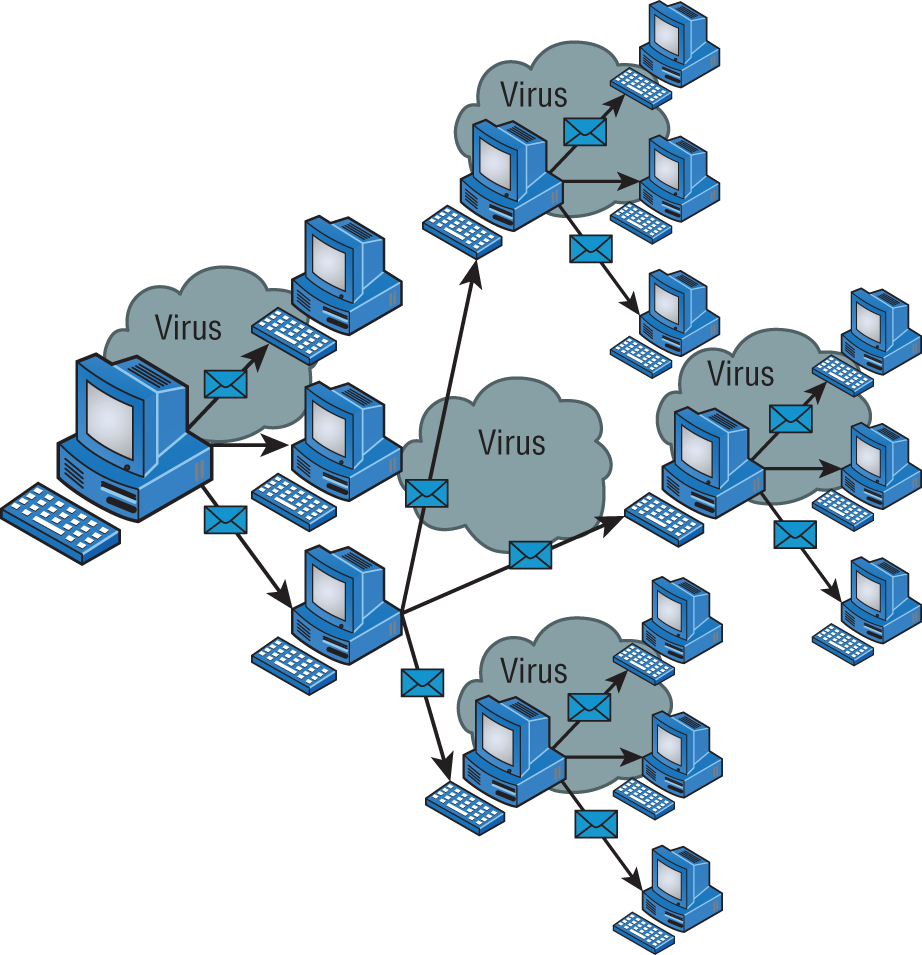
FIGURE 17.8 An email virus spreading rapidly
There are several different kinds of viruses, but the most popular ones are file viruses, macro (data file) viruses, and boot-sector viruses. Each type differs slightly in the way it works and how it infects your system. Predictably, many viruses attack popular applications like Microsoft Word, Excel, and PowerPoint because those programs are easy to use so it's easy to create a virus for them. Unlike with DoS attacks, writing a unique virus is considered a programming challenge, so the scoundrel who's able to come up with it not only gains respect from the hacking community but also gets to bask in the glow of the media frenzy that results from their creation and relish their 15 minutes of fame. This is also a big reason why viruses are becoming more and more complex and harder to eliminate.
Logic Bomb
A logic bomb is a type of malware that executes when a particular event takes place. For example, that event could be a time of day or a specific date or it could be the first time you open notepad.exe. Some logic bombs execute when forensics are being undertaken, and in that case the bomb might delete all digital evidence.
Ransomware
Ransomware is a class of malware that prevents or limits users from accessing their information or systems. In many cases the data is encrypted and the decryption key is only made available to the user when the ransom has been paid.
File Viruses
A file virus attacks executable application and system program files like those with filenames ending in .com, .exe, and .dll. These viruses do their damage by replacing some or all of the target program's code with their own. Only when the compromised file is executed can the virus do its dirty work. First, it loads itself into memory and waits to infect other executables, propagating its destructive effects throughout a system or network. A couple of well-known file viruses are Jerusalem and Nimda, the latter of which is actually an Internet worm that infects common Windows files and other files with filename extensions like .html, .htm, and .asp.
Macro Viruses
A macro is basically a script of commonly enacted commands used to automatically carry out tasks without requiring a user to initiate them. Some popular programs even give you the option of creating your own, personal scripts to perform tasks you do repeatedly in a single step instead of having to enter the individual commands one by one.
Similar to this, a macro virus uses something known as the Visual Basic macro-scripting language to perform nasty things in data files created with programs like those in the Microsoft Office Suite. Because macros are so easy to write, they're really common and usually fairly harmless, but they can be super annoying! People frequently find them infecting the files they're working on in Microsoft Word and PowerPoint. Suddenly you can't save the file even though the Save function is working, or you can't open a new document, only a template. As I said, these viruses won't crash your system, but they can ruin your day. Cap and Cap A are examples of macro viruses.
Boot-Sector Viruses
Boot-sector viruses work their way into the master boot record that's essentially the ground-zero sector on your hard disk where applications aren't supposed to live. When a computer boots up, it checks this area to find a pointer for its operating system. Boot-sector viruses overwrite your boot sector, making it appear as if there's no pointer to your operating system. You know you've got this type of virus when you power up the computer and get a Missing Operating System or Hard Disk Not Found error message. Monkey B, Michelangelo, Stoned, and Stealth Boot are a few examples of boot-sector viruses.
Multipartite Viruses
A multipartite virus is one that affects both the boot sector and files on your computer, making such a virus particularly dangerous and exasperatingly difficult to remove. Figure 17.9 gives you an idea of how a multipartite virus works. You can see that it is attacking the boot sector, memory, and the disk at once.
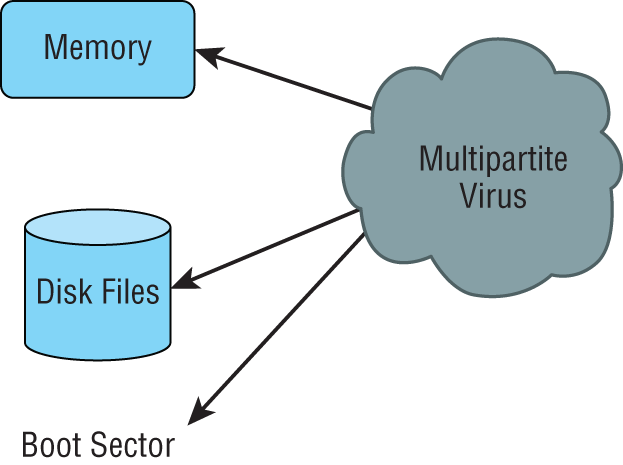
FIGURE 17.9 Botnet
Anthrax and Tequila are both multipartite viruses. These viruses are so nasty that you might end up reformatting your computer if you get one. The Anthrax virus, however, was more of a hoax then a real virus; what is really interesting about the Tequila virus is that it does nothing until the next reboot—it was no hoax!
Although many software companies can handle these, the best way to save your computer from a complete overhaul is to make sure you do not get a virus in the first place by using a good virus scan program as well as Windows Defender.
Zero-Day Attacks
Antivirus software uses definition files that identify known malware. These files must be updated frequently, but the update process can usually be automated so that it requires no help from the user. If a new virus is created that has not yet been identified in the list, you will not be protected until the virus definition is added and the new definition file is downloaded.
This condition is known as a zero-day attack because it is the first day the virus has been released and therefore no known fix exists. This term may also be applied to an operating system bug that has not been corrected.
Human and Environmental
While some vulnerabilities come from technical challenges such as attacks on cryptography and network protocols, many are a result of environmental issues within the facility or of human error and poor network practices by the users (we call these self-inflicted wounds). In the following sections, you'll learn about human and environmental vulnerabilities.
Social Engineering
Hackers are more sophisticated today than they were 10 years ago, but then again, so are network administrators. Because most of today's sys admins have secured their networks well enough to make it pretty tough for an outsider to gain access, hackers decided to try an easier route to gain information: they just asked the network's users for it.
Social engineering attacks occur when attackers use believable language and user gullibility to obtain user credentials or some other confidential information. The best countermeasure against social engineering threats is to provide user security awareness training. This training should be required and must occur on a regular basis because social engineering techniques evolve constantly.
Phishing
Phishing is a social engineering attack in which attackers try to learn personal information, including credit card information and financial data. This type of attack is usually carried out by implementing a fake website that is nearly identical to a legitimate website. Users are led there by fake emails that appear to come from a trusted source. Users enter data, including credentials, on the fake website, allowing the attackers to capture any information entered. Spear phishing is a phishing attack carried out against a specific target by learning about the target's habits and likes. The best defense is security awareness training for the users.
Environmental
Some attacks become possible because of the security environment we have allowed to develop. The following are issues that are created by user behavior.
Tailgating
Tailgating is the term used for someone being so close to you when you enter a building that they are able to come in right behind you without needing to use a key, a card, or any other security device. Many social-engineering intruders who need physical access to a site will use this method of gaining entry. Educate users to beware of this and other social-engineering ploys and prevent them from happening.
Piggybacking
Piggybacking and tailgating are similar but not the same. Piggybacking is done with the authorization of the person with access. Tailgating is done when the attacker sneaks inside without the person with access knowing. This is why access control vestibules (mantraps) and turnstiles deter tailgating and live guards and security training deter piggybacking.
Shoulder Surfing
Shoulder surfing involves nothing more than watching someone when they enter their sensitive data. They can see you entering a password, typing in a credit card number, or entering any other pertinent information. The best defense against this type of attack is simply to survey your environment before entering personal data. Privacy filters can be used that make the screen difficult to read unless you are directly in front of it.
Summary
In this chapter you learned about common attack types that one might expect on an enterprise network. These attack types can be categorized into technology-based attacks and those that are the result of human failure or of the network environment that exists.
Technology-based attacks include denial of service (DoS)/distributed denial of service (DDoS) attacks, on-path attacks, DNS poisoning, VLAN hopping, ARP spoofing, rogue DHCP and rogue access point (AP) attacks, evil twin attacks, ransomware, and password attacks.
Human and environmental attacks include social engineering, phishing, tailgating, piggybacking, and shoulder surfing.
Exam Essentials
- Explain common technology-based attacks. These include denial of service (DoS)/distributed denial of service (DDoS) attacks, on-path attacks, DNS poisoning, VLAN hopping, ARP spoofing, rogue DHCP and rogue access point (AP) attacks, evil twin attacks, ransomware, and password attacks.
- Describe (DoS)/distributed denial-of-service (DDoS) attacks. This includes the architecture and behavior of a botnet and of the role of the command and control server.
- Identify human and environmental attacks. These include social engineering, phishing, tailgating, piggybacking, and shoulder surfing.
Written Lab
Complete the table by filling in the appropriate countermeasure for each attack method.
You can find the answers in Appendix A.
| Attack | Countermeasure |
|---|---|
| Shoulder surfing | |
| Piggybacking | |
| Tailgating | |
| Phishing | |
| Brute-force attack |
Review Questions
You can find the answers to the review questions in Appendix B.
- Which of the following is not a technology-based attack?
- DoS
- Ping of death
- Shoulder surfing
- Malware
- A command and control server is a part of which of the following attacks?
- DDoS
- Ping of death
- Shoulder surfing
- Malware
- Which of the following is a DoS attack that floods its victim with spoofed broadcast ping messages?
- SYN flood
- Smurf
- Land attack
- Ping of death
- Which of the following is an attack that inundates the receiving machine with lots of packets that cause the victim to waste resources by holding connections open?
- Ping of death
- Zero day
- Smurf
- SYN flood
- In which of the following does the attacker (and his bots) send a small spoofed 8-byte UDP packet to vulnerable NTP servers that requests a large amount of data (megabytes worth of traffic) be sent to the DDoS's target IP address?
- SYN flood
- NTP amplification
- Smurf
- DNS amplification
- Which of the following was previously known as a man-in-the-middle attack?
- VLAN hopping
- On-path attack
- LAND attack
- Smurf
- Double tagging is a part of which of the following attacks?
- VLAN hopping
- Smurf
- DDoS
- Malware
- Which of the following is the process of adopting another system's MAC address for the purpose of receiving data meant for that system?
- Certificate spoofing
- ARP spoofing
- IP spoofing
- URL spoofing
- Which of the following is connected to your wired infrastructure without your knowledge?
- Rogue AP
- Command and control server
- Zombies
- Botnet
- Which of the following uses the same SSID as your AP?
- Rogue AP
- Rogue DHCP
- Evil twin
- Zombie
